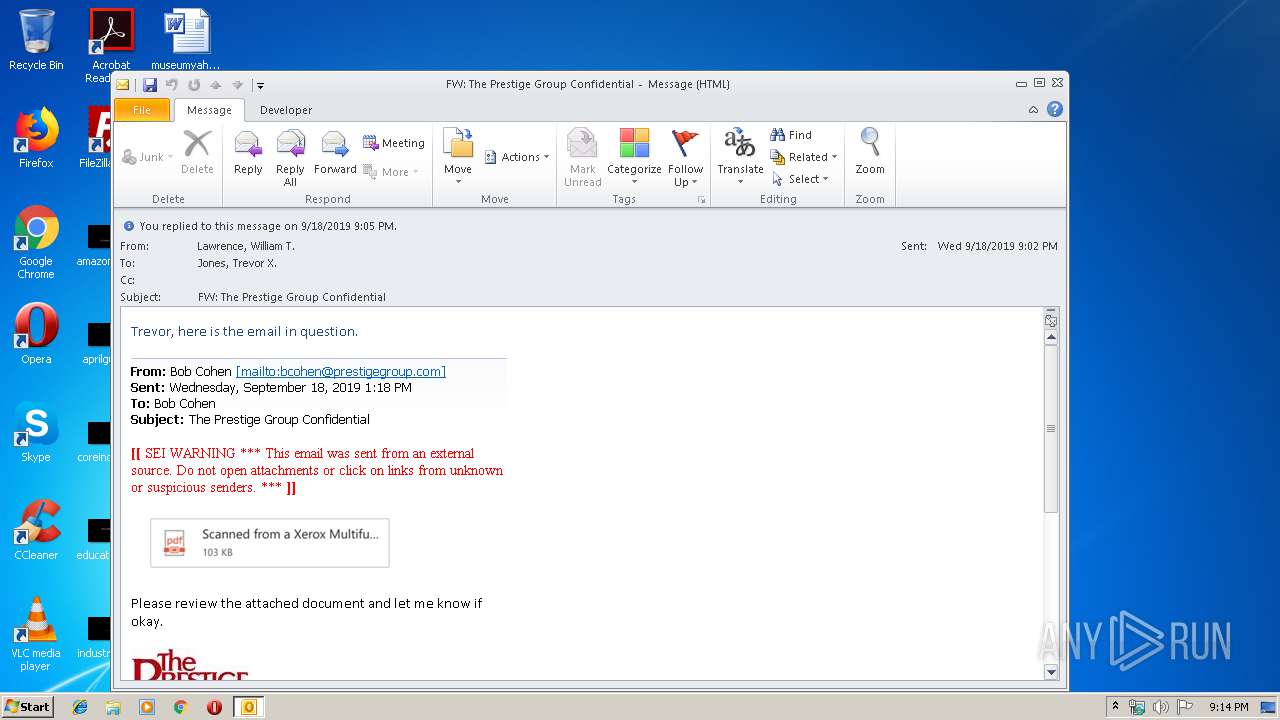
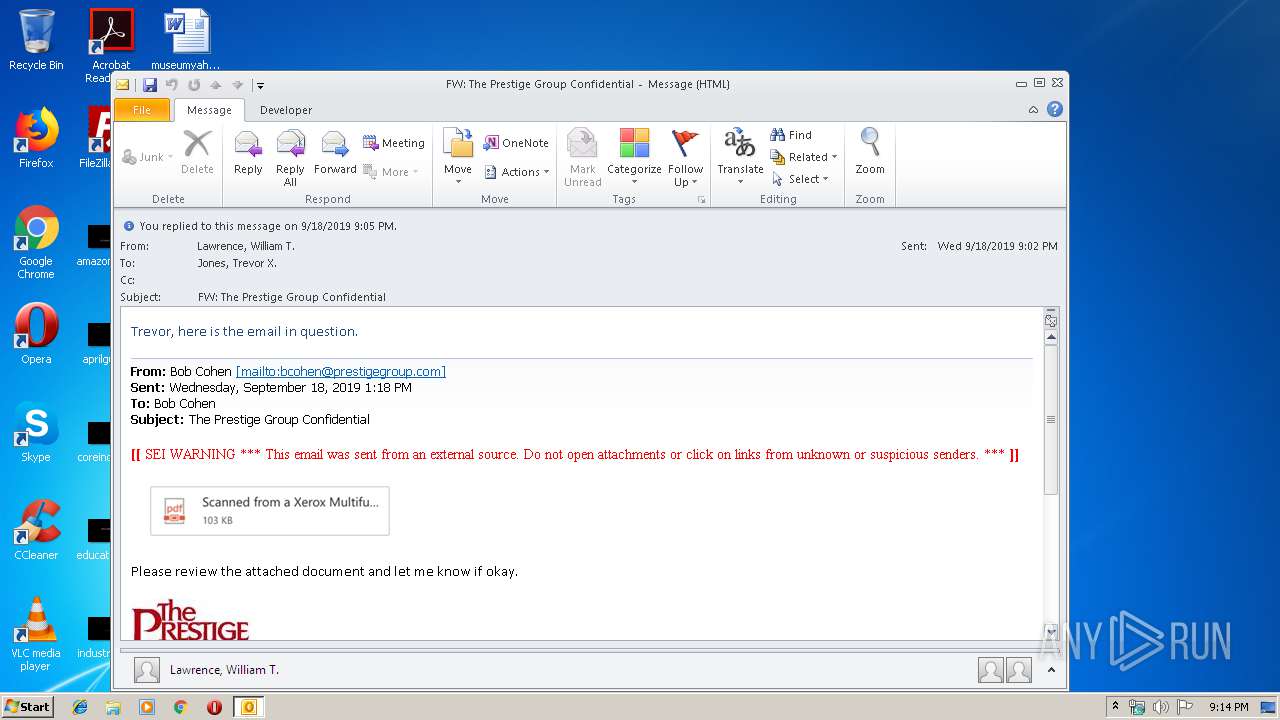
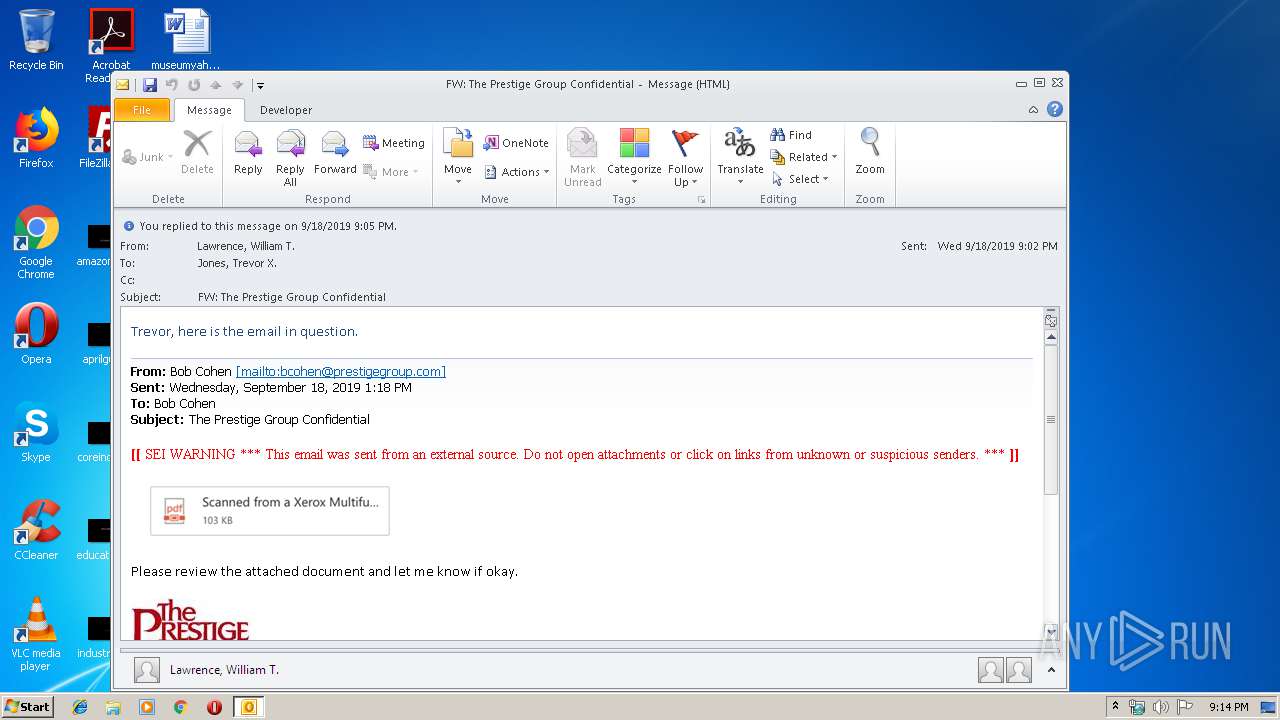
| File name: | FW The Prestige Group Confidential.msg |
| Full analysis: | https://app.any.run/tasks/f76eb2a2-4c05-4e89-bb8a-e9531332b10e |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2019, 20:13:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 9170AD14B4F7E6F37D9D2DAEE519E25D |
| SHA1: | B5E8329298824290031AE4505F57FFA63D4403B1 |
| SHA256: | 43E1A304B2177247F8FE682182E02FD88CD9B56F8BB45A96BB83E346CDE53236 |
| SSDEEP: | 768:2HXUIdIKknv8f7VkFwqmIBPsKQPsKjryXgRRQJ7BKEUlG/s5HiR7Mt1pL/IGlriO:Wd5Ks8+rFE5sk0nj8 |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3424)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3424)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3424)
Executed via COM
- sdiagnhost.exe (PID: 3736)
- sdiagnhost.exe (PID: 2932)
Uses IPCONFIG.EXE to discover IP address
- sdiagnhost.exe (PID: 3736)
Executable content was dropped or overwritten
- msdt.exe (PID: 3024)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3424)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3424)
Application launched itself
- iexplore.exe (PID: 408)
Reads Internet Cache Settings
- iexplore.exe (PID: 3360)
Reads internet explorer settings
- iexplore.exe (PID: 3360)
Changes internet zones settings
- iexplore.exe (PID: 408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
45
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
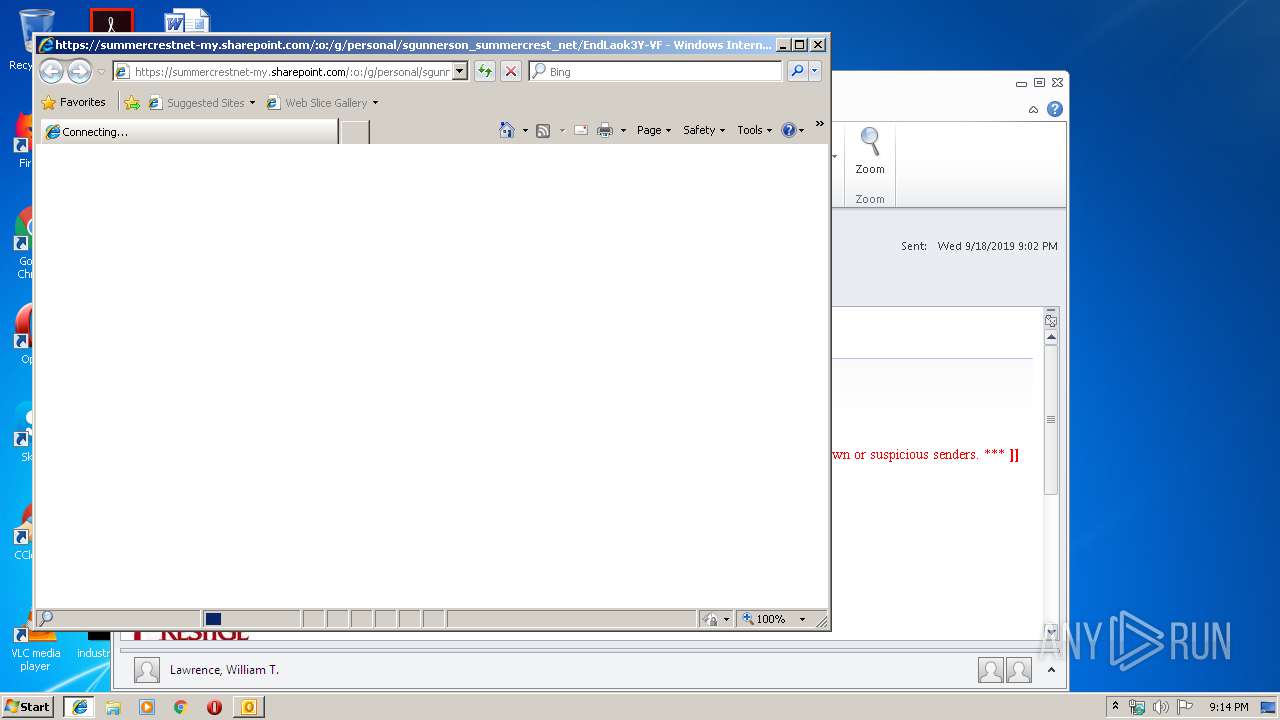
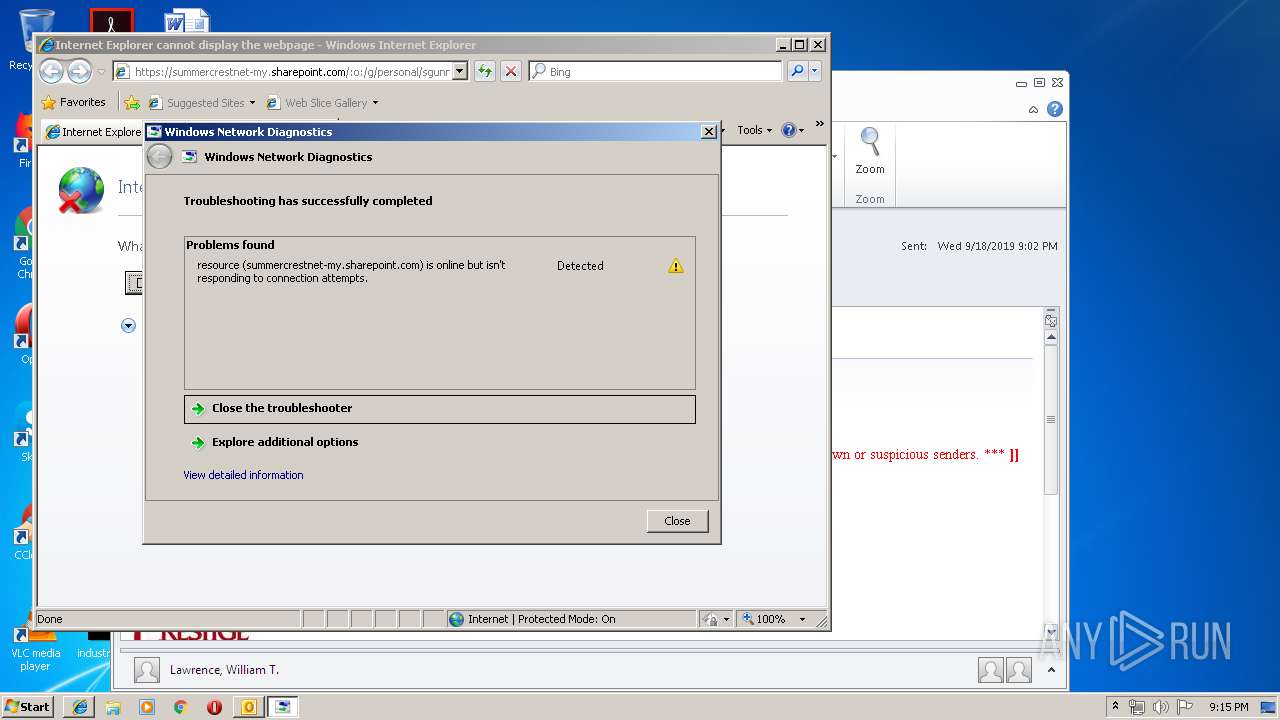
| 408 | "C:\Program Files\Internet Explorer\iexplore.exe" https://summercrestnet-my.sharepoint.com/:o:/g/personal/sgunnerson_summercrest_net/EndLaok3Y-VFumPw7Ym4FxMB-guZ0gwy4SGsejY7GmiOqg?e=3mUITi | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2700 | "C:\Windows\system32\ROUTE.EXE" print | C:\Windows\system32\ROUTE.EXE | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2932 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
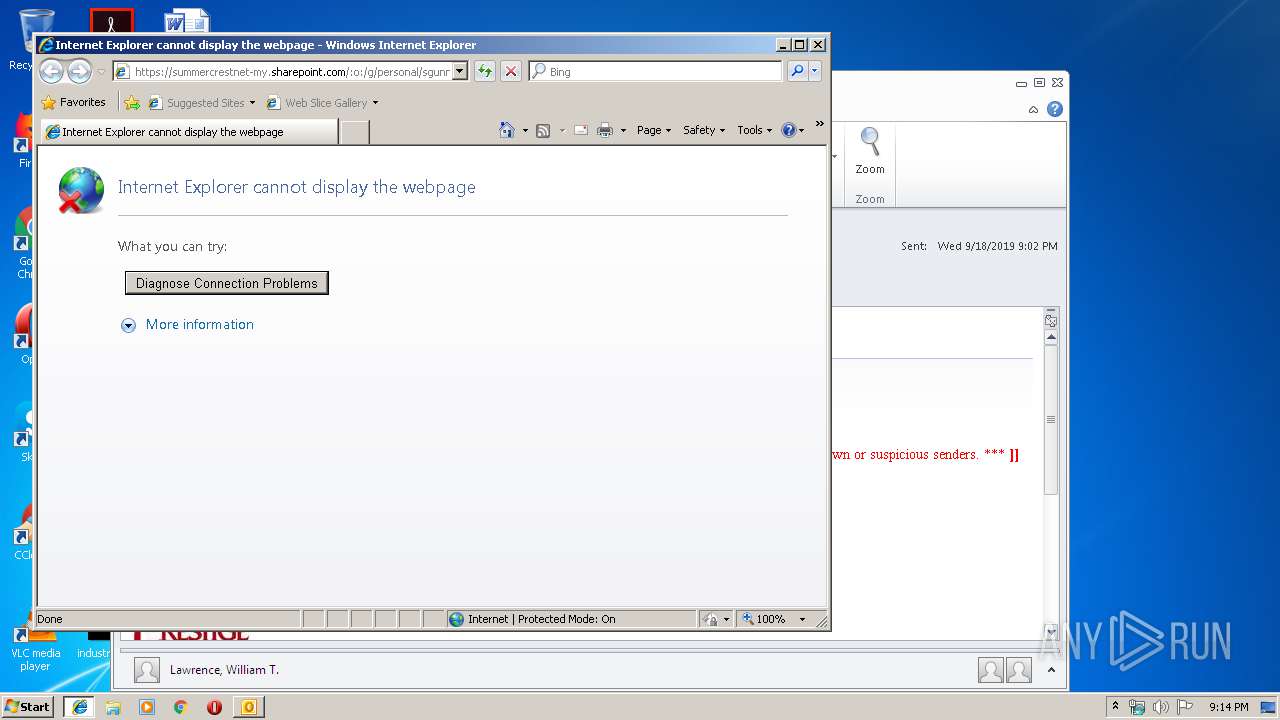
| 3024 | -modal 66108 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF1CA0.tmp -ep NetworkDiagnosticsWeb | C:\Windows\system32\msdt.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3360 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:408 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3376 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\system32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3424 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\FW The Prestige Group Confidential.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3736 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3816 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\system32\ipconfig.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 660
Read events
1 182
Write events
459
Delete events
19
Modification events
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | s}# |
Value: 737D2300600D0000010000000000000000000000 | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 600D00005A934BA15D6ED50100000000 | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220220640 | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3424) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1328676885 | |||
Executable files
4
Suspicious files
4
Text files
73
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR99E3.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\F59E0F9B.dat | image | |
MD5:— | SHA256:— | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CABEF182.dat | image | |
MD5:— | SHA256:— | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{97B32129-7266-43D1-A71F-6994C4890AC9}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:7D80C0A7E3849818695EAF4989186A3C | SHA256:72DC527D78A8E99331409803811CC2D287E812C008A1C869A6AEA69D7A44B597 | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_8906F323CE71674DA070AAA58F54D943.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_085900F7FE5D144F8AC8DB18F1DAC2B0.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_E15AD21F8B3EA04EB23DF3A769BEC26F.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
| 3424 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ContactPrefs_2_7BCFFF113541EE49A2A179CA5BC8A617.dat | xml | |
MD5:BBCF400BD7AE536EB03054021D6A6398 | SHA256:383020065C1F31F4FB09F448599A6D5E532C390AF4E5B8AF0771FE17A23222AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3424 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
408 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
984 | svchost.exe | 13.107.136.9:443 | summercrestnet-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
408 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3424 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3360 | iexplore.exe | 13.107.136.9:443 | summercrestnet-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
summercrestnet-my.sharepoint.com |
| suspicious |
www.bing.com |
| whitelisted |
dns.msftncsi.com |
| shared |