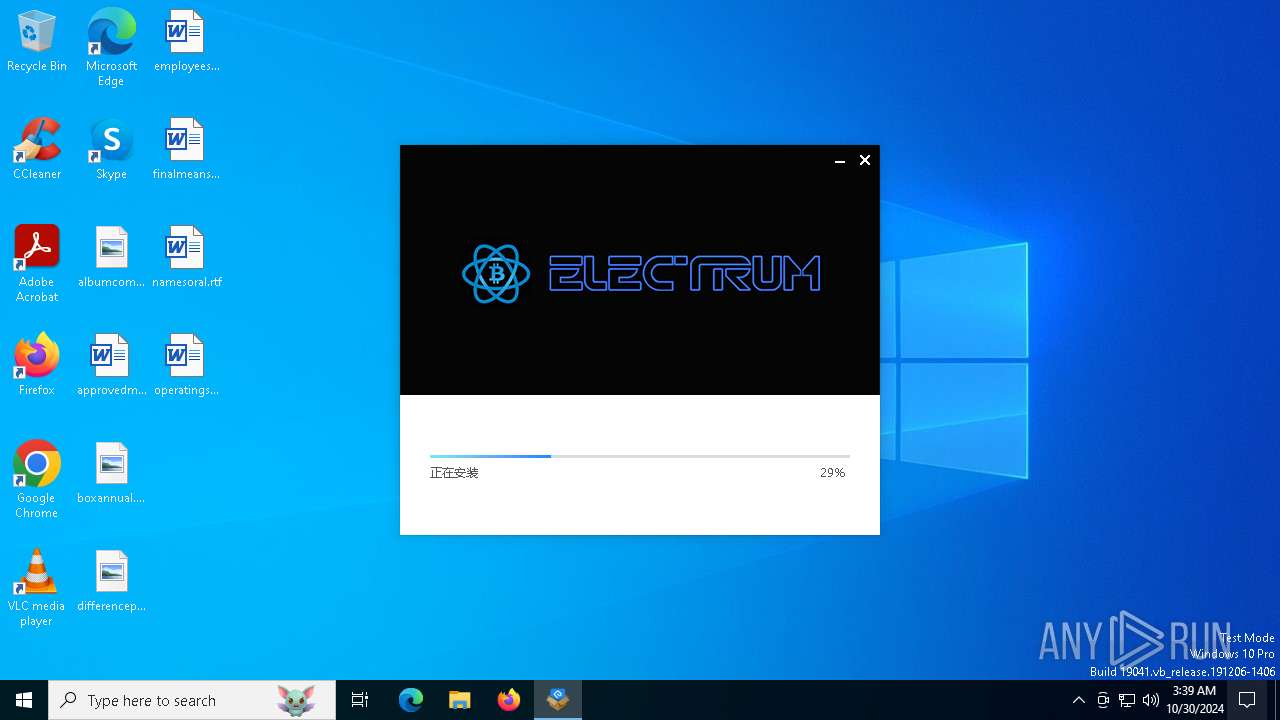
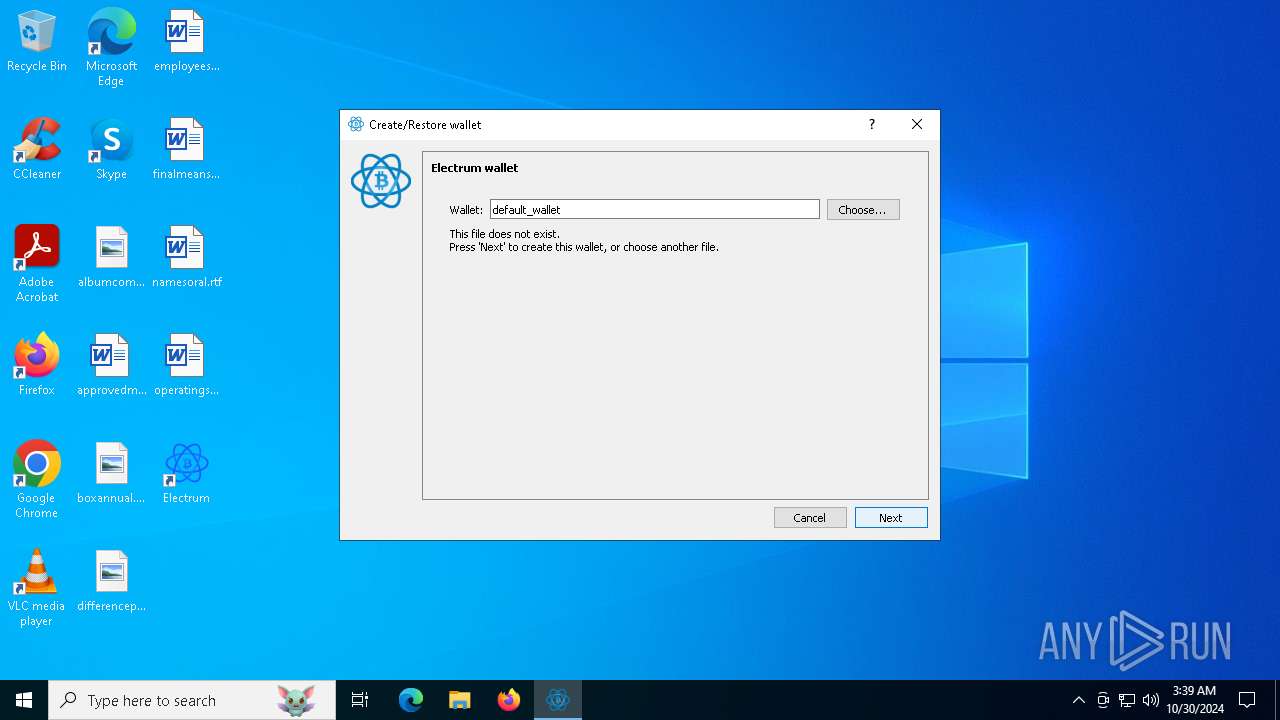
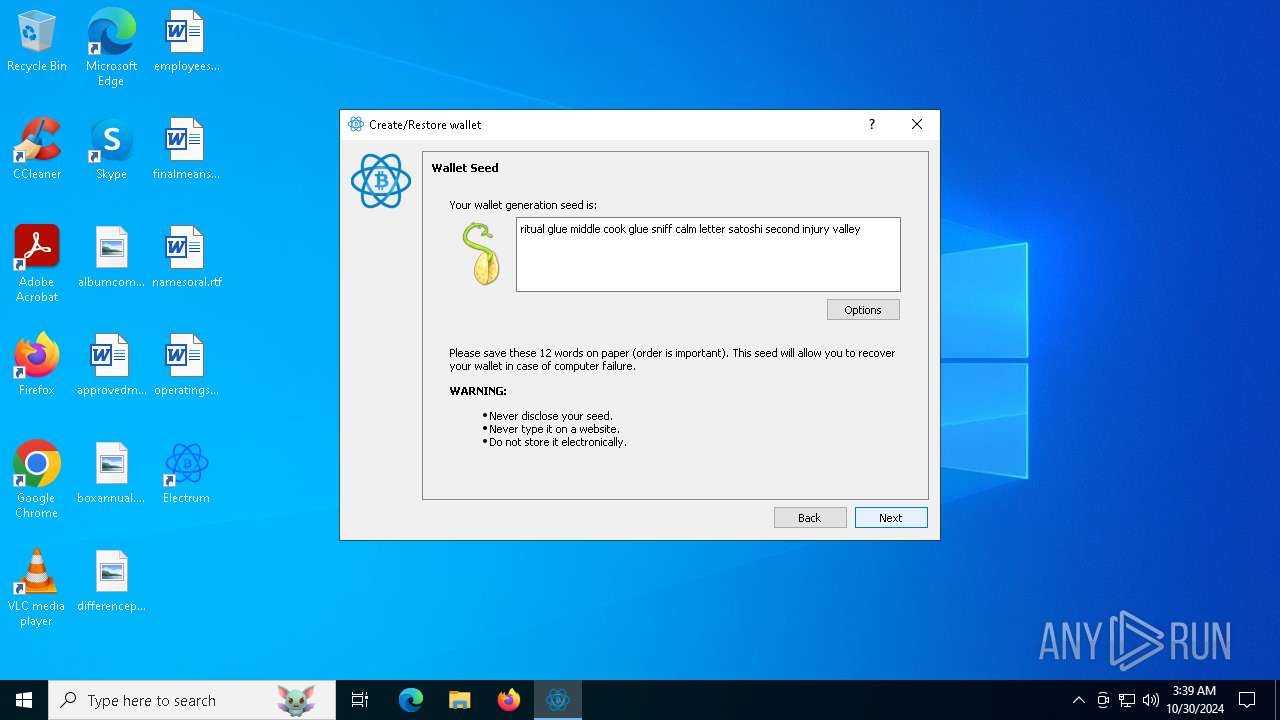
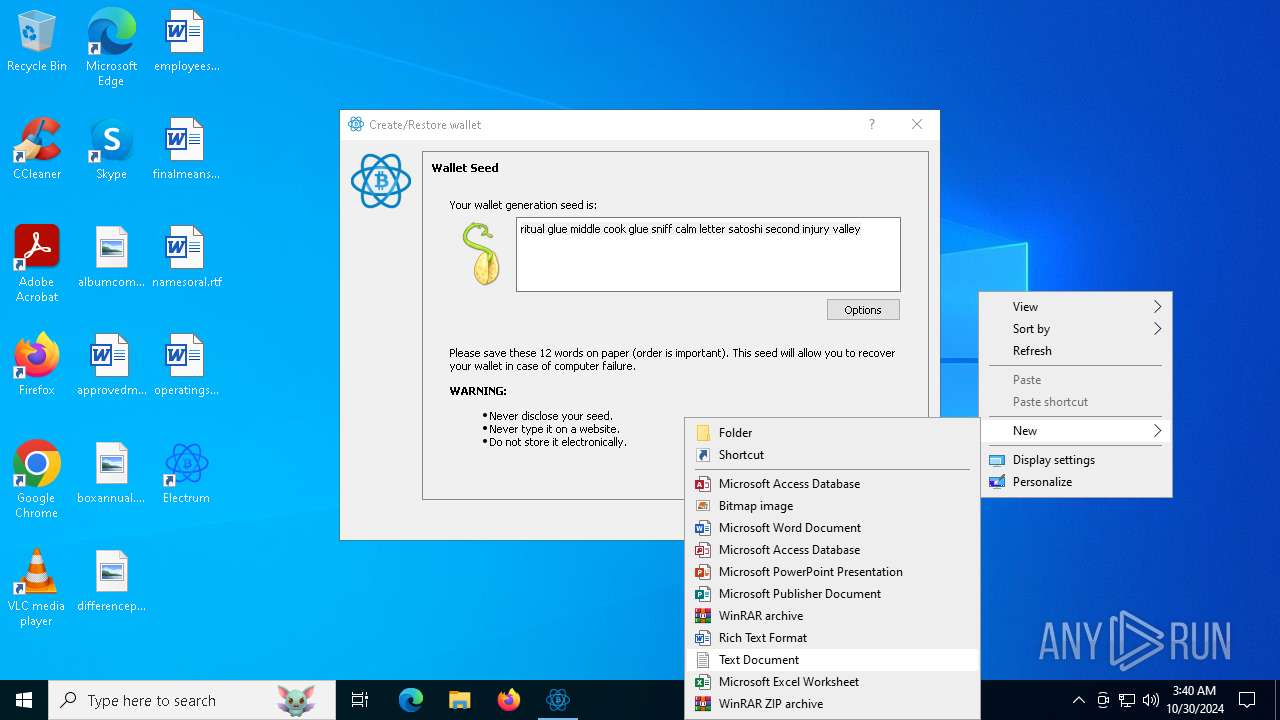
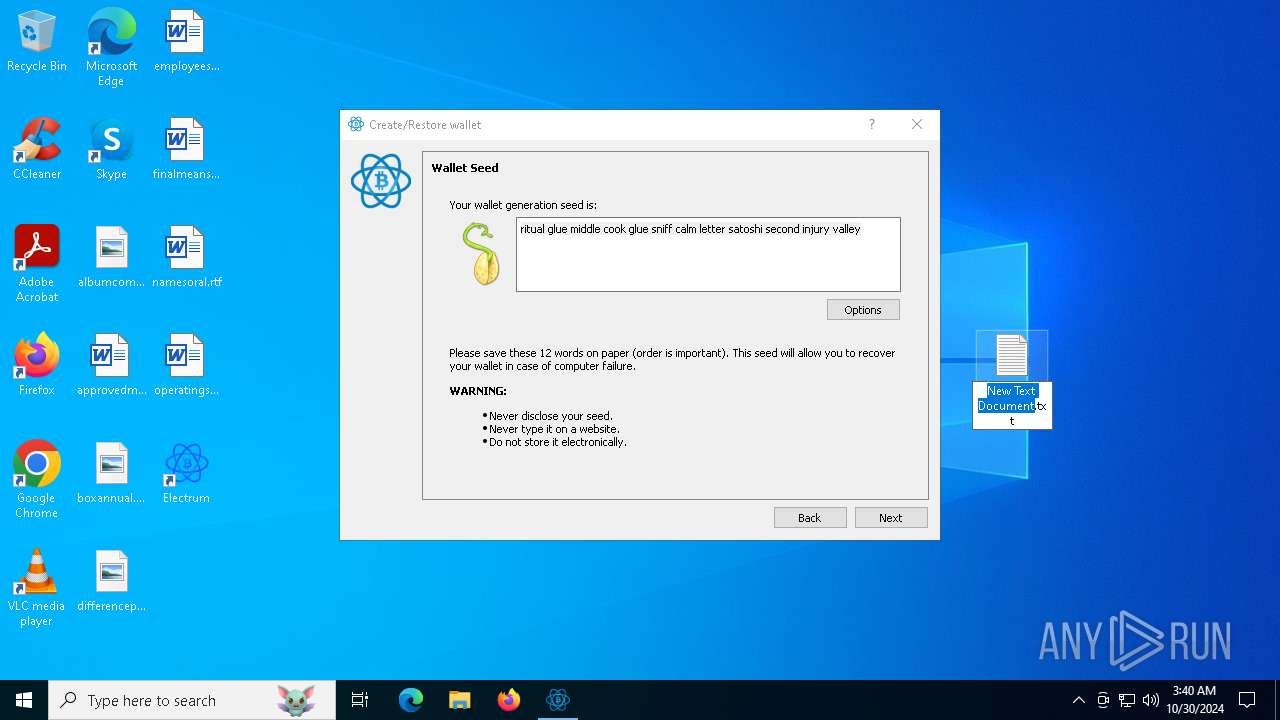
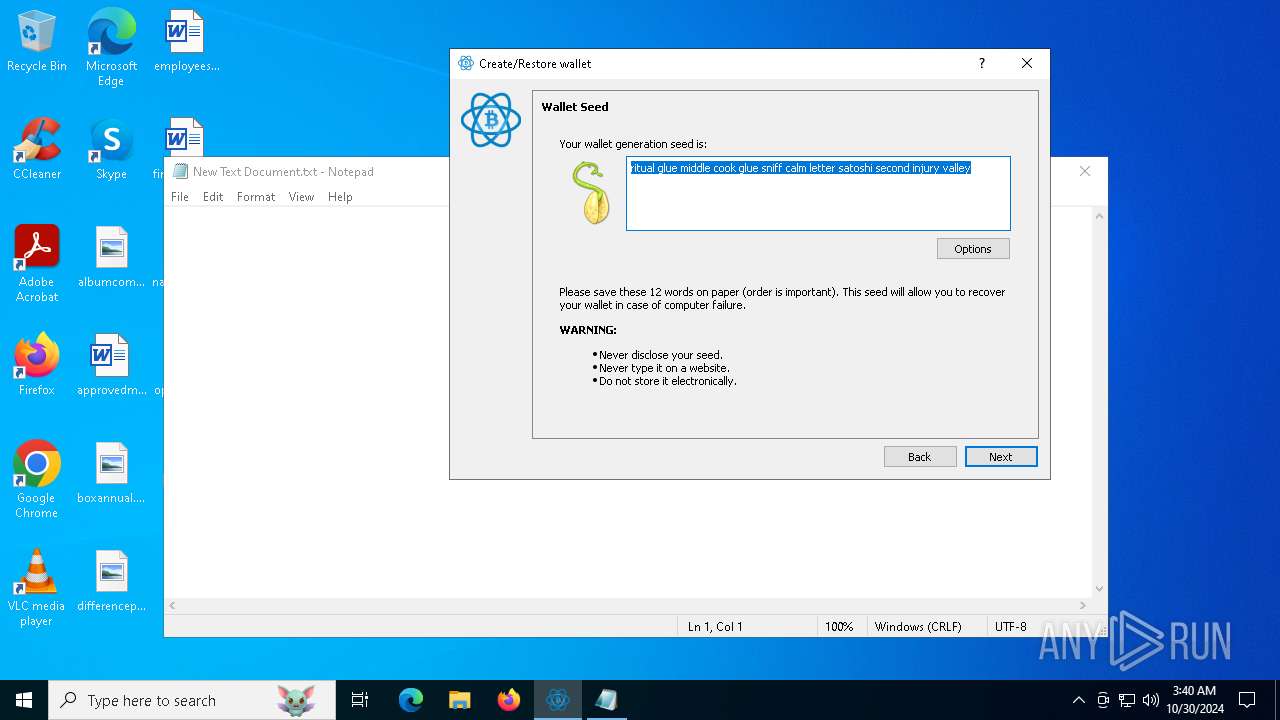
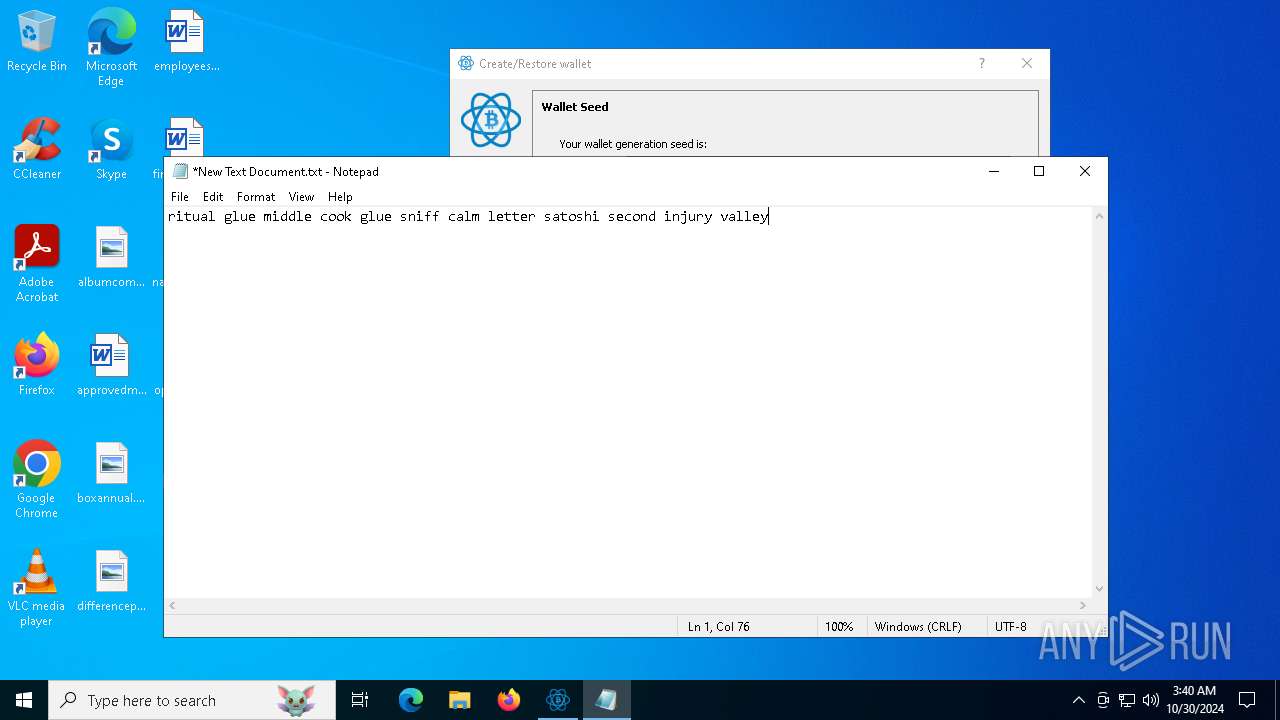
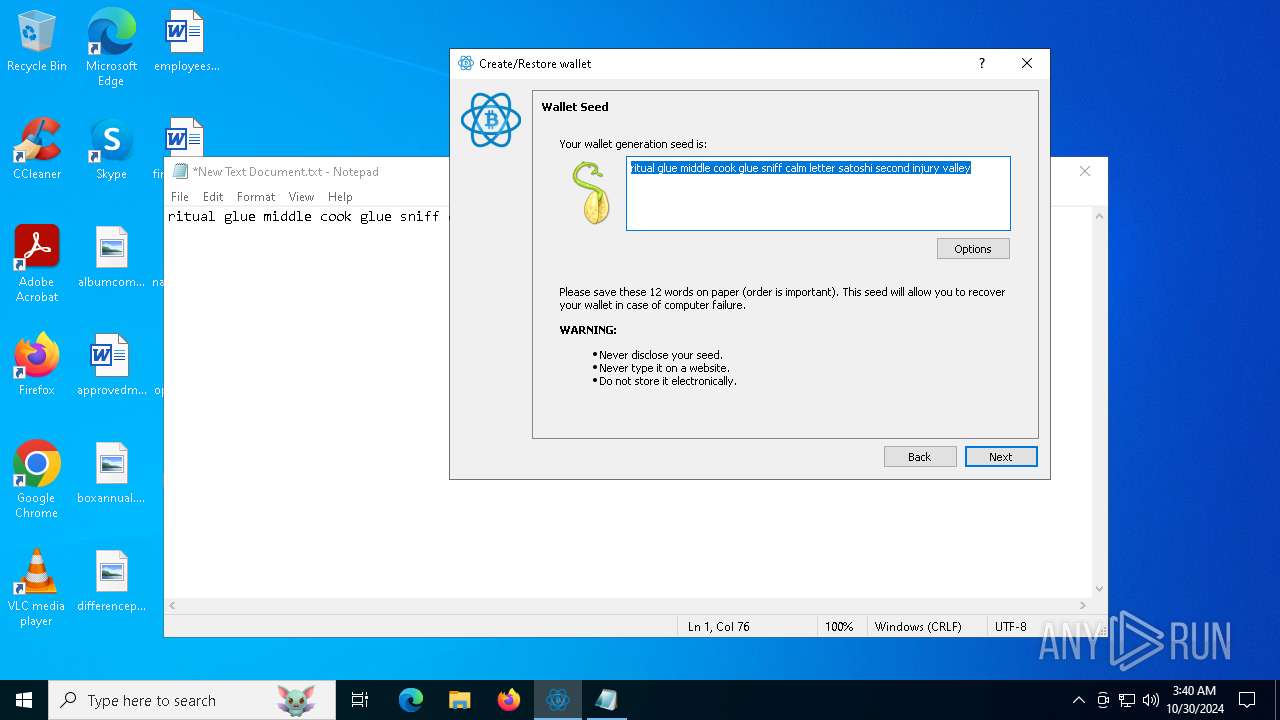
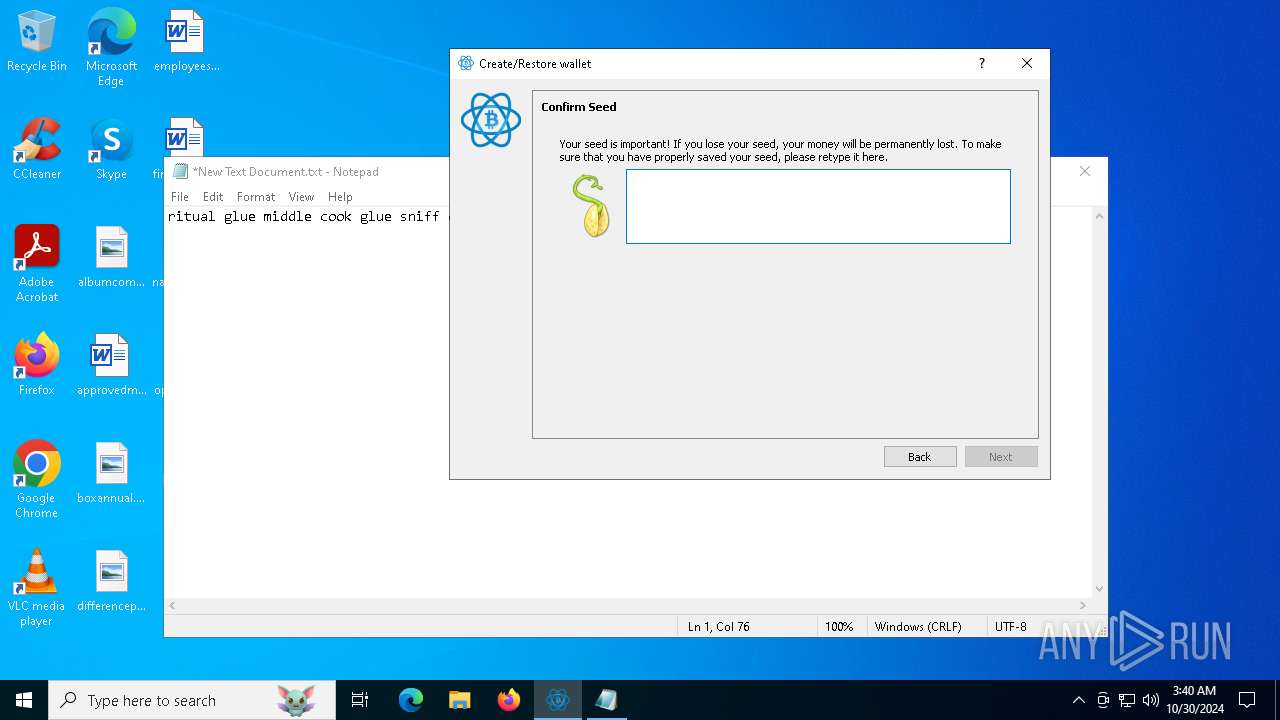
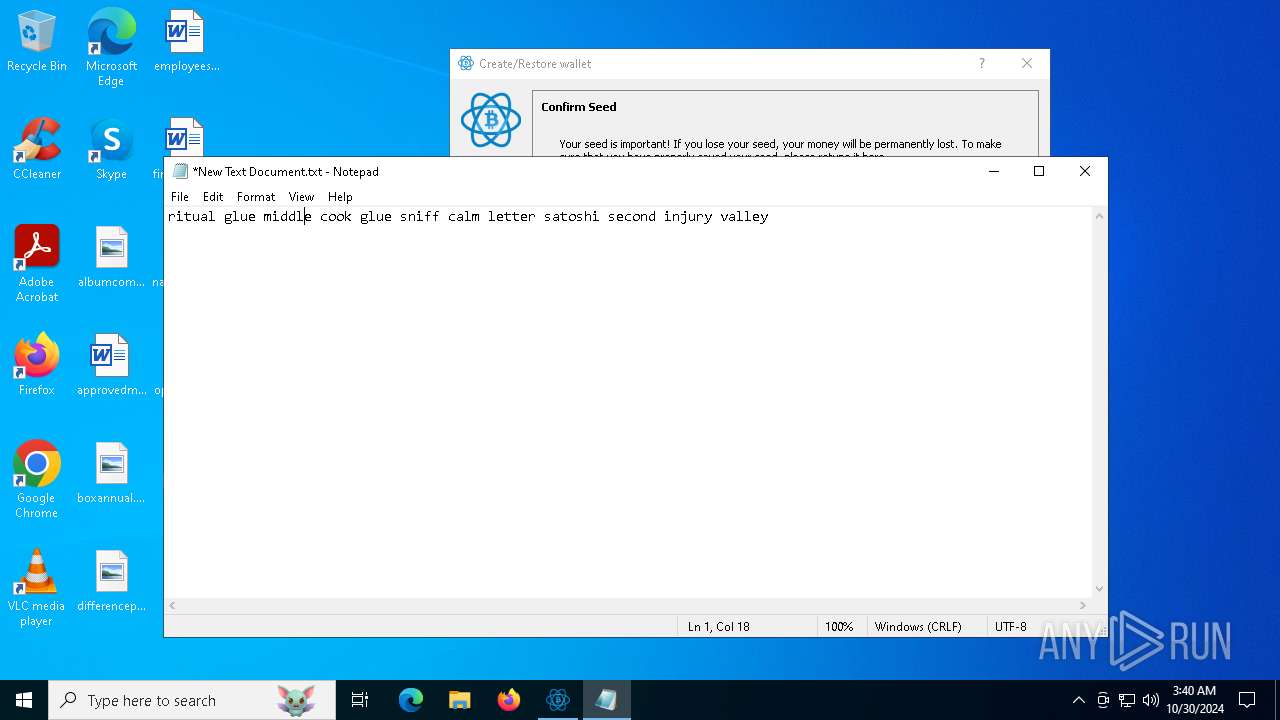
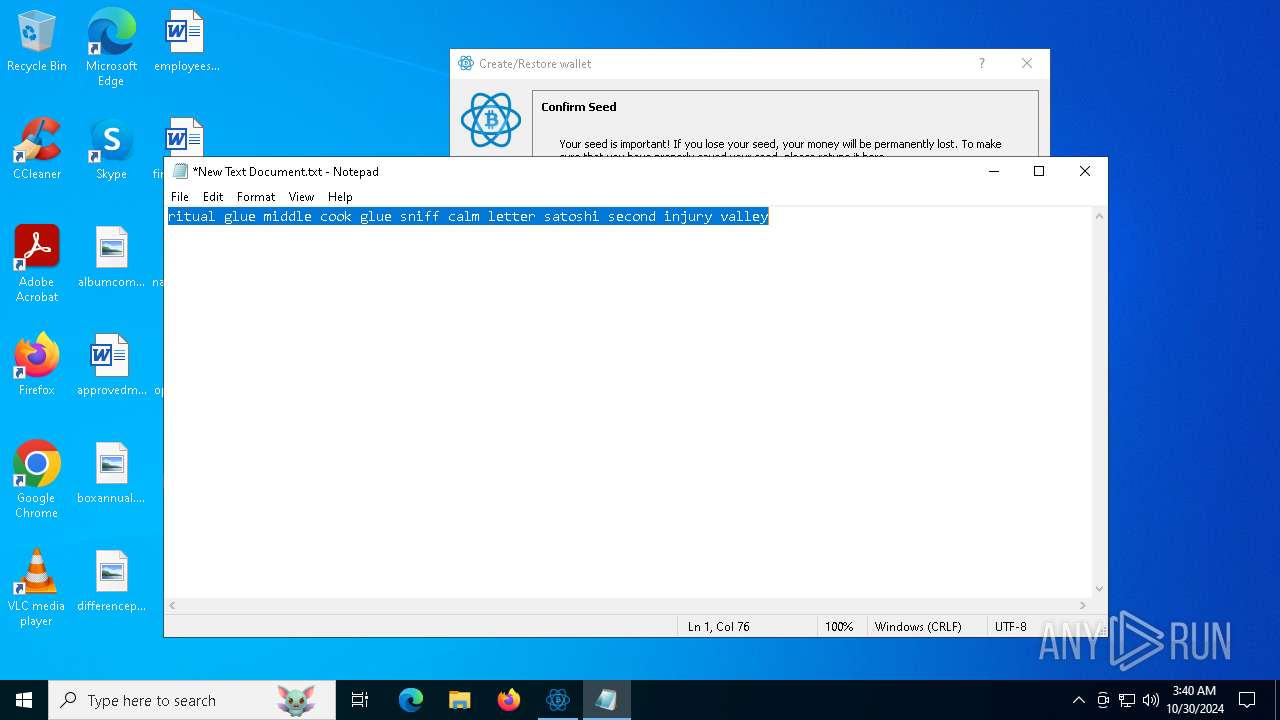
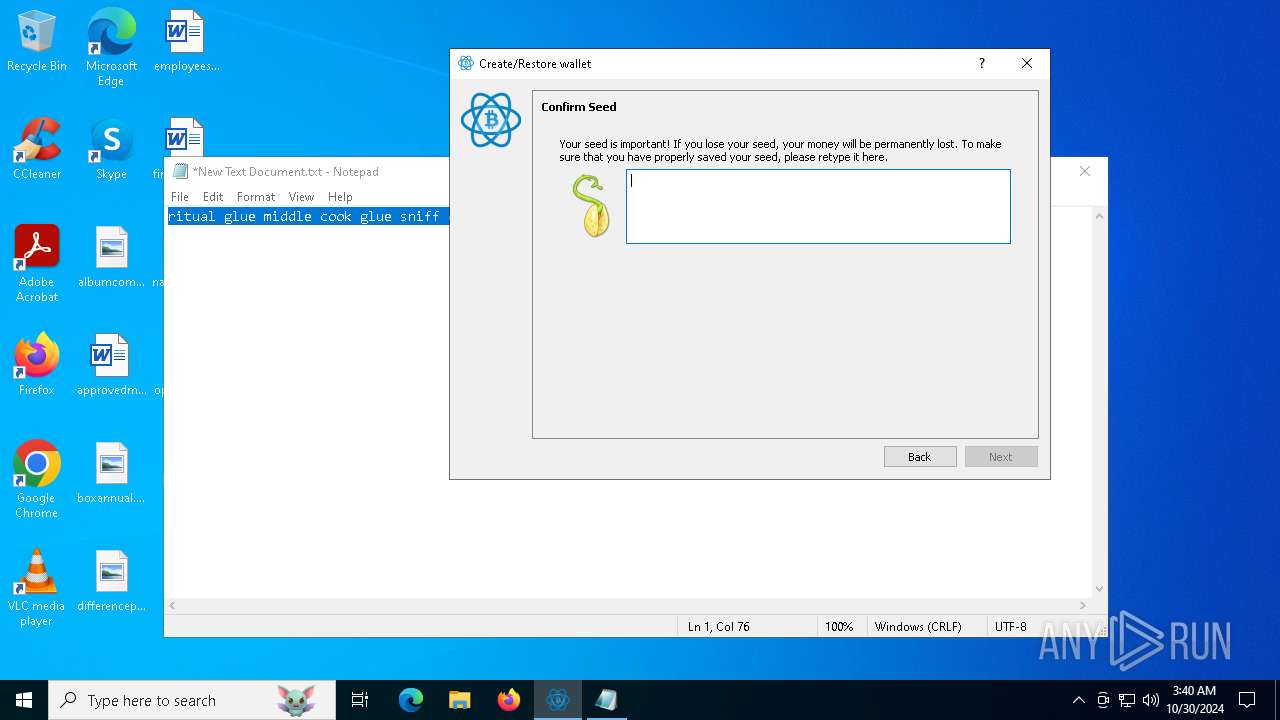
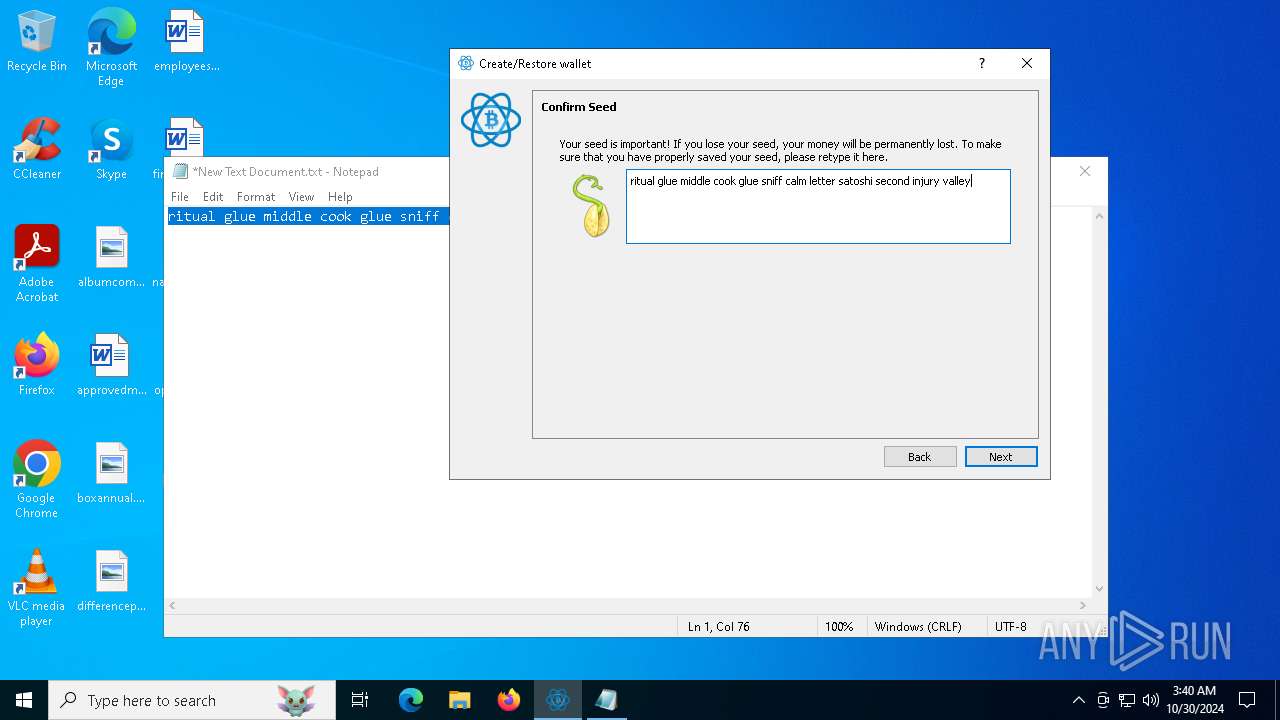
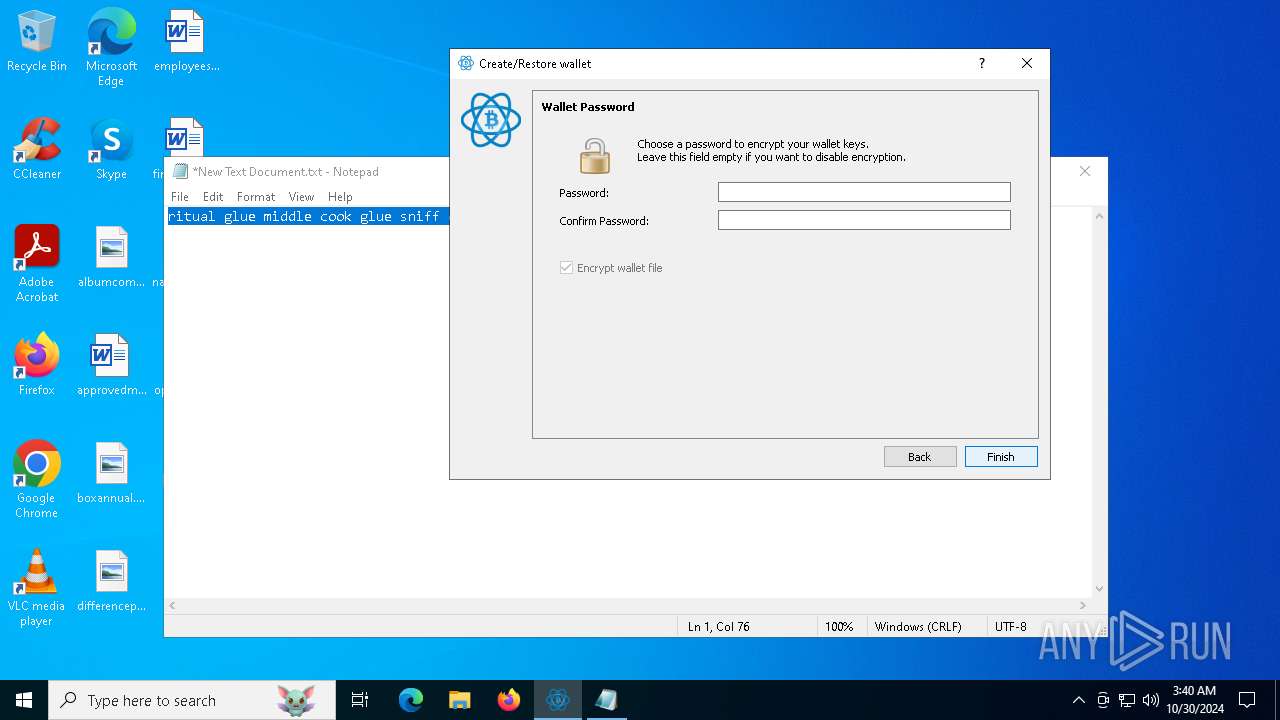
| File name: | electrumx64.exe |
| Full analysis: | https://app.any.run/tasks/22b1b2d5-4683-43f7-8943-02d118f0b7cb |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2024, 03:38:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | CF837466C42AA63D4E4DF0352A8063EF |
| SHA1: | 461A44B862408C89F16F845B7367B51800344A41 |
| SHA256: | 451070B87E0B3ACF9DE1F6FD858BFADBDAF23FE75CD6F56A29EC817946E70A42 |
| SSDEEP: | 393216:hsTjRbSdyHI7cekLo6h1q/la3/yu744BdSwo2:hSCy/Boy1qo3/t7Owo2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- electrumx64.exe (PID: 6812)
The process creates files with name similar to system file names
- electrumx64.exe (PID: 6812)
Executable content was dropped or overwritten
- electrumx64.exe (PID: 6812)
Process drops python dynamic module
- electrumx64.exe (PID: 6812)
Drops 7-zip archiver for unpacking
- electrumx64.exe (PID: 6812)
The process drops C-runtime libraries
- electrumx64.exe (PID: 6812)
Process drops legitimate windows executable
- electrumx64.exe (PID: 6812)
Starts CMD.EXE for commands execution
- electrum-4.5.8.exe (PID: 3108)
Connects to unusual port
- Shextutoply.exe (PID: 1788)
- electrum-4.5.8.exe (PID: 3108)
Potential Corporate Privacy Violation
- electrum-4.5.8.exe (PID: 3108)
INFO
Checks supported languages
- electrumx64.exe (PID: 6812)
Sends debugging messages
- electrumx64.exe (PID: 6812)
Create files in a temporary directory
- electrumx64.exe (PID: 6812)
Reads the computer name
- electrumx64.exe (PID: 6812)
UPX packer has been detected
- electrumx64.exe (PID: 6812)
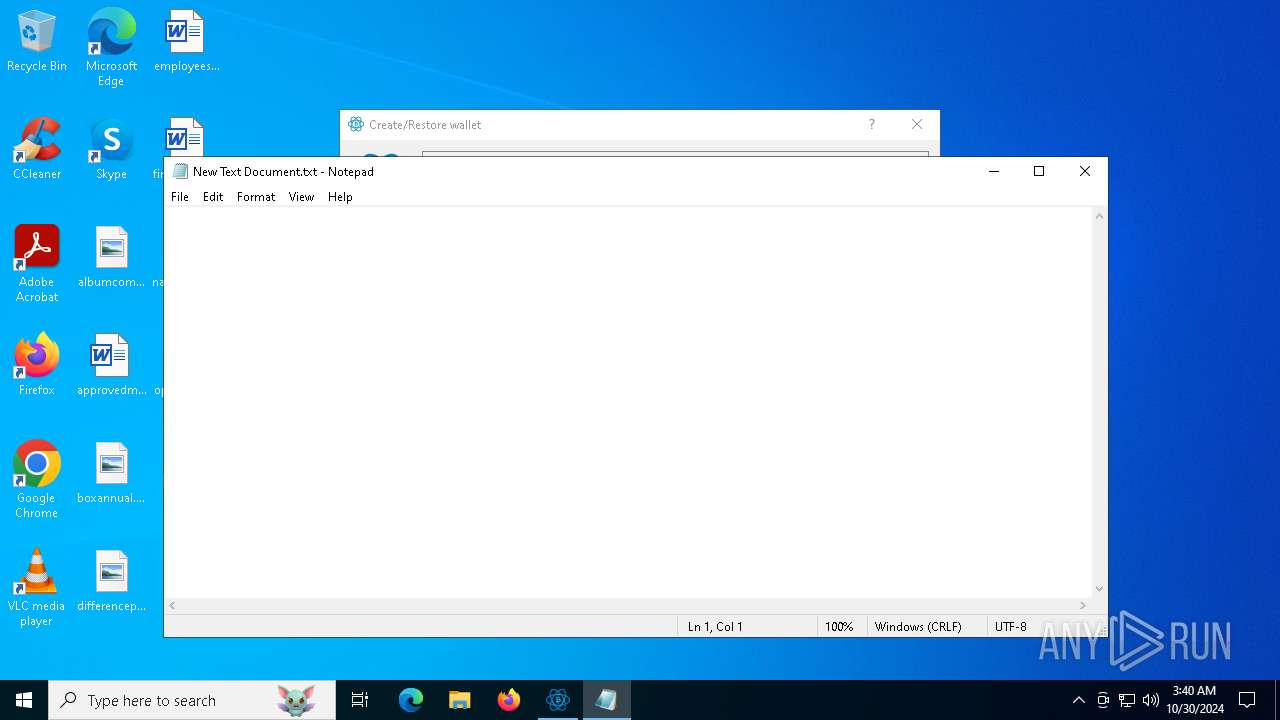
Manual execution by a user
- Shextutoply.exe (PID: 1788)
- notepad.exe (PID: 7004)
Checks operating system version
- electrum-4.5.8.exe (PID: 3108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:20:04+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 29696 |
| InitializedDataSize: | 489984 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x38af |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.5.0.0 |
| ProductVersionNumber: | 2.5.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Chinese (Simplified) |
| CompanyName: | Electrum |
| FileDescription: | Electrum |
| FileVersion: | 2.5.0.0 |
| InternalName: | appres\Shextutoply.exe |
| LegalCopyright: | Electrum Copyright(c)2024 |
| ProductName: | Electrum |
| ProductVersion: | 2.5.0.0 |
Total processes
134
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1336 | fsutil sparse setflag "C:\Users\admin\AppData\Roaming\Electrum\blockchain_headers" 1 | C:\Windows\SysWOW64\fsutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: fsutil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\SysWOW64\cmd.exe | — | electrum-4.5.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1788 | "C:\Electrum_27386\appres\Shextutoply.exe" 218467 | C:\Electrum_27386\appres\Shextutoply.exe | explorer.exe | ||||||||||||
User: admin Company: 厦门市百胜通软件技术有限公司 Integrity Level: MEDIUM Description: 转易侠HEIC转换器 Version: 2.2.0.4 Modules
| |||||||||||||||
| 3108 | "C:\Electrum_27386\electrum-4.5.8.exe" | C:\Electrum_27386\electrum-4.5.8.exe | Shextutoply.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4828 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\SysWOW64\cmd.exe | — | electrum-4.5.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6756 | C:\WINDOWS\system32\cmd.exe /c fsutil sparse setflag "C:\Users\admin\AppData\Roaming\Electrum\blockchain_headers" 1 | C:\Windows\SysWOW64\cmd.exe | — | electrum-4.5.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6812 | "C:\Users\admin\AppData\Local\Temp\electrumx64.exe" | C:\Users\admin\AppData\Local\Temp\electrumx64.exe | explorer.exe | ||||||||||||
User: admin Company: Electrum Integrity Level: MEDIUM Description: Electrum Exit code: 0 Version: 2.5.0.0 Modules
| |||||||||||||||
Total events
1 445
Read events
1 443
Write events
2
Delete events
0
Modification events
| (PID) Process: | (1788) Shextutoply.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ShextutoplyShextutoply |
Value: C:\Electrum_27386\appres\Shextutoply.exe | |||
| (PID) Process: | (1788) Shextutoply.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\J6UBF379D39E71EFHJ67I |
| Operation: | write | Name: | InstallTime |
Value: 2024-10-30 3:39:45 | |||
Executable files
98
Suspicious files
151
Text files
659
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6812 | electrumx64.exe | C:\Electrum_27386\app.7z | — | |
MD5:— | SHA256:— | |||
| 6812 | electrumx64.exe | C:\Users\admin\AppData\Local\Temp\nseD0D7.tmp\BgWorker.dll | executable | |
MD5:33EC04738007E665059CF40BC0F0C22B | SHA256:50F735AB8F3473423E6873D628150BBC0777BE7B4F6405247CDDF22BB00FB6BE | |||
| 6812 | electrumx64.exe | C:\Users\admin\AppData\Local\Temp\nseD0D7.tmp\logo.ico | image | |
MD5:E4A8817AA15F1CCB0E49DAD689C87D16 | SHA256:1B7E574335CA9D80B5523ABEA0BBD7DB0CD69C17A6BFD185FCCD3940B61BF973 | |||
| 6812 | electrumx64.exe | C:\Users\admin\AppData\Local\Temp\nseD0D7.tmp\System.dll | executable | |
MD5:BF712F32249029466FA86756F5546950 | SHA256:7851CB12FA4131F1FEE5DE390D650EF65CAC561279F1CFE70AD16CC9780210AF | |||
| 6812 | electrumx64.exe | C:\Electrum_27386\pyexpat.pyd | executable | |
MD5:92C72753FA5C8EAA615B007F89CDB482 | SHA256:EBBDE07AFB2BB356CD400E97D8AFB5ABBC121CC0CC90F99BEC9C3FA5CA60DE14 | |||
| 6812 | electrumx64.exe | C:\Electrum_27386\hid.cp310-win32.pyd | executable | |
MD5:084F1A8DB3FDF6520F6B63D7489B1971 | SHA256:59E478CB62FFEAF7B3EACB59B3BB94C3225E3307B2CB2370FAAB55C3B99E93C7 | |||
| 6812 | electrumx64.exe | C:\Users\admin\AppData\Local\Temp\nseD0D7.tmp\nsis7zU.dll | executable | |
MD5:06A47571AC922F82C098622B2F5F6F63 | SHA256:E4AB3064F2E094910AE80104EF9D371CCB74EBBEEED592582CF099ACD83F5FE9 | |||
| 6812 | electrumx64.exe | C:\Electrum_27386\_ctypes.pyd | executable | |
MD5:FF0992DFB0D4D90BDCEAAD68246C5C22 | SHA256:F879F86BF65CE05EE3467DF65C55B9837F9DFFB0F024C350C9A9869A08609759 | |||
| 6812 | electrumx64.exe | C:\Electrum_27386\_asyncio.pyd | executable | |
MD5:252C9B6FCC220FE16499ABF4A8E2A2E8 | SHA256:E01FDB89380EBF58700F40DCEBAFCB37F24970C8EA1F33063BDEA873B53E720D | |||
| 6812 | electrumx64.exe | C:\Electrum_27386\electrum.ico | image | |
MD5:8AEC9FD7C3D563FAED700948BB821327 | SHA256:2C4FE327580AAD0AA4B30FA15B2770BBBC0736D28C849D1B66C6767127697C4B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
100
DNS requests
63
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6500 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6500 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5196 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7056 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
624 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3108 | electrum-4.5.8.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.hopto .me |
3108 | electrum-4.5.8.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3108 | electrum-4.5.8.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.hopto .me |
3108 | electrum-4.5.8.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3108 | electrum-4.5.8.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
3108 | electrum-4.5.8.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
3108 | electrum-4.5.8.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
3108 | electrum-4.5.8.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
3108 | electrum-4.5.8.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 151 |
Process | Message |
|---|---|
electrumx64.exe | Window, caption, 0,0,0,390
|
electrumx64.exe | Window, showshadow, true
|
electrumx64.exe | Window, shadowcorner, 14,14,14,14
|
electrumx64.exe | Window, sizebox, 0,0,0,0
|
electrumx64.exe | Window, shadowimage, bk_shadow.png
|
electrumx64.exe | Window, shadowsize, 14
|
electrumx64.exe | Window, size, 480,390
|
electrumx64.exe | LabelUI, text, ????:
|
electrumx64.exe | RichEdit, bkimage, public\edit\edit0.png
|
electrumx64.exe | LabelUI, textcolor, #FF333333
|