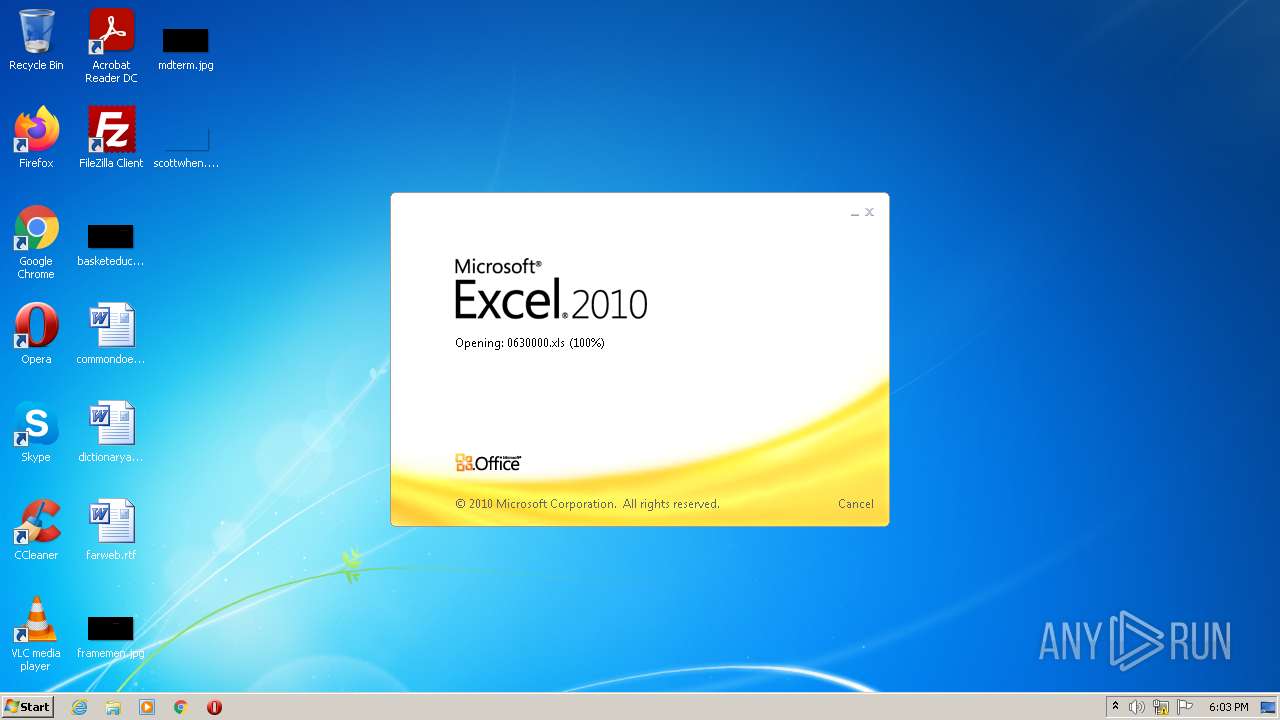
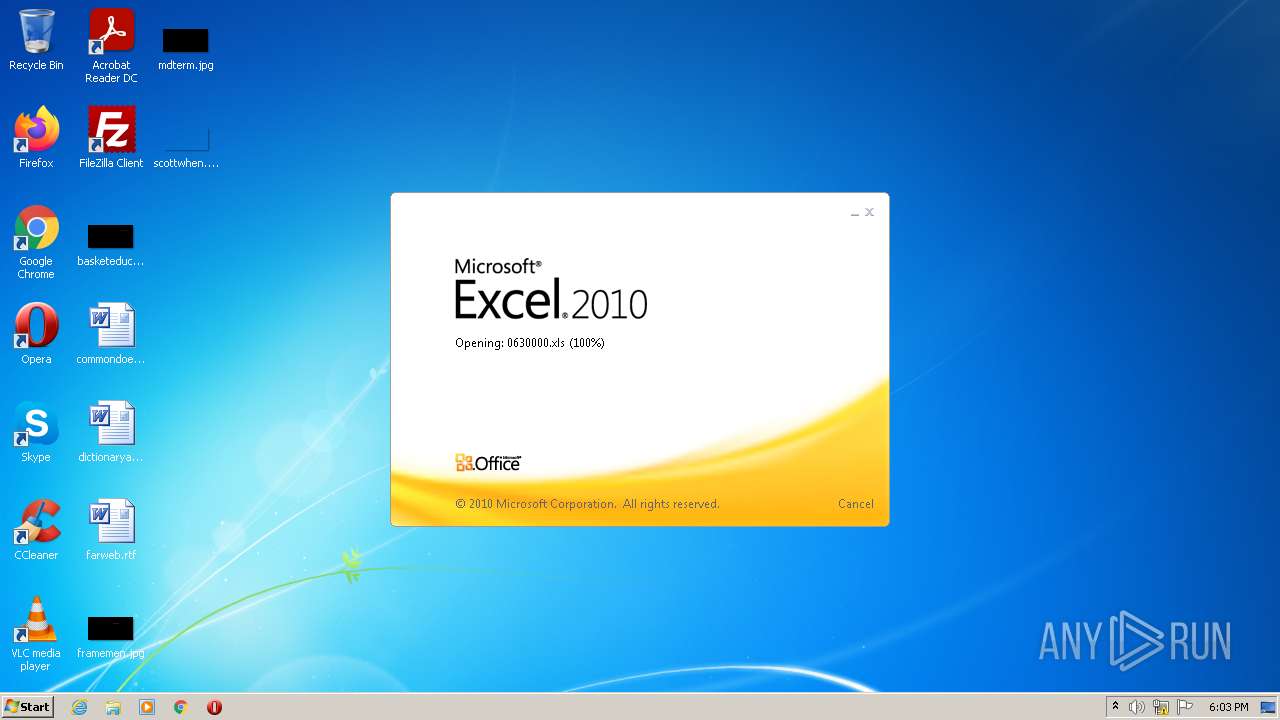
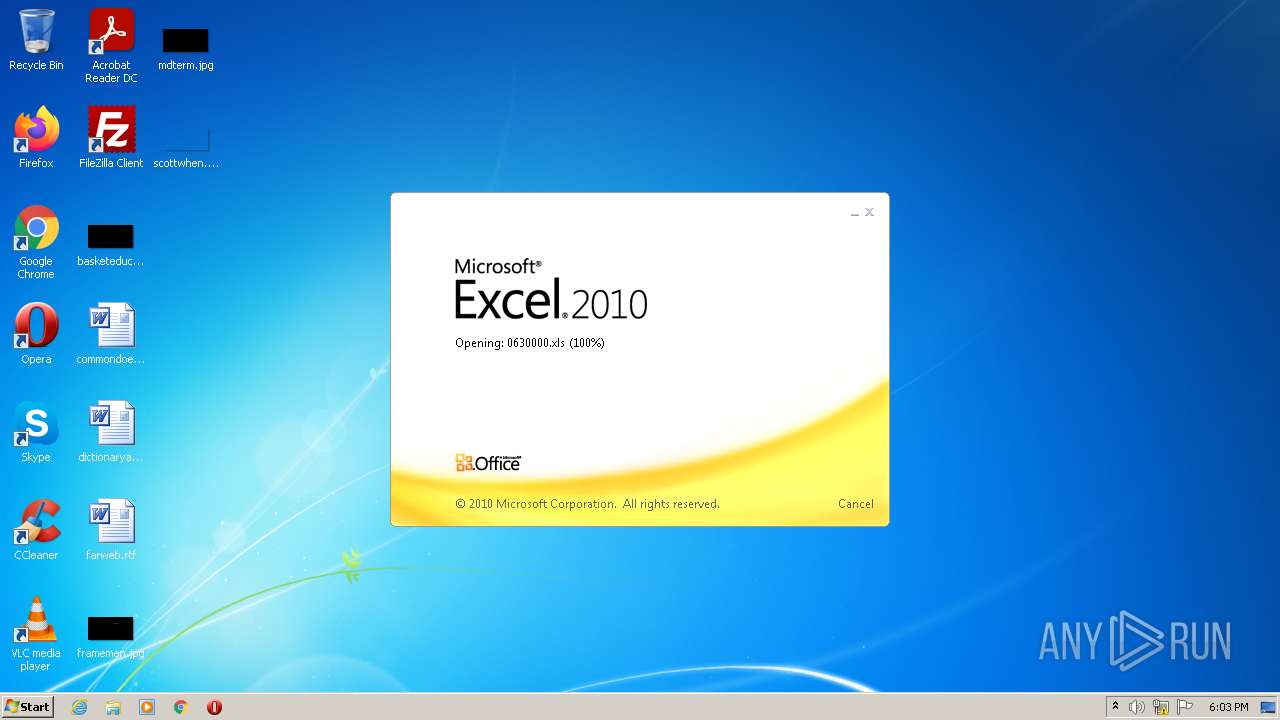
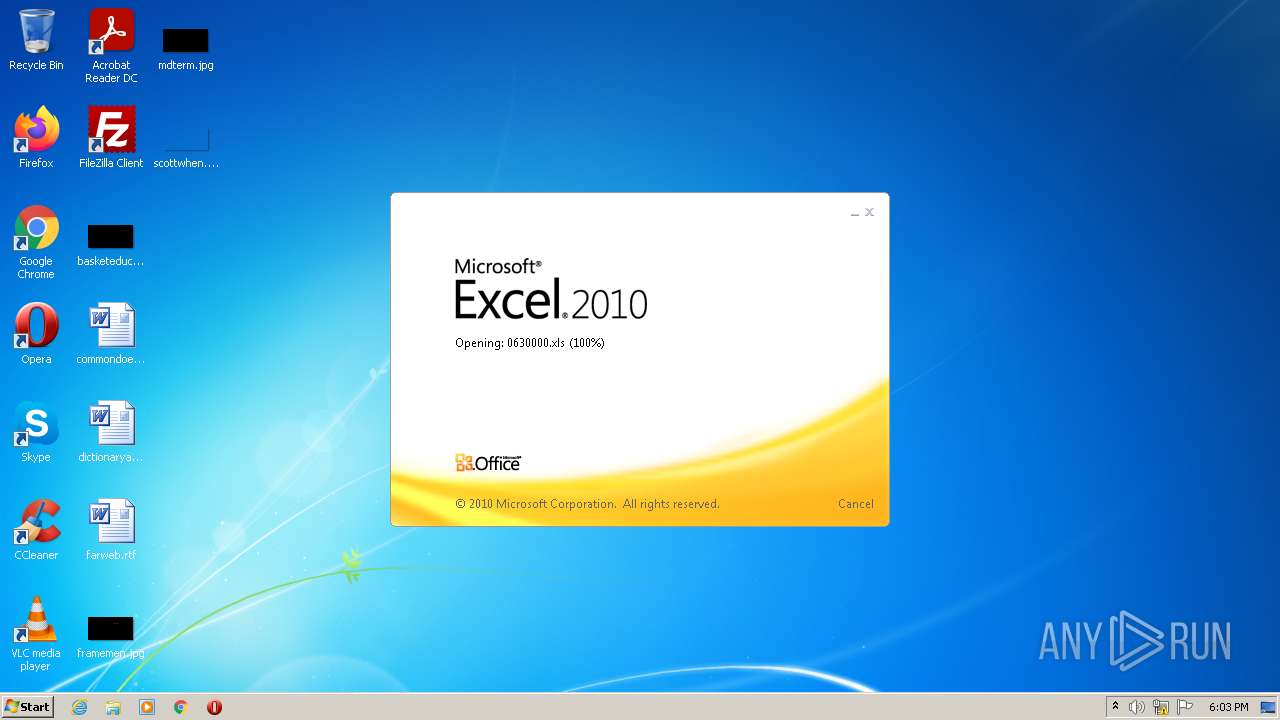
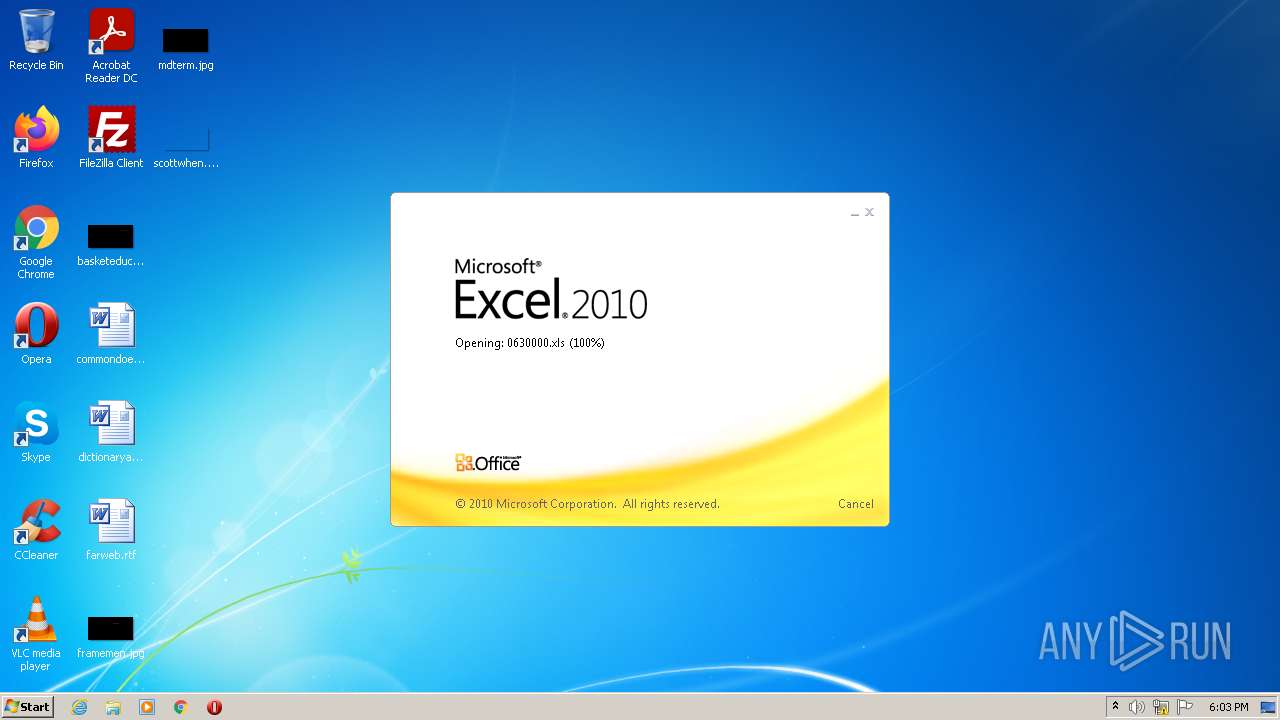
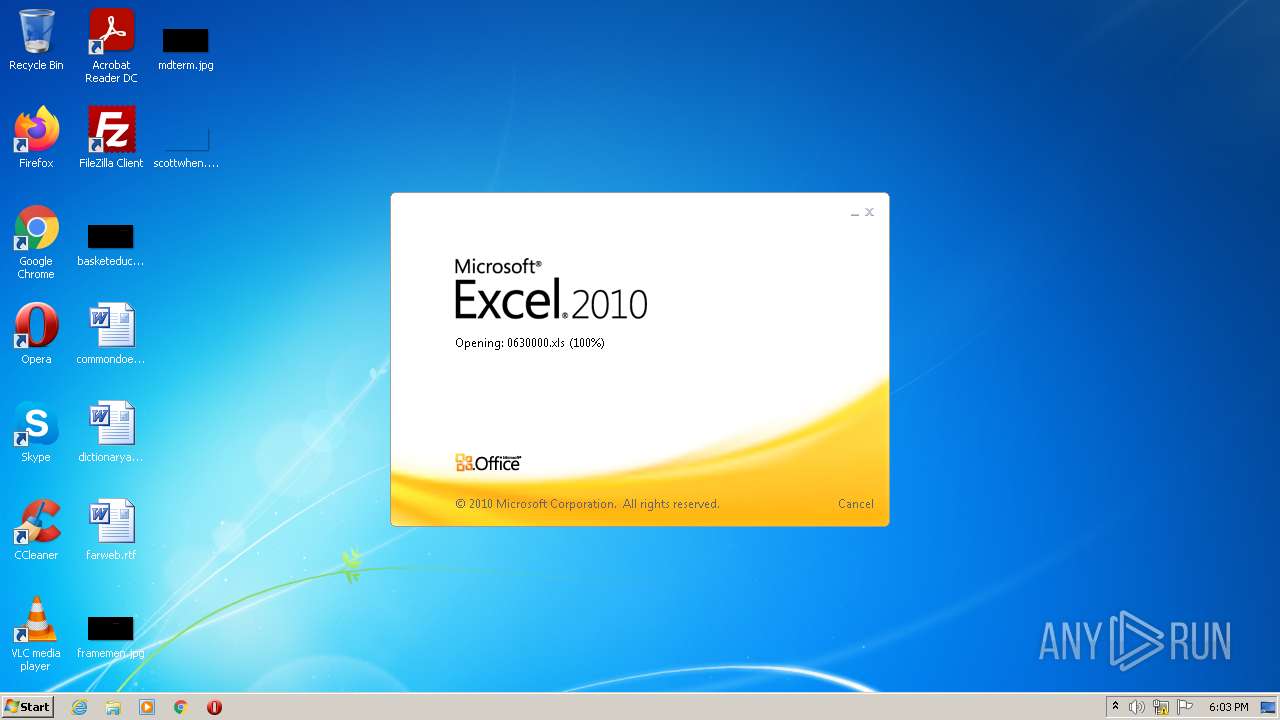
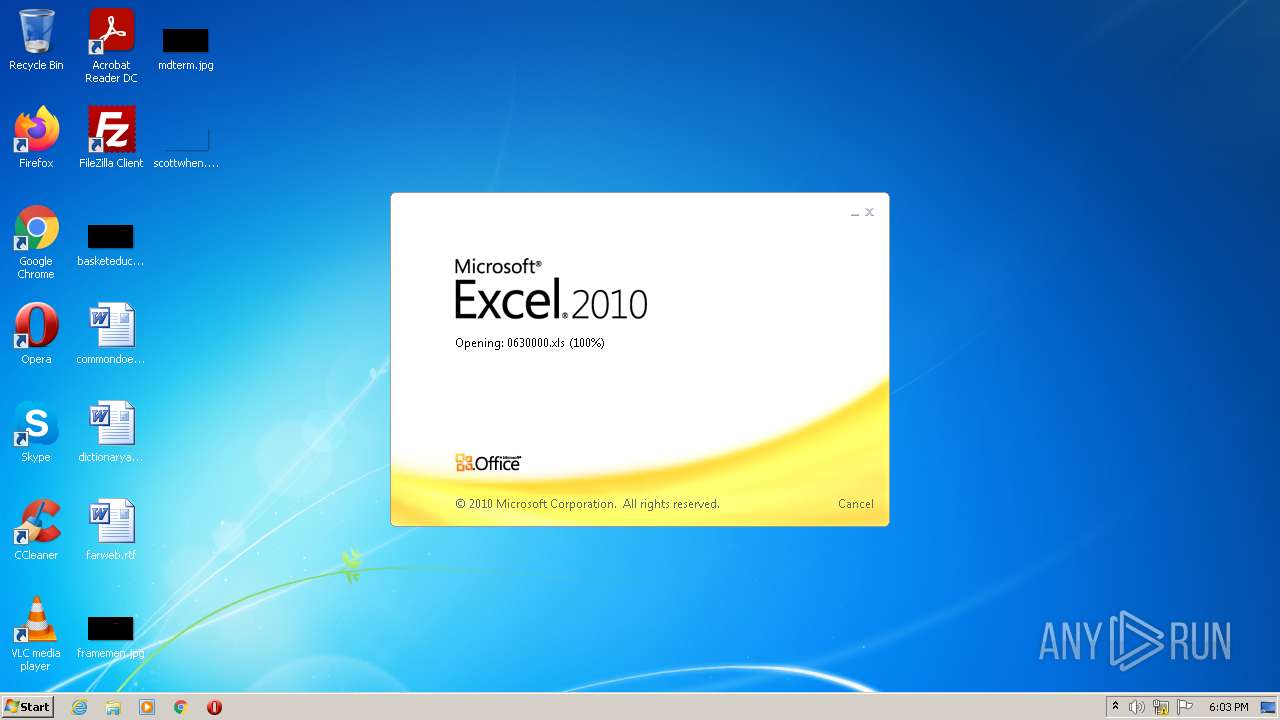
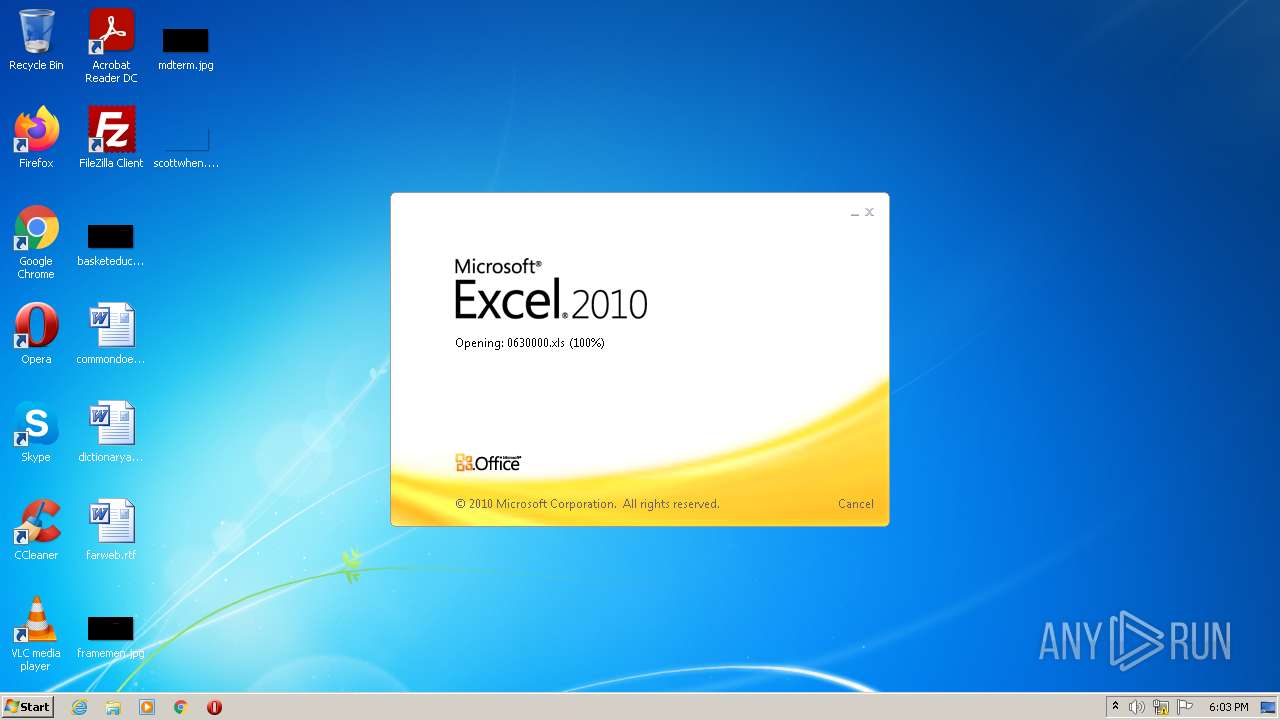
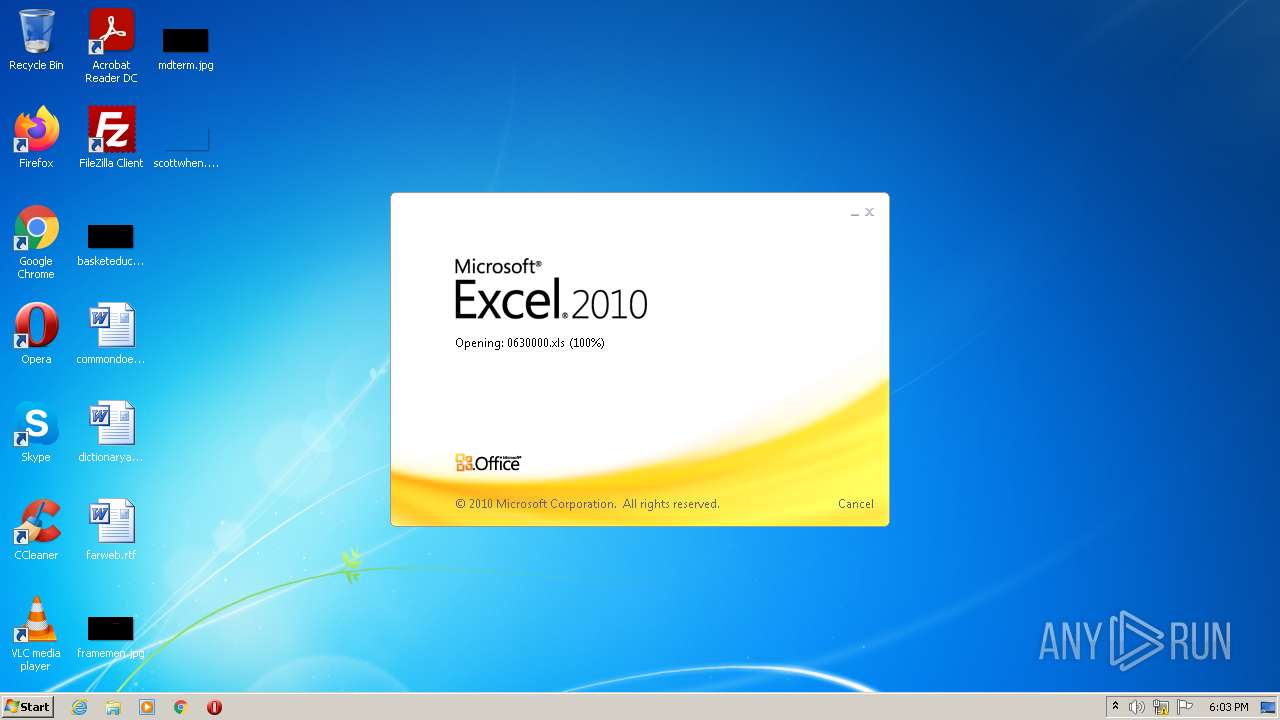
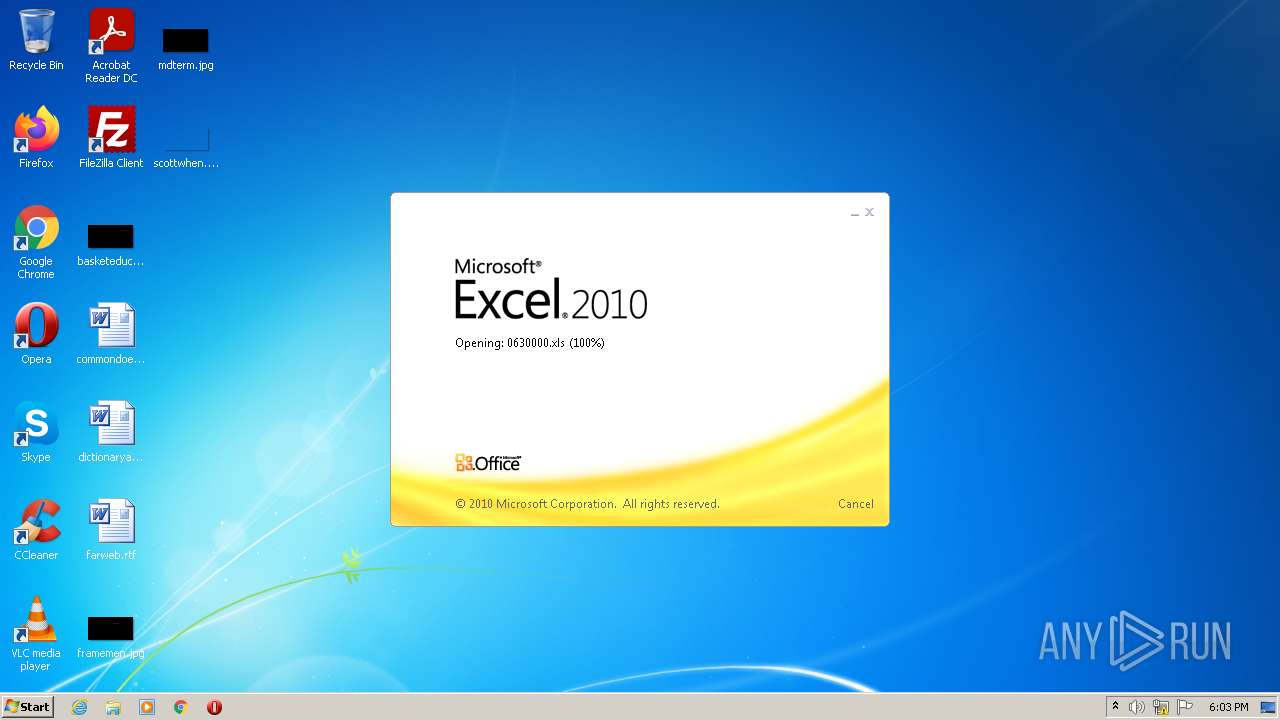
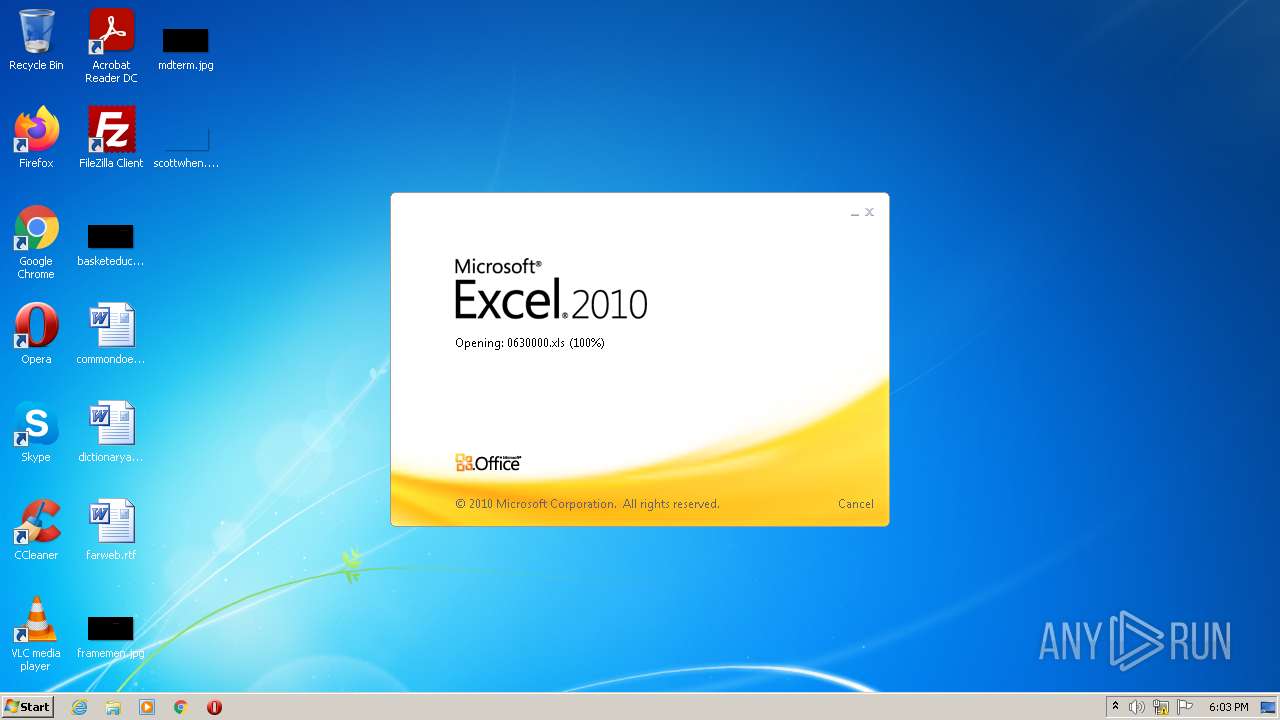
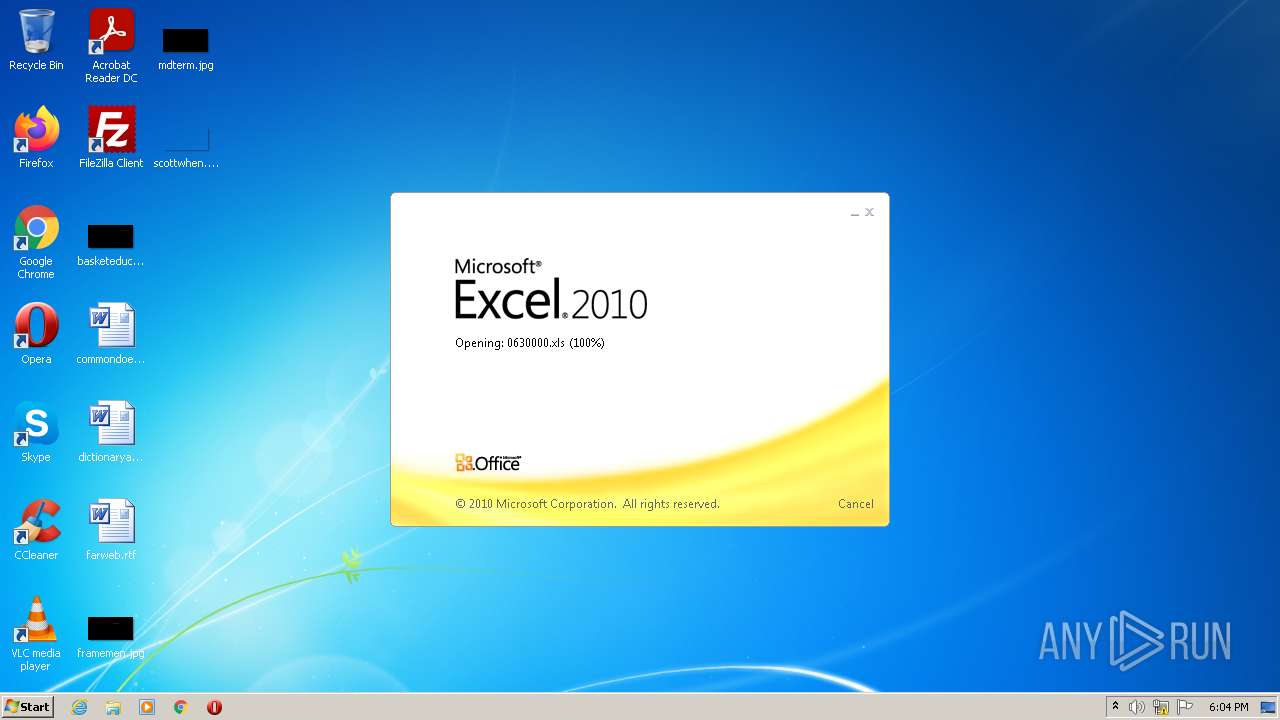
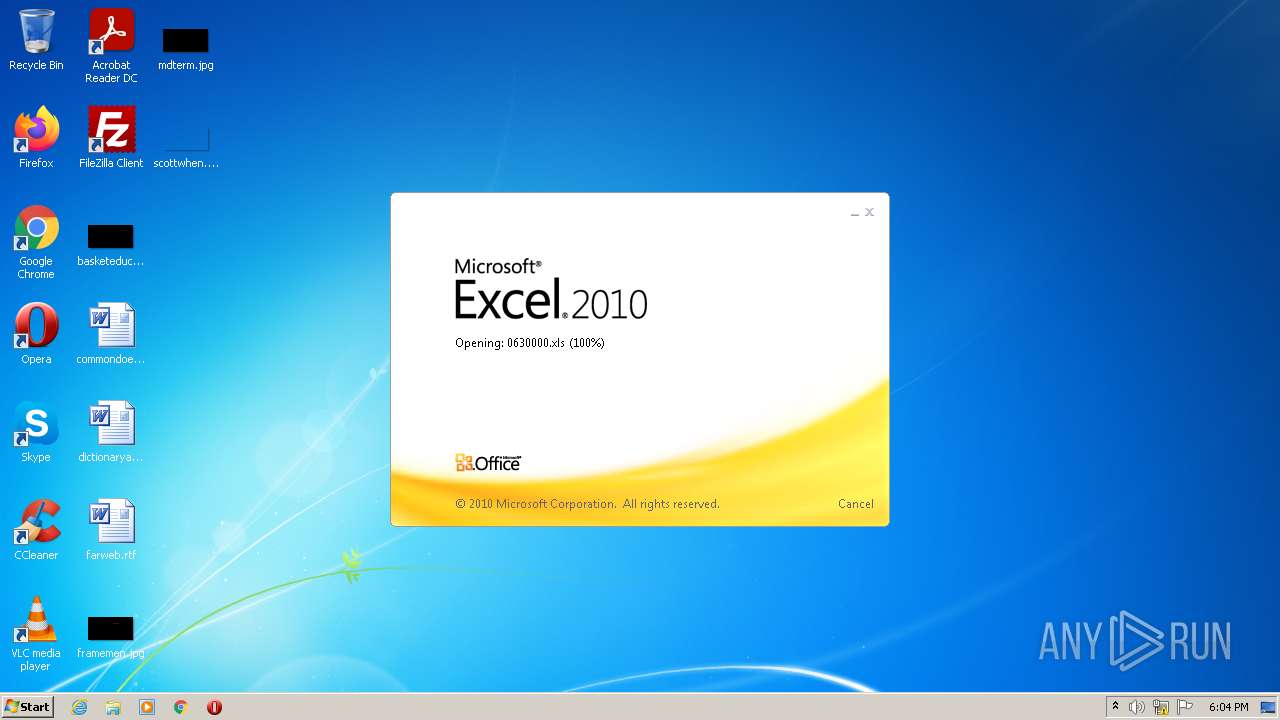
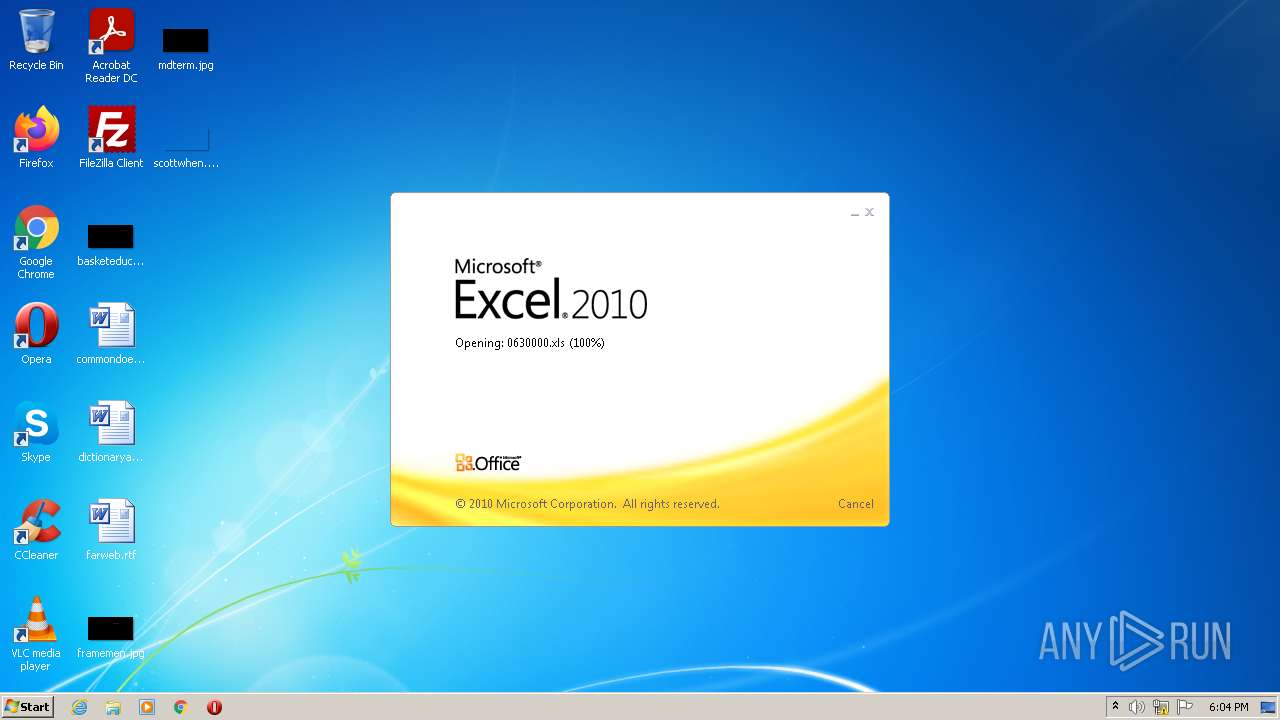
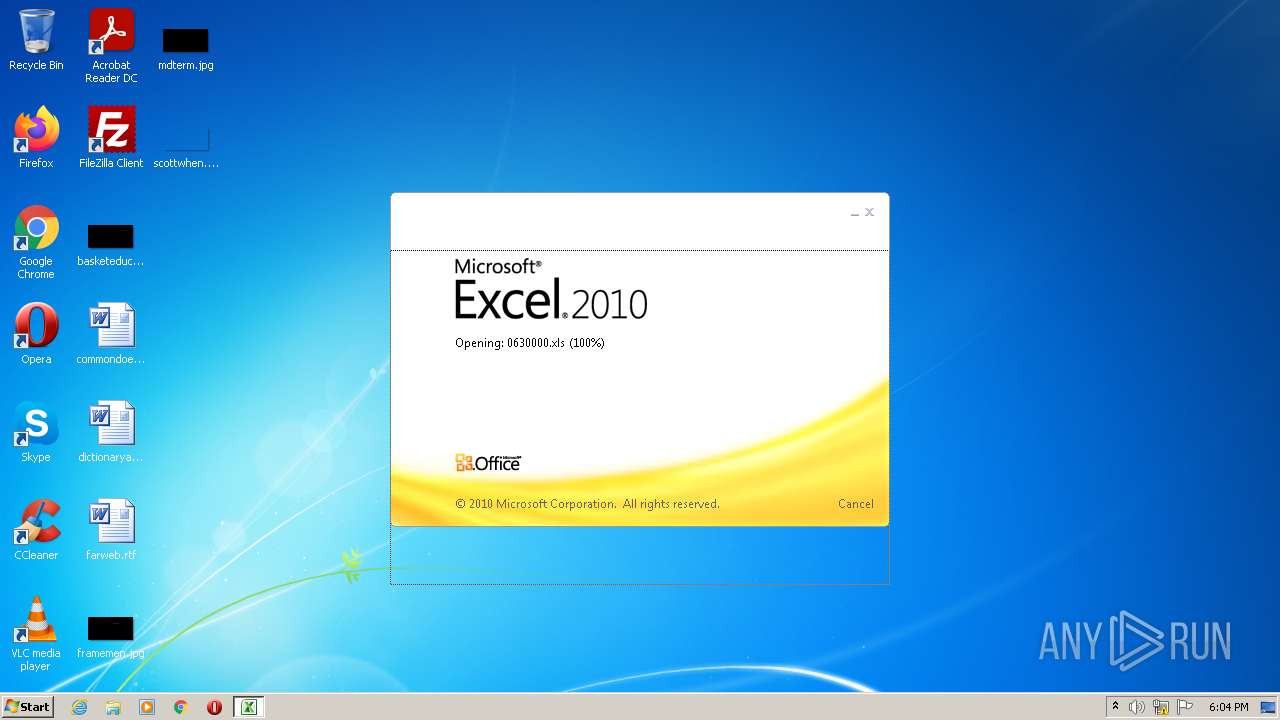
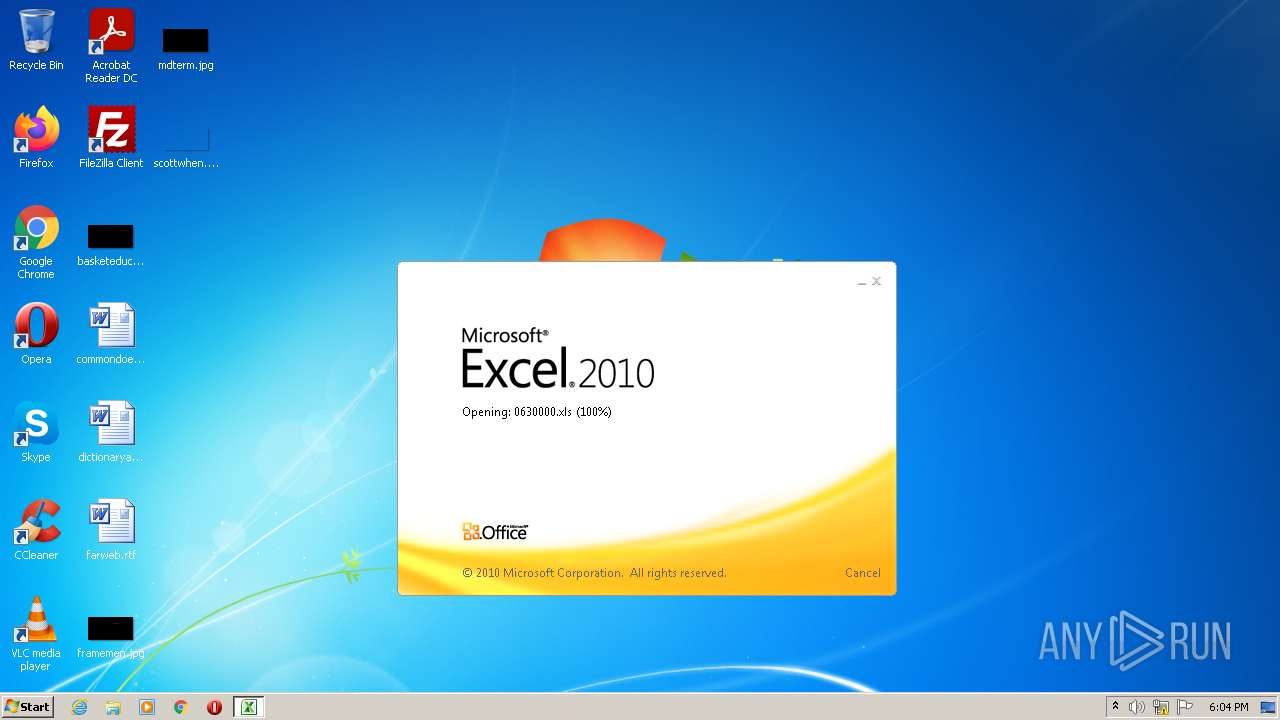
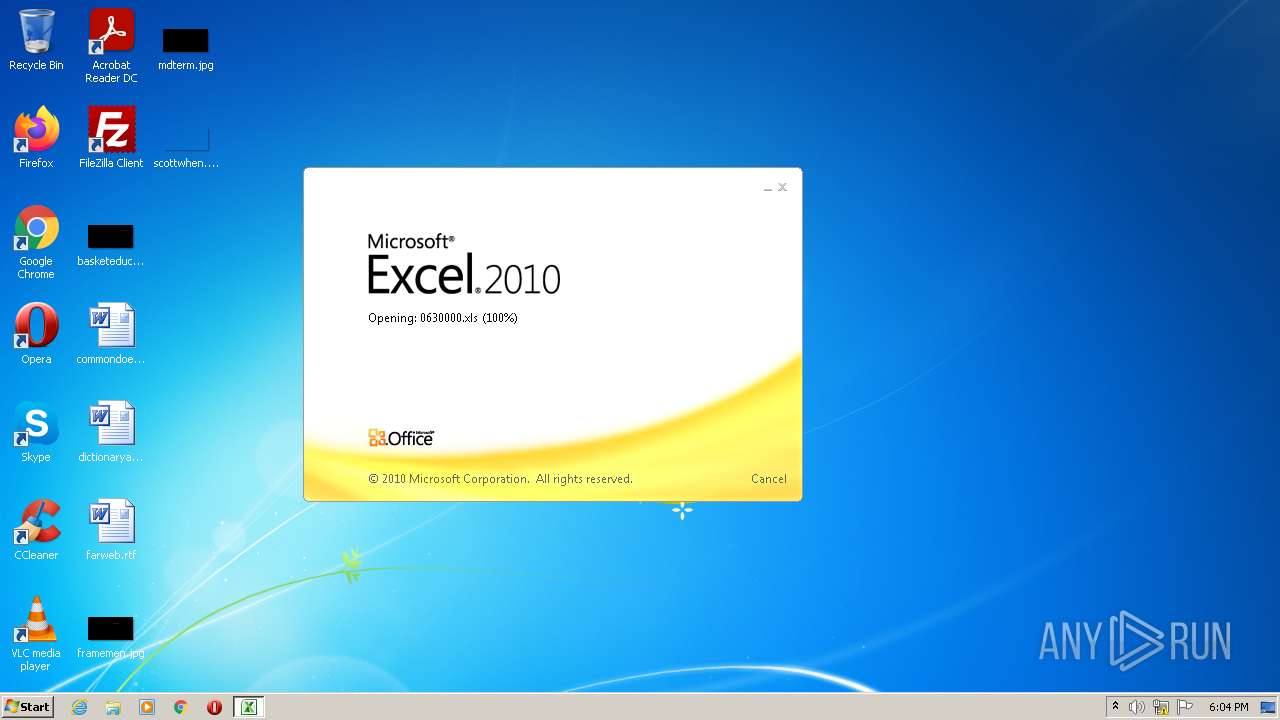
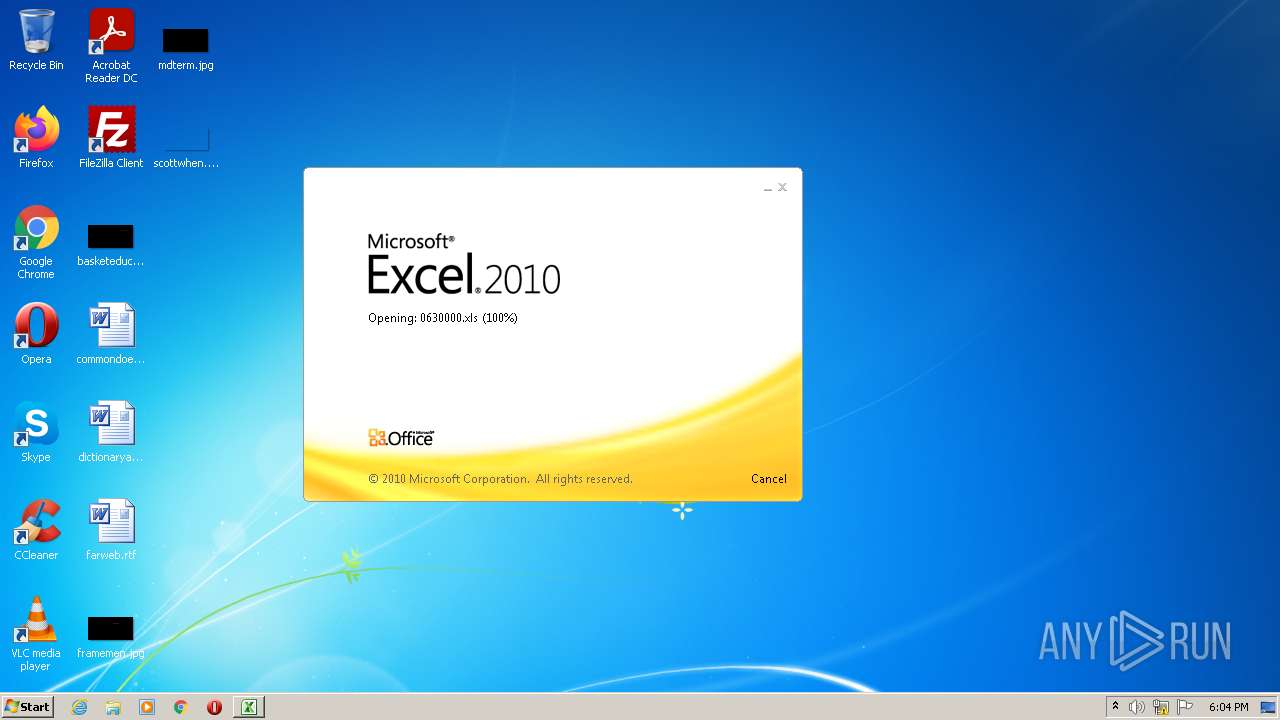
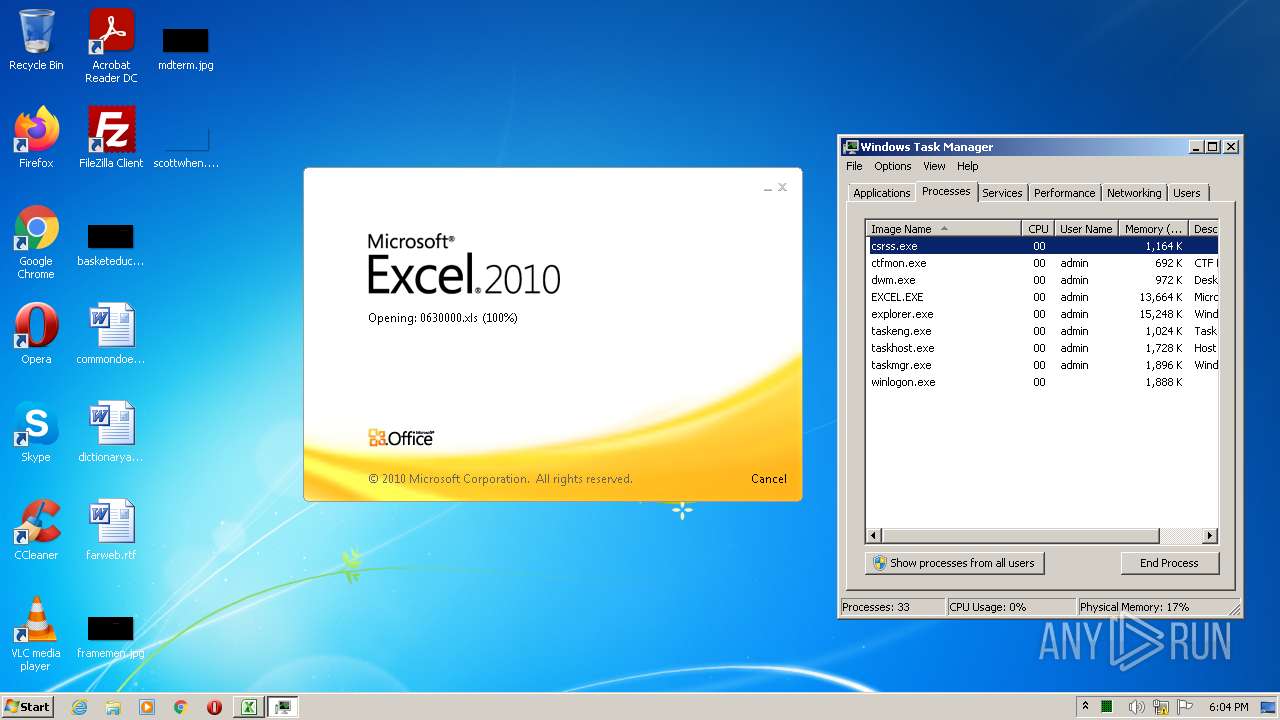
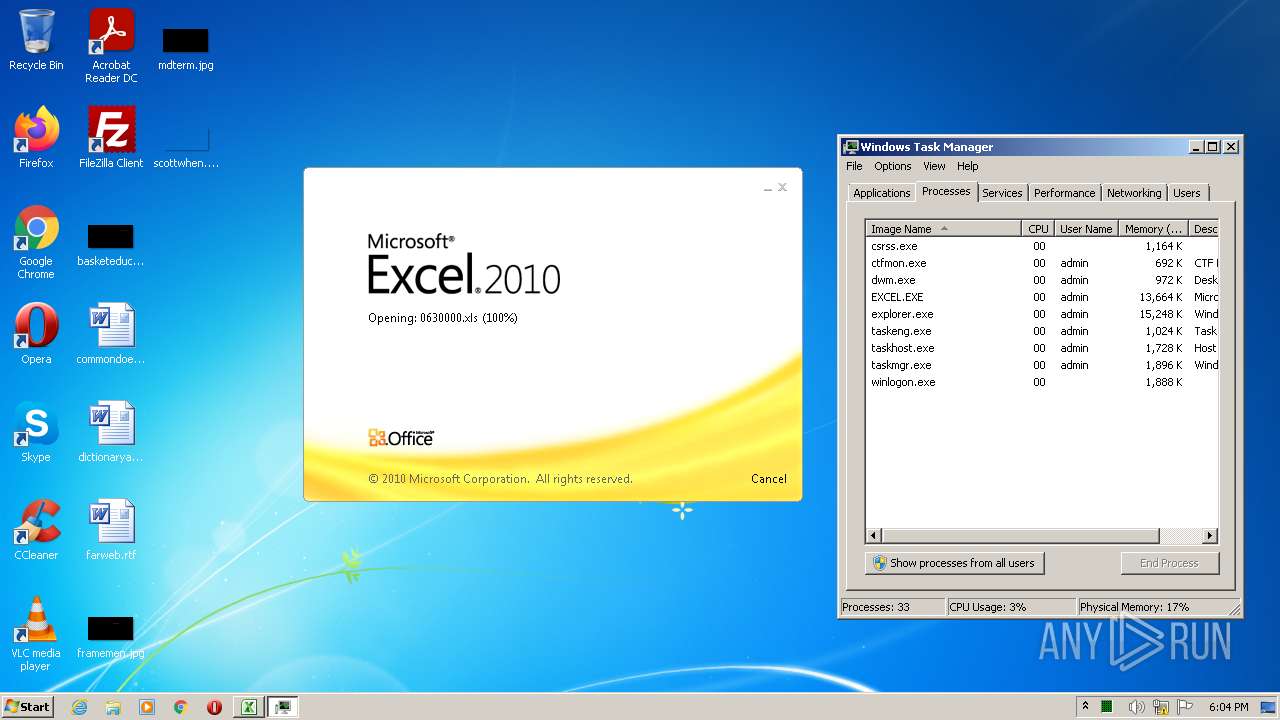
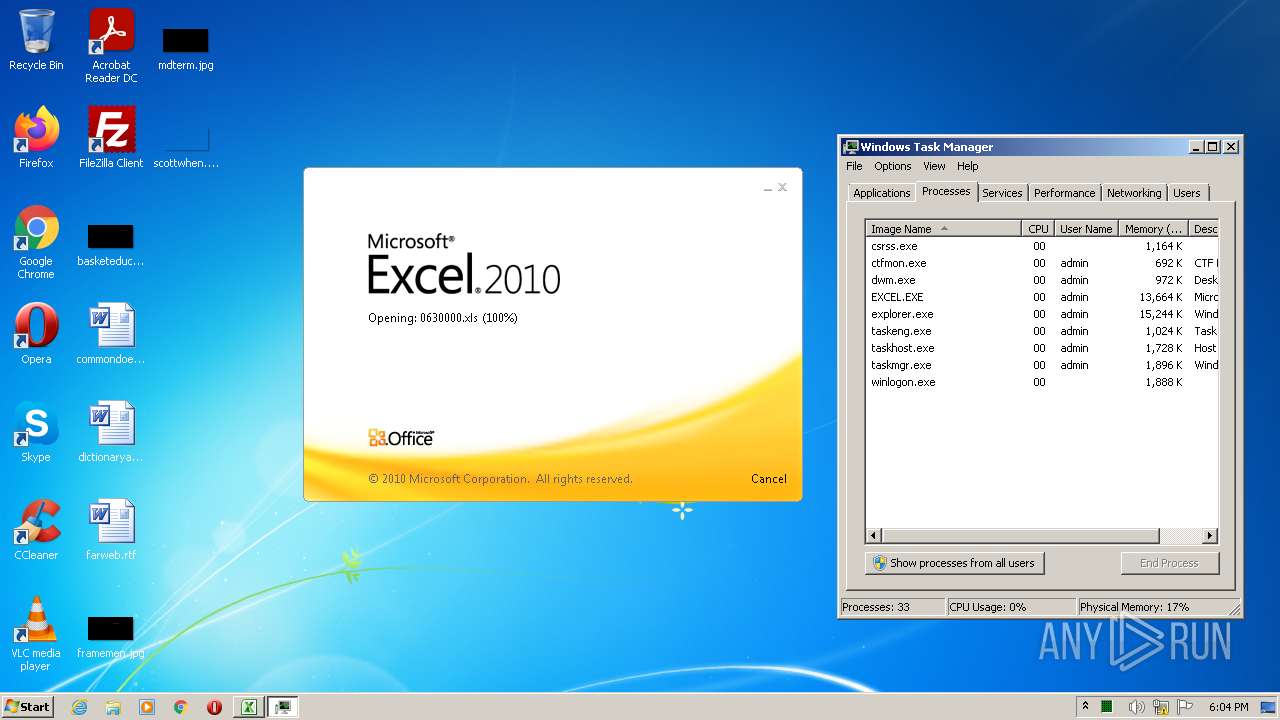
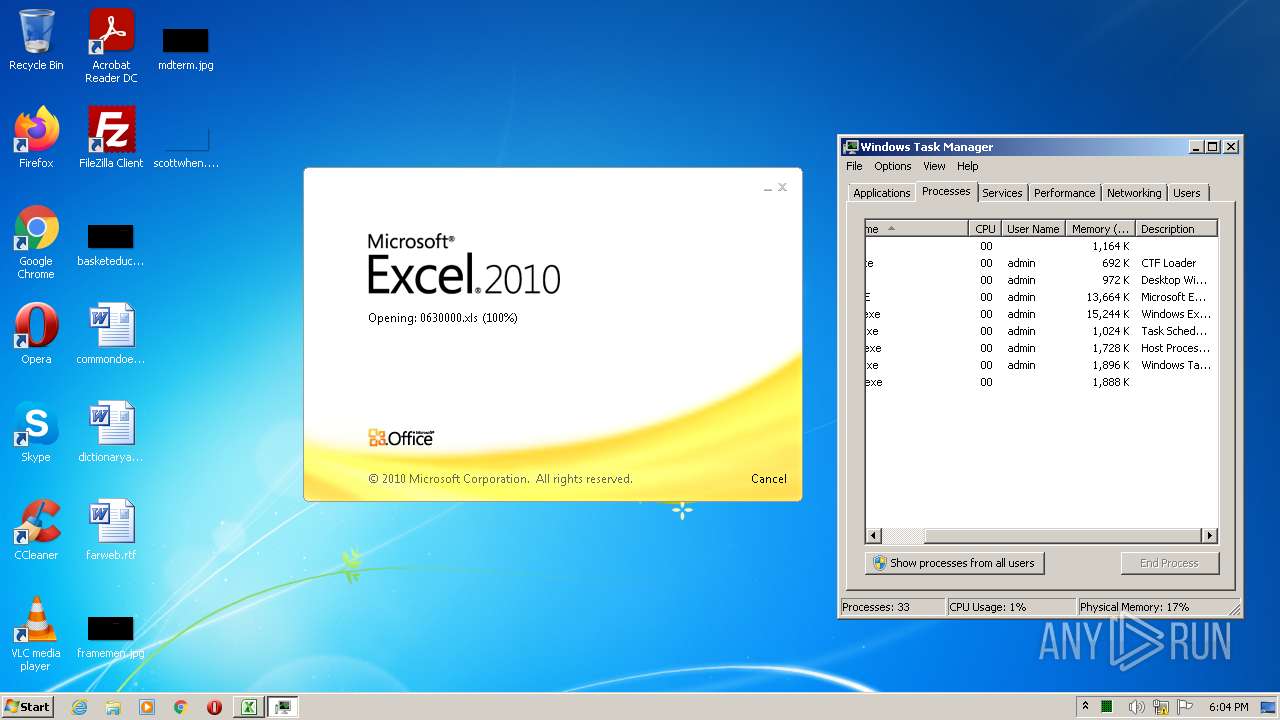
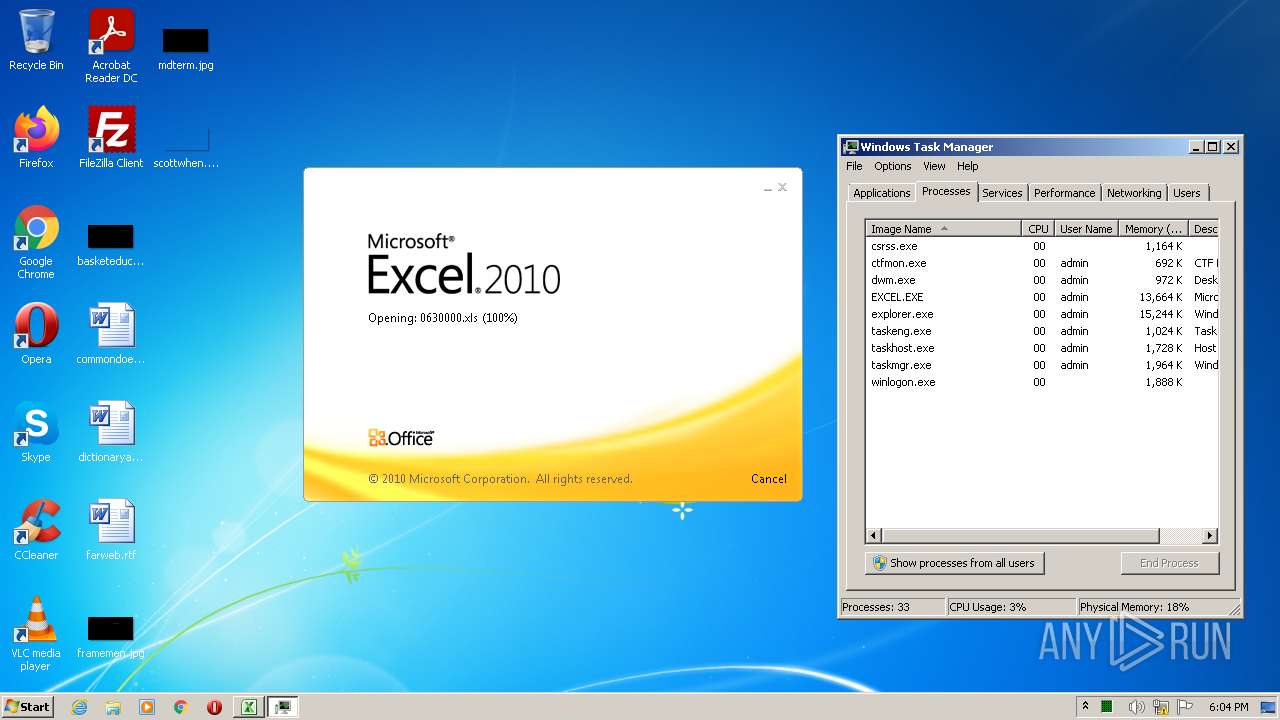
| File name: | 0630000.xls |
| Full analysis: | https://app.any.run/tasks/b9902ffc-5376-4049-a27f-78e430dbc509 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 17:03:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Author: Dream, Last Saved By: TYHRETH, Name of Creating Application: Microsoft Excel, Create Time/Date: Fri Jun 5 19:19:34 2015, Last Saved Time/Date: Thu May 19 17:58:23 2022, Security: 0 |
| MD5: | 3BC31916746ACD2F588E27B24E5BD90D |
| SHA1: | F587D8B3E2E67A599FC772544C0D9AF9F3BBD31A |
| SHA256: | 450F9B20D1647F065E7502C5990BCB0FE8D0386A7C8B2DFCB27B61C4D8A5960A |
| SSDEEP: | 1536:dfKpb8rGYrMPe3q7Q0XV5xtezEsi8/dg89s1a6Y+2jzLviHvDNHhOAL:9Kpb8rGYrMPe3q7Q0XV5xtezEsi8/dgt |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2532)
Registers / Runs the DLL via REGSVR32.EXE
- EXCEL.EXE (PID: 2532)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- EXCEL.EXE (PID: 2532)
- regsvr32.exe (PID: 2936)
- taskmgr.exe (PID: 2432)
Reads the computer name
- EXCEL.EXE (PID: 2532)
- taskmgr.exe (PID: 2432)
Checks Windows Trust Settings
- EXCEL.EXE (PID: 2532)
Reads settings of System Certificates
- EXCEL.EXE (PID: 2532)
Manual execution by user
- taskmgr.exe (PID: 2432)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| HeadingPairs: |
|
|---|---|
| TitleOfParts: |
|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 16 |
| Company: | - |
| CodePage: | Windows Cyrillic |
| Security: | None |
| ModifyDate: | 2022:05:19 16:58:23 |
| CreateDate: | 2015:06:05 18:19:34 |
| Software: | Microsoft Excel |
| LastModifiedBy: | TYHRETH |
| Author: | Dream |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2432 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2532 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2936 | C:\Windows\System32\regsvr32.exe /S ..\uxevr1.ocx | C:\Windows\System32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 020
Read events
5 934
Write events
75
Delete events
11
Modification events
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | ls; |
Value: 6C733B00E4090000010000000000000000000000 | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2532) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
7
Text files
0
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR474C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Cab93A8.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DC7F871A94DCC5407E47E2A8E763A49A | binary | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Tar93A9.tmp | cat | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_2DBE917624E9880FE0C7C5570D56E691 | der | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_2DBE917624E9880FE0C7C5570D56E691 | binary | |
MD5:— | SHA256:— | |||
| 2532 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
10
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2532 | EXCEL.EXE | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?92acce417065f35b | US | compressed | 60.0 Kb | whitelisted |
2532 | EXCEL.EXE | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEGfe9D7xe9riT%2FWUBgbSwIQ%3D | US | der | 471 b | whitelisted |
2532 | EXCEL.EXE | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEQDwHUvue3yjezwFZqwFlyRY | US | der | 728 b | whitelisted |
2532 | EXCEL.EXE | GET | 200 | 96.16.145.230:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
2532 | EXCEL.EXE | GET | 200 | 184.24.77.67:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQakzn38KvfTlLyfeiq3Cyyww%3D%3D | US | der | 503 b | shared |
1096 | svchost.exe | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4bf7b6919de7beb8 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2532 | EXCEL.EXE | 92.42.38.45:443 | www.megakonferans.com | Inetmar internet Hizmetleri San. Tic. Ltd. Sti | TR | suspicious |
2532 | EXCEL.EXE | 23.216.77.80:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
— | — | 96.16.145.230:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | suspicious |
2532 | EXCEL.EXE | 184.24.77.67:80 | r3.o.lencr.org | Time Warner Cable Internet LLC | US | unknown |
2532 | EXCEL.EXE | 172.64.155.188:80 | ocsp.comodoca.com | — | US | suspicious |
1096 | svchost.exe | 23.216.77.69:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
2532 | EXCEL.EXE | 191.252.105.151:443 | noronhalanches.com.br | Locaweb Serviços de Internet S/A | BR | suspicious |
2532 | EXCEL.EXE | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.megakonferans.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
noronhalanches.com.br |
| unknown |
ocsp.comodoca.com |
| whitelisted |