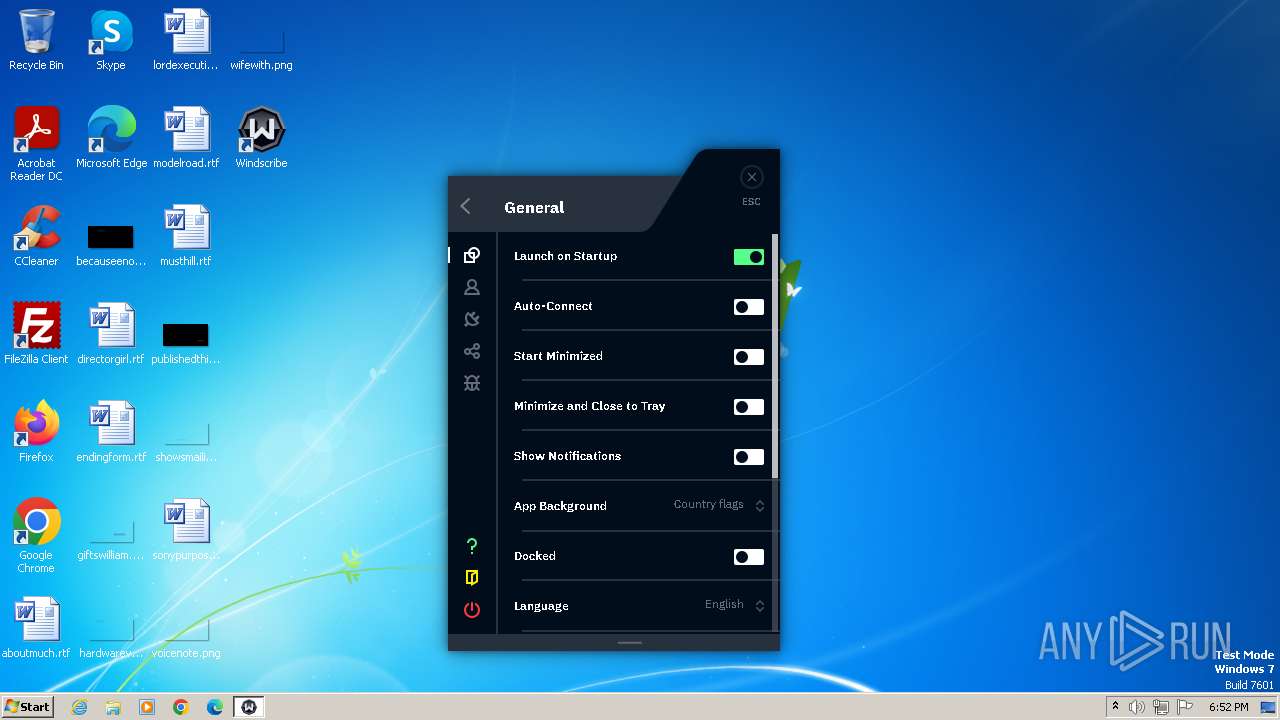
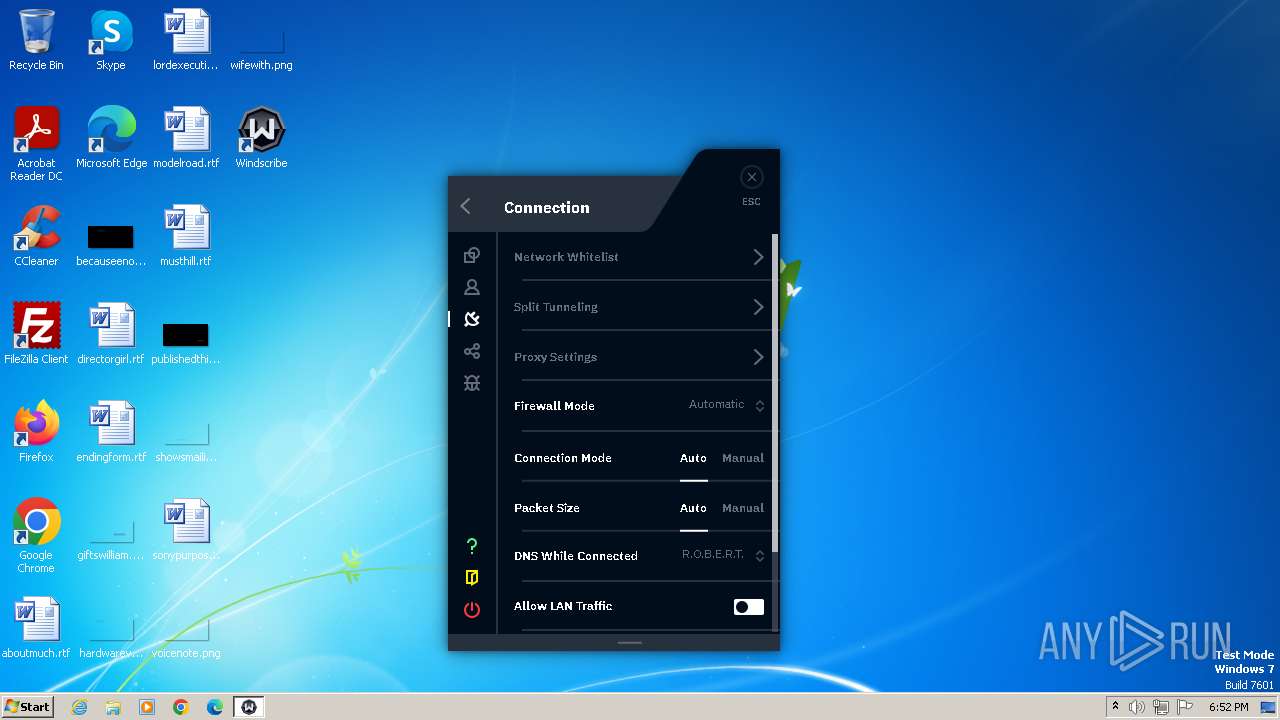
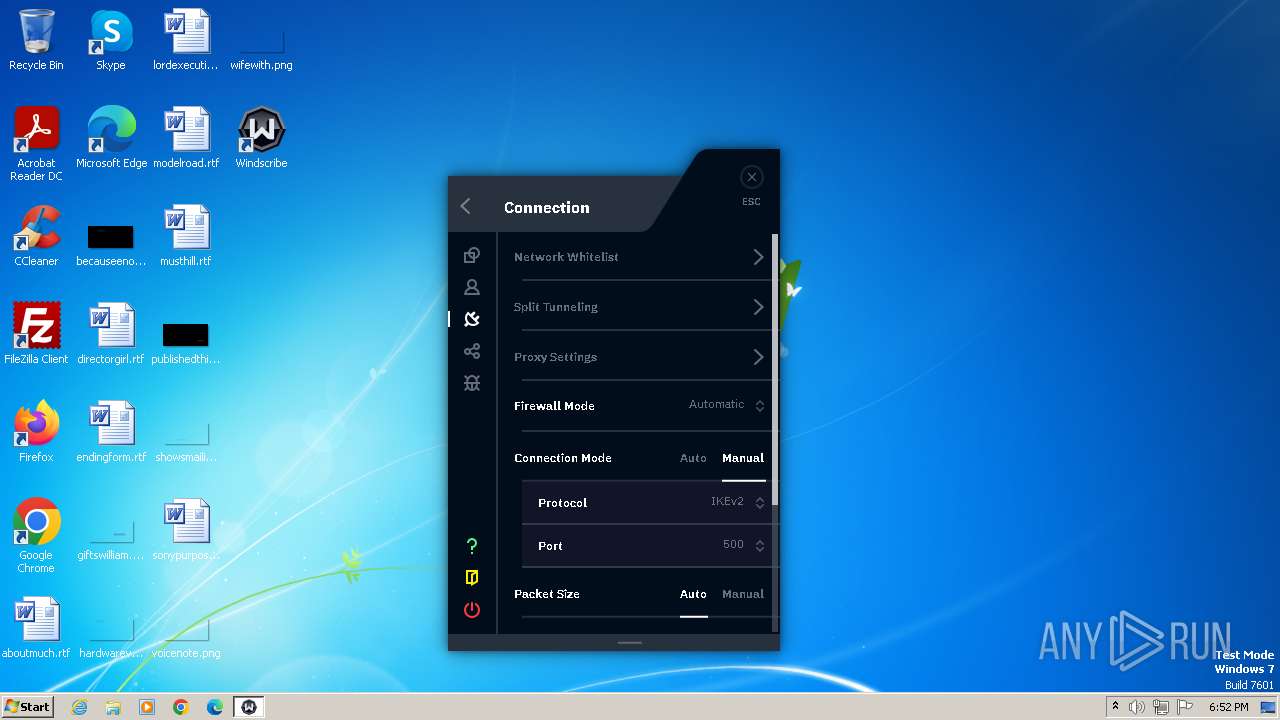
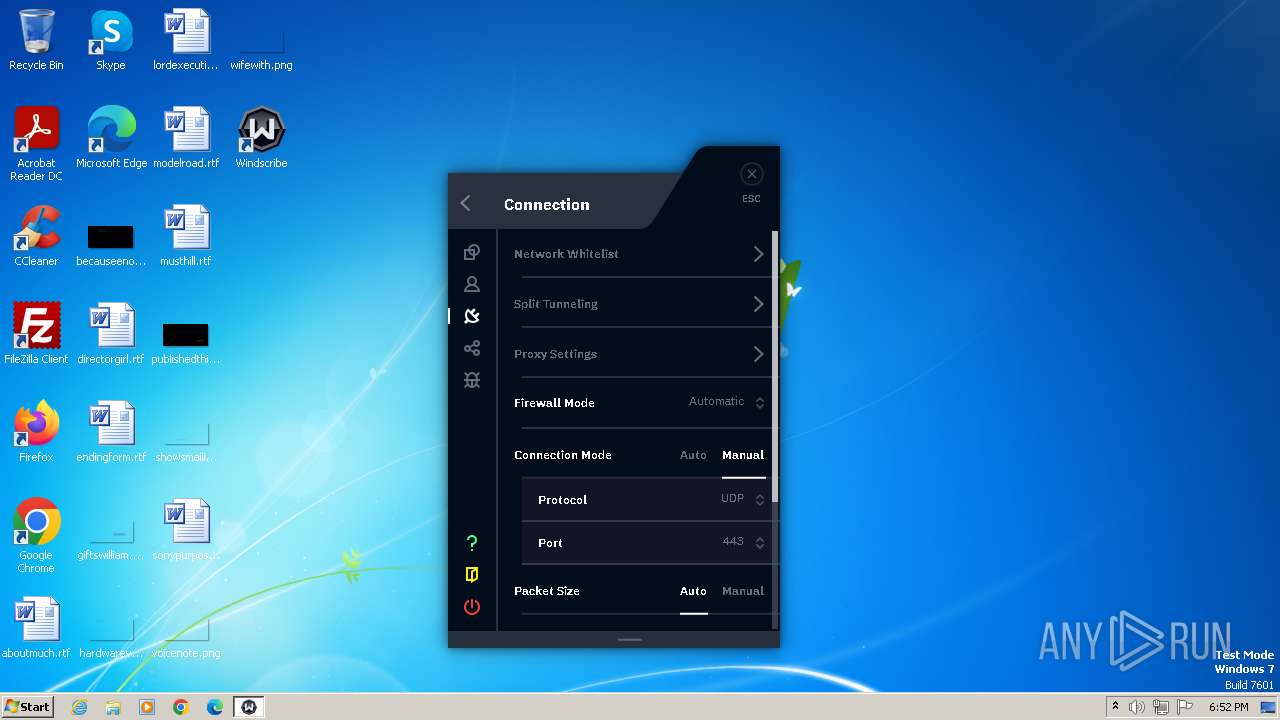
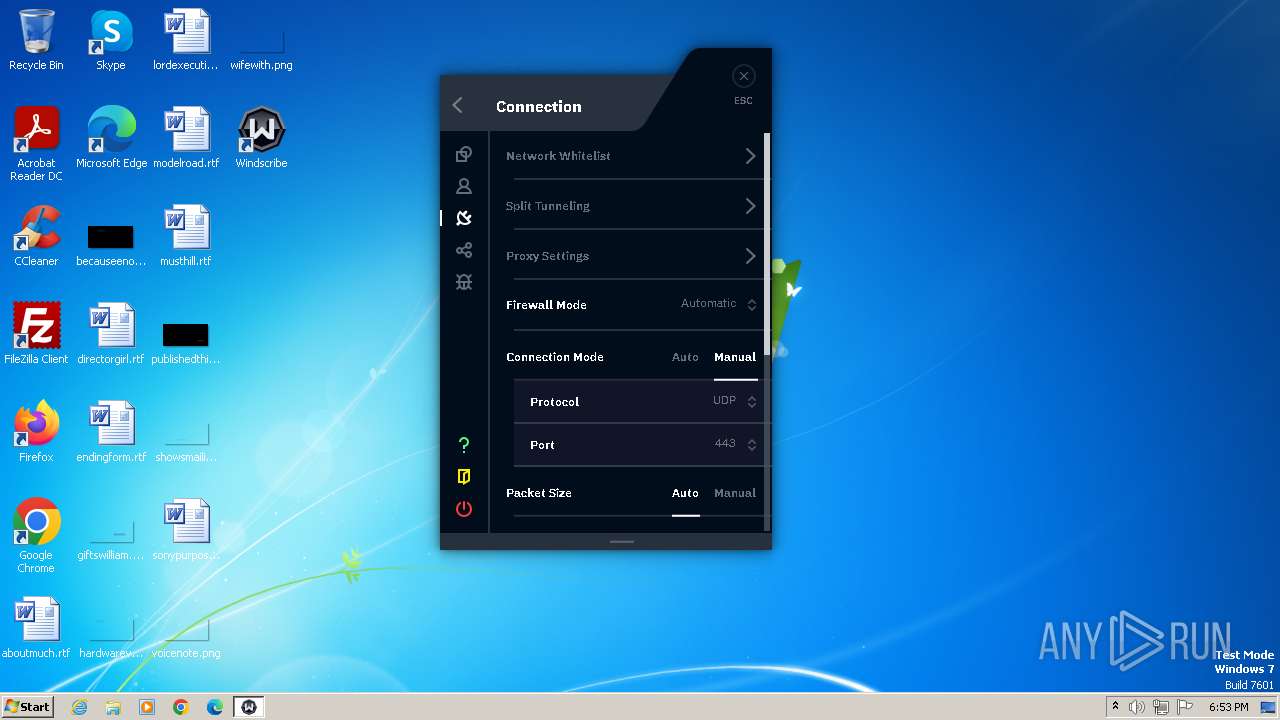
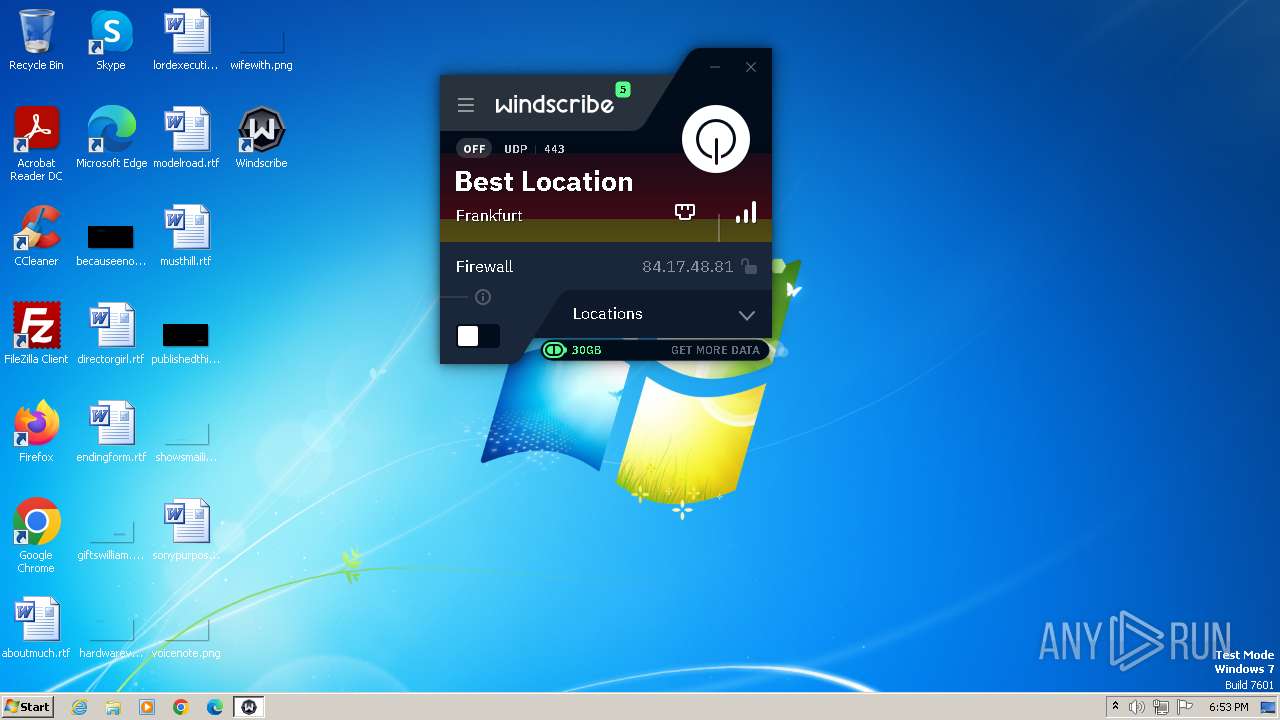
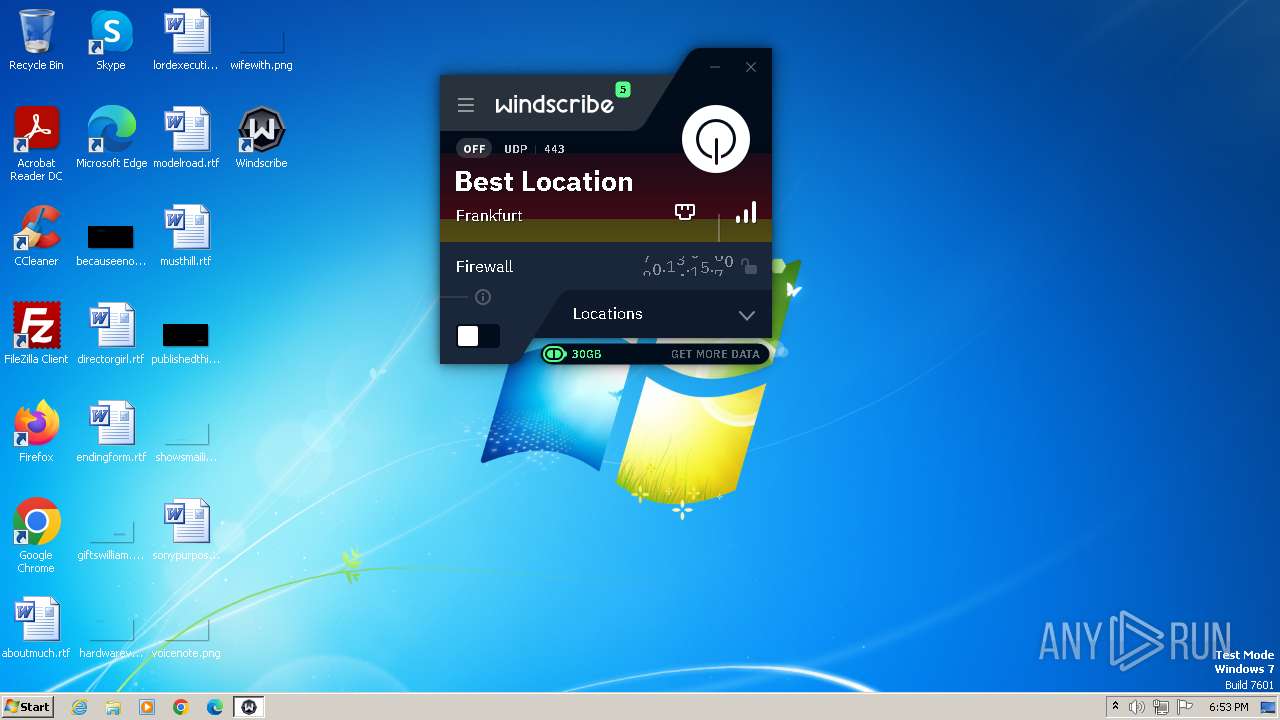
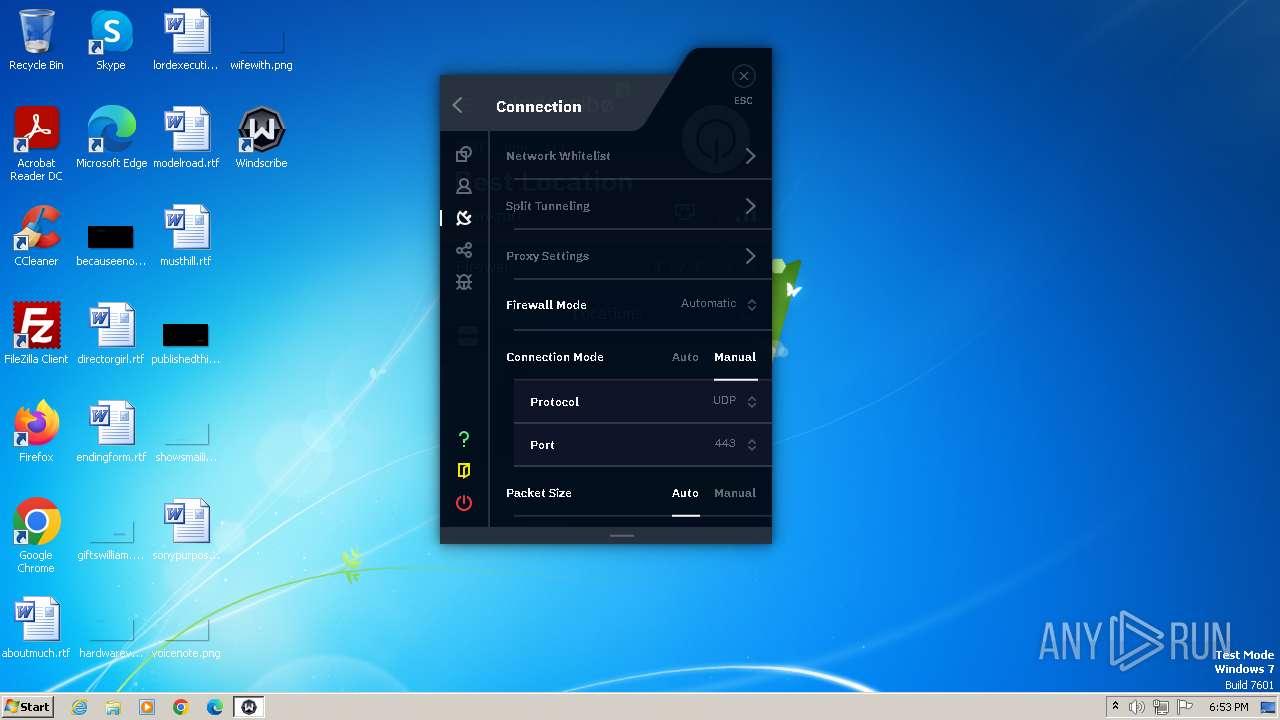
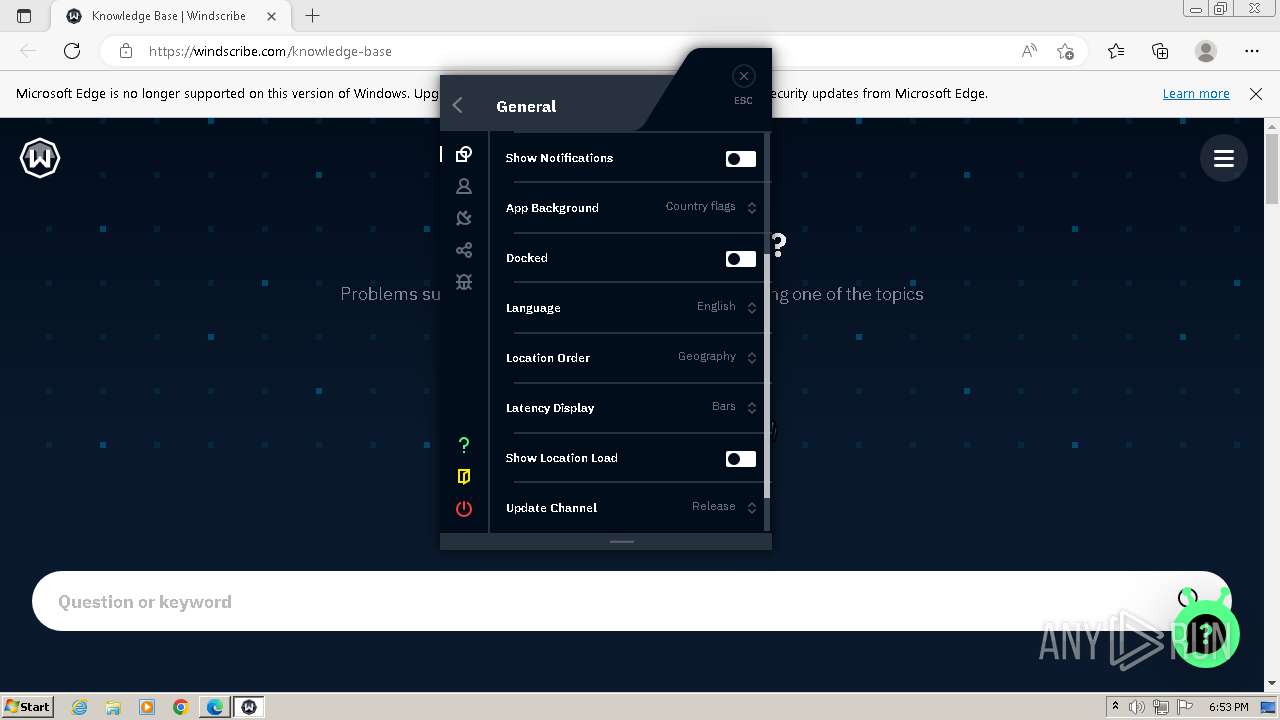
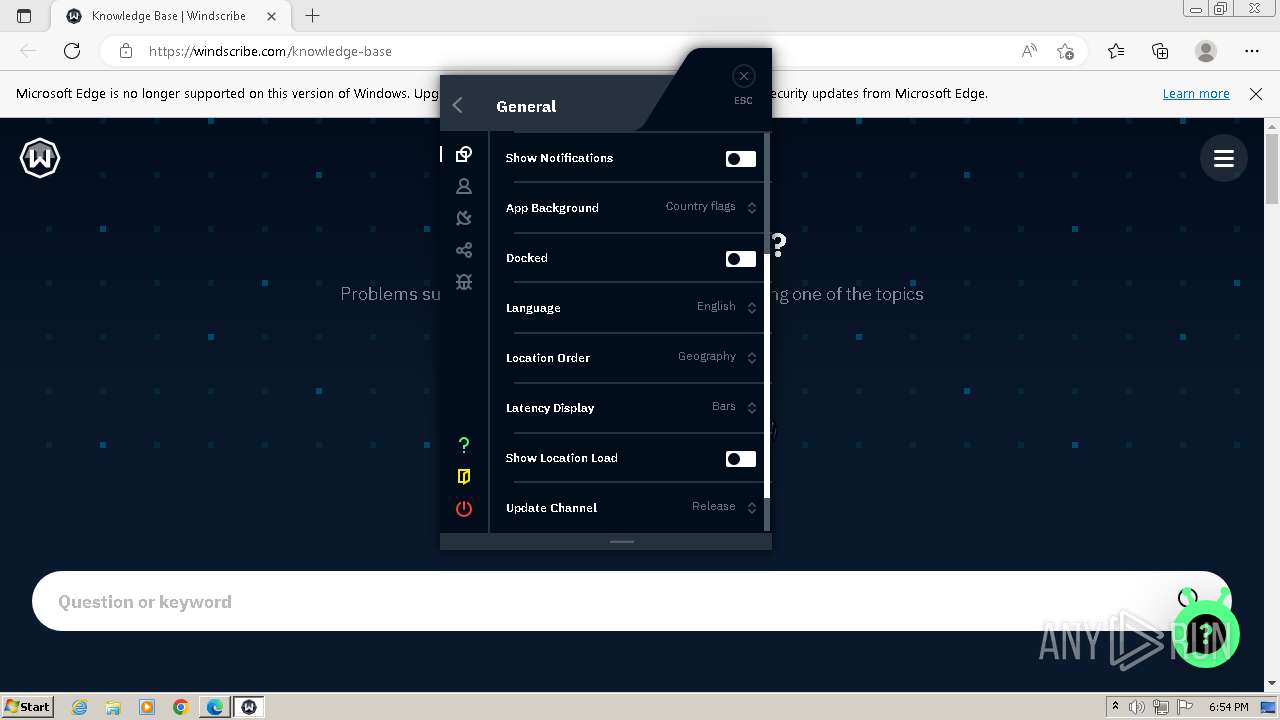
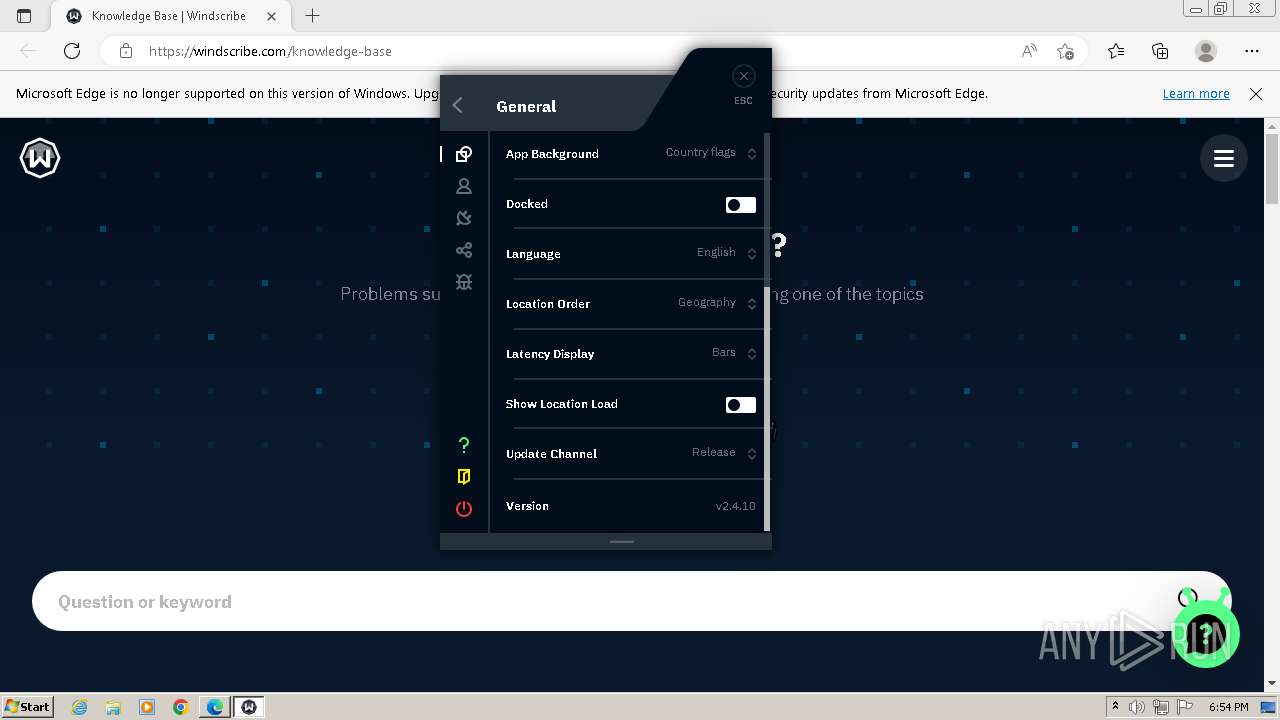
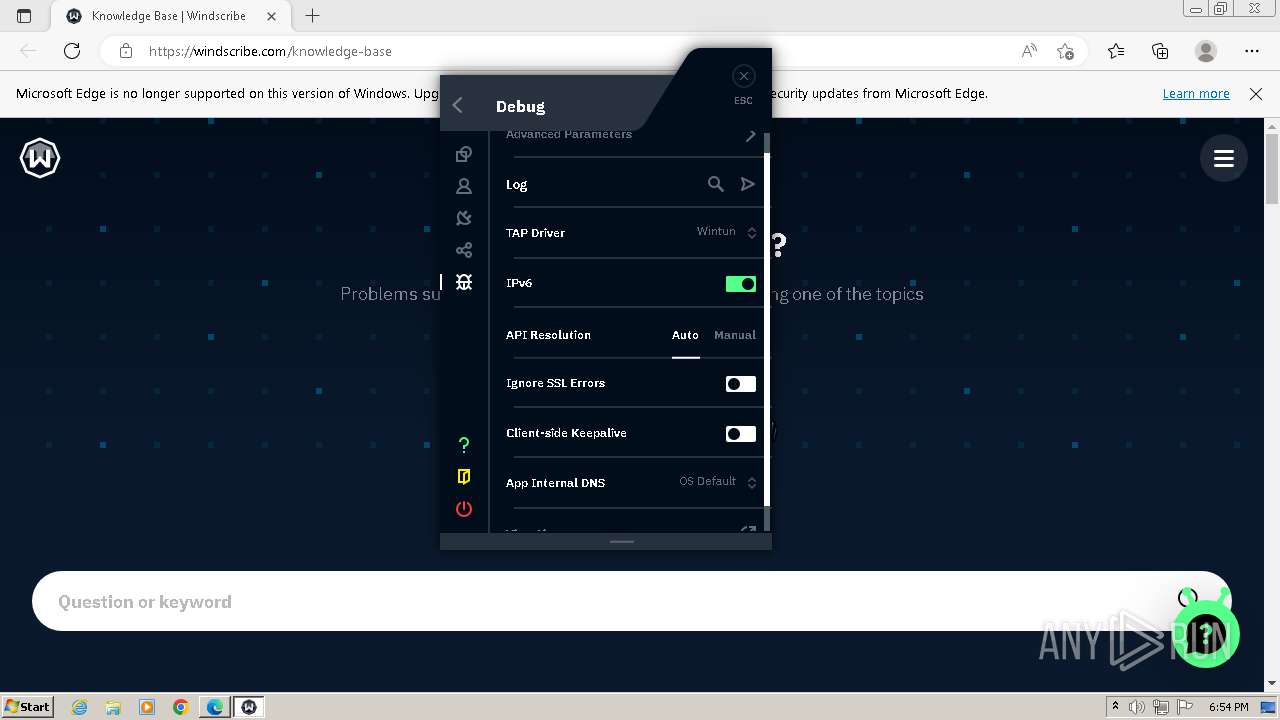
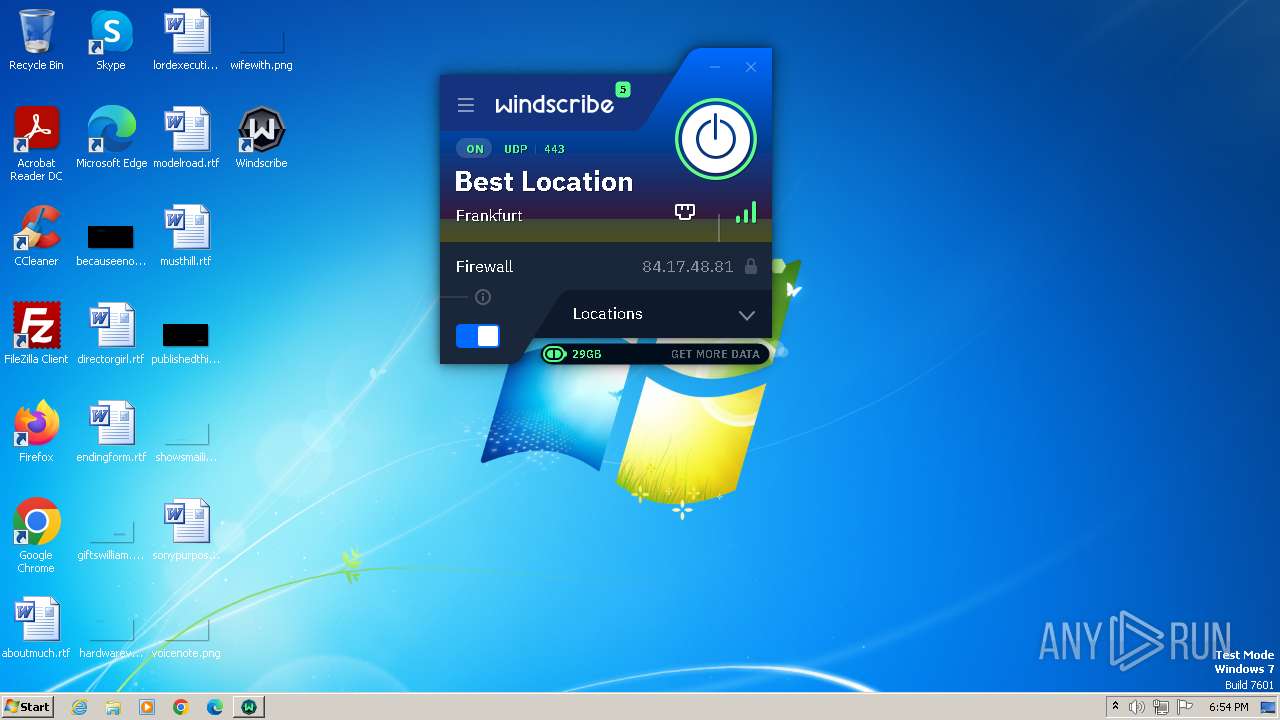
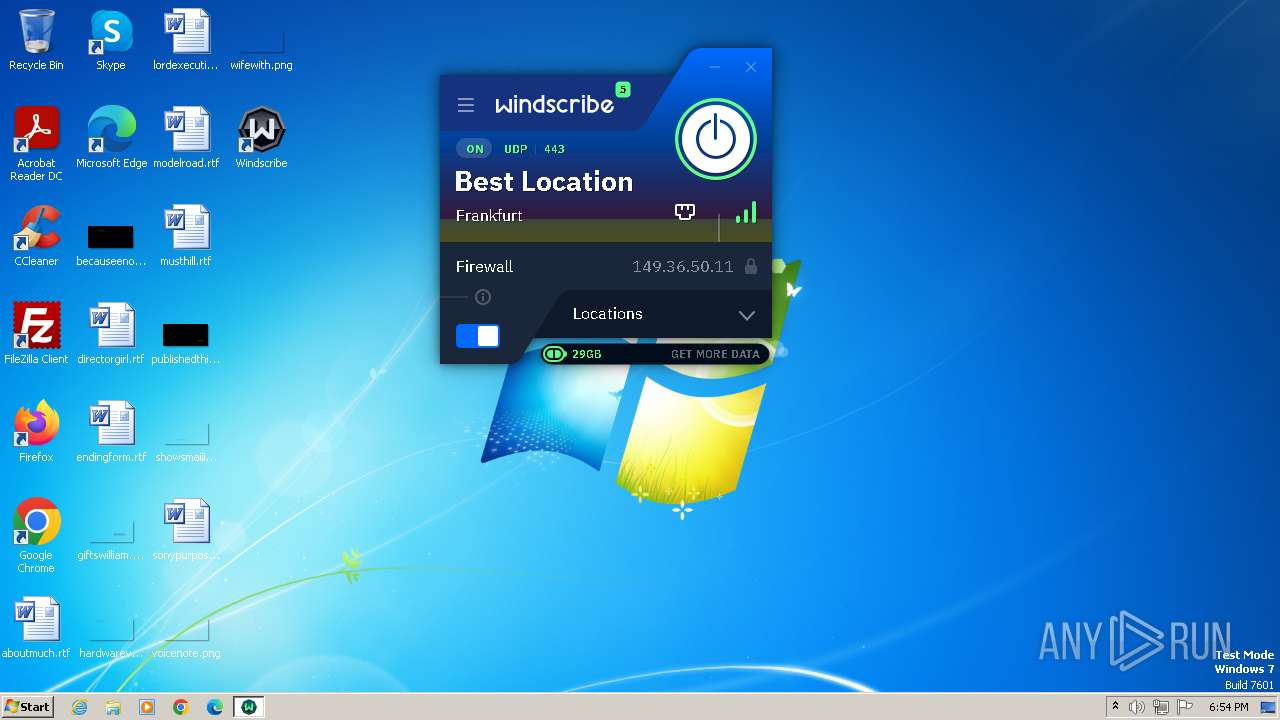
| URL: | https://assets.totallyacdn.com/desktop/win/Windscribe_2.4.exe |
| Full analysis: | https://app.any.run/tasks/d9e1b0c1-6b80-48cc-8b33-8e78e277943e |
| Verdict: | Malicious activity |
| Analysis date: | December 29, 2023, 18:50:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 89AE2EBCB79C9E8B1F9AA0C9D9D190AE |
| SHA1: | AEBF70649456DC31FB9C759A16DCCB3A2A135543 |
| SHA256: | 44B0C161B8434E6D2E83BE1D3FD765C935D4AC6BB8F82A1B07238E6AC24335EF |
| SSDEEP: | 3:N8kvlKEJJcBdIaAW1VKSMYWGcjRL4A:2kvlKd/G2tWGaL4A |
MALICIOUS
Creates a writable file in the system directory
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 2916)
- drvinst.exe (PID: 3072)
- drvinst.exe (PID: 2936)
- Windscribe_2.4.exe (PID: 1732)
- WindscribeService.exe (PID: 3660)
SUSPICIOUS
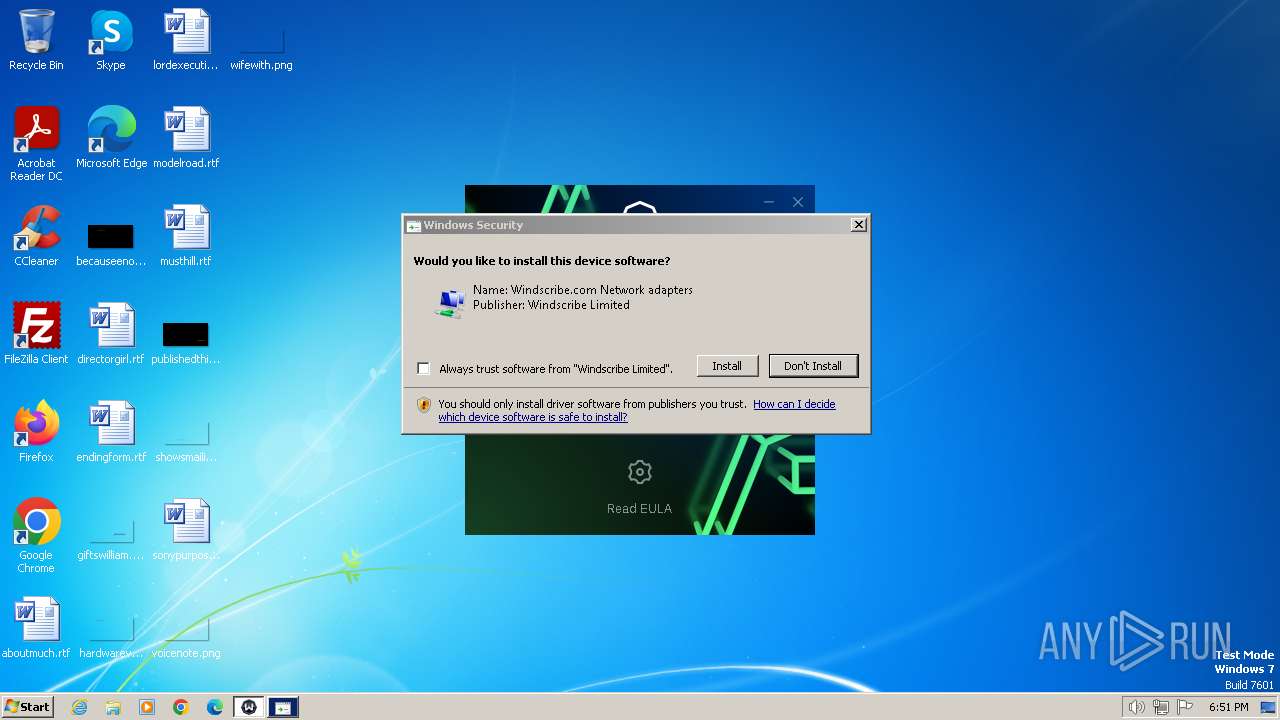
Drops a system driver (possible attempt to evade defenses)
- Windscribe_2.4.exe (PID: 1732)
- tapinstall.exe (PID: 2328)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 2916)
- tapinstall.exe (PID: 2360)
- drvinst.exe (PID: 3072)
- drvinst.exe (PID: 2936)
Starts SC.EXE for service management
- Windscribe_2.4.exe (PID: 1732)
Reads security settings of Internet Explorer
- tapinstall.exe (PID: 2328)
- tapinstall.exe (PID: 2360)
- Windscribe.exe (PID: 3504)
Checks Windows Trust Settings
- tapinstall.exe (PID: 2328)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 2916)
- tapinstall.exe (PID: 2360)
- drvinst.exe (PID: 3072)
- drvinst.exe (PID: 2936)
- Windscribe.exe (PID: 3504)
- WindscribeService.exe (PID: 3660)
Reads settings of System Certificates
- tapinstall.exe (PID: 2328)
- rundll32.exe (PID: 996)
- tapinstall.exe (PID: 2360)
- rundll32.exe (PID: 952)
- Windscribe.exe (PID: 3504)
Creates files in the driver directory
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 2916)
- drvinst.exe (PID: 3072)
- drvinst.exe (PID: 2936)
- Windscribe_2.4.exe (PID: 1732)
Creates or modifies Windows services
- Windscribe_2.4.exe (PID: 1732)
Reads the Internet Settings
- runonce.exe (PID: 2984)
- Windscribe.exe (PID: 3504)
Uses TASKKILL.EXE to kill process
- WindscribeService.exe (PID: 3660)
Uses WMIC.EXE
- WindscribeService.exe (PID: 3660)
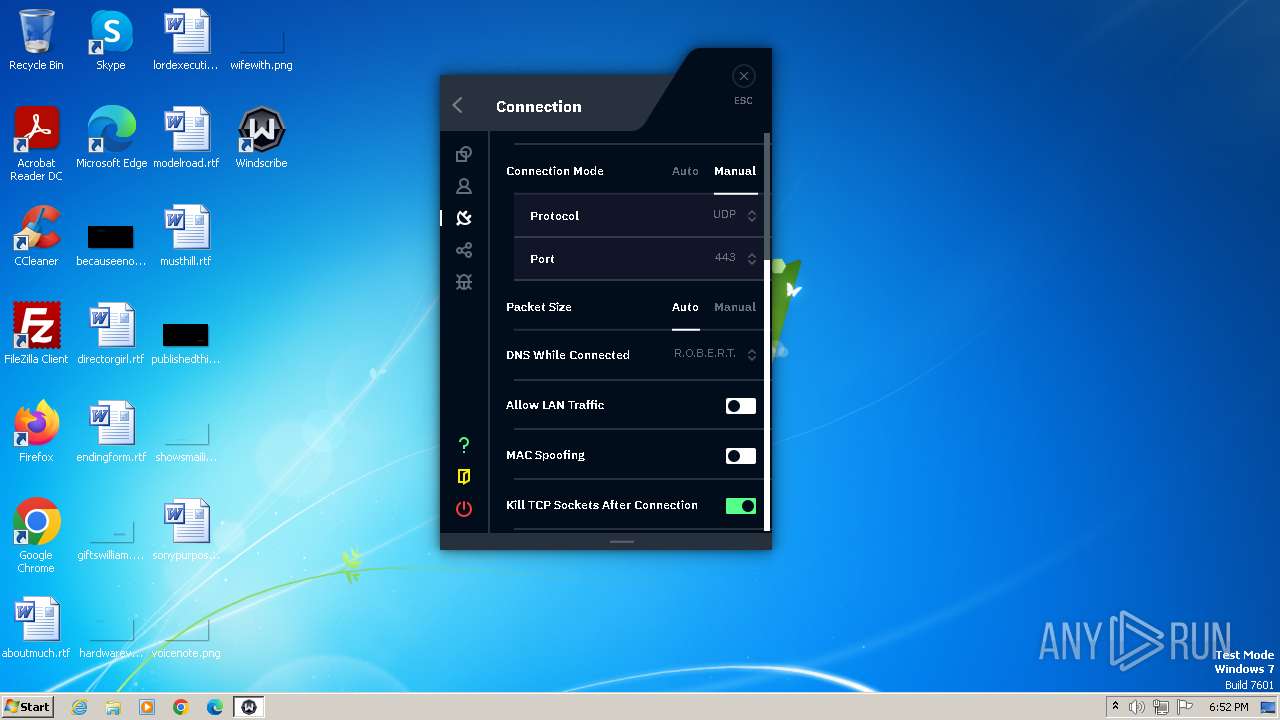
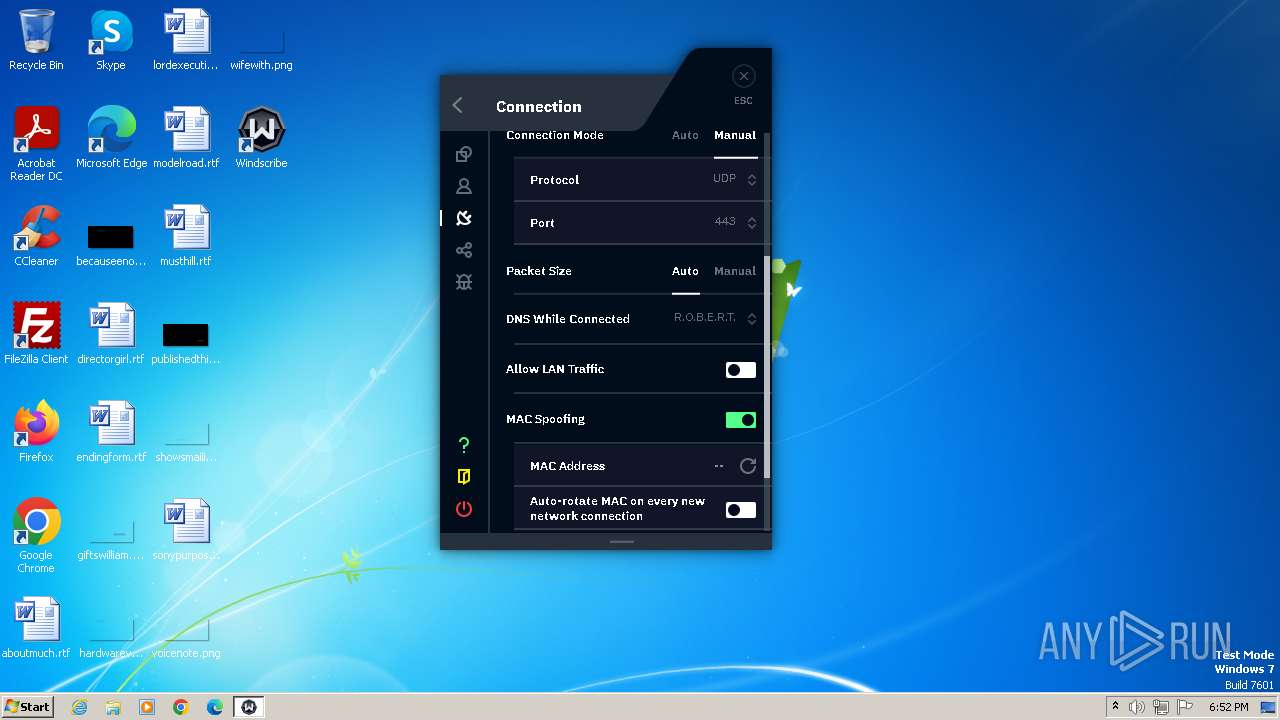
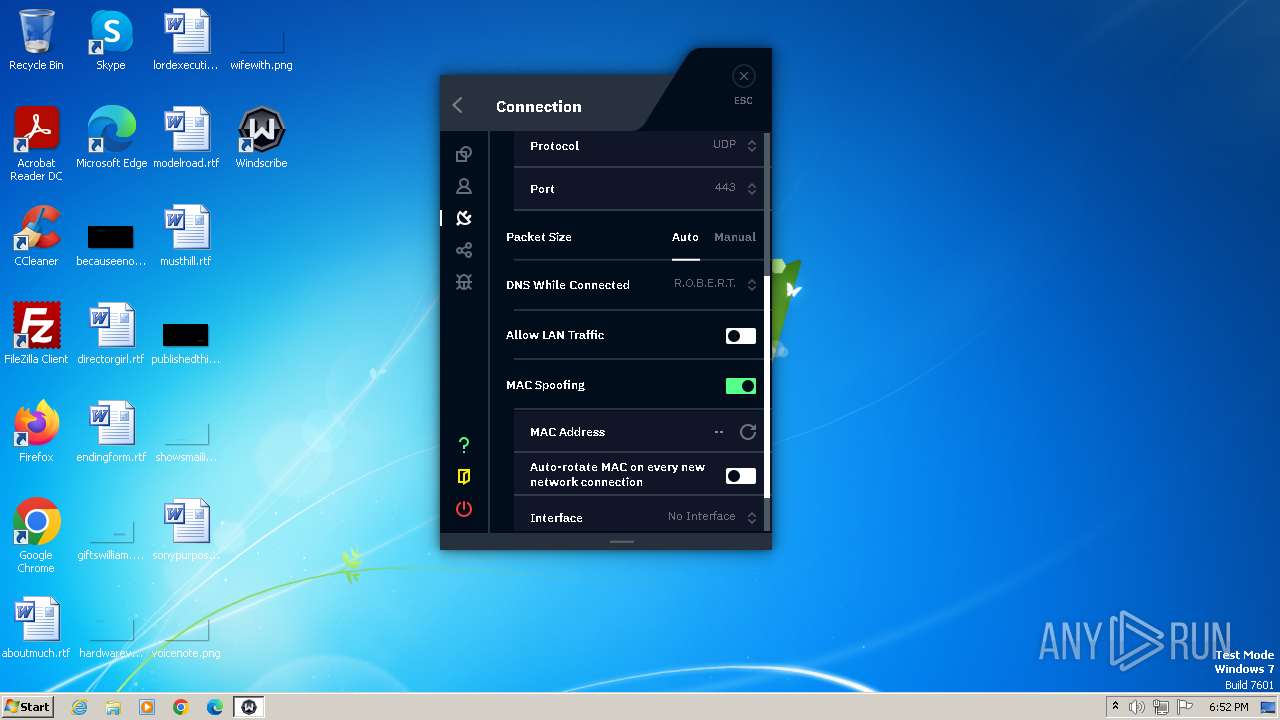
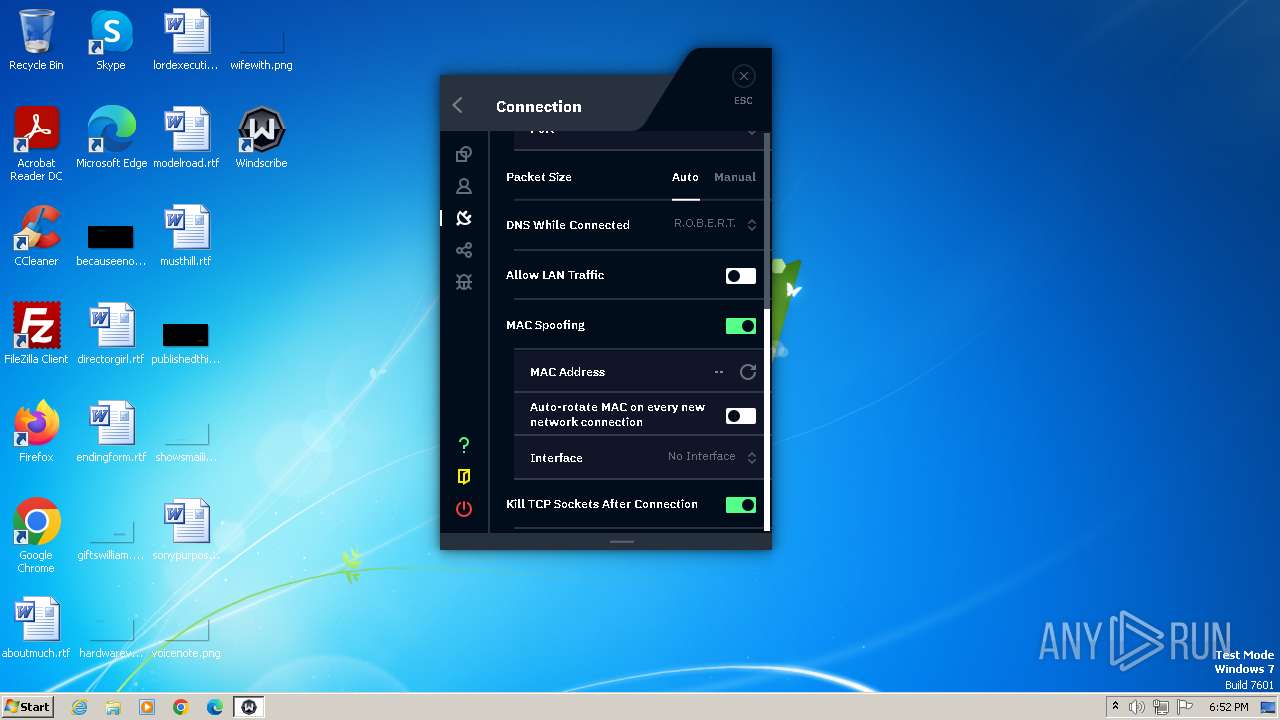
Suspicious use of NETSH.EXE
- windscribeopenvpn_2_5_4.exe (PID: 3036)
- windscribeopenvpn_2_5_4.exe (PID: 2540)
Uses ROUTE.EXE to modify routing table
- windscribeopenvpn_2_5_4.exe (PID: 3720)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 324)
- iexplore.exe (PID: 128)
- Windscribe_2.4.exe (PID: 1732)
- tapinstall.exe (PID: 2328)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 2916)
- tapinstall.exe (PID: 2360)
- drvinst.exe (PID: 3072)
- drvinst.exe (PID: 2936)
Application launched itself
- iexplore.exe (PID: 128)
- msedge.exe (PID: 4008)
- msedge.exe (PID: 3460)
The process uses the downloaded file
- iexplore.exe (PID: 128)
Creates files or folders in the user directory
- Windscribe_2.4.exe (PID: 1732)
- Windscribe.exe (PID: 3504)
Checks supported languages
- Windscribe_2.4.exe (PID: 1732)
- subinacl.exe (PID: 1892)
- tapinstall.exe (PID: 2328)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 2916)
- tapinstall.exe (PID: 2360)
- drvinst.exe (PID: 3072)
- drvinst.exe (PID: 2936)
- WindscribeLauncher.exe (PID: 3376)
- Windscribe.exe (PID: 3504)
- windscribeopenvpn_2_5_4.exe (PID: 3508)
- WindscribeService.exe (PID: 3660)
- windscribeopenvpn_2_5_4.exe (PID: 3036)
- wmpnscfg.exe (PID: 2984)
- wmpnscfg.exe (PID: 3544)
- wmpnscfg.exe (PID: 3512)
- wmpnscfg.exe (PID: 2964)
- wmpnscfg.exe (PID: 3600)
- windscribeopenvpn_2_5_4.exe (PID: 2540)
- wmpnscfg.exe (PID: 3828)
- wmpnscfg.exe (PID: 1876)
- wmpnscfg.exe (PID: 2992)
- wmpnscfg.exe (PID: 3728)
- windscribeopenvpn_2_5_4.exe (PID: 3720)
- wmpnscfg.exe (PID: 3740)
- wmpnscfg.exe (PID: 3712)
Reads the computer name
- Windscribe_2.4.exe (PID: 1732)
- subinacl.exe (PID: 1892)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 2916)
- tapinstall.exe (PID: 2360)
- tapinstall.exe (PID: 2328)
- drvinst.exe (PID: 3072)
- drvinst.exe (PID: 2936)
- Windscribe.exe (PID: 3504)
- WindscribeService.exe (PID: 3660)
- windscribeopenvpn_2_5_4.exe (PID: 3036)
- wmpnscfg.exe (PID: 2984)
- wmpnscfg.exe (PID: 3544)
- wmpnscfg.exe (PID: 3512)
- wmpnscfg.exe (PID: 2964)
- wmpnscfg.exe (PID: 3600)
- windscribeopenvpn_2_5_4.exe (PID: 2540)
- wmpnscfg.exe (PID: 3828)
- wmpnscfg.exe (PID: 1876)
- wmpnscfg.exe (PID: 2992)
- wmpnscfg.exe (PID: 3728)
- windscribeopenvpn_2_5_4.exe (PID: 3720)
- wmpnscfg.exe (PID: 3740)
- wmpnscfg.exe (PID: 3712)
Process drops legitimate windows executable
- Windscribe_2.4.exe (PID: 1732)
Dropped object may contain TOR URL's
- Windscribe_2.4.exe (PID: 1732)
The process drops C-runtime libraries
- Windscribe_2.4.exe (PID: 1732)
Creates files in the program directory
- Windscribe_2.4.exe (PID: 1732)
- WindscribeService.exe (PID: 3660)
Reads the machine GUID from the registry
- tapinstall.exe (PID: 2328)
- drvinst.exe (PID: 2740)
- drvinst.exe (PID: 2916)
- tapinstall.exe (PID: 2360)
- drvinst.exe (PID: 3072)
- drvinst.exe (PID: 2936)
- Windscribe_2.4.exe (PID: 1732)
- Windscribe.exe (PID: 3504)
- WindscribeService.exe (PID: 3660)
Create files in a temporary directory
- tapinstall.exe (PID: 2328)
- tapinstall.exe (PID: 2360)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 996)
- rundll32.exe (PID: 952)
Executes as Windows Service
- VSSVC.exe (PID: 1852)
- WindscribeService.exe (PID: 3660)
Reads Environment values
- drvinst.exe (PID: 2916)
- drvinst.exe (PID: 2936)
Reads the time zone
- runonce.exe (PID: 2984)
Manual execution by a user
- WindscribeLauncher.exe (PID: 3376)
- wmpnscfg.exe (PID: 2984)
- wmpnscfg.exe (PID: 3544)
- wmpnscfg.exe (PID: 3512)
- wmpnscfg.exe (PID: 2964)
- wmpnscfg.exe (PID: 3600)
- wmpnscfg.exe (PID: 3828)
- wmpnscfg.exe (PID: 1876)
- wmpnscfg.exe (PID: 2992)
- wmpnscfg.exe (PID: 3728)
- wmpnscfg.exe (PID: 3740)
- wmpnscfg.exe (PID: 3712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
149
Monitored processes
83
Malicious processes
12
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://assets.totallyacdn.com/desktop/win/Windscribe_2.4.exe" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 268 | wmic path win32_networkadapter where description="Windscribe VPN" get ConfigManagerErrorCode | C:\Windows\System32\wbem\WMIC.exe | — | WindscribeService.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2332 --field-trial-handle=1344,i,10623808429668117427,17544984278166945209,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:128 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 696 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.PageScreenshotProcessor --lang=en-US --service-sandbox-type=entity_extraction --mojo-platform-channel-handle=1420 --field-trial-handle=1344,i,10623808429668117427,17544984278166945209,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 844 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1332 --field-trial-handle=1384,i,5745233250445418174,17375871271343603392,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 876 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4456 --field-trial-handle=1344,i,10623808429668117427,17544984278166945209,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 912 | C:\Windows\system32\netsh.exe interface ip set dns 22 static 10.255.255.1 validate=no | C:\Windows\System32\netsh.exe | — | windscribeopenvpn_2_5_4.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{41ea6a39-1dca-6c19-c8c9-bb5bc03bf468} Global\{162c6be3-0191-1284-3bb8-a47980e73b66} C:\Windows\System32\DriverStore\Temp\{167061e3-1dca-6c19-42d1-094bd9c94d7b}\windtun420.inf C:\Windows\System32\DriverStore\Temp\{167061e3-1dca-6c19-42d1-094bd9c94d7b}\windtun420.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 996 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{380c2f6a-4159-2826-6a2f-0c3801051a05} Global\{5d7c9d05-ac5e-0e16-3642-5b1c5309a97d} C:\Windows\System32\DriverStore\Temp\{52db3fae-b85b-473d-172b-b254b49da539}\oemvista.inf C:\Windows\System32\DriverStore\Temp\{52db3fae-b85b-473d-172b-b254b49da539}\tapwindscribe0901.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
74 408
Read events
73 077
Write events
1 227
Delete events
104
Modification events
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (128) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
107
Suspicious files
198
Text files
84
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:C77DBECD7ADDFFA52CCA337D4D02B4A7 | SHA256:EE09DC80C864E73B7E971A71EA08090D1AF37A1629AF79A7CFE0A9B18D3B4439 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\Windscribe_2.4[1].exe | executable | |
MD5:20D87B31B51D0093754DDCF662BC7037 | SHA256:56FB0510448AC9EA349889B5ADEFCE62347C91FCBC03D235F7339AB13297B777 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:8108BA1DC25E7682F9ECE87C6A02C424 | SHA256:360708B242FAE7EE1270484EB9A1CA19362CD84054F04DD5BBA04850ED49ADE4 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:A60956E0639259EED68447AAA1517ECA | SHA256:B1A9965618636BE185E529CC8EA34AF490B374A7E38BC518E88629A3E8B4F380 | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{36FBC747-A67B-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:5C3D58909F0EEEC20E7717246E513F1C | SHA256:9BBFCE063F7C62F977C9E9E0B2275654E4A905E4CEBB80DD42CEC09761D424DB | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Windscribe_2.4.exe | executable | |
MD5:93F3733ADAB15B441472DCD88A8C22B6 | SHA256:4F222F9377B00E7C9B05D64D5E92A3CDB9FBFF1B3EEE88078EDA6114B4AA80B0 | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF20F1AD391D193B85.TMP | binary | |
MD5:379592FCD0C5E8AEF565EB03FCF9A8FB | SHA256:FB764076F81BA21B9D44E7E68B6B66CE4B9B7E87002F24DE8996D15AA3D910FC | |||
| 1732 | Windscribe_2.4.exe | C:\Program Files\Windscribe\splittunnel\windscribesplittunnel.cat | binary | |
MD5:66FD97366337DBB8D475CDBB6D5294E9 | SHA256:0DF9BDD0370BAA7D450EB744CE1D7CAF4C72B32F6677E7C07AE8A12552EAAC21 | |||
| 128 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Windscribe_2.4.exe.1gxywgb.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
285
DNS requests
55
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
324 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?16e53a13f7f2d96f | unknown | compressed | 4.66 Kb | unknown |
324 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7a9d8baceff24343 | unknown | compressed | 4.66 Kb | unknown |
3660 | WindscribeService.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnR4FoxLLkI7vkvsUIFlZt%2BlGH3gQUWsS5eyoKo6XqcQPAYPkt9mV1DlgCEA9e5DvupQ7V8Ox2W%2FZbE1A%3D | unknown | binary | 471 b | unknown |
324 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?eca8823d6d0692d6 | unknown | — | — | unknown |
3660 | WindscribeService.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
324 | iexplore.exe | 104.24.30.5:443 | assets.totallyacdn.com | CLOUDFLARENET | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
324 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
324 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3660 | WindscribeService.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
3504 | Windscribe.exe | 104.20.94.59:443 | api.windscribe.com | CLOUDFLARENET | — | shared |
3504 | Windscribe.exe | 185.244.214.34:443 | — | M247 Ltd | PL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
assets.totallyacdn.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.windscribe.com |
| unknown |
www.windscribe.com |
| unknown |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
windscribe.com |
| unknown |
Threats
Process | Message |
|---|---|
Windscribe.exe | [{gmt_time} 0.017] [basic] App version: "v2.4.10"
|
Windscribe.exe | [{gmt_time} 0.017] [basic] App start time: "Fri Dec 29 18:51:46 2023"
|
Windscribe.exe | [{gmt_time} 0.017] [basic] OS Version: "Windows 7 Service Pack 1 (major: 6, minor: 1) (build: 7601)"
|
Windscribe.exe | [{gmt_time} 0.041] [basic] Detected AntiSpyware products: "(name = Windows Defender, state = 393472 [disabled up-to-date])"
|
Windscribe.exe | [{gmt_time} 0.041] [basic] Detected Firewall products: empty
|
Windscribe.exe | [{gmt_time} 0.041] [basic] Detected AntiVirus products: empty
|
Windscribe.exe | [{gmt_time} 0.097] [basic] DpiScaleManager::constructor -> DPI: 96 ; scale: 1 ; devicePixelRatio: 1
|
Windscribe.exe | [{gmt_time} 0.092] [basic] Selected OpenVPN version: "2.5.4"
|
Windscribe.exe | [{gmt_time} 0.098] [basic] OS in dark mode: false
|
Windscribe.exe | [{gmt_time} 0.092] [basic] Detected OpenVPN versions: ("2.5.4")
|