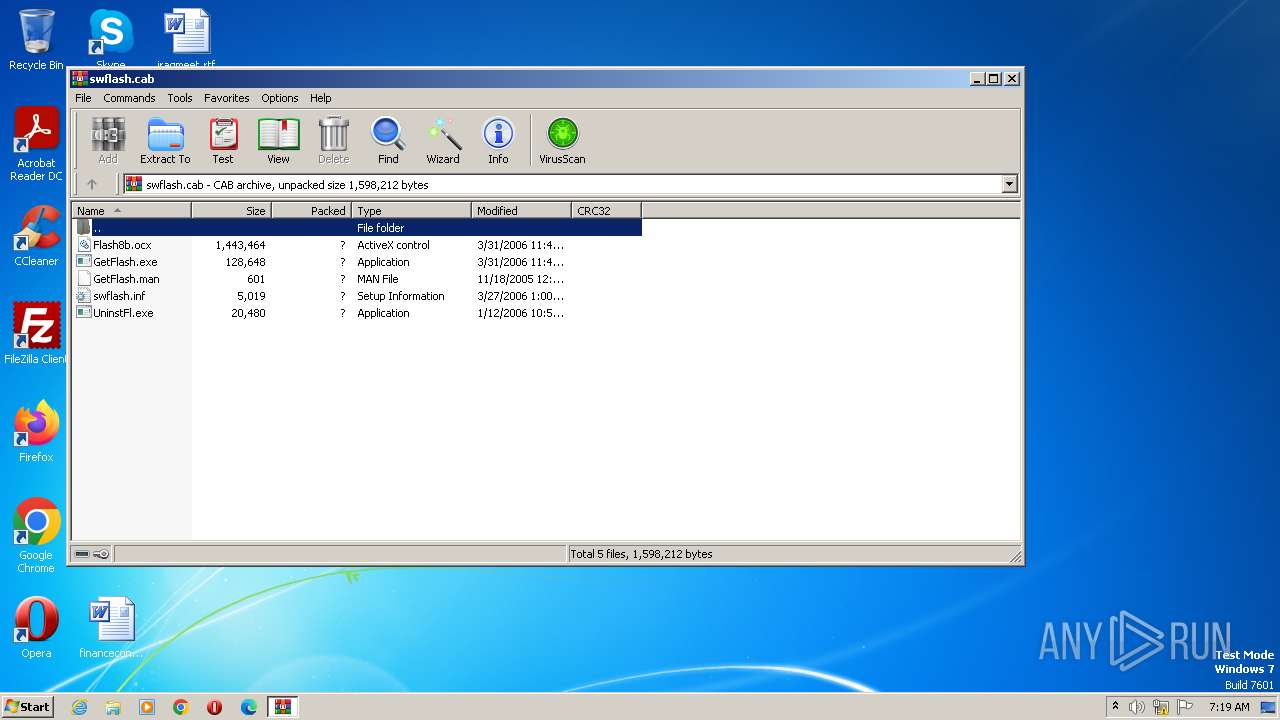
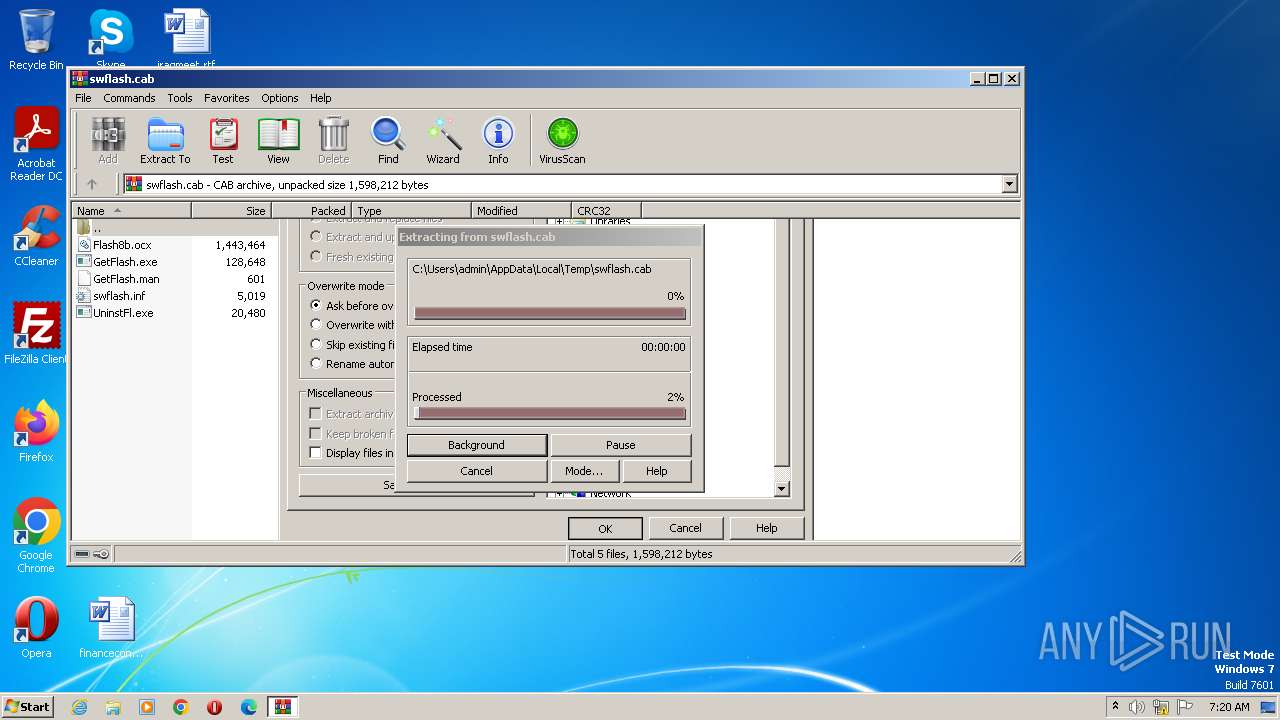
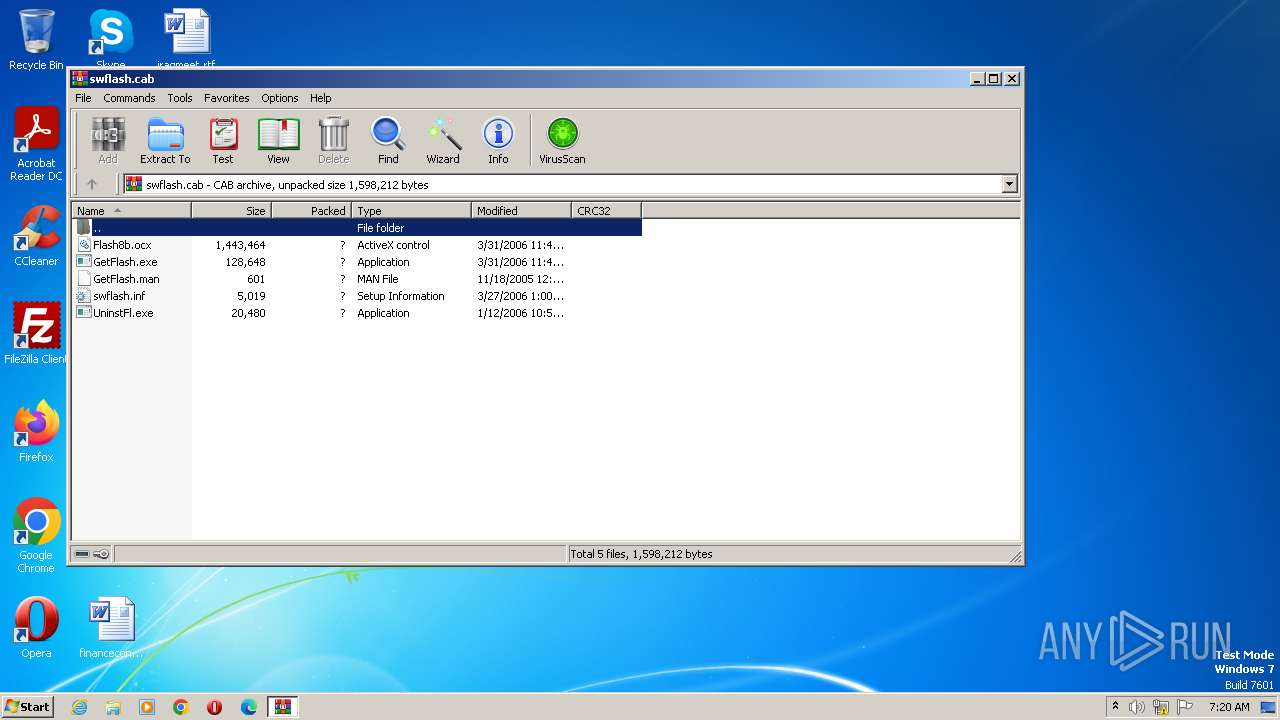
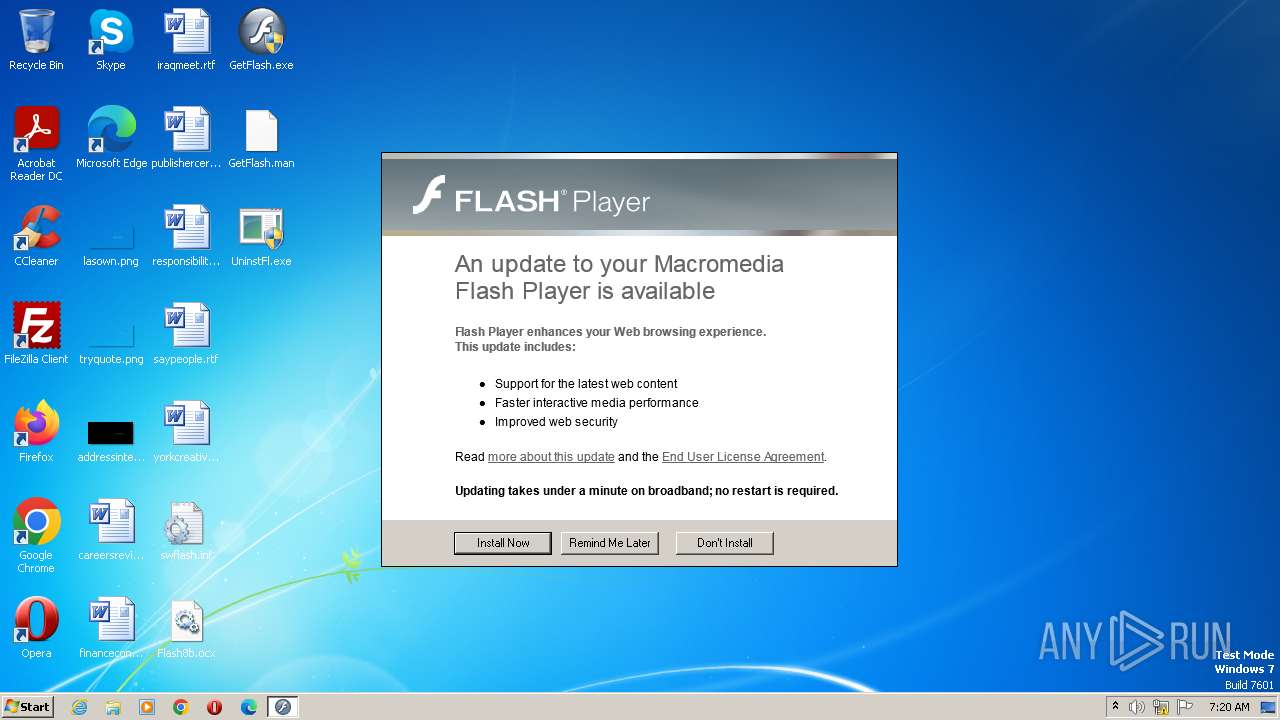
| File name: | swflash.cab |
| Full analysis: | https://app.any.run/tasks/2318457b-f243-40af-a12e-b2fc6b0544e0 |
| Verdict: | Malicious activity |
| Analysis date: | July 31, 2023, 06:19:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-cab-compressed |
| File info: | Microsoft Cabinet archive data, many, 739035 bytes, 5 files, at 0x44 +A "swflash.inf" +A "Flash8b.ocx", flags 0x4, ID 5628, number 1, extra bytes 20 in head, 49 datablocks, 0x1503 compression |
| MD5: | 7C2D5F5CA3B692FF7CCDBA52EADC91C1 |
| SHA1: | FD648FAB51614544536CFBD6D86CACC457C27854 |
| SHA256: | 43D8F56DFCA3A13759D4EAA04C3AE9EA6D718E475516D8651011596E8B975BEF |
| SSDEEP: | 12288:BMBAvsNoaknHxClXb4N50ny63u9gJxGE8x29FVONg0eltCblxVuzMHaFP2mLMXYZ:B0/v2Nany63uNk0elIug05MoaQpwit |
MALICIOUS
Application was dropped or rewritten from another process
- GetFlash.exe (PID: 2124)
- GetFlash.exe (PID: 3316)
SUSPICIOUS
Reads Microsoft Outlook installation path
- GetFlash.exe (PID: 2124)
Reads the Internet Settings
- GetFlash.exe (PID: 2124)
Reads Internet Explorer settings
- GetFlash.exe (PID: 2124)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 448)
Reads the computer name
- GetFlash.exe (PID: 2124)
Checks supported languages
- GetFlash.exe (PID: 2124)
Reads the machine GUID from the registry
- GetFlash.exe (PID: 2124)
The process checks LSA protection
- GetFlash.exe (PID: 2124)
Manual execution by a user
- GetFlash.exe (PID: 3316)
- GetFlash.exe (PID: 2124)
Checks proxy server information
- GetFlash.exe (PID: 2124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\swflash.cab" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1432 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\Desktop\GetFlash.exe" | C:\Users\admin\Desktop\GetFlash.exe | explorer.exe | ||||||||||||
User: admin Company: Macromedia, Inc. Integrity Level: HIGH Description: Macromedia Flash Player Updater 8.0 r24 Exit code: 3221225547 Version: 8,0,24,0 Modules
| |||||||||||||||
| 3316 | "C:\Users\admin\Desktop\GetFlash.exe" | C:\Users\admin\Desktop\GetFlash.exe | — | explorer.exe | |||||||||||
User: admin Company: Macromedia, Inc. Integrity Level: MEDIUM Description: Macromedia Flash Player Updater 8.0 r24 Exit code: 3221226540 Version: 8,0,24,0 Modules
| |||||||||||||||
Total events
1 524
Read events
1 482
Write events
42
Delete events
0
Modification events
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
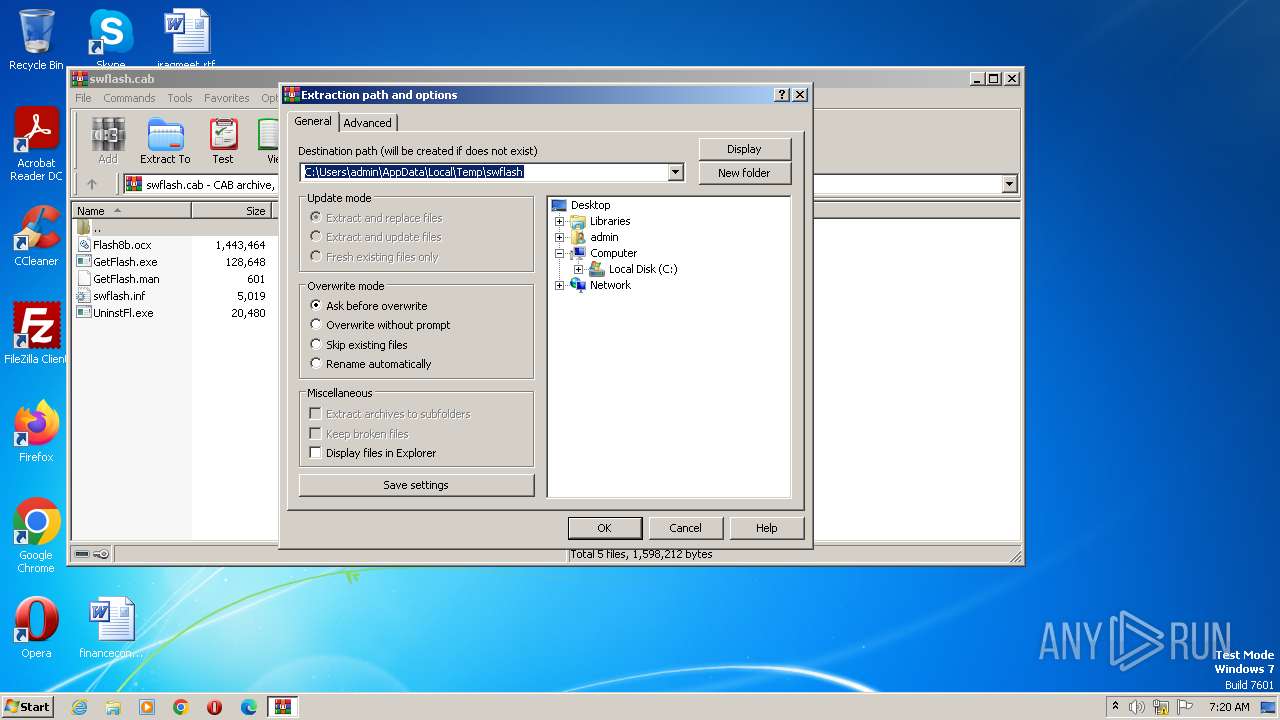
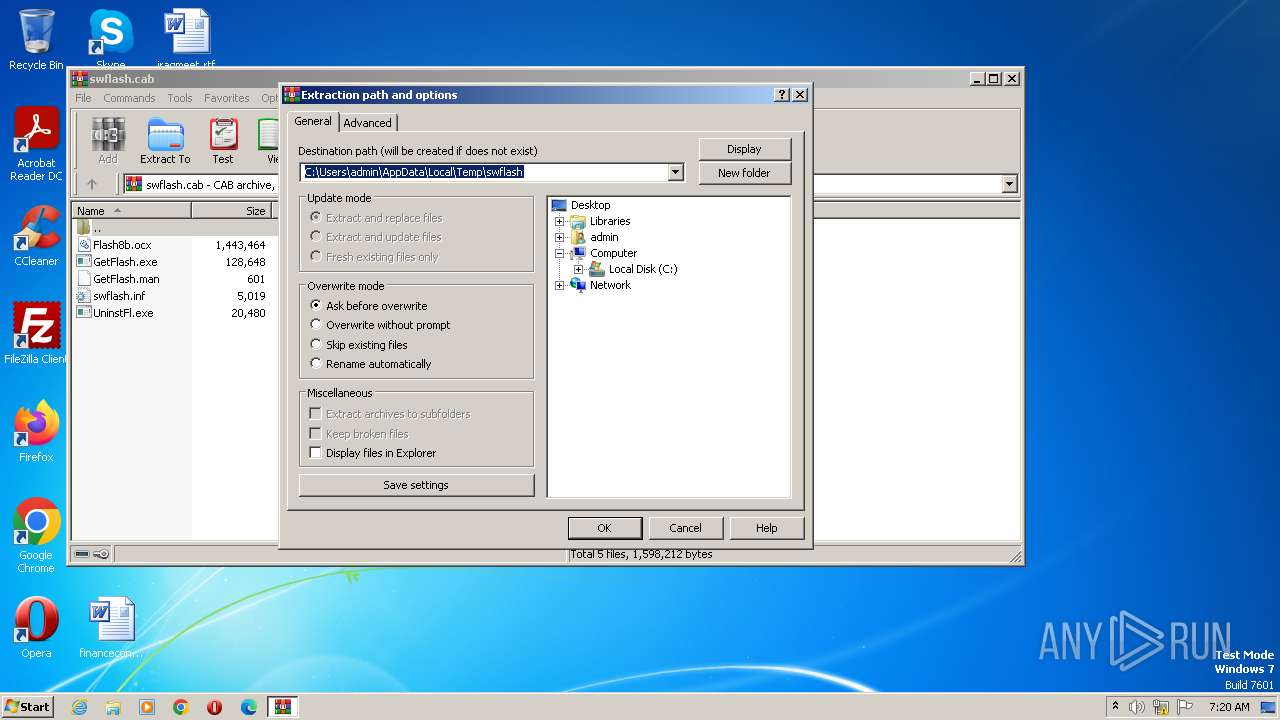
Value: C:\Users\admin\AppData\Local\Temp\swflash | |||
| (PID) Process: | (1432) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
6
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\swflash\swflash.inf | binary | |
MD5:EAD1D394A7E95C93F0B23C23905E9A1E | SHA256:DA3F717128ECBD212C8988E287FC2939C35BE0ECD112BAEB3457AEBFC1D3B570 | |||
| 448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\swflash\UninstFl.exe | executable | |
MD5:E363C03590D04CF7932EA54E7848F8FE | SHA256:36C8AFD35998F052B927DD5E80B92BDCB0FFC085F346C118D2784454A0C80D3E | |||
| 448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\swflash\GetFlash.man | xml | |
MD5:BDB09346869B49DBCBAD8741941393F6 | SHA256:613F5A26BDF0DA0D2BBBBE24E7945856E70B2887D27A88322D325B15F549D7CA | |||
| 448 | WinRAR.exe | C:\Users\admin\Desktop\UninstFl.exe | executable | |
MD5:E363C03590D04CF7932EA54E7848F8FE | SHA256:36C8AFD35998F052B927DD5E80B92BDCB0FFC085F346C118D2784454A0C80D3E | |||
| 448 | WinRAR.exe | C:\Users\admin\Desktop\swflash.inf | binary | |
MD5:EAD1D394A7E95C93F0B23C23905E9A1E | SHA256:DA3F717128ECBD212C8988E287FC2939C35BE0ECD112BAEB3457AEBFC1D3B570 | |||
| 448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\swflash\GetFlash.exe | executable | |
MD5:7CDFBA8F85658000A542AD3F40D6AC62 | SHA256:1C858BFE34D487192CF08F2AD271E67D50C1FA6DD5F6897348EE8762D45E0414 | |||
| 448 | WinRAR.exe | C:\Users\admin\Desktop\GetFlash.exe | executable | |
MD5:7CDFBA8F85658000A542AD3F40D6AC62 | SHA256:1C858BFE34D487192CF08F2AD271E67D50C1FA6DD5F6897348EE8762D45E0414 | |||
| 448 | WinRAR.exe | C:\Users\admin\Desktop\GetFlash.man | xml | |
MD5:BDB09346869B49DBCBAD8741941393F6 | SHA256:613F5A26BDF0DA0D2BBBBE24E7945856E70B2887D27A88322D325B15F549D7CA | |||
| 448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\swflash\Flash8b.ocx | executable | |
MD5:12719EDDAAB9CAEEF28C6E58192F594B | SHA256:FF12AC1EC68351653211BB9B9B54C31B98A61104C79FCE9EE6BD54EAD969DAE9 | |||
| 448 | WinRAR.exe | C:\Users\admin\Desktop\Flash8b.ocx | executable | |
MD5:12719EDDAAB9CAEEF28C6E58192F594B | SHA256:FF12AC1EC68351653211BB9B9B54C31B98A61104C79FCE9EE6BD54EAD969DAE9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
7
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
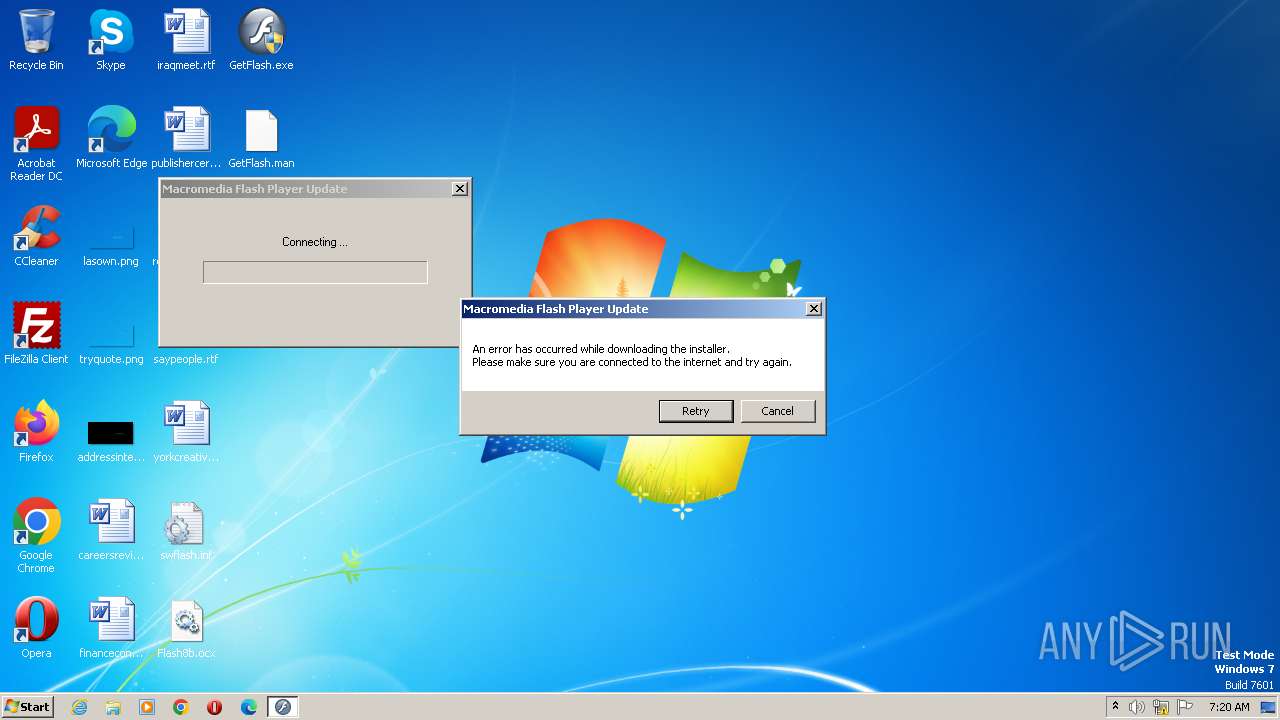
2124 | GetFlash.exe | GET | 404 | 104.102.49.111:80 | http://fpdownload.macromedia.com/pub/flashplayer/update/current/install/install_all_win_ax_sgn.z | DE | html | 261 b | whitelisted |
2124 | GetFlash.exe | GET | 404 | 104.102.49.111:80 | http://fpdownload.macromedia.com/pub/flashplayer/update/current/install/install_all_win_ax_sgn.z | DE | html | 261 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2124 | GetFlash.exe | 104.102.49.111:80 | fpdownload.macromedia.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fpdownload.macromedia.com |
| whitelisted |
dns.msftncsi.com |
| shared |