| File name: | fix (2).exe |
| Full analysis: | https://app.any.run/tasks/9dac2bad-d657-4586-8c80-f3b87d9d5f71 |
| Verdict: | Malicious activity |
| Analysis date: | April 04, 2025, 11:05:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | A8CB99D2C264011EC0B39907F38AF549 |
| SHA1: | 13D011DD2D5DB863D2A7CBE5B4DE34056C34B6E7 |
| SHA256: | 45039DCB58421AF89751AEFB2D982A8A6615BFA421D8863BD81AB600FD847E17 |
| SSDEEP: | 98304:apIlMqo442yBwGtXyN8pdHwePF0nixmHO4s/NI/JBRTVm2Al2hzKpxAKsDVQiS4J:oUmvE4q |
MALICIOUS
Changes the autorun value in the registry
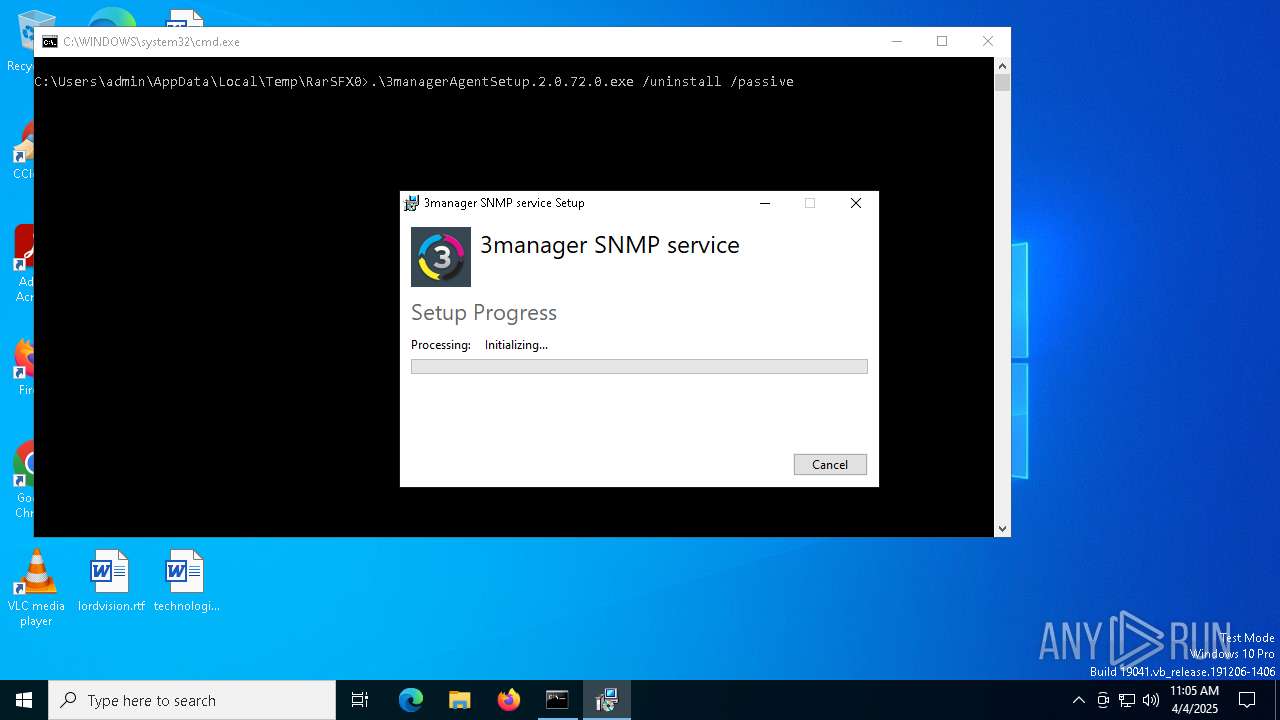
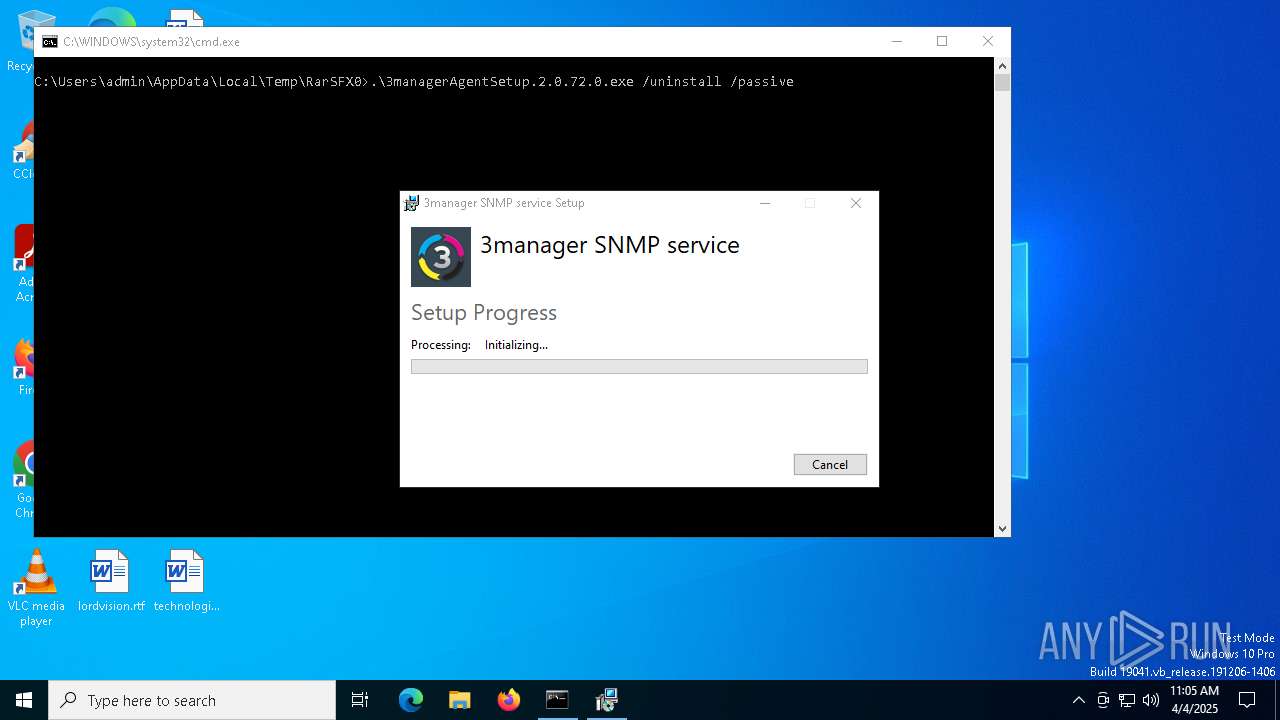
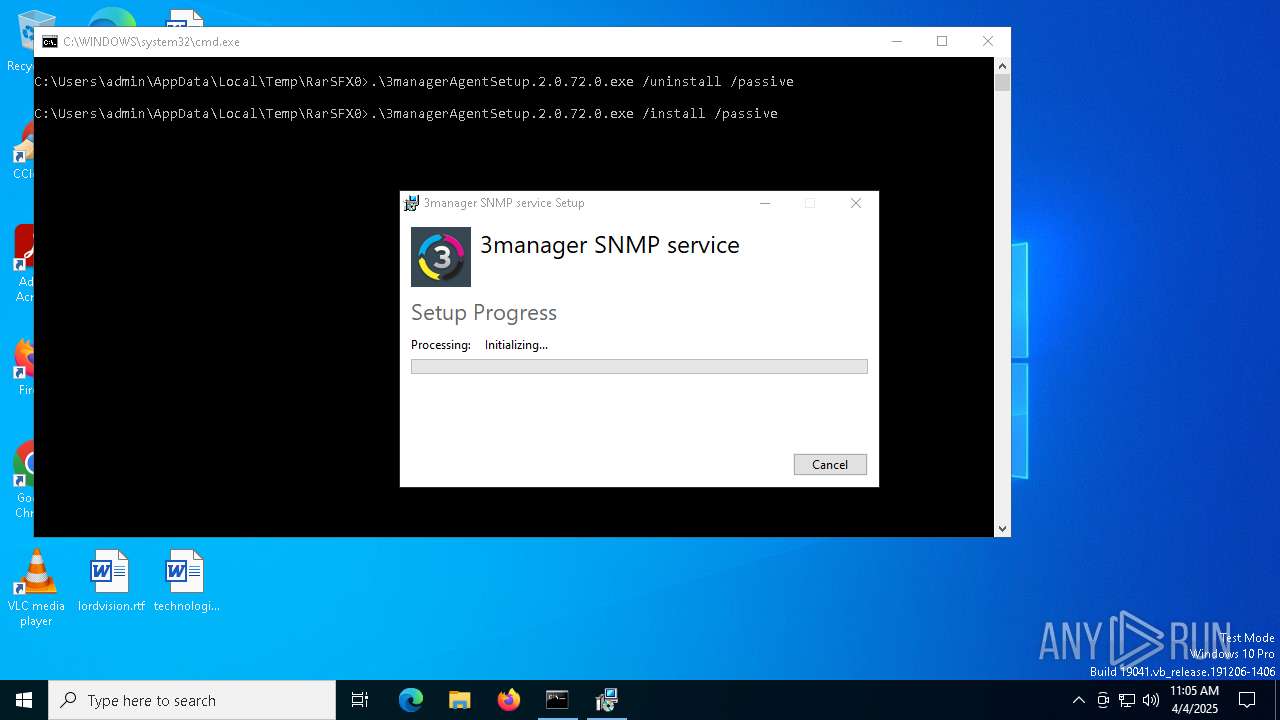
- 3managerAgentSetup.exe (PID: 7352)
- 3managerAgentSetup.exe (PID: 4920)
SUSPICIOUS
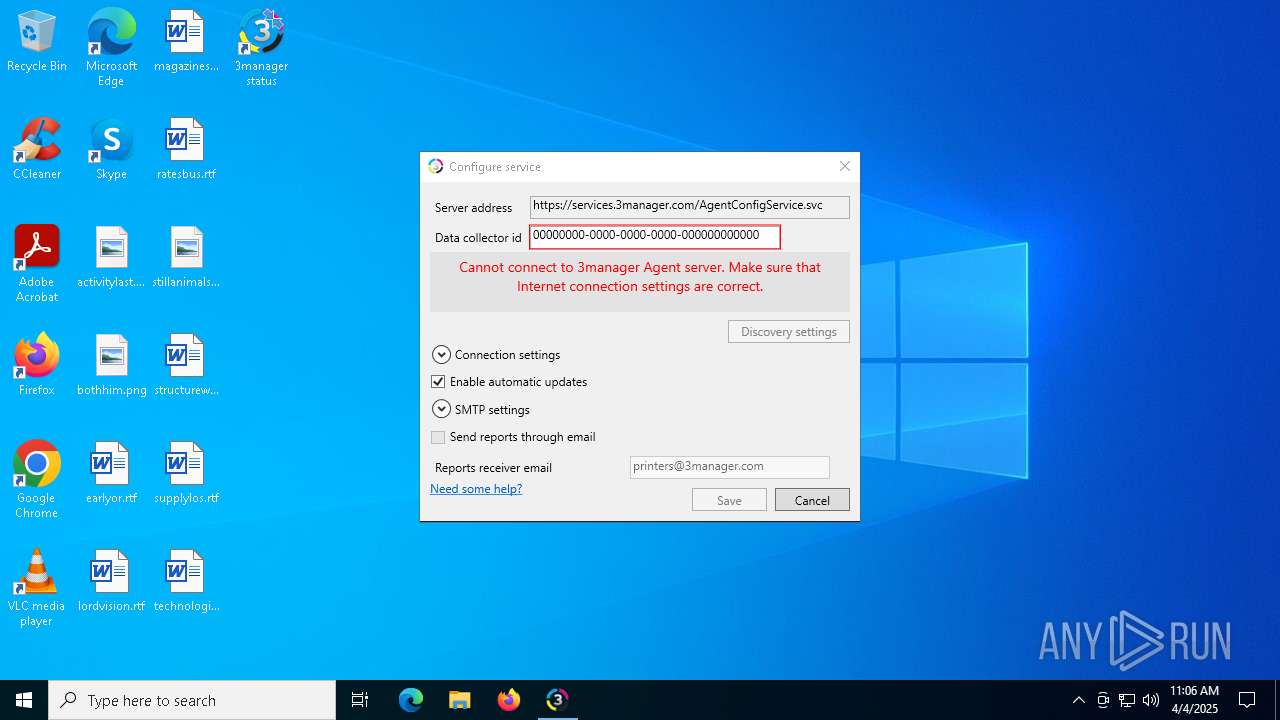
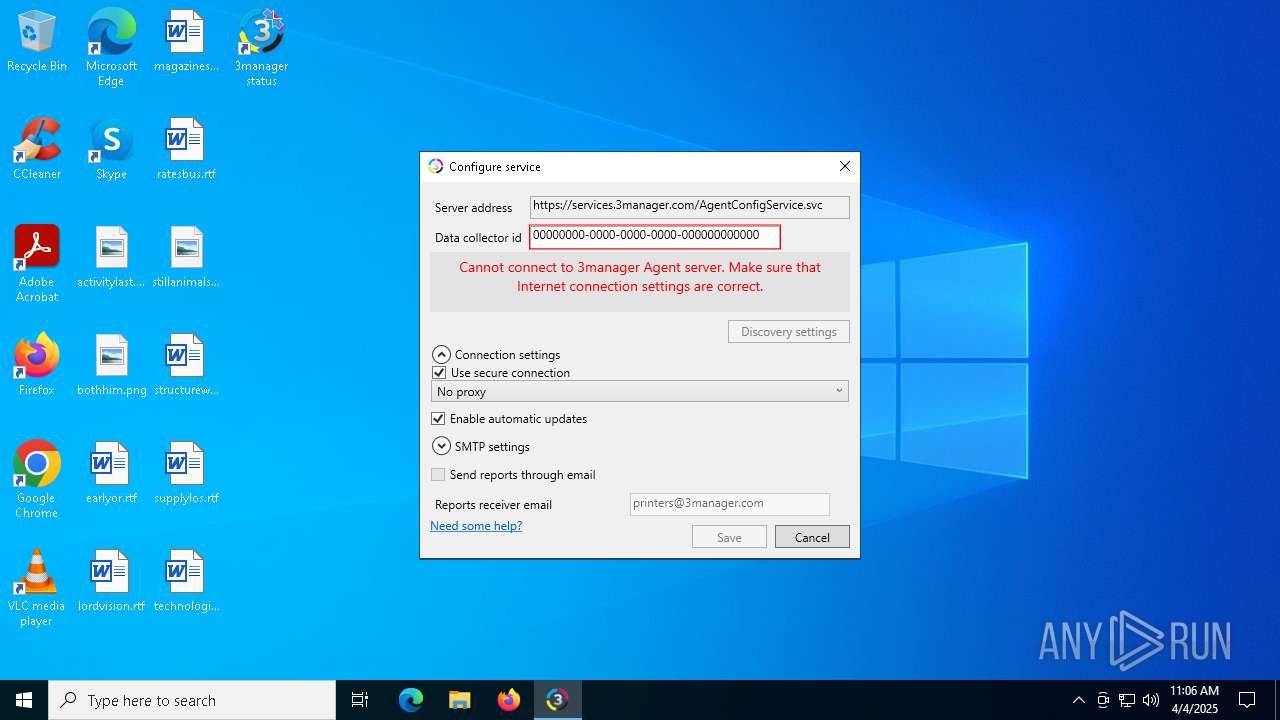
Reads security settings of Internet Explorer
- fix (2).exe (PID: 6032)
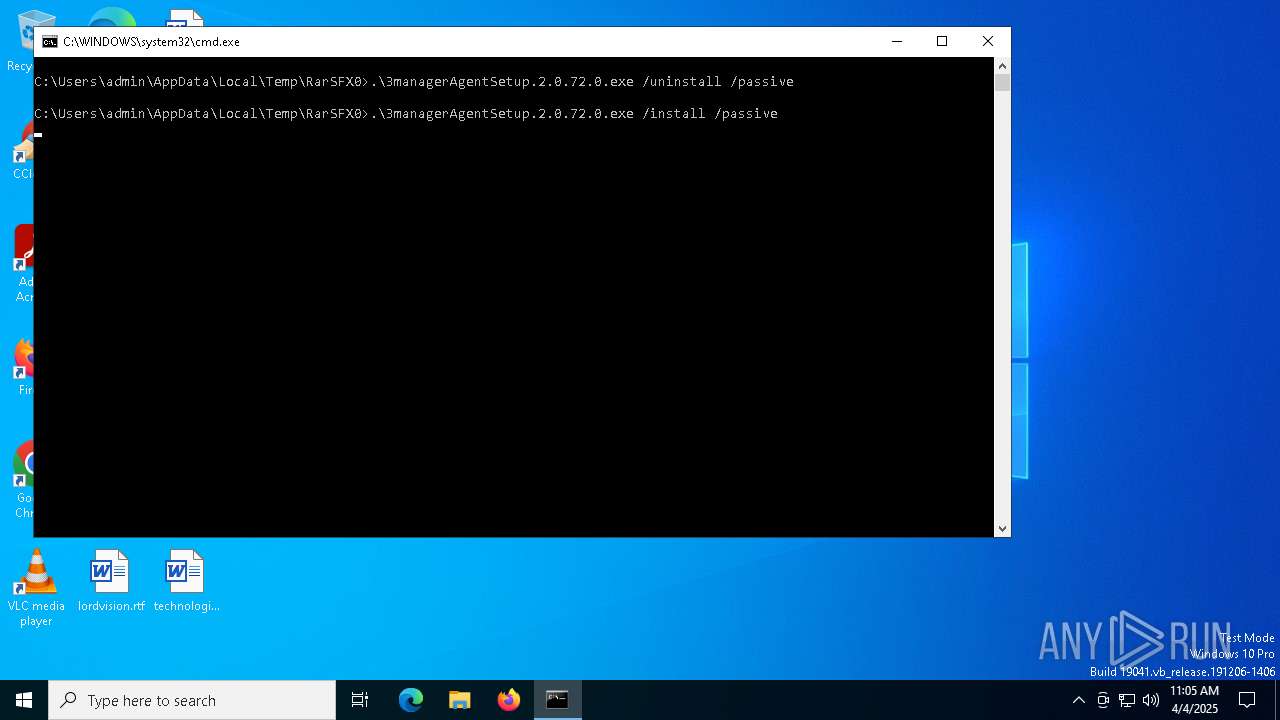
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
Starts CMD.EXE for commands execution
- fix (2).exe (PID: 6032)
Executable content was dropped or overwritten
- 3managerAgentSetup.2.0.72.0.exe (PID: 7220)
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- fix (2).exe (PID: 6032)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2960)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
- 3managerAgentSetup.exe (PID: 4920)
- rundll32.exe (PID: 7844)
Executing commands from a ".bat" file
- fix (2).exe (PID: 6032)
The executable file from the user directory is run by the CMD process
- 3managerAgentSetup.2.0.72.0.exe (PID: 7220)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2960)
Searches for installed software
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
- dllhost.exe (PID: 7400)
Starts itself from another location
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
Executes as Windows Service
- VSSVC.exe (PID: 7444)
- Agent.SnmpService.exe (PID: 5776)
Creates a software uninstall entry
- 3managerAgentSetup.exe (PID: 7352)
- 3managerAgentSetup.exe (PID: 4920)
There is functionality for taking screenshot (YARA)
- fix (2).exe (PID: 6032)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2392)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 7796)
Process drops legitimate windows executable
- msiexec.exe (PID: 2392)
INFO
Checks supported languages
- fix (2).exe (PID: 6032)
- 3managerAgentSetup.2.0.72.0.exe (PID: 7220)
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- 3managerAgentSetup.exe (PID: 7352)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2960)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
- 3managerAgentSetup.exe (PID: 4920)
- msiexec.exe (PID: 2392)
- msiexec.exe (PID: 7796)
- msiexec.exe (PID: 7892)
- Agent.SnmpService.exe (PID: 5776)
- Agent.ControlPanel.exe (PID: 5084)
Reads the computer name
- fix (2).exe (PID: 6032)
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- 3managerAgentSetup.exe (PID: 7352)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
- 3managerAgentSetup.exe (PID: 4920)
- msiexec.exe (PID: 2392)
- msiexec.exe (PID: 7892)
- msiexec.exe (PID: 7796)
- Agent.SnmpService.exe (PID: 5776)
- Agent.ControlPanel.exe (PID: 5084)
Create files in a temporary directory
- fix (2).exe (PID: 6032)
- 3managerAgentSetup.2.0.72.0.exe (PID: 7220)
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
Process checks computer location settings
- fix (2).exe (PID: 6032)
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
The sample compiled with english language support
- 3managerAgentSetup.2.0.72.0.exe (PID: 7220)
- 3managerAgentSetup.2.0.72.0.exe (PID: 7248)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2960)
- 3managerAgentSetup.2.0.72.0.exe (PID: 2600)
- 3managerAgentSetup.exe (PID: 4920)
- msiexec.exe (PID: 2392)
- fix (2).exe (PID: 6032)
Manages system restore points
- SrTasks.exe (PID: 2340)
- SrTasks.exe (PID: 6592)
Creates files in the program directory
- 3managerAgentSetup.exe (PID: 4920)
- Agent.SnmpService.exe (PID: 5776)
Reads the machine GUID from the registry
- 3managerAgentSetup.exe (PID: 4920)
- Agent.SnmpService.exe (PID: 5776)
- Agent.ControlPanel.exe (PID: 5084)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2392)
SQLite executable
- msiexec.exe (PID: 2392)
Reads the software policy settings
- Agent.SnmpService.exe (PID: 5776)
- slui.exe (PID: 7556)
Creates a software uninstall entry
- msiexec.exe (PID: 2392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:01:24 07:31:24+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 156160 |
| InitializedDataSize: | 330752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14280 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
160
Monitored processes
26
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2340 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 2147942487 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | "C:\Users\admin\AppData\Local\Temp\{87E0F159-E955-4A68-B339-33B4BCE04EB7}\.cr\3managerAgentSetup.2.0.72.0.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\RarSFX0\3managerAgentSetup.2.0.72.0.exe" -burn.filehandle.attached=580 -burn.filehandle.self=732 /install /passive | C:\Users\admin\AppData\Local\Temp\{87E0F159-E955-4A68-B339-33B4BCE04EB7}\.cr\3managerAgentSetup.2.0.72.0.exe | 3managerAgentSetup.2.0.72.0.exe | ||||||||||||
User: admin Company: 3Manager Integrity Level: MEDIUM Description: 3manager SNMP service Exit code: 0 Version: 2.0.72.0 Modules
| |||||||||||||||
| 2960 | .\3managerAgentSetup.2.0.72.0.exe /install /passive | C:\Users\admin\AppData\Local\Temp\RarSFX0\3managerAgentSetup.2.0.72.0.exe | cmd.exe | ||||||||||||
User: admin Company: 3Manager Integrity Level: MEDIUM Description: 3manager SNMP service Exit code: 0 Version: 2.0.72.0 Modules
| |||||||||||||||
| 3268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4812 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\RarSFX0\run.bat" " | C:\Windows\SysWOW64\cmd.exe | — | fix (2).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\Users\admin\AppData\Local\Temp\{594196A6-62BE-4BA9-9CA8-023AAFBCACC6}\.be\3managerAgentSetup.exe" -q -burn.elevated BurnPipe.{7EF0E916-E90B-465F-81D4-5CC91BDE71CC} {07683355-3E42-4BF4-A511-6ED1F26660B0} 2600 | C:\Users\admin\AppData\Local\Temp\{594196A6-62BE-4BA9-9CA8-023AAFBCACC6}\.be\3managerAgentSetup.exe | 3managerAgentSetup.2.0.72.0.exe | ||||||||||||
User: admin Company: 3Manager Integrity Level: HIGH Description: 3manager SNMP service Exit code: 0 Version: 2.0.72.0 Modules
| |||||||||||||||
| 5084 | "C:\Program Files (x86)\3Manager\SNMPService\Agent.ControlPanel.exe" /setup /bootstrapperPath=C:\Users\admin\AppData\Local\Temp\RarSFX0\3managerAgentSetup.2.0.72.0.exe | C:\Program Files (x86)\3Manager\SNMPService\Agent.ControlPanel.exe | — | msiexec.exe | |||||||||||
User: admin Company: 3Manager Integrity Level: HIGH Description: Agent.ControlPanel Exit code: 0 Version: 2.0.72.0 Modules
| |||||||||||||||
Total events
11 483
Read events
10 939
Write events
492
Delete events
52
Modification events
| (PID) Process: | (7352) 3managerAgentSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000028E44C7051A5DB01B81C0000BC1C0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7400) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7400) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000005BF9A87151A5DB01E81C0000B41D0000E80300000100000000000000000000002BB71C1ACF31064EB07895A07FA53CA500000000000000000000000000000000 | |||
| (PID) Process: | (7444) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B8EBB47151A5DB01141D0000D81D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7444) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B8EBB47151A5DB01141D0000341D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7444) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000C0BECC7151A5DB01141D0000301D0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7400) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000028E44C7051A5DB01E81C0000001D0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7400) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000961BA57051A5DB01E81C0000001D0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7400) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000961BA57051A5DB01E81C0000001D0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7400) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000009834AC7051A5DB01E81C0000001D0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
44
Suspicious files
26
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7400 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7248 | 3managerAgentSetup.2.0.72.0.exe | C:\Users\admin\AppData\Local\Temp\{A2D46EB6-6967-47C7-913D-4554DC6C67FC}\.ba\logo.png | image | |
MD5:FE32817E2672103CBDC45E19F22A7B1E | SHA256:F4FA662E2F1E21D6F73D0D8BF40F624AE3FC985728AA472D040486E0C92CA213 | |||
| 7220 | 3managerAgentSetup.2.0.72.0.exe | C:\Users\admin\AppData\Local\Temp\{EC5CAB47-2EB7-4286-B61D-5083F581EC9A}\.cr\3managerAgentSetup.2.0.72.0.exe | executable | |
MD5:2356E8C1157D7CAC57B436B6B003074F | SHA256:119652E98D845BC93FAF4E8B99B33A4D2E7FD1C10FFB41287F6AC50F91DC31B2 | |||
| 2600 | 3managerAgentSetup.2.0.72.0.exe | C:\Users\admin\AppData\Local\Temp\{594196A6-62BE-4BA9-9CA8-023AAFBCACC6}\.ba\1033\thm.wxl | xml | |
MD5:4832EEB04D3A62A114332C1C46DAA37C | SHA256:8DBFDB6AA0A3077BEE04FFE5E5CF7642731C9E8E618F77AA6EA30E428CCB8F5B | |||
| 6032 | fix (2).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\run.bat | text | |
MD5:98DEB9C0AA61AB745D619DDE687EEC40 | SHA256:2AEE3BAB3A6D4C349BA2786E9FD2E4CD2EA40DCA4A869344C354FCC3BD00E96F | |||
| 2600 | 3managerAgentSetup.2.0.72.0.exe | C:\Users\admin\AppData\Local\Temp\{594196A6-62BE-4BA9-9CA8-023AAFBCACC6}\.ba\thm.xml | xml | |
MD5:CC4D95074CBA46A406B28B94A52FE64F | SHA256:C0FC250407F5A62EBB1BCE9806E549D16CD5770BA76806697C72B58416243774 | |||
| 2600 | 3managerAgentSetup.2.0.72.0.exe | C:\Users\admin\AppData\Local\Temp\{594196A6-62BE-4BA9-9CA8-023AAFBCACC6}\.ba\thm.wxl | xml | |
MD5:4832EEB04D3A62A114332C1C46DAA37C | SHA256:8DBFDB6AA0A3077BEE04FFE5E5CF7642731C9E8E618F77AA6EA30E428CCB8F5B | |||
| 6032 | fix (2).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\3managerAgentSetup.2.0.72.0.exe | executable | |
MD5:E071E372D680EB129100B8817FBE7C03 | SHA256:59731161A19619EA9BBC604D9F57EE670AA5D7E6635654CB9E9AAEE4F44C914B | |||
| 7248 | 3managerAgentSetup.2.0.72.0.exe | C:\Users\admin\AppData\Local\Temp\{A2D46EB6-6967-47C7-913D-4554DC6C67FC}\.ba\wixstdba.dll | executable | |
MD5:8CA04519005AD03B4D9E062B97D7F79D | SHA256:7B9F919A3D1974FD8FA35AD189EDC8BF287F476BD377E713E616B26864A4B0D3 | |||
| 7248 | 3managerAgentSetup.2.0.72.0.exe | C:\Users\admin\AppData\Local\Temp\{A2D46EB6-6967-47C7-913D-4554DC6C67FC}\.ba\thm.wxl | xml | |
MD5:4832EEB04D3A62A114332C1C46DAA37C | SHA256:8DBFDB6AA0A3077BEE04FFE5E5CF7642731C9E8E618F77AA6EA30E428CCB8F5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1180 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1180 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8108 | svchost.exe | 69.192.162.125:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1180 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Agent.SnmpService.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\3Manager\SNMPService\x86\SQLite.Interop.dll"...
|
Agent.SnmpService.exe | SQLite error (1): no such table: Versions
|