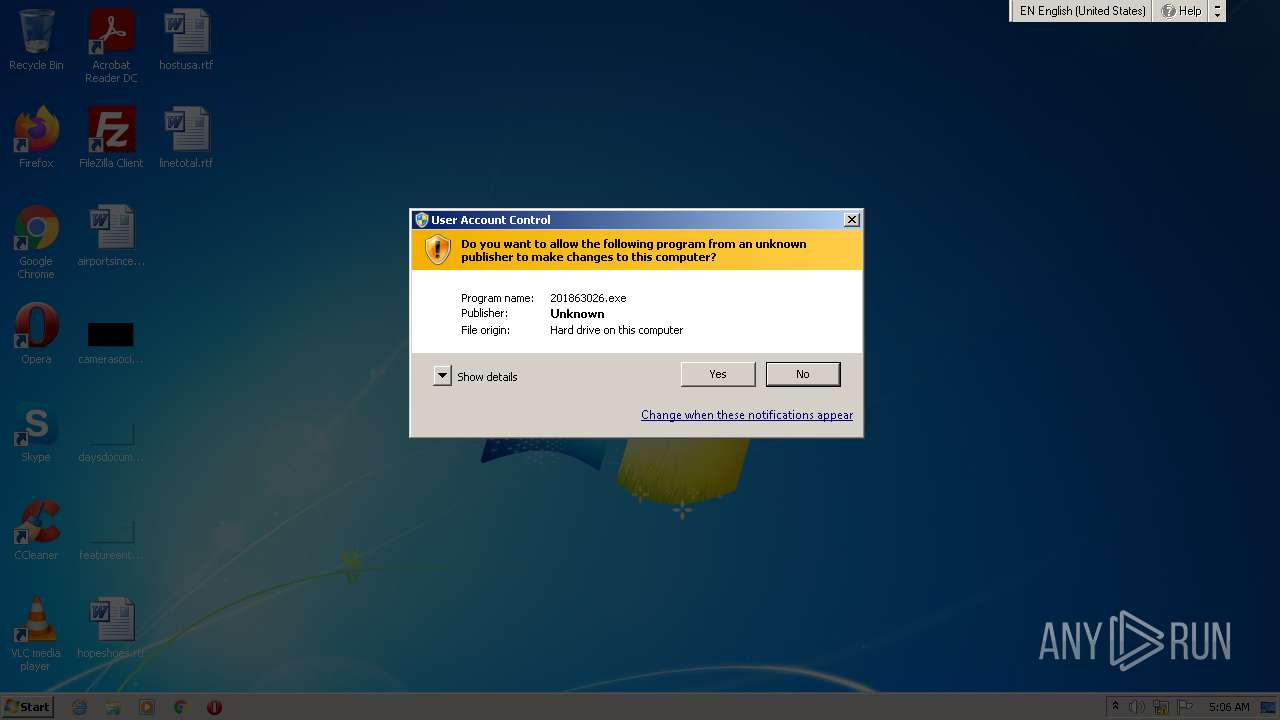
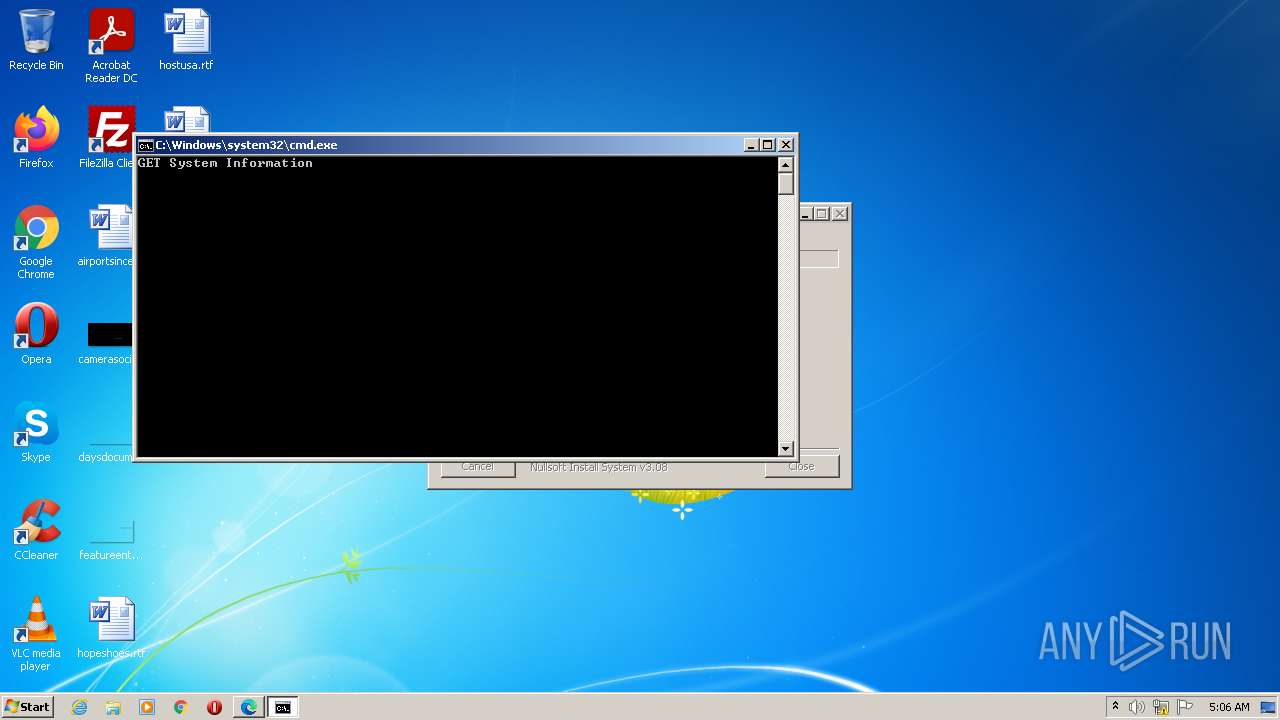
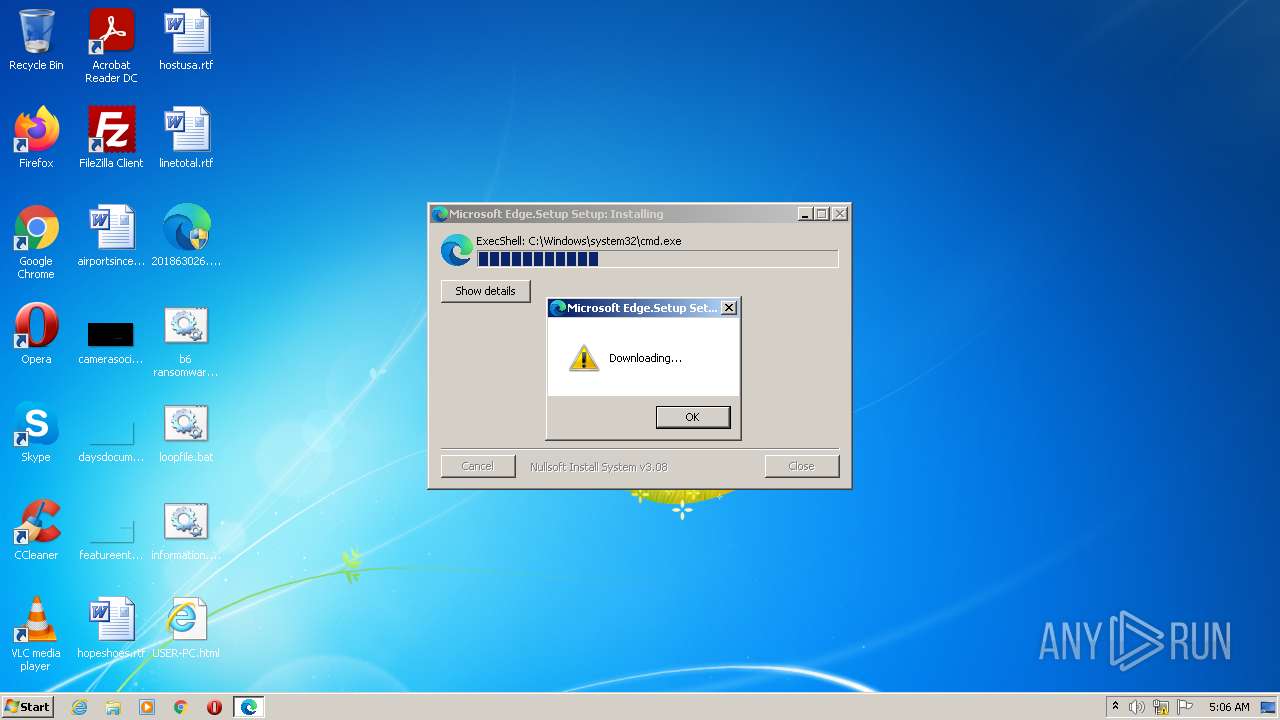
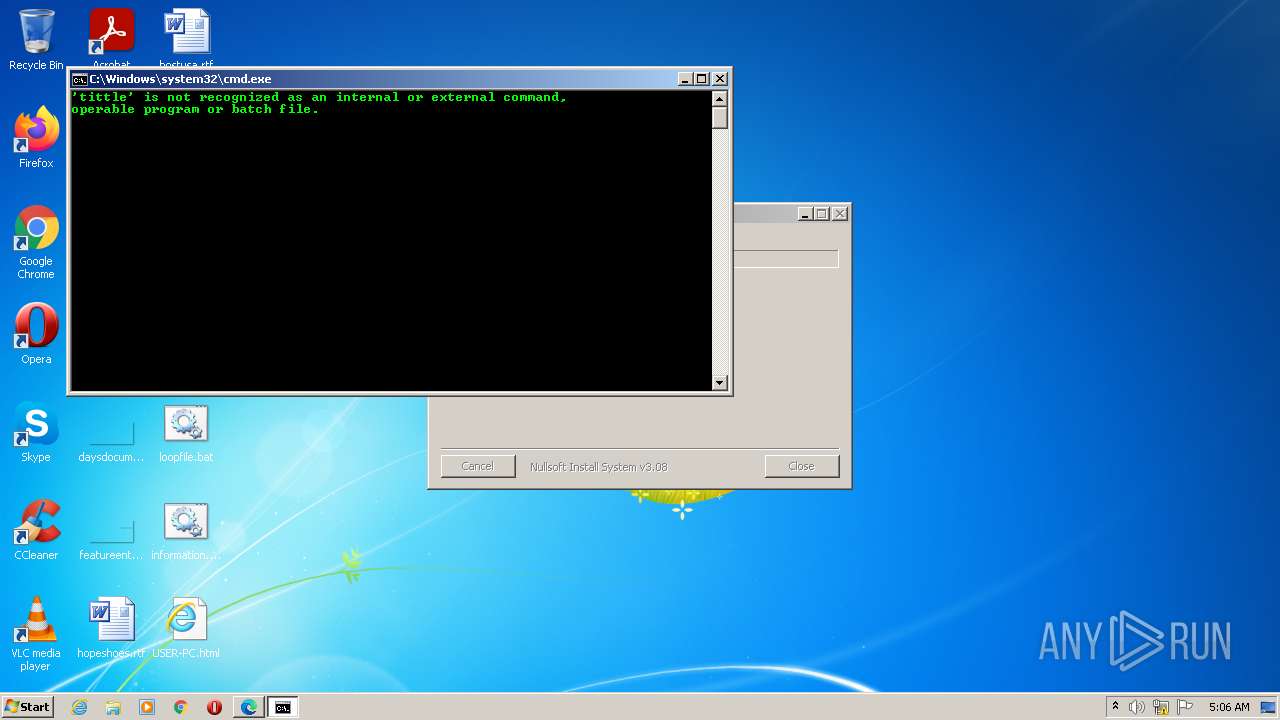
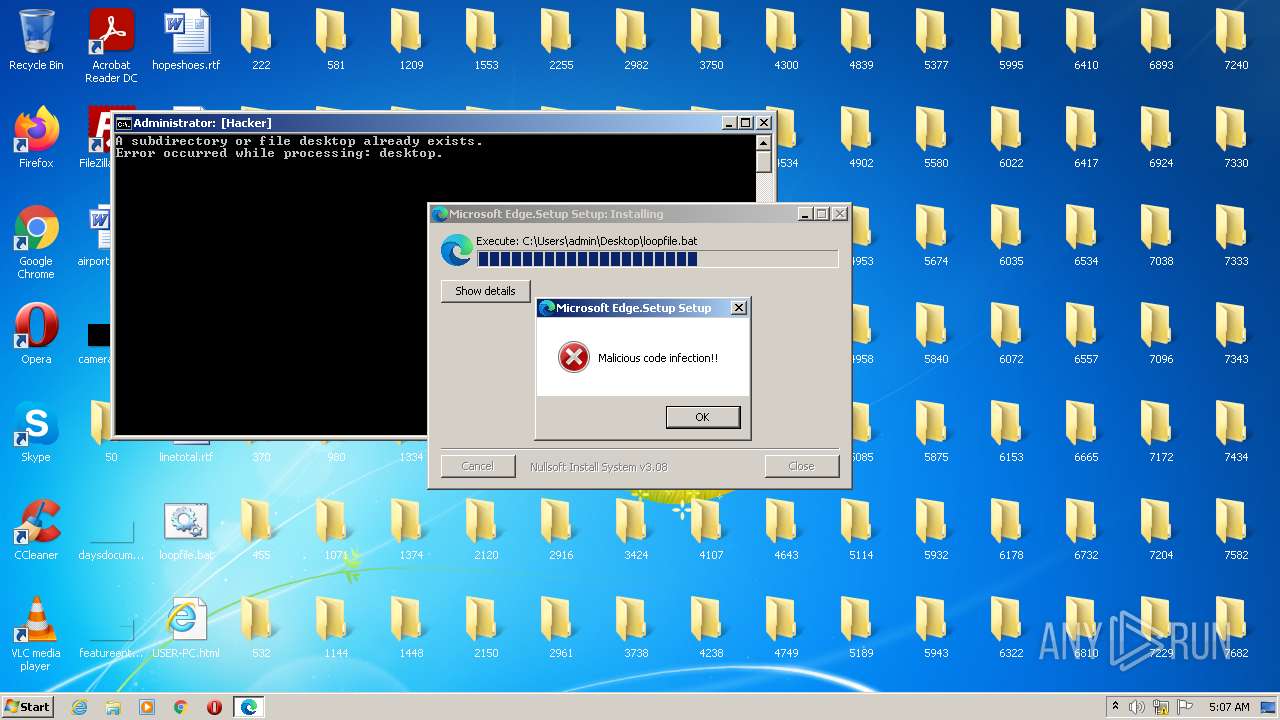
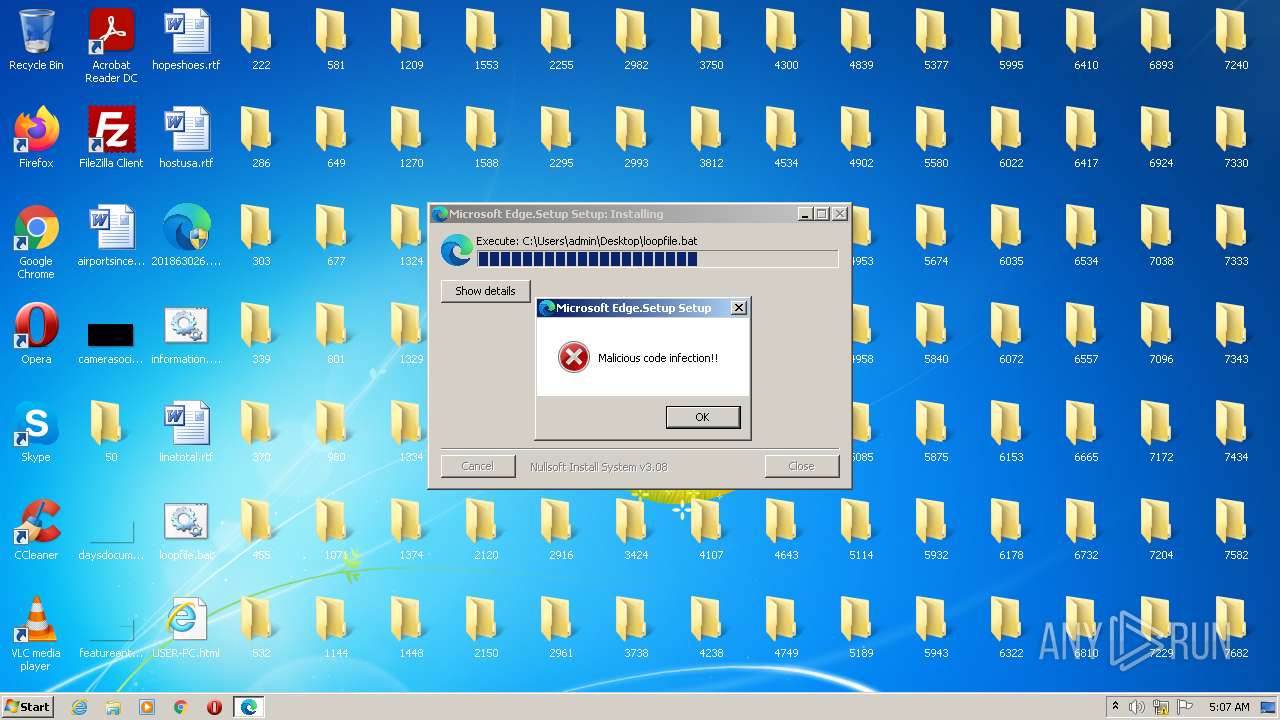
| File name: | 201863026.exe |
| Full analysis: | https://app.any.run/tasks/cb831f76-43ed-4033-a4b7-a4f15198cc75 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 04:06:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | DD7AB429877B349C7904762AA554253C |
| SHA1: | 12E0B742ED53A55FDF4DB984789EEAF5F6A271F5 |
| SHA256: | 44CE7D0EF048BDF80D7751B9F28234FB4CD4AD68A04DB60F430DB08315858596 |
| SSDEEP: | 3072:IfY/TU9fE9PEtuk/mDT9WvM2qy1KXlpnfyGWooQsBru+:+Ya6Cw9WPCniusdu+ |
MALICIOUS
Starts NET.EXE to view/change users localgroup
- cmd.exe (PID: 3852)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 3400)
- cmd.exe (PID: 2628)
Starts CertUtil for decode files
- cmd.exe (PID: 388)
SUSPICIOUS
Reads the computer name
- 201863026.exe (PID: 2848)
- msiexec.exe (PID: 3192)
Checks supported languages
- 201863026.exe (PID: 2848)
- cmd.exe (PID: 1936)
- msiexec.exe (PID: 3192)
- cmd.exe (PID: 3400)
- cmd.exe (PID: 1708)
- cmd.exe (PID: 3324)
- mode.com (PID: 2452)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 2628)
- cmd.exe (PID: 688)
- cmd.exe (PID: 1292)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 388)
- cmd.exe (PID: 768)
- cmd.exe (PID: 188)
- cmd.exe (PID: 2300)
- cmd.exe (PID: 2380)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 1936)
Starts CMD.EXE for commands execution
- 201863026.exe (PID: 2848)
- cmd.exe (PID: 1708)
- cmd.exe (PID: 388)
- cmd.exe (PID: 188)
Reads the time zone
- net1.exe (PID: 3332)
Application launched itself
- cmd.exe (PID: 388)
- cmd.exe (PID: 1708)
- cmd.exe (PID: 188)
Creates files in the Windows directory
- certutil.exe (PID: 1300)
- certutil.exe (PID: 2268)
- certutil.exe (PID: 1936)
- certutil.exe (PID: 120)
- certutil.exe (PID: 2444)
- certutil.exe (PID: 3524)
- certutil.exe (PID: 3224)
- certutil.exe (PID: 3888)
- certutil.exe (PID: 1176)
- certutil.exe (PID: 3264)
- certutil.exe (PID: 3176)
- certutil.exe (PID: 1988)
- certutil.exe (PID: 972)
- certutil.exe (PID: 124)
- certutil.exe (PID: 3496)
- certutil.exe (PID: 3728)
- certutil.exe (PID: 2388)
- certutil.exe (PID: 480)
- certutil.exe (PID: 2548)
- certutil.exe (PID: 2132)
- certutil.exe (PID: 2044)
- certutil.exe (PID: 2504)
- certutil.exe (PID: 904)
- certutil.exe (PID: 1436)
- certutil.exe (PID: 2692)
- certutil.exe (PID: 4044)
- certutil.exe (PID: 3220)
Removes files from Windows directory
- certutil.exe (PID: 1300)
- certutil.exe (PID: 2268)
- certutil.exe (PID: 120)
- certutil.exe (PID: 1936)
- certutil.exe (PID: 2444)
- certutil.exe (PID: 3524)
- certutil.exe (PID: 3224)
- certutil.exe (PID: 3888)
- certutil.exe (PID: 1176)
- certutil.exe (PID: 3264)
- certutil.exe (PID: 3176)
- certutil.exe (PID: 1988)
- certutil.exe (PID: 972)
- certutil.exe (PID: 3496)
- certutil.exe (PID: 124)
- certutil.exe (PID: 3728)
- certutil.exe (PID: 2388)
- certutil.exe (PID: 480)
- certutil.exe (PID: 2132)
- certutil.exe (PID: 2548)
- certutil.exe (PID: 904)
- certutil.exe (PID: 1436)
- certutil.exe (PID: 2044)
- certutil.exe (PID: 2692)
- certutil.exe (PID: 2504)
- certutil.exe (PID: 4044)
- certutil.exe (PID: 3220)
Starts CertUtil for decode files
- cmd.exe (PID: 188)
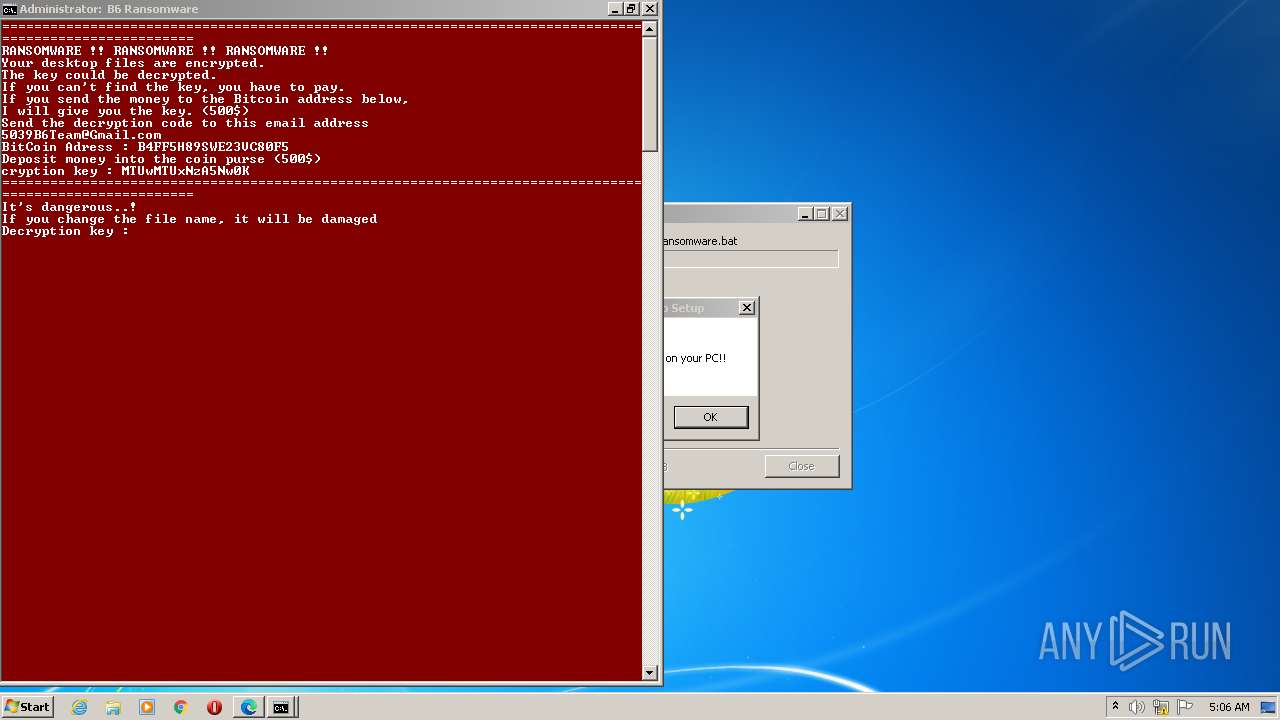
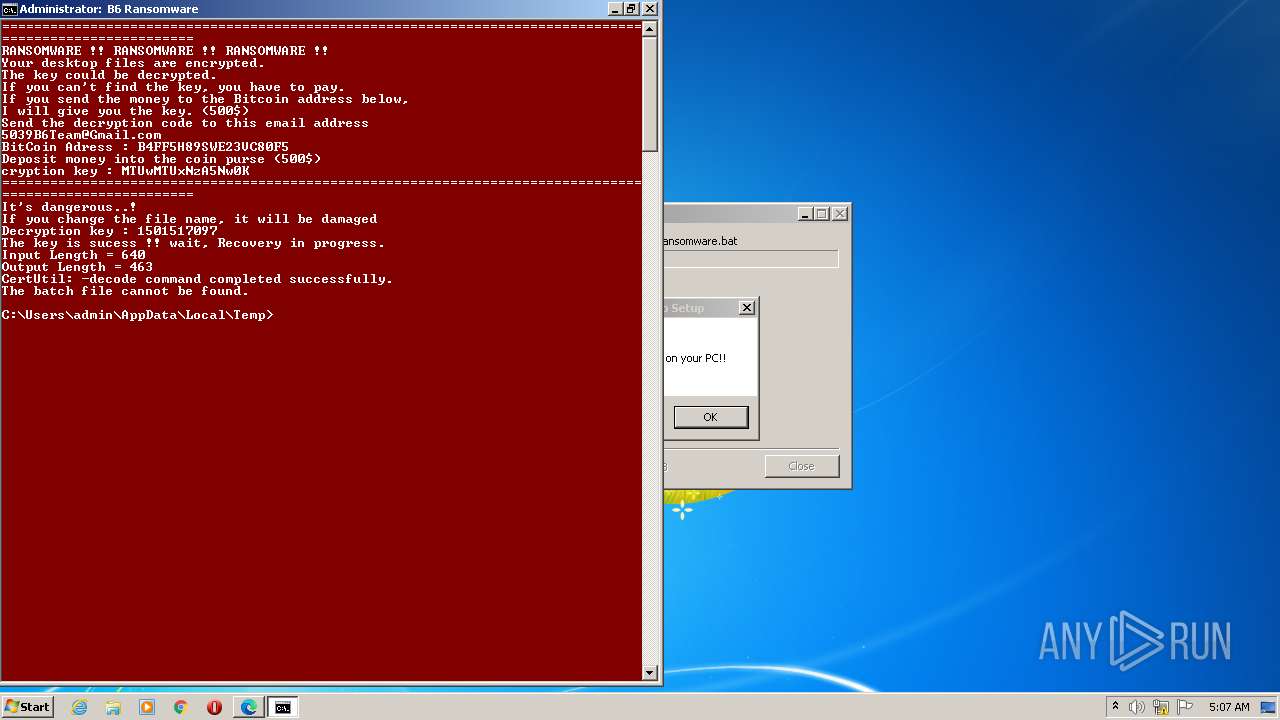
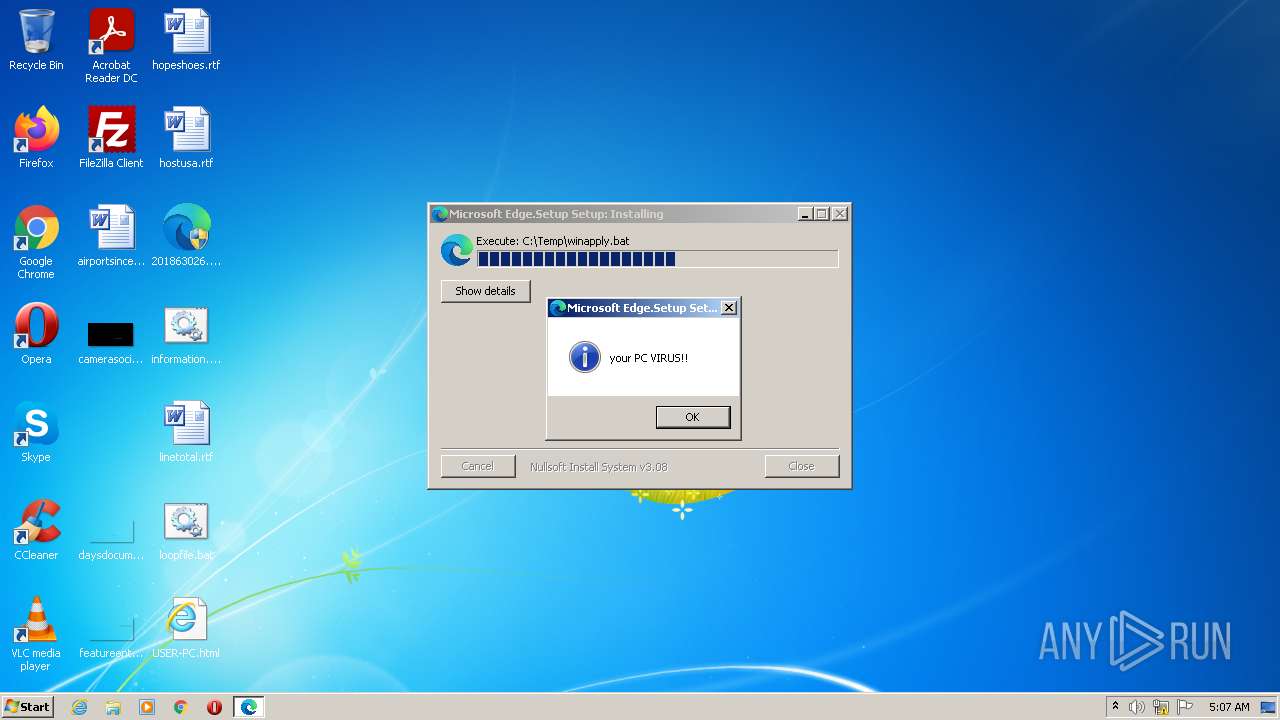
Changes the desktop background image
- 201863026.exe (PID: 2848)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 2300)
INFO
Checks supported languages
- WMIC.exe (PID: 3364)
- WMIC.exe (PID: 1616)
- WMIC.exe (PID: 1600)
- WMIC.exe (PID: 2600)
- WMIC.exe (PID: 3088)
- WMIC.exe (PID: 2400)
- WMIC.exe (PID: 2300)
- WMIC.exe (PID: 3784)
- WMIC.exe (PID: 2772)
- WMIC.exe (PID: 2540)
- WMIC.exe (PID: 3876)
- net.exe (PID: 3096)
- net.exe (PID: 3200)
- net1.exe (PID: 3412)
- net1.exe (PID: 1156)
- net.exe (PID: 3076)
- net1.exe (PID: 3332)
- xcopy.exe (PID: 3604)
- cacls.exe (PID: 660)
- certutil.exe (PID: 1300)
- cacls.exe (PID: 1596)
- certutil.exe (PID: 120)
- findstr.exe (PID: 3076)
- certutil.exe (PID: 2268)
- findstr.exe (PID: 1932)
- timeout.exe (PID: 3072)
- findstr.exe (PID: 2676)
- certutil.exe (PID: 3224)
- findstr.exe (PID: 2220)
- certutil.exe (PID: 2444)
- certutil.exe (PID: 1936)
- findstr.exe (PID: 2416)
- findstr.exe (PID: 3308)
- certutil.exe (PID: 3524)
- findstr.exe (PID: 468)
- certutil.exe (PID: 3888)
- findstr.exe (PID: 1060)
- certutil.exe (PID: 1176)
- findstr.exe (PID: 2044)
- certutil.exe (PID: 3264)
- findstr.exe (PID: 2736)
- certutil.exe (PID: 3176)
- findstr.exe (PID: 3524)
- certutil.exe (PID: 1988)
- findstr.exe (PID: 3032)
- certutil.exe (PID: 972)
- findstr.exe (PID: 3288)
- certutil.exe (PID: 124)
- certutil.exe (PID: 3496)
- certutil.exe (PID: 2388)
- certutil.exe (PID: 3728)
- certutil.exe (PID: 2132)
- certutil.exe (PID: 2548)
- certutil.exe (PID: 480)
- certutil.exe (PID: 2692)
- certutil.exe (PID: 2504)
- certutil.exe (PID: 904)
- certutil.exe (PID: 1436)
- certutil.exe (PID: 2044)
- certutil.exe (PID: 3220)
- certutil.exe (PID: 4044)
- rundll32.exe (PID: 3592)
Reads the computer name
- WMIC.exe (PID: 3364)
- WMIC.exe (PID: 1616)
- WMIC.exe (PID: 1600)
- WMIC.exe (PID: 2600)
- WMIC.exe (PID: 3088)
- WMIC.exe (PID: 2400)
- WMIC.exe (PID: 3876)
- WMIC.exe (PID: 3784)
- WMIC.exe (PID: 2300)
- WMIC.exe (PID: 2772)
- WMIC.exe (PID: 2540)
- net1.exe (PID: 3332)
- net1.exe (PID: 3412)
- net1.exe (PID: 1156)
- cacls.exe (PID: 660)
- cacls.exe (PID: 1596)
- certutil.exe (PID: 2268)
- certutil.exe (PID: 1300)
- certutil.exe (PID: 120)
- certutil.exe (PID: 2444)
- certutil.exe (PID: 1936)
- certutil.exe (PID: 3224)
- certutil.exe (PID: 3888)
- certutil.exe (PID: 3524)
- certutil.exe (PID: 1176)
- certutil.exe (PID: 3264)
- certutil.exe (PID: 3176)
- certutil.exe (PID: 1988)
- certutil.exe (PID: 972)
- certutil.exe (PID: 124)
- certutil.exe (PID: 3496)
- certutil.exe (PID: 2388)
- certutil.exe (PID: 480)
- certutil.exe (PID: 2132)
- certutil.exe (PID: 2548)
- certutil.exe (PID: 3728)
- certutil.exe (PID: 2504)
- certutil.exe (PID: 2044)
- certutil.exe (PID: 2692)
- certutil.exe (PID: 904)
- certutil.exe (PID: 4044)
- certutil.exe (PID: 1436)
- certutil.exe (PID: 3220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2021-Sep-25 21:56:47 |
| Detected languages: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 216 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 5 |
| TimeDateStamp: | 2021-Sep-25 21:56:47 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 26230 | 26624 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.41746 |
.rdata | 32768 | 5018 | 5120 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.14107 |
.data | 40960 | 131960 | 1536 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.11058 |
.ndata | 176128 | 65536 | 0 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rsrc | 241664 | 43416 | 43520 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.75354 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 7.81232 | 41501 | UNKNOWN | English - United States | RT_ICON |
103 | 1.51664 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.66174 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.88094 | 284 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.48825 | 96 | UNKNOWN | English - United States | RT_DIALOG |
1 (#2) | 5.28747 | 841 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
134
Monitored processes
80
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | certutil /encode "C:\Users\admin\Desktop\airportsince.rtf" "lock.txt" | C:\Windows\system32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
| 124 | certutil -decode "C:\Users\admin\Desktop\201863026.exe" "\Users\admin\Desktop\\201863026." | C:\Windows\system32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 2147942413 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
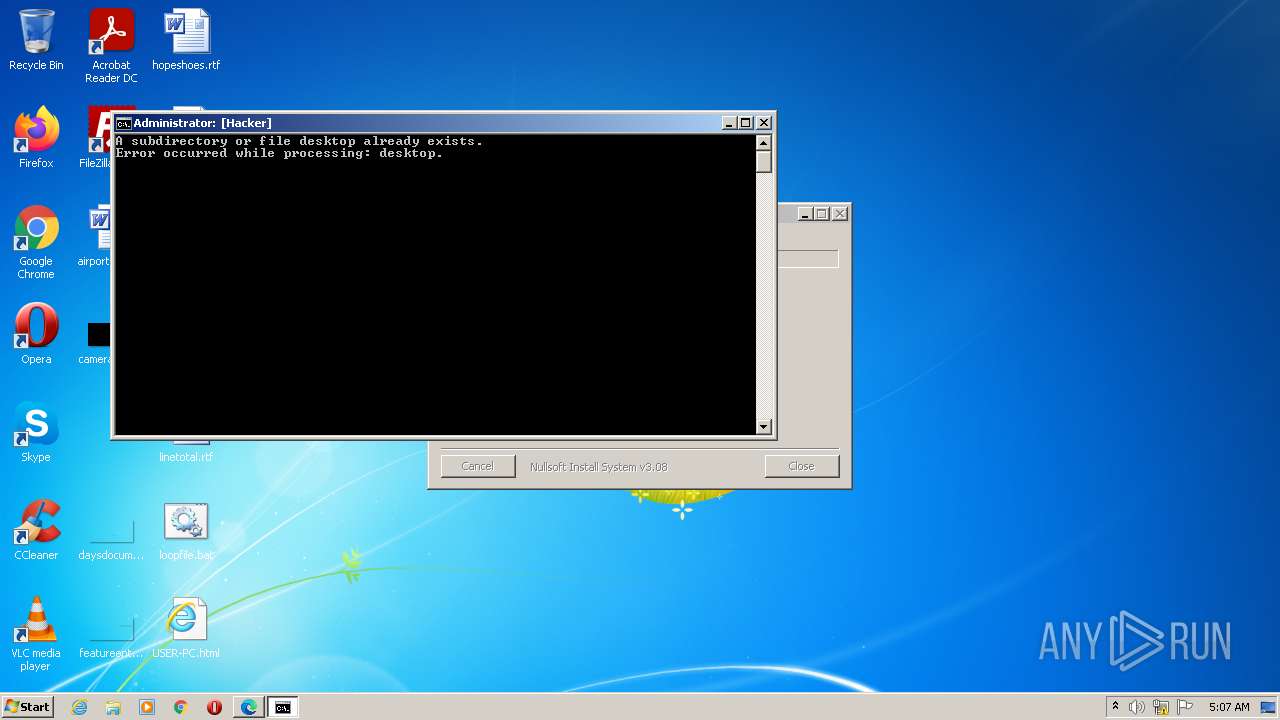
| 188 | C:\Windows\system32\cmd.exe /K b6re.bat | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 388 | C:\Windows\system32\cmd.exe /K "C:\Users\admin\AppData\b6 ransomware.bat" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 468 | findstr /v /c:- lock.txt | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | certutil -decode "C:\Users\admin\Desktop\b6 ransomware.bat" "\Users\admin\Desktop\\b6 ransomware." | C:\Windows\system32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 2147942413 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
| 660 | "C:\Windows\system32\cacls.exe" "C:\Windows\system32\config\system" | C:\Windows\system32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 688 | "C:\Windows\system32\cmd.exe" /c net user Administrator 101010 >> C:\Users\admin\AppData\Local\Temp\info.txt | C:\Windows\system32\cmd.exe | — | 201863026.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 768 | C:\Windows\system32\cmd.exe /c dir /b /s /a-h-d | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 904 | certutil -decode "C:\Users\admin\Desktop\information.bat.B6" "\Users\admin\Desktop\\information.bat." | C:\Windows\system32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
Total events
2 121
Read events
2 111
Write events
10
Delete events
0
Modification events
| (PID) Process: | (2848) 201863026.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2848) 201863026.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2848) 201863026.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2848) 201863026.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2848) 201863026.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | wallpaper |
Value: C:\Temp\rand.JPG | |||
| (PID) Process: | (2848) 201863026.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | wallpaperstyle |
Value: 6 | |||
Executable files
0
Suspicious files
0
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1936 | cmd.exe | C:\Users\admin\Desktop\USER-PC.html | html | |
MD5:— | SHA256:— | |||
| 388 | cmd.exe | C:\Users\admin\AppData\Local\Temp\b6r | text | |
MD5:— | SHA256:— | |||
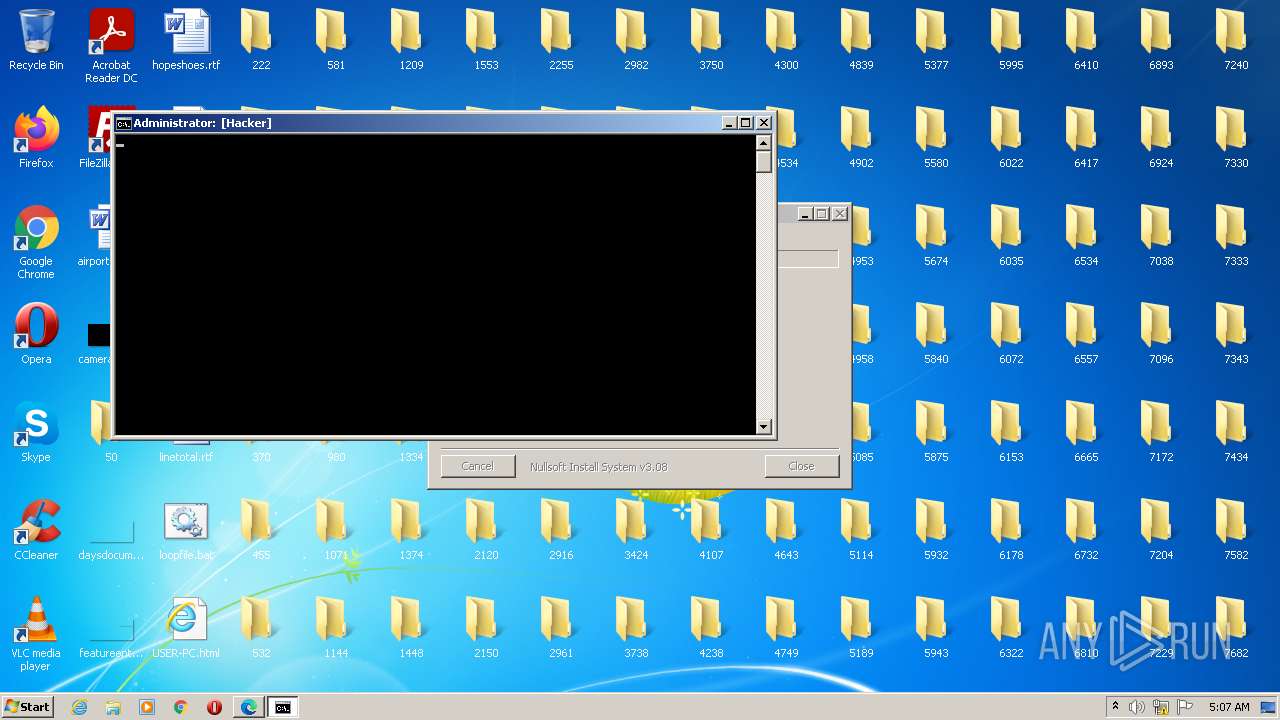
| 2848 | 201863026.exe | C:\Users\admin\Desktop\loopfile.bat | text | |
MD5:62933B06A3D49DB78F36DFFDEBFBE48C | SHA256:D2F97B09462CC4863FA9D6CB8A0B0DCE035B45B7A1E2AE0F04DB63983EA383C2 | |||
| 2848 | 201863026.exe | C:\Temp\winapply.bat | text | |
MD5:A9EDD79D0509E10A12F780A2064D7EEC | SHA256:0C9F0D0194FCDD44C9C11EC9F41F945B34D79F2BC9D605DA49493254B9829B8F | |||
| 2848 | 201863026.exe | C:\Temp\rand.JPG | image | |
MD5:41192B03351DE6DEA01FA56A4AE0D00B | SHA256:49EDD8FA85FB8A6B227B718EDF245CD8E6527457D4773206938F0C9C51562AB0 | |||
| 2628 | cmd.exe | C:\Users\admin\AppData\Local\Temp\info.txt | text | |
MD5:12B47862DDAF9E0B1751A51A63C05887 | SHA256:CD4E03ACB3F078230ADBEB8228058F8E12A3E768C0B83BEF9A6DBA00F6677DE3 | |||
| 2848 | 201863026.exe | C:\Temp\matrix.bat | text | |
MD5:0293000D86A840CCC8B3D975C5B3F1F0 | SHA256:5FE0ACE5B36EAD6C3FC76C67C4751CC8AD568B4C8C86C1E01869E51AB46001E6 | |||
| 2644 | cmd.exe | C:\Users\admin\Desktop\b6 ransomware.bat | text | |
MD5:77CBC6B6A2865CF4C477DEB058E19936 | SHA256:AB7E431B53A62CD2E01200160C37BD888AC0755FAB1DADE4ACCA72B229D1E2B7 | |||
| 2848 | 201863026.exe | C:\Users\admin\Desktop\b6 ransomware.bat | text | |
MD5:77CBC6B6A2865CF4C477DEB058E19936 | SHA256:AB7E431B53A62CD2E01200160C37BD888AC0755FAB1DADE4ACCA72B229D1E2B7 | |||
| 2848 | 201863026.exe | C:\Users\admin\Desktop\information.bat | text | |
MD5:F3C20C9F6364A4356B80552657404953 | SHA256:0BDB529F76A8E829F9080C39B4707E89F95F935C7126CB8614E3D16032B3C26F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report