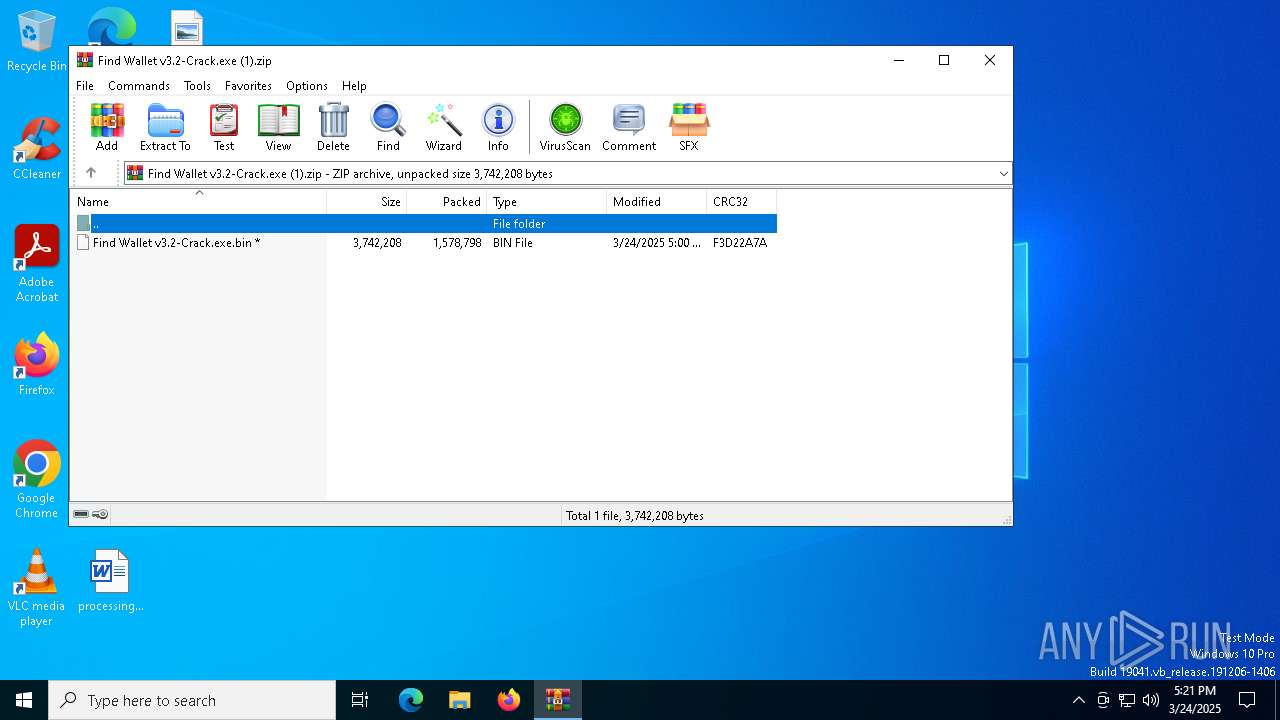
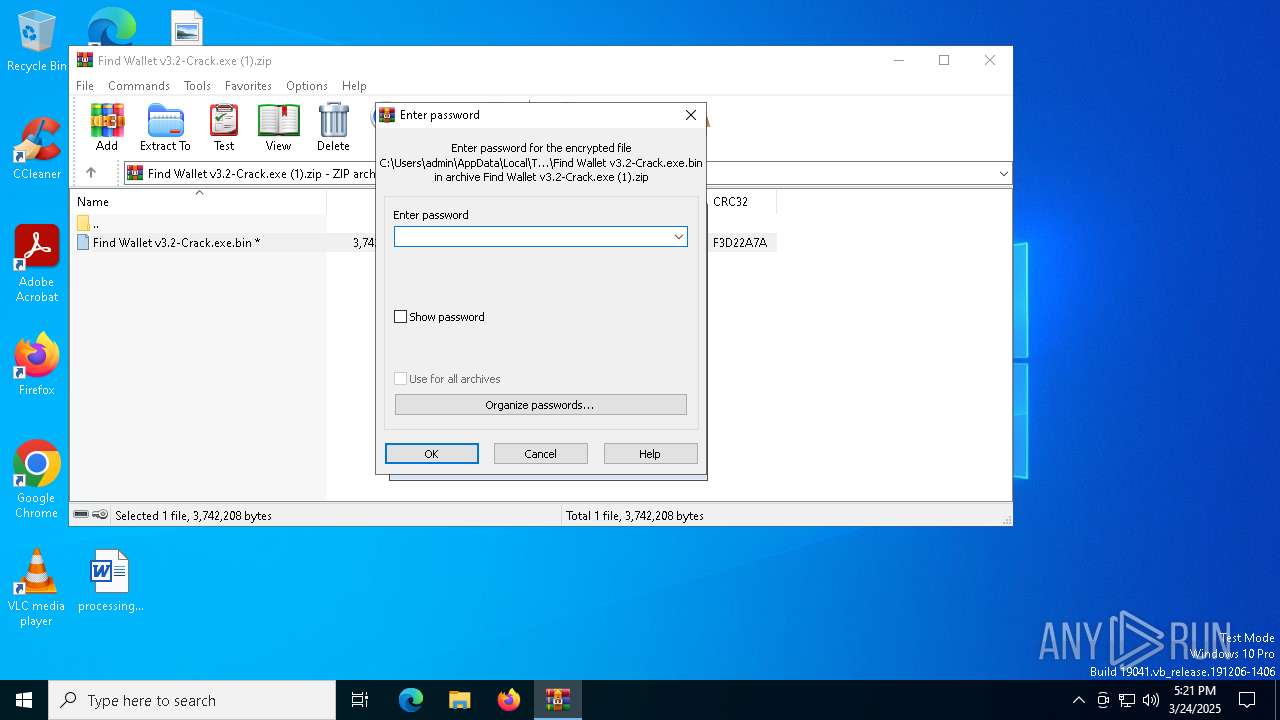
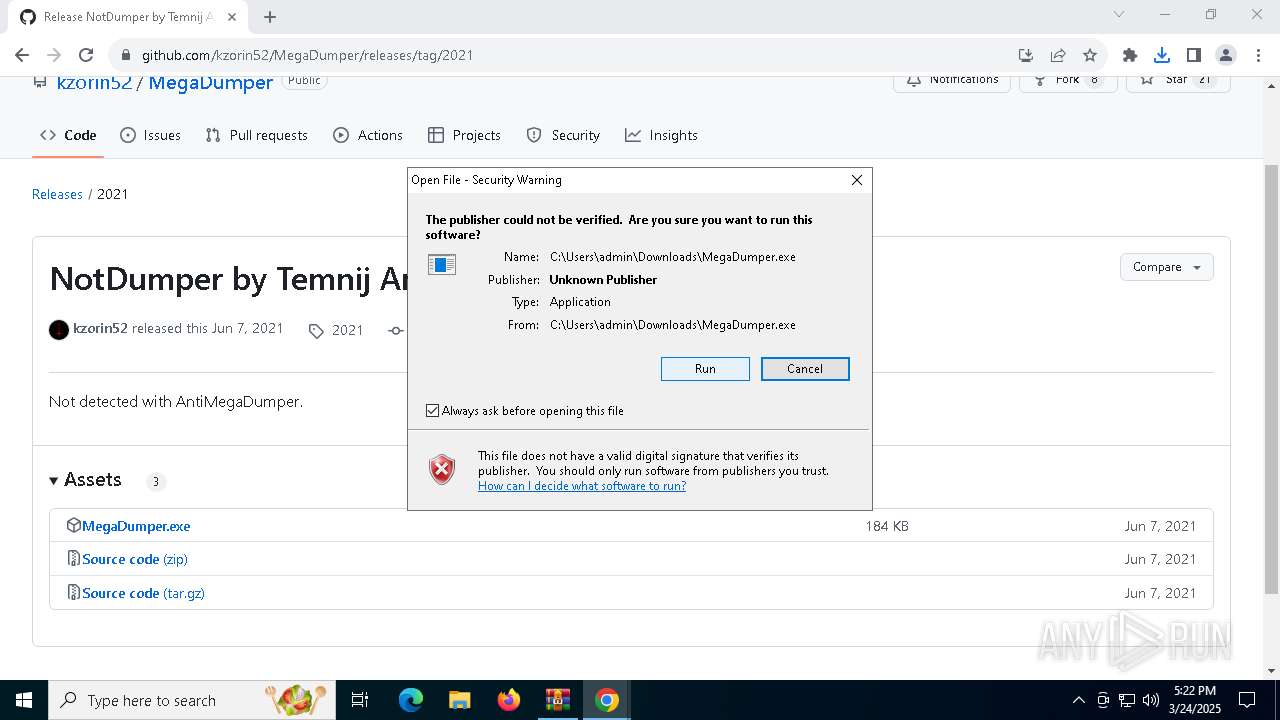
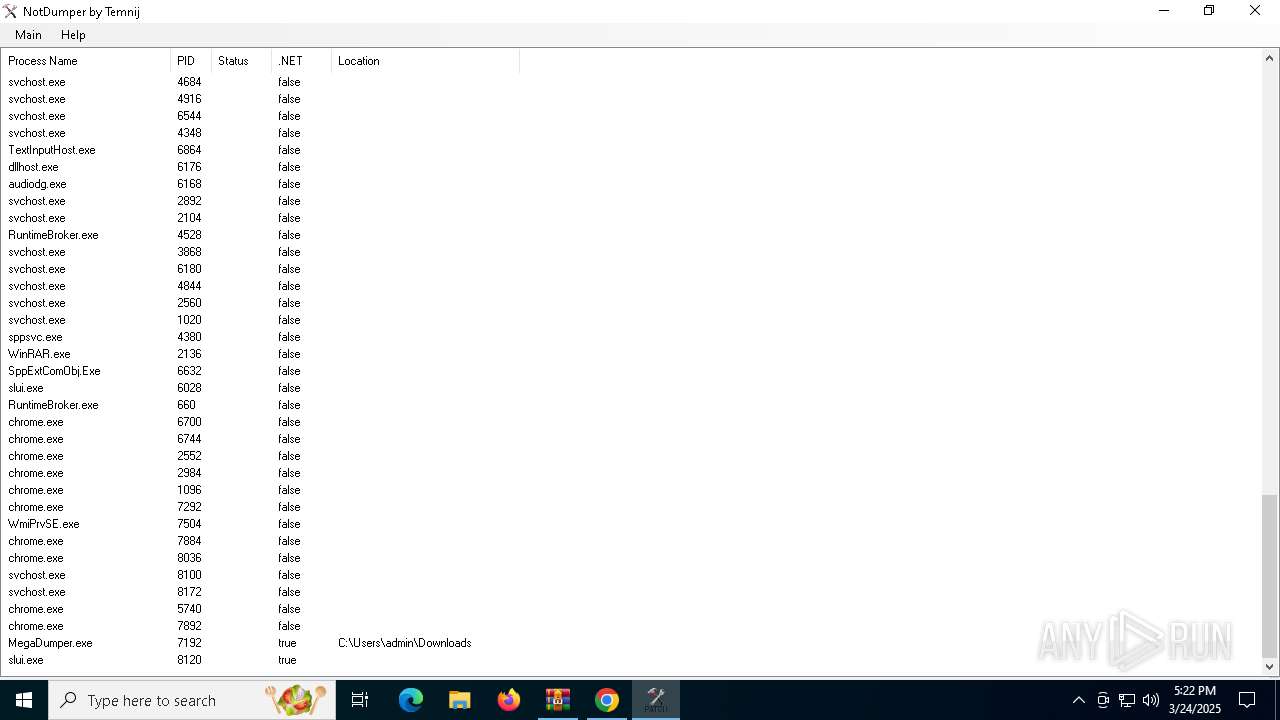
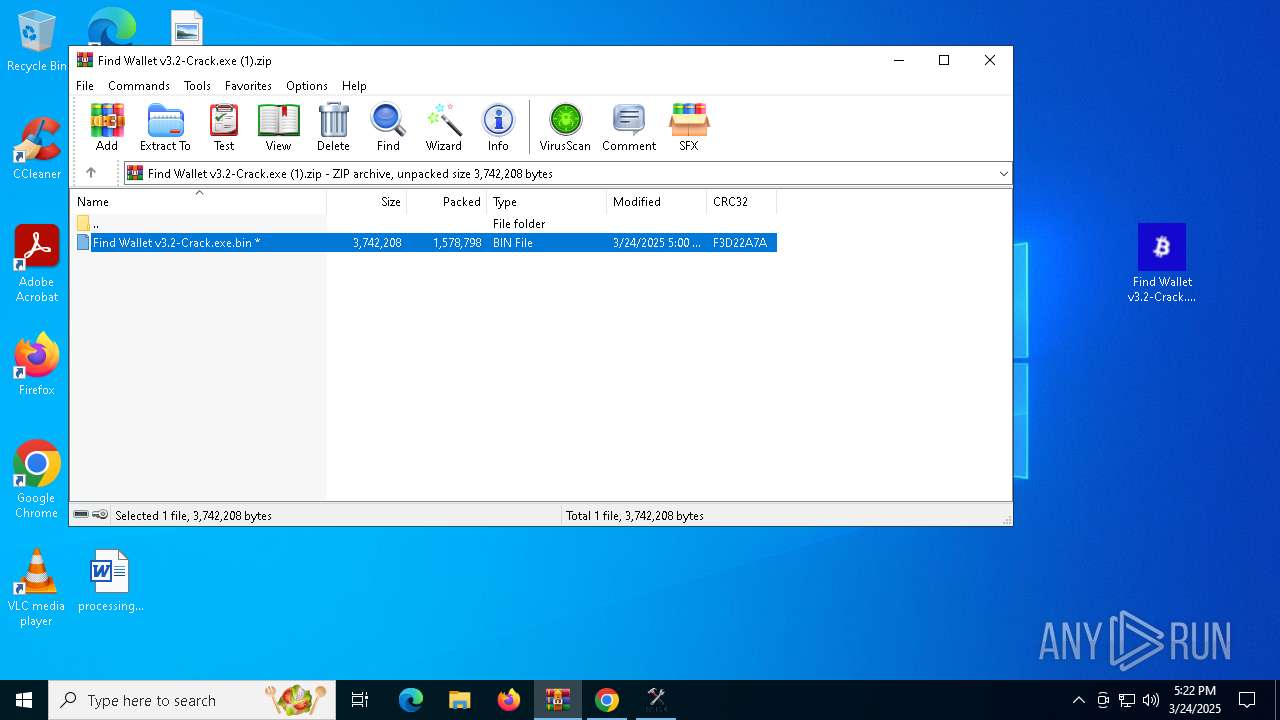
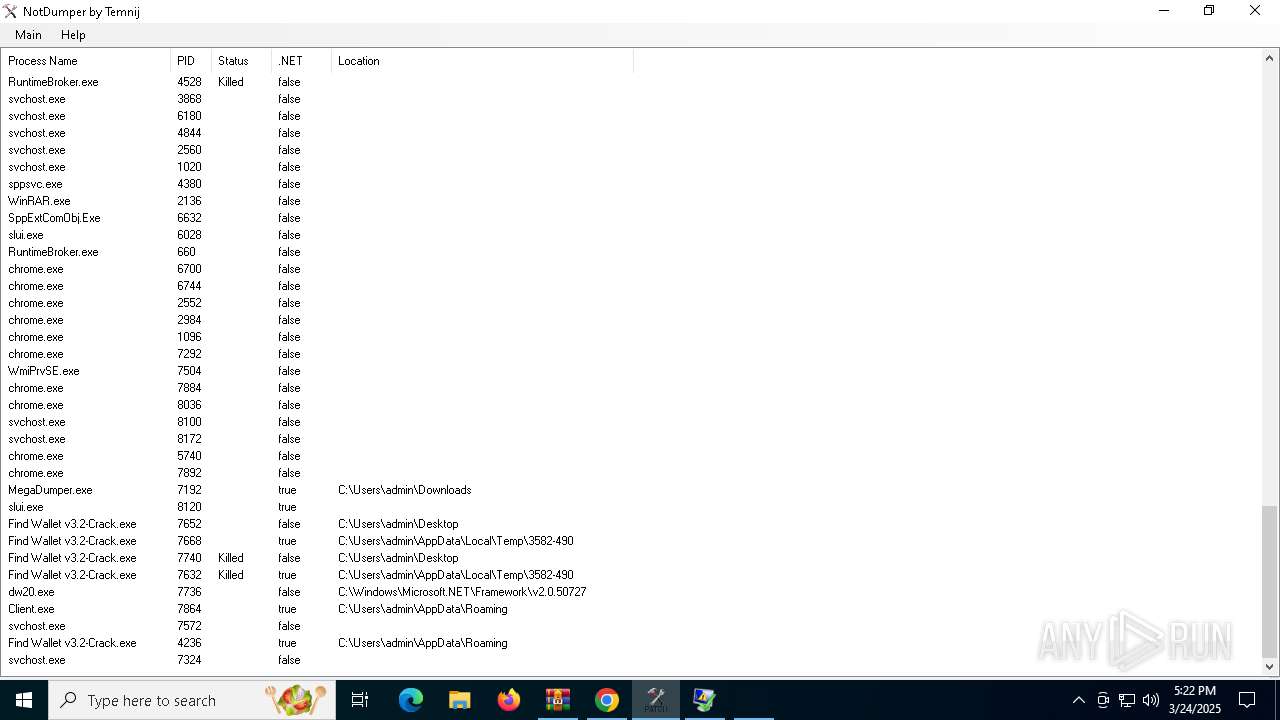
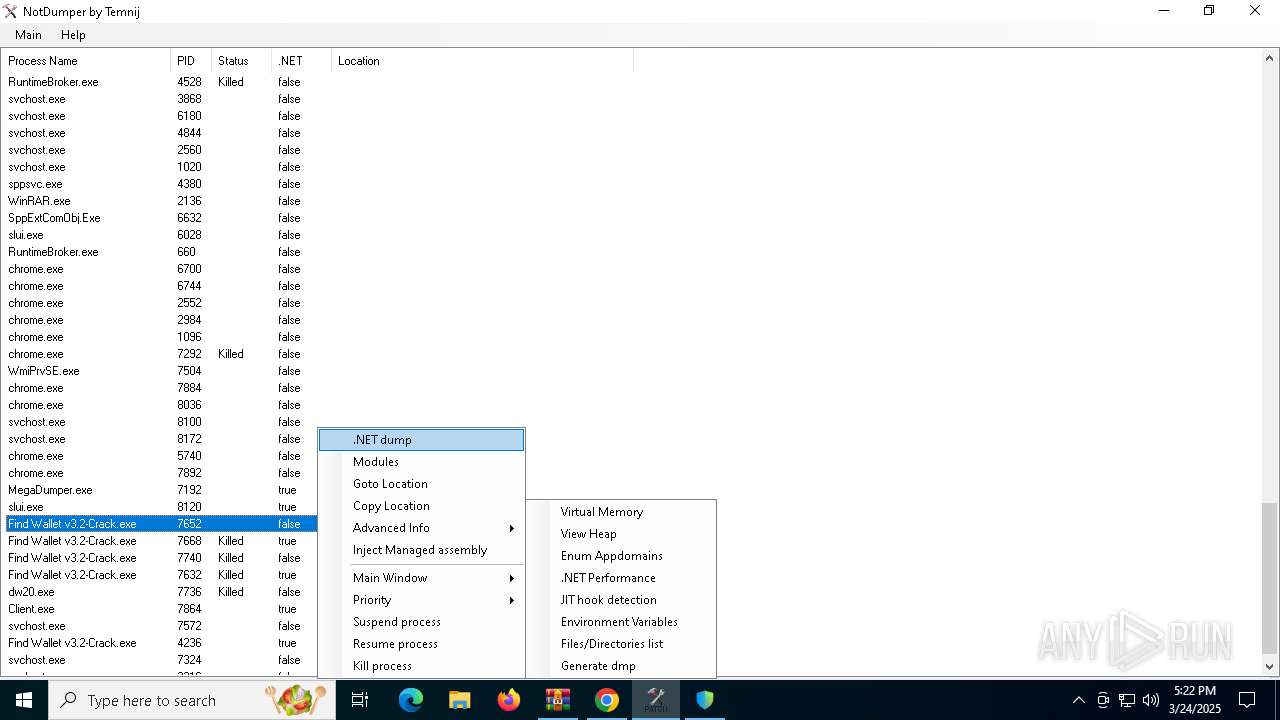
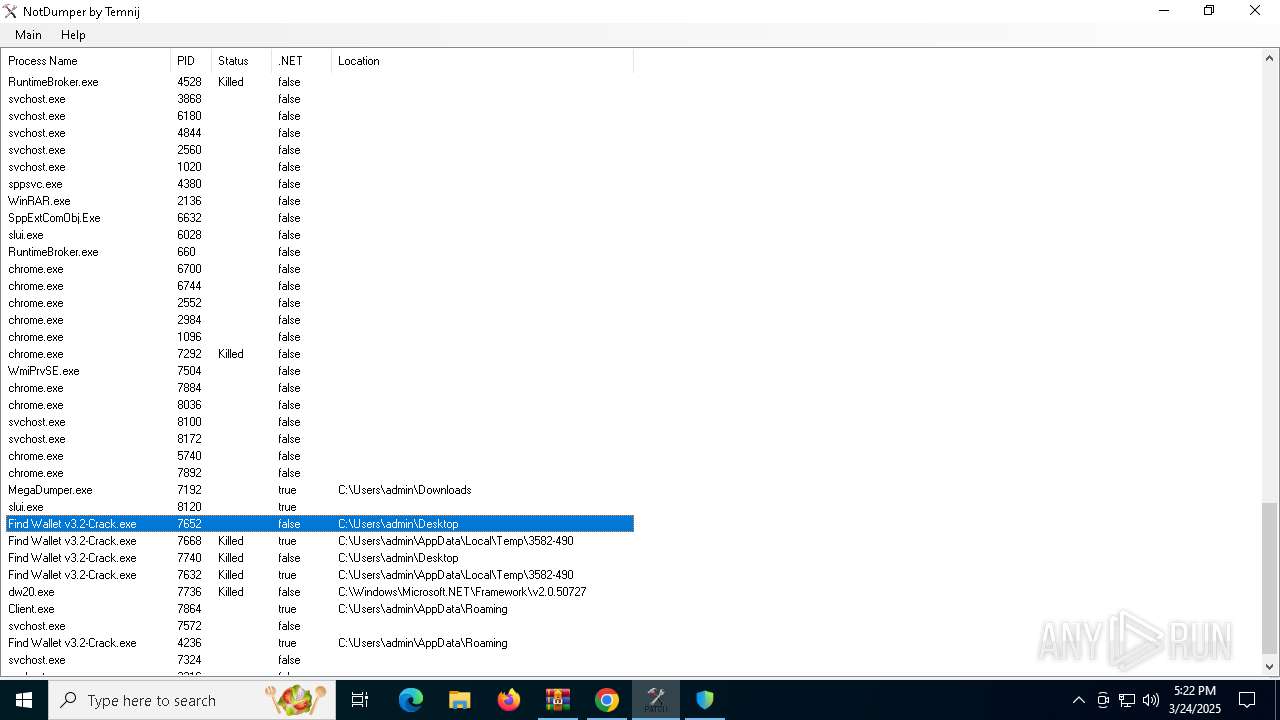
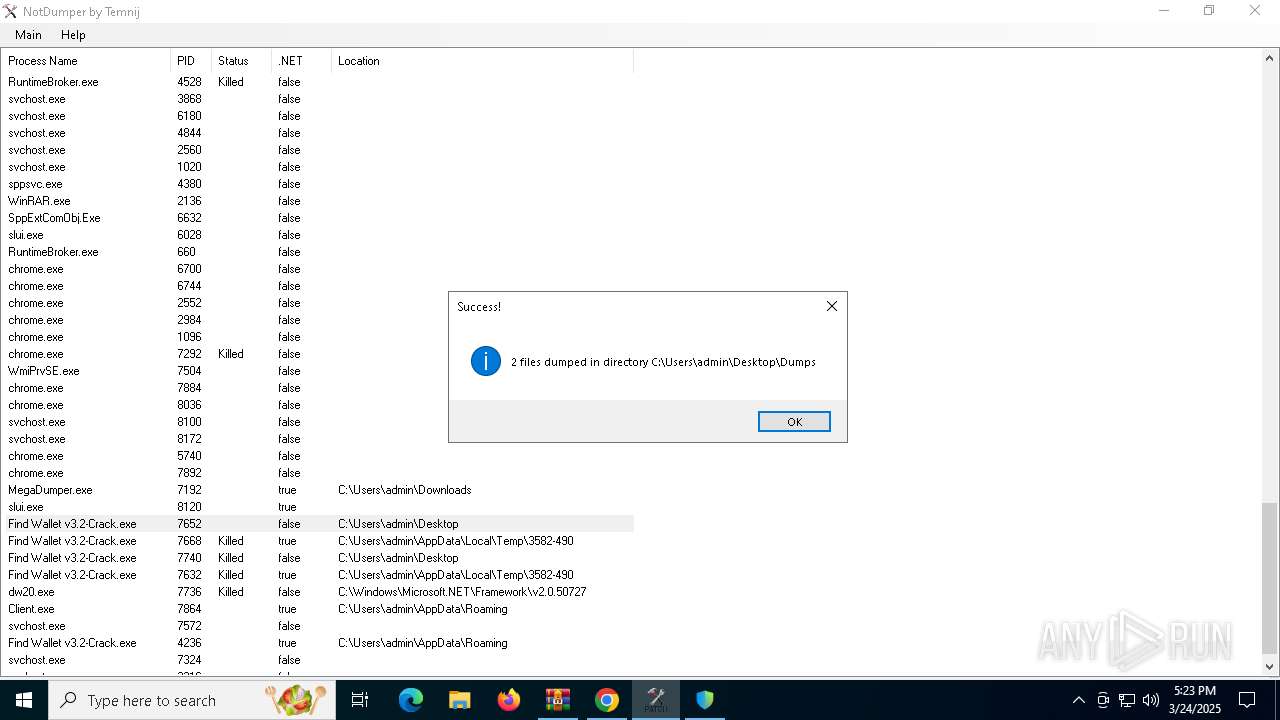
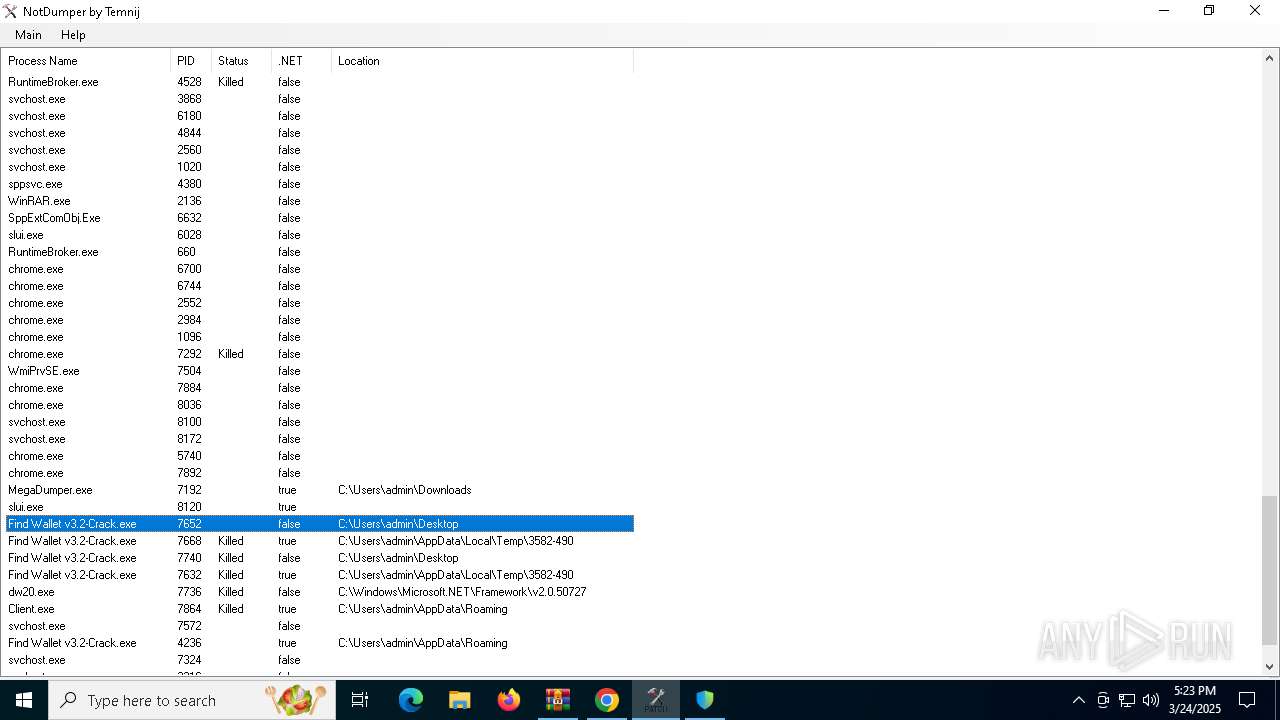
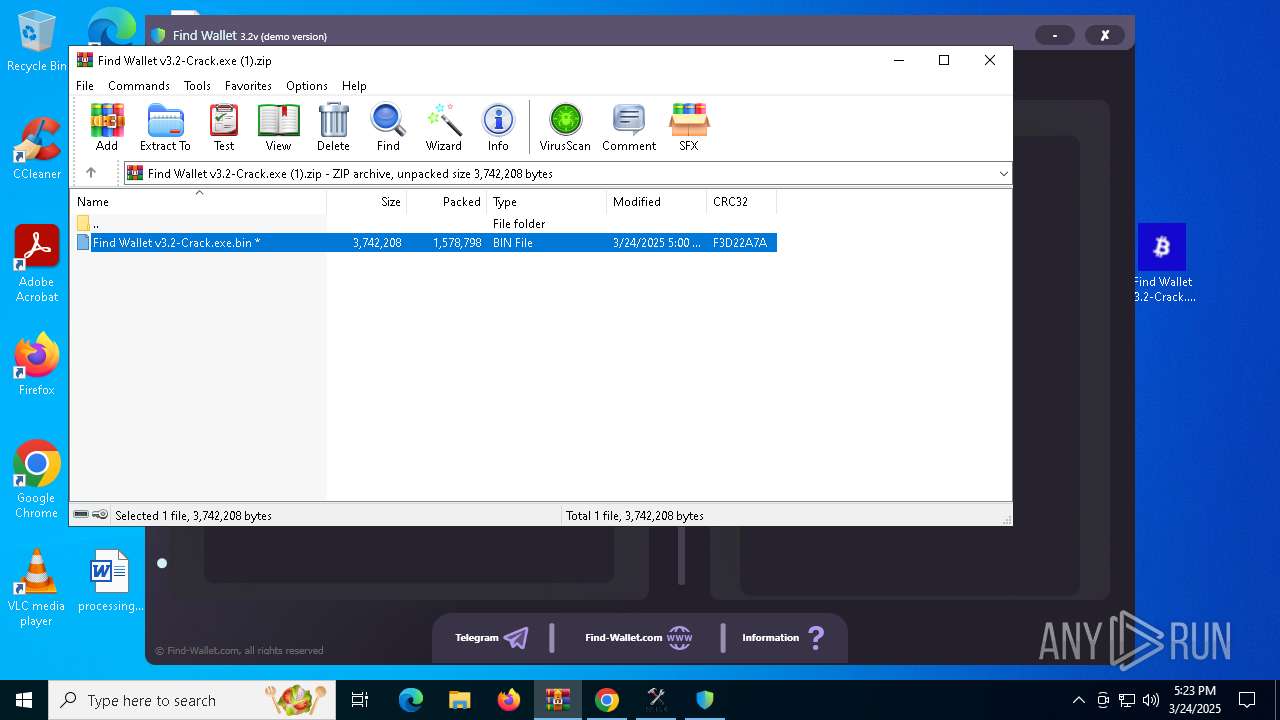
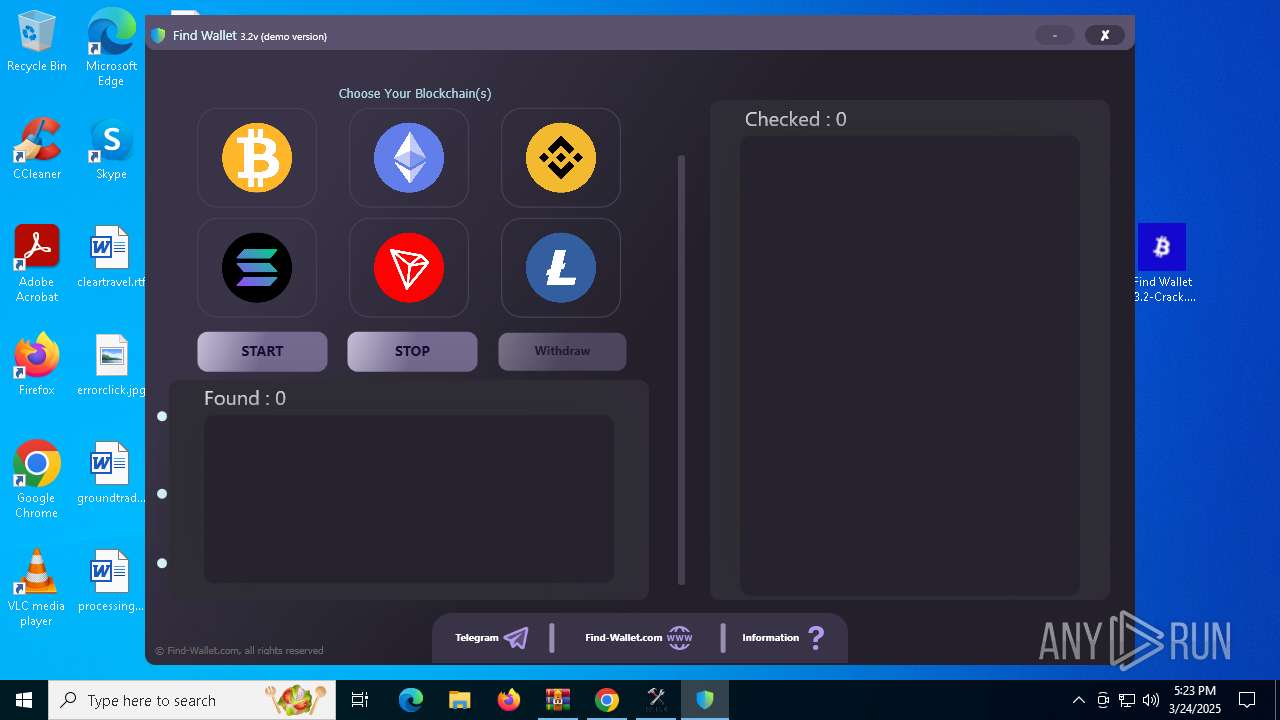
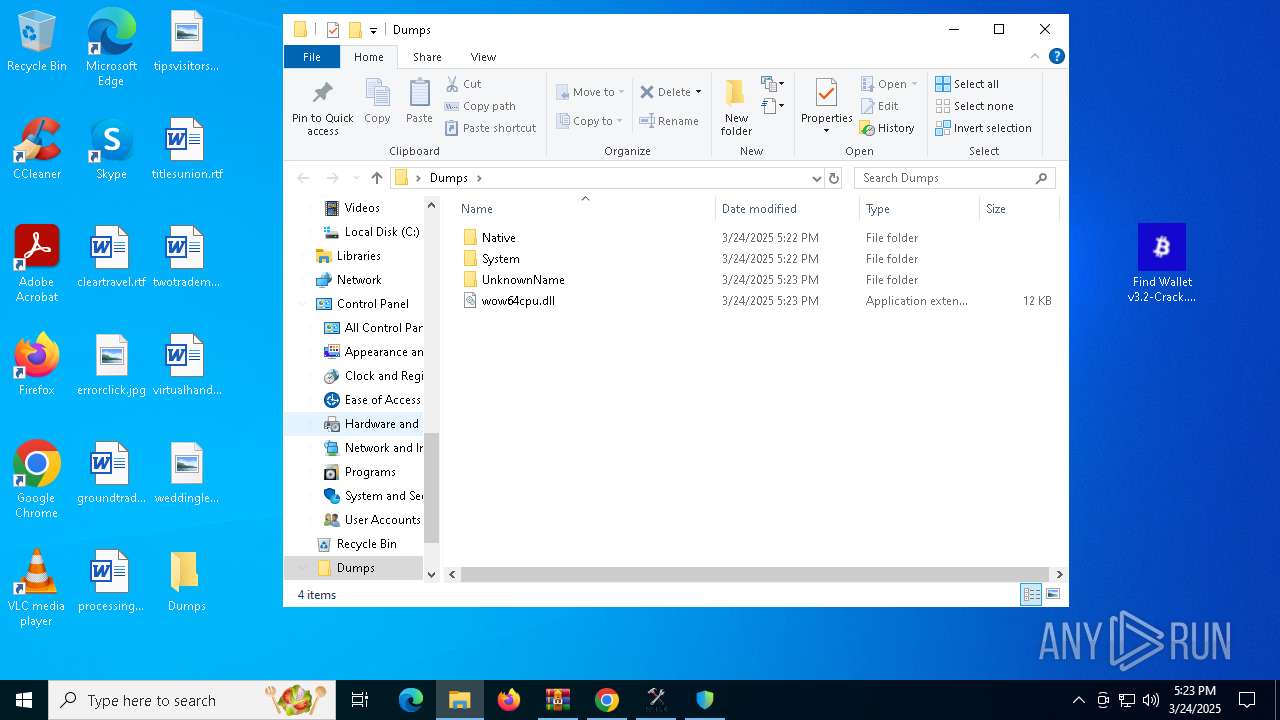
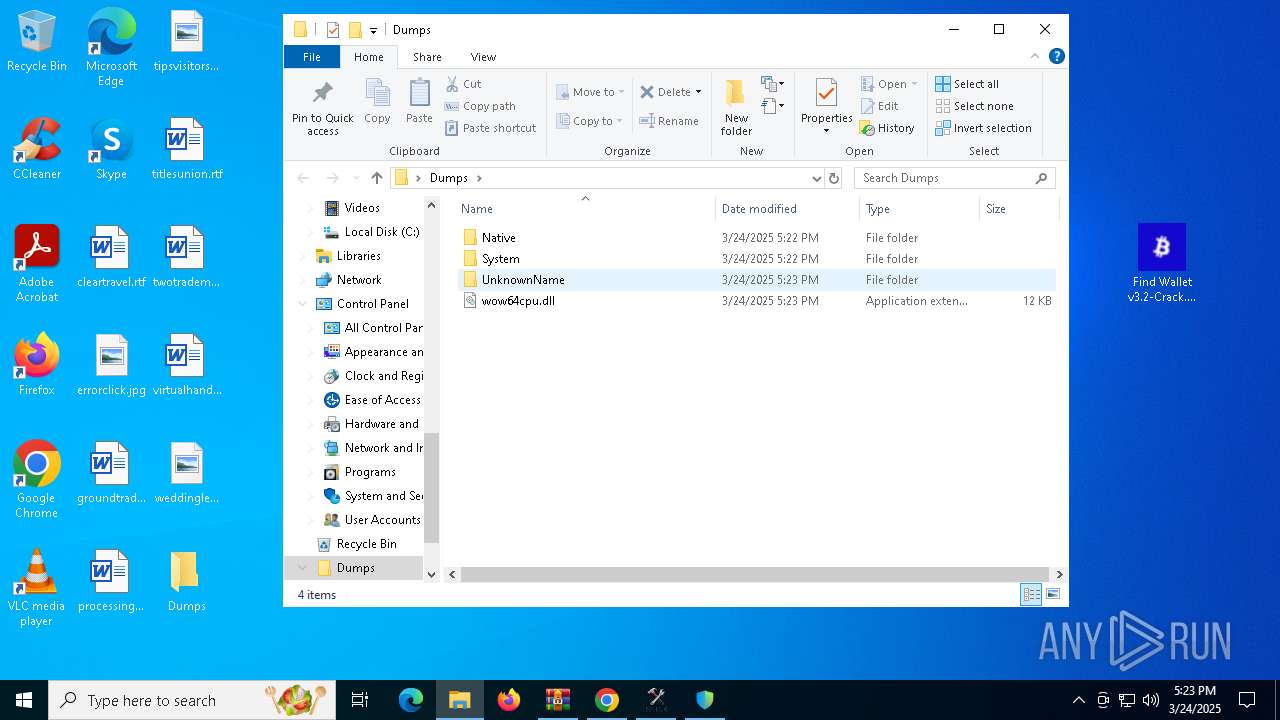
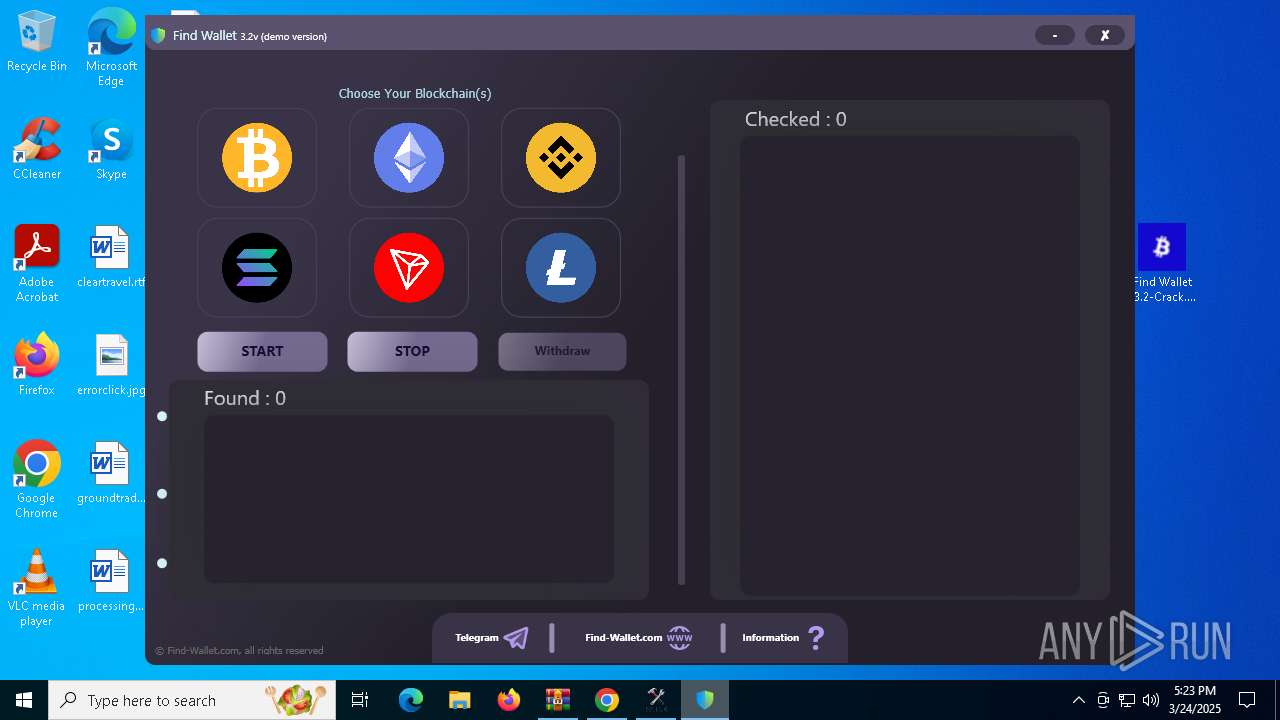
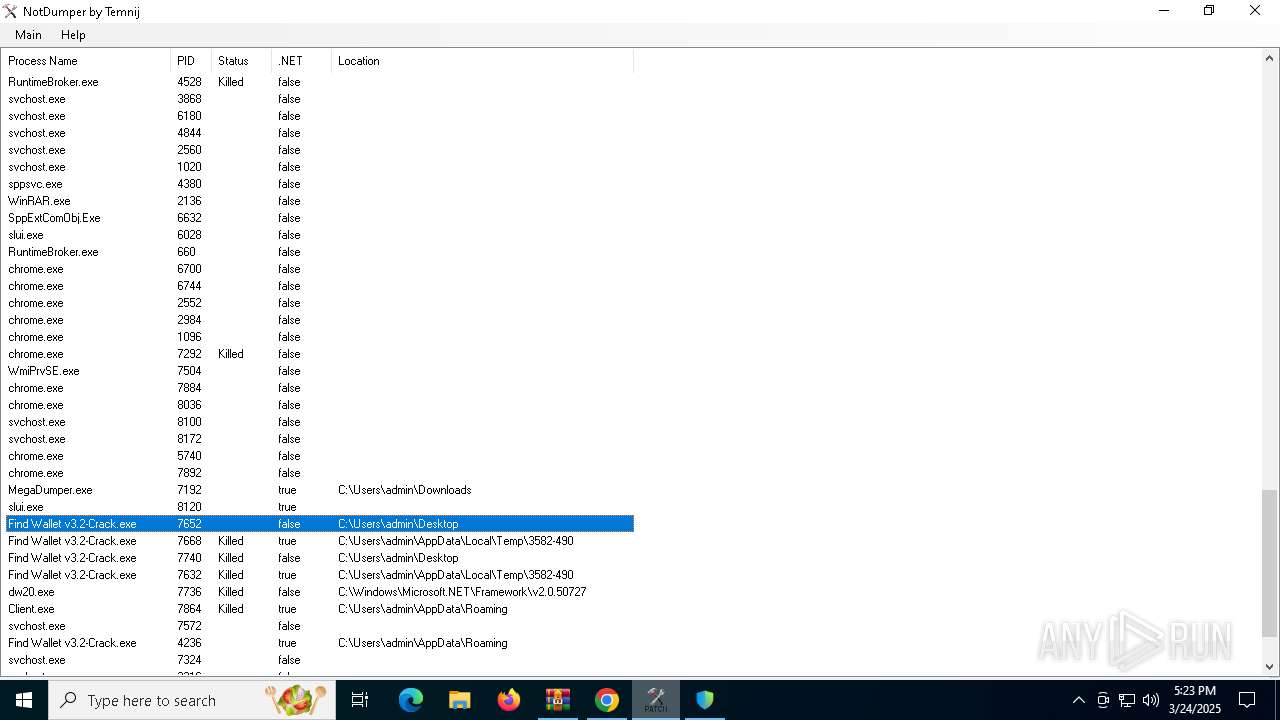
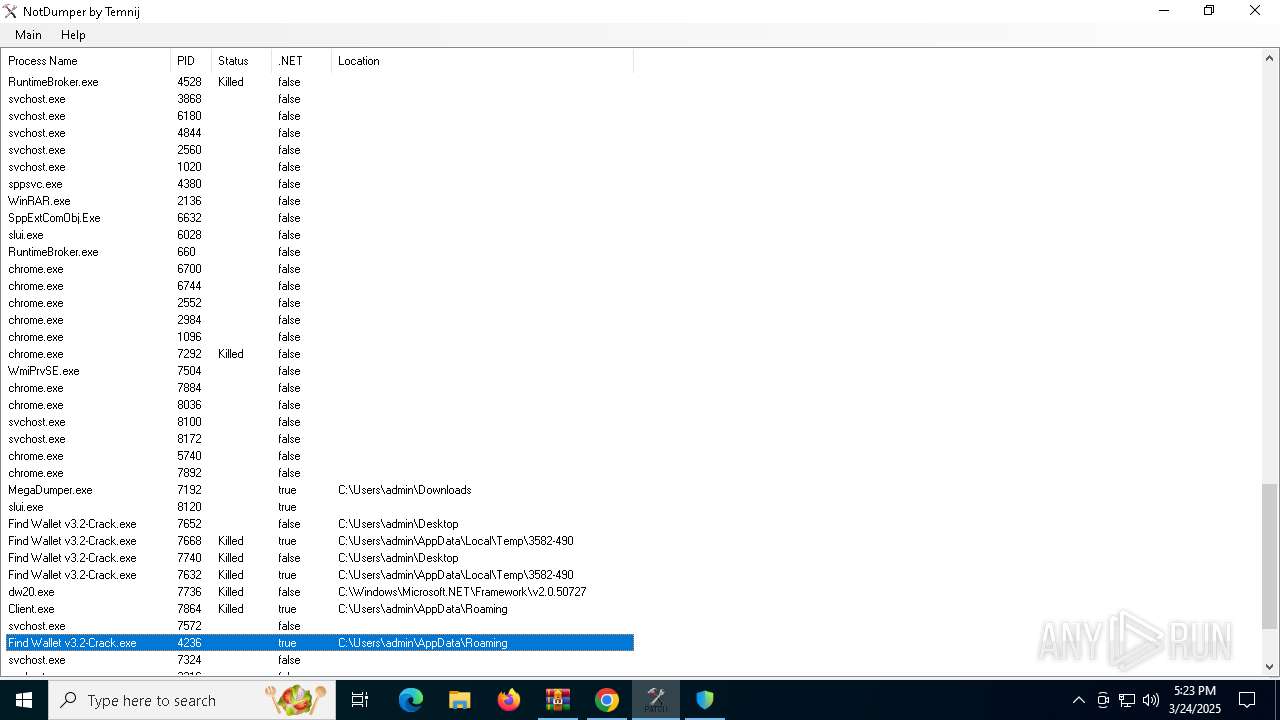
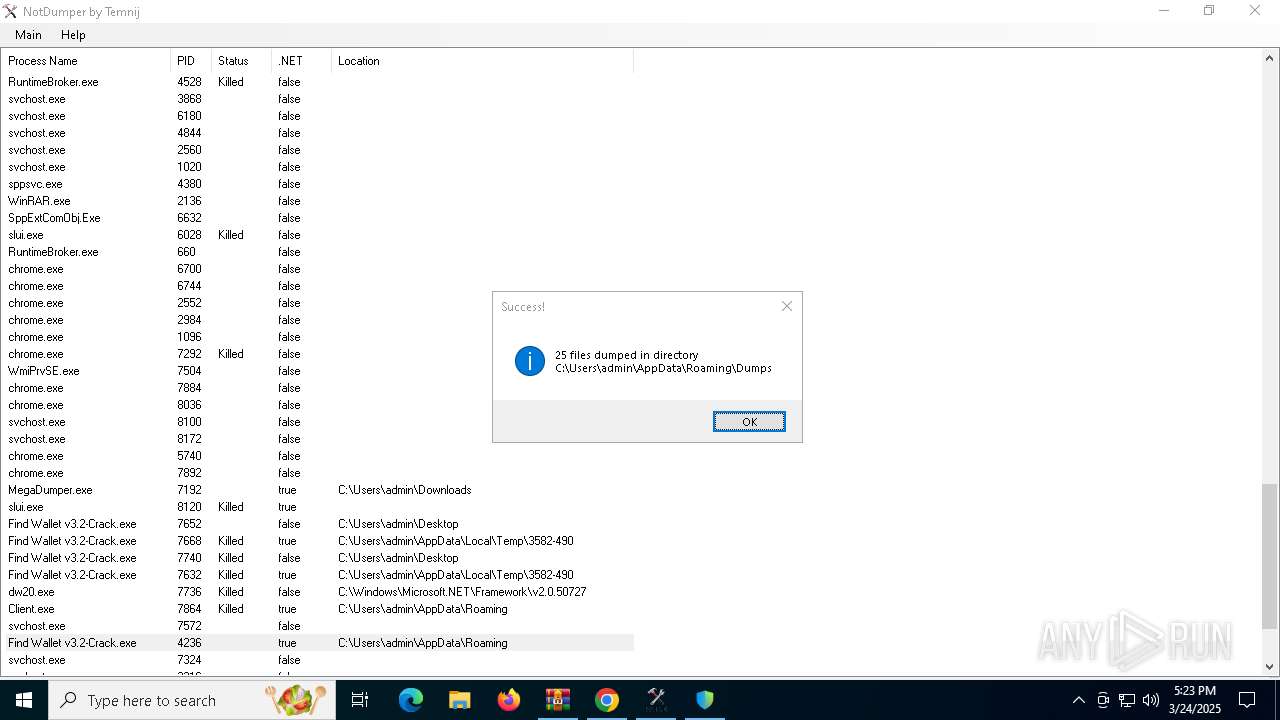
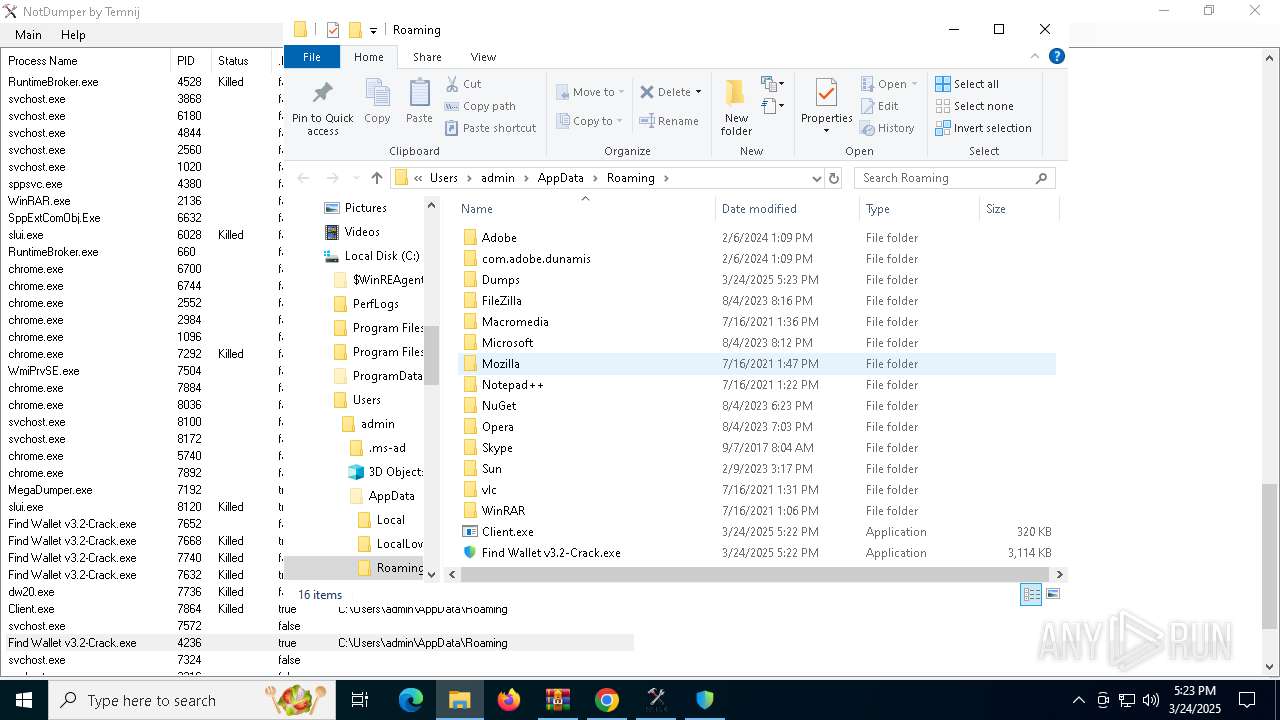
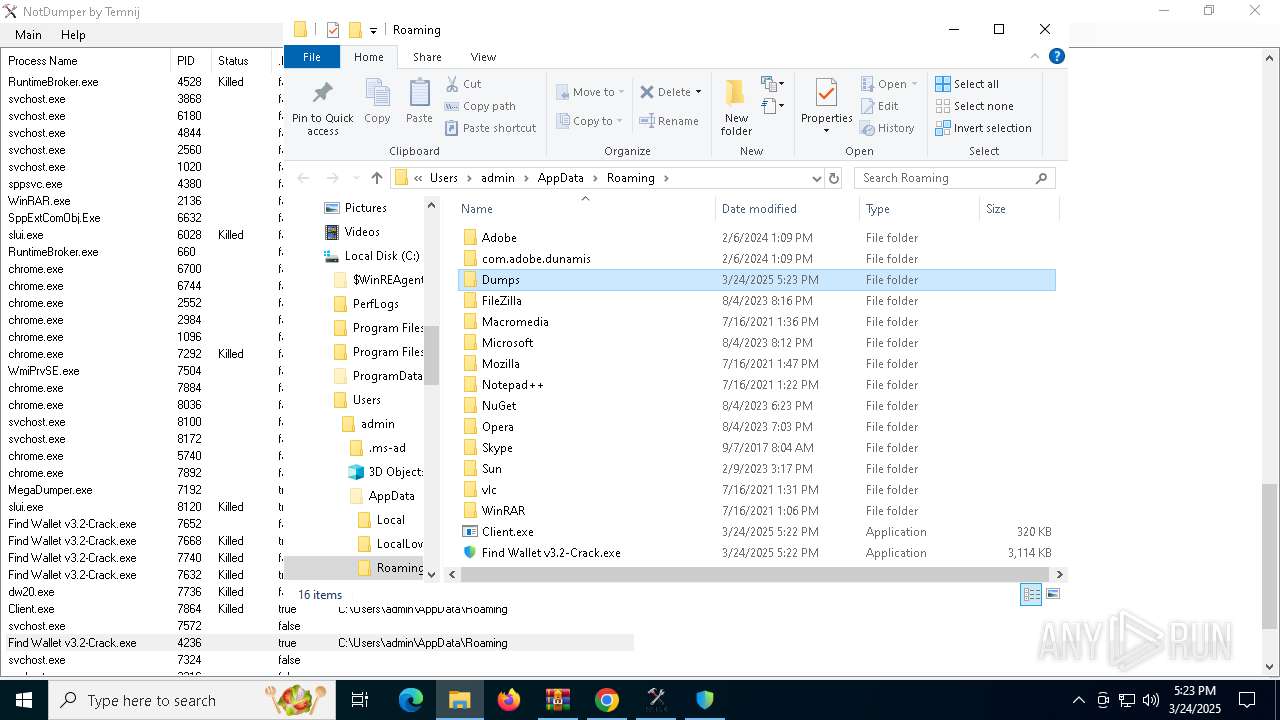
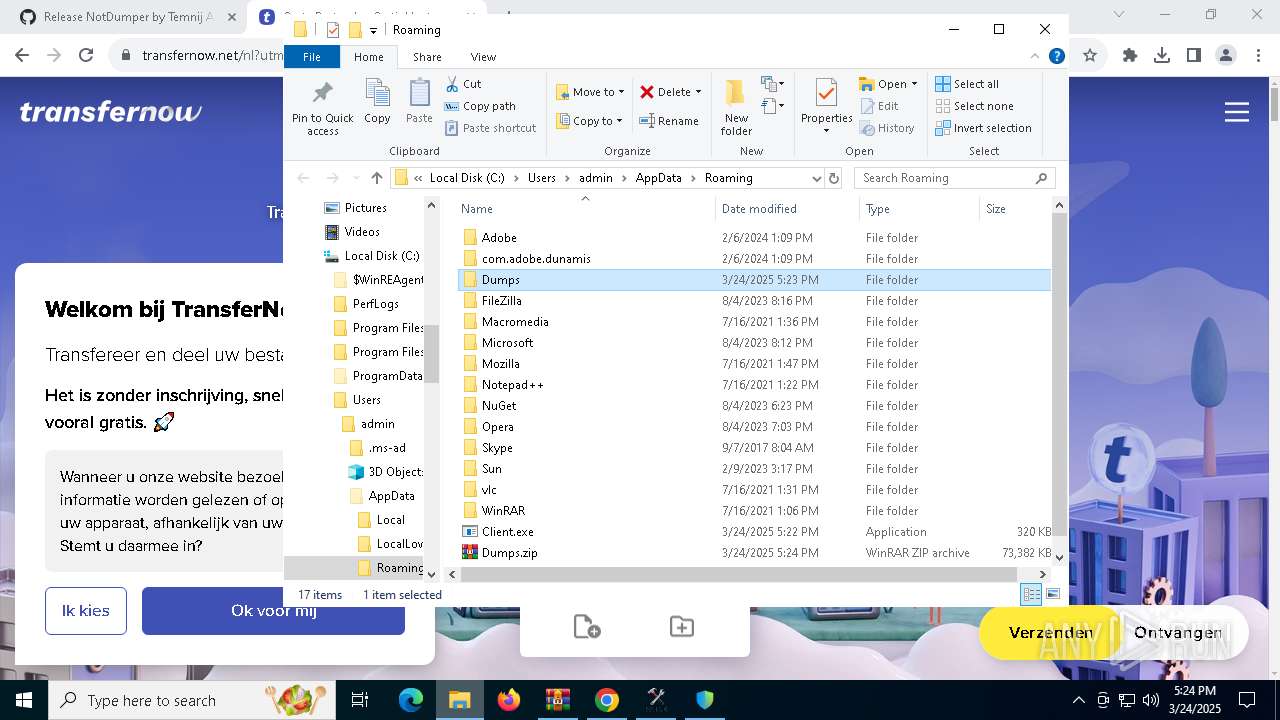
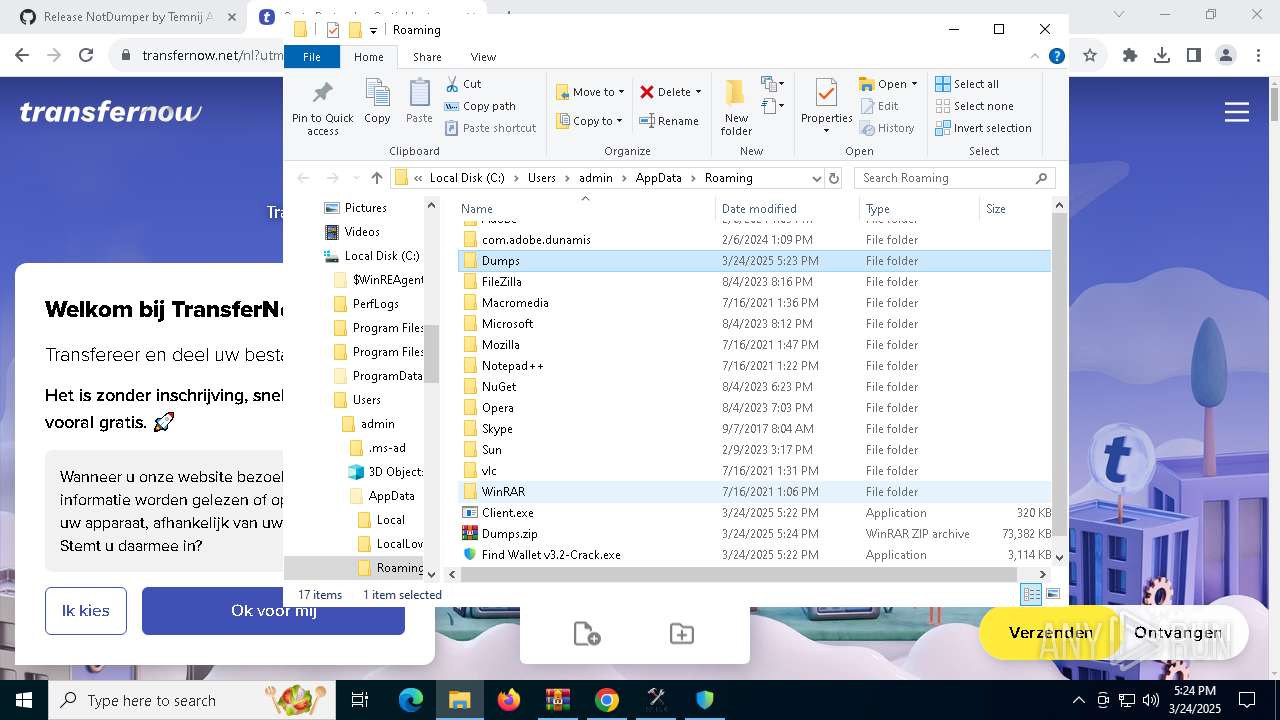
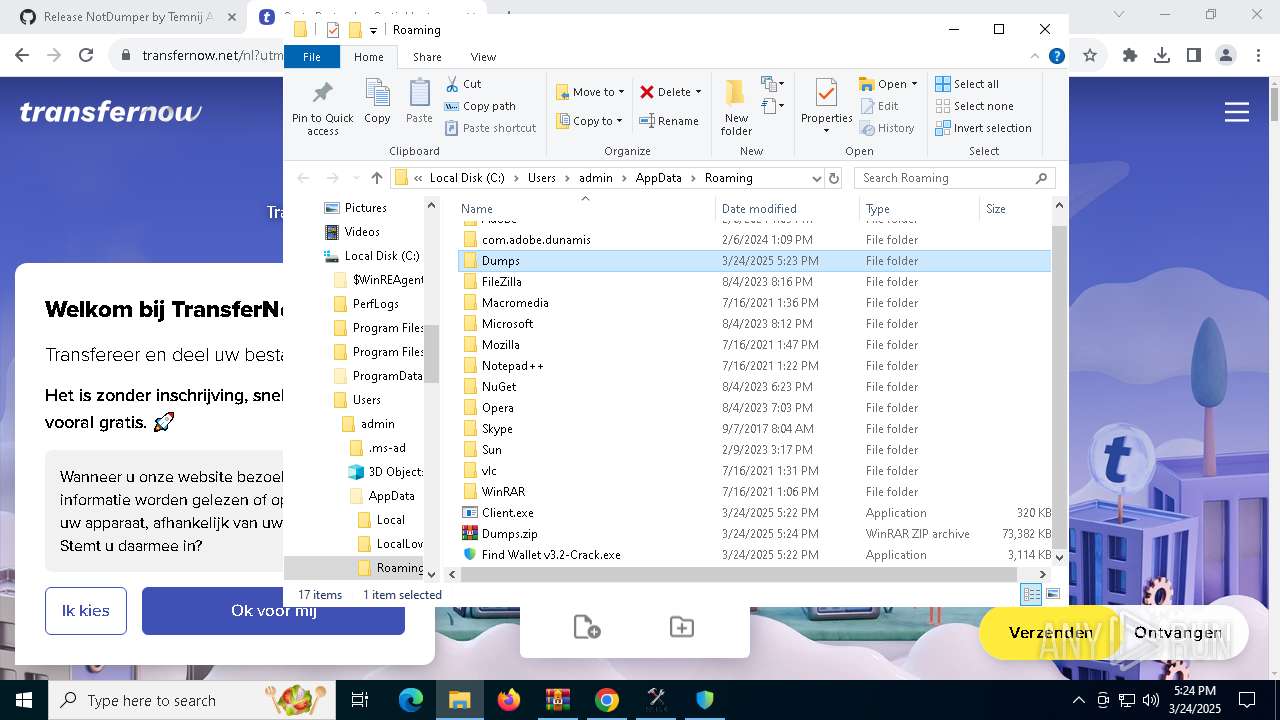
| File name: | Find Wallet v3.2-Crack.exe (1).zip |
| Full analysis: | https://app.any.run/tasks/8a73c6d7-7229-4129-b1db-737ed73810dc |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | March 24, 2025, 17:21:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | A120ED61743037749D09523F8FC3BFE8 |
| SHA1: | 7CAB5C95D64A3FEB7D28497062E787B31C3BAEE7 |
| SHA256: | 43C503336E9AE2118E61467181BF97D14094E1345F25B9DFD15A1B5FF5F75514 |
| SSDEEP: | 49152:NIHju7djxY/PhLHrciIIPu7Z7FL83WPk1nnNFWSxjm/CkBmBv3Y9S5njnMXZ00FG:xBNYnhXIIm7Zx5CnnN0SxjMCkBm9dQB+ |
MALICIOUS
NESHTA mutex has been found
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Find Wallet v3.2-Crack.exe (PID: 7740)
Steals credentials from Web Browsers
- Client.exe (PID: 7864)
Actions looks like stealing of personal data
- Client.exe (PID: 7864)
- Find Wallet v3.2-Crack.exe (PID: 7652)
SUSPICIOUS
Executable content was dropped or overwritten
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Find Wallet v3.2-Crack.exe (PID: 7632)
- MegaDumper.exe (PID: 7192)
Mutex name with non-standard characters
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Find Wallet v3.2-Crack.exe (PID: 7740)
Reads security settings of Internet Explorer
- Find Wallet v3.2-Crack.exe (PID: 7740)
- Find Wallet v3.2-Crack.exe (PID: 7632)
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Find Wallet v3.2-Crack.exe (PID: 4236)
Reads the date of Windows installation
- dw20.exe (PID: 7736)
Write to the desktop.ini file (may be used to cloak folders)
- Client.exe (PID: 7864)
Checks for external IP
- Client.exe (PID: 7864)
- svchost.exe (PID: 2196)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Client.exe (PID: 7864)
There is functionality for taking screenshot (YARA)
- Find Wallet v3.2-Crack.exe (PID: 7652)
Process drops legitimate windows executable
- MegaDumper.exe (PID: 7192)
Possible usage of Discord/Telegram API has been detected (YARA)
- Client.exe (PID: 7864)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2136)
- chrome.exe (PID: 2984)
- chrome.exe (PID: 6700)
- chrome.exe (PID: 7360)
- chrome.exe (PID: 4336)
Checks supported languages
- SearchApp.exe (PID: 2924)
- MegaDumper.exe (PID: 7192)
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Find Wallet v3.2-Crack.exe (PID: 7668)
- Find Wallet v3.2-Crack.exe (PID: 7740)
- Find Wallet v3.2-Crack.exe (PID: 7632)
- dw20.exe (PID: 7736)
- Client.exe (PID: 7864)
- Find Wallet v3.2-Crack.exe (PID: 4236)
Process checks computer location settings
- SearchApp.exe (PID: 2924)
- Find Wallet v3.2-Crack.exe (PID: 7740)
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Find Wallet v3.2-Crack.exe (PID: 7632)
- dw20.exe (PID: 7736)
Manual execution by a user
- chrome.exe (PID: 6700)
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Find Wallet v3.2-Crack.exe (PID: 7740)
- WinRAR.exe (PID: 8180)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 2924)
- MegaDumper.exe (PID: 7192)
- dw20.exe (PID: 7736)
- Client.exe (PID: 7864)
- Find Wallet v3.2-Crack.exe (PID: 4236)
Reads the software policy settings
- SearchApp.exe (PID: 2924)
- slui.exe (PID: 6028)
- Client.exe (PID: 7864)
- dw20.exe (PID: 7736)
Autorun file from Downloads
- chrome.exe (PID: 6700)
- chrome.exe (PID: 496)
Reads the computer name
- MegaDumper.exe (PID: 7192)
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Find Wallet v3.2-Crack.exe (PID: 7740)
- dw20.exe (PID: 7736)
- Find Wallet v3.2-Crack.exe (PID: 7632)
- Client.exe (PID: 7864)
- Find Wallet v3.2-Crack.exe (PID: 4236)
Create files in a temporary directory
- Find Wallet v3.2-Crack.exe (PID: 7652)
- Client.exe (PID: 7864)
Application launched itself
- chrome.exe (PID: 6700)
Creates files or folders in the user directory
- Find Wallet v3.2-Crack.exe (PID: 7632)
- Client.exe (PID: 7864)
- dw20.exe (PID: 7736)
- MegaDumper.exe (PID: 7192)
Reads product name
- dw20.exe (PID: 7736)
Creates files in the program directory
- dw20.exe (PID: 7736)
Disables trace logs
- Client.exe (PID: 7864)
Reads Environment values
- dw20.exe (PID: 7736)
Reads CPU info
- dw20.exe (PID: 7736)
- Client.exe (PID: 7864)
Checks proxy server information
- dw20.exe (PID: 7736)
- Find Wallet v3.2-Crack.exe (PID: 4236)
- Client.exe (PID: 7864)
- slui.exe (PID: 8120)
The sample compiled with english language support
- MegaDumper.exe (PID: 7192)
- chrome.exe (PID: 7360)
- chrome.exe (PID: 4336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7864) Client.exe
Telegram-Tokens (1)7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE
Telegram-Info-Links
7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE
Get info about bothttps://api.telegram.org/bot7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE/getMe
Get incoming updateshttps://api.telegram.org/bot7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE/getUpdates
Get webhookhttps://api.telegram.org/bot7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE
End-PointsendDocument
Args
chat_id (1)6022885401
caption (1)==== RL STEALER ====
⏰ Date => 03/24/2025 5:22
💻System => Windows 10 Pro (64 Bit)
👤 User => admin
🆔 PC => DESKTOP-JGLLJLD
🏴 Country => [The Netherlands]
🔍 IP => 212.30.37.95
📝 Language => 🇺🇸 en-US
🔓 Antivirus => W
Token7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE
End-PointsendDocument
Args
Token7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE
End-PointsendDocument
Args
chat_id (1)6022885401
caption (1)==== RL STEALER ====
Token7382635608:AAH72k3AVhMfbaRzEcdg26C7uJVMHPOHjiE
End-PointsendDocument
Args
chat_id (1)6022885401
caption (1)==== RL STEALER ====
⏰ Date => 03/24/2025 5:22
💻System => Windows 10 Pro (64 Bit)
👤 User =%3
Telegram-Responses
oktrue
result
message_id4805
from
id7382635608
is_bottrue
first_nameNew Wallet Finder
usernameWallet_finder_0_1_bot
chat
id6022885401
first_nameJznif.jixz
last_nameOfficial
usernameUnknown_lutin
typeprivate
date1742836970
document
file_nameC UsersadminAppDataRoamingDESKTOP-JGLLJLD@[The Netherlands].zip
mime_typeapplication/zip
file_idBQACAgUAAxkDAAISxWfhlOpAEbMYI2yh24epUTiucHqQAAJFFgACwwYIV3zgDhtjtzDoNgQ
file_unique_idAgADRRYAAsMGCFc
file_size106895
caption==== RL STEALER ====
⏰ Date => 03/24/2025 5:22
💻System => Windows 10 Pro (64 Bit)
👤 User => admin
🆔 PC => DESKTOP-JGLLJLD
🏴 Country => [The Netherlands]
🔍 IP => 212.30.37.95
📝 Language => 🇺🇸 en-US
🔓 Antivirus => Windows Defender.
===={ User Data }====
📂 FileGrabber => 29
📦 Telegram => ❌...
caption_entities
offset167
length12
typeurl
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:03:24 17:00:32 |
| ZipCRC: | 0xf3d22a7a |
| ZipCompressedSize: | 1578798 |
| ZipUncompressedSize: | 3742208 |
| ZipFileName: | Find Wallet v3.2-Crack.exe.bin |
Total processes
207
Monitored processes
64
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3256 --field-trial-handle=1924,i,11336921531986820102,15044132351074195836,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=39 --mojo-platform-channel-handle=7108 --field-trial-handle=1924,i,11336921531986820102,15044132351074195836,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2320 --field-trial-handle=1924,i,11336921531986820102,15044132351074195836,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=40 --mojo-platform-channel-handle=7372 --field-trial-handle=1924,i,11336921531986820102,15044132351074195836,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Find Wallet v3.2-Crack.exe (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1920 --field-trial-handle=1924,i,11336921531986820102,15044132351074195836,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2924 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2072 --field-trial-handle=1924,i,11336921531986820102,15044132351074195836,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=41 --mojo-platform-channel-handle=7036 --field-trial-handle=1924,i,11336921531986820102,15044132351074195836,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
29 752
Read events
29 533
Write events
190
Delete events
29
Modification events
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Find Wallet v3.2-Crack.exe (1).zip | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
Executable files
87
Suspicious files
983
Text files
245
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\pNXV2ymlrFEAOVLUgJkRBRwYFkY[1].js | s | |
MD5:1C4D6CA041F994E18637E8F5566A1F3F | SHA256:B87B991D28DAFD48331B81C759EA51D00E0D9256CD8593B3A9A56B1129F3B9DF | |||
| 2136 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2136.20278\Find Wallet v3.2-Crack.exe.bin | executable | |
MD5:A5AAD19F2467992040DCE284A1D34016 | SHA256:6131F59ADE95F5AAF4F78C1CBD31F033AE508BAE3418D30AD9B7E35E3F96BEB6 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:29DE55D0A7A581B230CC2D70686CD03A | SHA256:D9F161C1FE8751953E4F3819993C16C2A61A0121B527E09862C34C89E7B6C677 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\vOJNaIfAXvJzmnBm845ss-M9YR8[1].css | text | |
MD5:87BBB1A289EDC24C9F06B88229765467 | SHA256:85B291C46F9D1EEEC71DB839F649D748F48B203EA836F3ACE3B9B761947D960C | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\Q6mzjrsCw2J4u7BHEvcLILQ0jdw[1].css | text | |
MD5:3D1822E87F43F7997F6BC42A8BB7B4B9 | SHA256:9D37A302F2CF56F4ED0F97A532CB0641F738FC30742FDEDEBED85551A911F575 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:908111EB0FFB1360D5DD61279C21703E | SHA256:1ED87CF425DED994B05A842271AB4D28A76F399E571688CF2E7B186F70DC3059 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\fvNdnrKxhhxDQUEi09cCaSWpzzE[1].css | text | |
MD5:15DC838A1A66277F9F4D915124DFFBBC | SHA256:9C947D5F732431197DA9DB1F159CB3D4CDC5DBFE55FDC0A9513E571FF31236A1 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\-iNIzuEypRdgRJ6xnyVHizZ3bpM.br[1].js | binary | |
MD5:E86ABEFE45E62F7E2F865D8A344D0B6F | SHA256:5D54790C856CE13811590E18AC3B0ACEEFEFB61258852490F4C5C60748365E89 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\Init[1].htm | html | |
MD5:B26CB7C39888D16E0D122E3D5E39397D | SHA256:3F01D0C53E72AB65558BFFC8741B713DDBCE80758EC7CA3DA5E9C6F2D7ACAC28 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\QNBBNqWD9F_Blep-UqQSqnMp-FI[1].css | text | |
MD5:77373397A17BD1987DFCA2E68D022ECF | SHA256:A319AF2E953E7AFDA681B85A62F629A5C37344AF47D2FCD23AB45E1D99497F13 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
221
DNS requests
211
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.110.122:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7272 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7272 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7736 | dw20.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7736 | dw20.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7864 | Client.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/xml | unknown | — | — | whitelisted |
7864 | Client.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/xml | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 88.221.110.122:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5344 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7864 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Checker Domain (freegeoip .app) |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain Domain in DNS Lookup (ipbase .com) |
7864 | Client.exe | Potentially Bad Traffic | ET INFO Observed External IP Lookup Domain (ipbase .com in TLS SNI) |
7864 | Client.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] SNI External IP Domain Lookup (freegeoip .app) |
7864 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
7864 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
7864 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
7864 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |
7864 | Client.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |