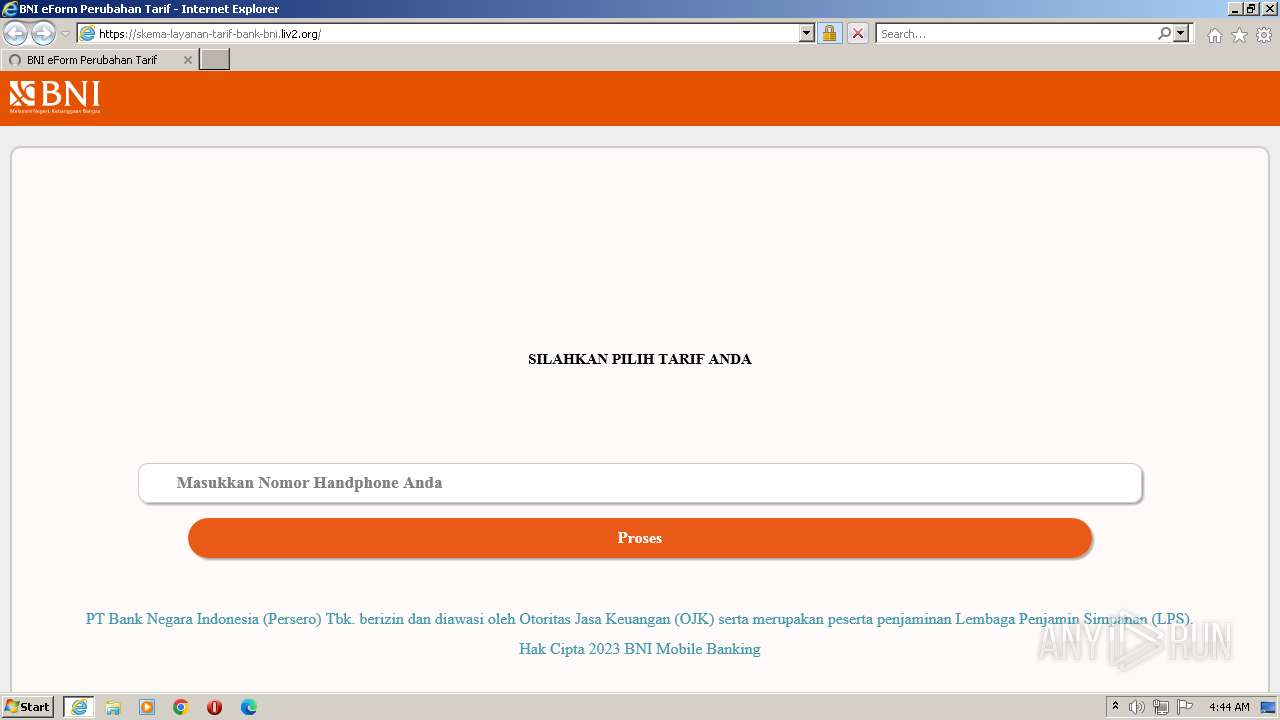
| URL: | https://skema-layanan-tarif-bank-bni.liv2.org/ |
| Full analysis: | https://app.any.run/tasks/8fb5b068-bc9c-4877-8005-91acc10ff6c2 |
| Verdict: | No threats detected |
| Analysis date: | August 10, 2023, 03:43:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9F929F7A557849D2F4BB1770DFA99627 |
| SHA1: | D63B4862967E4871EF7BA17857711AE127036C4C |
| SHA256: | 44E7C0C429C97ACC367B5D43D396945B6EC24515E6B3063BBA0FC7119E9C79BE |
| SSDEEP: | 3:N8Dicn6UHELjKSK:2uvUHELjKSK |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 1276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1276 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://skema-layanan-tarif-bank-bni.liv2.org/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1740 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1276 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
14 434
Read events
14 370
Write events
64
Delete events
0
Modification events
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000004E010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
22
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:CFBC16E33DCBEF6F773F0F79AF528F45 | SHA256:F0937890FB1053069BAAC97B7992C6D22CB74CAE20317FC05D51070D96950FFA | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:BDC293E17778D52D89ABA5298E7ED434 | SHA256:623AA547671899329706845F54E35597248AC207A11D3EA9746BF494F7FDF6A3 | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:81B5FA624E1571060038860C112F464D | SHA256:4E0BEB84FEEFA0C9D45CCA1A8D5C7696BEEBE790A560FC944FC9EDC5EE6AAB0E | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:0CEF7497B990A50E3F2CF9E72A8114DF | SHA256:1D5115D1971EF19FBD0880130756BA98D84D934C9E71BC11A375D0F0130E075A | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:2880AAF7DCB16E8BEF5F7FDBADA9975A | SHA256:BCD71026972D4185FAFC53691D533F80D77A97C8C2622CD4594E44BCAD8262F0 | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:1192D04C164D9A55C9BDDB38A5E9FB85 | SHA256:9E4A11C88F2A95C193FBBF1F1DAE4526BB594E3243E4BDAA3027A26E499365B8 | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\Y08C2YR0.htm | html | |
MD5:AB2B93CFBB35FEF8D15D5F297B2F94A0 | SHA256:DFFD68A6A11E6B1BAF02DFC296A2A1029B66E347E12F26266E7243AA49A13A01 | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:FE3E7A69792B1FB2BF9CA2DFFD3BE54C | SHA256:9D460F3DFFCD7BF5DFA4E7211F407BF49C0139FB023E88318651D5FD1F0EE563 | |||
| 1740 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\b9f7dde[1].svg | image | |
MD5:B9F7DDEFAA7D400C896A7E270B985659 | SHA256:498C69CE9039F1A4547BCFE2CBEBD6A2E29972E9CB2B18F1017338C0BD1085C6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
46
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1276 | iexplore.exe | GET | 304 | 8.253.190.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dfc7e8957d95857c | US | — | — | whitelisted |
1276 | iexplore.exe | GET | 304 | 8.253.190.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b9526e163e7f840c | US | — | — | whitelisted |
1740 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | US | der | 471 b | whitelisted |
1740 | iexplore.exe | GET | 200 | 8.253.190.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3d06d49fe9b3dc3e | US | compressed | 4.70 Kb | whitelisted |
1740 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | binary | 1.41 Kb | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
1740 | iexplore.exe | GET | 200 | 104.18.14.101:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | binary | 2.18 Kb | whitelisted |
1740 | iexplore.exe | GET | 200 | 104.18.14.101:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCyXhvYXqpequcK0vpKKT6j | US | binary | 472 b | whitelisted |
1740 | iexplore.exe | GET | 200 | 8.253.190.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c63aad77b928e2ed | US | compressed | 4.70 Kb | whitelisted |
1740 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | US | der | 724 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1740 | iexplore.exe | 188.114.96.3:443 | skema-layanan-tarif-bank-bni.liv2.org | CLOUDFLARENET | NL | malicious |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1740 | iexplore.exe | 8.253.190.121:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
1740 | iexplore.exe | 34.36.71.3:443 | infobanknews.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
1276 | iexplore.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
1276 | iexplore.exe | 8.253.190.121:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
1276 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
skema-layanan-tarif-bank-bni.liv2.org |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
bukarekening.bni.co.id |
| unknown |
unpkg.com |
| whitelisted |
applycreditcard.bni.co.id |
| unknown |
infobanknews.com |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |