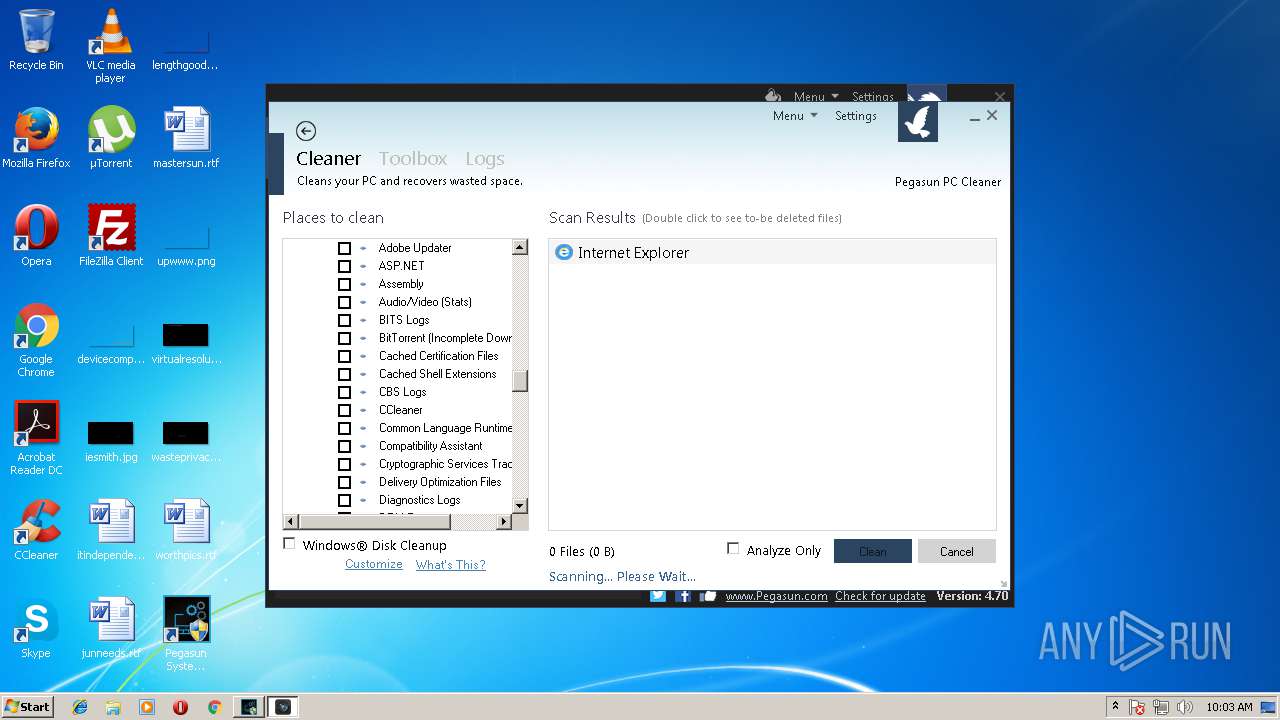
| download: | SystemUtilities.exe |
| Full analysis: | https://app.any.run/tasks/4c1d1871-9c44-47ce-9047-a7af1d8b75c5 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2018, 09:01:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 338B50A471EEDB1841A52BCE45016D7A |
| SHA1: | E3E570DC2988A66DA4640BB338D418D803F9417B |
| SHA256: | 43E7FAAD0E076BE3E508EAFE1C330D7840375609E2A5FF20B09579983D217AFC |
| SSDEEP: | 98304:C5EeFFQRni+odHXU3ZEE13W2x+m4TQ0uk5G774E1LcpKsSsmYbNyqhaQ:0aRnlz13Zx8TQpkK0EapKsSY9H |
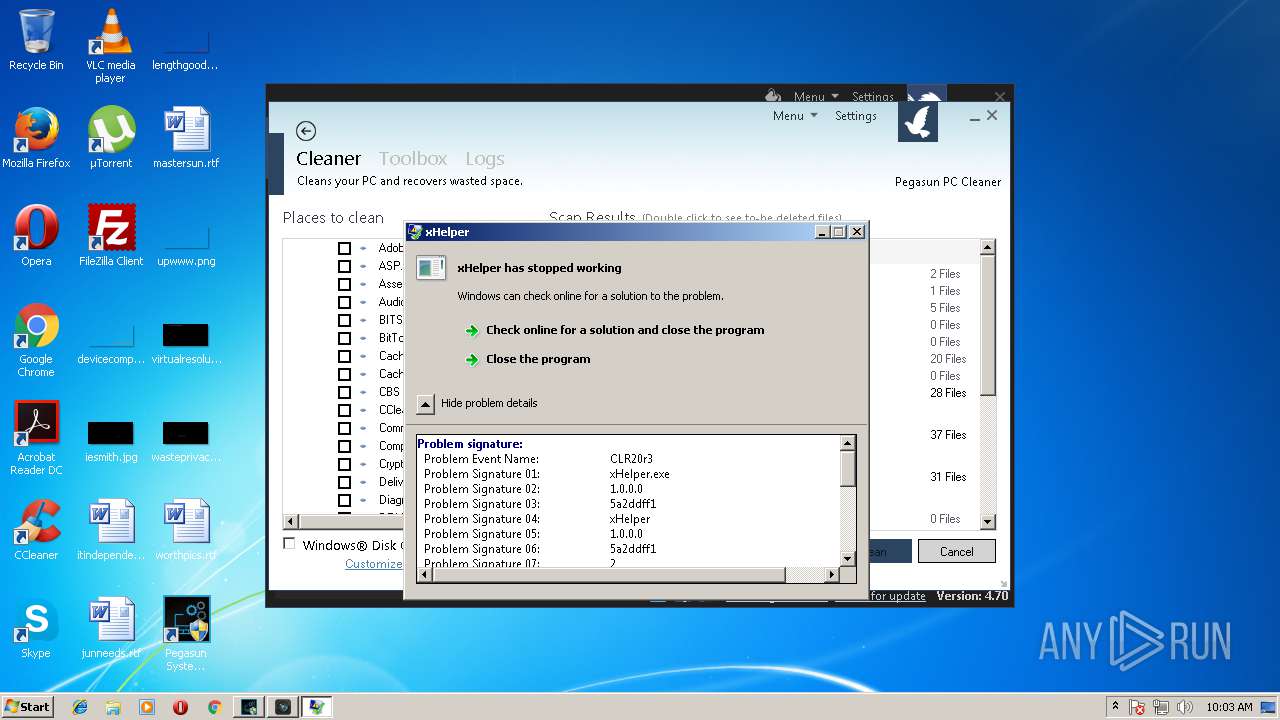
MALICIOUS
Application was dropped or rewritten from another process
- sHelper.exe (PID: 1476)
- SystemUtilities.exe (PID: 2852)
- SystemUtilities.exe (PID: 1540)
- PCCleaner.exe (PID: 3064)
- xHelper.exe (PID: 2764)
Loads dropped or rewritten executable
- sHelper.exe (PID: 1476)
Changes settings of System certificates
- sHelper.exe (PID: 1476)
SUSPICIOUS
Executable content was dropped or overwritten
- SystemUtilities.exe (PID: 2504)
- SystemUtilities.tmp (PID: 2952)
- SystemUtilities.exe (PID: 2240)
Creates files in the user directory
- SystemUtilities.exe (PID: 2852)
- sHelper.exe (PID: 1476)
- rundll32.exe (PID: 2212)
- rundll32.exe (PID: 3404)
Adds / modifies Windows certificates
- sHelper.exe (PID: 1476)
Writes to a desktop.ini file (may be used to cloak folders)
- PCCleaner.exe (PID: 3064)
- rundll32.exe (PID: 3404)
- rundll32.exe (PID: 2212)
Application launched itself
- software_reporter_tool.exe (PID: 2092)
Starts Internet Explorer
- rundll32.exe (PID: 2212)
Removes files from Windows directory
- PCCleaner.exe (PID: 3064)
INFO
Dropped object may contain URL's
- SystemUtilities.exe (PID: 2240)
- SystemUtilities.exe (PID: 2504)
- sHelper.exe (PID: 1476)
- SystemUtilities.tmp (PID: 2952)
- chrome.exe (PID: 3384)
- chrome.exe (PID: 1576)
Application was dropped or rewritten from another process
- SystemUtilities.tmp (PID: 2152)
- SystemUtilities.tmp (PID: 2952)
Creates files in the program directory
- SystemUtilities.tmp (PID: 2952)
Dropped object may contain Bitcoin addresses
- SystemUtilities.tmp (PID: 2952)
Creates a software uninstall entry
- SystemUtilities.tmp (PID: 2952)
Creates files in the user directory
- iexplore.exe (PID: 2660)
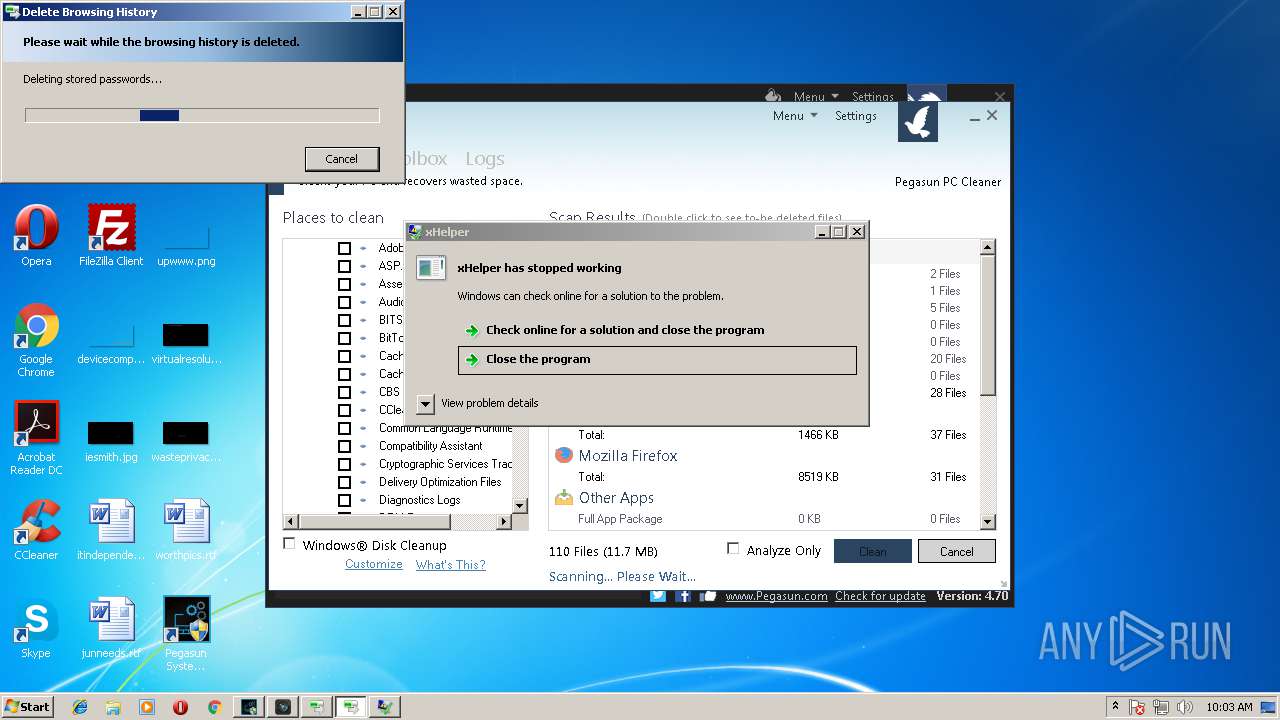
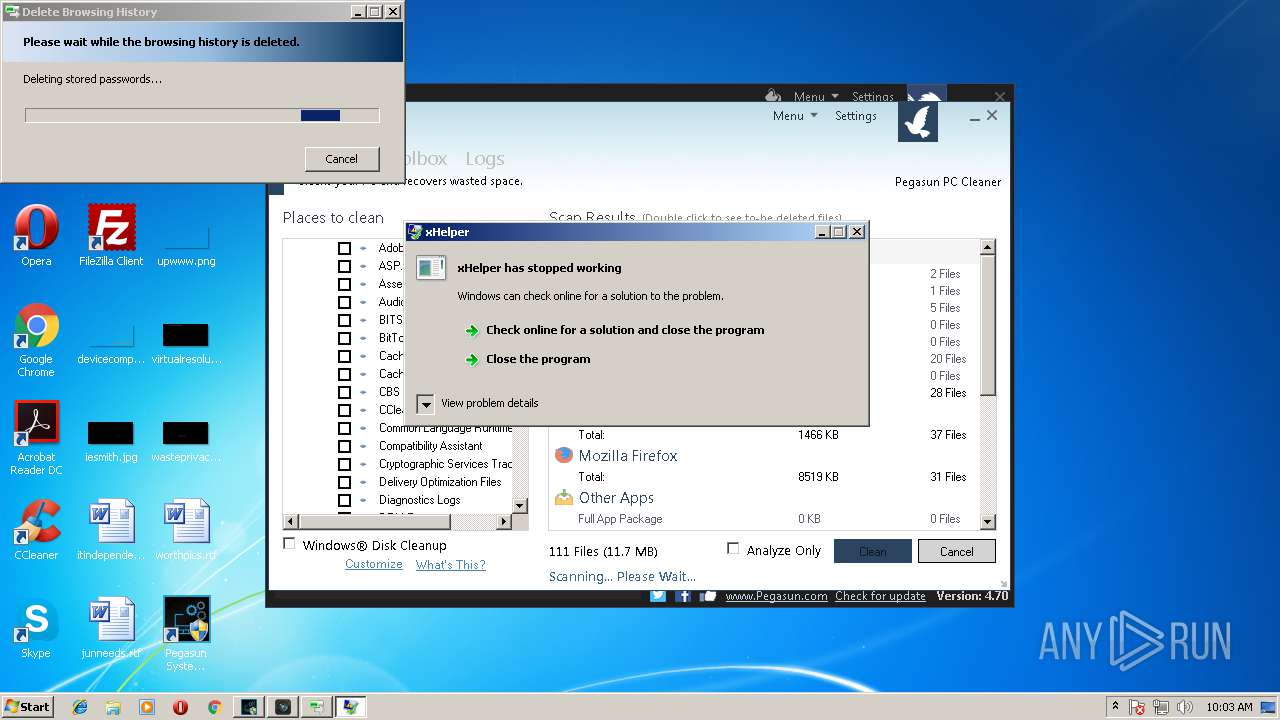
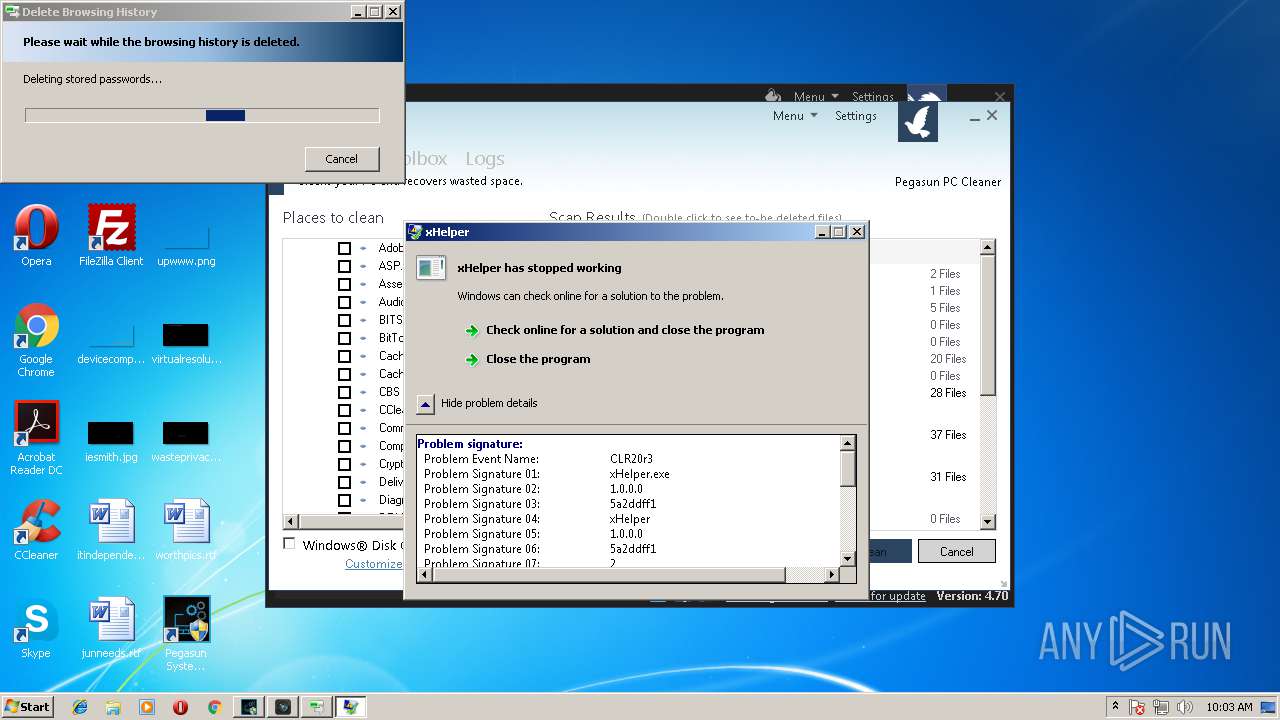
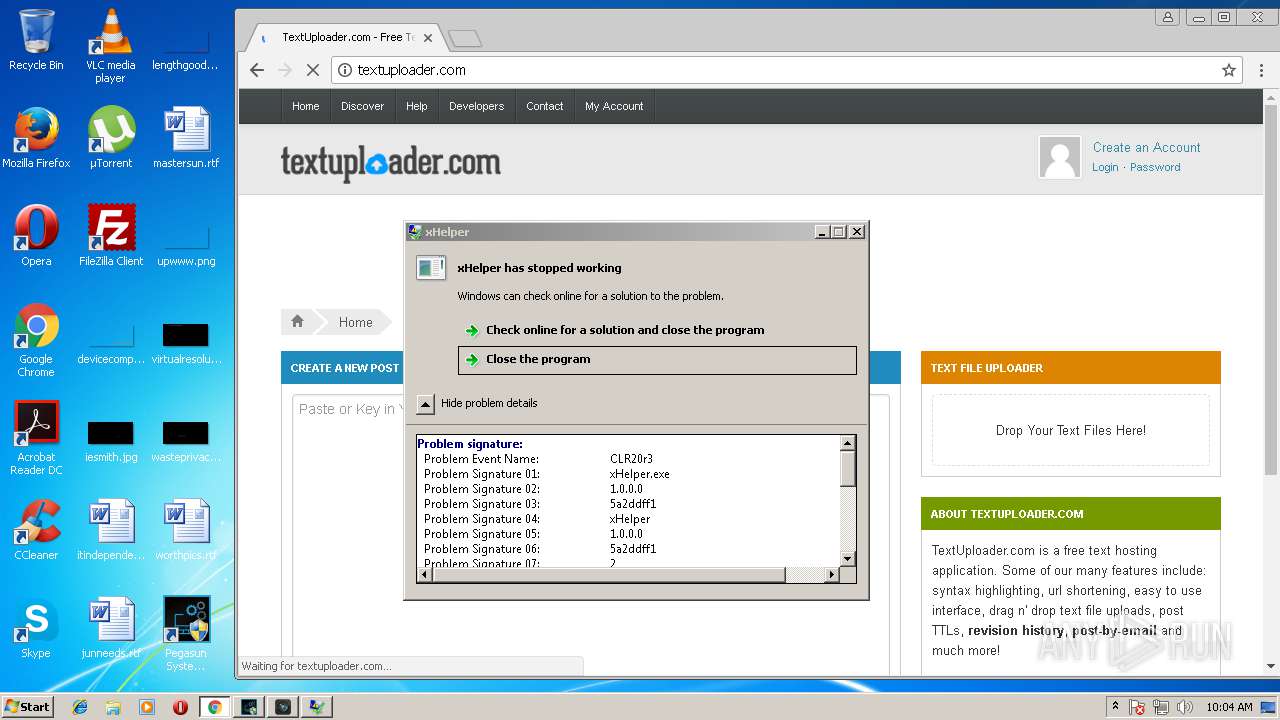
Application was crashed
- xHelper.exe (PID: 2764)
Application launched itself
- chrome.exe (PID: 1576)
Loads the Task Scheduler COM API
- software_reporter_tool.exe (PID: 2092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41472 |
| InitializedDataSize: | 45568 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa98 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.70.0.0 |
| ProductVersionNumber: | 4.70.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
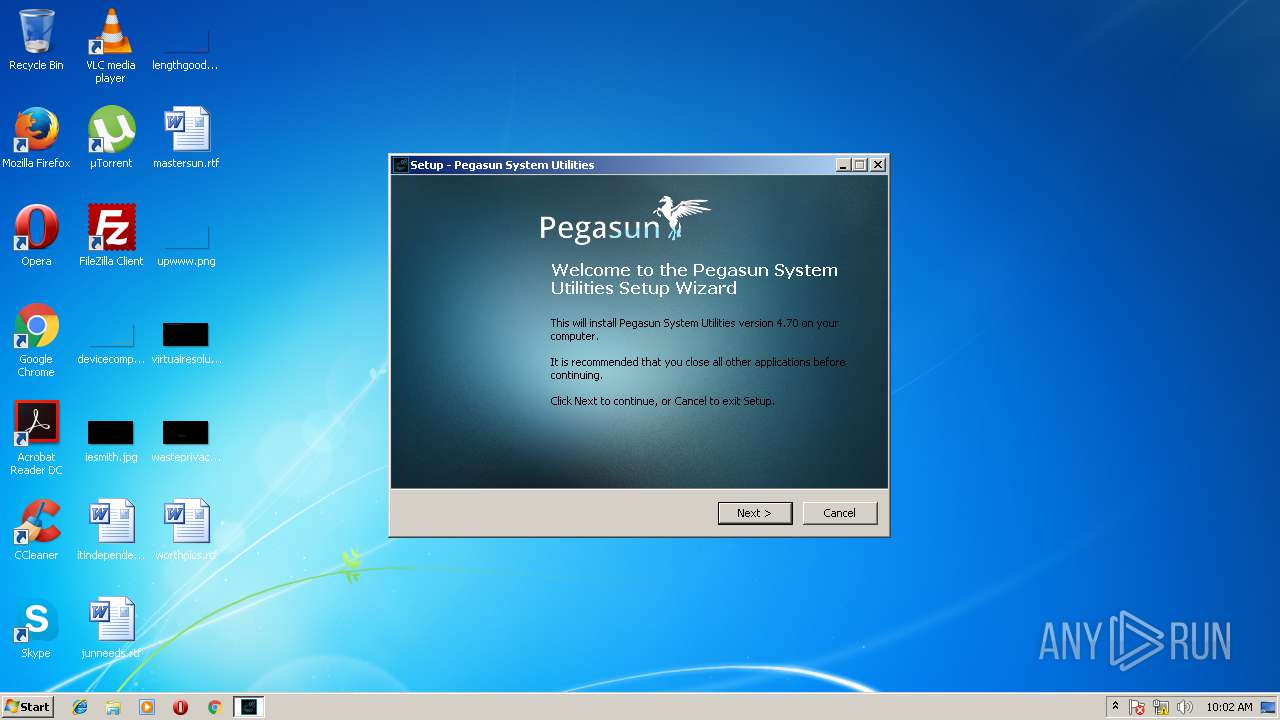
| CompanyName: | Pegasun |
| FileDescription: | Speed up slow computer. |
| FileVersion: | Speed up slow comput |
| LegalCopyright: | 2017 |
| ProductName: | Pegasun System Utilities |
| ProductVersion: | 4.70 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Pegasun |
| FileDescription: | Speed up slow computer. |
| FileVersion: | Speed up slow comput |
| LegalCopyright: | 2017 |
| ProductName: | Pegasun System Utilities |
| ProductVersion: | 4.70 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x0000A1D0 | 0x0000A200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.64375 |
DATA | 0x0000C000 | 0x00000250 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.74012 |
BSS | 0x0000D000 | 0x00000E94 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0000E000 | 0x0000097C | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.48608 |
.tls | 0x0000F000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00010000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.190489 |
.reloc | 0x00011000 | 0x0000091C | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0 |
.rsrc | 0x00012000 | 0x0000A1C8 | 0x0000A200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.74553 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.13965 | 1580 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 3.81529 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 3.81529 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 3.88808 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 5.91429 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 5.91429 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 3.63134 | 1640 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 5.53518 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 5.52604 | 7336 | Latin 1 / Western European | English - United States | RT_ICON |
10 | 7.95273 | 13550 | Latin 1 / Western European | English - United States | RT_ICON |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
76
Monitored processes
30
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1604,9511503947383339109,2542619588077970422,131072 --service-pipe-token=B1D059C18E5E945ADD352486CEC3FBB8 --lang=en-US --disable-client-side-phishing-detection --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=B1D059C18E5E945ADD352486CEC3FBB8 --renderer-client-id=5 --mojo-platform-channel-handle=3276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
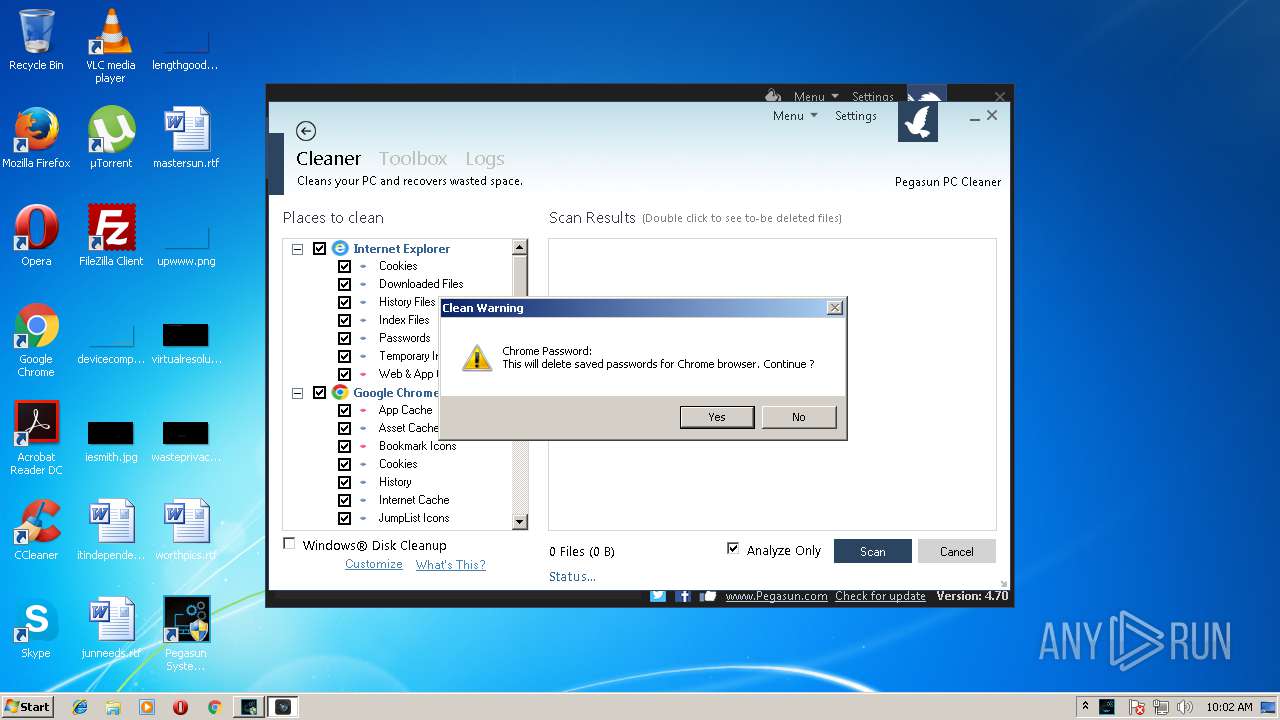
| 960 | "C:\Windows\System32\rundll32.exe" InetCpl.cpl,ClearMyTracksByProcess 8 | C:\Windows\System32\rundll32.exe | — | PCCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1476 | "bin/sHelper.exe" -update -check | C:\Program Files\Pegasun\SystemUtilities\bin\sHelper.exe | SystemUtilities.exe | ||||||||||||
User: admin Company: Pegasun Integrity Level: HIGH Description: Helper Exit code: 0 Version: 1.50.0.0 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=860 --on-initialized-event-handle=296 --parent-handle=300 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Pegasun\SystemUtilities\SystemUtilities.exe" | C:\Program Files\Pegasun\SystemUtilities\SystemUtilities.exe | — | SystemUtilities.tmp | |||||||||||
User: admin Company: Pegasun Integrity Level: MEDIUM Description: Pegasun System Utilities Exit code: 3221226540 Version: 4.70.0.0 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 1692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1604,9511503947383339109,2542619588077970422,131072 --service-pipe-token=48C1E4AE19F63EA04C82CD91493620ED --lang=en-US --extension-process --disable-client-side-phishing-detection --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=48C1E4AE19F63EA04C82CD91493620ED --renderer-client-id=2 --mojo-platform-channel-handle=1780 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 2092 | "C:\Users\admin\AppData\Local\Google\Chrome\User Data\SwReporter\23.129.0\software_reporter_tool.exe" --session-id=xw3gzD8sts0PZnegwNljO5qsw9DKslm3qussI0y/ | C:\Users\admin\AppData\Local\Google\Chrome\User Data\SwReporter\23.129.0\software_reporter_tool.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Integrity Level: MEDIUM Description: Software Reporter Tool Exit code: 2 Version: 23.129.0 Modules
| |||||||||||||||
| 2152 | "C:\Users\admin\AppData\Local\Temp\is-E3L0R.tmp\SystemUtilities.tmp" /SL5="$B0226,4704488,88064,C:\Users\admin\AppData\Local\Temp\SystemUtilities.exe" | C:\Users\admin\AppData\Local\Temp\is-E3L0R.tmp\SystemUtilities.tmp | — | SystemUtilities.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2212 | "C:\Windows\System32\rundll32.exe" InetCpl.cpl,ClearMyTracksByProcess 1 | C:\Windows\System32\rundll32.exe | — | PCCleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 259
Read events
1 772
Write events
425
Delete events
62
Modification events
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 880B0000FC13D138D0F4D301 | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: E10B6A5224796CC7235F08EE279512105317CEDCC28C59B9CFA0D77B39F4DF9D | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Pegasun\SystemUtilities\SystemUtilities.exe | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: CF34B6ADAA9859EE6C3DF6BBC92A68C4139B0982BD5FE42FEEE501B70CB95A7B | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{BFDC3B26-7DB0-43D3-BC84-7E9649C157EA}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.9 (a) | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{BFDC3B26-7DB0-43D3-BC84-7E9649C157EA}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Pegasun\SystemUtilities | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{BFDC3B26-7DB0-43D3-BC84-7E9649C157EA}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Pegasun\SystemUtilities\ | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{BFDC3B26-7DB0-43D3-BC84-7E9649C157EA}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Pegasun System Utilities | |||
| (PID) Process: | (2952) SystemUtilities.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{BFDC3B26-7DB0-43D3-BC84-7E9649C157EA}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
45
Suspicious files
56
Text files
182
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\is-1364H.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\is-MGUU4.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\is-6HG4B.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\is-ECO2L.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\bin\is-HN1MD.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\bin\is-GP36E.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\bin\is-719OQ.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\bin\is-2ADVU.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\bin\is-9BRRT.tmp | — | |
MD5:— | SHA256:— | |||
| 2952 | SystemUtilities.tmp | C:\Program Files\Pegasun\SystemUtilities\bin\is-QM50T.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
47
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1576 | chrome.exe | GET | 200 | 104.19.199.151:80 | http://cdnjs.cloudflare.com/ajax/libs/jquery-powertip/1.1.0/jquery.powertip.css | US | text | 437 b | whitelisted |
1576 | chrome.exe | GET | 200 | 104.25.61.13:80 | http://textuploader.com/assets/css/beoro.css | US | text | 10.0 Kb | suspicious |
1576 | chrome.exe | GET | 200 | 104.25.61.13:80 | http://textuploader.com/ | US | html | 3.96 Kb | suspicious |
1576 | chrome.exe | GET | 200 | 104.25.61.13:80 | http://textuploader.com/assets/css/tu_custom.css | US | text | 519 b | suspicious |
1576 | chrome.exe | GET | 200 | 104.25.61.13:80 | http://textuploader.com/assets/js/beoro_common.js | US | text | 1.52 Kb | suspicious |
1576 | chrome.exe | GET | 200 | 104.25.61.13:80 | http://textuploader.com/assets/js/jquery.actual.min.js | US | text | 611 b | suspicious |
1576 | chrome.exe | GET | 200 | 104.25.61.13:80 | http://textuploader.com/assets/js/tu_dropzone.js | US | text | 733 b | suspicious |
1576 | chrome.exe | GET | 200 | 104.19.199.151:80 | http://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.3.0/css/bootstrap-responsive.min.css | US | text | 3.81 Kb | whitelisted |
1576 | chrome.exe | GET | 200 | 104.19.199.151:80 | http://cdnjs.cloudflare.com/ajax/libs/twitter-bootstrap/2.3.0/css/bootstrap.min.css | US | text | 16.5 Kb | whitelisted |
1576 | chrome.exe | GET | 200 | 192.0.73.2:80 | http://www.gravatar.com/avatar/d41d8cd98f00b204e9800998ecf8427e?s=80&r=g&d=mm | US | image | 1.29 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1576 | chrome.exe | 172.217.21.228:443 | www.google.com | Google Inc. | US | whitelisted |
1576 | chrome.exe | 216.58.207.46:443 | apis.google.com | Google Inc. | US | whitelisted |
1576 | chrome.exe | 172.217.16.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1576 | chrome.exe | 104.25.61.13:80 | textuploader.com | Cloudflare Inc | US | shared |
1576 | chrome.exe | 192.0.73.2:80 | www.gravatar.com | Automattic, Inc | US | whitelisted |
1576 | chrome.exe | 216.58.210.2:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
1576 | chrome.exe | 216.58.210.2:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
1576 | chrome.exe | 172.217.22.78:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
1576 | chrome.exe | 104.19.199.151:80 | cdnjs.cloudflare.com | Cloudflare Inc | US | shared |
1576 | chrome.exe | 172.217.22.78:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pegasun.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
www.google.ru |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
textuploader.com |
| suspicious |
cdnjs.cloudflare.com |
| whitelisted |
www.gravatar.com |
| whitelisted |