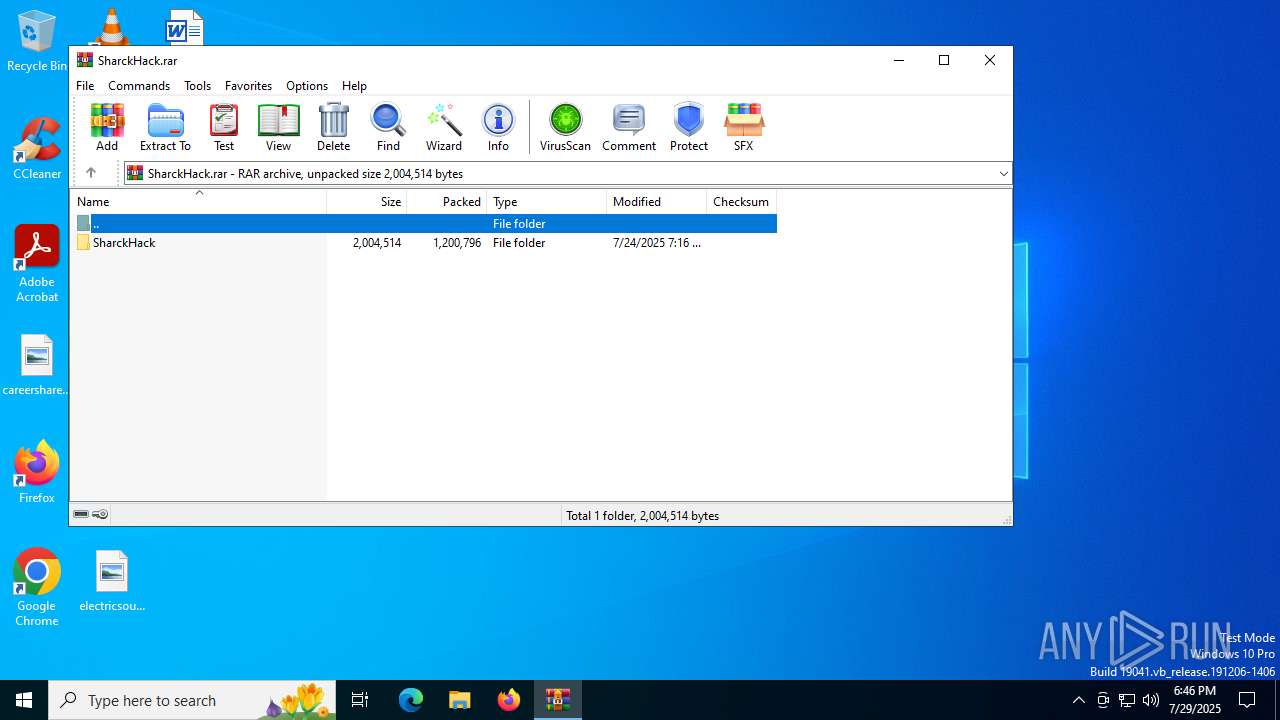
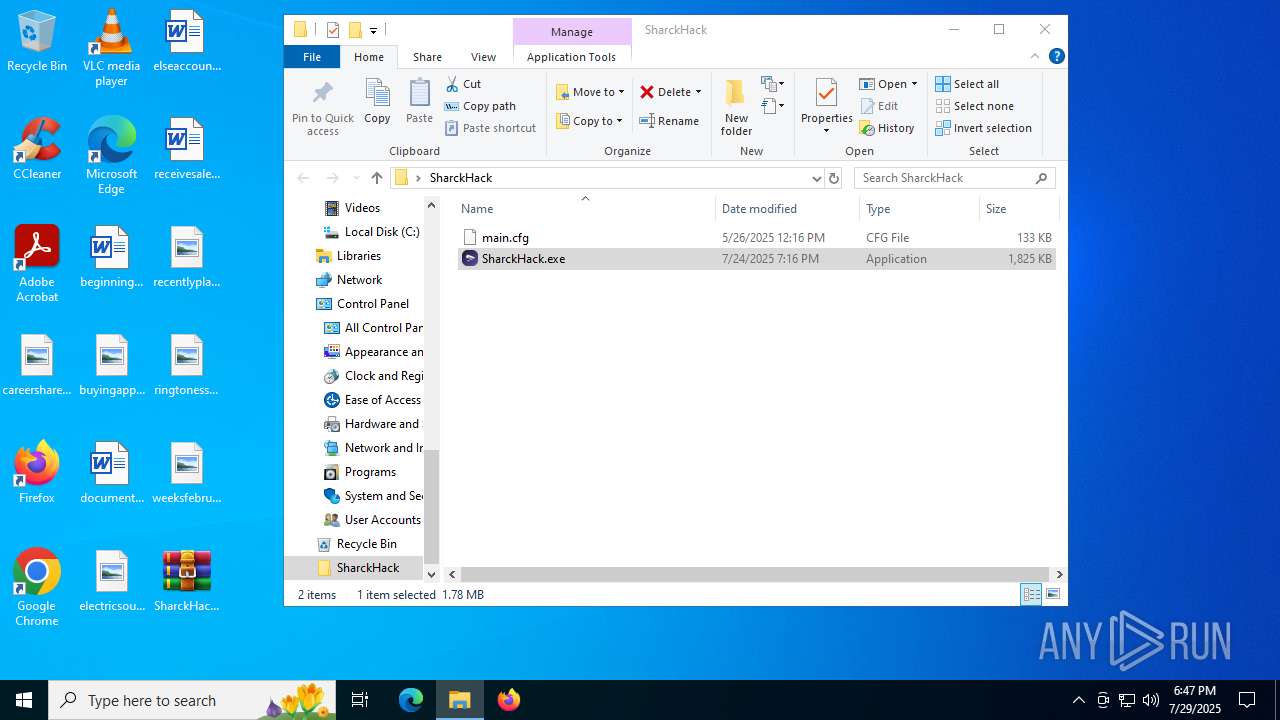
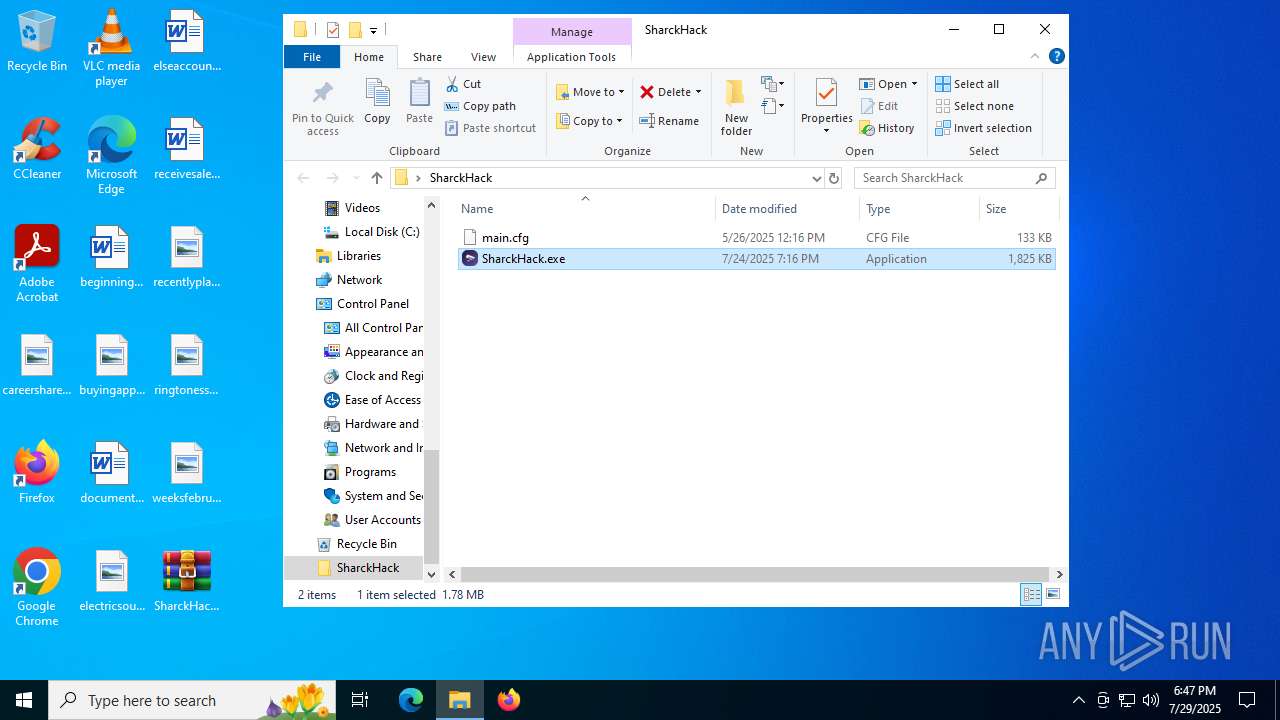
| File name: | SharckHack.rar |
| Full analysis: | https://app.any.run/tasks/508a2c86-02ea-445b-b6b4-252c2a6b6e21 |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2025, 18:46:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 831D99F1E250166499D837C0C3A4BE6B |
| SHA1: | CA7485D4E47C0269A9A1A2E5CA72F362F01BF9F3 |
| SHA256: | 441088AFADE634228CDD5D77AF8E226111E5CF08F78E8C22C2664276256F964C |
| SSDEEP: | 49152:iTh1/N64A01/p7Hj2p1KSF3Sb2DpDALFJdqY9rx8XVACJnafw7Zp20fWo5W9heWZ:iTh116jC/d0gvbSYbdNBnmJ7Zp2DsWjV |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2492)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6356)
- cmd.exe (PID: 5476)
Changes the login/logoff helper path in the registry
- SharckHack.exe (PID: 5684)
Changes the AppInit_DLLs value (autorun option)
- SharckHack.exe (PID: 5684)
SUSPICIOUS
Reads security settings of Internet Explorer
- SharckHack.exe (PID: 2348)
- SharckHack.exe (PID: 4944)
- SharckHack.exe (PID: 5684)
- SharckHack.exe (PID: 6508)
Reads the date of Windows installation
- SharckHack.exe (PID: 2348)
- SharckHack.exe (PID: 4944)
- SharckHack.exe (PID: 5684)
- SharckHack.exe (PID: 6508)
Executable content was dropped or overwritten
- SharckHack.exe (PID: 2348)
- SharckHack.exe (PID: 5684)
Executes application which crashes
- MSBuild.exe (PID: 2580)
- MSBuild.exe (PID: 4024)
Starts CMD.EXE for commands execution
- SharckHack.exe (PID: 5684)
- System 32 (PID: 3488)
- SharckHack.exe (PID: 6256)
Application launched itself
- SharckHack.exe (PID: 4944)
INFO
Manual execution by a user
- SharckHack.exe (PID: 2348)
- System 32 (PID: 3488)
- SharckHack.exe (PID: 6508)
Checks supported languages
- SharckHack.exe (PID: 2348)
- SharkHack.exe (PID: 3572)
- SharckHack.exe (PID: 4944)
- MSBuild.exe (PID: 2580)
- SharckHack.exe (PID: 5684)
- SharckHack.exe (PID: 6508)
- MSBuild.exe (PID: 4024)
- SharckHack.exe (PID: 6256)
- System 32 (PID: 3488)
- SharkHack.exe (PID: 1740)
Reads the computer name
- SharckHack.exe (PID: 2348)
- SharckHack.exe (PID: 4944)
- MSBuild.exe (PID: 2580)
- SharckHack.exe (PID: 5684)
- System 32 (PID: 3488)
- SharckHack.exe (PID: 6256)
- SharckHack.exe (PID: 6508)
- MSBuild.exe (PID: 4024)
Reads the machine GUID from the registry
- SharckHack.exe (PID: 2348)
- SharckHack.exe (PID: 4944)
- MSBuild.exe (PID: 2580)
- SharckHack.exe (PID: 5684)
- System 32 (PID: 3488)
- SharckHack.exe (PID: 6508)
- SharckHack.exe (PID: 6256)
- MSBuild.exe (PID: 4024)
Create files in a temporary directory
- SharckHack.exe (PID: 2348)
- SharckHack.exe (PID: 6508)
Process checks computer location settings
- SharckHack.exe (PID: 2348)
- SharckHack.exe (PID: 4944)
- SharckHack.exe (PID: 6508)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2492)
Launching a file from Task Scheduler
- cmd.exe (PID: 5476)
Checks proxy server information
- slui.exe (PID: 1980)
- WerFault.exe (PID: 2064)
- WerFault.exe (PID: 5168)
Creates files or folders in the user directory
- WerFault.exe (PID: 2064)
- WerFault.exe (PID: 5168)
Reads the software policy settings
- WerFault.exe (PID: 2064)
- slui.exe (PID: 1980)
- WerFault.exe (PID: 5168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 2864 |
| UncompressedSize: | 135714 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | SharckHack/main.cfg |
Total processes
183
Monitored processes
30
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1644 | schtasks /run /i /tn "System 32" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\AppData\Local\Temp\SharkHack.exe" | C:\Users\admin\AppData\Local\Temp\SharkHack.exe | — | SharckHack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 1944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1980 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2064 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2580 -s 896 | C:\Windows\SysWOW64\WerFault.exe | MSBuild.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2348 | "C:\Users\admin\Desktop\SharckHack\SharckHack.exe" | C:\Users\admin\Desktop\SharckHack\SharckHack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2492 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\SharckHack.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2580 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | SharkHack.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 3221225477 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2628 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | SharkHack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2660 | schtasks /create /f /sc minute /mo 30 /tn "System 32" /tr "C:\WINDOWS\System 32" /RL HIGHEST | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 833
Read events
11 811
Write events
22
Delete events
0
Modification events
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SharckHack.rar | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3900000085000000F90300006E020000 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
4
Suspicious files
3
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5684 | SharckHack.exe | C:\Windows\System 32 | — | |
MD5:— | SHA256:— | |||
| 2064 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_MSBuild.exe_479535bad843f75b4b54569e4ccd3fe83ad1d2_b901be97_2cbf1861-80ce-4575-a591-6bf5d1d3ba05\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2064 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\MSBuild.exe.2580.dmp | — | |
MD5:— | SHA256:— | |||
| 5168 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_MSBuild.exe_479535bad843f75b4b54569e4ccd3fe83ad1d2_b901be97_79f61e55-8239-4089-a7ec-28480b0ed9c1\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5168 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\MSBuild.exe.4024.dmp | — | |
MD5:— | SHA256:— | |||
| 2348 | SharckHack.exe | C:\Users\admin\AppData\Local\Temp\SharkHack.exe | executable | |
MD5:F5543DC8E02BF550DFD023BDC1FE25EF | SHA256:6D71F28DD1791115BA74298B362A6930DCFB08425A088213DB4CF2D293FD8D84 | |||
| 5684 | SharckHack.exe | C:\Windows\xdwd.dll | executable | |
MD5:16E5A492C9C6AE34C59683BE9C51FA31 | SHA256:35C8D022E1D917F1AABDCEAE98097CCC072161B302F84C768CA63E4B32AC2B66 | |||
| 2064 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER647F.tmp.xml | xml | |
MD5:5AD812AEC37D75539D1C9126EE0EF8D5 | SHA256:F6ECCCAA2DB864922CE3B2A3579931AAAE3C105218658BCB4128B50E5745ABD1 | |||
| 2348 | SharckHack.exe | C:\Users\admin\AppData\Local\Temp\SharckHack.exe | executable | |
MD5:CDA8360793FA762650CBB6B894525CC4 | SHA256:F68BD4A95D509F5B159A503007D9AE0364E39E10930D95071259485621C8AE72 | |||
| 2064 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:0F7B8F6A846AA9CA52FA562DDDCDB5ED | SHA256:AFF90E65A81289B80D1FCC5E71B3D88E5D1AAFE22CE358EB6E28A56D1845263D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
72
DNS requests
40
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.38:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6540 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1560 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1560 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2064 | WerFault.exe | GET | 200 | 23.216.77.16:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 104.76.201.34:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2064 | WerFault.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4228 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.38:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5328 | SearchApp.exe | 92.123.104.59:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5328 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |