| File name: | Downloader_Diablo2_frFR.exe |
| Full analysis: | https://app.any.run/tasks/0a348c51-6200-4254-9bf7-e66369e8ac7b |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 03:11:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 51E9C66E88D2BDF104D470F116E5B922 |
| SHA1: | 758F3FE56888276052679D7827614D8AE582FA70 |
| SHA256: | 44FDBF9D4C025E59248B4730C8E3146783E1DCF7843854BE98DAD011A1E069DD |
| SSDEEP: | 49152:b2BYDgYLCnujaMULb2DJT1JRWp1N9RoHxPhLniyOyhIhAMqgas:4YDgY2Yef2TXCHoHuyOyhICxs |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- Downloader_Diablo2_frFR.exe (PID: 3248)
Reads Internet Cache Settings
- Downloader_Diablo2_frFR.exe (PID: 3248)
Reads internet explorer settings
- Downloader_Diablo2_frFR.exe (PID: 3248)
INFO
Reads settings of System Certificates
- Downloader_Diablo2_frFR.exe (PID: 3248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:08:06 04:14:25+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 819200 |
| InitializedDataSize: | 454656 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa38a3 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.2.0.1285 |
| ProductVersionNumber: | 2.2.0.1285 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Blizzard Entertainment |
| FileDescription: | Blizzard Downloader |
| FileVersion: | 2, 2, 0, 1285 |
| InternalName: | BlizzardDownloader |
| LegalCopyright: | (c) 2004-2010 Blizzard Entertainment |
| OriginalFileName: | BlizzardDownloader.exe |
| ProductName: | Blizzard Downloader |
| ProductVersion: | 2, 2, 0, 1285 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Aug-2010 02:14:25 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | Blizzard Entertainment |
| FileDescription: | Blizzard Downloader |
| FileVersion: | 2, 2, 0, 1285 |
| InternalName: | BlizzardDownloader |
| LegalCopyright: | (c) 2004-2010 Blizzard Entertainment |
| OriginalFilename: | BlizzardDownloader.exe |
| ProductName: | Blizzard Downloader |
| ProductVersion: | 2, 2, 0, 1285 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 06-Aug-2010 02:14:25 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000C7F5F | 0x000C8000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.68039 |
.rdata | 0x000C9000 | 0x0004613E | 0x00047000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.05482 |
.data | 0x00110000 | 0x000143B8 | 0x00007000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.88476 |
.rsrc | 0x00125000 | 0x00020D78 | 0x00021000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.43711 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.08641 | 720 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 3.82425 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 3.85418 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 6.4567 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 6.72856 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 6.05448 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 6.19081 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 6.04245 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 5.73163 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 4.51429 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
MSIMG32.dll |
OLEAUT32.dll |
RPCRT4.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
Total processes
34
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3248 | "C:\Users\admin\AppData\Local\Temp\Downloader_Diablo2_frFR.exe" | C:\Users\admin\AppData\Local\Temp\Downloader_Diablo2_frFR.exe | explorer.exe | ||||||||||||
User: admin Company: Blizzard Entertainment Integrity Level: MEDIUM Description: Blizzard Downloader Exit code: 0 Version: 2, 2, 0, 1285 Modules
| |||||||||||||||
Total events
718
Read events
687
Write events
31
Delete events
0
Modification events
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-2 |
Value: Access the computers and devices that are on your network. | |||
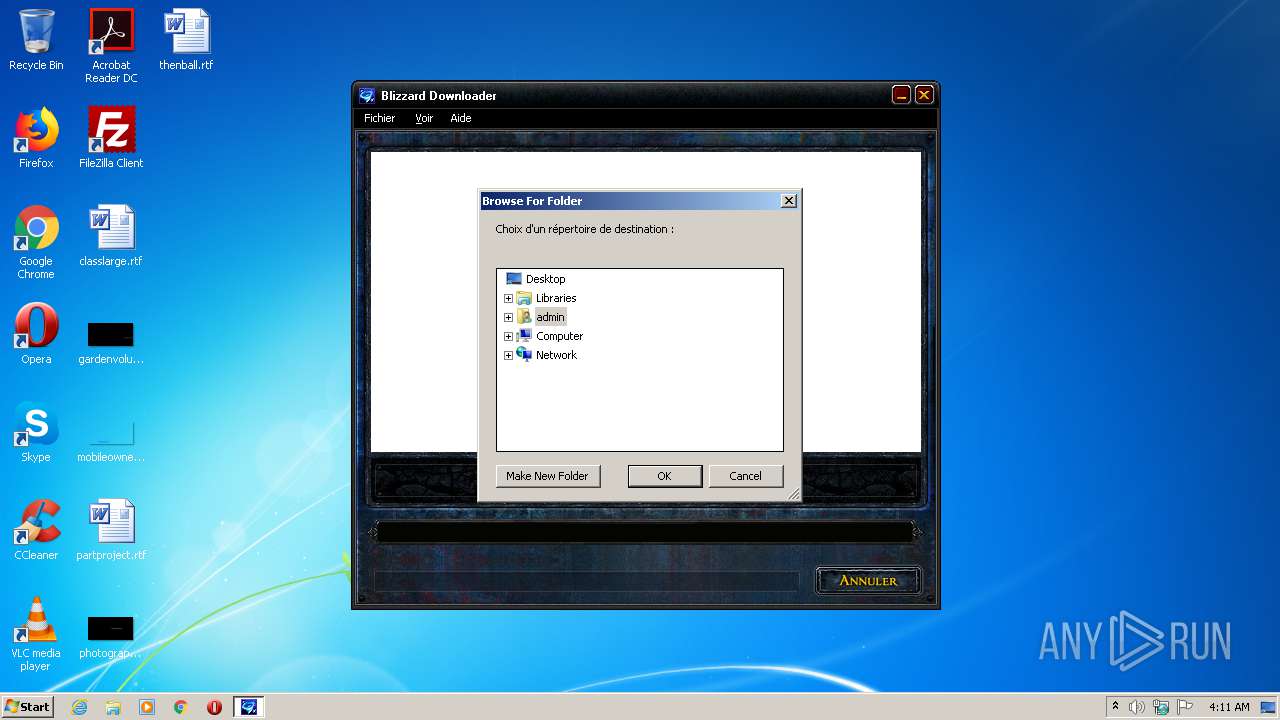
| (PID) Process: | (3248) Downloader_Diablo2_frFR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
Executable files
0
Suspicious files
20
Text files
71
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\Local\Temp\Cab643E.tmp | — | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\Local\Temp\Tar643F.tmp | — | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\Local\Temp\_TR5E03.tmp | torrent | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_93E4B2BA79A897B3100CCB27F2D3BF4F | binary | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_5FDD03068CBBD8A96F3AB9595BA10093 | der | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FC5A820A001B41D68902E051F36A5282_9B21FCC8CE91B1027236BD6C0193C8E4 | binary | |
MD5:— | SHA256:— | |||
| 3248 | Downloader_Diablo2_frFR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FC5A820A001B41D68902E051F36A5282_9B21FCC8CE91B1027236BD6C0193C8E4 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
16
DNS requests
16
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3248 | Downloader_Diablo2_frFR.exe | GET | — | 12.129.222.52:80 | http://12.129.222.52/update/Downloader.ini | US | — | — | suspicious |
3248 | Downloader_Diablo2_frFR.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
3248 | Downloader_Diablo2_frFR.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
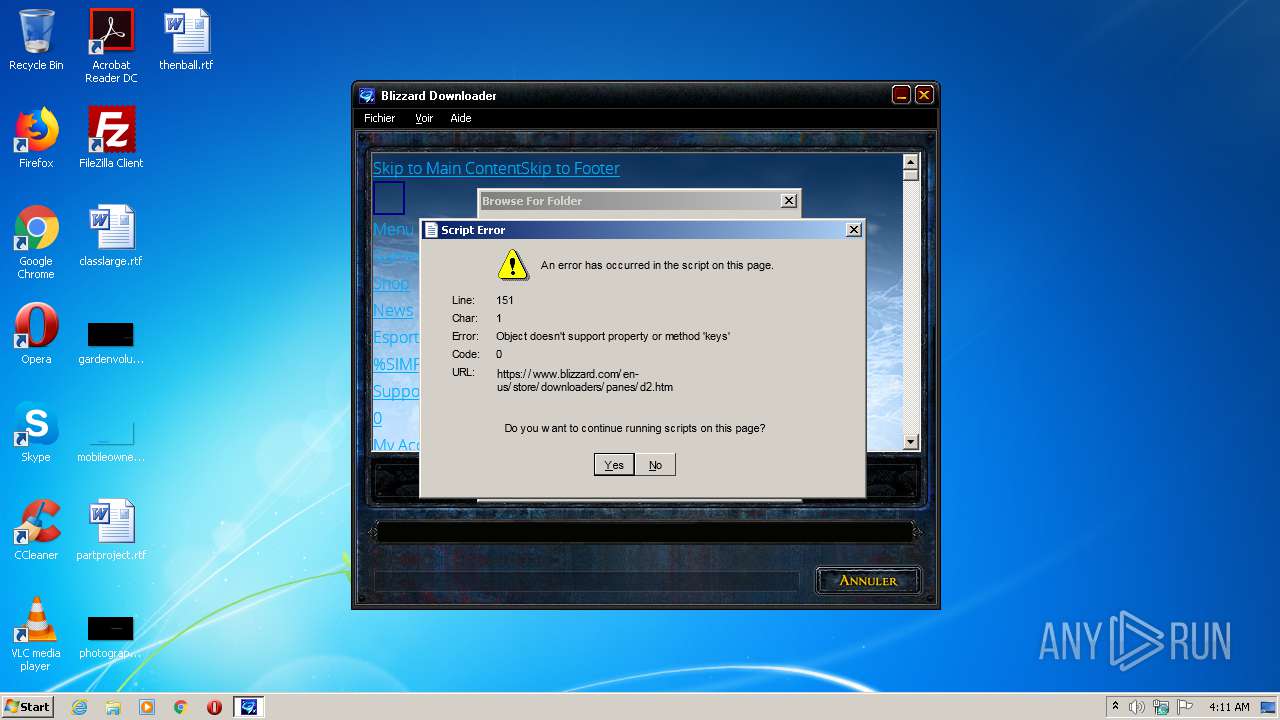
3248 | Downloader_Diablo2_frFR.exe | GET | 307 | 54.171.248.246:80 | http://www.blizzard.com/store/downloaders/panes/d2.htm | IE | html | 187 b | unknown |
3248 | Downloader_Diablo2_frFR.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
3248 | Downloader_Diablo2_frFR.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
3248 | Downloader_Diablo2_frFR.exe | GET | 200 | 13.35.253.97:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3248 | Downloader_Diablo2_frFR.exe | GET | 200 | 13.35.253.5:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3248 | Downloader_Diablo2_frFR.exe | GET | 200 | 13.35.253.165:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAgHDzg1Ixr%2B7A%2BFh3smVB4%3D | US | der | 471 b | whitelisted |
3248 | Downloader_Diablo2_frFR.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3248 | Downloader_Diablo2_frFR.exe | 12.129.222.52:80 | us.version.worldofwarcraft.com | AT&T Enhanced Network Services | US | suspicious |
— | — | 54.171.248.246:80 | www.blizzard.com | Amazon.com, Inc. | IE | unknown |
3248 | Downloader_Diablo2_frFR.exe | 54.171.248.246:443 | www.blizzard.com | Amazon.com, Inc. | IE | unknown |
3248 | Downloader_Diablo2_frFR.exe | 13.35.253.148:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
3248 | Downloader_Diablo2_frFR.exe | 13.35.253.5:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
3248 | Downloader_Diablo2_frFR.exe | 13.35.253.110:443 | d9me64que7cqs.cloudfront.net | — | US | suspicious |
3248 | Downloader_Diablo2_frFR.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3248 | Downloader_Diablo2_frFR.exe | 13.35.253.97:80 | o.ss2.us | — | US | unknown |
3248 | Downloader_Diablo2_frFR.exe | 13.35.253.165:80 | ocsp.sca1b.amazontrust.com | — | US | whitelisted |
3248 | Downloader_Diablo2_frFR.exe | 2.16.177.91:443 | blznav.akamaized.net | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
us.version.worldofwarcraft.com |
| suspicious |
eu.version.worldofwarcraft.com |
| unknown |
kr.version.worldofwarcraft.com |
| unknown |
cn.version.warcraftchina.com |
| unknown |
tw.version.worldofwarcraft.com |
| unknown |
www.blizzard.com |
| unknown |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3248 | Downloader_Diablo2_frFR.exe | Potential Corporate Privacy Violation | ET GAMES Blizzard Downloader Client User-Agent (Blizzard Downloader 2.x) |
3248 | Downloader_Diablo2_frFR.exe | Potential Corporate Privacy Violation | ET GAMES Blizzard Web Downloader Install Detected |