| File name: | SecuriteInfo.com.FileRepPup.29913.28349 |
| Full analysis: | https://app.any.run/tasks/4fd600e9-acf8-41e3-b15d-8f20d2a99bc8 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 16:55:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | E31838F368F6733FE82FEDAECD51FBA1 |
| SHA1: | 0214D81EF29C2A825E44DEEC77BCC3693843E24D |
| SHA256: | 44FA3E34D6C2E76C0FCEAEDF241B3F31F5C3F0F0F35823A0B4C712A3F09D8A8A |
| SSDEEP: | 196608:rIqu6wjYBKVyj08HBw7WxxMxyemPlj0jQkzz5:taj1H8X8yemdj0j7P5 |
MALICIOUS
Vulnerable driver has been detected
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Drops 7-zip archiver for unpacking
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Executable content was dropped or overwritten
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
There is functionality for taking screenshot (YARA)
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Reads security settings of Internet Explorer
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Adds/modifies Windows certificates
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
INFO
Checks supported languages
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
The sample compiled with chinese language support
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Create files in a temporary directory
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Checks proxy server information
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Reads the machine GUID from the registry
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Reads the computer name
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
The sample compiled with english language support
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Reads the software policy settings
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
- slui.exe (PID: 5048)
Creates files or folders in the user directory
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Creates files in the program directory
- SecuriteInfo.com.FileRepPup.29913.28349.exe (PID: 5376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:27 06:28:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 1184256 |
| InitializedDataSize: | 1335296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x73842 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.5025.1025.427 |
| ProductVersionNumber: | 1.5025.1025.427 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
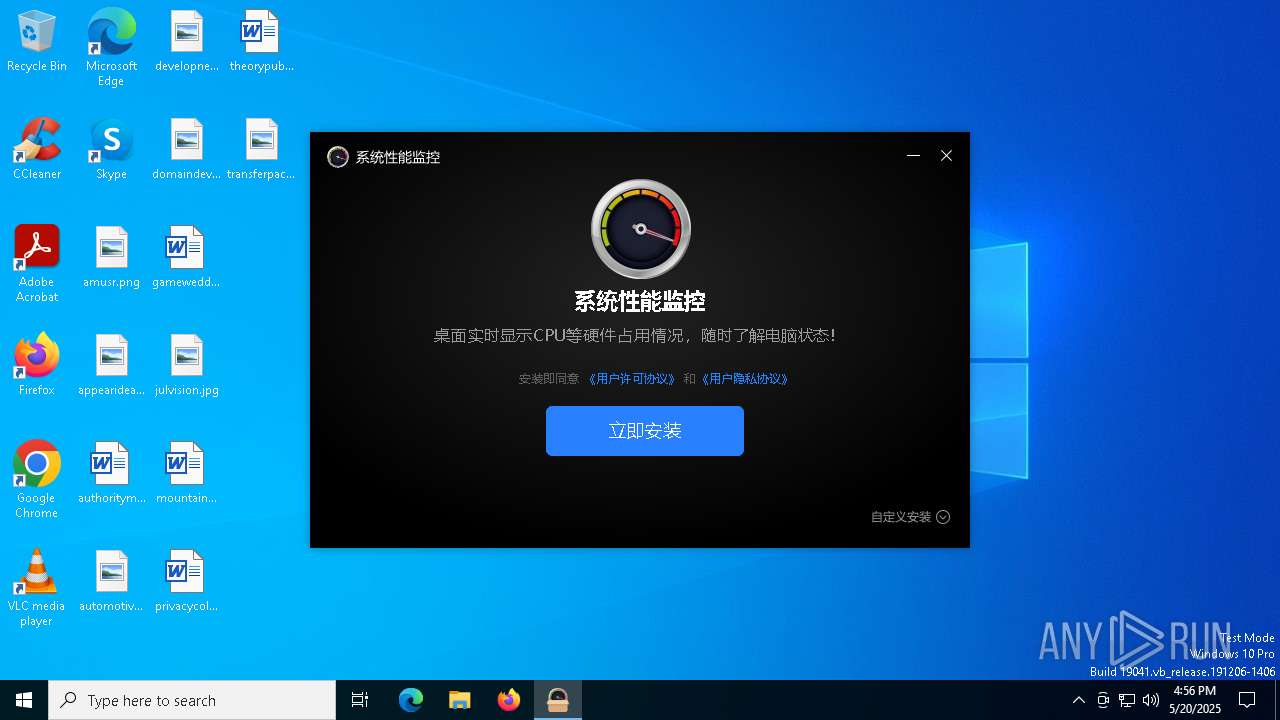
| FileDescription: | 系统性能监控 |
| FileVersion: | 1.5025.1025.427 |
| LegalCopyright: | Copyright (C) 2025 |
| ProductName: | 系统性能监控 |
| ProductVersion: | 1.5025.1025.427 |
Total processes
137
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4424 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4728 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5048 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5376 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.FileRepPup.29913.28349.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.FileRepPup.29913.28349.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 系统性能监控 Version: 1.5025.1025.427 Modules
| |||||||||||||||
| 5576 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.FileRepPup.29913.28349.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.FileRepPup.29913.28349.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 系统性能监控 Exit code: 3221226540 Version: 1.5025.1025.427 Modules
| |||||||||||||||
Total events
6 651
Read events
6 637
Write events
10
Delete events
4
Modification events
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\ComMaster |
| Operation: | write | Name: | mid |
Value: 80342cb959da2233832ae840f019ccba8b56b331eb673be97c52113eab1cd1bc | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\ComMaster |
| Operation: | write | Name: | m2 |
Value: fe9694f777e256d0cc4755a6dd1f6ad7651f60d32bec | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\ComMaster |
| Operation: | write | Name: | stat_rand |
Value: 33 | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 8094640EB5A7A1CA119C1FDDD59F810263A7FBD1 |
Value: | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\8094640EB5A7A1CA119C1FDDD59F810263A7FBD1 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000004FDD07E4D42264391E0C3742EAD1C6AE7A000000010000000C000000300A06082B06010505070309140000000100000014000000AE6C05A39313E2A2E7E2D71CD6C7F07FC86753A06200000001000000200000002CABEAFE37D06CA22ABA7391C0033D25982952C453647349763A3AB5AD6CCF69090000000100000056000000305406082B0601050507030206082B06010505070303060A2B0601040182370A030C060A2B0601040182370A030406082B0601050507030406082B0601050507030906082B0601050507030106082B06010505070308190000000100000010000000CB9DD0FCEAAA492F75CE292C21BBFBDD0300000001000000140000008094640EB5A7A1CA119C1FDDD59F810263A7FBD10F0000000100000030000000EA09C51D4C3A334CE4ACD2BC08C6A9BE352E334F45C4FCCFCAB63EDB9F82DC87D4BD2ED2FADAE11163FB954809984FF153000000010000007E000000307C301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301F06092B06010401A032010230123010060A2B0601040182373C0101030200C0301B060567810C010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D0020005200360000007F0000000100000016000000301406082B0601050507030306082B060105050703091D0000000100000010000000521F5C98970D19A8E515EF6EEB6D48EF7E00000001000000080000000080C82B6886D701200000000100000087050000308205833082036BA003020102020E45E6BB038333C3856548E6FF4551300D06092A864886F70D01010C0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523631133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3134313231303030303030305A170D3334313231303030303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523631133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820222300D06092A864886F70D01010105000382020F003082020A02820201009507E873CA66F9EC14CA7B3CF70D08F1B4450B2C82B448C6EB5B3CAE83B841923314A46F7FE92ACCC6B0886BC5B689D1C6B2FF14CE511421EC4ADD1B5AC6D687EE4D3A1506ED64660B9280CA44DE73944EF3A7897F4F786308C812506D42662F4DB979284D521A8A1A80B719810E7EC48ABC644C211C4368D73D3C8AC5B266D5909AB73106C5BEE26D3206A61EF9B9EBAAA3B8BFBE826350D0F01889DFE40F79F5EAA21F2AD2702E7BE7BC93BB6D53E2487C8C100738FF66B277617EE0EA8C3CAAB4A4F6F3954A12076DFD8CB289CFD0A06177C85874B0D4233AF75D3ACAA2DB9D09DE5D442D90F181CD5792FA7EBC50046334DF6B9318BE6B36B239E4AC2436B7F0EFB61C135793B6DEB2F8E285B773A2B835AA45F2E09D36A16F548AF172566E2E88C55142441594EEA3C538969B4E4E5A0B47F30636497730BC7137E5A6EC210875FCE661163F77D5D99197840A6CD4024D74C014EDFD39FB83F25E14A104B00BE9FEEE8FE16E0BB208B36166096AB1063A659659C0F035FDC9DA288D1A118770810AA89A751D9E3A8605009EDB80D625F9DC059E27594C76395BEAF9A5A1D8830FD1FFDF3011F985CF3348F5CA6D64142C7A584FD34B0849C595641A630E793DF5B38CCA58AD9C4245796E0E87195C54B165B6BF8C9BDC13E90D6FB82EDC676EC98B11B584148A0019708379919791D41A27BF371E3207D814633C284CAF0203010001A3633061300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E04160414AE6C05A39313E2A2E7E2D71CD6C7F07FC86753A0301F0603551D23041830168014AE6C05A39313E2A2E7E2D71CD6C7F07FC86753A0300D06092A864886F70D01010C050003820201008325EDE8D1FD9552CD9EC004A09169E65CD084DEDCADA24FE84778D66598A95BA83C877C028AD16EB71673E65FC05498D574BEC1CDE21191AD23183DDDE1724496B4955EC07B8E99781643135657B3A2B33BB577DC4072ACA3EB9B353EB10821A1E7C443377932BEB5E79C2C4CBC4329998E30D3AC21E0E31DFAD80733765400222AB94D202E7068DAE553FC835CD39DF2FF440C4466F2D2E3BD46001A6D02BA255D8DA13151DD54461C4DDB9996EF1A1C045CA615EF78E079FE5DDB3EAA4C55FD9A15A96FE1A6FBDF7030E9C3EE4246EDC2930589FA7D637B3FD071817C00E898AE0E7834C325FBAF0A9F206BDD3B138F128CE2411A487A73A07769C7B65C7F82C81EFE581B282BA86CAD5E6DC005D27BB7EB80FE2537FE029B68AC425DC3EEF5CCDCF05075D236699CE67B04DF6E0669B6DE0A09485987EB7B14607A64AA6943EF91C74CEC18DD6CEF532D8C99E15EF2723ECF54C8BD67ECA40F4C45FFD3B93023074C8F10BF8696D9995AB499571CA4CCBB158953BA2C050FE4C49E19B11834D54C9DBAEDF71FAF24950478A803BBEE81E5DA5F7C8B4AA1907425A7B33E4BC82C56BDC7C8EF38E25C92F079F79C84BA742D6101207E7ED1F24F07595F8B2D4352EB460C94E1F566477977D5545B1FAD2437CB455A4EA04448C8D8B099C5158409F6D64949C065B8E61A716EA0A8F182E8453E6CD602D70A6783055AC9A410 | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\8094640EB5A7A1CA119C1FDDD59F810263A7FBD1 |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000001000007E00000001000000080000000080C82B6886D7011D0000000100000010000000521F5C98970D19A8E515EF6EEB6D48EF7F0000000100000016000000301406082B0601050507030306082B060105050703090B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D00200052003600000053000000010000007E000000307C301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301F06092B06010401A032010230123010060A2B0601040182373C0101030200C0301B060567810C010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00F0000000100000030000000EA09C51D4C3A334CE4ACD2BC08C6A9BE352E334F45C4FCCFCAB63EDB9F82DC87D4BD2ED2FADAE11163FB954809984FF10300000001000000140000008094640EB5A7A1CA119C1FDDD59F810263A7FBD1190000000100000010000000CB9DD0FCEAAA492F75CE292C21BBFBDD090000000100000056000000305406082B0601050507030206082B06010505070303060A2B0601040182370A030C060A2B0601040182370A030406082B0601050507030406082B0601050507030906082B0601050507030106082B060105050703086200000001000000200000002CABEAFE37D06CA22ABA7391C0033D25982952C453647349763A3AB5AD6CCF69140000000100000014000000AE6C05A39313E2A2E7E2D71CD6C7F07FC86753A07A000000010000000C000000300A06082B060105050703090400000001000000100000004FDD07E4D42264391E0C3742EAD1C6AE200000000100000087050000308205833082036BA003020102020E45E6BB038333C3856548E6FF4551300D06092A864886F70D01010C0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523631133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3134313231303030303030305A170D3334313231303030303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523631133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820222300D06092A864886F70D01010105000382020F003082020A02820201009507E873CA66F9EC14CA7B3CF70D08F1B4450B2C82B448C6EB5B3CAE83B841923314A46F7FE92ACCC6B0886BC5B689D1C6B2FF14CE511421EC4ADD1B5AC6D687EE4D3A1506ED64660B9280CA44DE73944EF3A7897F4F786308C812506D42662F4DB979284D521A8A1A80B719810E7EC48ABC644C211C4368D73D3C8AC5B266D5909AB73106C5BEE26D3206A61EF9B9EBAAA3B8BFBE826350D0F01889DFE40F79F5EAA21F2AD2702E7BE7BC93BB6D53E2487C8C100738FF66B277617EE0EA8C3CAAB4A4F6F3954A12076DFD8CB289CFD0A06177C85874B0D4233AF75D3ACAA2DB9D09DE5D442D90F181CD5792FA7EBC50046334DF6B9318BE6B36B239E4AC2436B7F0EFB61C135793B6DEB2F8E285B773A2B835AA45F2E09D36A16F548AF172566E2E88C55142441594EEA3C538969B4E4E5A0B47F30636497730BC7137E5A6EC210875FCE661163F77D5D99197840A6CD4024D74C014EDFD39FB83F25E14A104B00BE9FEEE8FE16E0BB208B36166096AB1063A659659C0F035FDC9DA288D1A118770810AA89A751D9E3A8605009EDB80D625F9DC059E27594C76395BEAF9A5A1D8830FD1FFDF3011F985CF3348F5CA6D64142C7A584FD34B0849C595641A630E793DF5B38CCA58AD9C4245796E0E87195C54B165B6BF8C9BDC13E90D6FB82EDC676EC98B11B584148A0019708379919791D41A27BF371E3207D814633C284CAF0203010001A3633061300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E04160414AE6C05A39313E2A2E7E2D71CD6C7F07FC86753A0301F0603551D23041830168014AE6C05A39313E2A2E7E2D71CD6C7F07FC86753A0300D06092A864886F70D01010C050003820201008325EDE8D1FD9552CD9EC004A09169E65CD084DEDCADA24FE84778D66598A95BA83C877C028AD16EB71673E65FC05498D574BEC1CDE21191AD23183DDDE1724496B4955EC07B8E99781643135657B3A2B33BB577DC4072ACA3EB9B353EB10821A1E7C443377932BEB5E79C2C4CBC4329998E30D3AC21E0E31DFAD80733765400222AB94D202E7068DAE553FC835CD39DF2FF440C4466F2D2E3BD46001A6D02BA255D8DA13151DD54461C4DDB9996EF1A1C045CA615EF78E079FE5DDB3EAA4C55FD9A15A96FE1A6FBDF7030E9C3EE4246EDC2930589FA7D637B3FD071817C00E898AE0E7834C325FBAF0A9F206BDD3B138F128CE2411A487A73A07769C7B65C7F82C81EFE581B282BA86CAD5E6DC005D27BB7EB80FE2537FE029B68AC425DC3EEF5CCDCF05075D236699CE67B04DF6E0669B6DE0A09485987EB7B14607A64AA6943EF91C74CEC18DD6CEF532D8C99E15EF2723ECF54C8BD67ECA40F4C45FFD3B93023074C8F10BF8696D9995AB499571CA4CCBB158953BA2C050FE4C49E19B11834D54C9DBAEDF71FAF24950478A803BBEE81E5DA5F7C8B4AA1907425A7B33E4BC82C56BDC7C8EF38E25C92F079F79C84BA742D6101207E7ED1F24F07595F8B2D4352EB460C94E1F566477977D5545B1FAD2437CB455A4EA04448C8D8B099C5158409F6D64949C065B8E61A716EA0A8F182E8453E6CD602D70A6783055AC9A410 | |||
| (PID) Process: | (5376) SecuriteInfo.com.FileRepPup.29913.28349.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D69B561148F01C77C54578C10926DF5B856976AD |
Value: | |||
Executable files
39
Suspicious files
8
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\Program Files (x86)\MonitorPro\{5543862C-3E02-483a-A5DF-5AE970387314}.tf | binary | |
MD5:49AC30FA6A49465B6DCC0F79C98D1060 | SHA256:8E5E38B2DEB2C9FDD3FD9E1057D3792E04F4A7FA4690027A511F429E59B84CC5 | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\Users\admin\AppData\Local\Temp\{CF3DA26B-263F-442d-9A31-009C67E3D56D}.tmp | compressed | |
MD5:63E30406776937F5ADFCD3837CD5BCE6 | SHA256:F77CCADEEE05B2ECC2D67482FDE9F601D256581CFB57ED95AE8104DB4017502B | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\ProgramData\{2BB210B6-C206-49b6-ADB0-C794CD10E596}.tmp\{3CA93FA3-7D0E-4aa9-974F-DB11B44EEA66}.tf | binary | |
MD5:0E6C688962967C138E6428BD4109E44D | SHA256:6A7A6FEC5DA0DEA0AFF2E24FD6EF344E1716C783D1631EACCA5F6E237FF9ADD0 | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\Users\admin\AppData\Local\Temp\{C42F8EC2-84E3-478c-A092-2C5414611725}.tmp\7z.dll | executable | |
MD5:2888126384D873CC49AF32BBE34BB296 | SHA256:ABA19501A8033495664879E09E60E4788537D387CF038FA8769E5B178BCCDCB4 | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\ProgramData\{2BB210B6-C206-49b6-ADB0-C794CD10E596}.tmp\game\widef.dat | binary | |
MD5:78601450E8124D307A7D6F2C45EB3405 | SHA256:AC4922C89C04172E42235DC458B00F0CAD756C1AAE99B928E01905DD74590367 | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\ProgramData\{2BB210B6-C206-49b6-ADB0-C794CD10E596}.tmp\Plugin\PopMgr.tpi | executable | |
MD5:AA3BA223D6FB0FF66B015793663C1625 | SHA256:D73C5E260BF1E326BAB561073176A6C99713C75FCD8908794204D59A9850F281 | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\ProgramData\{2BB210B6-C206-49b6-ADB0-C794CD10E596}.tmp\SuperApp\monitor_pro\monitor_pro.dat | text | |
MD5:A62B7D665F0C64492C4430E0D2ED87CE | SHA256:18F0C592C07F60B65B24396C2125DC059996C045A4A0997987AB88AE775624E4 | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\ProgramData\{2BB210B6-C206-49b6-ADB0-C794CD10E596}.tmp\Themes\UI\feedback.dat | text | |
MD5:246454DE71677EE33671C2CDADF1AB09 | SHA256:FE7F614FA43123071C6F5CCE0FF451BD8C191050B2748803CBE0C5A5AD40D412 | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\Users\admin\AppData\Local\Temp\{CD65DEC0-6842-4f4f-B55E-44889CE39C99}.tf | binary | |
MD5:48AB9C8FB5FC45BF70B1EAFE6C13FA55 | SHA256:0E388940C8322C1FC9283F95D343F669A5995B624387F63D493EB0D6C413B646 | |||
| 5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | C:\ProgramData\{2BB210B6-C206-49b6-ADB0-C794CD10E596}.tmp\updatecfg.ini | text | |
MD5:010FC5154D5333CBD7A2E93E76A72320 | SHA256:4539831B3F23817BB660369794B77EFD5C8E9A1C534131E7A452894611245B41 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
21
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | GET | 200 | 106.15.136.209:80 | http://s.ludashi.com/pc_all?app=monitor_pro&pid=home&mid=80342cb959da2233832ae840f019ccba&mid2=fe9694f777e256d0cc4755a6dd1f6ad7651f60d32bec&appver=1.5025.1025.427&modver=1.5025.1025.427&type=install&action=start&ex_ary[os]=10.0.19045&ex_ary[new_user]=1&ex_ary[ms_mid]=bb926e54-e3ca-40fd-ae90-2764341e7792&ex_ary[interval]=0 | unknown | — | — | whitelisted |
4688 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4688 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5376 | SecuriteInfo.com.FileRepPup.29913.28349.exe | 106.15.136.209:80 | s.ludashi.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | whitelisted |
4688 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4688 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4688 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
s.ludashi.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |