| File name: | new 1.js |
| Full analysis: | https://app.any.run/tasks/c505b68d-9a47-4472-a816-d25629558989 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2019, 10:57:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with no line terminators |
| MD5: | FA9FF48989DBF7306D4F27E8CAD98120 |
| SHA1: | 0F23888E4C01D17A31FC1581955BE41DE747B9A3 |
| SHA256: | 43BBDF589DB9D532FD420C639B7ECB2141A2FB54E2C81FE4CAB012F7DC68FFE7 |
| SSDEEP: | 24:MB/cdYciIN+iAUx/e5YFu3FVPi+U010/+jHoarzSGG+8y5/A/XS2:dwIQiTSYePP/5EaD8y5Id |
MALICIOUS
Changes settings of System certificates
- WScript.exe (PID: 1524)
SUSPICIOUS
Uses ATTRIB.EXE to modify file attributes
- WScript.exe (PID: 1524)
Adds / modifies Windows certificates
- WScript.exe (PID: 1524)
Creates files in the user directory
- WScript.exe (PID: 1524)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 1524)
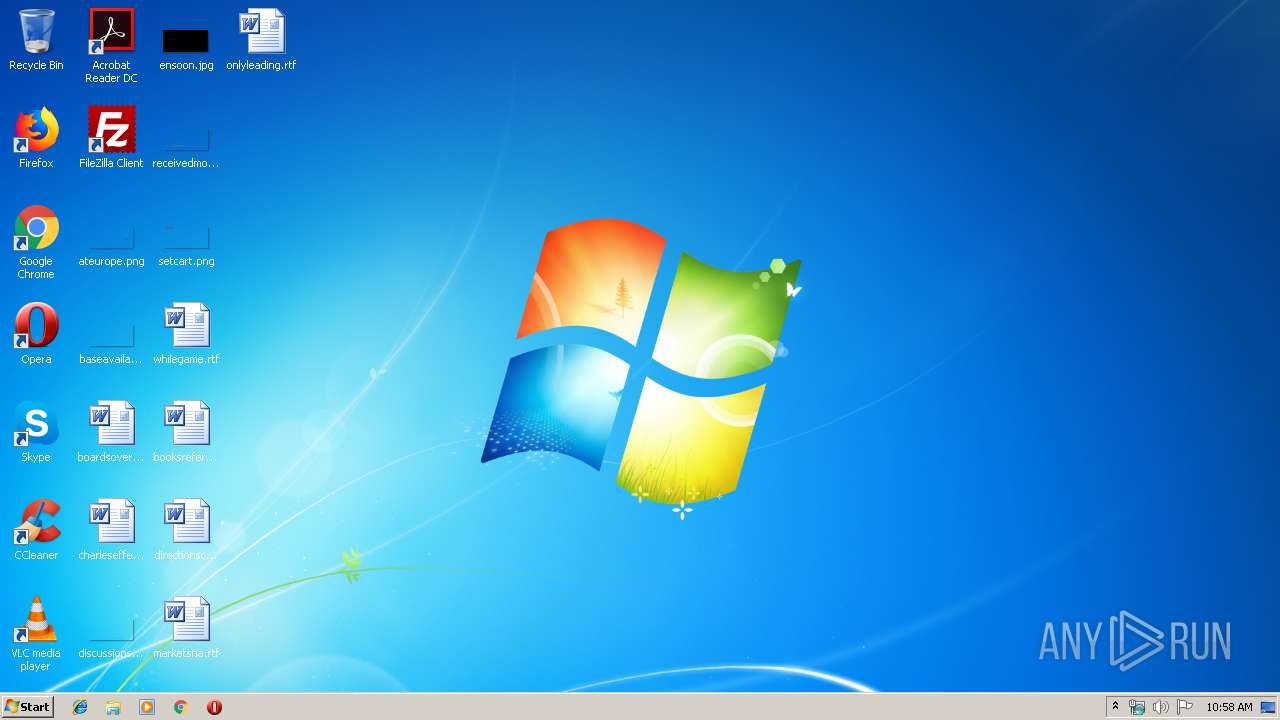
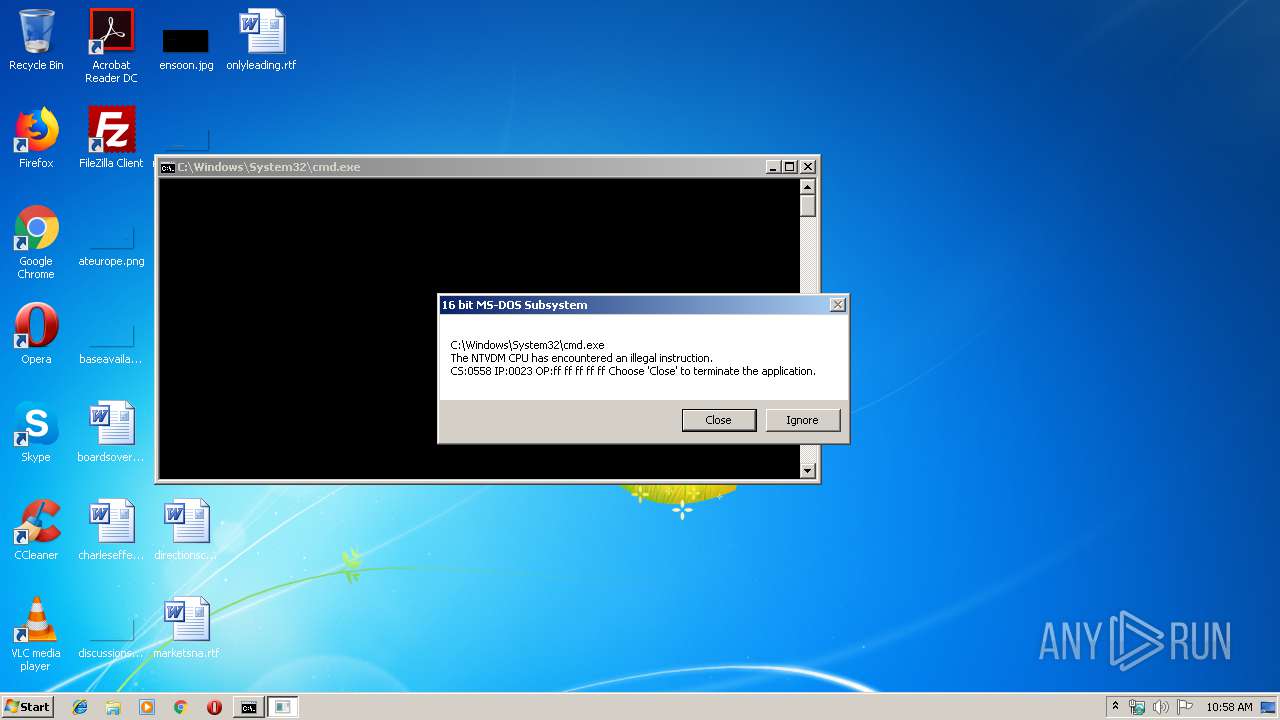
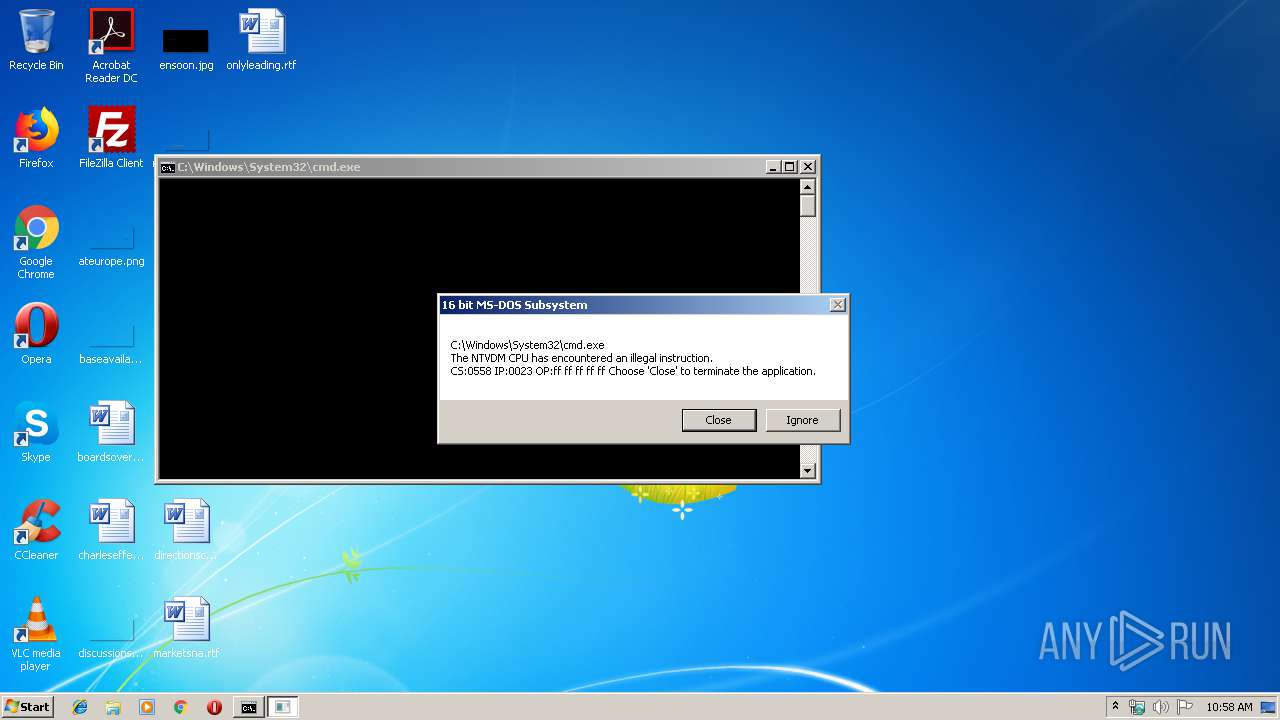
Executes application which crashes
- cmd.exe (PID: 2444)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | attrib +H "C:\Users\admin\AppData\Roaming\stub.exe" | C:\Windows\System32\attrib.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1296 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\system32\ntvdm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1524 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\new 1.js" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2444 | cmd /Q /V:OFF /C call "C:\Users\admin\AppData\Roaming\stub.exe" >nul | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2960 | attrib -H "C:\Users\admin\AppData\Roaming\stub.exe" | C:\Windows\System32\attrib.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
93
Read events
59
Write events
32
Delete events
2
Modification events
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (1524) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1296 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs8D33.tmp | — | |
MD5:— | SHA256:— | |||
| 1296 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs8D44.tmp | — | |
MD5:— | SHA256:— | |||
| 1524 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@discordapp[1].txt | text | |
MD5:— | SHA256:— | |||
| 1524 | WScript.exe | C:\Users\admin\AppData\Roaming\stub.exe | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1524 | WScript.exe | 104.16.13.231:443 | cdn.discordapp.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |