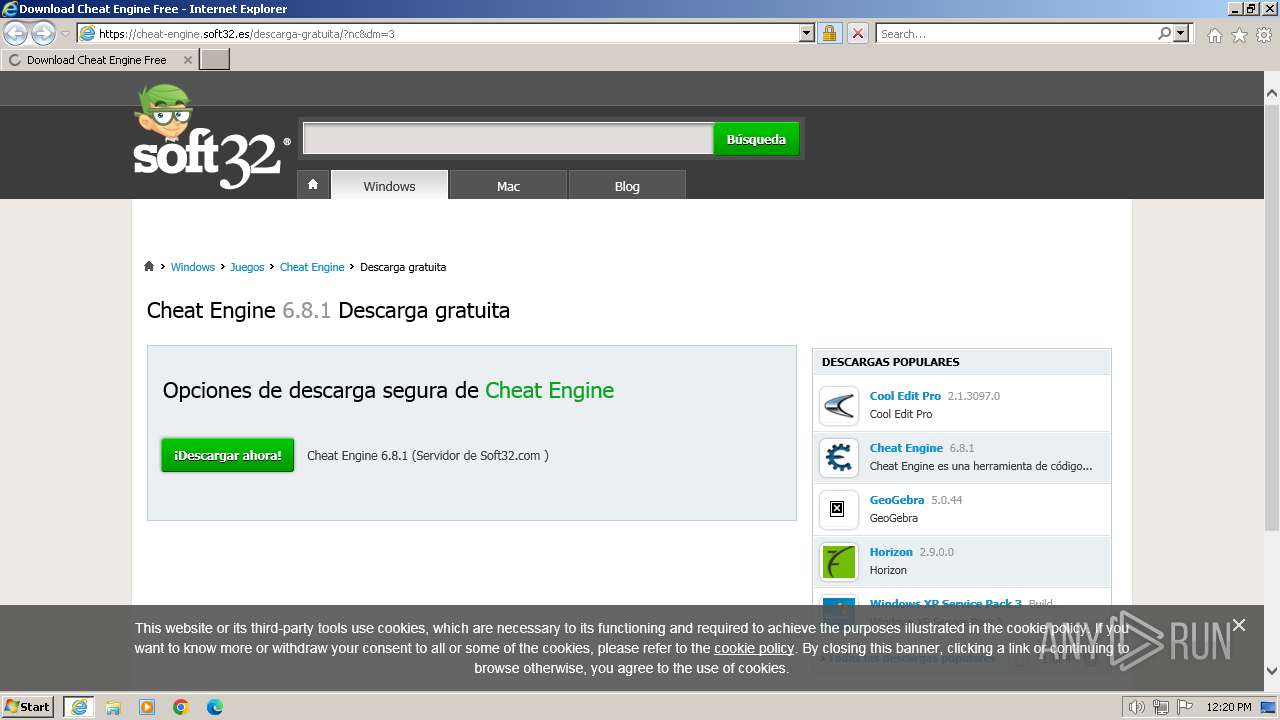
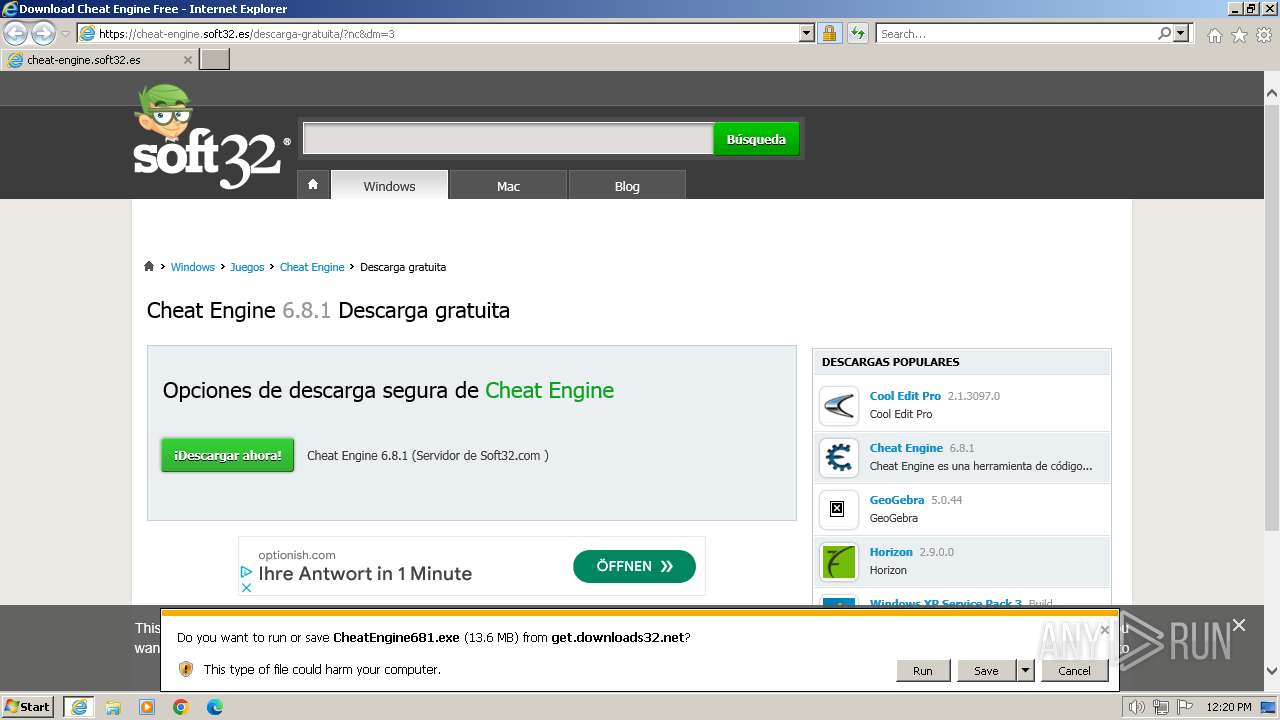
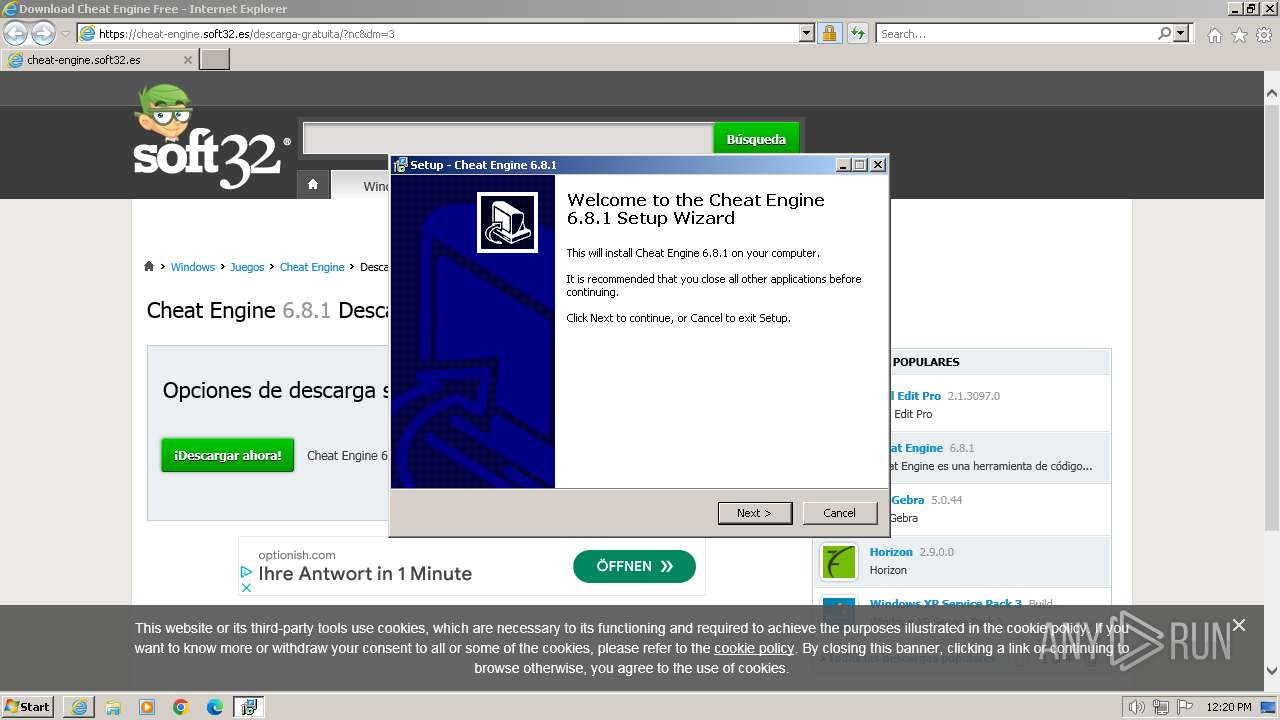
| URL: | https://cheat-engine.soft32.es/descarga-gratuita/?nc |
| Full analysis: | https://app.any.run/tasks/f1ae5454-1d5c-49d3-b559-7134886b8ed3 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2024, 12:19:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B4E8DAB242A2B50982F8701FACB10F0C |
| SHA1: | 125BC50E51DE876EA70783EB9F52BA1B4DEE4886 |
| SHA256: | 43A8B5A78C04E51F35F7B0ABF576E7B42FCB87F98C5675EF2D1CB35C43C17B21 |
| SSDEEP: | 3:N8QoNMLApN1xTXfXdQ8Gn:2QoNM05c8G |
MALICIOUS
Drops the executable file immediately after the start
- CheatEngine681.exe (PID: 2072)
- CheatEngine681.exe (PID: 3324)
- CheatEngine681.tmp (PID: 2060)
Actions looks like stealing of personal data
- CheatEngine681.tmp (PID: 2060)
Antivirus name has been found in the command line (generic signature)
- ceregreset.exe (PID: 984)
SUSPICIOUS
Executable content was dropped or overwritten
- CheatEngine681.exe (PID: 2072)
- CheatEngine681.exe (PID: 3324)
- CheatEngine681.tmp (PID: 2060)
Reads the Windows owner or organization settings
- CheatEngine681.tmp (PID: 2060)
Reads the Internet Settings
- CheatEngine681.tmp (PID: 2060)
- Cheat Engine.exe (PID: 952)
- cheatengine-i386.exe (PID: 664)
Reads Microsoft Outlook installation path
- CheatEngine681.tmp (PID: 2060)
Reads security settings of Internet Explorer
- CheatEngine681.tmp (PID: 2060)
- Cheat Engine.exe (PID: 952)
- cheatengine-i386.exe (PID: 664)
Reads the BIOS version
- CheatEngine681.tmp (PID: 2060)
Reads Internet Explorer settings
- CheatEngine681.tmp (PID: 2060)
Process drops SQLite DLL files
- CheatEngine681.tmp (PID: 2060)
Process drops legitimate windows executable
- CheatEngine681.tmp (PID: 2060)
Uses ICACLS.EXE to modify access control lists
- CheatEngine681.tmp (PID: 2060)
Checks Windows Trust Settings
- cheatengine-i386.exe (PID: 664)
Drops a system driver (possible attempt to evade defenses)
- CheatEngine681.tmp (PID: 2060)
Non-standard symbols in registry
- CheatEngine681.tmp (PID: 2060)
Reads settings of System Certificates
- cheatengine-i386.exe (PID: 664)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 1432)
Application launched itself
- iexplore.exe (PID: 1432)
- msedge.exe (PID: 3312)
- msedge.exe (PID: 3808)
Checks supported languages
- CheatEngine681.exe (PID: 2072)
- CheatEngine681.tmp (PID: 2156)
- CheatEngine681.exe (PID: 3324)
- CheatEngine681.tmp (PID: 2060)
- Kernelmoduleunloader.exe (PID: 3528)
- windowsrepair.exe (PID: 992)
- ceregreset.exe (PID: 984)
- cheatengine-i386.exe (PID: 664)
- Cheat Engine.exe (PID: 952)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3892)
- iexplore.exe (PID: 1432)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3892)
- iexplore.exe (PID: 1432)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1432)
Reads the computer name
- CheatEngine681.tmp (PID: 2156)
- CheatEngine681.tmp (PID: 2060)
- Kernelmoduleunloader.exe (PID: 3528)
- Cheat Engine.exe (PID: 952)
- cheatengine-i386.exe (PID: 664)
Create files in a temporary directory
- CheatEngine681.exe (PID: 2072)
- CheatEngine681.exe (PID: 3324)
- CheatEngine681.tmp (PID: 2060)
- cheatengine-i386.exe (PID: 664)
Reads product name
- CheatEngine681.tmp (PID: 2060)
Reads the machine GUID from the registry
- CheatEngine681.tmp (PID: 2060)
- cheatengine-i386.exe (PID: 664)
Process checks whether UAC notifications are on
- CheatEngine681.tmp (PID: 2060)
Reads Environment values
- CheatEngine681.tmp (PID: 2060)
Creates files in the program directory
- CheatEngine681.tmp (PID: 2060)
Checks proxy server information
- CheatEngine681.tmp (PID: 2060)
- cheatengine-i386.exe (PID: 664)
Reads Windows Product ID
- CheatEngine681.tmp (PID: 2060)
Reads CPU info
- CheatEngine681.tmp (PID: 2060)
Creates a software uninstall entry
- CheatEngine681.tmp (PID: 2060)
Reads the software policy settings
- cheatengine-i386.exe (PID: 664)
Creates files or folders in the user directory
- cheatengine-i386.exe (PID: 664)
Manual execution by a user
- msedge.exe (PID: 3808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
74
Monitored processes
25
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1416 --field-trial-handle=1280,i,14836155765645281725,15945124212229273986,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Cheat Engine 6.8.1\cheatengine-i386.exe" | C:\Program Files\Cheat Engine 6.8.1\cheatengine-i386.exe | Cheat Engine.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Exit code: 0 Version: 6.8.1.5602 Modules
| |||||||||||||||
| 764 | "icacls" "C:\Program Files\Cheat Engine 6.8.1" /grant *S-1-15-2-1:(OI)(CI)(RX) /T | C:\Windows\System32\icacls.exe | — | CheatEngine681.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 1332 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Program Files\Cheat Engine 6.8.1\Cheat Engine.exe" | C:\Program Files\Cheat Engine 6.8.1\Cheat Engine.exe | — | CheatEngine681.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 6.3.0.0 Modules
| |||||||||||||||
| 984 | "C:\Program Files\Cheat Engine 6.8.1\ceregreset.exe" -silent -dontdeletecustomtypes -dontdeleteversioncheck | C:\Program Files\Cheat Engine 6.8.1\ceregreset.exe | — | CheatEngine681.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Cheat Engine 6.8.1\windowsrepair.exe" /s | C:\Program Files\Cheat Engine 6.8.1\windowsrepair.exe | — | CheatEngine681.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://cheat-engine.soft32.es/descarga-gratuita/?nc" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2060 | "C:\Users\admin\AppData\Local\Temp\is-EB5C7.tmp\CheatEngine681.tmp" /SL5="$150190,14068795,56832,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\CheatEngine681.exe" /SPAWNWND=$1A0164 /NOTIFYWND=$A021E | C:\Users\admin\AppData\Local\Temp\is-EB5C7.tmp\CheatEngine681.tmp | CheatEngine681.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\CheatEngine681.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\CheatEngine681.exe | iexplore.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: MEDIUM Description: Cheat Engine 6.8.1 Setup Exit code: 0 Version: 6.8.1.2 Modules
| |||||||||||||||
| 2156 | "C:\Users\admin\AppData\Local\Temp\is-I87L0.tmp\CheatEngine681.tmp" /SL5="$A021E,14068795,56832,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\CheatEngine681.exe" | C:\Users\admin\AppData\Local\Temp\is-I87L0.tmp\CheatEngine681.tmp | — | CheatEngine681.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
37 015
Read events
36 587
Write events
335
Delete events
93
Modification events
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31093678 | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31093678 | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1432) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
107
Suspicious files
78
Text files
352
Unknown types
60
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B130ACF64536217C36F220BAF7B06104 | SHA256:DF1DB936EC6086C5715133C00D4B5CA192FF403958C5111F24E3F5C6BAFD380B | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:220BC8F796C5AA021F85AA60FA47A9E5 | SHA256:74EB3F2B46733EA2246AFE1941C3DB831E4EA9C59D5A22BF15E4142DE52DE87A | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:CBDB82F538C5D7CA849F55C5ABFBCF41 | SHA256:791127B4509EA89BE6F775491168FC4C23A8455651D85C07F6583C6FD409BC37 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:D46387A37C3F21A61A1B467B97E1D77B | SHA256:58B8179411C32BA2FD688A2EFC11B23E86DD0C83FC63233556F06E0F3320127E | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\375RQGMT.txt | text | |
MD5:9BC63E23622A583F5BFB5140C21F20C6 | SHA256:1F9918D2DDE62DCE6D11B34FA8F57209E5A4940B7AE587B13F2ACEEE22CD2C0B | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:447723AA115FD0C4C39B43DB122BC490 | SHA256:A47A0480DD2FCBE005B6C86C47C4166C48ED782CE12384C9F5A355D173EF30D0 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\descarga-gratuita[1].htm | html | |
MD5:C9A88B6E7052C1BAB49E3A19D62F11A5 | SHA256:16C66199CE499024FAA186B348ED7FCBC24C17F024E080BB6A171C413A3155F7 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:5D8F7B1C393FF00DE21F682F78942993 | SHA256:FC8EF68E41508D55F9272B96BC7D075B05A35800A8781E1AF1D6D82171B103C1 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:E683DE4B64CDB28EBA42AE704968F1E5 | SHA256:1A1FE0EDB5E43698A6A4BFBBCCF1AD778BBBD3C77D3B1748504DBF6DE8195682 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
102
DNS requests
57
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3892 | iexplore.exe | GET | 304 | 95.100.100.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC%2BP0iGO7o7nQoIudW3BwdU | unknown | binary | 472 b | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCimReIRyQtphKmdTNhBzaE | unknown | binary | 472 b | unknown |
3892 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | unknown | binary | 471 b | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCRd4hKrA6aBAnnS3UYBsso | unknown | binary | 472 b | unknown |
3892 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEA1G3Q9Nl61wpcro6VMkzO8%3D | unknown | binary | 471 b | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEmjnEcAcBIRCdkf7NhadAI%3D | unknown | binary | 471 b | unknown |
3892 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
3892 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCwbnjJ3cYOcgqEPZxiPEyj | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3892 | iexplore.exe | 18.173.187.44:443 | cheat-engine.soft32.es | — | US | unknown |
3892 | iexplore.exe | 95.100.100.50:80 | ctldl.windowsupdate.com | Akamai International B.V. | PT | unknown |
3892 | iexplore.exe | 108.138.34.92:80 | o.ss2.us | AMAZON-02 | US | unknown |
1432 | iexplore.exe | 128.177.173.175:443 | www.bing.com | ZAYO-6461 | US | unknown |
3892 | iexplore.exe | 18.66.190.71:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | unknown |
1432 | iexplore.exe | 95.100.100.50:80 | ctldl.windowsupdate.com | Akamai International B.V. | PT | unknown |
1432 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3892 | iexplore.exe | 18.66.188.227:443 | d3gx3uz4yj2hnq.cloudfront.net | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cheat-engine.soft32.es |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.digicert.com |
| whitelisted |
d3gx3uz4yj2hnq.cloudfront.net |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Kernelmoduleunloader.exe | Kernelmodule unloader |
Kernelmoduleunloader.exe | Setup. So do not show messages |
Kernelmoduleunloader.exe | attempting to unload |
Kernelmoduleunloader.exe | SCManager opened |
Kernelmoduleunloader.exe | count=0 |
Kernelmoduleunloader.exe | setup=true |
cheatengine-i386.exe | Offset of LBR_Count=760 |
cheatengine-i386.exe | sizeof fxstate = 512 |
cheatengine-i386.exe | TSymbolListHandler.create 1 |
cheatengine-i386.exe | TSymbolListHandler.create 2 |