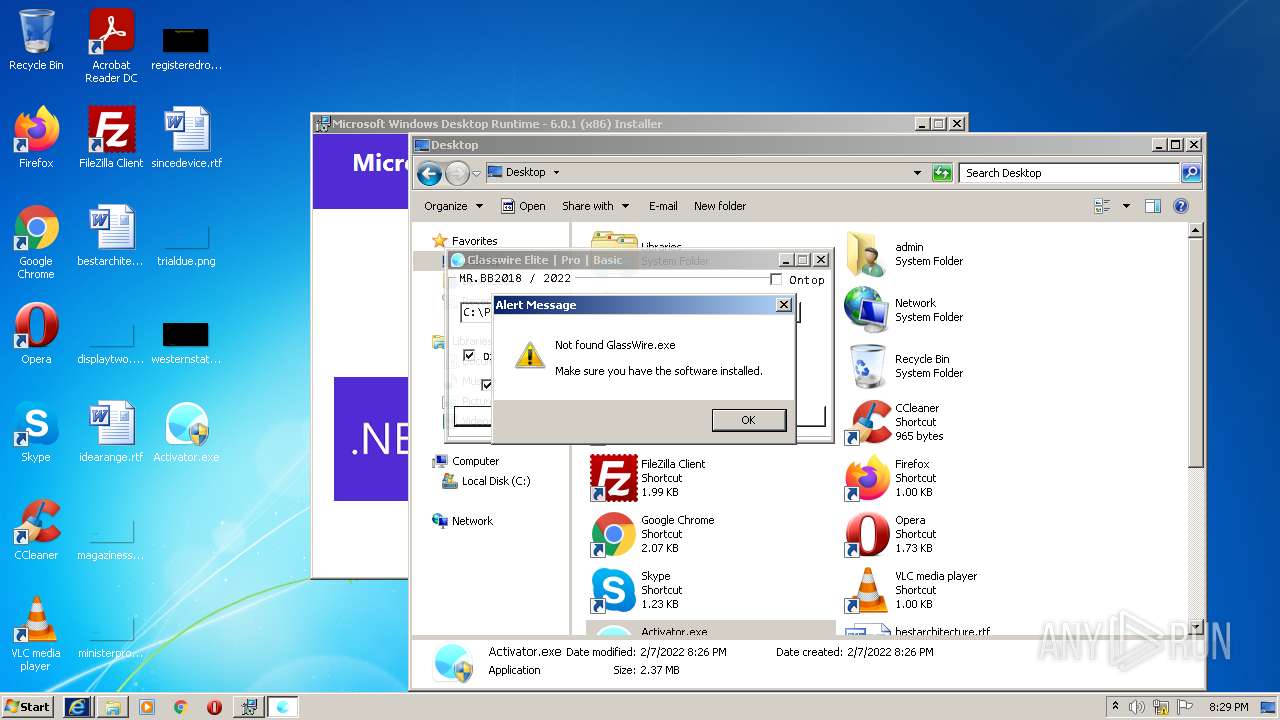
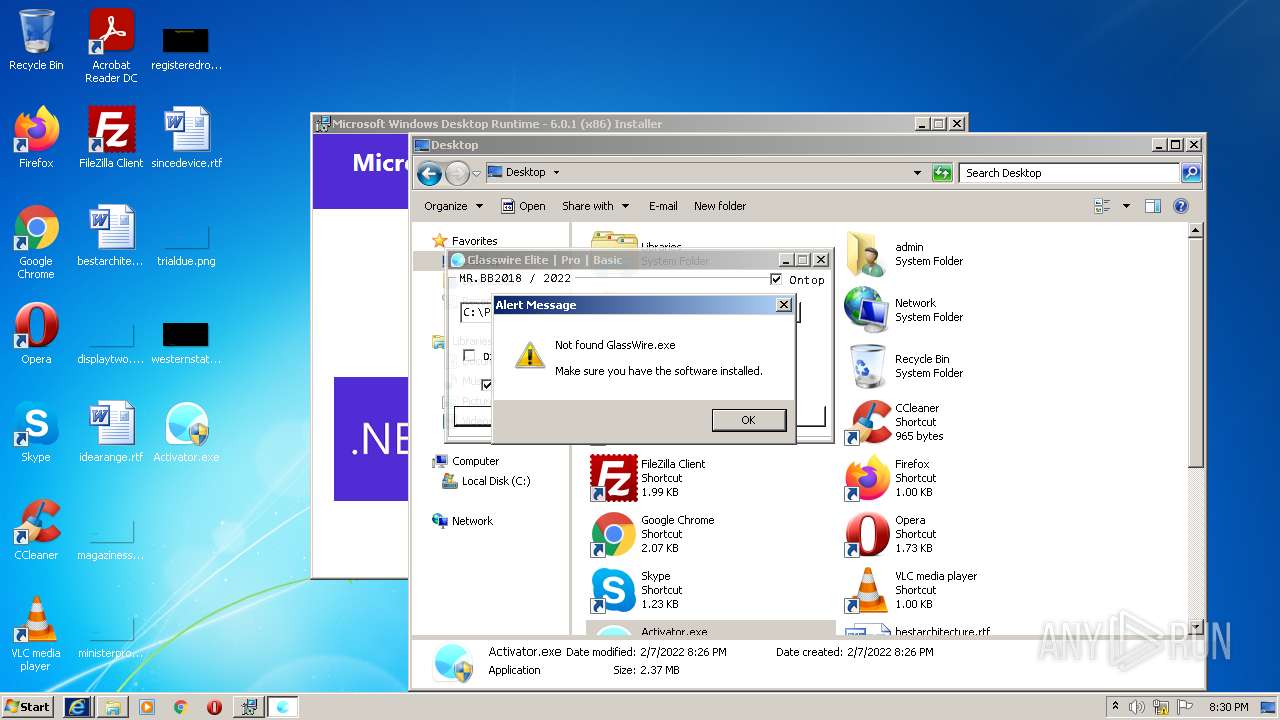
| File name: | Activator.exe |
| Full analysis: | https://app.any.run/tasks/d6965683-ee5c-48e1-9ac4-f4dfc4a3f950 |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2022, 20:26:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 47605B44FB253C18AAA0ABC7F7688AAE |
| SHA1: | EA35F8F324E52A2045AAED2F13DF82CD5DF67D1B |
| SHA256: | 44C672836786B6CEA43303683830D14106EDA34FDD6B6EA880F7BACF774EA261 |
| SSDEEP: | 24576:mhoeNJhvzMP85eMP8scMP8QwtOdtONtOI97B:aJVIUVUaUTO/OvOIFB |
MALICIOUS
Application was dropped or rewritten from another process
- dotnet-runtime-6.0.1-win-x86.exe (PID: 4052)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2068)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
Drops executable file immediately after starts
- dotnet-runtime-6.0.1-win-x86.exe (PID: 4052)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2068)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
Changes the autorun value in the registry
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3632)
- MsiExec.exe (PID: 1084)
- Activator.exe (PID: 1484)
Starts NET.EXE for service management
- Activator.exe (PID: 3024)
SUSPICIOUS
Checks supported languages
- Activator.exe (PID: 3184)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 4052)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- Activator.exe (PID: 1484)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2068)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
- Activator.exe (PID: 3024)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2680)
- iexplore.exe (PID: 3324)
Reads the computer name
- Activator.exe (PID: 3184)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- Activator.exe (PID: 1484)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
- Activator.exe (PID: 3024)
Starts Internet Explorer
- Activator.exe (PID: 3184)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2680)
- iexplore.exe (PID: 3928)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 4052)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- msiexec.exe (PID: 2376)
- iexplore.exe (PID: 3324)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2068)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
Drops a file that was compiled in debug mode
- iexplore.exe (PID: 2680)
- iexplore.exe (PID: 3928)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 4052)
- msiexec.exe (PID: 2376)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2068)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
Creates files in the Windows directory
- dotnet-runtime-6.0.1-win-x86.exe (PID: 4052)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2068)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
Starts itself from another location
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
Creates a directory in Program Files
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- msiexec.exe (PID: 2376)
Searches for installed software
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 2580)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
Creates files in the program directory
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- msiexec.exe (PID: 2376)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
- Activator.exe (PID: 3024)
Creates a software uninstall entry
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- msiexec.exe (PID: 2376)
- windowsdesktop-runtime-6.0.1-win-x86.exe (PID: 1484)
Reads Windows owner or organization settings
- msiexec.exe (PID: 2376)
Reads the Windows organization settings
- msiexec.exe (PID: 2376)
Application launched itself
- msiexec.exe (PID: 2376)
Drops a file with too old compile date
- msiexec.exe (PID: 2376)
Executed as Windows Service
- msiexec.exe (PID: 2376)
Removes files from Windows directory
- dotnet-runtime-6.0.1-win-x86.exe (PID: 2320)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 4052)
Drops a file with a compile date too recent
- msiexec.exe (PID: 2376)
INFO
Checks supported languages
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 2680)
- msiexec.exe (PID: 2376)
- MsiExec.exe (PID: 3632)
- MsiExec.exe (PID: 3388)
- explorer.exe (PID: 2456)
- MsiExec.exe (PID: 1084)
- iexplore.exe (PID: 3324)
- MsiExec.exe (PID: 1852)
- net1.exe (PID: 2540)
- net.exe (PID: 3704)
- net1.exe (PID: 2464)
- net.exe (PID: 3660)
Application launched itself
- iexplore.exe (PID: 3928)
Reads the computer name
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 2680)
- msiexec.exe (PID: 2376)
- MsiExec.exe (PID: 1084)
- explorer.exe (PID: 2456)
- MsiExec.exe (PID: 3632)
- MsiExec.exe (PID: 3388)
- iexplore.exe (PID: 3324)
- MsiExec.exe (PID: 1852)
- net1.exe (PID: 2464)
- net1.exe (PID: 2540)
Checks Windows Trust Settings
- iexplore.exe (PID: 2680)
- iexplore.exe (PID: 3928)
- msiexec.exe (PID: 2376)
- iexplore.exe (PID: 3324)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2680)
Reads settings of System Certificates
- iexplore.exe (PID: 2680)
- iexplore.exe (PID: 3928)
- msiexec.exe (PID: 2376)
- iexplore.exe (PID: 3324)
- Activator.exe (PID: 3024)
Changes internet zones settings
- iexplore.exe (PID: 3928)
Reads internet explorer settings
- iexplore.exe (PID: 2680)
- iexplore.exe (PID: 3324)
Changes settings of System certificates
- iexplore.exe (PID: 2680)
Creates files in the user directory
- iexplore.exe (PID: 2680)
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 3324)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2680)
- dotnet-runtime-6.0.1-win-x86.exe (PID: 568)
- msiexec.exe (PID: 2376)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3928)
Manual execution by user
- Activator.exe (PID: 3460)
- explorer.exe (PID: 2456)
- Activator.exe (PID: 1484)
- Activator.exe (PID: 3732)
- Activator.exe (PID: 3024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| AssemblyVersion: | 4.3.0.0 |
|---|---|
| ProductVersion: | 1.0.0 |
| ProductName: | GW_2022 |
| OriginalFileName: | GW_2022.dll |
| LegalCopyright: | 2022 |
| InternalName: | GW_2022.dll |
| FileVersion: | 4.3.0.0 |
| FileDescription: | GW_2022 |
| CompanyName: | GW_2022 |
| Comments: | MR.BB2018 |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 4.3.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x10380 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 156672 |
| CodeSize: | 78848 |
| LinkerVersion: | 14.29 |
| PEType: | PE32 |
| TimeStamp: | 2021:10:23 01:52:21+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 22-Oct-2021 23:52:21 |
| Debug artifacts: |
|
| Comments: | MR.BB2018 |
| CompanyName: | GW_2022 |
| FileDescription: | GW_2022 |
| FileVersion: | 4.3.0.0 |
| InternalName: | GW_2022.dll |
| LegalCopyright: | 2022 |
| OriginalFilename: | GW_2022.dll |
| ProductName: | GW_2022 |
| ProductVersion: | 1.0.0 |
| Assembly Version: | 4.3.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 22-Oct-2021 23:52:21 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001337A | 0x00013400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.43973 |
.rdata | 0x00015000 | 0x00006936 | 0x00006A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.46565 |
.data | 0x0001C000 | 0x00000E78 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.29447 |
.rsrc | 0x0001D000 | 0x0001DDA4 | 0x0001DE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.34693 |
.reloc | 0x0003B000 | 0x00001170 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.54037 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.01752 | 3411 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 3.01971 | 67624 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 3.24389 | 16936 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 3.37618 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 3.62902 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 3.8746 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
32512 | 2.79908 | 90 | Latin 1 / Western European | UNKNOWN | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
api-ms-win-crt-convert-l1-1-0.dll |
api-ms-win-crt-heap-l1-1-0.dll |
api-ms-win-crt-locale-l1-1-0.dll |
api-ms-win-crt-math-l1-1-0.dll |
api-ms-win-crt-runtime-l1-1-0.dll |
api-ms-win-crt-stdio-l1-1-0.dll |
Total processes
75
Monitored processes
25
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 568 | "C:\Windows\Temp\{C3EB830D-8ED4-4282-9FB4-A2913478DD7D}\.be\dotnet-runtime-6.0.1-win-x86.exe" -q -burn.elevated BurnPipe.{D456F394-9CFF-4FFF-AFE5-8ADE887E663E} {7FD0D8D8-C660-42AA-B990-6C8954BC748A} 2320 | C:\Windows\Temp\{C3EB830D-8ED4-4282-9FB4-A2913478DD7D}\.be\dotnet-runtime-6.0.1-win-x86.exe | dotnet-runtime-6.0.1-win-x86.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Runtime - 6.0.1 (x86) Exit code: 0 Version: 6.0.1.30717 | ||||
| 1084 | C:\Windows\system32\MsiExec.exe -Embedding 6771D4A78E27F329121BBB03D796C7FC | C:\Windows\system32\MsiExec.exe | — | msiexec.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 1484 | "C:\Users\admin\Desktop\Activator.exe" | C:\Users\admin\Desktop\Activator.exe | Explorer.EXE | |
User: admin Company: GW_2022 Integrity Level: HIGH Description: GW_2022 Exit code: 2147516566 Version: 4.3.0.0 | ||||
| 1484 | "C:\Windows\Temp\{AAE239D0-2909-4CD5-9953-55EE22DF301A}\.be\windowsdesktop-runtime-6.0.1-win-x86.exe" -q -burn.elevated BurnPipe.{EF96FB0E-F36C-48D0-A207-B9516EAD28AA} {875FF625-96BD-4E03-BD56-BFFA030D0541} 2580 | C:\Windows\Temp\{AAE239D0-2909-4CD5-9953-55EE22DF301A}\.be\windowsdesktop-runtime-6.0.1-win-x86.exe | windowsdesktop-runtime-6.0.1-win-x86.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Desktop Runtime - 6.0.1 (x86) Exit code: 0 Version: 6.0.1.30718 | ||||
| 1852 | C:\Windows\system32\MsiExec.exe -Embedding A0F5C0C9B7DFAD63B281ADA543276E86 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 2068 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\windowsdesktop-runtime-6.0.1-win-x86.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\windowsdesktop-runtime-6.0.1-win-x86.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Desktop Runtime - 6.0.1 (x86) Exit code: 0 Version: 6.0.1.30718 | ||||
| 2320 | "C:\Windows\Temp\{0DA5393F-2FCE-49C9-B1A6-D8CFF49AFD90}\.cr\dotnet-runtime-6.0.1-win-x86.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\dotnet-runtime-6.0.1-win-x86.exe" -burn.filehandle.attached=152 -burn.filehandle.self=160 | C:\Windows\Temp\{0DA5393F-2FCE-49C9-B1A6-D8CFF49AFD90}\.cr\dotnet-runtime-6.0.1-win-x86.exe | dotnet-runtime-6.0.1-win-x86.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Runtime - 6.0.1 (x86) Exit code: 0 Version: 6.0.1.30717 | ||||
| 2376 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) | ||||
| 2456 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2464 | C:\Windows\system32\net1 stop GlassWire | C:\Windows\system32\net1.exe | — | net.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
528
Suspicious files
33
Text files
114
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2680 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_E503B048B745DFA14B81FCFC68D6DECE | der | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\bootstrap-custom.min[1].css | text | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\analytics.min[1].js | text | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\ZUFJ16FX.txt | text | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\culture-selector.min[1].js | text | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\youtube-brand-logo[1].svg | image | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\cookie-consent.min[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
59
DNS requests
26
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2680 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
2680 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2680 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2680 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
2680 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
3928 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
2680 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9d1d0134ec2bed86 | US | compressed | 4.70 Kb | whitelisted |
2680 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
2680 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2680 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?25c94600568d0463 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2680 | iexplore.exe | 13.107.246.44:443 | dotnet.microsoft.com | Microsoft Corporation | US | suspicious |
2680 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2680 | iexplore.exe | 23.59.69.7:443 | www.microsoft.com | Akamai Technologies, Inc. | US | suspicious |
2680 | iexplore.exe | 2.16.186.32:443 | statics-marketingsites-wcus-ms-com.akamaized.net | Akamai International B.V. | — | whitelisted |
2680 | iexplore.exe | 2.16.186.40:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | — | whitelisted |
2680 | iexplore.exe | 152.199.21.175:443 | az416426.vo.msecnd.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3928 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2680 | iexplore.exe | 40.78.253.203:443 | dc.services.visualstudio.com | Microsoft Corporation | US | unknown |
2680 | iexplore.exe | 96.16.143.41:443 | aka.ms | Akamai International B.V. | US | whitelisted |
2680 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
aka.ms |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
statics-marketingsites-wcus-ms-com.akamaized.net |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |
wcpstatic.microsoft.com |
| whitelisted |
api.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
3024 | Activator.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
3024 | Activator.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
3024 | Activator.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
Process | Message |
|---|---|
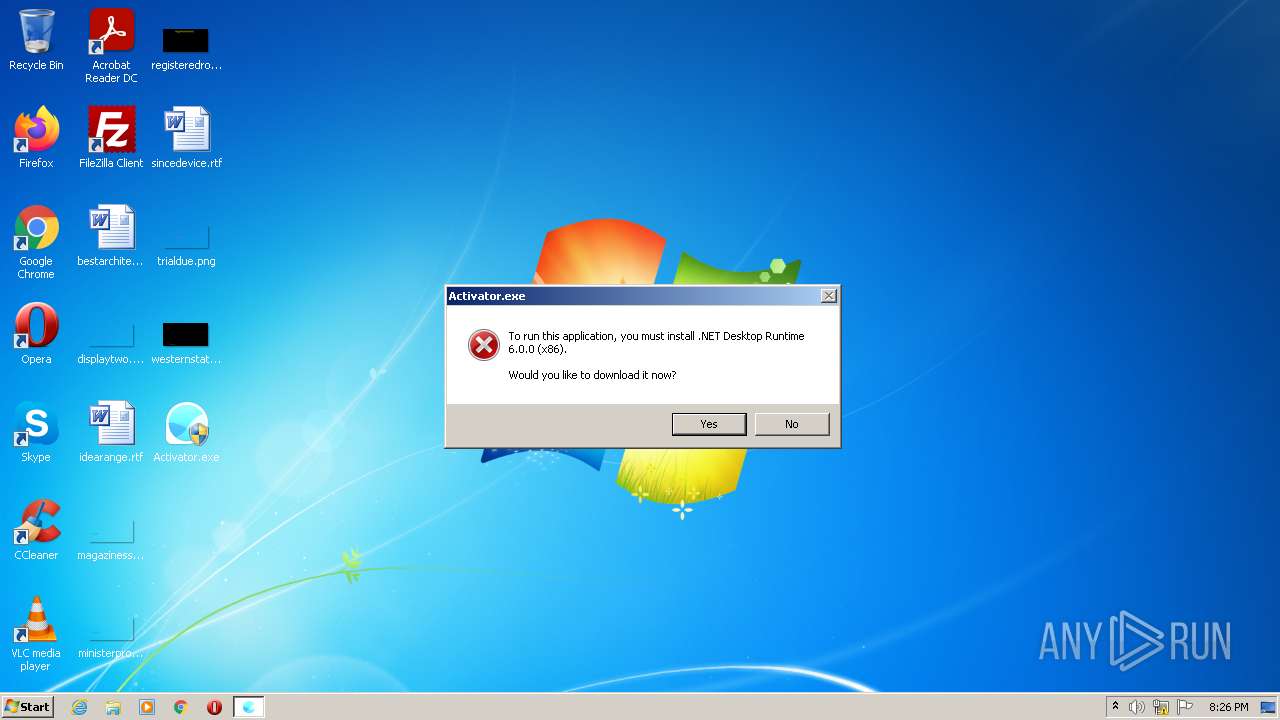
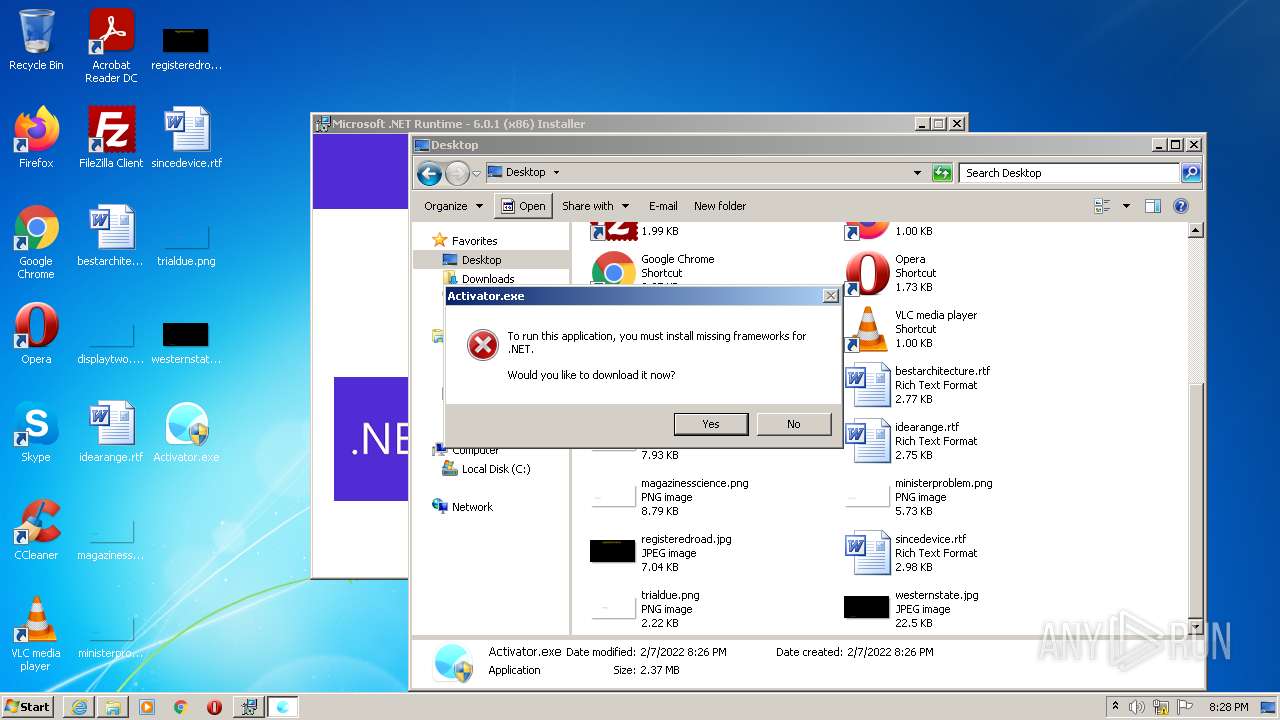
Activator.exe | A fatal error occurred. The required library hostfxr.dll could not be found.
If this is a self-contained application, that library should exist in [C:\Users\admin\Desktop\].
If this is a framework-dependent application, install the runtime in the global location [C:\Program Files\dotnet] or use the DOTNET_ROOT environment variable to specify the runtime location or register the runtime location in [HKLM\SOFTWARE\dotnet\Setup\InstalledVersions\x86\InstallLocation]. |
Activator.exe | The .NET runtime can be found at: |
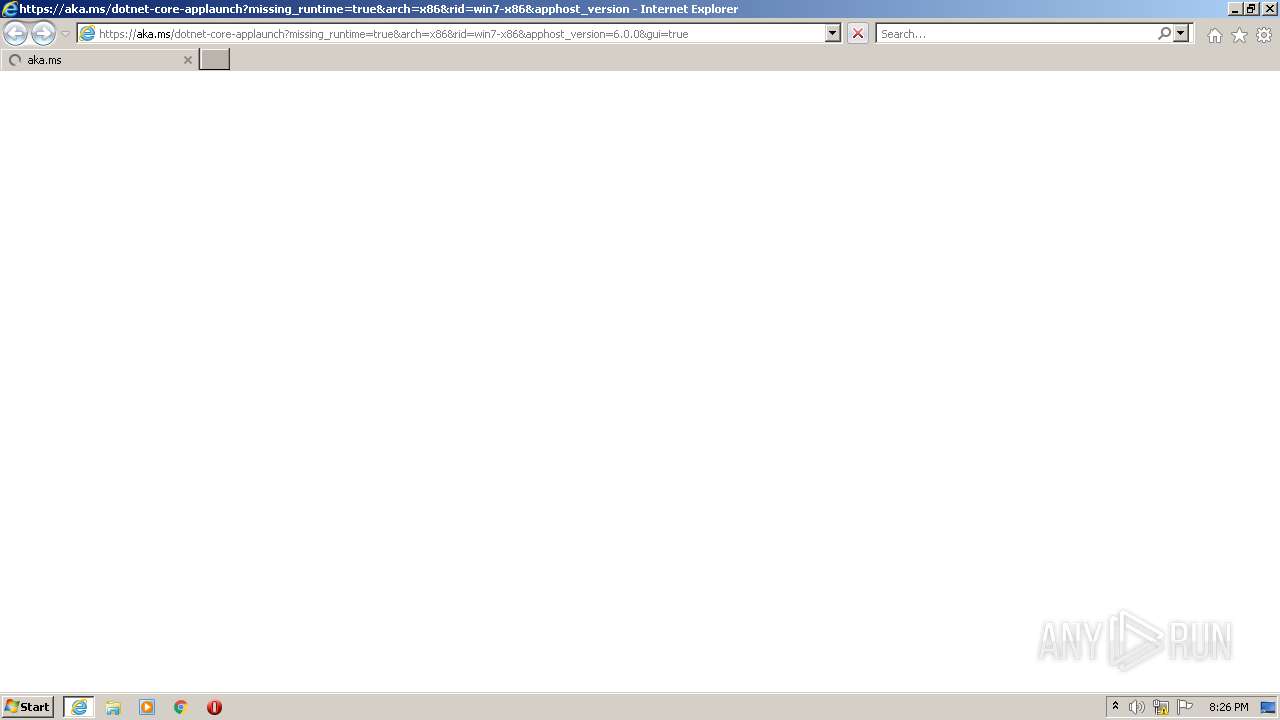
Activator.exe | - https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x86&rid=win7-x86&apphost_version=6.0.0 |
Activator.exe | It was not possible to find any compatible framework version |
Activator.exe | The framework 'Microsoft.WindowsDesktop.App', version '6.0.0' (x86) was not found. |
Activator.exe | - No frameworks were found. |
Activator.exe | You can resolve the problem by installing the specified framework and/or SDK. |
Activator.exe | The specified framework can be found at: |
Activator.exe | - https://aka.ms/dotnet-core-applaunch?framework=Microsoft.WindowsDesktop.App&framework_version=6.0.0&arch=x86&rid=win7-x86 |
Activator.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 3024. Message ID: [0x2509].
|