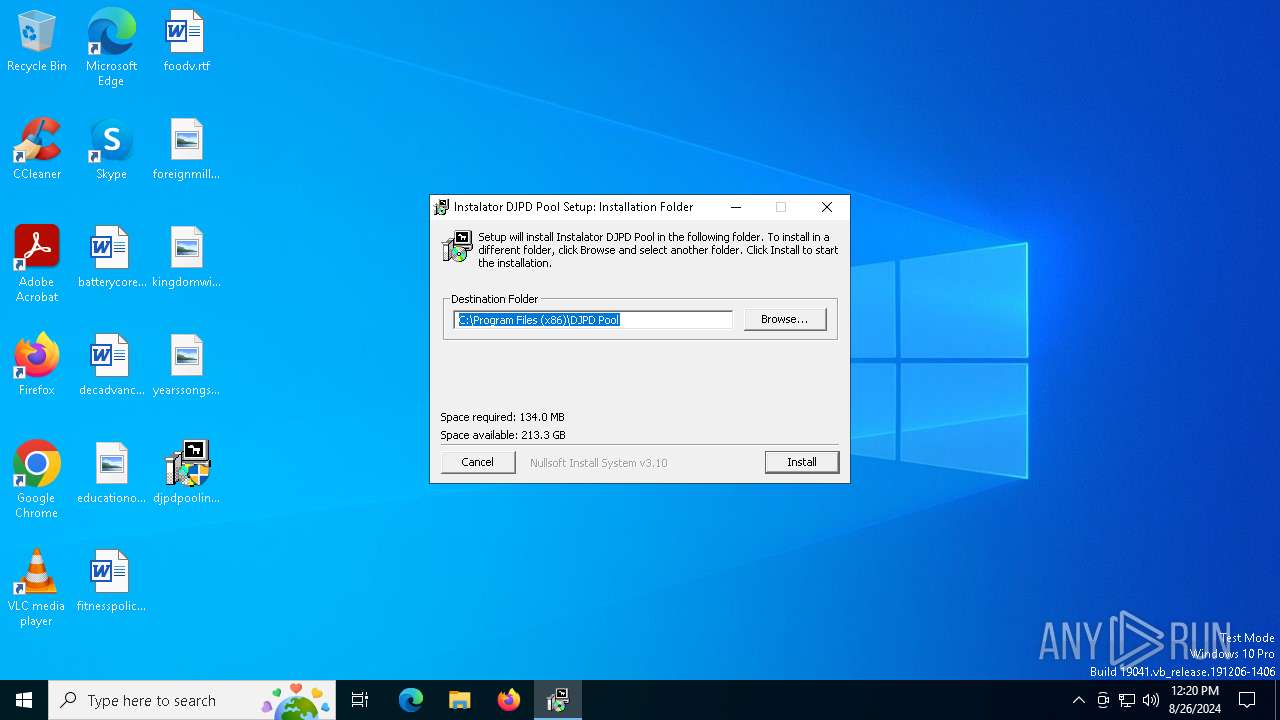
| File name: | djpdpoolinstaller.exe |
| Full analysis: | https://app.any.run/tasks/cf802b6a-a983-45ce-a880-8914a93708df |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 12:20:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 43ABDF24EE5A8420CD4492047FB1B079 |
| SHA1: | 2FBEFD6C2AB5A06B0D7EBD108552E2CE064FB8DA |
| SHA256: | 43636CD71616BD53F23D46CF26F23FC266D3CBDCF8386D08C9DA8E95CED61A02 |
| SSDEEP: | 786432:7B4lxq4UiulMOnfyfu6WR+1VpjPGzZhSTVli:7B4ls4iTfyW6WR+1VhPSrSxk |
MALICIOUS
Detects Cygwin installation
- msiexec.exe (PID: 4088)
SUSPICIOUS
Drops the executable file immediately after the start
- djpdpoolinstaller.exe (PID: 6996)
- msiexec.exe (PID: 4088)
Checks Windows Trust Settings
- msiexec.exe (PID: 4088)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 4088)
Executable content was dropped or overwritten
- djpdpoolinstaller.exe (PID: 6996)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 4088)
Executes as Windows Service
- launcher-x64.exe (PID: 1752)
- netbird.exe (PID: 6140)
Process drops legitimate windows executable
- djpdpoolinstaller.exe (PID: 6996)
Starts CMD.EXE for commands execution
- djpdpoolinstaller.exe (PID: 6996)
The process drops C-runtime libraries
- djpdpoolinstaller.exe (PID: 6996)
Creates or modifies Windows services
- msiexec.exe (PID: 7080)
Process drops python dynamic module
- djpdpoolinstaller.exe (PID: 6996)
INFO
Create files in a temporary directory
- djpdpoolinstaller.exe (PID: 6996)
Reads the computer name
- djpdpoolinstaller.exe (PID: 6996)
- msiexec.exe (PID: 4088)
- msiexec.exe (PID: 2820)
- msiexec.exe (PID: 892)
- launcher-x64.exe (PID: 1752)
Checks supported languages
- djpdpoolinstaller.exe (PID: 6996)
- msiexec.exe (PID: 4088)
- msiexec.exe (PID: 2820)
- msiexec.exe (PID: 892)
- launcher-x64.exe (PID: 1752)
Reads the machine GUID from the registry
- msiexec.exe (PID: 4088)
Reads the software policy settings
- msiexec.exe (PID: 4088)
Creates files or folders in the user directory
- msiexec.exe (PID: 4088)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4088)
Creates a software uninstall entry
- msiexec.exe (PID: 4088)
Application launched itself
- msiexec.exe (PID: 4088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:19+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3665 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.4.0.0 |
| ProductVersionNumber: | 2.4.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | DJPD |
| FileVersion: | 2.4 |
| LegalCopyright: | Copyright 2024 DJPD |
| ProductName: | DJPD Pool |
Total processes
126
Monitored processes
14
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 892 | C:\Windows\syswow64\MsiExec.exe -Embedding AD2CEBC88445E170CCD86FDF8FB5BAFE E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | launcher-x64.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | "C:\Program Files (x86)\WinFsp\SxS\sxs.20240826T122054Z\bin\launcher-x64.exe" | C:\Program Files (x86)\WinFsp\SxS\sxs.20240826T122054Z\bin\launcher-x64.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Navimatics LLC Integrity Level: SYSTEM Description: Windows File System Proxy Version: 2.1.24051.9a65718 Modules
| |||||||||||||||
| 1776 | msiexec /i sshfs.msi /quiet | C:\Windows\SysWOW64\msiexec.exe | — | djpdpoolinstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2820 | C:\Windows\syswow64\MsiExec.exe -Embedding D7C96824DA64055EC5188400801AB834 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4088 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
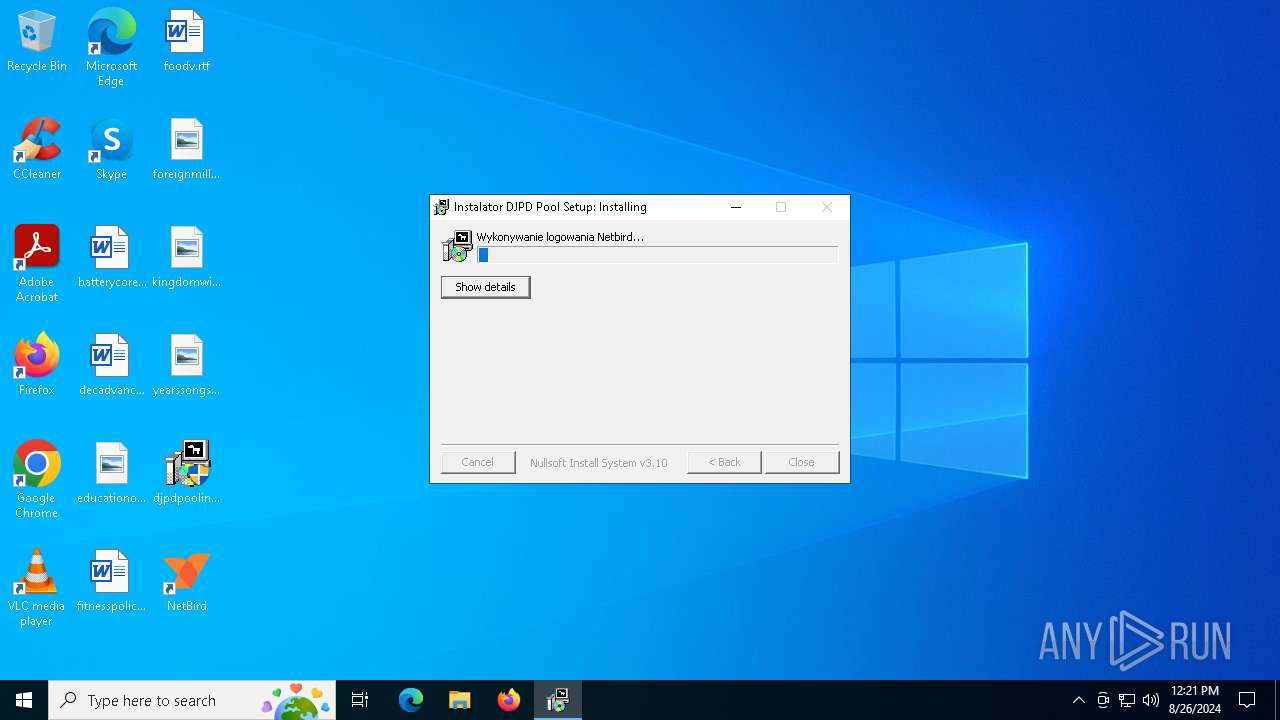
| 4404 | cmd.exe /c "netbird login -m https://nb.djpd.pl:443 & netbird up" | C:\Windows\SysWOW64\cmd.exe | — | djpdpoolinstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 4876 | "C:\Users\admin\Desktop\djpdpoolinstaller.exe" | C:\Users\admin\Desktop\djpdpoolinstaller.exe | — | explorer.exe | |||||||||||
User: admin Company: DJPD Integrity Level: MEDIUM Exit code: 3221226540 Version: 2.4 Modules
| |||||||||||||||
| 6140 | "C:\Program Files\Netbird\netbird.exe" service run config C:\ProgramData\Netbird\config.json log-level info | C:\Program Files\Netbird\netbird.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Version: 0.28.8.0 | |||||||||||||||
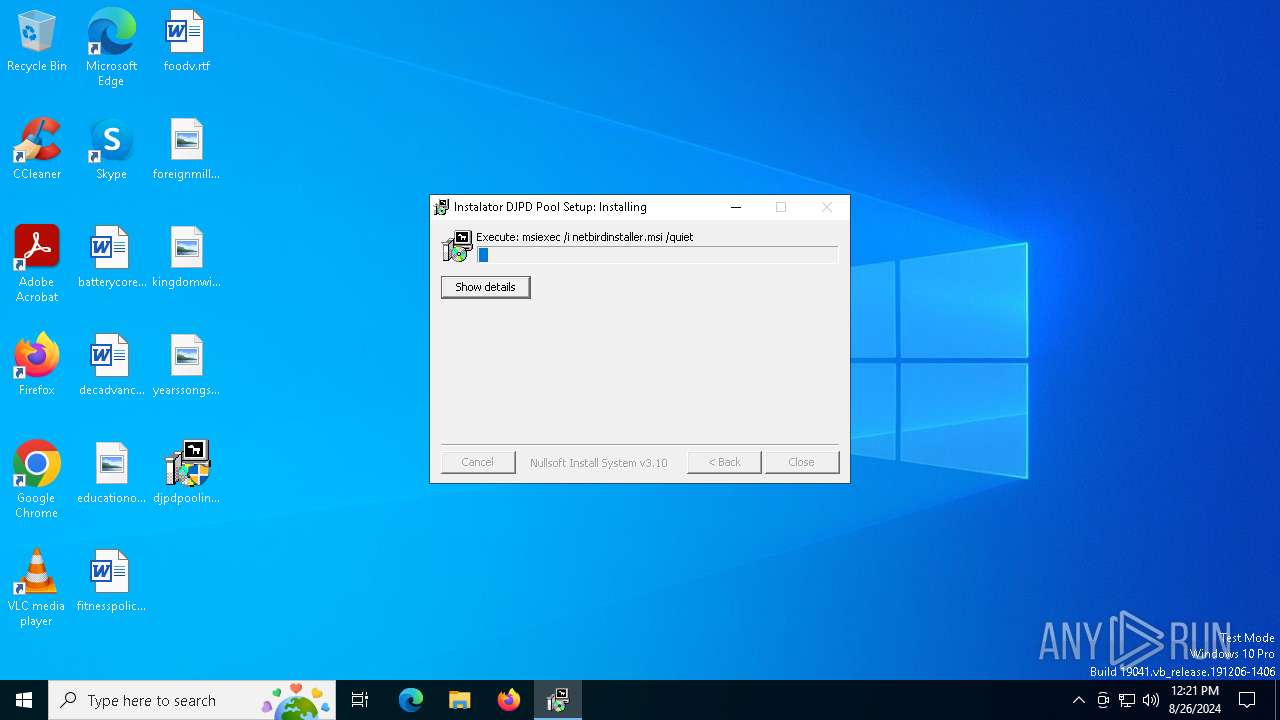
| 6396 | msiexec /i netbirdinstaller.msi /quiet | C:\Windows\SysWOW64\msiexec.exe | — | djpdpoolinstaller.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
Total events
8 008
Read events
7 731
Write events
260
Delete events
17
Modification events
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: F80F0000DF1DF461B2F7DA01 | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 5144119E09EE1E4BA84D7DA56016CE7C70964BC61D21A5A70A664EF819757A89 | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\1313fa.rbs |
Value: 31127474 | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\1313fa.rbsLow |
Value: | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\36C54643732BB2B47B20E8BB6A626D40 |
| Operation: | write | Name: | 0D75C008A43F55740A285ABBD3FE5878 |
Value: 22:\Software\SSHFS-Win\InstallDir | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\E245303D9042DD851970108EA693FCAA |
| Operation: | write | Name: | 0D75C008A43F55740A285ABBD3FE5878 |
Value: C:\Program Files\SSHFS-Win\License.txt | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\66979FE3E94EB0A46BD8E52BDB6AC112 |
| Operation: | write | Name: | 0D75C008A43F55740A285ABBD3FE5878 |
Value: 22:\Software\WOW6432Node\WinFsp\Services\sshfs\Executable | |||
| (PID) Process: | (4088) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\ED2A1E8F1602DA2408F533FBF057CD53 |
| Operation: | write | Name: | 0D75C008A43F55740A285ABBD3FE5878 |
Value: 22:\Software\WOW6432Node\WinFsp\Services\sshfs.r\Executable | |||
Executable files
84
Suspicious files
63
Text files
933
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6996 | djpdpoolinstaller.exe | C:\Users\admin\AppData\Local\Temp\sshfs.msi | — | |
MD5:— | SHA256:— | |||
| 4088 | msiexec.exe | C:\Windows\Installer\1313f8.msi | — | |
MD5:— | SHA256:— | |||
| 4088 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\DA3B6E45325D5FFF28CF6BAD6065C907_8E0CE67692F4A2065EA56AD27F041788 | binary | |
MD5:DF9E4DA3ABE1544D2D4DF1B9DEBF5FE4 | SHA256:32DF3C67F09B0EA3BC042E6605BAF8EE8FE8F7ABE35973FC875C3F983A06F814 | |||
| 4088 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8890A77645B73478F5B1DED18ACBF795_C090A8C88B266C6FF99A97210E92B44D | binary | |
MD5:F72AF7689238CE1EB2124E4F9F39931D | SHA256:B4BCAFCBC51D21292DC5166E9C363FC51C0106A4CCC3CAE315263FC9D620F8B7 | |||
| 4088 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DA3B6E45325D5FFF28CF6BAD6065C907_8E0CE67692F4A2065EA56AD27F041788 | binary | |
MD5:A84050FB18B20C87C62631A68EE3D7CA | SHA256:2C965EC4279BA48BADE62B2D60158F39C29C677D9E4DB900E180525BBC2C56F7 | |||
| 4088 | msiexec.exe | C:\Windows\Installer\MSI1C55.tmp | binary | |
MD5:9BE346D851D10C906F0FBF5AD0448033 | SHA256:C31CE70E12A52B0ECA519C8FA5D26FBEA7F7C0827D6CE26CC697382A99889320 | |||
| 4088 | msiexec.exe | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngen.log | text | |
MD5:40400196F32D33CB1DEB75C179795820 | SHA256:D8724BAB33EF12B8AA3B04B8724F2FDB1236F30245384D1DFEBFFBC12ADA00F2 | |||
| 4088 | msiexec.exe | C:\Windows\Temp\~DF2202D88324314036.TMP | binary | |
MD5:0D9BFF74616C8B314F06142ACA1EE7A3 | SHA256:821ADB349B9CEB9AB1FE947D9E530AD87CB0DC249DB95072E5C19715E0EB0ED4 | |||
| 4088 | msiexec.exe | C:\Program Files\SSHFS-Win\bin\cygcrypto-1.1.dll | executable | |
MD5:0FD20A79633B3D4025B60F8ADB48A47F | SHA256:75342DC85872041292B35F94E4C9DDD1B15F209DA38D06C8D7E2875D6DCE1F0B | |||
| 4088 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8890A77645B73478F5B1DED18ACBF795_C090A8C88B266C6FF99A97210E92B44D | binary | |
MD5:C3A36974240204FB6D778B69AF8D56F7 | SHA256:CD54E6B78090573CF706F4AE371B778C9A4AE6065D9BA7C0086D48F0931BEEB1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4088 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | unknown | — | — | whitelisted |
4088 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEA1LmzteDNDk8DmcEJinVIQ%3D | unknown | — | — | whitelisted |
4088 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEA%2B4p0C5FY0DUUO8WdnwQCk%3D | unknown | — | — | whitelisted |
4088 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSE67Nbq3jfQQg8yXEpbmqLTNn7XwQUm1%2BwNrqdBq4ZJ73AoCLAi4s4d%2B0CEAytC0uc8lY%2BJbW8KgNyN8w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 18.239.36.80:80 | http://crls.ssl.com/SSLcom-SubCA-EV-CodeSigning-RSA-4096-R3.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 100.24.223.135:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQg3SSkKA74hABkhmlBtJTz8w3hlAQU%2BWC71OPVNPa49QaAJadz20ZpqJ4CEEJLalPOx2YUHCpjsaUcQQQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4088 | msiexec.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 100.24.223.135:80 | ocsps.ssl.com | AMAZON-AES | US | whitelisted |
— | — | 18.239.36.80:80 | crls.ssl.com | — | US | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsps.ssl.com |
| whitelisted |
crls.ssl.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msiexec.exe | FspFsctlRegister = 0
|
msiexec.exe | FspNpRegister = 0
|
msiexec.exe | FspEventLogRegister = 0
|