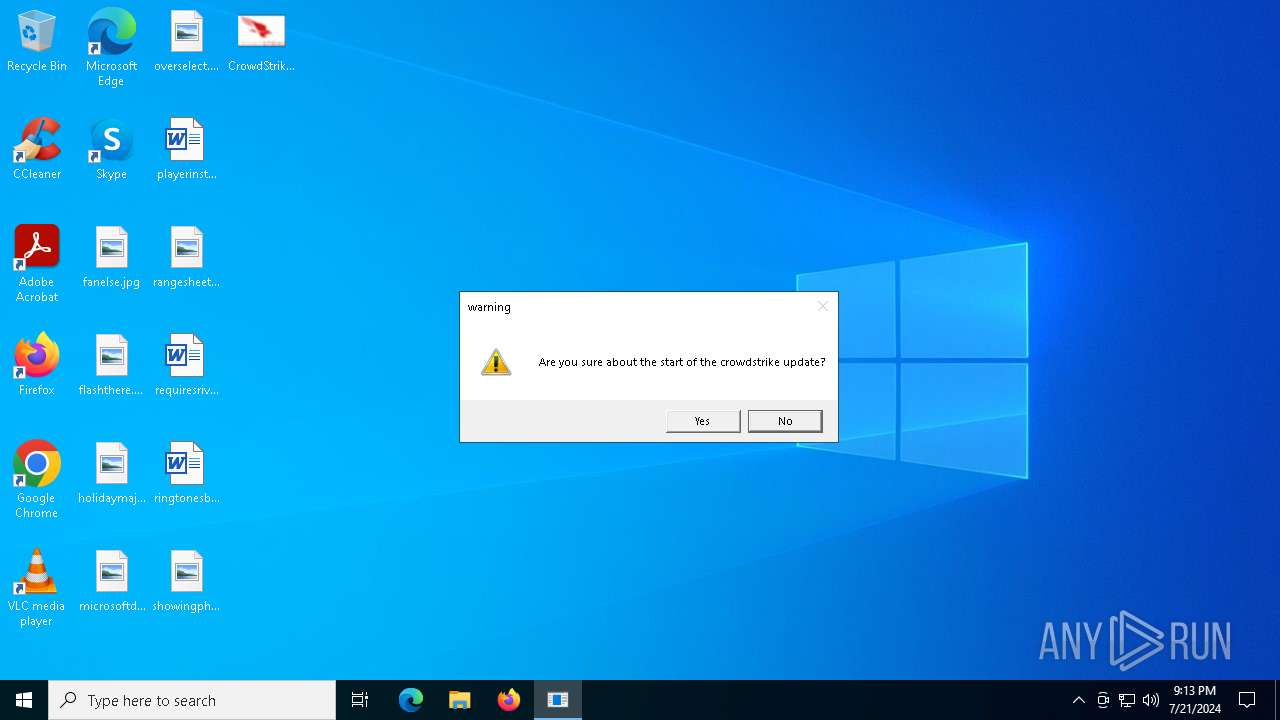
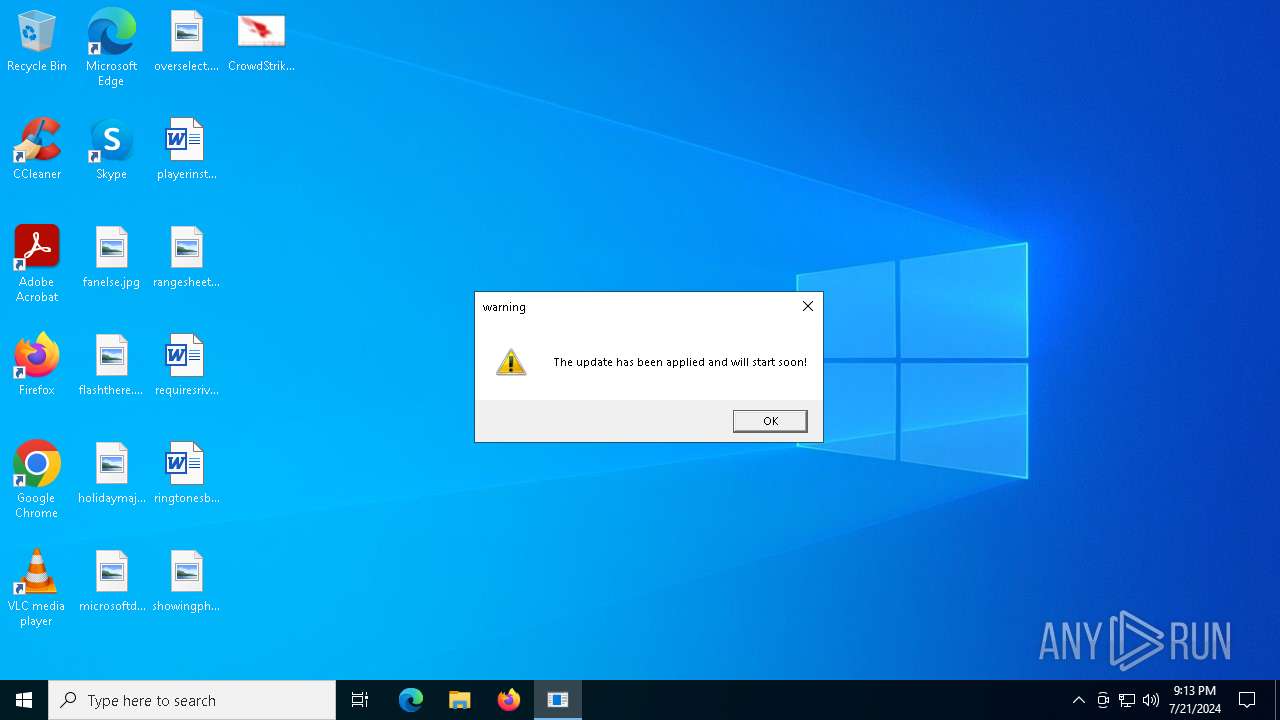
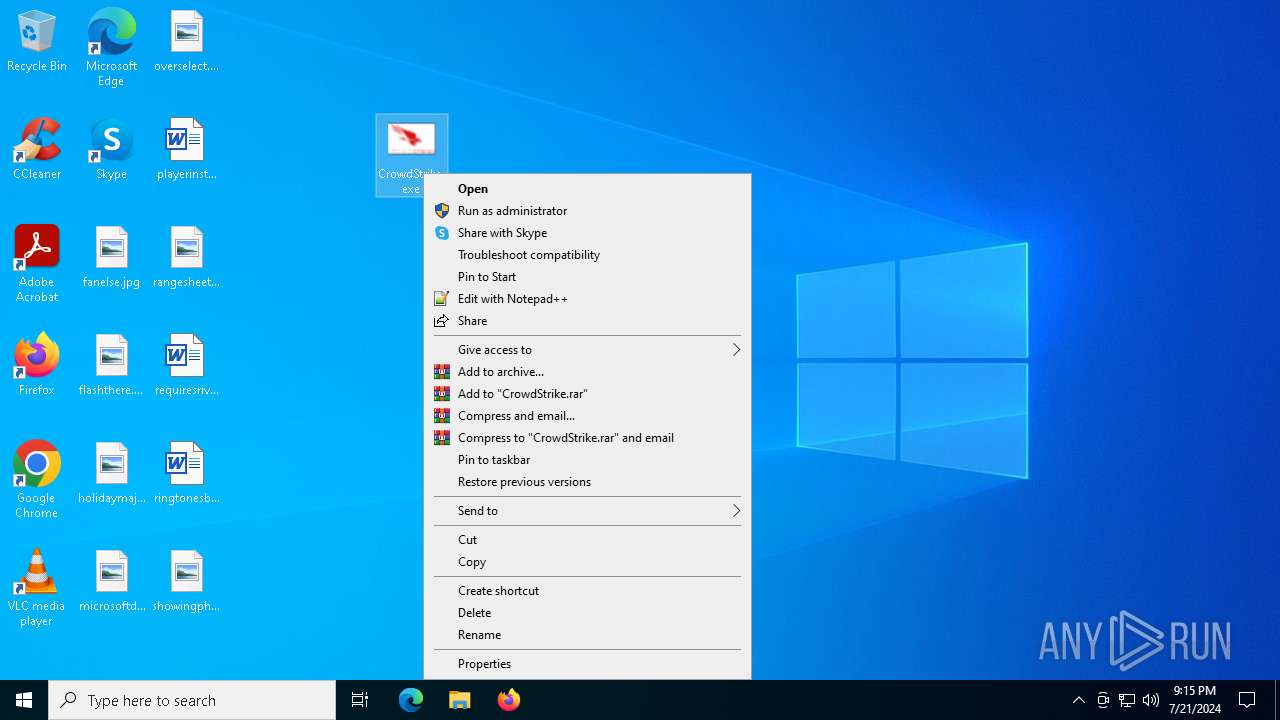
| File name: | CrowdStrike |
| Full analysis: | https://app.any.run/tasks/2e3c3060-0486-4049-8370-d43f8f0fbb23 |
| Verdict: | Malicious activity |
| Analysis date: | July 21, 2024, 21:13:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 755C0350038DAEFB29B888B6F8739E81 |
| SHA1: | 5B2F56953B3C925693386CAE5974251479F03928 |
| SHA256: | 4491901EFF338AB52C85A77A3FBD3CE80FDA738046EE3B7DA7BE468DA5B331A3 |
| SSDEEP: | 98304:CO4TQUWqwtFki0Kgxu3EgjvhjHcAf5/3rk6+YCJ28ZAj/nb2kk/9HXwsWJt2UGfR:lEv |
MALICIOUS
Drops the executable file immediately after the start
- CrowdStrike.exe (PID: 6348)
- cmd.exe (PID: 7604)
- Champion.pif (PID: 6604)
- RegAsm.exe (PID: 6084)
- RegAsm.exe (PID: 7332)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 6912)
- findstr.exe (PID: 6320)
- findstr.exe (PID: 4972)
- findstr.exe (PID: 5624)
- findstr.exe (PID: 5156)
- findstr.exe (PID: 7660)
- findstr.exe (PID: 7080)
- findstr.exe (PID: 7292)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 6084)
SUSPICIOUS
Reads security settings of Internet Explorer
- CrowdStrike.exe (PID: 6348)
- Champion.pif (PID: 6660)
- CrowdStrike.exe (PID: 1144)
- CrowdStrike.exe (PID: 3540)
- Champion.pif (PID: 2968)
- CrowdStrike.exe (PID: 1144)
Reads the date of Windows installation
- CrowdStrike.exe (PID: 6348)
- Champion.pif (PID: 6660)
- CrowdStrike.exe (PID: 1144)
- CrowdStrike.exe (PID: 3540)
- Champion.pif (PID: 2968)
- CrowdStrike.exe (PID: 1144)
Starts CMD.EXE for commands execution
- CrowdStrike.exe (PID: 6348)
- cmd.exe (PID: 7604)
- Champion.pif (PID: 6660)
- CrowdStrike.exe (PID: 1144)
- cmd.exe (PID: 7548)
- CrowdStrike.exe (PID: 3540)
- cmd.exe (PID: 7800)
- Champion.pif (PID: 2968)
- cmd.exe (PID: 6288)
- CrowdStrike.exe (PID: 1144)
Executing commands from ".cmd" file
- CrowdStrike.exe (PID: 6348)
- CrowdStrike.exe (PID: 1144)
- CrowdStrike.exe (PID: 3540)
- CrowdStrike.exe (PID: 1144)
Get information on the list of running processes
- cmd.exe (PID: 7604)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 6288)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7604)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 6288)
Application launched itself
- cmd.exe (PID: 7604)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 6288)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 7604)
Suspicious file concatenation
- cmd.exe (PID: 2476)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 3792)
- cmd.exe (PID: 7864)
Executable content was dropped or overwritten
- cmd.exe (PID: 7604)
- Champion.pif (PID: 6604)
- RegAsm.exe (PID: 6084)
- RegAsm.exe (PID: 7332)
Starts application with an unusual extension
- cmd.exe (PID: 7604)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 6288)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7604)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 6288)
The executable file from the user directory is run by the CMD process
- Champion.pif (PID: 6660)
- Champion.pif (PID: 6604)
- Champion.pif (PID: 2968)
- Champion.pif (PID: 3624)
The process creates files with name similar to system file names
- Champion.pif (PID: 6604)
Starts a Microsoft application from unusual location
- RegAsm.exe (PID: 6084)
- RegAsm.exe (PID: 7332)
Process drops legitimate windows executable
- Champion.pif (PID: 6604)
Drops a system driver (possible attempt to evade defenses)
- RegAsm.exe (PID: 6084)
- RegAsm.exe (PID: 7332)
Checks for external IP
- RegAsm.exe (PID: 6084)
Executes application which crashes
- RegAsm.exe (PID: 6084)
- GameBar.exe (PID: 6264)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RegAsm.exe (PID: 6084)
INFO
Checks supported languages
- CrowdStrike.exe (PID: 6348)
- Champion.pif (PID: 6660)
- CrowdStrike.exe (PID: 1144)
- Champion.pif (PID: 6604)
- RegAsm.exe (PID: 6084)
- CrowdStrike.exe (PID: 3540)
- Champion.pif (PID: 2968)
- CrowdStrike.exe (PID: 1144)
- Champion.pif (PID: 3624)
- RegAsm.exe (PID: 7332)
Create files in a temporary directory
- CrowdStrike.exe (PID: 6348)
- CrowdStrike.exe (PID: 1144)
- Champion.pif (PID: 6604)
- RegAsm.exe (PID: 6084)
- CrowdStrike.exe (PID: 3540)
- CrowdStrike.exe (PID: 1144)
- RegAsm.exe (PID: 7332)
Process checks computer location settings
- CrowdStrike.exe (PID: 6348)
- Champion.pif (PID: 6660)
- CrowdStrike.exe (PID: 1144)
- CrowdStrike.exe (PID: 3540)
- Champion.pif (PID: 2968)
- CrowdStrike.exe (PID: 1144)
Reads the computer name
- CrowdStrike.exe (PID: 6348)
- Champion.pif (PID: 6660)
- CrowdStrike.exe (PID: 1144)
- Champion.pif (PID: 6604)
- RegAsm.exe (PID: 6084)
- CrowdStrike.exe (PID: 3540)
- Champion.pif (PID: 2968)
- CrowdStrike.exe (PID: 1144)
- Champion.pif (PID: 3624)
- RegAsm.exe (PID: 7332)
Reads mouse settings
- Champion.pif (PID: 6660)
- Champion.pif (PID: 6604)
- Champion.pif (PID: 2968)
- Champion.pif (PID: 3624)
Checks proxy server information
- RegAsm.exe (PID: 6084)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 6084)
Reads Environment values
- RegAsm.exe (PID: 6084)
Disables trace logs
- RegAsm.exe (PID: 6084)
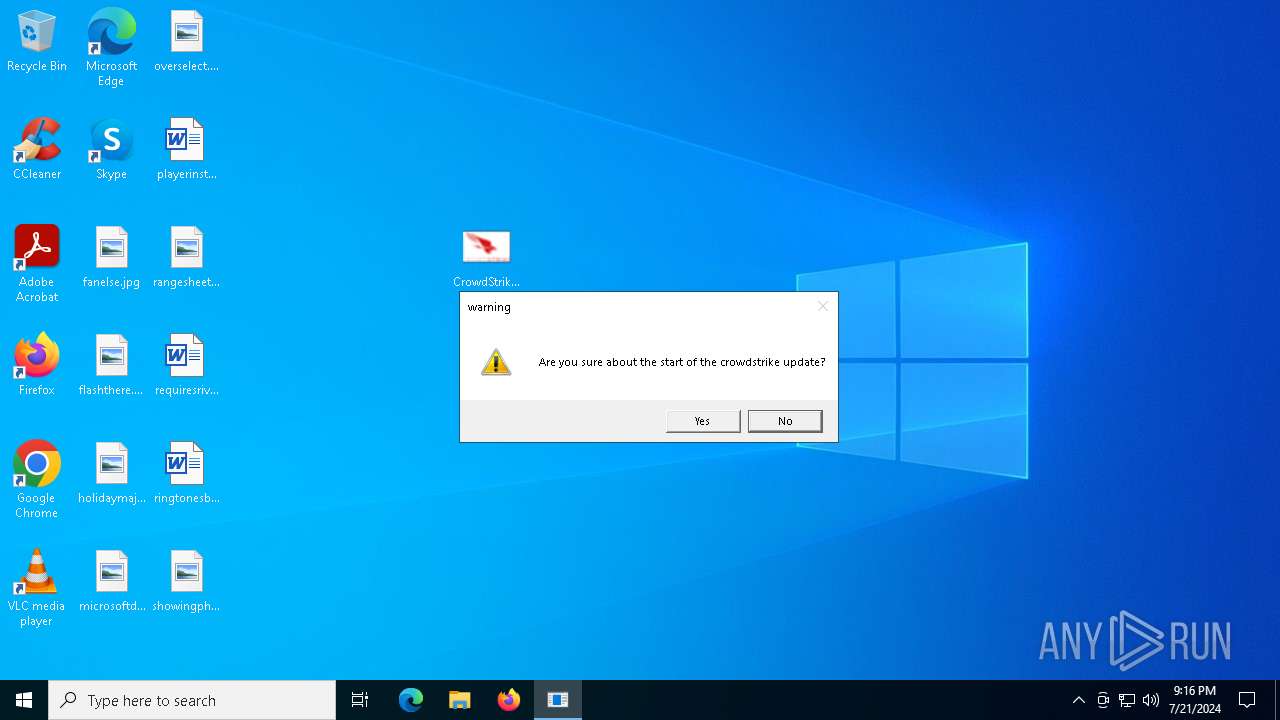
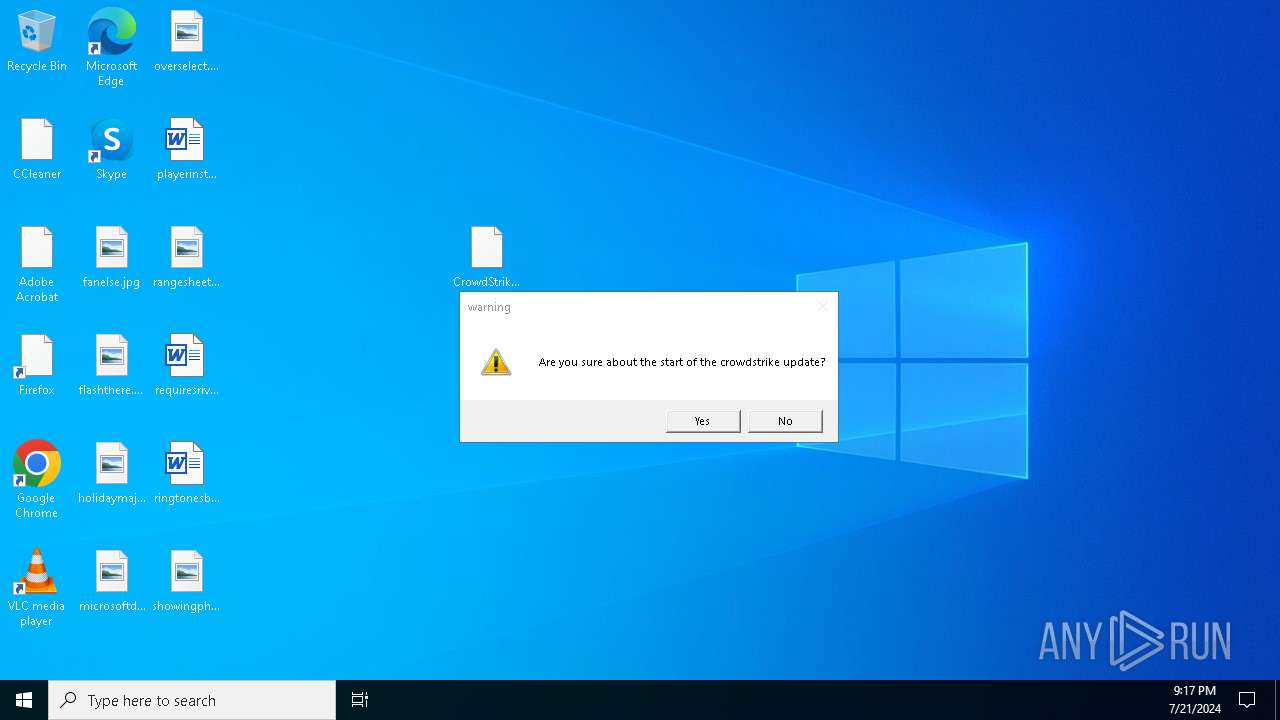
Manual execution by a user
- CrowdStrike.exe (PID: 3540)
- WerFault.exe (PID: 8160)
Reads the software policy settings
- RegAsm.exe (PID: 6084)
Attempting to use instant messaging service
- RegAsm.exe (PID: 6084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:19:54+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 28160 |
| InitializedDataSize: | 446976 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x3883 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
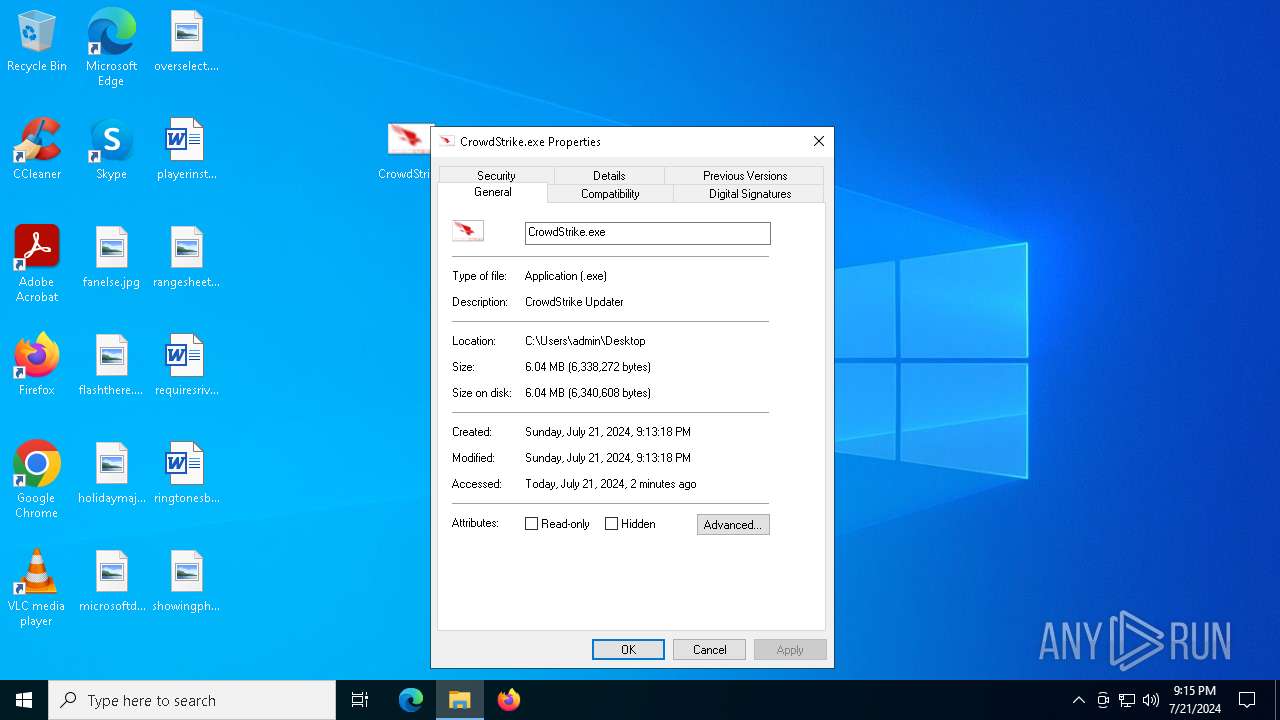
| FileDescription: | CrowdStrike Updater |
| FileVersion: | 1.0.0.0 |
| InternalName: | CrowdStrike Updater.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | CrowdStrike Updater.exe |
| ProductName: | CrowdStrike |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
231
Monitored processes
63
Malicious processes
12
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | findstr /V "locatedflatrendsoperating" Ukraine | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 676 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | C:\Users\admin\Desktop\CrowdStrike.exe | C:\Users\admin\Desktop\CrowdStrike.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: CrowdStrike Updater Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1144 | C:\Users\admin\Desktop\CrowdStrike.exe | C:\Users\admin\Desktop\CrowdStrike.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: CrowdStrike Updater Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1212 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 1220 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 | |||||||||||||||
| 1332 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2476 | cmd /c copy /b Treating + Viagra + Vision + Jul + Str 564784\L | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2620 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 728
Read events
10 665
Write events
63
Delete events
0
Modification events
| (PID) Process: | (6348) CrowdStrike.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6348) CrowdStrike.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6348) CrowdStrike.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6348) CrowdStrike.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6660) Champion.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6660) Champion.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6660) Champion.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6660) Champion.pif | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1144) CrowdStrike.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1144) CrowdStrike.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
8
Suspicious files
1 062
Text files
144
Unknown types
112
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Consequences | pgc | |
MD5:19E98CBB75F1B8BD8EFDE5FE0ABD34B2 | SHA256:DF0CB092CD377DF6571BB86BB48E586E1A5012EDBE1C8A180DE8BE3FAE080356 | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Honda | binary | |
MD5:A964F4C9C7CA51DAC3A481EB260810C3 | SHA256:547AE8F99A07865535955A2B3913C9F8D5B06EB08AFE36816F60841E19024CD0 | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Recipes | binary | |
MD5:D0808D4907E66F73A821AB6E7FC942C1 | SHA256:221EEE5A84FDE75849816CDBB84F723E5C96A3E81922692DB21E7844B8537A04 | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Wave | binary | |
MD5:E27F5F4215920D7C0DB01D3A07E32FAD | SHA256:C5A836D0021A235D4FC30764DFD4A2ABB33B23CA25F4DCA4A9BA7A8423F7753E | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Handle | binary | |
MD5:4DD2539DAA375331505B81E8BAD6F6F3 | SHA256:2FA5DFE0785E6E2EE3CF30277E09BDB46D2B7FC096D40D6AAF78EC27F5B6B68B | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Halo | binary | |
MD5:E859420711C0FAFFEDF33DA17A2EB4B1 | SHA256:5010762DC34EB3679AFE29CDA9C2040309D8A784BEA758F64ED4977773C20465 | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Develops | binary | |
MD5:6DB6B2AE5BAAE977FAE168E4A08641B4 | SHA256:88C137E5726172061F509246ADA7D2D3CB8E5DABCF35CADF1D49C49B073A80A4 | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Democracy | binary | |
MD5:DEE42E543988CD988E8AEB4B03F488EB | SHA256:8F444581168196C045FABDE65F1C0667154AFE2FE6302E7FF342AEFD3B6B829D | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Sept | mp3 | |
MD5:ED3292F153EC8B60B8F7FFB1CA9F0858 | SHA256:1E8C217DF502D035EA3B1AC2212C20C9B9DA4DD6FF81D1C3C41A0AF00D8C0D5D | |||
| 6348 | CrowdStrike.exe | C:\Users\admin\AppData\Local\Temp\Often | abr | |
MD5:8C1308689913B76D47B2FEA6C94378C6 | SHA256:E0055A2B04595818CDC4B3C5EDB54539E5C3EDF69E134914E6BAD45AB56D0A04 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
46
DNS requests
20
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6084 | RegAsm.exe | GET | 200 | 104.16.184.241:80 | http://icanhazip.com/ | unknown | — | — | shared |
— | — | GET | 200 | 104.16.184.241:80 | http://icanhazip.com/ | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4716 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
532 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7856 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4716 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
XLuvBdVPcngNKMPfoEAAuT.XLuvBdVPcngNKMPfoEAAuT |
| unknown |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6084 | RegAsm.exe | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
6084 | RegAsm.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
2168 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6084 | RegAsm.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
6084 | RegAsm.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
— | — | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |