| File name: | 08829182025.pdf |
| Full analysis: | https://app.any.run/tasks/2c0469db-2b86-46ec-a53c-21e271ad98e8 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 13:19:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.1, 1 page(s) |
| MD5: | 82B5C5BFCA53C75F256A4540D54C5BBD |
| SHA1: | 0B27BE92D4619D5321EFA4E53EAEED61F41BFF3C |
| SHA256: | 43A8CC1A5492DCDC5FF4039E7923637A472E0D10B7F1CBFD3BF07267E1F662D1 |
| SSDEEP: | 49152:vGpwIOUzehobXez2/mEubYX60xUxTpJme0qhHgaF8E737XHNxMGHbCLYVFD:vGeI53OzcAuWTpJme0sHgk8E7378G4y |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 4892)
- powershell.exe (PID: 3012)
- powershell.exe (PID: 7848)
- powershell.exe (PID: 7468)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 8316)
Changes powershell execution policy (Bypass)
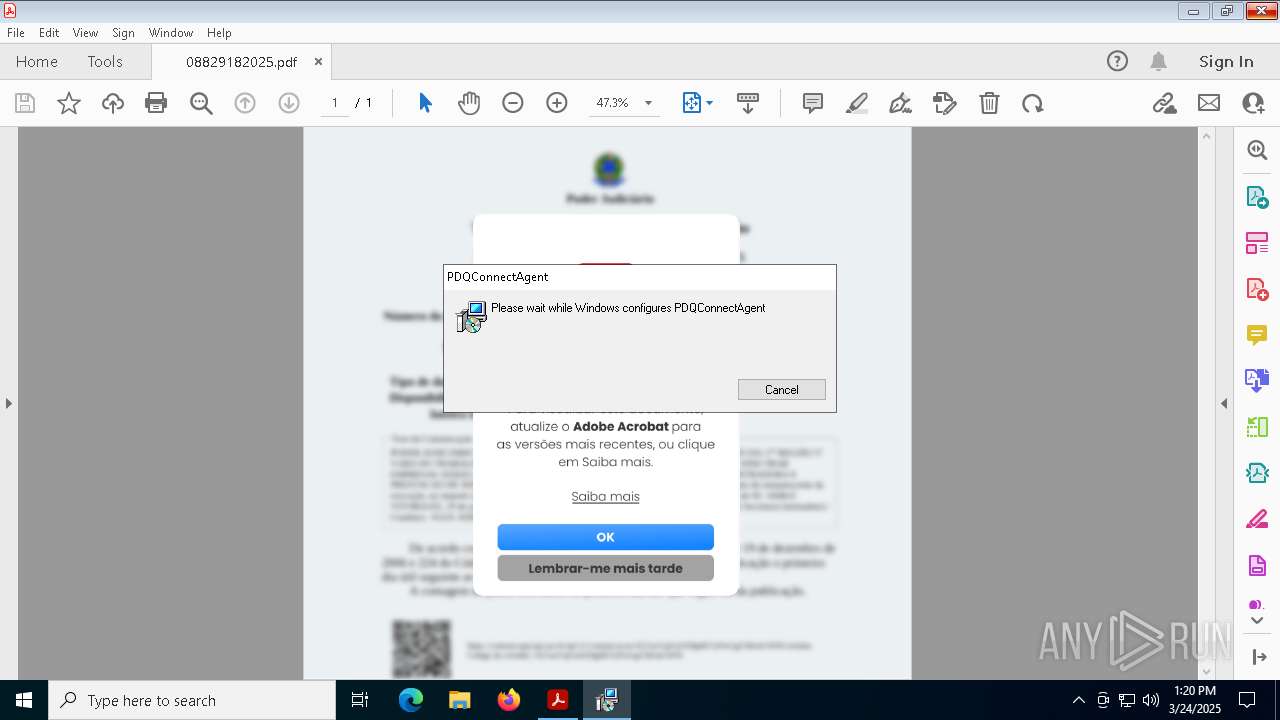
- pdq-connect-agent.exe (PID: 5392)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 8796)
- pdq-connect-agent.exe (PID: 4812)
- pdq-connect-updater.exe (PID: 3268)
- pdq-connect-agent.exe (PID: 5392)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 5008)
- msiexec.exe (PID: 7828)
- msiexec.exe (PID: 7408)
- msiexec.exe (PID: 7480)
Executable content was dropped or overwritten
- rundll32.exe (PID: 4652)
- rundll32.exe (PID: 1676)
- rundll32.exe (PID: 7992)
- rundll32.exe (PID: 5960)
- rundll32.exe (PID: 9080)
- rundll32.exe (PID: 840)
- pdq-connect-agent.exe (PID: 4812)
- rundll32.exe (PID: 8736)
- rundll32.exe (PID: 8624)
- rundll32.exe (PID: 2772)
- rundll32.exe (PID: 7148)
- rundll32.exe (PID: 2288)
- rundll32.exe (PID: 9168)
- rundll32.exe (PID: 2516)
- rundll32.exe (PID: 4244)
Windows service management via SC.EXE
- sc.exe (PID: 8772)
- sc.exe (PID: 1196)
PDQConnect is probably used for system patching and software deployment
- sc.exe (PID: 8772)
- sc.exe (PID: 1196)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6964)
Starts SC.EXE for service management
- rundll32.exe (PID: 9080)
- rundll32.exe (PID: 2516)
Starts POWERSHELL.EXE for commands execution
- pdq-connect-agent.exe (PID: 5392)
The process hide an interactive prompt from the user
- pdq-connect-agent.exe (PID: 5392)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 4892)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4172)
The process hides Powershell's copyright startup banner
- pdq-connect-agent.exe (PID: 5392)
The process bypasses the loading of PowerShell profile settings
- pdq-connect-agent.exe (PID: 5392)
INFO
Application launched itself
- Acrobat.exe (PID: 7332)
- AcroCEF.exe (PID: 7792)
- msedge.exe (PID: 7180)
- msedge.exe (PID: 8992)
- msiexec.exe (PID: 6964)
Reads the computer name
- identity_helper.exe (PID: 9204)
- msiexec.exe (PID: 6964)
- identity_helper.exe (PID: 8680)
- pdq-connect-updater.exe (PID: 3268)
- pdq-connect-agent.exe (PID: 5392)
Checks supported languages
- identity_helper.exe (PID: 9204)
- msiexec.exe (PID: 6964)
- msiexec.exe (PID: 5008)
- msiexec.exe (PID: 7828)
- identity_helper.exe (PID: 8680)
- pdq-connect-updater.exe (PID: 3268)
- msiexec.exe (PID: 7480)
- pdq-connect-agent.exe (PID: 5392)
- ShellExperienceHost.exe (PID: 8436)
Reads Environment values
- identity_helper.exe (PID: 9204)
- identity_helper.exe (PID: 8680)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8604)
- BackgroundTransferHost.exe (PID: 8940)
- BackgroundTransferHost.exe (PID: 8900)
- BackgroundTransferHost.exe (PID: 8364)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 8940)
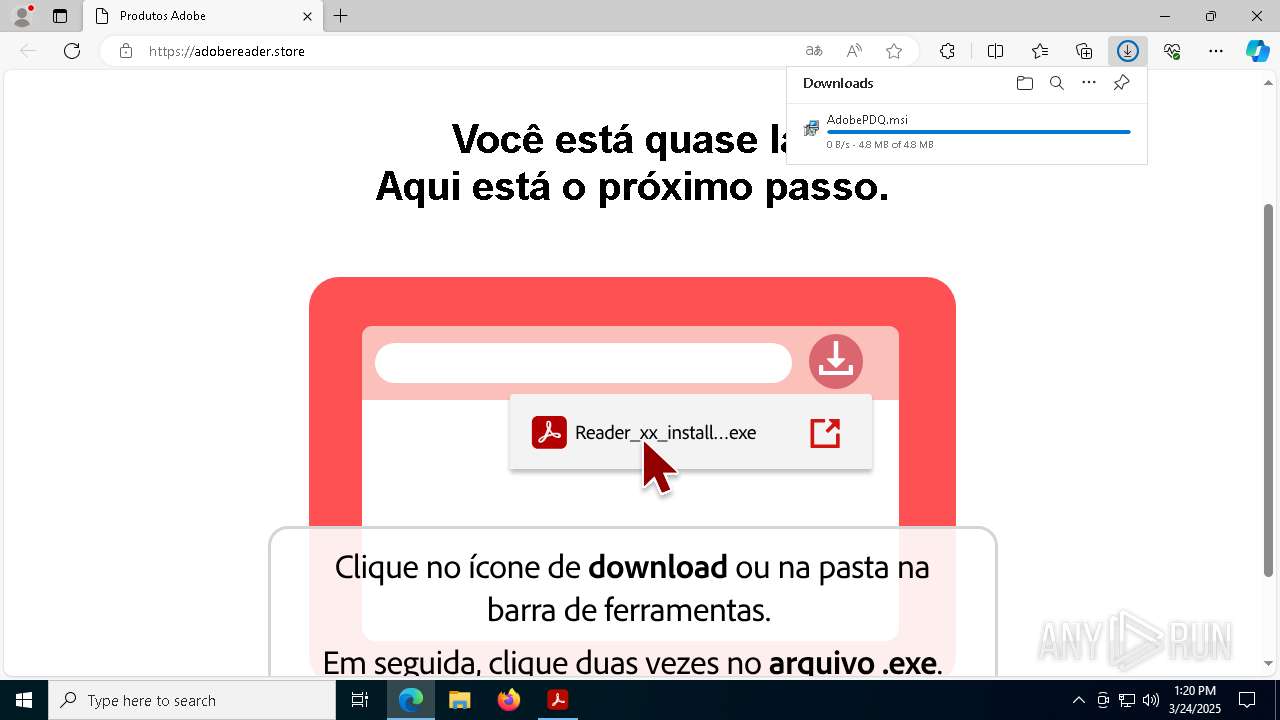
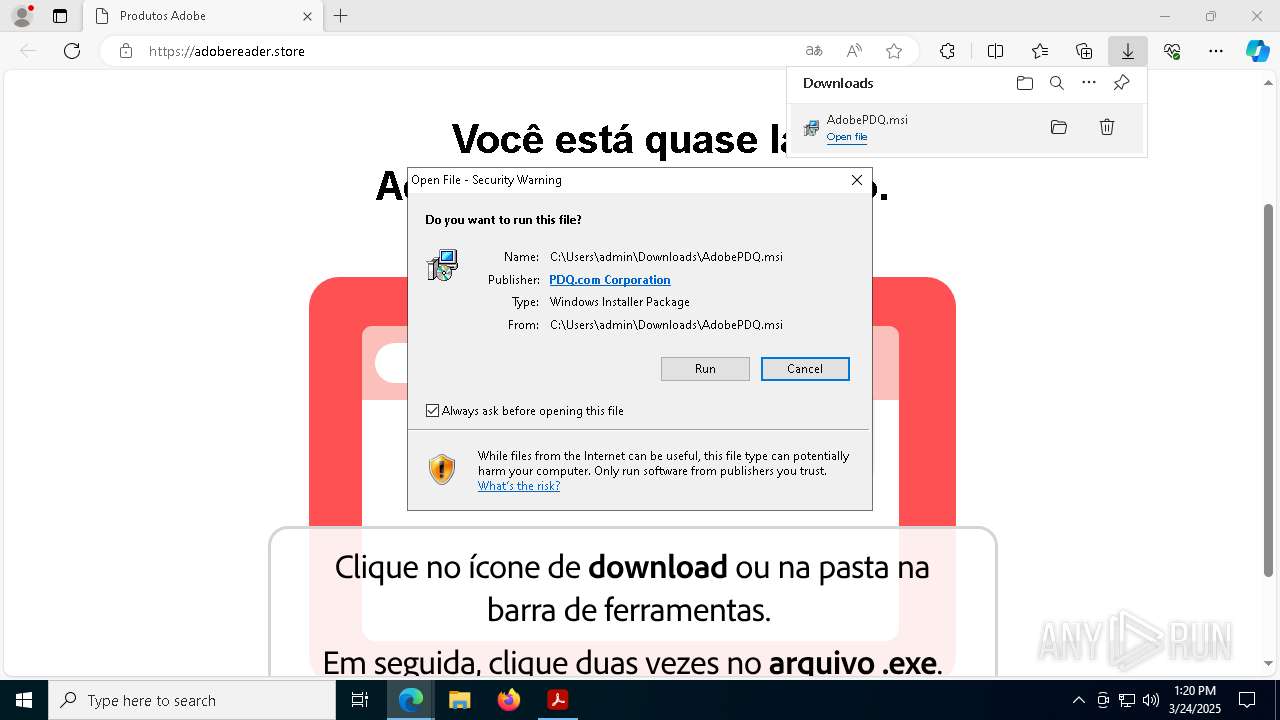
Autorun file from Downloads
- msedge.exe (PID: 4212)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7180)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 8940)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 8940)
- msiexec.exe (PID: 7620)
- msiexec.exe (PID: 6964)
- slui.exe (PID: 7692)
- pdq-connect-agent.exe (PID: 4812)
- pdq-connect-updater.exe (PID: 3268)
- pdq-connect-agent.exe (PID: 5392)
Create files in a temporary directory
- rundll32.exe (PID: 1676)
Manages system restore points
- SrTasks.exe (PID: 8720)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6964)
The sample compiled with english language support
- msiexec.exe (PID: 6964)
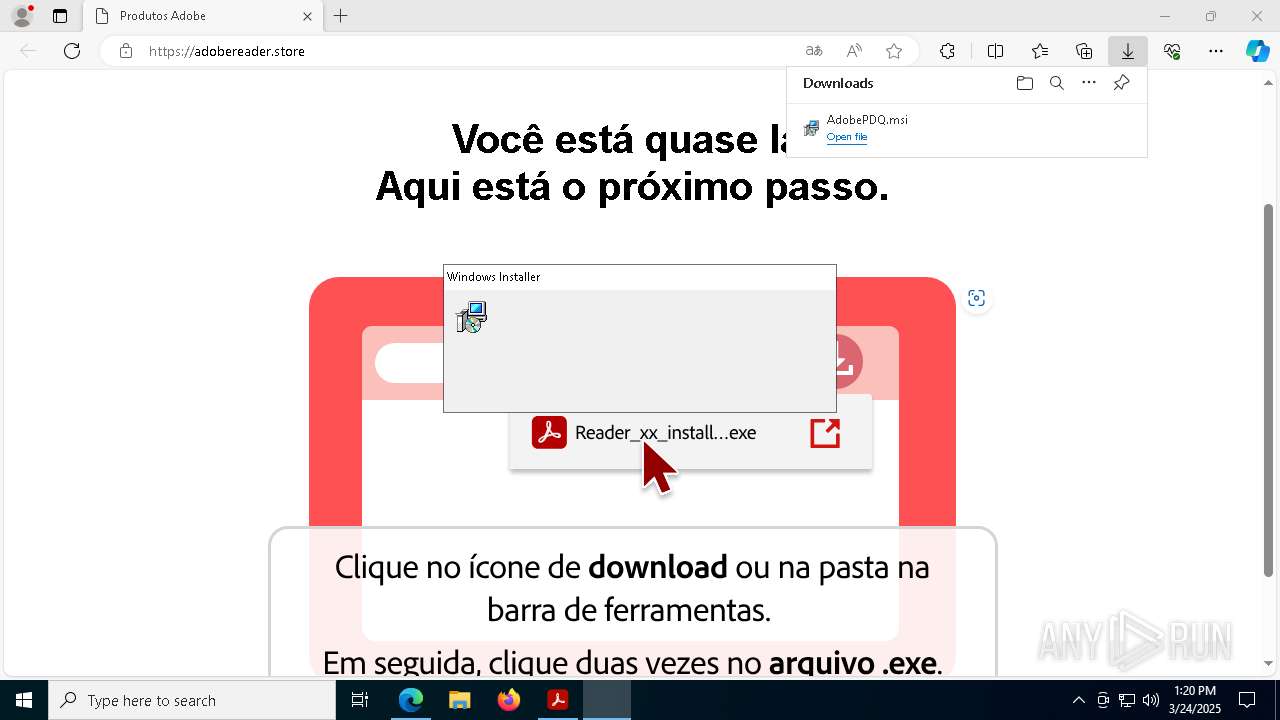
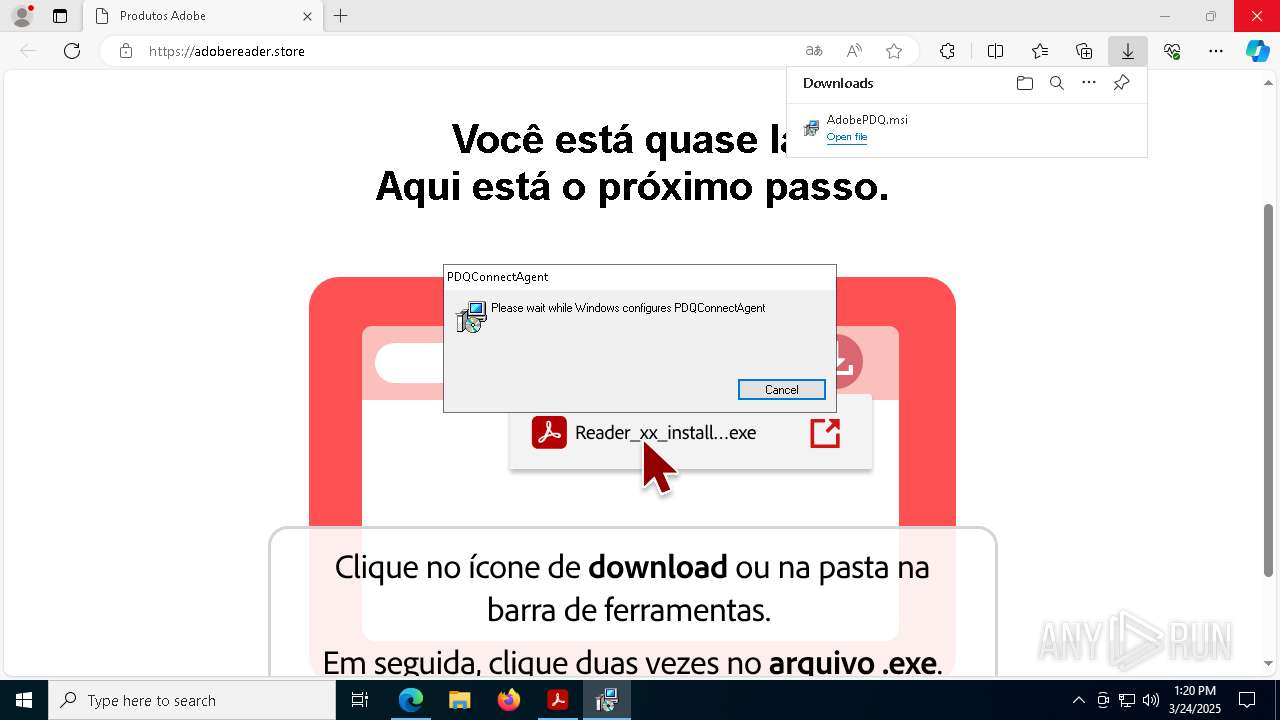
PDQCONNECT has been detected
- msiexec.exe (PID: 7828)
- rundll32.exe (PID: 9080)
- pdq-connect-agent.exe (PID: 4812)
- msiexec.exe (PID: 7480)
- rundll32.exe (PID: 2516)
Creates files in the program directory
- pdq-connect-agent.exe (PID: 4812)
Manual execution by a user
- Taskmgr.exe (PID: 8928)
- Taskmgr.exe (PID: 2332)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.1 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
Total processes
395
Monitored processes
120
Malicious processes
4
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 840 | rundll32.exe "C:\WINDOWS\Installer\MSIC7CD.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1165343 61 WixSharp!WixSharp.ManagedProjectActions.WixSharp_InitRuntime_Action | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7936 --field-trial-handle=2136,i,1778319238233493409,1905913706823608979,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=3032 --field-trial-handle=1624,i,13280573450705985845,10489085464814340939,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1196 | "C:\WINDOWS\system32\sc.exe" start "PDQConnectAgent" | C:\Windows\System32\sc.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2700 --field-trial-handle=1624,i,13280573450705985845,10489085464814340939,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3732 --field-trial-handle=2136,i,1778319238233493409,1905913706823608979,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1676 | rundll32.exe "C:\WINDOWS\Installer\MSIB100.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1159500 16 WixSharp!WixSharp.ManagedProjectActions.WixSharp_BeforeInstall_Action | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2288 | rundll32.exe "C:\WINDOWS\Installer\MSI107D.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1183906 144 pdqconnectagent-setup!pdqconnectagent_setup.CustomActions.CreateEventSource | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2368 --field-trial-handle=2136,i,1778319238233493409,1905913706823608979,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
73 503
Read events
72 682
Write events
654
Delete events
167
Modification events
| (PID) Process: | (7332) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumAcrobatLaunches |
Value: 7 | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ToolsSearch |
| Operation: | write | Name: | iSearchHintIndex |
Value: 3 | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\DLLInjection |
| Operation: | write | Name: | bBlockDLLInjection |
Value: 0 | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | sProductGUID |
Value: 4143524F4241545F475549445F4E474C5F44554D4D5900 | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | sProductGUID |
Value: 4143524F5F5245534944554500 | |||
Executable files
85
Suspicious files
419
Text files
117
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7488 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 7488 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 7792 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old | text | |
MD5:EB1590F2607E1CE46DBF6A521F772EA0 | SHA256:4355D9A8A115BA4E41178B456A8A5578846EB1F7EC9509249C2405F758F31731 | |||
| 7792 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:268741B1BD8D6D98AEFABCE38CDE415A | SHA256:DB265C438701AA63E530C0F3C504FDC0ECDC143B8198D0C795D2C47D31956491 | |||
| 7792 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old~RF10d8ed.TMP | text | |
MD5:7383516745DEC1E86152192435F92D1F | SHA256:E22D34BBD915EEB277D4F4138D176EACE5577CF035EF7C2C80A4BC4D9B6C0E1D | |||
| 7792 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:93C418E9309075D900BF6907AEA2405C | SHA256:41F6DB616F1508E097FB6B2F5216E4E79D08706B9D0E7602BE2560BC1A2F2084 | |||
| 7332 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 7792 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old | text | |
MD5:8412AEEF2309E13FC954061D9BCEFFF4 | SHA256:D062D7B5DF5F3BCB753E97AB5D1DCD9CF62058D9103DA383DBE1F482FC1D4644 | |||
| 7792 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:DBAB4631058FE1B86D09FD1C12BDEA13 | SHA256:EA42B35F2AFBFBF487AF9D1D51179B3F5594EFA832AB1F1A1DC0EE814E4E307A | |||
| 7792 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old~RF10d90c.TMP | text | |
MD5:ED7D8AAE48211E2BFAF557130572C62A | SHA256:A5CF8D8ADC86DCA357396AF7E3A24A116072D5C1E5552EEB76601AE2673DED6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
93
DNS requests
79
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8976 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8940 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8976 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7180 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
7180 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEA5NZ%2FZDFskqO3oXzEaXao8%3D | unknown | — | — | whitelisted |
7180 | msedge.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRhtVltVOu8OqBzmsd%2B%2FeFfks3xTQQUvGsiZZ2MaObmHgXx2HIl1LjgSMACEAvcoEuhCK%2FAlHGPdKmo6gs%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4784 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8024 | AcroCEF.exe | 2.19.104.203:443 | geo2.adobe.com | AKAMAI-AS | DE | whitelisted |
8024 | AcroCEF.exe | 3.233.129.217:443 | p13n.adobe.io | AMAZON-AES | US | whitelisted |
8024 | AcroCEF.exe | 2.23.244.205:443 | armmf.adobe.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
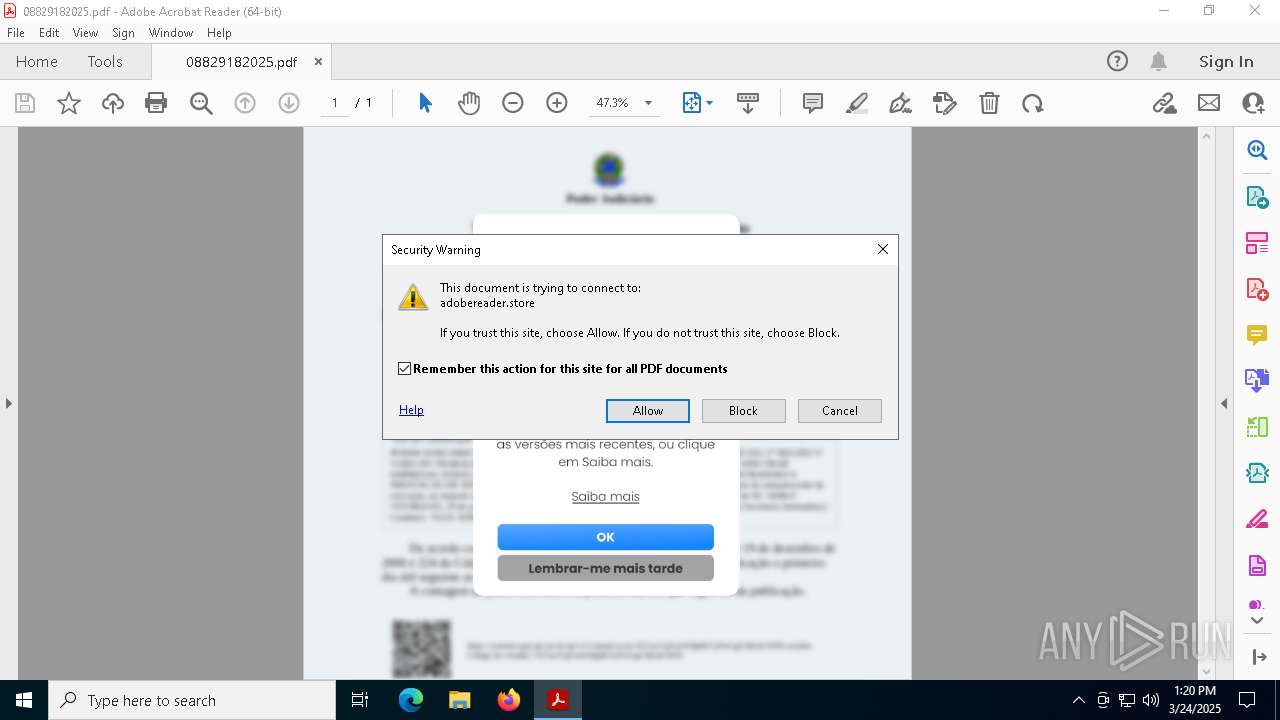
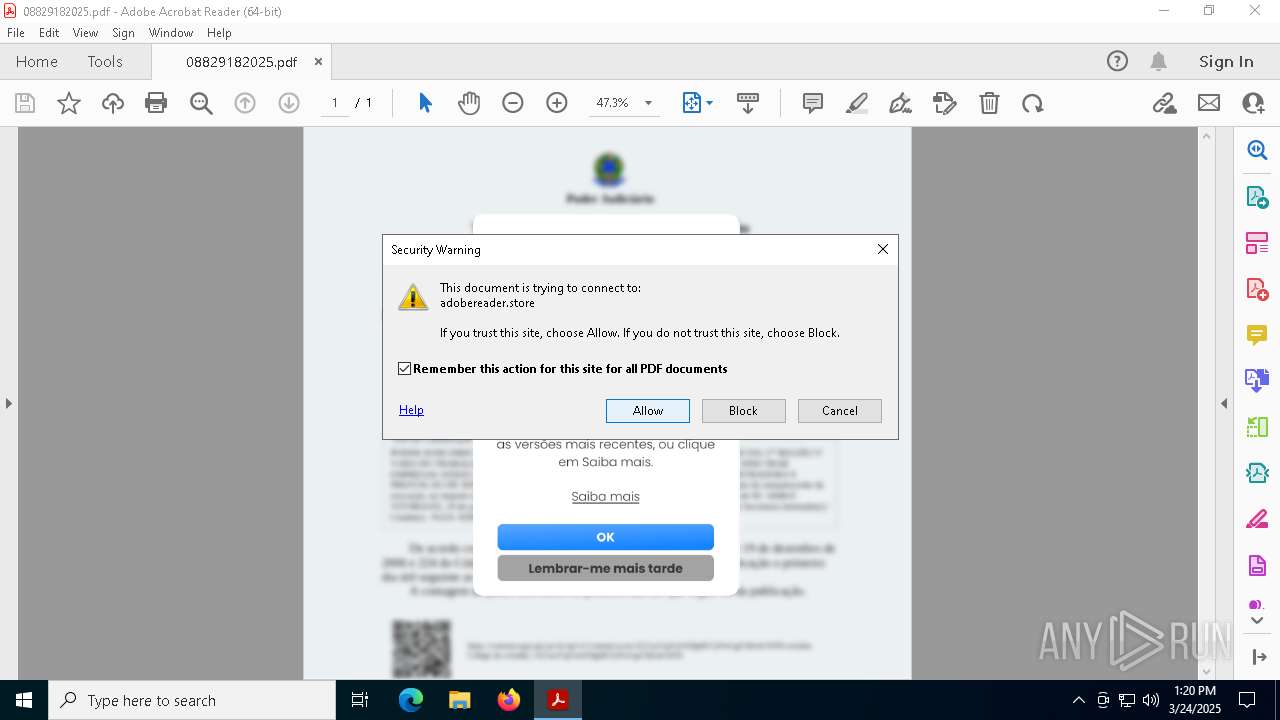
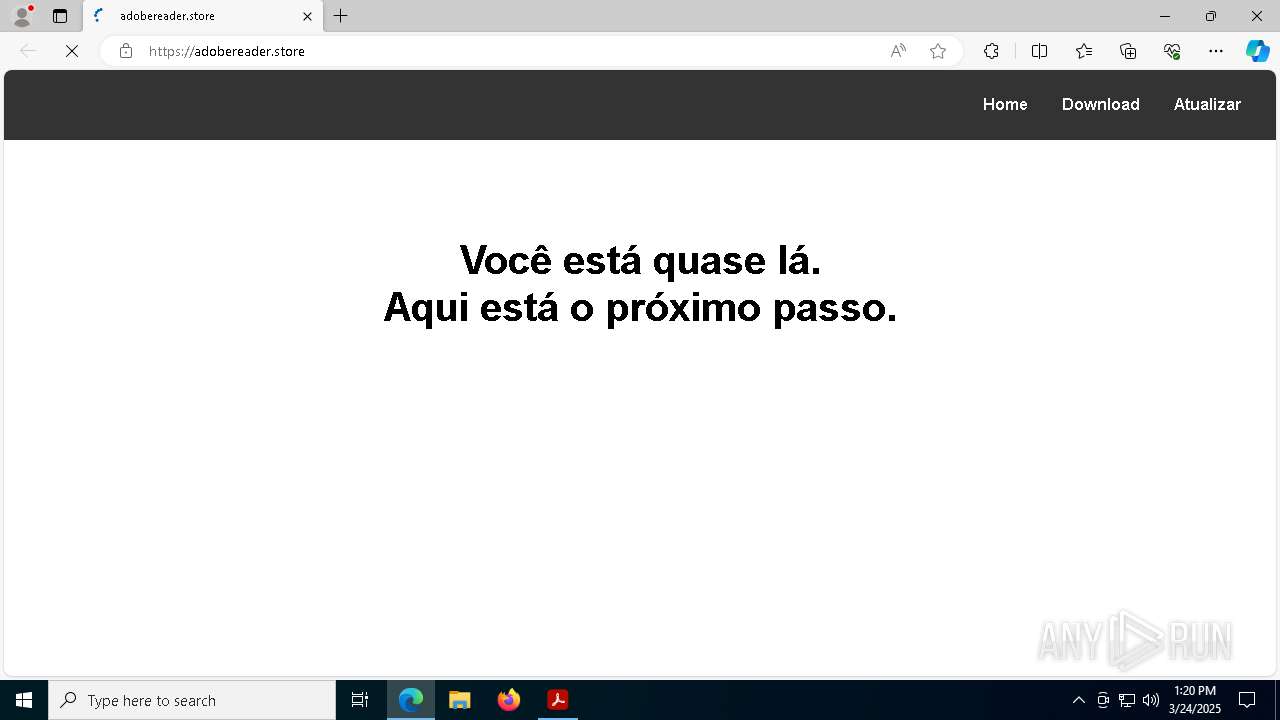
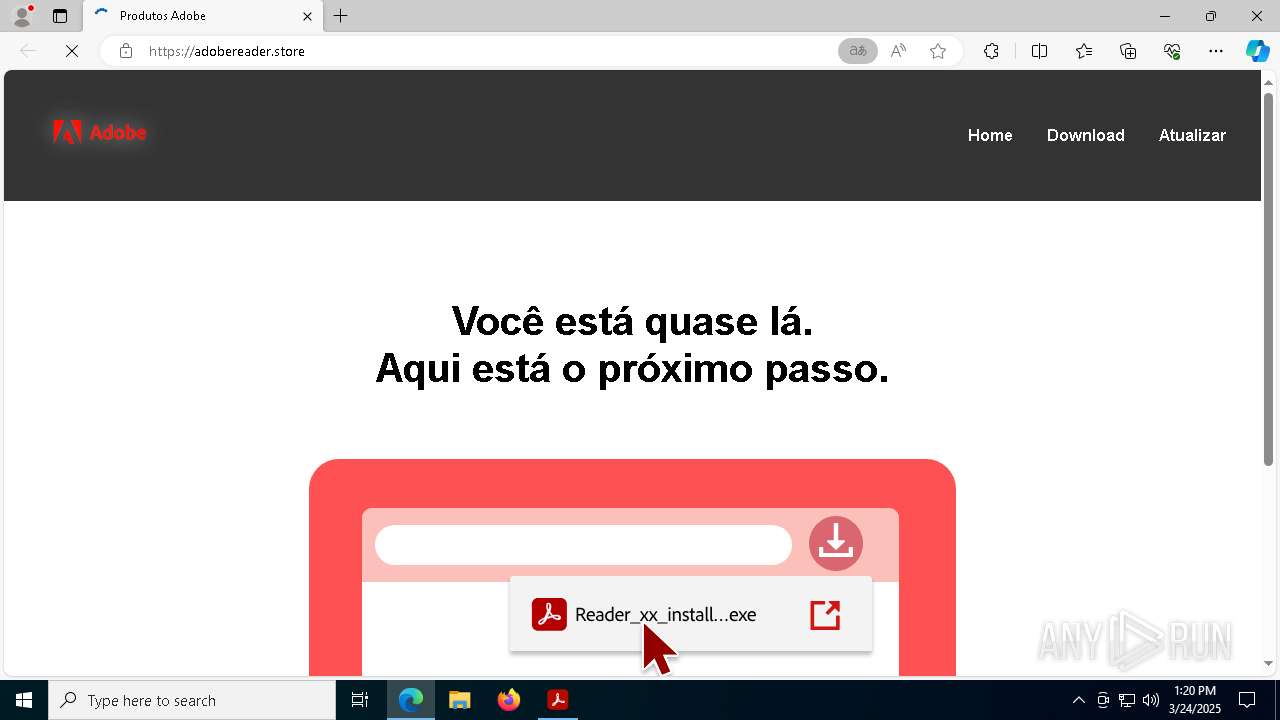
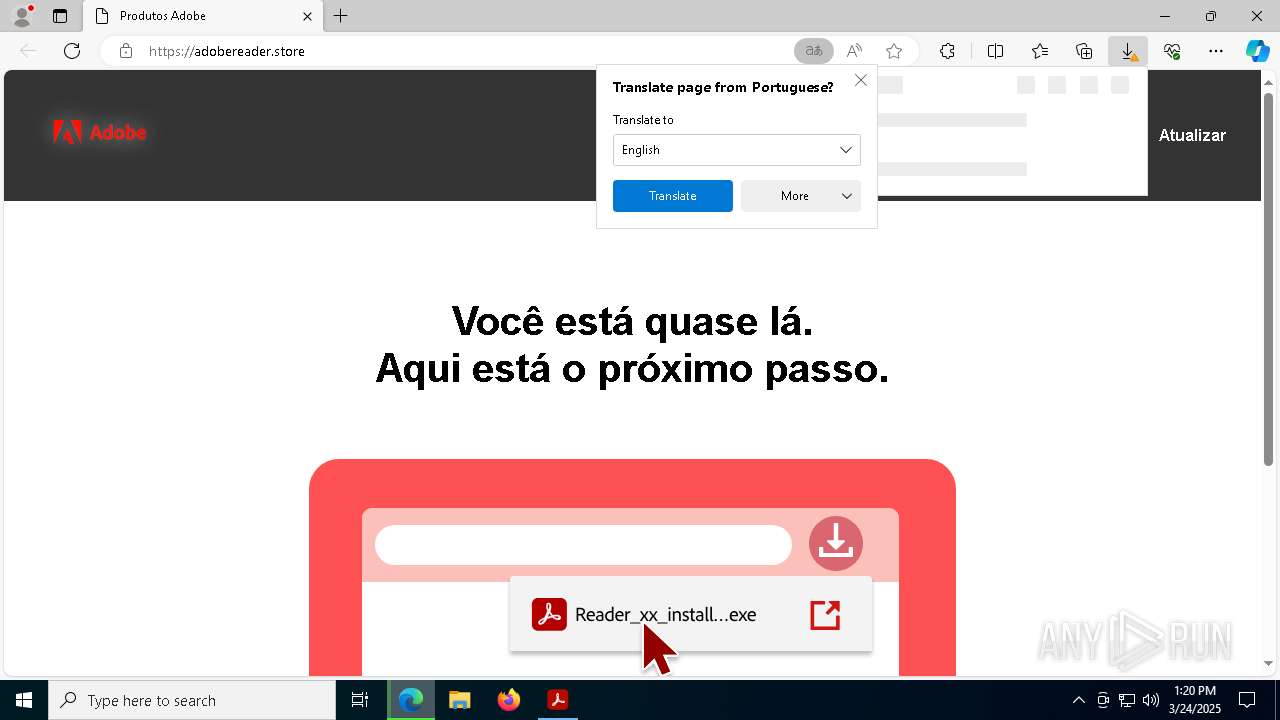
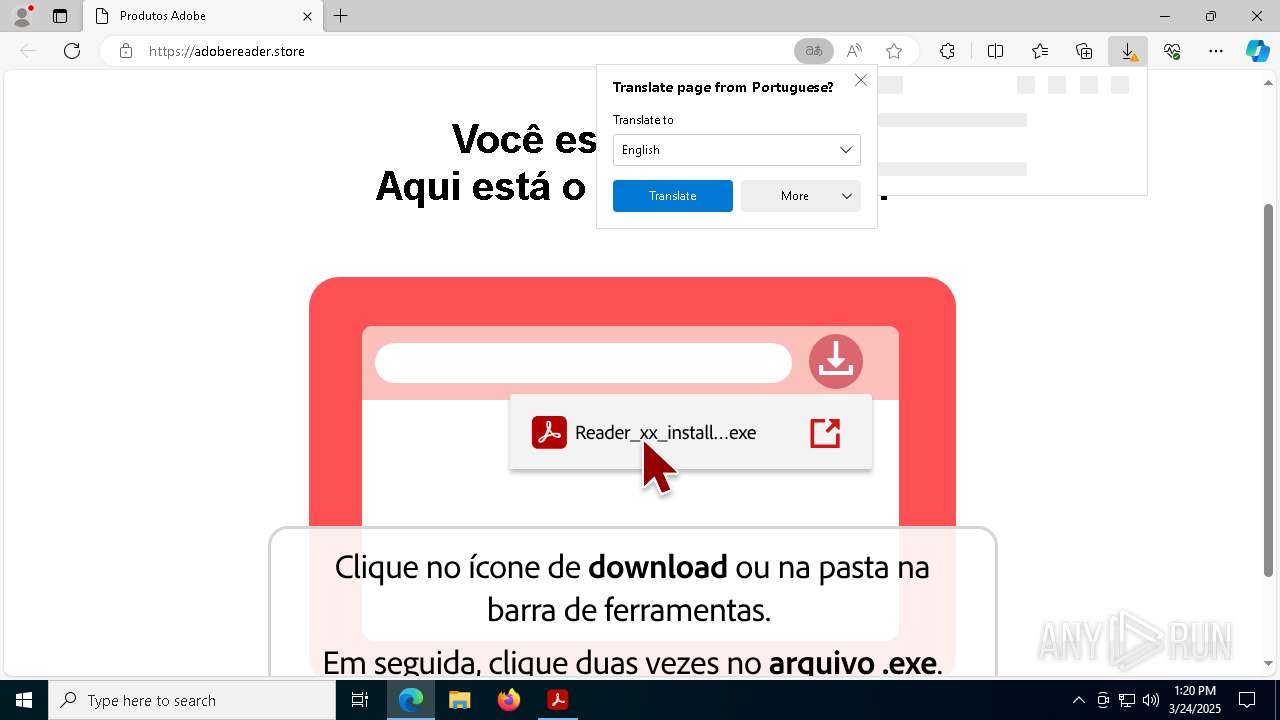
adobereader.store |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare R2 Storage (r2 .cloudflarestorage .com) |