| File name: | 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe |
| Full analysis: | https://app.any.run/tasks/7f9a2ea0-e9f3-42c2-a8f8-1d4aab2704cd |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2024, 02:59:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 059B378BF1770BDBEA5A02C83399CDB0 |
| SHA1: | 6E482362F5C090BC12BAA425C3F01271E6981601 |
| SHA256: | 437CB914AEB1FCA0A714380AC400101E4E594A13FE245CF589B8A8BCA3AE46BA |
| SSDEEP: | 6144:379NieV8mSjbU9asmAHiuCb8ogg6CARPISUOgW9X+hOGzC/:3RAeV8JAhiBbh1YKZzcukG2/ |
MALICIOUS
Drops the executable file immediately after the start
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- powershell.exe (PID: 6260)
- ZPHYQEF.exe (PID: 6748)
- OFU.exe (PID: 6968)
- AYXI.exe (PID: 7124)
- PBHMRNL.exe (PID: 4716)
- LYN.exe (PID: 4360)
- ZJJ.exe (PID: 1604)
- EMNO.exe (PID: 6384)
- GKGRXCS.exe (PID: 6856)
- MKNEG.exe (PID: 7088)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- DNMM.exe (PID: 5720)
- OGPFK.exe (PID: 6276)
- OZYGQK.exe (PID: 6672)
- MOXJC.exe (PID: 6860)
- OXHFWF.exe (PID: 3740)
- OMYLIT.exe (PID: 5196)
- FIXCWA.exe (PID: 6448)
- WVHV.exe (PID: 5548)
- BGD.exe (PID: 6896)
- FYGC.exe (PID: 4284)
- DWFV.exe (PID: 4776)
- XCGGEVL.exe (PID: 6364)
- IZJMQBM.exe (PID: 1864)
- USME.exe (PID: 4004)
- HCQDE.exe (PID: 6356)
- DAOA.exe (PID: 1616)
- LJLB.exe (PID: 3592)
- ZQIIW.exe (PID: 6656)
- URNWQ.exe (PID: 6320)
- STUCKC.exe (PID: 1752)
- WZPACS.exe (PID: 6368)
- CAW.exe (PID: 2588)
- UKWYWDU.exe (PID: 6448)
- KSFHZ.exe (PID: 6836)
- VLIA.exe (PID: 4628)
- MBHCLZ.exe (PID: 3592)
- OZIF.exe (PID: 3712)
- NJRGGAL.exe (PID: 636)
- NHFW.exe (PID: 6736)
- RZLOJ.exe (PID: 4424)
- LQNAL.exe (PID: 3708)
- VSOX.exe (PID: 4916)
- ELE.exe (PID: 4628)
- RWIKN.exe (PID: 624)
- CTTIH.exe (PID: 3640)
- AZHS.exe (PID: 6316)
- QWPO.exe (PID: 6308)
- TXSXD.exe (PID: 6652)
- CPQ.exe (PID: 6348)
- NUTS.exe (PID: 5528)
- TFPP.exe (PID: 4936)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- OZDEYX.exe (PID: 6548)
- GCUI.exe (PID: 4264)
- DSIYXP.exe (PID: 1728)
- DZAFJL.exe (PID: 3708)
- FAKCJQI.exe (PID: 5244)
- QVEFCGG.exe (PID: 1720)
- QTN.exe (PID: 6356)
- OJM.exe (PID: 4148)
- LOSN.exe (PID: 3740)
- CZIKK.exe (PID: 7060)
- BSRMY.exe (PID: 6840)
- FAL.exe (PID: 6292)
- UFRRI.exe (PID: 6276)
- FYUAZL.exe (PID: 6300)
- SVQUU.exe (PID: 6652)
- UESPG.exe (PID: 4916)
- RJXMVEU.exe (PID: 4264)
- HZEXZYK.exe (PID: 7144)
- NFSZIM.exe (PID: 6436)
- UKAWEP.exe (PID: 32)
- JKXWP.exe (PID: 2332)
- PNBVUN.exe (PID: 232)
- NLAFGG.exe (PID: 5720)
- CJG.exe (PID: 4000)
- PUCBSHW.exe (PID: 6204)
- CWG.exe (PID: 5896)
- LKRA.exe (PID: 1604)
- VSSV.exe (PID: 7040)
- YUN.exe (PID: 1864)
- HYT.exe (PID: 6316)
- RIN.exe (PID: 704)
- GBSFJ.exe (PID: 5556)
- EDRD.exe (PID: 380)
- CZQUQ.exe (PID: 3732)
- EXRWP.exe (PID: 3708)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- BAY.exe (PID: 2764)
- XYEY.exe (PID: 6676)
- LJA.exe (PID: 1204)
- ZOGUM.exe (PID: 7056)
- WMMRT.exe (PID: 4148)
- JXIYGR.exe (PID: 2304)
- ZNOAKL.exe (PID: 3808)
- NXKZP.exe (PID: 5952)
- JVQWEM.exe (PID: 7120)
- UOL.exe (PID: 6124)
- JTRMUDH.exe (PID: 6416)
- FZXB.exe (PID: 1488)
- NJFC.exe (PID: 5592)
- USDD.exe (PID: 6284)
- RPAAH.exe (PID: 6688)
- NGVI.exe (PID: 2288)
- GDGOX.exe (PID: 6672)
- EUWA.exe (PID: 7132)
- LGKMCD.exe (PID: 232)
- ILIJJ.exe (PID: 4360)
- TELCRCL.exe (PID: 6408)
- XMFKU.exe (PID: 380)
- PSOQSOS.exe (PID: 1728)
- PAFPM.exe (PID: 2580)
- MYUFHXM.exe (PID: 3648)
- QGO.exe (PID: 4036)
- NKMNGNW.exe (PID: 588)
- BZRGLMX.exe (PID: 6552)
- PEPD.exe (PID: 5352)
- XPXE.exe (PID: 6348)
- ZMYZ.exe (PID: 6892)
- QCXJ.exe (PID: 7064)
- USRRBHG.exe (PID: 6180)
- KIYU.exe (PID: 2524)
- QIGI.exe (PID: 2104)
- XJDI.exe (PID: 2608)
- DLCOB.exe (PID: 2588)
- FCEKNN.exe (PID: 7152)
- QFP.exe (PID: 4544)
- SDJ.exe (PID: 3680)
- HSFMT.exe (PID: 6300)
- QSP.exe (PID: 4312)
- HWO.exe (PID: 6716)
- WFYKKJ.exe (PID: 2736)
- PGX.exe (PID: 5280)
- AZSM.exe (PID: 7060)
- SQJ.exe (PID: 2132)
- LKEHRT.exe (PID: 2044)
- YNAFWKM.exe (PID: 1572)
- LYEMBB.exe (PID: 2896)
- RBAKGTJ.exe (PID: 6976)
- ELERTK.exe (PID: 4524)
- EWE.exe (PID: 2088)
- RHIQENV.exe (PID: 4636)
- NEOO.exe (PID: 2392)
- PCH.exe (PID: 4484)
- TDK.exe (PID: 5232)
- GSOSDGN.exe (PID: 6404)
- TNTS.exe (PID: 6276)
- KGVZNLM.exe (PID: 4936)
- DJVCS.exe (PID: 1748)
- QURBXG.exe (PID: 3100)
- ESXYEI.exe (PID: 1728)
- DQVBQ.exe (PID: 5608)
- EGOLE.exe (PID: 3656)
- KVBOFHE.exe (PID: 2008)
- JGZMFCZ.exe (PID: 1176)
- GGHA.exe (PID: 2480)
- ZYYRTB.exe (PID: 3648)
- URD.exe (PID: 2484)
- FKGR.exe (PID: 6408)
- QHSXW.exe (PID: 5080)
- SFLRUY.exe (PID: 5720)
- FIHYZ.exe (PID: 1860)
- STLW.exe (PID: 5996)
- JJKHQ.exe (PID: 1568)
- DOXSOEK.exe (PID: 6196)
- FOPWX.exe (PID: 924)
- FEY.exe (PID: 6800)
- TPUSASM.exe (PID: 4612)
- GSYRFK.exe (PID: 7076)
- LDUPKBK.exe (PID: 4716)
- JTTAWMZ.exe (PID: 6264)
- PDX.exe (PID: 3396)
- LBD.exe (PID: 6516)
- YMZC.exe (PID: 7080)
- YWHW.exe (PID: 6932)
- JPKOJ.exe (PID: 5836)
- XAHV.exe (PID: 1748)
- KDDTT.exe (PID: 3508)
- KVLVH.exe (PID: 4704)
- ODFD.exe (PID: 6432)
- CJLARU.exe (PID: 6980)
- BMKRFA.exe (PID: 1192)
- BKTXDN.exe (PID: 6836)
- GVPWIEM.exe (PID: 5008)
- MKWXRHH.exe (PID: 4380)
- EFNAVDP.exe (PID: 6404)
- KOSFZP.exe (PID: 5872)
- GTX.exe (PID: 5592)
- SMAV.exe (PID: 2748)
- FLWZTYT.exe (PID: 6652)
- ZEJO.exe (PID: 5072)
- QUIZ.exe (PID: 7152)
- HFGP.exe (PID: 7072)
- OQHQTD.exe (PID: 1724)
- FOOTFW.exe (PID: 6424)
- QGJMNEQ.exe (PID: 5352)
- LTOV.exe (PID: 4380)
- YWS.exe (PID: 1808)
- WKZUW.exe (PID: 4664)
- TQXKD.exe (PID: 3656)
- VCXR.exe (PID: 6092)
- ANT.exe (PID: 6348)
- ZON.exe (PID: 1728)
- NRCHOUR.exe (PID: 6332)
- PZE.exe (PID: 1324)
- ZCN.exe (PID: 380)
- CYZXON.exe (PID: 3644)
- ZHGH.exe (PID: 6476)
- NBOKZJL.exe (PID: 3956)
Creates a writable file in the system directory
- ZPHYQEF.exe (PID: 6748)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- FIXCWA.exe (PID: 6448)
- BGD.exe (PID: 6896)
- ZQIIW.exe (PID: 6656)
- KSFHZ.exe (PID: 6836)
- VLIA.exe (PID: 4628)
- NJRGGAL.exe (PID: 636)
- CTTIH.exe (PID: 3640)
- QWPO.exe (PID: 6308)
- AZHS.exe (PID: 6316)
- CPQ.exe (PID: 6348)
- OZDEYX.exe (PID: 6548)
- GCUI.exe (PID: 4264)
- QVEFCGG.exe (PID: 1720)
- CZIKK.exe (PID: 7060)
- FAL.exe (PID: 6292)
- UESPG.exe (PID: 4916)
- NFSZIM.exe (PID: 6436)
- UKAWEP.exe (PID: 32)
- NLAFGG.exe (PID: 5720)
- LKRA.exe (PID: 1604)
- YUN.exe (PID: 1864)
- RIN.exe (PID: 704)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- XYEY.exe (PID: 6676)
SUSPICIOUS
Reads the date of Windows installation
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- ZPHYQEF.exe (PID: 6748)
- OFU.exe (PID: 6968)
- PBHMRNL.exe (PID: 4716)
- AYXI.exe (PID: 7124)
- LYN.exe (PID: 4360)
- EMNO.exe (PID: 6384)
- ZJJ.exe (PID: 1604)
- MKNEG.exe (PID: 7088)
- GKGRXCS.exe (PID: 6856)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- DNMM.exe (PID: 5720)
- OZYGQK.exe (PID: 6672)
- OGPFK.exe (PID: 6276)
- MOXJC.exe (PID: 6860)
- OMYLIT.exe (PID: 5196)
- FIXCWA.exe (PID: 6448)
- OXHFWF.exe (PID: 3740)
- BGD.exe (PID: 6896)
- WVHV.exe (PID: 5548)
- DWFV.exe (PID: 4776)
- FYGC.exe (PID: 4284)
- XCGGEVL.exe (PID: 6364)
- USME.exe (PID: 4004)
- HCQDE.exe (PID: 6356)
- IZJMQBM.exe (PID: 1864)
- DAOA.exe (PID: 1616)
- LJLB.exe (PID: 3592)
- ZQIIW.exe (PID: 6656)
- STUCKC.exe (PID: 1752)
- URNWQ.exe (PID: 6320)
- WZPACS.exe (PID: 6368)
- UKWYWDU.exe (PID: 6448)
- KSFHZ.exe (PID: 6836)
- CAW.exe (PID: 2588)
- VLIA.exe (PID: 4628)
- MBHCLZ.exe (PID: 3592)
- OZIF.exe (PID: 3712)
- NJRGGAL.exe (PID: 636)
- RZLOJ.exe (PID: 4424)
- NHFW.exe (PID: 6736)
- VSOX.exe (PID: 4916)
- ELE.exe (PID: 4628)
- LQNAL.exe (PID: 3708)
- RWIKN.exe (PID: 624)
- CTTIH.exe (PID: 3640)
- QWPO.exe (PID: 6308)
- AZHS.exe (PID: 6316)
- TXSXD.exe (PID: 6652)
- NUTS.exe (PID: 5528)
- CPQ.exe (PID: 6348)
- TFPP.exe (PID: 4936)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- GCUI.exe (PID: 4264)
- OZDEYX.exe (PID: 6548)
- DSIYXP.exe (PID: 1728)
- DZAFJL.exe (PID: 3708)
- QVEFCGG.exe (PID: 1720)
- FAKCJQI.exe (PID: 5244)
- QTN.exe (PID: 6356)
- LOSN.exe (PID: 3740)
- OJM.exe (PID: 4148)
- BSRMY.exe (PID: 6840)
- CZIKK.exe (PID: 7060)
- FAL.exe (PID: 6292)
- UFRRI.exe (PID: 6276)
- FYUAZL.exe (PID: 6300)
- SVQUU.exe (PID: 6652)
- UESPG.exe (PID: 4916)
- HZEXZYK.exe (PID: 7144)
- RJXMVEU.exe (PID: 4264)
- UKAWEP.exe (PID: 32)
- NFSZIM.exe (PID: 6436)
- JKXWP.exe (PID: 2332)
- PNBVUN.exe (PID: 232)
- CJG.exe (PID: 4000)
- NLAFGG.exe (PID: 5720)
- PUCBSHW.exe (PID: 6204)
- LKRA.exe (PID: 1604)
- CWG.exe (PID: 5896)
- YUN.exe (PID: 1864)
- VSSV.exe (PID: 7040)
- RIN.exe (PID: 704)
- HYT.exe (PID: 6316)
- EDRD.exe (PID: 380)
- GBSFJ.exe (PID: 5556)
- CZQUQ.exe (PID: 3732)
- EXRWP.exe (PID: 3708)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- XYEY.exe (PID: 6676)
- BAY.exe (PID: 2764)
- LJA.exe (PID: 1204)
- ZOGUM.exe (PID: 7056)
Reads security settings of Internet Explorer
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- ZPHYQEF.exe (PID: 6748)
- OFU.exe (PID: 6968)
- PBHMRNL.exe (PID: 4716)
- AYXI.exe (PID: 7124)
- LYN.exe (PID: 4360)
- ZJJ.exe (PID: 1604)
- EMNO.exe (PID: 6384)
- GKGRXCS.exe (PID: 6856)
- MKNEG.exe (PID: 7088)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- DNMM.exe (PID: 5720)
- OZYGQK.exe (PID: 6672)
- OGPFK.exe (PID: 6276)
- OMYLIT.exe (PID: 5196)
- MOXJC.exe (PID: 6860)
- OXHFWF.exe (PID: 3740)
- FIXCWA.exe (PID: 6448)
- WVHV.exe (PID: 5548)
- BGD.exe (PID: 6896)
- DWFV.exe (PID: 4776)
- FYGC.exe (PID: 4284)
- XCGGEVL.exe (PID: 6364)
- USME.exe (PID: 4004)
- IZJMQBM.exe (PID: 1864)
- HCQDE.exe (PID: 6356)
- DAOA.exe (PID: 1616)
- LJLB.exe (PID: 3592)
- ZQIIW.exe (PID: 6656)
- STUCKC.exe (PID: 1752)
- URNWQ.exe (PID: 6320)
- UKWYWDU.exe (PID: 6448)
- WZPACS.exe (PID: 6368)
- KSFHZ.exe (PID: 6836)
- CAW.exe (PID: 2588)
- VLIA.exe (PID: 4628)
- MBHCLZ.exe (PID: 3592)
- OZIF.exe (PID: 3712)
- NJRGGAL.exe (PID: 636)
- RZLOJ.exe (PID: 4424)
- NHFW.exe (PID: 6736)
- VSOX.exe (PID: 4916)
- LQNAL.exe (PID: 3708)
- ELE.exe (PID: 4628)
- RWIKN.exe (PID: 624)
- CTTIH.exe (PID: 3640)
- QWPO.exe (PID: 6308)
- TXSXD.exe (PID: 6652)
- AZHS.exe (PID: 6316)
- NUTS.exe (PID: 5528)
- CPQ.exe (PID: 6348)
- TFPP.exe (PID: 4936)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- OZDEYX.exe (PID: 6548)
- GCUI.exe (PID: 4264)
- DZAFJL.exe (PID: 3708)
- DSIYXP.exe (PID: 1728)
- QVEFCGG.exe (PID: 1720)
- FAKCJQI.exe (PID: 5244)
- QTN.exe (PID: 6356)
- OJM.exe (PID: 4148)
- LOSN.exe (PID: 3740)
- CZIKK.exe (PID: 7060)
- BSRMY.exe (PID: 6840)
- UFRRI.exe (PID: 6276)
- FAL.exe (PID: 6292)
- FYUAZL.exe (PID: 6300)
- SVQUU.exe (PID: 6652)
- UESPG.exe (PID: 4916)
- HZEXZYK.exe (PID: 7144)
- RJXMVEU.exe (PID: 4264)
- UKAWEP.exe (PID: 32)
- NFSZIM.exe (PID: 6436)
- PNBVUN.exe (PID: 232)
- JKXWP.exe (PID: 2332)
- NLAFGG.exe (PID: 5720)
- CJG.exe (PID: 4000)
- PUCBSHW.exe (PID: 6204)
- CWG.exe (PID: 5896)
- LKRA.exe (PID: 1604)
- YUN.exe (PID: 1864)
- VSSV.exe (PID: 7040)
- RIN.exe (PID: 704)
- HYT.exe (PID: 6316)
- EDRD.exe (PID: 380)
- GBSFJ.exe (PID: 5556)
- CZQUQ.exe (PID: 3732)
- EXRWP.exe (PID: 3708)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- BAY.exe (PID: 2764)
- XYEY.exe (PID: 6676)
- LJA.exe (PID: 1204)
- ZOGUM.exe (PID: 7056)
Starts CMD.EXE for commands execution
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- ZPHYQEF.exe (PID: 6748)
- OFU.exe (PID: 6968)
- AYXI.exe (PID: 7124)
- PBHMRNL.exe (PID: 4716)
- LYN.exe (PID: 4360)
- ZJJ.exe (PID: 1604)
- EMNO.exe (PID: 6384)
- GKGRXCS.exe (PID: 6856)
- MKNEG.exe (PID: 7088)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- DNMM.exe (PID: 5720)
- OGPFK.exe (PID: 6276)
- OZYGQK.exe (PID: 6672)
- MOXJC.exe (PID: 6860)
- OMYLIT.exe (PID: 5196)
- FIXCWA.exe (PID: 6448)
- OXHFWF.exe (PID: 3740)
- WVHV.exe (PID: 5548)
- BGD.exe (PID: 6896)
- DWFV.exe (PID: 4776)
- XCGGEVL.exe (PID: 6364)
- FYGC.exe (PID: 4284)
- USME.exe (PID: 4004)
- IZJMQBM.exe (PID: 1864)
- HCQDE.exe (PID: 6356)
- DAOA.exe (PID: 1616)
- ZQIIW.exe (PID: 6656)
- LJLB.exe (PID: 3592)
- STUCKC.exe (PID: 1752)
- URNWQ.exe (PID: 6320)
- UKWYWDU.exe (PID: 6448)
- WZPACS.exe (PID: 6368)
- CAW.exe (PID: 2588)
- KSFHZ.exe (PID: 6836)
- VLIA.exe (PID: 4628)
- MBHCLZ.exe (PID: 3592)
- OZIF.exe (PID: 3712)
- RZLOJ.exe (PID: 4424)
- NJRGGAL.exe (PID: 636)
- VSOX.exe (PID: 4916)
- NHFW.exe (PID: 6736)
- ELE.exe (PID: 4628)
- LQNAL.exe (PID: 3708)
- RWIKN.exe (PID: 624)
- QWPO.exe (PID: 6308)
- CTTIH.exe (PID: 3640)
- AZHS.exe (PID: 6316)
- TXSXD.exe (PID: 6652)
- NUTS.exe (PID: 5528)
- CPQ.exe (PID: 6348)
- TFPP.exe (PID: 4936)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- OZDEYX.exe (PID: 6548)
- GCUI.exe (PID: 4264)
- DZAFJL.exe (PID: 3708)
- DSIYXP.exe (PID: 1728)
- QVEFCGG.exe (PID: 1720)
- QTN.exe (PID: 6356)
- FAKCJQI.exe (PID: 5244)
- OJM.exe (PID: 4148)
- LOSN.exe (PID: 3740)
- CZIKK.exe (PID: 7060)
- BSRMY.exe (PID: 6840)
- FAL.exe (PID: 6292)
- UFRRI.exe (PID: 6276)
- FYUAZL.exe (PID: 6300)
- SVQUU.exe (PID: 6652)
- UESPG.exe (PID: 4916)
- HZEXZYK.exe (PID: 7144)
- RJXMVEU.exe (PID: 4264)
- UKAWEP.exe (PID: 32)
- NFSZIM.exe (PID: 6436)
- JKXWP.exe (PID: 2332)
- NLAFGG.exe (PID: 5720)
- PNBVUN.exe (PID: 232)
- PUCBSHW.exe (PID: 6204)
- CJG.exe (PID: 4000)
- LKRA.exe (PID: 1604)
- CWG.exe (PID: 5896)
- YUN.exe (PID: 1864)
- VSSV.exe (PID: 7040)
- RIN.exe (PID: 704)
- EDRD.exe (PID: 380)
- GBSFJ.exe (PID: 5556)
- HYT.exe (PID: 6316)
- CZQUQ.exe (PID: 3732)
- EXRWP.exe (PID: 3708)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- BAY.exe (PID: 2764)
- XYEY.exe (PID: 6676)
- LJA.exe (PID: 1204)
- ZOGUM.exe (PID: 7056)
- JXIYGR.exe (PID: 2304)
- ZNOAKL.exe (PID: 3808)
- NXKZP.exe (PID: 5952)
- WMMRT.exe (PID: 4148)
- JVQWEM.exe (PID: 7120)
- UOL.exe (PID: 6124)
- JTRMUDH.exe (PID: 6416)
- NJFC.exe (PID: 5592)
- FZXB.exe (PID: 1488)
- EUWA.exe (PID: 7132)
- USDD.exe (PID: 6284)
- RPAAH.exe (PID: 6688)
- NGVI.exe (PID: 2288)
- ILIJJ.exe (PID: 4360)
- TELCRCL.exe (PID: 6408)
- XMFKU.exe (PID: 380)
- GDGOX.exe (PID: 6672)
- LGKMCD.exe (PID: 232)
- NKMNGNW.exe (PID: 588)
- PSOQSOS.exe (PID: 1728)
- PAFPM.exe (PID: 2580)
- MYUFHXM.exe (PID: 3648)
- QGO.exe (PID: 4036)
- BZRGLMX.exe (PID: 6552)
- PEPD.exe (PID: 5352)
- XPXE.exe (PID: 6348)
- QCXJ.exe (PID: 7064)
- USRRBHG.exe (PID: 6180)
- KIYU.exe (PID: 2524)
- QIGI.exe (PID: 2104)
- ZMYZ.exe (PID: 6892)
- DLCOB.exe (PID: 2588)
- XJDI.exe (PID: 2608)
- FCEKNN.exe (PID: 7152)
- SDJ.exe (PID: 3680)
- QFP.exe (PID: 4544)
- HSFMT.exe (PID: 6300)
- QSP.exe (PID: 4312)
- AZSM.exe (PID: 7060)
- PGX.exe (PID: 5280)
- SQJ.exe (PID: 2132)
- HWO.exe (PID: 6716)
- YNAFWKM.exe (PID: 1572)
- LYEMBB.exe (PID: 2896)
- WFYKKJ.exe (PID: 2736)
- LKEHRT.exe (PID: 2044)
- EWE.exe (PID: 2088)
- RHIQENV.exe (PID: 4636)
- NEOO.exe (PID: 2392)
- RBAKGTJ.exe (PID: 6976)
- ELERTK.exe (PID: 4524)
- PCH.exe (PID: 4484)
- GSOSDGN.exe (PID: 6404)
- TDK.exe (PID: 5232)
- TNTS.exe (PID: 6276)
- EGOLE.exe (PID: 3656)
- KGVZNLM.exe (PID: 4936)
- DJVCS.exe (PID: 1748)
- QURBXG.exe (PID: 3100)
- ESXYEI.exe (PID: 1728)
- ZYYRTB.exe (PID: 3648)
- KVBOFHE.exe (PID: 2008)
- JGZMFCZ.exe (PID: 1176)
- GGHA.exe (PID: 2480)
- DQVBQ.exe (PID: 5608)
- URD.exe (PID: 2484)
- FKGR.exe (PID: 6408)
- QHSXW.exe (PID: 5080)
- SFLRUY.exe (PID: 5720)
- FIHYZ.exe (PID: 1860)
- STLW.exe (PID: 5996)
- JJKHQ.exe (PID: 1568)
- FOPWX.exe (PID: 924)
- DOXSOEK.exe (PID: 6196)
- GSYRFK.exe (PID: 7076)
- TPUSASM.exe (PID: 4612)
- LDUPKBK.exe (PID: 4716)
- JTTAWMZ.exe (PID: 6264)
- FEY.exe (PID: 6800)
- PDX.exe (PID: 3396)
- LBD.exe (PID: 6516)
- YMZC.exe (PID: 7080)
- YWHW.exe (PID: 6932)
- KDDTT.exe (PID: 3508)
- KVLVH.exe (PID: 4704)
- JPKOJ.exe (PID: 5836)
- XAHV.exe (PID: 1748)
- NBOKZJL.exe (PID: 3956)
- BMKRFA.exe (PID: 1192)
- ODFD.exe (PID: 6432)
- EFNAVDP.exe (PID: 6404)
- BKTXDN.exe (PID: 6836)
- GVPWIEM.exe (PID: 5008)
- MKWXRHH.exe (PID: 4380)
- FLWZTYT.exe (PID: 6652)
- KOSFZP.exe (PID: 5872)
- GTX.exe (PID: 5592)
- ZEJO.exe (PID: 5072)
- QUIZ.exe (PID: 7152)
- HFGP.exe (PID: 7072)
- OQHQTD.exe (PID: 1724)
- SMAV.exe (PID: 2748)
- FOOTFW.exe (PID: 6424)
- LTOV.exe (PID: 4380)
- YWS.exe (PID: 1808)
- QGJMNEQ.exe (PID: 5352)
- VCXR.exe (PID: 6092)
- ANT.exe (PID: 6348)
- WKZUW.exe (PID: 4664)
- TQXKD.exe (PID: 3656)
- NRCHOUR.exe (PID: 6332)
- ZON.exe (PID: 1728)
- CYZXON.exe (PID: 3644)
- PZE.exe (PID: 1324)
- ZCN.exe (PID: 380)
- ZHGH.exe (PID: 6476)
- CJLARU.exe (PID: 6980)
Executable content was dropped or overwritten
- ZPHYQEF.exe (PID: 6748)
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- OFU.exe (PID: 6968)
- AYXI.exe (PID: 7124)
- PBHMRNL.exe (PID: 4716)
- LYN.exe (PID: 4360)
- ZJJ.exe (PID: 1604)
- EMNO.exe (PID: 6384)
- GKGRXCS.exe (PID: 6856)
- MKNEG.exe (PID: 7088)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- DNMM.exe (PID: 5720)
- OGPFK.exe (PID: 6276)
- OZYGQK.exe (PID: 6672)
- MOXJC.exe (PID: 6860)
- OMYLIT.exe (PID: 5196)
- FIXCWA.exe (PID: 6448)
- WVHV.exe (PID: 5548)
- OXHFWF.exe (PID: 3740)
- BGD.exe (PID: 6896)
- DWFV.exe (PID: 4776)
- FYGC.exe (PID: 4284)
- XCGGEVL.exe (PID: 6364)
- IZJMQBM.exe (PID: 1864)
- HCQDE.exe (PID: 6356)
- USME.exe (PID: 4004)
- ZQIIW.exe (PID: 6656)
- DAOA.exe (PID: 1616)
- LJLB.exe (PID: 3592)
- URNWQ.exe (PID: 6320)
- STUCKC.exe (PID: 1752)
- WZPACS.exe (PID: 6368)
- CAW.exe (PID: 2588)
- UKWYWDU.exe (PID: 6448)
- KSFHZ.exe (PID: 6836)
- VLIA.exe (PID: 4628)
- MBHCLZ.exe (PID: 3592)
- NJRGGAL.exe (PID: 636)
- OZIF.exe (PID: 3712)
- RZLOJ.exe (PID: 4424)
- NHFW.exe (PID: 6736)
- VSOX.exe (PID: 4916)
- LQNAL.exe (PID: 3708)
- ELE.exe (PID: 4628)
- CTTIH.exe (PID: 3640)
- RWIKN.exe (PID: 624)
- AZHS.exe (PID: 6316)
- QWPO.exe (PID: 6308)
- TXSXD.exe (PID: 6652)
- NUTS.exe (PID: 5528)
- CPQ.exe (PID: 6348)
- TFPP.exe (PID: 4936)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- GCUI.exe (PID: 4264)
- OZDEYX.exe (PID: 6548)
- DZAFJL.exe (PID: 3708)
- DSIYXP.exe (PID: 1728)
- QVEFCGG.exe (PID: 1720)
- FAKCJQI.exe (PID: 5244)
- QTN.exe (PID: 6356)
- OJM.exe (PID: 4148)
- CZIKK.exe (PID: 7060)
- LOSN.exe (PID: 3740)
- BSRMY.exe (PID: 6840)
- FAL.exe (PID: 6292)
- UFRRI.exe (PID: 6276)
- FYUAZL.exe (PID: 6300)
- SVQUU.exe (PID: 6652)
- UESPG.exe (PID: 4916)
- RJXMVEU.exe (PID: 4264)
- HZEXZYK.exe (PID: 7144)
- NFSZIM.exe (PID: 6436)
- UKAWEP.exe (PID: 32)
- JKXWP.exe (PID: 2332)
- PNBVUN.exe (PID: 232)
- NLAFGG.exe (PID: 5720)
- CJG.exe (PID: 4000)
- PUCBSHW.exe (PID: 6204)
- CWG.exe (PID: 5896)
- LKRA.exe (PID: 1604)
- VSSV.exe (PID: 7040)
- YUN.exe (PID: 1864)
- RIN.exe (PID: 704)
- HYT.exe (PID: 6316)
- EDRD.exe (PID: 380)
- GBSFJ.exe (PID: 5556)
- CZQUQ.exe (PID: 3732)
- EXRWP.exe (PID: 3708)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- XYEY.exe (PID: 6676)
- BAY.exe (PID: 2764)
- LJA.exe (PID: 1204)
- ZOGUM.exe (PID: 7056)
- WMMRT.exe (PID: 4148)
- JXIYGR.exe (PID: 2304)
- ZNOAKL.exe (PID: 3808)
- JVQWEM.exe (PID: 7120)
- NXKZP.exe (PID: 5952)
- JTRMUDH.exe (PID: 6416)
- NJFC.exe (PID: 5592)
- UOL.exe (PID: 6124)
- FZXB.exe (PID: 1488)
- RPAAH.exe (PID: 6688)
- USDD.exe (PID: 6284)
- NGVI.exe (PID: 2288)
- EUWA.exe (PID: 7132)
- LGKMCD.exe (PID: 232)
- ILIJJ.exe (PID: 4360)
- TELCRCL.exe (PID: 6408)
- XMFKU.exe (PID: 380)
- GDGOX.exe (PID: 6672)
- NKMNGNW.exe (PID: 588)
- PSOQSOS.exe (PID: 1728)
- MYUFHXM.exe (PID: 3648)
- PAFPM.exe (PID: 2580)
- XPXE.exe (PID: 6348)
- BZRGLMX.exe (PID: 6552)
- PEPD.exe (PID: 5352)
- ZMYZ.exe (PID: 6892)
- QGO.exe (PID: 4036)
- QCXJ.exe (PID: 7064)
- USRRBHG.exe (PID: 6180)
- KIYU.exe (PID: 2524)
- QIGI.exe (PID: 2104)
- DLCOB.exe (PID: 2588)
- XJDI.exe (PID: 2608)
- FCEKNN.exe (PID: 7152)
- SDJ.exe (PID: 3680)
- QFP.exe (PID: 4544)
- HSFMT.exe (PID: 6300)
- QSP.exe (PID: 4312)
- SQJ.exe (PID: 2132)
- HWO.exe (PID: 6716)
- PGX.exe (PID: 5280)
- AZSM.exe (PID: 7060)
- LKEHRT.exe (PID: 2044)
- LYEMBB.exe (PID: 2896)
- WFYKKJ.exe (PID: 2736)
- YNAFWKM.exe (PID: 1572)
- ELERTK.exe (PID: 4524)
- NEOO.exe (PID: 2392)
- RHIQENV.exe (PID: 4636)
- RBAKGTJ.exe (PID: 6976)
- EWE.exe (PID: 2088)
- PCH.exe (PID: 4484)
- GSOSDGN.exe (PID: 6404)
- TDK.exe (PID: 5232)
- TNTS.exe (PID: 6276)
- EGOLE.exe (PID: 3656)
- KGVZNLM.exe (PID: 4936)
- DJVCS.exe (PID: 1748)
- QURBXG.exe (PID: 3100)
- ESXYEI.exe (PID: 1728)
- KVBOFHE.exe (PID: 2008)
- ZYYRTB.exe (PID: 3648)
- JGZMFCZ.exe (PID: 1176)
- GGHA.exe (PID: 2480)
- DQVBQ.exe (PID: 5608)
- FKGR.exe (PID: 6408)
- SFLRUY.exe (PID: 5720)
- QHSXW.exe (PID: 5080)
- FIHYZ.exe (PID: 1860)
- URD.exe (PID: 2484)
- STLW.exe (PID: 5996)
- JJKHQ.exe (PID: 1568)
- FOPWX.exe (PID: 924)
- DOXSOEK.exe (PID: 6196)
- FEY.exe (PID: 6800)
- TPUSASM.exe (PID: 4612)
- GSYRFK.exe (PID: 7076)
- LDUPKBK.exe (PID: 4716)
- PDX.exe (PID: 3396)
- JTTAWMZ.exe (PID: 6264)
- LBD.exe (PID: 6516)
- YMZC.exe (PID: 7080)
- YWHW.exe (PID: 6932)
- JPKOJ.exe (PID: 5836)
- XAHV.exe (PID: 1748)
- KDDTT.exe (PID: 3508)
- KVLVH.exe (PID: 4704)
- ODFD.exe (PID: 6432)
- NBOKZJL.exe (PID: 3956)
- BMKRFA.exe (PID: 1192)
- MKWXRHH.exe (PID: 4380)
- CJLARU.exe (PID: 6980)
- BKTXDN.exe (PID: 6836)
- GVPWIEM.exe (PID: 5008)
- EFNAVDP.exe (PID: 6404)
- GTX.exe (PID: 5592)
- SMAV.exe (PID: 2748)
- FLWZTYT.exe (PID: 6652)
- KOSFZP.exe (PID: 5872)
- ZEJO.exe (PID: 5072)
- HFGP.exe (PID: 7072)
- QUIZ.exe (PID: 7152)
- OQHQTD.exe (PID: 1724)
- FOOTFW.exe (PID: 6424)
- QGJMNEQ.exe (PID: 5352)
- LTOV.exe (PID: 4380)
- YWS.exe (PID: 1808)
- VCXR.exe (PID: 6092)
- ANT.exe (PID: 6348)
- WKZUW.exe (PID: 4664)
- TQXKD.exe (PID: 3656)
- NRCHOUR.exe (PID: 6332)
- ZON.exe (PID: 1728)
- PZE.exe (PID: 1324)
- CYZXON.exe (PID: 3644)
- ZHGH.exe (PID: 6476)
- ZCN.exe (PID: 380)
Executing commands from a ".bat" file
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- ZPHYQEF.exe (PID: 6748)
- OFU.exe (PID: 6968)
- PBHMRNL.exe (PID: 4716)
- AYXI.exe (PID: 7124)
- LYN.exe (PID: 4360)
- EMNO.exe (PID: 6384)
- ZJJ.exe (PID: 1604)
- GKGRXCS.exe (PID: 6856)
- MKNEG.exe (PID: 7088)
- UDWYU.exe (PID: 4940)
- DNMM.exe (PID: 5720)
- OSPAS.exe (PID: 6352)
- OGPFK.exe (PID: 6276)
- OZYGQK.exe (PID: 6672)
- MOXJC.exe (PID: 6860)
- OMYLIT.exe (PID: 5196)
- OXHFWF.exe (PID: 3740)
- FIXCWA.exe (PID: 6448)
- WVHV.exe (PID: 5548)
- BGD.exe (PID: 6896)
- DWFV.exe (PID: 4776)
- XCGGEVL.exe (PID: 6364)
- FYGC.exe (PID: 4284)
- USME.exe (PID: 4004)
- IZJMQBM.exe (PID: 1864)
- HCQDE.exe (PID: 6356)
- DAOA.exe (PID: 1616)
- ZQIIW.exe (PID: 6656)
- LJLB.exe (PID: 3592)
- STUCKC.exe (PID: 1752)
- URNWQ.exe (PID: 6320)
- UKWYWDU.exe (PID: 6448)
- WZPACS.exe (PID: 6368)
- CAW.exe (PID: 2588)
- KSFHZ.exe (PID: 6836)
- VLIA.exe (PID: 4628)
- MBHCLZ.exe (PID: 3592)
- OZIF.exe (PID: 3712)
- RZLOJ.exe (PID: 4424)
- NJRGGAL.exe (PID: 636)
- VSOX.exe (PID: 4916)
- NHFW.exe (PID: 6736)
- ELE.exe (PID: 4628)
- LQNAL.exe (PID: 3708)
- RWIKN.exe (PID: 624)
- QWPO.exe (PID: 6308)
- CTTIH.exe (PID: 3640)
- AZHS.exe (PID: 6316)
- TXSXD.exe (PID: 6652)
- NUTS.exe (PID: 5528)
- CPQ.exe (PID: 6348)
- TFPP.exe (PID: 4936)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- OZDEYX.exe (PID: 6548)
- GCUI.exe (PID: 4264)
- DZAFJL.exe (PID: 3708)
- DSIYXP.exe (PID: 1728)
- QVEFCGG.exe (PID: 1720)
- QTN.exe (PID: 6356)
- FAKCJQI.exe (PID: 5244)
- OJM.exe (PID: 4148)
- LOSN.exe (PID: 3740)
- BSRMY.exe (PID: 6840)
- CZIKK.exe (PID: 7060)
- FAL.exe (PID: 6292)
- UFRRI.exe (PID: 6276)
- SVQUU.exe (PID: 6652)
- UESPG.exe (PID: 4916)
- FYUAZL.exe (PID: 6300)
- HZEXZYK.exe (PID: 7144)
- RJXMVEU.exe (PID: 4264)
- UKAWEP.exe (PID: 32)
- PNBVUN.exe (PID: 232)
- NFSZIM.exe (PID: 6436)
- JKXWP.exe (PID: 2332)
- NLAFGG.exe (PID: 5720)
- PUCBSHW.exe (PID: 6204)
- CJG.exe (PID: 4000)
- LKRA.exe (PID: 1604)
- CWG.exe (PID: 5896)
- VSSV.exe (PID: 7040)
- YUN.exe (PID: 1864)
- RIN.exe (PID: 704)
- HYT.exe (PID: 6316)
- EDRD.exe (PID: 380)
- CZQUQ.exe (PID: 3732)
- EXRWP.exe (PID: 3708)
- GBSFJ.exe (PID: 5556)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- BAY.exe (PID: 2764)
- XYEY.exe (PID: 6676)
- ZOGUM.exe (PID: 7056)
- LJA.exe (PID: 1204)
- WMMRT.exe (PID: 4148)
- JXIYGR.exe (PID: 2304)
- ZNOAKL.exe (PID: 3808)
- NXKZP.exe (PID: 5952)
- JVQWEM.exe (PID: 7120)
- UOL.exe (PID: 6124)
- JTRMUDH.exe (PID: 6416)
- FZXB.exe (PID: 1488)
- NJFC.exe (PID: 5592)
- USDD.exe (PID: 6284)
- RPAAH.exe (PID: 6688)
- NGVI.exe (PID: 2288)
- EUWA.exe (PID: 7132)
- LGKMCD.exe (PID: 232)
- ILIJJ.exe (PID: 4360)
- TELCRCL.exe (PID: 6408)
- GDGOX.exe (PID: 6672)
- PAFPM.exe (PID: 2580)
- PSOQSOS.exe (PID: 1728)
- XMFKU.exe (PID: 380)
- NKMNGNW.exe (PID: 588)
- MYUFHXM.exe (PID: 3648)
- BZRGLMX.exe (PID: 6552)
- XPXE.exe (PID: 6348)
- QGO.exe (PID: 4036)
- PEPD.exe (PID: 5352)
- QCXJ.exe (PID: 7064)
- USRRBHG.exe (PID: 6180)
- KIYU.exe (PID: 2524)
- QIGI.exe (PID: 2104)
- ZMYZ.exe (PID: 6892)
- DLCOB.exe (PID: 2588)
- FCEKNN.exe (PID: 7152)
- XJDI.exe (PID: 2608)
- SDJ.exe (PID: 3680)
- HSFMT.exe (PID: 6300)
- QFP.exe (PID: 4544)
- QSP.exe (PID: 4312)
- HWO.exe (PID: 6716)
- PGX.exe (PID: 5280)
- AZSM.exe (PID: 7060)
- SQJ.exe (PID: 2132)
- LKEHRT.exe (PID: 2044)
- LYEMBB.exe (PID: 2896)
- WFYKKJ.exe (PID: 2736)
- YNAFWKM.exe (PID: 1572)
- ELERTK.exe (PID: 4524)
- NEOO.exe (PID: 2392)
- RBAKGTJ.exe (PID: 6976)
- EWE.exe (PID: 2088)
- RHIQENV.exe (PID: 4636)
- GSOSDGN.exe (PID: 6404)
- TDK.exe (PID: 5232)
- TNTS.exe (PID: 6276)
- PCH.exe (PID: 4484)
- KGVZNLM.exe (PID: 4936)
- DJVCS.exe (PID: 1748)
- QURBXG.exe (PID: 3100)
- ESXYEI.exe (PID: 1728)
- EGOLE.exe (PID: 3656)
- DQVBQ.exe (PID: 5608)
- ZYYRTB.exe (PID: 3648)
- KVBOFHE.exe (PID: 2008)
- JGZMFCZ.exe (PID: 1176)
- GGHA.exe (PID: 2480)
- URD.exe (PID: 2484)
- FKGR.exe (PID: 6408)
- QHSXW.exe (PID: 5080)
- SFLRUY.exe (PID: 5720)
- FIHYZ.exe (PID: 1860)
- STLW.exe (PID: 5996)
- JJKHQ.exe (PID: 1568)
- FOPWX.exe (PID: 924)
- DOXSOEK.exe (PID: 6196)
- FEY.exe (PID: 6800)
- TPUSASM.exe (PID: 4612)
- GSYRFK.exe (PID: 7076)
- LDUPKBK.exe (PID: 4716)
- JTTAWMZ.exe (PID: 6264)
- LBD.exe (PID: 6516)
- YMZC.exe (PID: 7080)
- YWHW.exe (PID: 6932)
- PDX.exe (PID: 3396)
- XAHV.exe (PID: 1748)
- KDDTT.exe (PID: 3508)
- KVLVH.exe (PID: 4704)
- JPKOJ.exe (PID: 5836)
- NBOKZJL.exe (PID: 3956)
- BMKRFA.exe (PID: 1192)
- ODFD.exe (PID: 6432)
- CJLARU.exe (PID: 6980)
- EFNAVDP.exe (PID: 6404)
- BKTXDN.exe (PID: 6836)
- MKWXRHH.exe (PID: 4380)
- GTX.exe (PID: 5592)
- GVPWIEM.exe (PID: 5008)
- FLWZTYT.exe (PID: 6652)
- KOSFZP.exe (PID: 5872)
- QUIZ.exe (PID: 7152)
- HFGP.exe (PID: 7072)
- SMAV.exe (PID: 2748)
- ZEJO.exe (PID: 5072)
- OQHQTD.exe (PID: 1724)
- FOOTFW.exe (PID: 6424)
- YWS.exe (PID: 1808)
- QGJMNEQ.exe (PID: 5352)
- LTOV.exe (PID: 4380)
- VCXR.exe (PID: 6092)
- ANT.exe (PID: 6348)
- WKZUW.exe (PID: 4664)
- TQXKD.exe (PID: 3656)
- CYZXON.exe (PID: 3644)
- NRCHOUR.exe (PID: 6332)
- ZON.exe (PID: 1728)
- PZE.exe (PID: 1324)
- ZCN.exe (PID: 380)
- ZHGH.exe (PID: 6476)
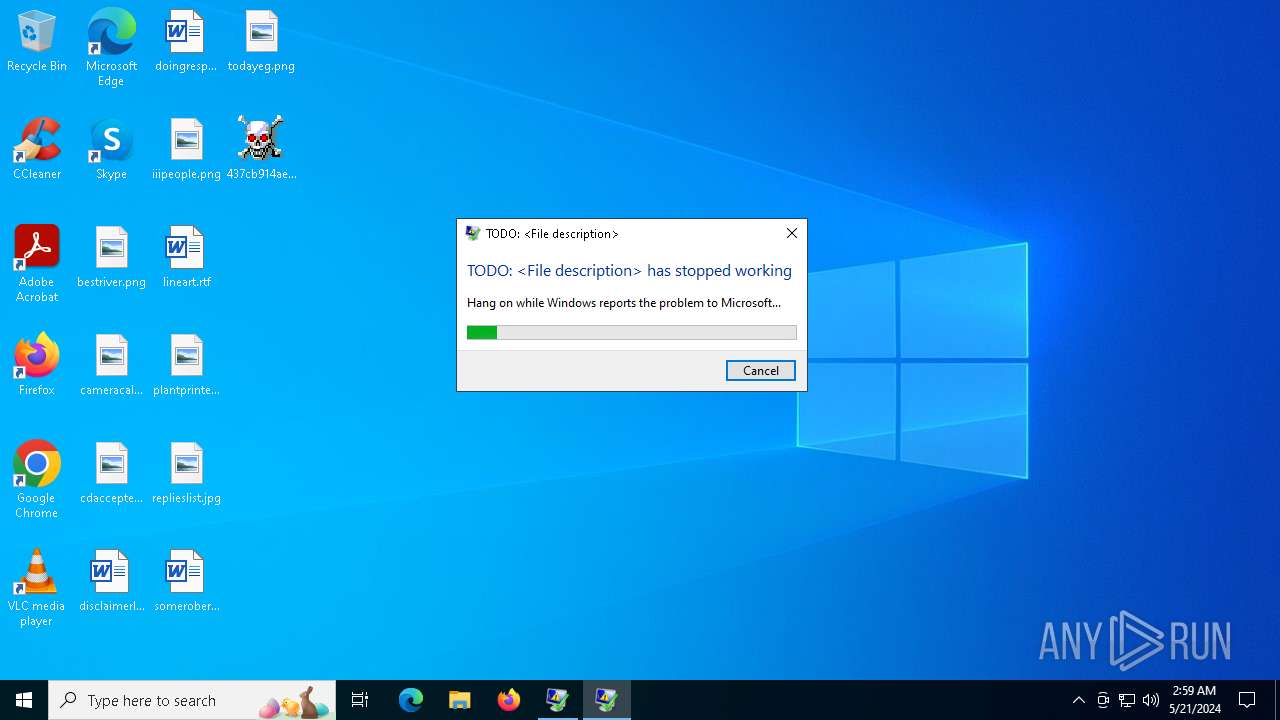
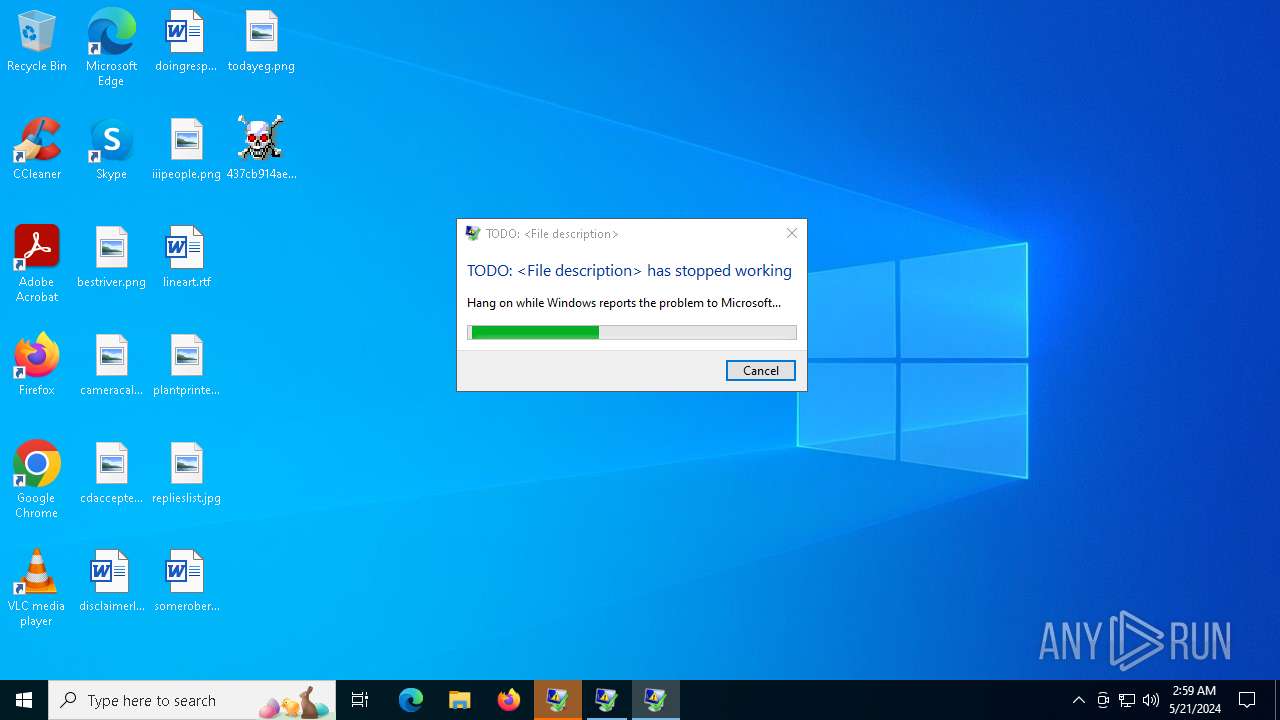
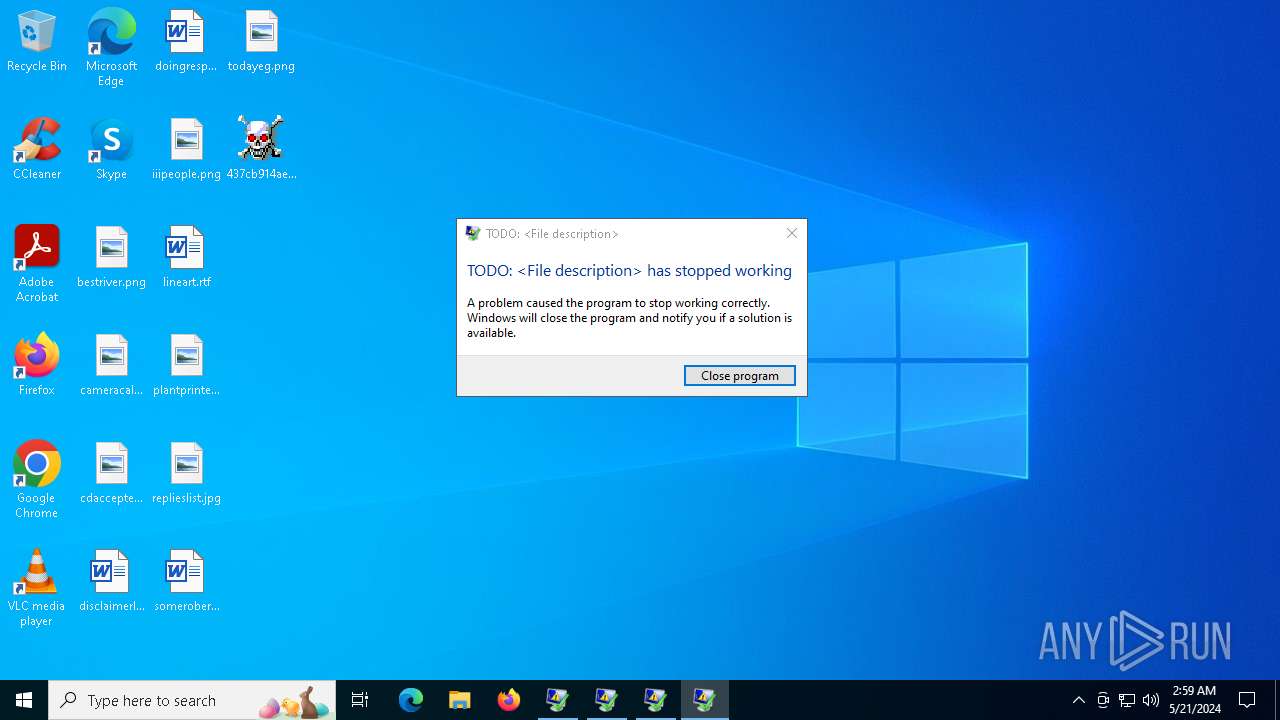
Executes application which crashes
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- ZPHYQEF.exe (PID: 6748)
- OFU.exe (PID: 6968)
- AYXI.exe (PID: 7124)
- OGPFK.exe (PID: 6276)
- WVHV.exe (PID: 5548)
- KSFHZ.exe (PID: 6836)
- NHFW.exe (PID: 6736)
- RWIKN.exe (PID: 624)
- TXSXD.exe (PID: 6652)
- RJWG.exe (PID: 7080)
- QVEFCGG.exe (PID: 1720)
- CZIKK.exe (PID: 7060)
- FYUAZL.exe (PID: 6300)
- LKRA.exe (PID: 1604)
- WMMRT.exe (PID: 4148)
- RPAAH.exe (PID: 6688)
- TELCRCL.exe (PID: 6408)
- ZMYZ.exe (PID: 6892)
- SQJ.exe (PID: 2132)
- LKEHRT.exe (PID: 2044)
- RHIQENV.exe (PID: 4636)
- TNTS.exe (PID: 6276)
- DQVBQ.exe (PID: 5608)
- FKGR.exe (PID: 6408)
- FOPWX.exe (PID: 924)
- GSYRFK.exe (PID: 7076)
- YWHW.exe (PID: 6932)
- CJLARU.exe (PID: 6980)
- GVPWIEM.exe (PID: 5008)
- SMAV.exe (PID: 2748)
- TQXKD.exe (PID: 3656)
- ZCN.exe (PID: 380)
INFO
Reads the computer name
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- ZPHYQEF.exe (PID: 6748)
- OFU.exe (PID: 6968)
- AYXI.exe (PID: 7124)
- PBHMRNL.exe (PID: 4716)
- ZJJ.exe (PID: 1604)
- LYN.exe (PID: 4360)
- EMNO.exe (PID: 6384)
- GKGRXCS.exe (PID: 6856)
- MKNEG.exe (PID: 7088)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- DNMM.exe (PID: 5720)
- OGPFK.exe (PID: 6276)
- OZYGQK.exe (PID: 6672)
- MOXJC.exe (PID: 6860)
- OMYLIT.exe (PID: 5196)
- OXHFWF.exe (PID: 3740)
- FIXCWA.exe (PID: 6448)
- WVHV.exe (PID: 5548)
- BGD.exe (PID: 6896)
- FYGC.exe (PID: 4284)
- DWFV.exe (PID: 4776)
- XCGGEVL.exe (PID: 6364)
- IZJMQBM.exe (PID: 1864)
- USME.exe (PID: 4004)
- HCQDE.exe (PID: 6356)
- DAOA.exe (PID: 1616)
- ZQIIW.exe (PID: 6656)
- LJLB.exe (PID: 3592)
- STUCKC.exe (PID: 1752)
- URNWQ.exe (PID: 6320)
- UKWYWDU.exe (PID: 6448)
- WZPACS.exe (PID: 6368)
- CAW.exe (PID: 2588)
- KSFHZ.exe (PID: 6836)
- MBHCLZ.exe (PID: 3592)
- VLIA.exe (PID: 4628)
- NJRGGAL.exe (PID: 636)
- OZIF.exe (PID: 3712)
- RZLOJ.exe (PID: 4424)
- NHFW.exe (PID: 6736)
- VSOX.exe (PID: 4916)
- LQNAL.exe (PID: 3708)
- RWIKN.exe (PID: 624)
- ELE.exe (PID: 4628)
- CTTIH.exe (PID: 3640)
- AZHS.exe (PID: 6316)
- QWPO.exe (PID: 6308)
- TXSXD.exe (PID: 6652)
- CPQ.exe (PID: 6348)
- TFPP.exe (PID: 4936)
- NUTS.exe (PID: 5528)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- OZDEYX.exe (PID: 6548)
- GCUI.exe (PID: 4264)
- DZAFJL.exe (PID: 3708)
- DSIYXP.exe (PID: 1728)
- QVEFCGG.exe (PID: 1720)
- FAKCJQI.exe (PID: 5244)
- QTN.exe (PID: 6356)
- OJM.exe (PID: 4148)
- LOSN.exe (PID: 3740)
- CZIKK.exe (PID: 7060)
- BSRMY.exe (PID: 6840)
- FAL.exe (PID: 6292)
- UFRRI.exe (PID: 6276)
- FYUAZL.exe (PID: 6300)
- SVQUU.exe (PID: 6652)
- UESPG.exe (PID: 4916)
- RJXMVEU.exe (PID: 4264)
- HZEXZYK.exe (PID: 7144)
- UKAWEP.exe (PID: 32)
- NFSZIM.exe (PID: 6436)
- PNBVUN.exe (PID: 232)
- JKXWP.exe (PID: 2332)
- NLAFGG.exe (PID: 5720)
- CJG.exe (PID: 4000)
- PUCBSHW.exe (PID: 6204)
- CWG.exe (PID: 5896)
- LKRA.exe (PID: 1604)
- YUN.exe (PID: 1864)
- VSSV.exe (PID: 7040)
- RIN.exe (PID: 704)
- HYT.exe (PID: 6316)
- GBSFJ.exe (PID: 5556)
- EDRD.exe (PID: 380)
- EXRWP.exe (PID: 3708)
- CZQUQ.exe (PID: 3732)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- XYEY.exe (PID: 6676)
- BAY.exe (PID: 2764)
- LJA.exe (PID: 1204)
- ZOGUM.exe (PID: 7056)
- WMMRT.exe (PID: 4148)
Checks supported languages
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- ZPHYQEF.exe (PID: 6748)
- AYXI.exe (PID: 7124)
- OFU.exe (PID: 6968)
- PBHMRNL.exe (PID: 4716)
- LYN.exe (PID: 4360)
- ZJJ.exe (PID: 1604)
- EMNO.exe (PID: 6384)
- GKGRXCS.exe (PID: 6856)
- MKNEG.exe (PID: 7088)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- DNMM.exe (PID: 5720)
- OGPFK.exe (PID: 6276)
- OZYGQK.exe (PID: 6672)
- MOXJC.exe (PID: 6860)
- OMYLIT.exe (PID: 5196)
- OXHFWF.exe (PID: 3740)
- FIXCWA.exe (PID: 6448)
- WVHV.exe (PID: 5548)
- BGD.exe (PID: 6896)
- FYGC.exe (PID: 4284)
- DWFV.exe (PID: 4776)
- IZJMQBM.exe (PID: 1864)
- XCGGEVL.exe (PID: 6364)
- USME.exe (PID: 4004)
- HCQDE.exe (PID: 6356)
- DAOA.exe (PID: 1616)
- ZQIIW.exe (PID: 6656)
- LJLB.exe (PID: 3592)
- STUCKC.exe (PID: 1752)
- URNWQ.exe (PID: 6320)
- UKWYWDU.exe (PID: 6448)
- WZPACS.exe (PID: 6368)
- CAW.exe (PID: 2588)
- KSFHZ.exe (PID: 6836)
- VLIA.exe (PID: 4628)
- MBHCLZ.exe (PID: 3592)
- NJRGGAL.exe (PID: 636)
- OZIF.exe (PID: 3712)
- RZLOJ.exe (PID: 4424)
- NHFW.exe (PID: 6736)
- VSOX.exe (PID: 4916)
- LQNAL.exe (PID: 3708)
- ELE.exe (PID: 4628)
- RWIKN.exe (PID: 624)
- CTTIH.exe (PID: 3640)
- AZHS.exe (PID: 6316)
- QWPO.exe (PID: 6308)
- TXSXD.exe (PID: 6652)
- NUTS.exe (PID: 5528)
- CPQ.exe (PID: 6348)
- TFPP.exe (PID: 4936)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- OZDEYX.exe (PID: 6548)
- GCUI.exe (PID: 4264)
- DZAFJL.exe (PID: 3708)
- DSIYXP.exe (PID: 1728)
- FAKCJQI.exe (PID: 5244)
- QVEFCGG.exe (PID: 1720)
- OJM.exe (PID: 4148)
- QTN.exe (PID: 6356)
- LOSN.exe (PID: 3740)
- CZIKK.exe (PID: 7060)
- BSRMY.exe (PID: 6840)
- FAL.exe (PID: 6292)
- UFRRI.exe (PID: 6276)
- SVQUU.exe (PID: 6652)
- FYUAZL.exe (PID: 6300)
- RJXMVEU.exe (PID: 4264)
- UESPG.exe (PID: 4916)
- HZEXZYK.exe (PID: 7144)
- UKAWEP.exe (PID: 32)
- NFSZIM.exe (PID: 6436)
- PNBVUN.exe (PID: 232)
- JKXWP.exe (PID: 2332)
- NLAFGG.exe (PID: 5720)
- CJG.exe (PID: 4000)
- PUCBSHW.exe (PID: 6204)
- CWG.exe (PID: 5896)
- LKRA.exe (PID: 1604)
- YUN.exe (PID: 1864)
- VSSV.exe (PID: 7040)
- RIN.exe (PID: 704)
- HYT.exe (PID: 6316)
- GBSFJ.exe (PID: 5556)
- EDRD.exe (PID: 380)
- EXRWP.exe (PID: 3708)
- OKC.exe (PID: 5940)
- CZQUQ.exe (PID: 3732)
- KQI.exe (PID: 6332)
- XYEY.exe (PID: 6676)
- BAY.exe (PID: 2764)
- ZOGUM.exe (PID: 7056)
- WMMRT.exe (PID: 4148)
- LJA.exe (PID: 1204)
Process checks computer location settings
- 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe (PID: 6508)
- ZPHYQEF.exe (PID: 6748)
- OFU.exe (PID: 6968)
- AYXI.exe (PID: 7124)
- PBHMRNL.exe (PID: 4716)
- LYN.exe (PID: 4360)
- ZJJ.exe (PID: 1604)
- EMNO.exe (PID: 6384)
- GKGRXCS.exe (PID: 6856)
- MKNEG.exe (PID: 7088)
- UDWYU.exe (PID: 4940)
- OSPAS.exe (PID: 6352)
- DNMM.exe (PID: 5720)
- OZYGQK.exe (PID: 6672)
- OGPFK.exe (PID: 6276)
- MOXJC.exe (PID: 6860)
- OMYLIT.exe (PID: 5196)
- OXHFWF.exe (PID: 3740)
- FIXCWA.exe (PID: 6448)
- WVHV.exe (PID: 5548)
- BGD.exe (PID: 6896)
- FYGC.exe (PID: 4284)
- DWFV.exe (PID: 4776)
- XCGGEVL.exe (PID: 6364)
- USME.exe (PID: 4004)
- IZJMQBM.exe (PID: 1864)
- HCQDE.exe (PID: 6356)
- DAOA.exe (PID: 1616)
- LJLB.exe (PID: 3592)
- ZQIIW.exe (PID: 6656)
- URNWQ.exe (PID: 6320)
- STUCKC.exe (PID: 1752)
- UKWYWDU.exe (PID: 6448)
- WZPACS.exe (PID: 6368)
- CAW.exe (PID: 2588)
- KSFHZ.exe (PID: 6836)
- MBHCLZ.exe (PID: 3592)
- VLIA.exe (PID: 4628)
- OZIF.exe (PID: 3712)
- NJRGGAL.exe (PID: 636)
- RZLOJ.exe (PID: 4424)
- NHFW.exe (PID: 6736)
- VSOX.exe (PID: 4916)
- LQNAL.exe (PID: 3708)
- ELE.exe (PID: 4628)
- CTTIH.exe (PID: 3640)
- RWIKN.exe (PID: 624)
- QWPO.exe (PID: 6308)
- AZHS.exe (PID: 6316)
- TXSXD.exe (PID: 6652)
- NUTS.exe (PID: 5528)
- CPQ.exe (PID: 6348)
- TFPP.exe (PID: 4936)
- JDWR.exe (PID: 2796)
- RJWG.exe (PID: 7080)
- OOUD.exe (PID: 7072)
- OZDEYX.exe (PID: 6548)
- GCUI.exe (PID: 4264)
- DZAFJL.exe (PID: 3708)
- DSIYXP.exe (PID: 1728)
- QVEFCGG.exe (PID: 1720)
- FAKCJQI.exe (PID: 5244)
- QTN.exe (PID: 6356)
- OJM.exe (PID: 4148)
- LOSN.exe (PID: 3740)
- BSRMY.exe (PID: 6840)
- CZIKK.exe (PID: 7060)
- UFRRI.exe (PID: 6276)
- FAL.exe (PID: 6292)
- FYUAZL.exe (PID: 6300)
- SVQUU.exe (PID: 6652)
- UESPG.exe (PID: 4916)
- HZEXZYK.exe (PID: 7144)
- RJXMVEU.exe (PID: 4264)
- UKAWEP.exe (PID: 32)
- NFSZIM.exe (PID: 6436)
- JKXWP.exe (PID: 2332)
- PNBVUN.exe (PID: 232)
- CJG.exe (PID: 4000)
- NLAFGG.exe (PID: 5720)
- PUCBSHW.exe (PID: 6204)
- LKRA.exe (PID: 1604)
- CWG.exe (PID: 5896)
- VSSV.exe (PID: 7040)
- YUN.exe (PID: 1864)
- RIN.exe (PID: 704)
- HYT.exe (PID: 6316)
- EDRD.exe (PID: 380)
- GBSFJ.exe (PID: 5556)
- CZQUQ.exe (PID: 3732)
- EXRWP.exe (PID: 3708)
- OKC.exe (PID: 5940)
- KQI.exe (PID: 6332)
- BAY.exe (PID: 2764)
- XYEY.exe (PID: 6676)
- LJA.exe (PID: 1204)
- ZOGUM.exe (PID: 7056)
Checks proxy server information
- WerFault.exe (PID: 6784)
- WerFault.exe (PID: 6956)
- WerFault.exe (PID: 3688)
- WerFault.exe (PID: 7100)
- WerFault.exe (PID: 6552)
- WerFault.exe (PID: 6720)
- WerFault.exe (PID: 5872)
- WerFault.exe (PID: 1720)
- WerFault.exe (PID: 6732)
- WerFault.exe (PID: 1788)
- WerFault.exe (PID: 2332)
- WerFault.exe (PID: 4704)
- WerFault.exe (PID: 1364)
- WerFault.exe (PID: 1120)
- WerFault.exe (PID: 4936)
Reads the software policy settings
- WerFault.exe (PID: 6956)
- WerFault.exe (PID: 6784)
- WerFault.exe (PID: 3688)
- WerFault.exe (PID: 7100)
- WerFault.exe (PID: 6552)
- WerFault.exe (PID: 6720)
- WerFault.exe (PID: 5872)
- WerFault.exe (PID: 1720)
- WerFault.exe (PID: 6732)
- WerFault.exe (PID: 1788)
- WerFault.exe (PID: 2332)
- WerFault.exe (PID: 4704)
- WerFault.exe (PID: 1364)
- WerFault.exe (PID: 1120)
- WerFault.exe (PID: 4936)
Creates files or folders in the user directory
- WerFault.exe (PID: 3688)
- WerFault.exe (PID: 6552)
- WerFault.exe (PID: 6720)
- WerFault.exe (PID: 5872)
- WerFault.exe (PID: 1720)
- WerFault.exe (PID: 6732)
- WerFault.exe (PID: 1788)
- WerFault.exe (PID: 2332)
- WerFault.exe (PID: 4704)
- WerFault.exe (PID: 1364)
- WerFault.exe (PID: 1120)
- WerFault.exe (PID: 4936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:06:02 06:27:43+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 147456 |
| InitializedDataSize: | 61981 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2419b |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | TODO: <Company name> |
| FileDescription: | TODO: <File description> |
| FileVersion: | 1.0.0.1 |
| InternalName: | AdwTest.exe |
| LegalCopyright: | TODO: (c) <Company name>. All rights reserved. |
| OriginalFileName: | AdwTest.exe |
| ProductName: | TODO: <Product name> |
| ProductVersion: | 1.0.0.1 |
Total processes
1 009
Monitored processes
679
Malicious processes
68
Suspicious processes
208
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | C:\windows\system\UKAWEP.exe | C:\Windows\System\UKAWEP.exe | cmd.exe | ||||||||||||
User: admin Company: TODO: <Company name> Integrity Level: HIGH Description: TODO: <File description> Exit code: 3221225477 Version: 1.0.0.1 Modules
| |||||||||||||||
| 32 | C:\WINDOWS\system32\cmd.exe /c ""C:\windows\NGVI.exe.bat" " | C:\Windows\SysWOW64\cmd.exe | — | RPAAH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 72 | C:\WINDOWS\system32\cmd.exe /c ""C:\windows\system\JPKOJ.exe.bat" " | C:\Windows\SysWOW64\cmd.exe | — | YWHW.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | C:\windows\system\PNBVUN.exe | C:\Windows\System\PNBVUN.exe | cmd.exe | ||||||||||||
User: admin Company: TODO: <Company name> Integrity Level: HIGH Description: TODO: <File description> Exit code: 3221225477 Version: 1.0.0.1 Modules
| |||||||||||||||
| 232 | C:\windows\system32\LGKMCD.exe | C:\Windows\SysWOW64\LGKMCD.exe | cmd.exe | ||||||||||||
User: admin Company: TODO: <Company name> Integrity Level: HIGH Description: TODO: <File description> Exit code: 3221225477 Version: 1.0.0.1 | |||||||||||||||
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 232 | C:\WINDOWS\system32\cmd.exe /c ""C:\windows\system32\YMZC.exe.bat" " | C:\Windows\SysWOW64\cmd.exe | — | LBD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 308 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
212 879
Read events
211 737
Write events
1 097
Delete events
45
Modification events
| (PID) Process: | (6260) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6260) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6260) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6260) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6508) 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6508) 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6508) 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6508) 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6784) WerFault.exe | Key: | \REGISTRY\A\{e5621f5d-27a1-abd6-9a01-94d78c2011c8}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (6784) WerFault.exe | Key: | \REGISTRY\A\{e5621f5d-27a1-abd6-9a01-94d78c2011c8}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
214
Suspicious files
67
Text files
280
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6260 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | — | |
MD5:— | SHA256:— | |||
| 6260 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\39TQH5P4GIR3DP2NG9HX.temp | binary | |
MD5:03DAF9C6A11390B29881991BAA9A04CF | SHA256:59F806DCA974C8F83ADBB23039E64A9C2FC3EB7C0B13CFBAB27212A8CA81A7F7 | |||
| 6956 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_ZPHYQEF.exe_598adcb45bf1654f43af1e629783077b5ccfe33_f1c70969_b654d003-2e1b-4954-8cd6-52000da935b8\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6784 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_437cb914aeb1fca0_f9f8319f726ac4afd76673727f76e8cb3871bc_b1376e18_1ed1dd1a-5e7a-41ea-b550-9b12f6c0fdfd\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6784 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER5284.tmp.xml | xml | |
MD5:83F651EC36CC2444C3CC47BC9C0FD35B | SHA256:EA8BE48209C0E69B073BE9019B8664DF3D28A011805AF33C4CF24D43C198B85A | |||
| 6508 | 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe | C:\windows\system\ZPHYQEF.exe | executable | |
MD5:85DC3DFB87B9FCD7F825C9C9E8654C53 | SHA256:D2153D0A13FEC9FF963EC2C6C7227C3FC8D8C40BA383F369E3D2E0FD60614B88 | |||
| 6968 | OFU.exe | C:\windows\system\AYXI.exe | executable | |
MD5:85DC3DFB87B9FCD7F825C9C9E8654C53 | SHA256:D2153D0A13FEC9FF963EC2C6C7227C3FC8D8C40BA383F369E3D2E0FD60614B88 | |||
| 6508 | 437cb914aeb1fca0a714380ac400101e4e594a13fe245cf589b8a8bca3ae46ba.exe | C:\windows\system\ZPHYQEF.exe.bat | text | |
MD5:46D59FF8591EBA540D91B82EC692D79A | SHA256:AE58EFF1A04CC8D92219A763EA300750840C6C36D1CF05F3A95C0556187269B6 | |||
| 6748 | ZPHYQEF.exe | C:\windows\SysWOW64\OFU.exe.bat | text | |
MD5:F6D45FCD822BF4ACA3605D1660648719 | SHA256:2859851334DE9CA2DC49418490388277E1595FE1C1D68E9EE12783EB4D635F18 | |||
| 7100 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_OFU.exe_defab58af04b78bb24db88ee9e3fb5ae92ca0d1_e2df9ed8_8f99a4df-e176-4893-884f-5bb34962ade9\Report.wer | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
51
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5380 | svchost.exe | GET | 200 | 2.18.121.212:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4856 | RUXIMICS.exe | GET | 200 | 2.18.121.212:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.18.121.212:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4856 | RUXIMICS.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5380 | svchost.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | POST | 200 | 52.182.143.209:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
5380 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4856 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5140 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5380 | svchost.exe | 2.18.121.212:80 | crl.microsoft.com | AKAMAI-AS | FR | unknown |
4856 | RUXIMICS.exe | 2.18.121.212:80 | crl.microsoft.com | AKAMAI-AS | FR | unknown |
5140 | MoUsoCoreWorker.exe | 2.18.121.212:80 | crl.microsoft.com | AKAMAI-AS | FR | unknown |
5140 | MoUsoCoreWorker.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | unknown |
4856 | RUXIMICS.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | unknown |
5380 | svchost.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |