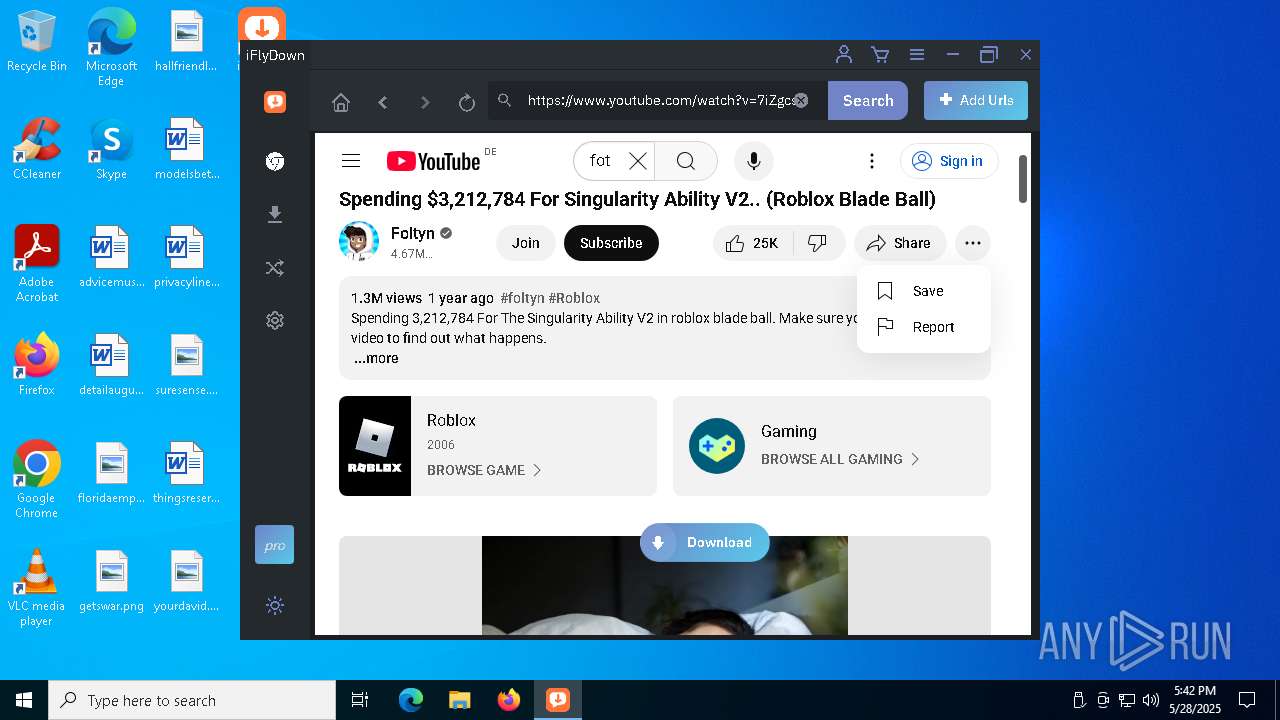
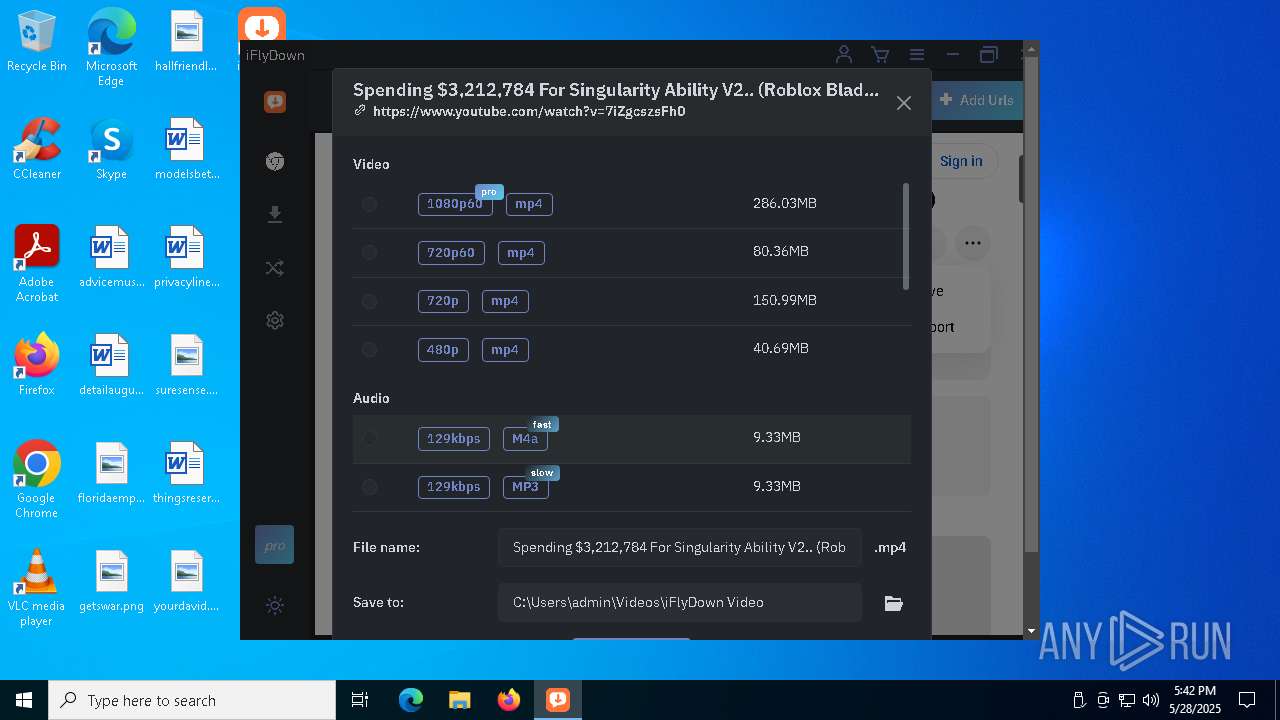
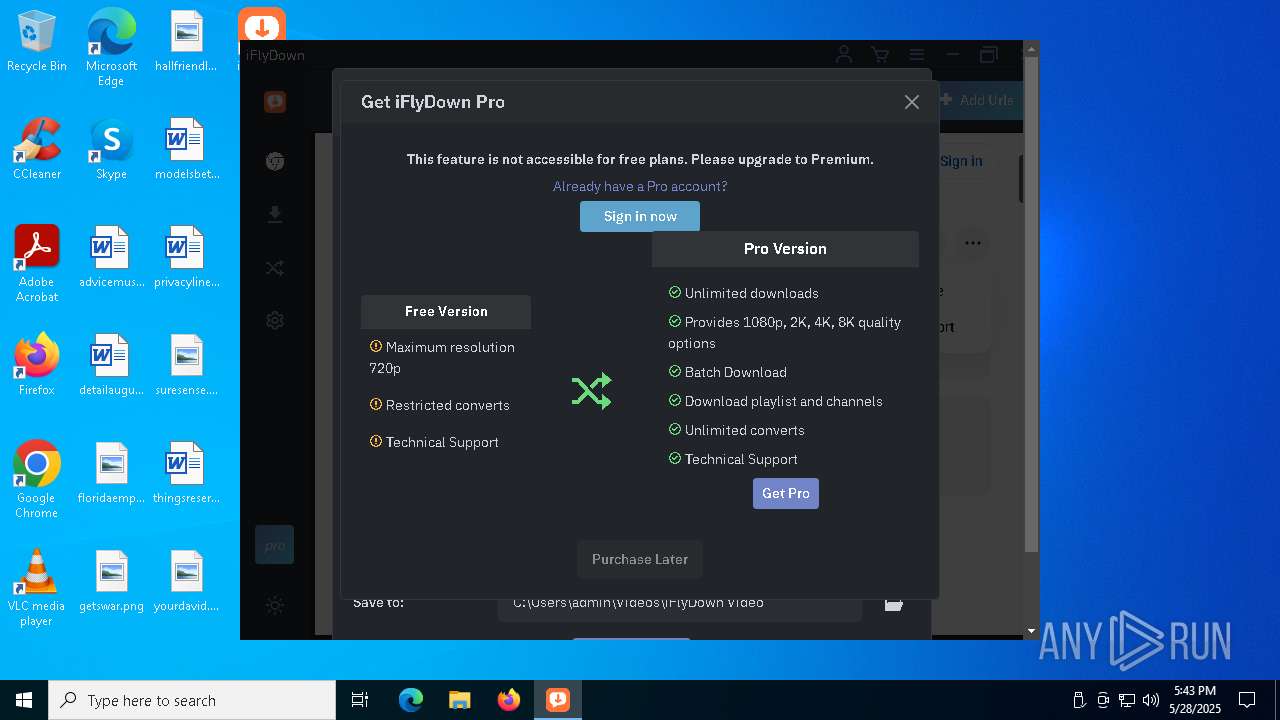
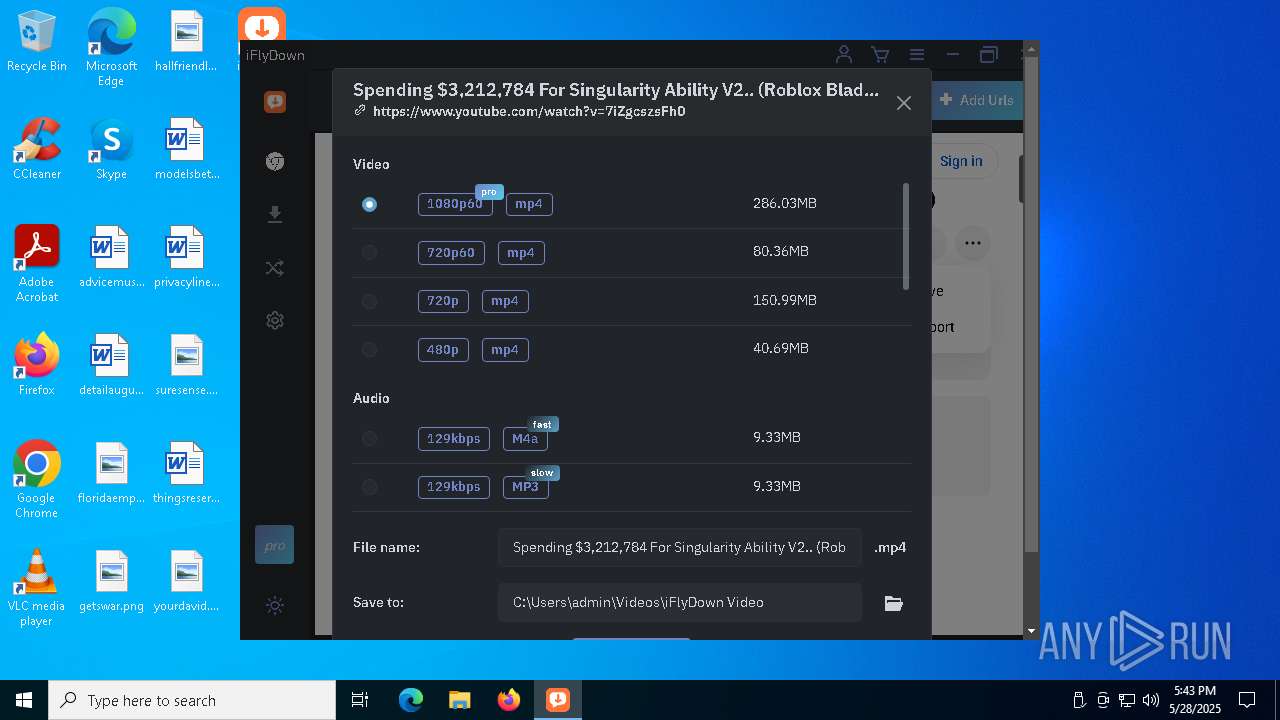
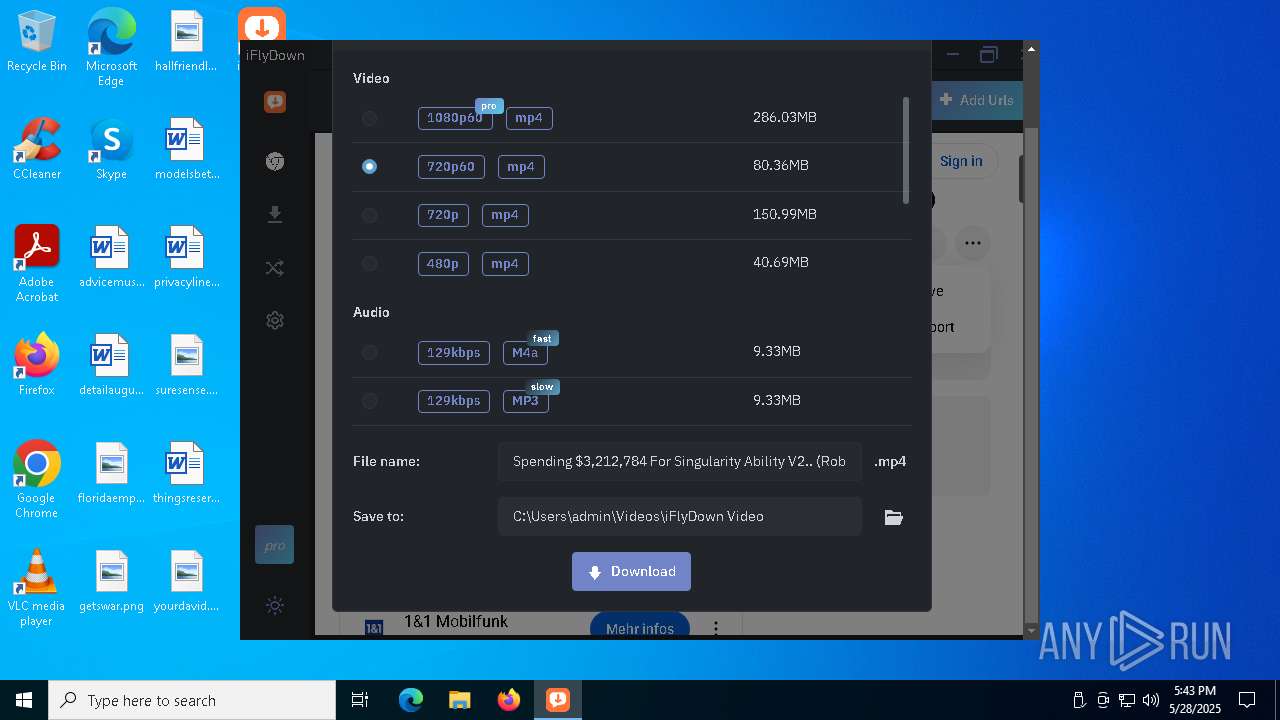
| File name: | iFlyDownInstall_v11.10.12.exe |
| Full analysis: | https://app.any.run/tasks/06000c1a-ae7e-48ca-a71a-bbce048bcc5e |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2025, 17:41:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | DBC36095482AE57901A8A33D75E81D7B |
| SHA1: | 35EB5069E8E31091B2C5FFBEFC1197F0430A1148 |
| SHA256: | 440E528ABC0726E2AF65CE8FE1B6A38B0E08DB0A949A92ECFF9561D9137DF107 |
| SSDEEP: | 49152:V54CAufXBXqB7zXCBmkjT+JtqynAO6ZCmSxbv0kFgQ0Qh1lhUqxg0AShC6gWg/wy:V54C9XBa5XCBmHtqyAO6smSlvMQ0QrTK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
The process creates files with name similar to system file names
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
There is functionality for taking screenshot (YARA)
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Drops 7-zip archiver for unpacking
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Executable content was dropped or overwritten
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Process drops python dynamic module
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Process drops legitimate windows executable
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Creates a software uninstall entry
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Application launched itself
- iFlyDown.exe (PID: 5984)
The process drops C-runtime libraries
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Starts application with an unusual extension
- cmd.exe (PID: 5624)
- cmd.exe (PID: 3872)
Starts CMD.EXE for commands execution
- iFlyDown.exe (PID: 5428)
- yt-dlp.exe (PID: 7252)
- yt-dlp.exe (PID: 7504)
INFO
Checks supported languages
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
- iFlyDown.exe (PID: 3332)
- iFlyDown.exe (PID: 6592)
- iFlyDown.exe (PID: 5428)
- iFlyDown.exe (PID: 5984)
- iFlyDown.exe (PID: 6540)
- chcp.com (PID: 4000)
- chcp.com (PID: 6108)
- iFlyDown.exe (PID: 2852)
- iFlyDown.exe (PID: 776)
Create files in a temporary directory
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
- iFlyDown.exe (PID: 5984)
The sample compiled with english language support
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Reads the computer name
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
- iFlyDown.exe (PID: 5984)
- iFlyDown.exe (PID: 6592)
- iFlyDown.exe (PID: 3332)
The sample compiled with chinese language support
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Creates files in the program directory
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Reads the software policy settings
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
UPX packer has been detected
- iFlyDownInstall_v11.10.12.exe (PID: 4272)
Manual execution by a user
- iFlyDown.exe (PID: 5984)
Creates files or folders in the user directory
- iFlyDown.exe (PID: 6540)
- iFlyDown.exe (PID: 5984)
- iFlyDown.exe (PID: 6592)
Checks proxy server information
- iFlyDown.exe (PID: 5984)
Reads the machine GUID from the registry
- iFlyDown.exe (PID: 5984)
Reads Environment values
- iFlyDown.exe (PID: 5984)
- iFlyDown.exe (PID: 5428)
Reads product name
- iFlyDown.exe (PID: 5984)
- iFlyDown.exe (PID: 5428)
Process checks computer location settings
- iFlyDown.exe (PID: 5984)
- iFlyDown.exe (PID: 2852)
- iFlyDown.exe (PID: 776)
- iFlyDown.exe (PID: 5428)
Changes the display of characters in the console
- cmd.exe (PID: 3872)
- cmd.exe (PID: 5624)
Checks operating system version
- yt-dlp.exe (PID: 7252)
- yt-dlp.exe (PID: 7504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:11:22 09:54:59+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 28672 |
| InitializedDataSize: | 186368 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3a0b |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.10.12.0 |
| ProductVersionNumber: | 11.10.12.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | iFly Co. |
| FileDescription: | iFlyDown |
| FileVersion: | 11.10.12.0 |
| InternalName: | iFlyDown.exe |
| LegalCopyright: | iFly Co. Copyright(c)2024 |
| ProductName: | iFlyDown |
| ProductVersion: | 11.10.12.0 |
Total processes
166
Monitored processes
33
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Program Files\iFlyDown\iFlyDown.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\iFlyDown" --standard-schemes --secure-schemes=sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=sentry-ipc --service-worker-schemes --streaming-schemes --app-user-model-id=iFlyDown --app-path="C:\Program Files\iFlyDown\resources\app.asar" --enable-sandbox --enable-blink-features --disable-blink-features --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3444 --field-trial-handle=1876,i,7934621786731338565,17451813127757278676,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Program Files\iFlyDown\iFlyDown.exe | — | iFlyDown.exe | |||||||||||
User: admin Company: iFlyDown Integrity Level: LOW Description: iFlyDown Exit code: 0 Version: 11.10.12 Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | "C:\Program Files\iFlyDown\iFlyDown.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\iFlyDown" --standard-schemes --secure-schemes=sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=sentry-ipc --service-worker-schemes --streaming-schemes --app-user-model-id=iFlyDown --app-path="C:\Program Files\iFlyDown\resources\app.asar" --enable-sandbox --enable-blink-features --disable-blink-features --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=4392 --field-trial-handle=1876,i,7934621786731338565,17451813127757278676,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Program Files\iFlyDown\iFlyDown.exe | — | iFlyDown.exe | |||||||||||
User: admin Company: iFlyDown Integrity Level: LOW Description: iFlyDown Version: 11.10.12 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\iFlyDown\iFlyDown.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\iFlyDown" --standard-schemes --secure-schemes=sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=sentry-ipc --service-worker-schemes --streaming-schemes --app-user-model-id=iFlyDown --app-path="C:\Program Files\iFlyDown\resources\app.asar" --enable-sandbox --enable-blink-features --disable-blink-features --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3300 --field-trial-handle=1876,i,7934621786731338565,17451813127757278676,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand /prefetch:1 | C:\Program Files\iFlyDown\iFlyDown.exe | — | iFlyDown.exe | |||||||||||
User: admin Company: iFlyDown Integrity Level: LOW Description: iFlyDown Exit code: 0 Version: 11.10.12 Modules
| |||||||||||||||
| 2984 | "C:\Program Files\iFlyDown\iFlyDown.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --user-data-dir="C:\Users\admin\AppData\Roaming\iFlyDown" --standard-schemes --secure-schemes=sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=sentry-ipc --service-worker-schemes --streaming-schemes --mojo-platform-channel-handle=3488 --field-trial-handle=1876,i,7934621786731338565,17451813127757278676,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\Program Files\iFlyDown\iFlyDown.exe | — | iFlyDown.exe | |||||||||||
User: admin Company: iFlyDown Integrity Level: LOW Description: iFlyDown Version: 11.10.12 Modules
| |||||||||||||||
| 3332 | "C:\Program Files\iFlyDown\iFlyDown.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\iFlyDown" --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1872 --field-trial-handle=1876,i,7934621786731338565,17451813127757278676,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand /prefetch:2 | C:\Program Files\iFlyDown\iFlyDown.exe | — | iFlyDown.exe | |||||||||||
User: admin Company: iFlyDown Integrity Level: LOW Description: iFlyDown Version: 11.10.12 Modules
| |||||||||||||||
| 3872 | C:\WINDOWS\system32\cmd.exe /d /s /c "chcp" | C:\Windows\System32\cmd.exe | — | iFlyDown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4000 | chcp | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4016 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 344
Read events
5 315
Write events
10
Delete events
19
Modification events
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\iFlyDown |
| Operation: | write | Name: | shortcut |
Value: true | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | iFlyDown |
Value: | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\iFlyDown |
| Operation: | write | Name: | autorun |
Value: false | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\iFlyDown |
| Operation: | write | Name: | InstPath |
Value: C:\Program Files\iFlyDown | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\iFlyDown |
| Operation: | write | Name: | LanguageID |
Value: 1033 | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\iFlyDown |
| Operation: | write | Name: | DisplayName |
Value: iFlyDown | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\iFlyDown |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\iFlyDown\uninst.exe | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\iFlyDown |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\iFlyDown\iFlyDown.exe | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\iFlyDown |
| Operation: | write | Name: | Publisher |
Value: iFly Co. | |||
| (PID) Process: | (4272) iFlyDownInstall_v11.10.12.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\iFlyDown |
| Operation: | write | Name: | DisplayVersion |
Value: 11.10.12.0 | |||
Executable files
131
Suspicious files
309
Text files
60
Unknown types
86
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Program Files\iFlyDown\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Program Files\iFlyDown\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Users\admin\AppData\Local\Temp\nskAA2D.tmp\licence_1033.rtf | text | |
MD5:DBD8F2D2E6F2E2420D20356721D7F55E | SHA256:B7DCF071EE0C993497679A8B091196CA7E3763BA265CA15789BAD4BE2ADDEC5E | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Users\admin\AppData\Local\Temp\nskAA2D.tmp\BgWorker.dll | executable | |
MD5:33EC04738007E665059CF40BC0F0C22B | SHA256:50F735AB8F3473423E6873D628150BBC0777BE7B4F6405247CDDF22BB00FB6BE | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Users\admin\AppData\Local\Temp\nskAA2D.tmp\System.dll | executable | |
MD5:E38D8FF9F749EE1B141A122FEC7280E0 | SHA256:00F7604D4F36A728C7759F4D9CF3E30C9728C503557AAC49BBCD55CFC3E4FCB4 | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Program Files\iFlyDown\app.7z | compressed | |
MD5:378D02DAABF0D9FFCCA257C2A33B5483 | SHA256:C0CB9C8EB2AC2C7F4A9EC1053B3A099ED7ABCE28920A27BFCCB781F64742EC14 | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Users\admin\AppData\Local\Temp\nskAA2D.tmp\licence_2052.rtf | text | |
MD5:DBD8F2D2E6F2E2420D20356721D7F55E | SHA256:B7DCF071EE0C993497679A8B091196CA7E3763BA265CA15789BAD4BE2ADDEC5E | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Program Files\iFlyDown\locales\af.pak | pgc | |
MD5:917A688D64ECCF67FEF5A5EB0908B6D4 | SHA256:6981249837AD767FC030EDC8838878A5E493FB08CC49982CFFAED16CFBEB564D | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Users\admin\AppData\Local\Temp\nskAA2D.tmp\logo.ico | image | |
MD5:3697FC83423BC493861DE4074110733B | SHA256:9D081B9E2A1F5DD21B96A2DB5263725B9B17AD281CC87374649FC94C1E97012D | |||
| 4272 | iFlyDownInstall_v11.10.12.exe | C:\Users\admin\AppData\Local\Temp\nskAA2D.tmp\skin.zip | compressed | |
MD5:ED4162A255C10390F307EC2A31E94B8A | SHA256:386403A8036AAEBEB490AD3CB4D60F9749B233EF0C8B7193BB61FE7243A7E0BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
78
DNS requests
76
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2136 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2136 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5796 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1020 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
apk.iflydown.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6592 | iFlyDown.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6592 | iFlyDown.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |