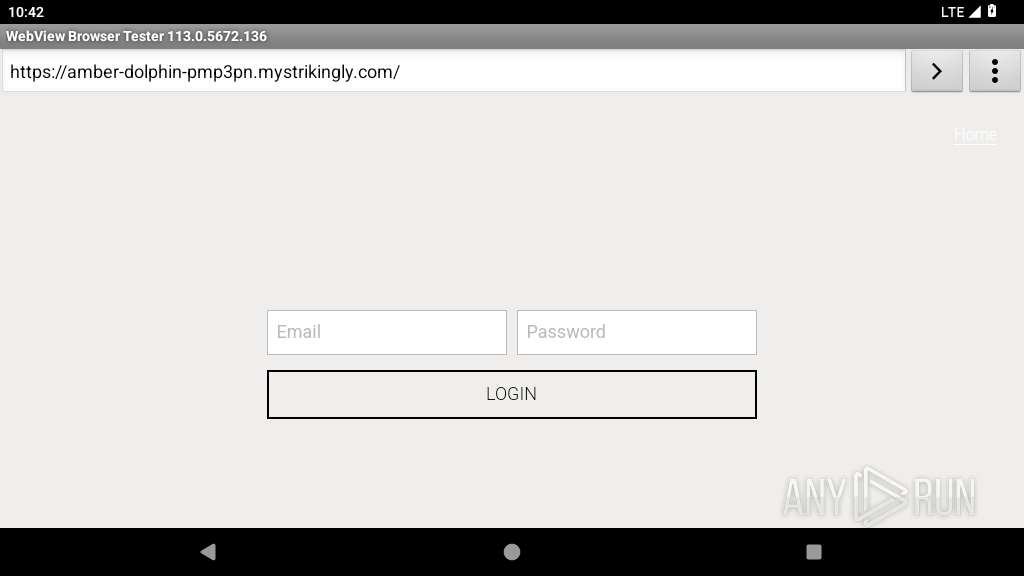
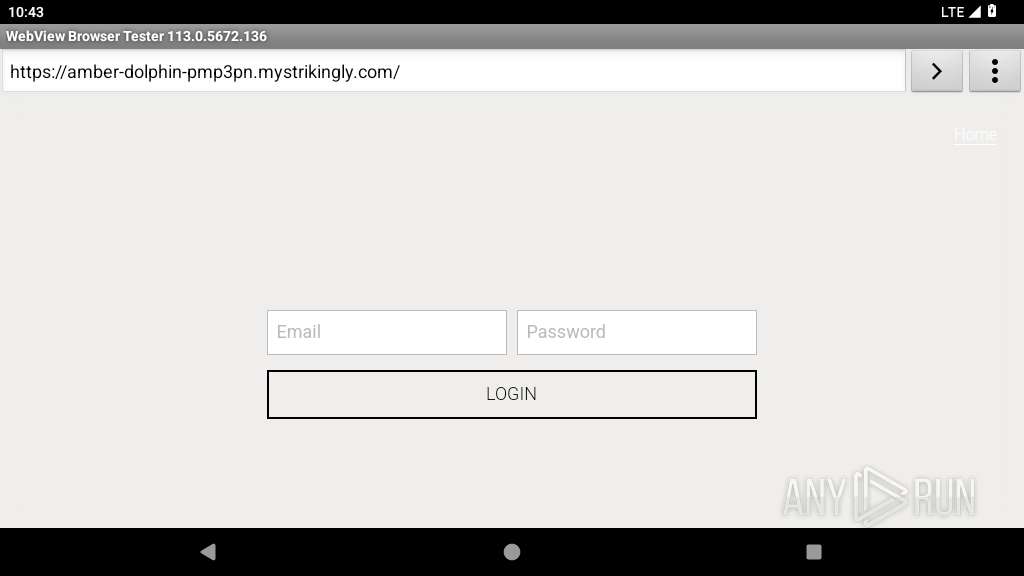
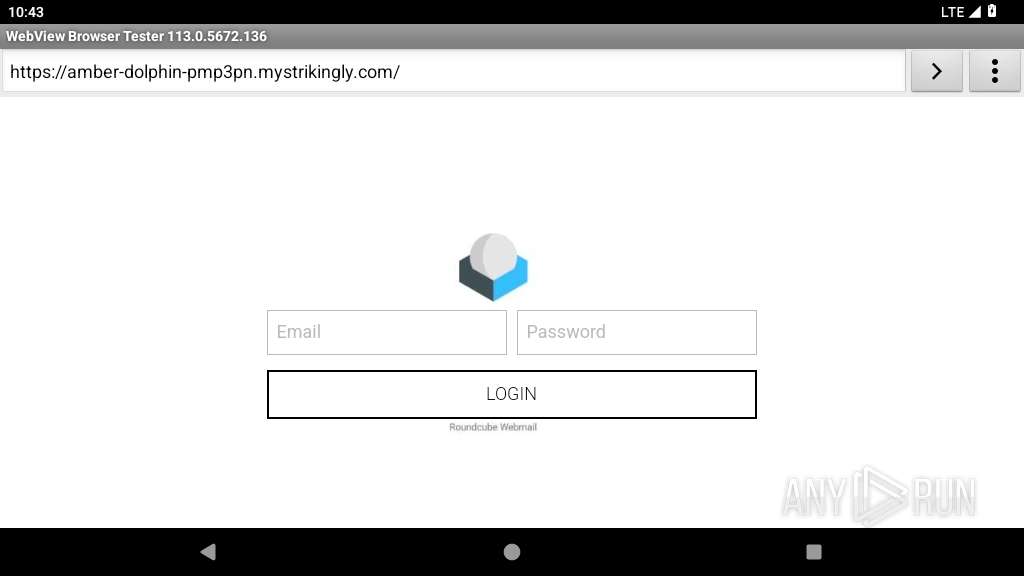
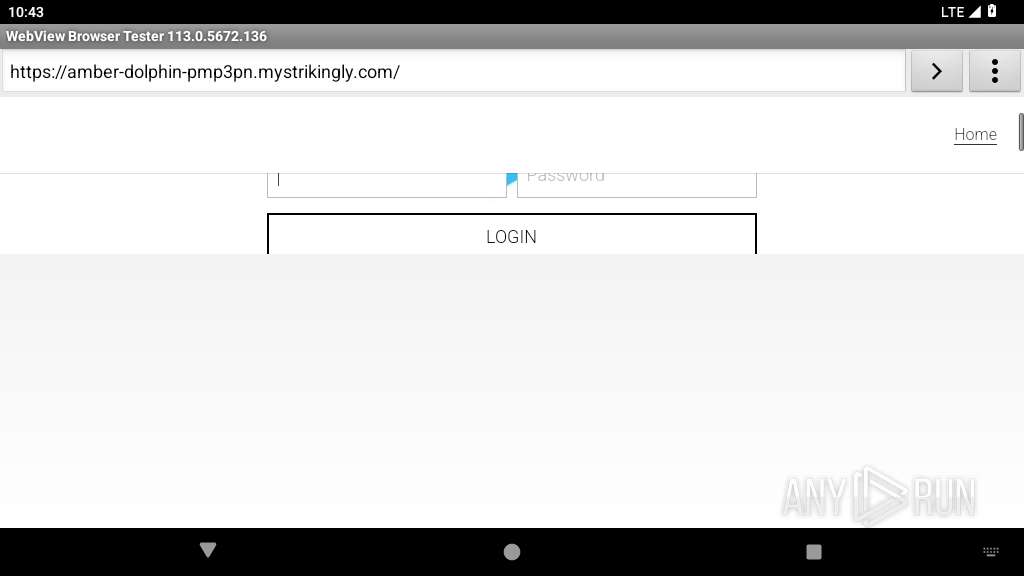
| URL: | https://amber-dolphin-pmp3pn.mystrikingly.com/ |
| Full analysis: | https://app.any.run/tasks/150195b8-1268-4d29-a75a-5f1d73fa12a0 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 22:42:47 |
| OS: | Android 14 |
| Tags: | |
| Indicators: | |
| MD5: | 5316572334705FFCF914E62D5DB57AC3 |
| SHA1: | BFB3E793DE7D88840DAD3640F259930CF952C418 |
| SHA256: | 4391DE8FB2BC634432149628B05A536318D91A4493928C917DA47F0F89722139 |
| SSDEEP: | 3:N8UYBSVe8TLNZ3Ht:2UsSM8T5Z9 |
MALICIOUS
PHISHING has been detected (SURICATA)
- netd (PID: 345)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
127
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 345 | /system/bin/netd | /system/bin/netd | init | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2240 | org.chromium.webview_shell | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2267 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2287 | webview_zygote | /system/bin/app_process32 | — | app_process32 |
User: webview_zygote Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2318 | zygote | /system/bin/app_process32 | app_process32 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
25
DNS requests
20
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.186.99:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
449 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 216.239.35.8:123 | time.android.com | — | — | whitelisted |
— | — | 142.250.185.100:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.186.99:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 64.233.184.81:443 | staging-remoteprovisioning.sandbox.googleapis.com | GOOGLE | US | whitelisted |
2267 | app_process32 | 142.250.186.67:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2240 | app_process64 | 52.84.150.39:443 | amber-dolphin-pmp3pn.mystrikingly.com | AMAZON-02 | US | unknown |
2318 | app_process32 | 142.250.181.227:443 | update.googleapis.com | GOOGLE | US | whitelisted |
2318 | app_process32 | 172.217.18.14:443 | google.com | GOOGLE | US | whitelisted |
2240 | app_process64 | 18.245.60.5:443 | static-assets.strikinglycdn.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
time.android.com |
| whitelisted |
google.com |
| whitelisted |
staging-remoteprovisioning.sandbox.googleapis.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
amber-dolphin-pmp3pn.mystrikingly.com |
| unknown |
update.googleapis.com |
| whitelisted |
dl.google.com |
| whitelisted |
static-fonts-css.strikinglycdn.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |
345 | netd | Not Suspicious Traffic | INFO [ANY.RUN] Online Site Builder (mystrikingly .com) |
345 | netd | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
345 | netd | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (mystrikingly) |
345 | netd | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |