| File name: | 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe |
| Full analysis: | https://app.any.run/tasks/d01378d2-e9a1-4cc9-9d04-95f44d0c28e0 |
| Verdict: | Malicious activity |
| Analysis date: | October 03, 2024, 13:18:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 732E5334CD83CDA54FAE059C26F30B9C |
| SHA1: | A5E5E32568548BD6AC59CD6370855109ACD5E3E2 |
| SHA256: | 44079FA5E464F78AF652B066EBDFD5AFAE69018F0ED079EDFE25ADA693CA6C1A |
| SSDEEP: | 98304:BRc7ovDV00m1FtpyJGB7yC7F3rh5k07frEIDPAY/Nu9V9jdJgIwT2bAPn3wsJBjy:ejvjgfZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
Reads the BIOS version
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 2924)
Checks Windows Trust Settings
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
Starts CMD.EXE for commands execution
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
INFO
Checks supported languages
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
Themida protector has been detected
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
Process checks computer location settings
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
Reads the computer name
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
The process uses the downloaded file
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
Reads the machine GUID from the registry
- 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe (PID: 2648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2089:11:27 21:37:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 50176 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x978058 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Fiery LLC |
| FileDescription: | LogCapture |
| FileVersion: | 1.0.0.0 |
| InternalName: | LogCapture.exe |
| LegalCopyright: | Copyright © 2024 Fiery LLC |
| LegalTrademarks: | Fiery Driven® |
| OriginalFileName: | LogCapture.exe |
| ProductName: | LogCapture |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
140
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1256 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
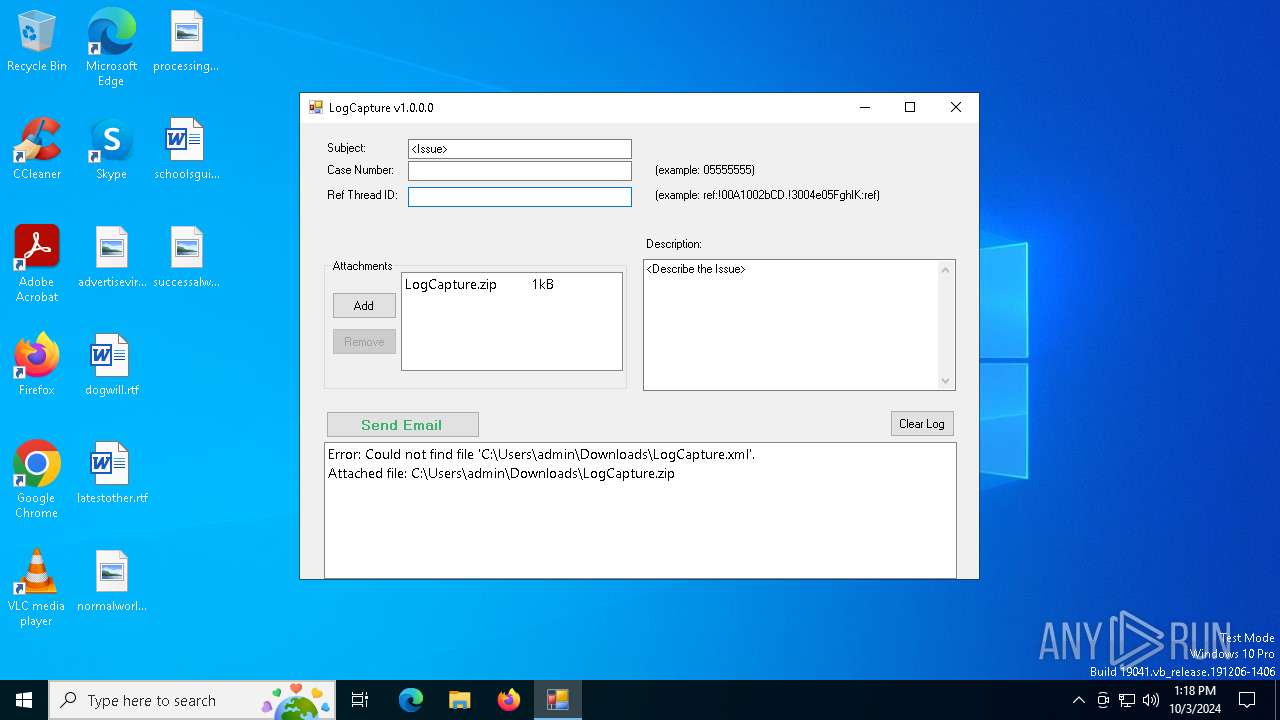
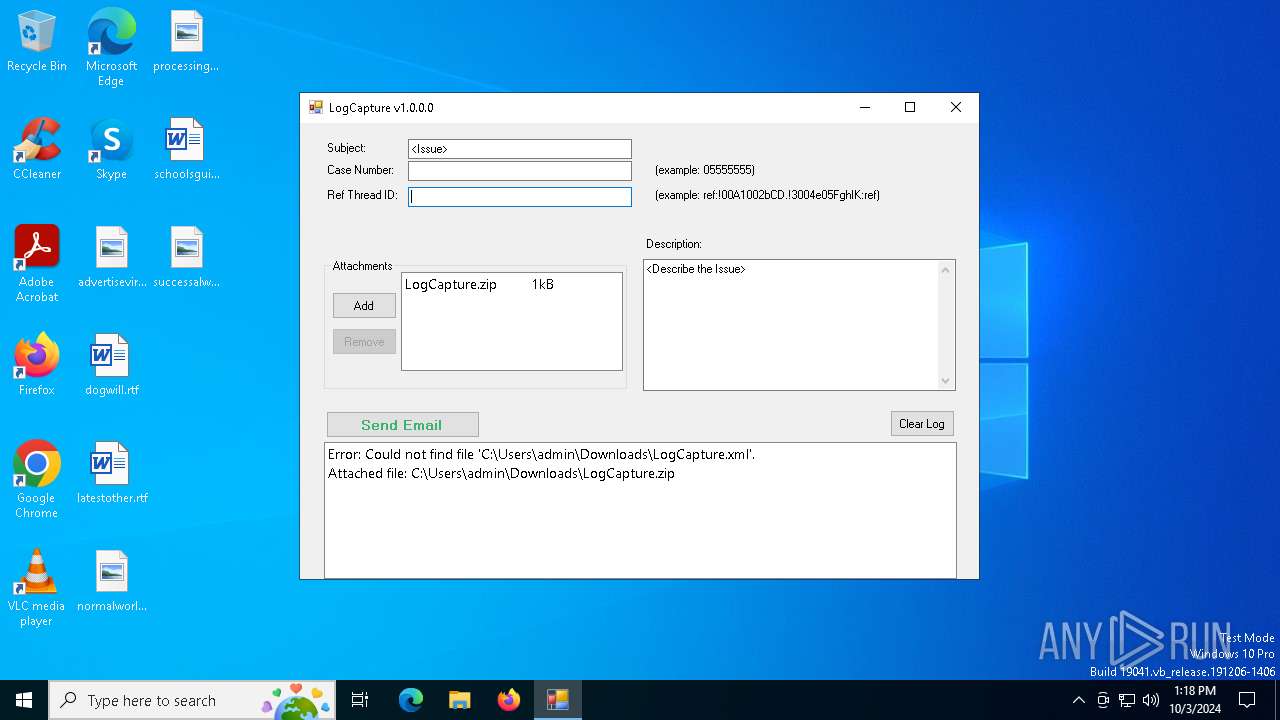
| 2648 | "C:\Users\admin\Downloads\23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe" | C:\Users\admin\Downloads\23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe | explorer.exe | ||||||||||||
User: admin Company: Fiery LLC Integrity Level: MEDIUM Description: LogCapture Version: 1.0.0.0 Modules
| |||||||||||||||
| 2924 | "C:\Windows\System32\cmd.exe" /C systeminfo > "C:\Users\admin\Downloads\Temp\SystemInfo.txt" | C:\Windows\SysWOW64\cmd.exe | — | 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4600 | systeminfo | C:\Windows\SysWOW64\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6416 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 449
Read events
5 447
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6416) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31135126 | |||
| (PID) Process: | (6416) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
Executable files
0
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2648 | 23348_216533479_44079fa5e464f78af652b066ebdfd5afae69018f0ed079edfe25ada693ca6c1a_logcapture.exe | C:\Users\admin\Downloads\LogCapture.zip | compressed | |
MD5:E240DFB4826866B1C52CD4304B7D9DFA | SHA256:8F8782274D788794EFBD3B062AEA26EBE5370B77B6F5CB52408703DE90ED1B81 | |||
| 2924 | cmd.exe | C:\Users\admin\Downloads\Temp\SystemInfo.txt | text | |
MD5:2E67E72FEEBF965F3E1EB057E9323939 | SHA256:567667E2235F3BADE470C7484E5E25BE00CB6DCA193DBF47FEC74D8311AB7AF5 | |||
| 6416 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:E524951F9C674C038CFC81440DFE0EC7 | SHA256:6C94E39AE042DEDADCA2A92D9A4F6F5F5E196A030BB2550F18EC39B95D7DF447 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
58
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5500 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6972 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6972 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6336 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5996 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |