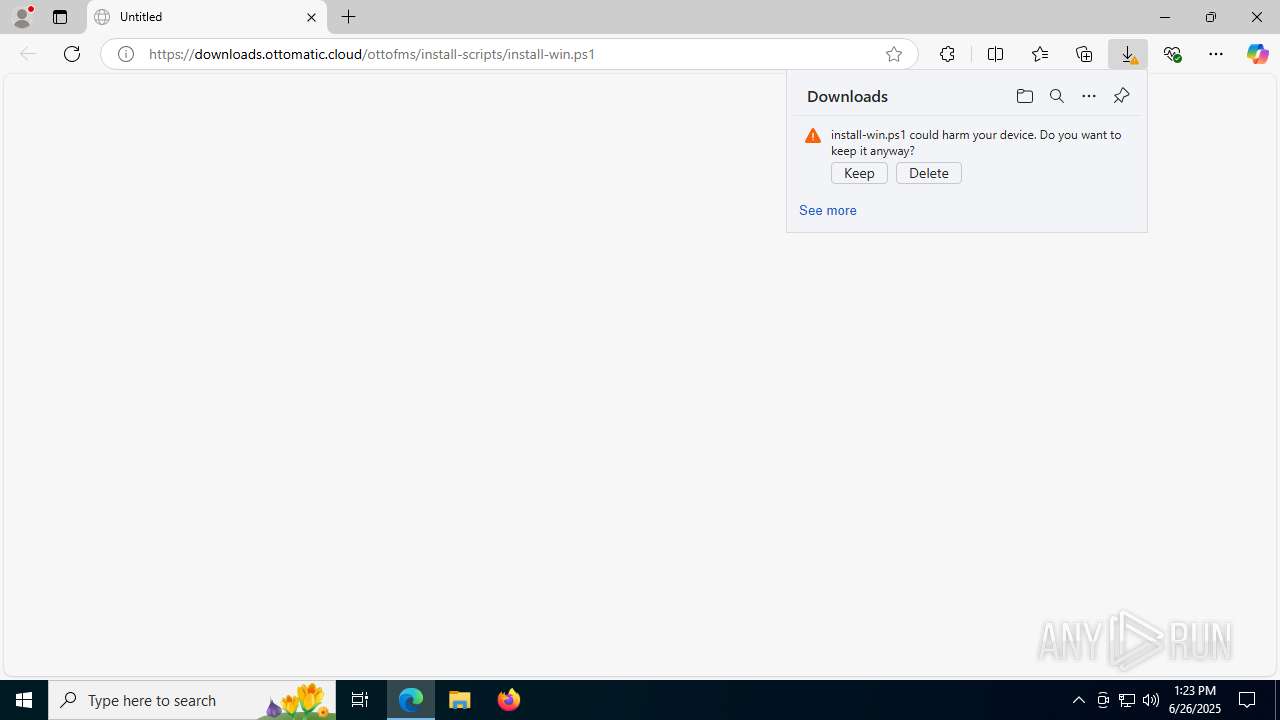
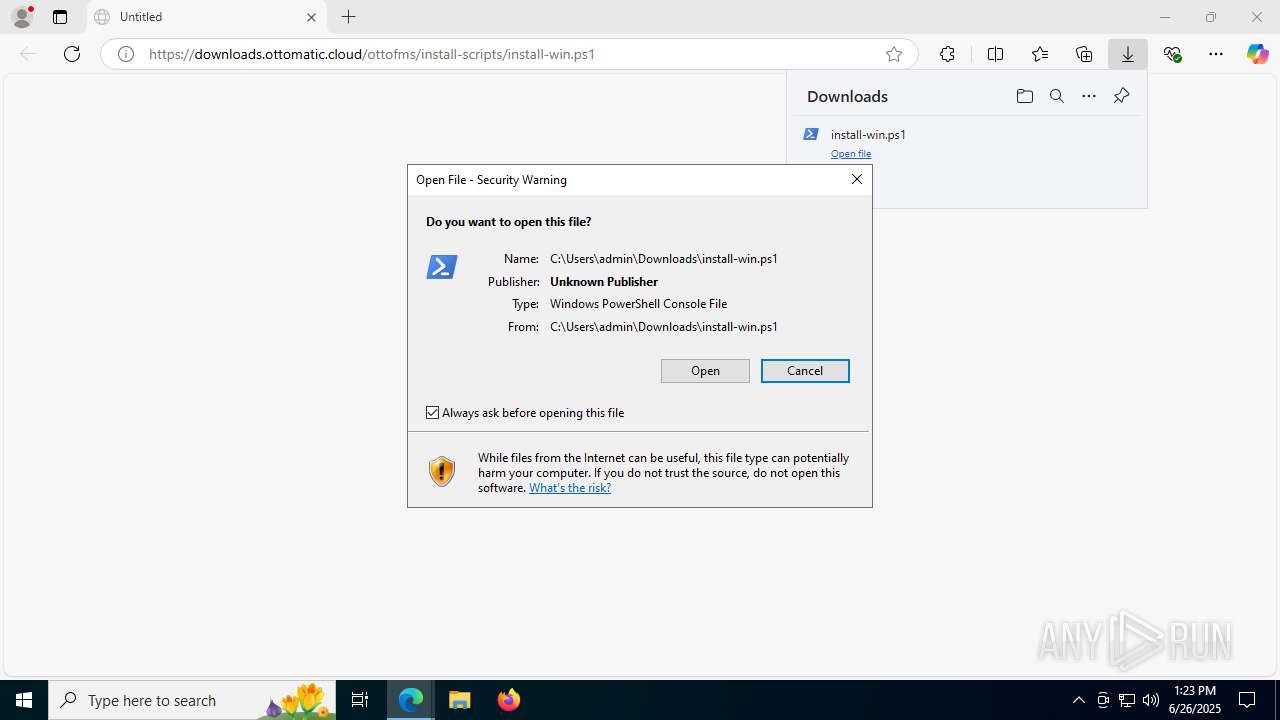
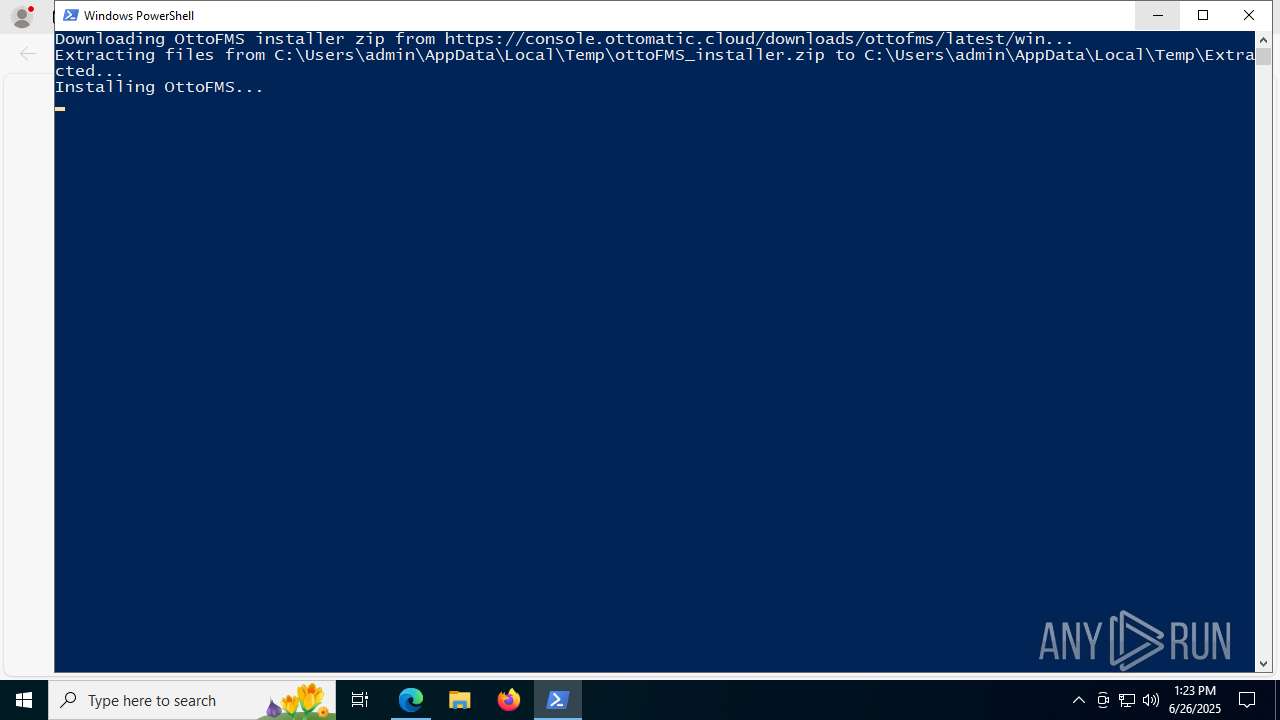
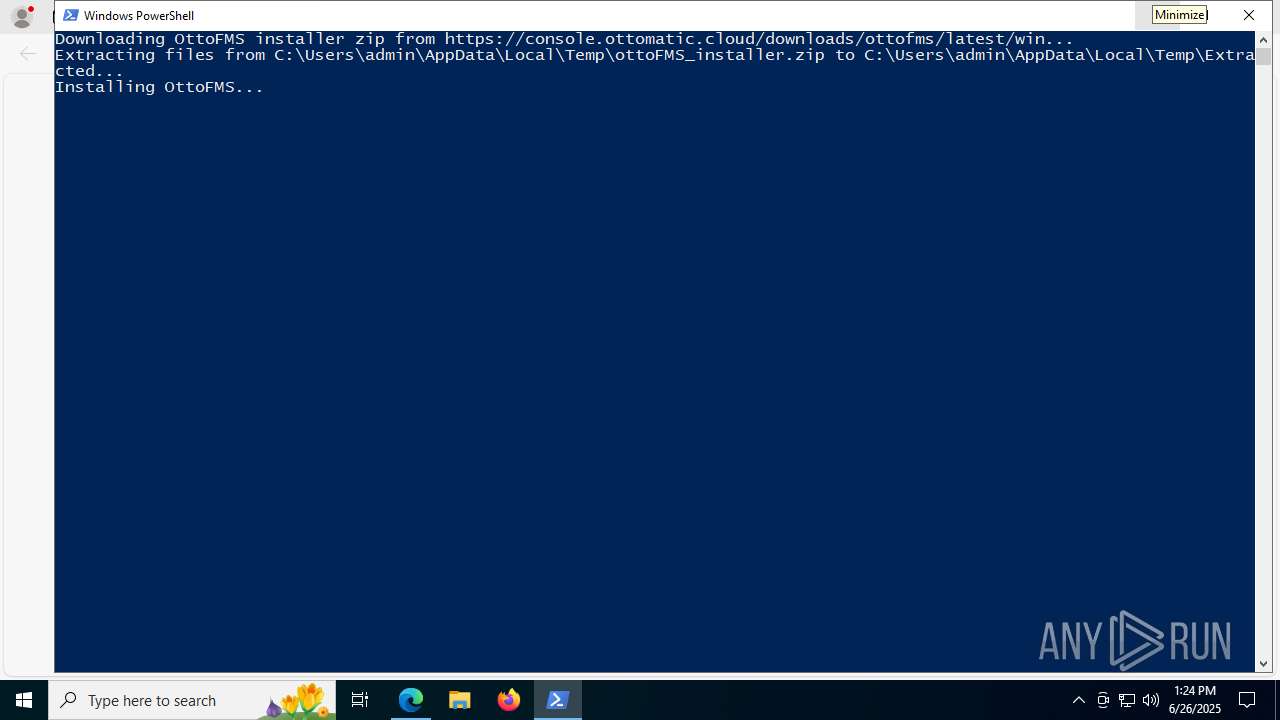
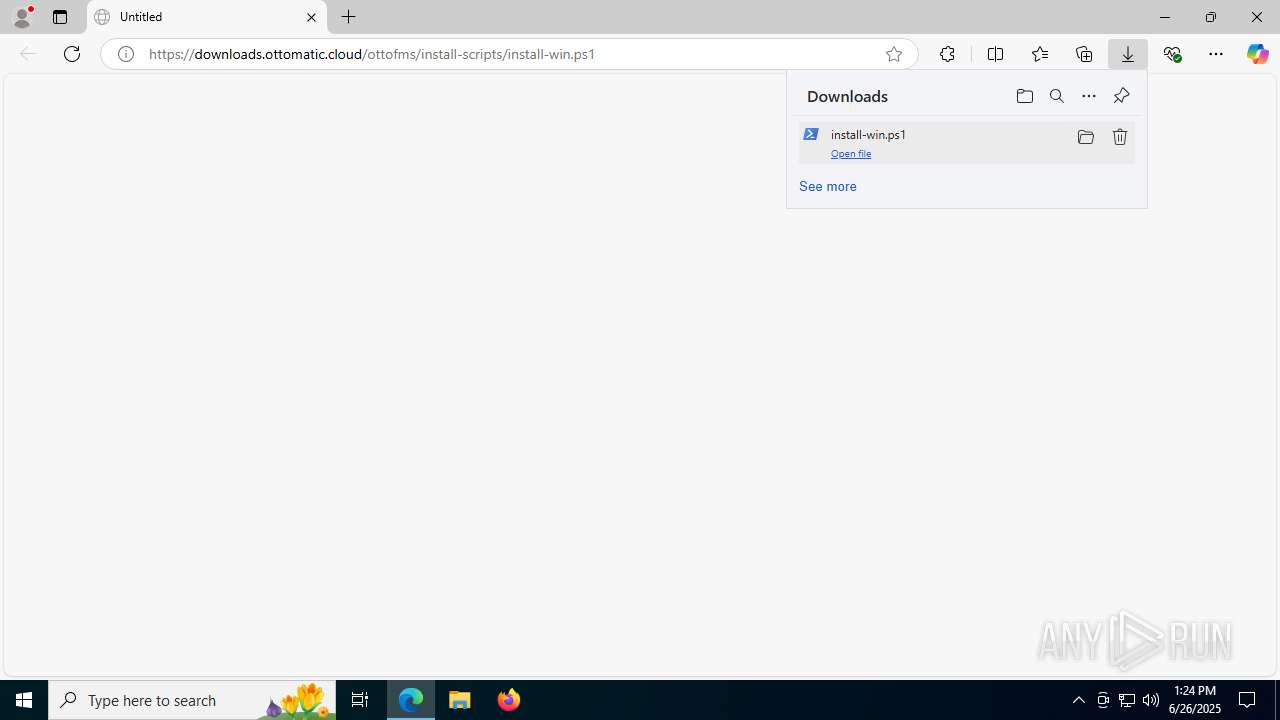
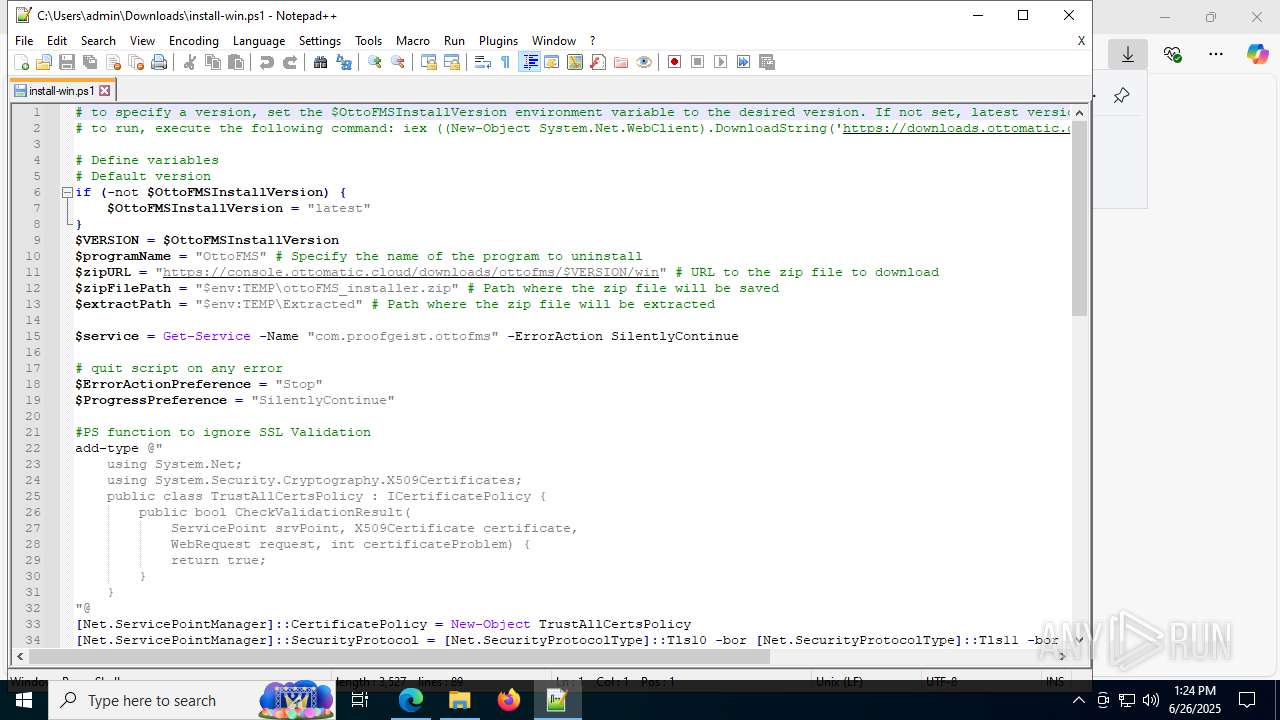
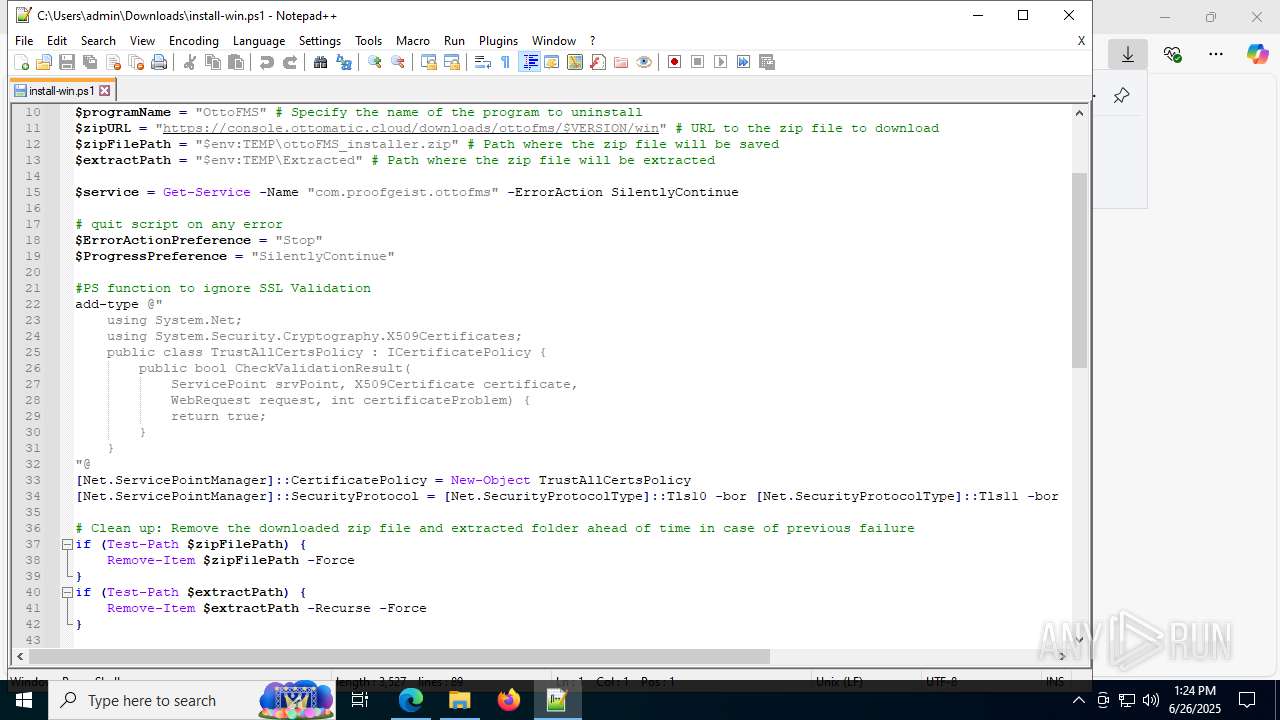
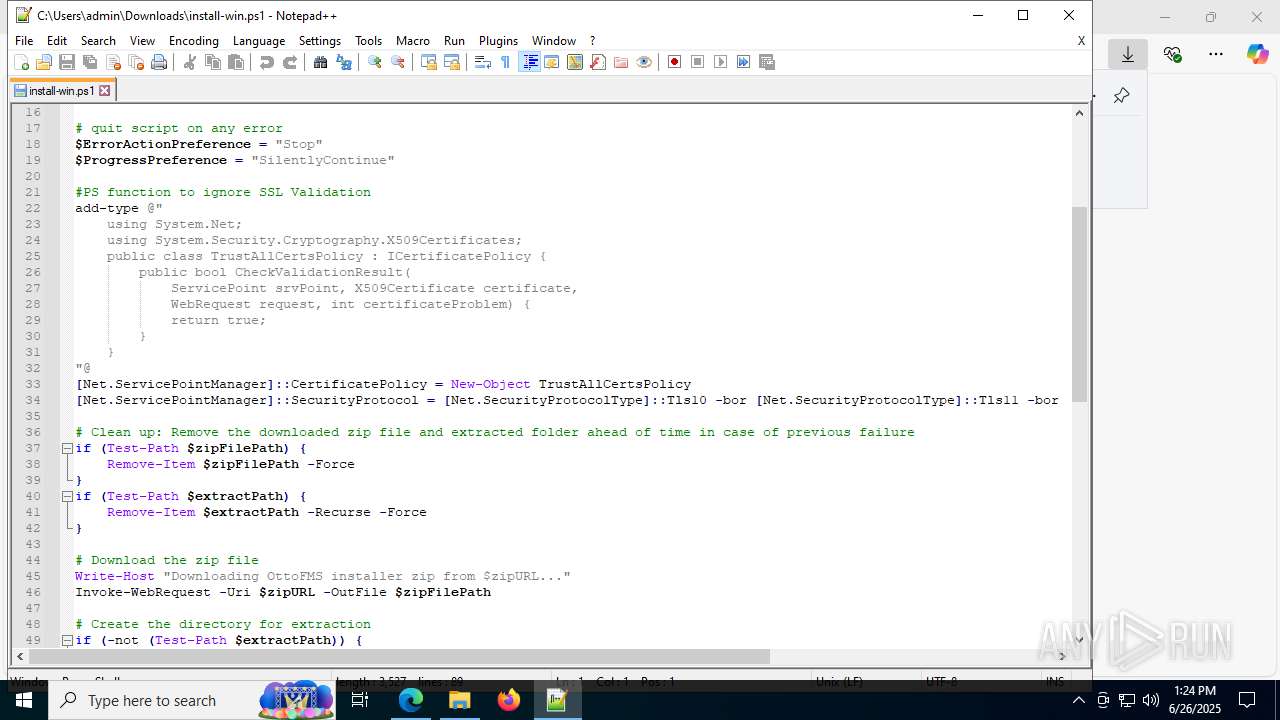
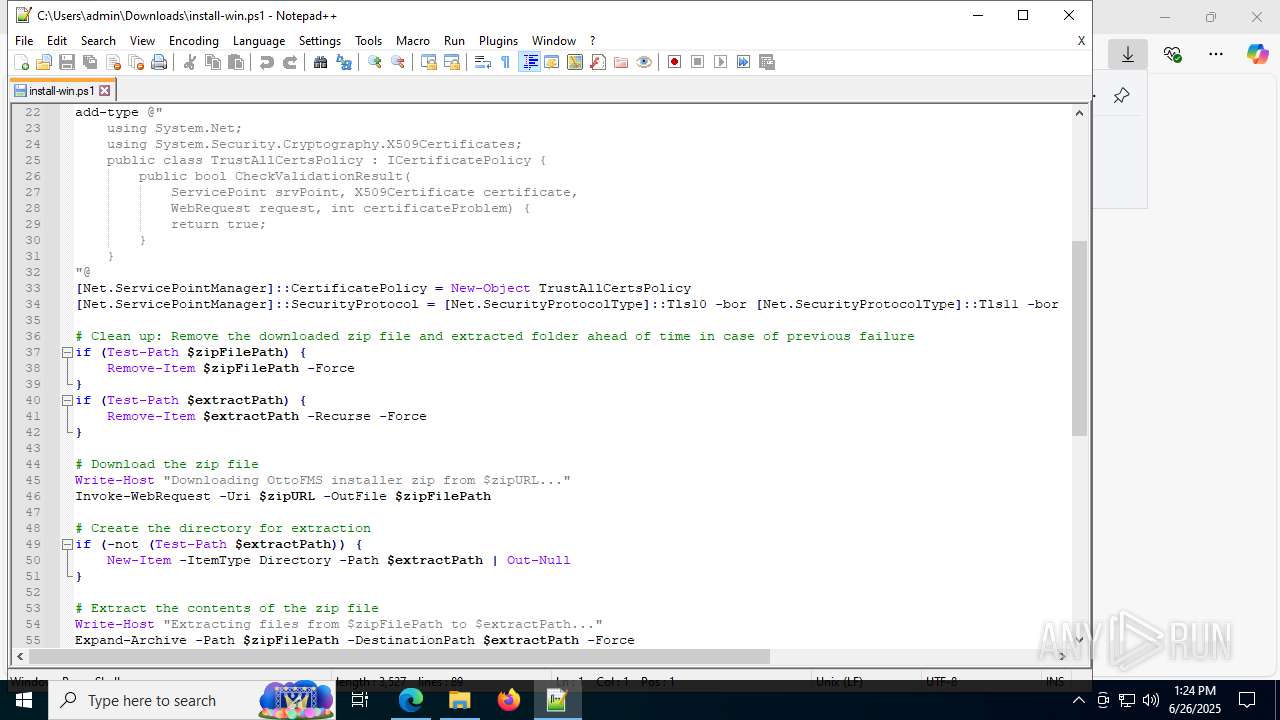
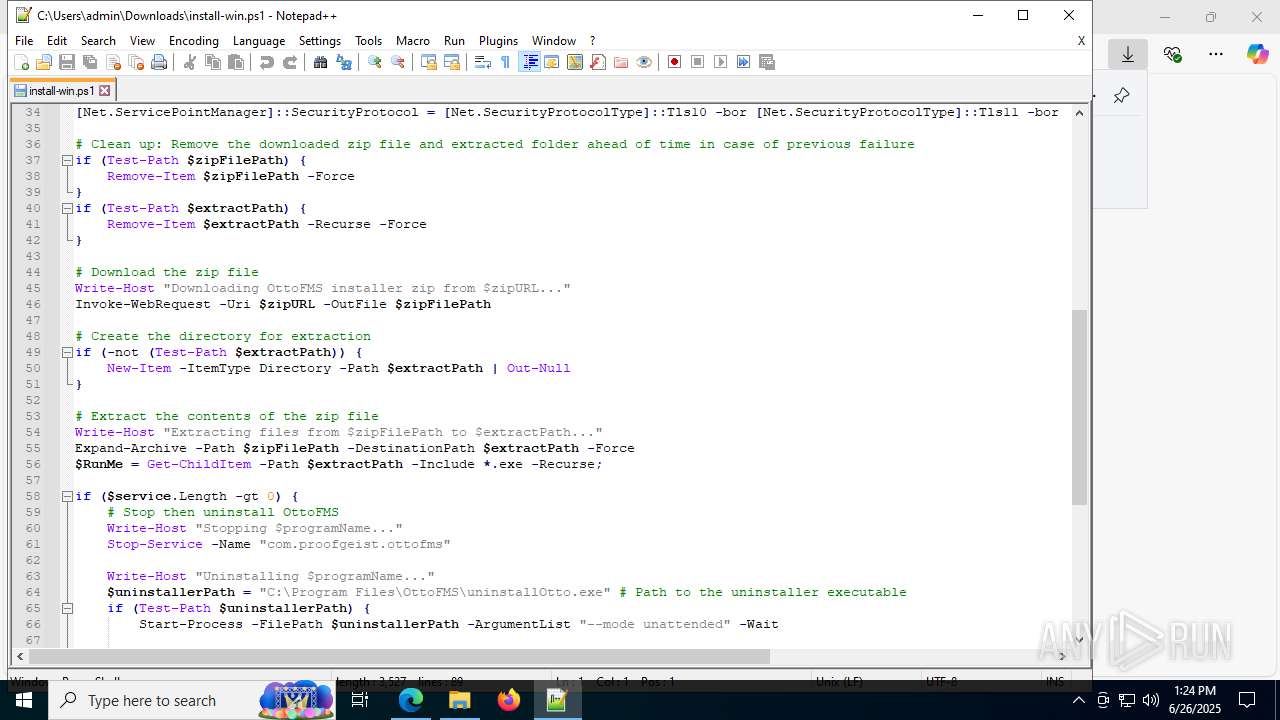
| URL: | https://downloads.ottomatic.cloud/ottofms/install-scripts/install-win.ps1 |
| Full analysis: | https://app.any.run/tasks/6687322f-0c25-44d0-8cd4-a406f8c456c2 |
| Verdict: | Malicious activity |
| Analysis date: | June 26, 2025, 13:23:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 7D62326AA25FE8B46988948817B138EC |
| SHA1: | 8E004D14CADCC3F9AC15FBACC2098BAA31E2BC33 |
| SHA256: | 43FF5B3DD60976E70F074FE1342B195497FA52B3DDA2A26D2A6959F154F6A482 |
| SSDEEP: | 3:N8SE4LKI9aLJeLVGW7MGSAT:2S3nGeMG1 |
MALICIOUS
Starts POWERSHELL.EXE for commands execution
- msedge.exe (PID: 4968)
Changes powershell execution policy (Bypass)
- msedge.exe (PID: 4968)
Bypass execution policy to execute commands
- powershell.exe (PID: 8100)
Executing a file with an untrusted certificate
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 4444)
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
SUSPICIOUS
The process executes Powershell scripts
- msedge.exe (PID: 4968)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7404)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 8100)
Executable content was dropped or overwritten
- csc.exe (PID: 7404)
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 8100)
Mutex name with non-standard characters
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
Executes as Windows Service
- nssm.exe (PID: 7292)
Starts CMD.EXE for commands execution
- ottofms-win-x64.exe (PID: 4916)
- ottofms-win-x64.exe (PID: 7768)
- ottofms-win-x64.exe (PID: 7872)
- ottofms-win-x64.exe (PID: 7700)
- ottofms-win-x64.exe (PID: 1524)
Creates a software uninstall entry
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
INFO
Application launched itself
- msedge.exe (PID: 4968)
Launching a file from the Downloads directory
- msedge.exe (PID: 4968)
Reads Environment values
- identity_helper.exe (PID: 7576)
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
- ottofms-win-x64.exe (PID: 4916)
- ottofms-win-x64.exe (PID: 7872)
- ottofms-win-x64.exe (PID: 7768)
- identity_helper.exe (PID: 5460)
- ottofms-win-x64.exe (PID: 7700)
- ottofms-win-x64.exe (PID: 1524)
Reads the computer name
- identity_helper.exe (PID: 7576)
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
- nssm.exe (PID: 7960)
- nssm.exe (PID: 6672)
- nssm.exe (PID: 4400)
- nssm.exe (PID: 7972)
- nssm.exe (PID: 868)
- nssm.exe (PID: 7388)
- nssm.exe (PID: 7292)
- nssm.exe (PID: 8040)
- identity_helper.exe (PID: 5460)
Reads Microsoft Office registry keys
- msedge.exe (PID: 4968)
Checks supported languages
- identity_helper.exe (PID: 7576)
- csc.exe (PID: 7404)
- cvtres.exe (PID: 7200)
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
- nssm.exe (PID: 7960)
- nssm.exe (PID: 8040)
- nssm.exe (PID: 7972)
- nssm.exe (PID: 4400)
- nssm.exe (PID: 6672)
- nssm.exe (PID: 868)
- nssm.exe (PID: 7388)
- ottofms-win-x64.exe (PID: 4916)
- nssm.exe (PID: 7292)
- ottofms-win-x64.exe (PID: 7872)
- ottofms-win-x64.exe (PID: 7768)
- identity_helper.exe (PID: 5460)
- ottofms-win-x64.exe (PID: 7700)
- ottofms-win-x64.exe (PID: 1524)
Reads the machine GUID from the registry
- csc.exe (PID: 7404)
Create files in a temporary directory
- csc.exe (PID: 7404)
- cvtres.exe (PID: 7200)
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
Checks proxy server information
- powershell.exe (PID: 8100)
Disables trace logs
- powershell.exe (PID: 8100)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 8100)
The executable file from the user directory is run by the Powershell process
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 4444)
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
The sample compiled with english language support
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
Process checks whether UAC notifications are on
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
Reads CPU info
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
Reads the time zone
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
Creates files in the program directory
- OttoFMS-4.11.0-windows-x64-installer.exe (PID: 7920)
- ottofms-win-x64.exe (PID: 4916)
- nssm.exe (PID: 7292)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 8100)
Reads product name
- ottofms-win-x64.exe (PID: 4916)
- ottofms-win-x64.exe (PID: 7768)
- ottofms-win-x64.exe (PID: 7700)
- ottofms-win-x64.exe (PID: 7872)
- ottofms-win-x64.exe (PID: 1524)
Manual execution by a user
- notepad++.exe (PID: 3196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
201
Monitored processes
61
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | "C:\PROGRA~1\OttoFMS\bin\nssm\nssm.exe" set com.proofgeist.ottofms Description "Provides OttoFMS API and Web Application" | C:\Program Files\OttoFMS\bin\nssm\nssm.exe | — | OttoFMS-4.11.0-windows-x64-installer.exe | |||||||||||
User: admin Integrity Level: HIGH Description: The non-sucking service manager Exit code: 0 Version: 2.24 Modules
| |||||||||||||||
| 1336 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3652,i,10363001235660546879,18207515699872708452,262144 --variations-seed-version --mojo-platform-channel-handle=3692 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1524 | "C:\Program Files/OttoFMS\bin\ottofms-win-x64.exe" | C:\Program Files\OttoFMS\bin\ottofms-win-x64.exe | — | nssm.exe | |||||||||||
User: SYSTEM Company: Node.js Integrity Level: SYSTEM Description: Node.js JavaScript Runtime Exit code: 1 Version: 20.18.2 Modules
| |||||||||||||||
| 1732 | C:\WINDOWS\system32\cmd.exe /d /s /c "where fmsadmin" | C:\Windows\System32\cmd.exe | — | ottofms-win-x64.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | nssm.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3196 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Downloads\install-win.ps1" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 3752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | nssm.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4160 | C:\WINDOWS\system32\cmd.exe /d /s /c "where fmsadmin" | C:\Windows\System32\cmd.exe | — | ottofms-win-x64.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | "C:\PROGRA~1\OttoFMS\bin\nssm\nssm.exe" set com.proofgeist.ottofms Start SERVICE_AUTO_START | C:\Program Files\OttoFMS\bin\nssm\nssm.exe | — | OttoFMS-4.11.0-windows-x64-installer.exe | |||||||||||
User: admin Integrity Level: HIGH Description: The non-sucking service manager Exit code: 0 Version: 2.24 Modules
| |||||||||||||||
| 4444 | "C:\Users\admin\AppData\Local\Temp\Extracted\OttoFMS-4.11.0-windows-x64-installer\OttoFMS-4.11.0-windows-x64-installer.exe" --mode unattended | C:\Users\admin\AppData\Local\Temp\Extracted\OttoFMS-4.11.0-windows-x64-installer\OttoFMS-4.11.0-windows-x64-installer.exe | — | powershell.exe | |||||||||||
User: admin Company: Proof+Geist Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
15 875
Read events
15 832
Write events
43
Delete events
0
Modification events
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B5BADFC00F972F00 | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {962C2CE0-3E7A-4F02-A967-CEF09D3FCAC0} | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6B2900D7-D102-43FF-9917-F76BE1818F07} | |||
| (PID) Process: | (4968) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2EBDFAC00F972F00 | |||
Executable files
18
Suspicious files
190
Text files
63
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF175a35.TMP | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF175a35.TMP | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF175a45.TMP | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF175a45.TMP | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF175a64.TMP | — | |
MD5:— | SHA256:— | |||
| 4968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
53
DNS requests
44
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7016 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:FtqY55ibBqmscNpoBHR0rbL-Ot0AYwBDP1JGYnXMGz4&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7200 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1200 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7200 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5172 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7016 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7016 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7016 | msedge.exe | 169.150.247.36:443 | downloads.ottomatic.cloud | — | GB | unknown |
7016 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7016 | msedge.exe | 92.123.104.53:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
downloads.ottomatic.cloud |
| unknown |
copilot.microsoft.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
www.bing.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
— | — | Potentially Bad Traffic | ET INFO Possible Chrome Plugin install |
— | — | Potentially Bad Traffic | ET HUNTING Generic Powershell DownloadString Command |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|