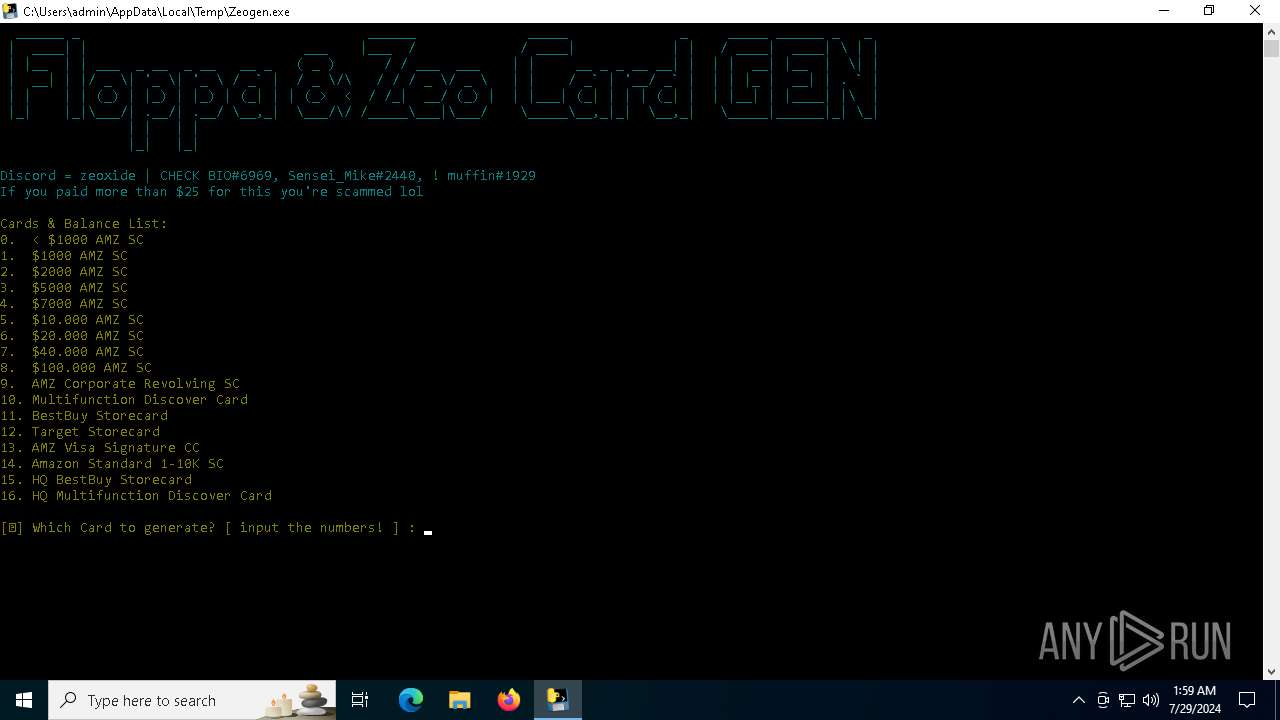
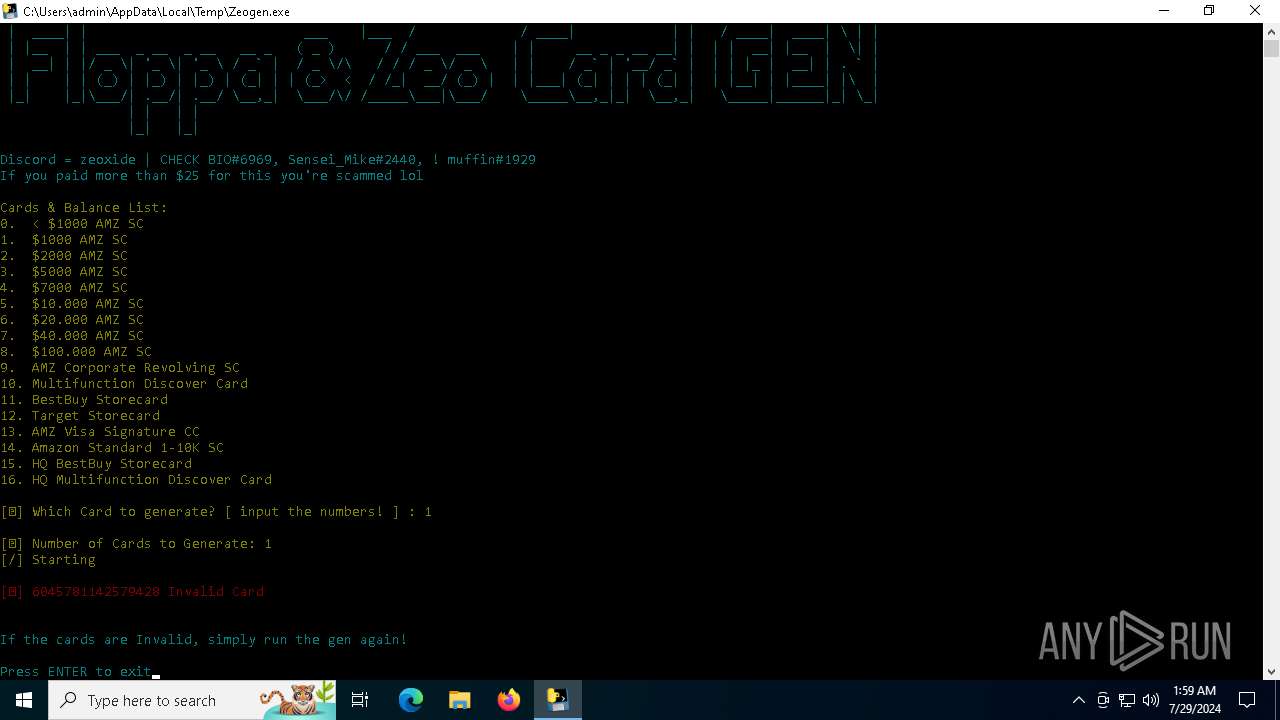
| File name: | Zeogen.exe |
| Full analysis: | https://app.any.run/tasks/04f23e6a-e514-422d-bf02-953f6362b04d |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2024, 01:59:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | C6C519E43407EAAAF240077F1E8FA418 |
| SHA1: | D5B20223F96619E997AB58D5E98CD10322A2ABD3 |
| SHA256: | 43717D6C756379B64D7F8289E2BCD7A585CED7FCDE720DB6171A190DE648DBD2 |
| SSDEEP: | 196608:8T6DSL2Vmd6+D0JJVAzDaku99mEQcy6d/AyfRL6H:PSL2Vmd6m0JJVAzDakArZd/Ayfw |
MALICIOUS
Drops the executable file immediately after the start
- Zeogen.exe (PID: 1596)
SUSPICIOUS
Process drops legitimate windows executable
- Zeogen.exe (PID: 1596)
Executable content was dropped or overwritten
- Zeogen.exe (PID: 1596)
The process drops C-runtime libraries
- Zeogen.exe (PID: 1596)
Process drops python dynamic module
- Zeogen.exe (PID: 1596)
Application launched itself
- Zeogen.exe (PID: 1596)
Loads Python modules
- Zeogen.exe (PID: 2952)
INFO
Create files in a temporary directory
- Zeogen.exe (PID: 1596)
Checks supported languages
- Zeogen.exe (PID: 1596)
- Zeogen.exe (PID: 2952)
Reads the computer name
- Zeogen.exe (PID: 1596)
Reads the machine GUID from the registry
- Zeogen.exe (PID: 2952)
Checks proxy server information
- slui.exe (PID: 528)
Reads the software policy settings
- slui.exe (PID: 528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:04:06 04:00:53+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 144896 |
| InitializedDataSize: | 146944 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9d30 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
143
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Zeogen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 528 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1596 | "C:\Users\admin\AppData\Local\Temp\Zeogen.exe" | C:\Users\admin\AppData\Local\Temp\Zeogen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\AppData\Local\Temp\Zeogen.exe" | C:\Users\admin\AppData\Local\Temp\Zeogen.exe | — | Zeogen.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 128
Read events
1 128
Write events
0
Delete events
0
Modification events
Executable files
19
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\VCRUNTIME140.dll | executable | |
MD5:A87575E7CF8967E481241F13940EE4F7 | SHA256:DED5ADAA94341E6C62AEA03845762591666381DCA30EB7C17261DD154121B83E | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_lzma.pyd | executable | |
MD5:AD02EA81A127A401F4DF84C082F3CCE6 | SHA256:4213FBB6936AD3EAC1E1BA28F10E15719176BC3A59FF01DDC6828DD7EEE52132 | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_ctypes.pyd | executable | |
MD5:38D9D8ED2B7DF64790150A2A523FD3B9 | SHA256:11DAEF02AFE45D9F3987BAB5C2B6EF75B2B6F6F79704C45675D532F090F14B8B | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_bz2.pyd | executable | |
MD5:7F2BBA8A38712D00907F6E37F0CE6028 | SHA256:CD04EBE932B2CB2FD7F01C25412BDDD77B476FA47D0AFF69A04A27D3BFE4B37B | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_multiprocessing.pyd | executable | |
MD5:7FCFF5C455D0D1B0B9C5C247518360DC | SHA256:CC6FF1CB52B57248F9FB49CEE4A4EF868DB12B3656CBC7BC6F11614357E183CF | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_queue.pyd | executable | |
MD5:F9718FE21174D8428F022AAF60BF92DA | SHA256:95E1C419E08D8AB229B8C64D51FD301CD9D75A659DFC05E75B0317CA0A4F22E3 | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_socket.pyd | executable | |
MD5:0A6C6FD7697E4C3757014FA6BF6DD615 | SHA256:A611E9B4F4E5FE67E945B771D79CF15C48441ECFA11CE186CEC9BF233DC20C0D | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_asyncio.pyd | executable | |
MD5:43E7DA594AF7C0655CB9F57BD5556A49 | SHA256:6241F72162099095F111819FD5B9B2A0995ED7CF45CA08F1D0134AB7B3FE601A | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_hashlib.pyd | executable | |
MD5:75ED91D3B7A40ECA5B32A13B90191EAD | SHA256:202535A5CEB0BF70C2046639A3884C24F2CCCB1BD92827E61B5A7A663D9399BA | |||
| 1596 | Zeogen.exe | C:\Users\admin\AppData\Local\Temp\_MEI15962\_decimal.pyd | executable | |
MD5:1139CC9D936B6028305749568EC5CAC7 | SHA256:67A47D85CC1A21069610C85DA64FC031231D43AF7876DFC48361C57D88EFEE0B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
49
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3992 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4128 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | unknown |
6716 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6592 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
488 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fp.msedge.net |
| whitelisted |