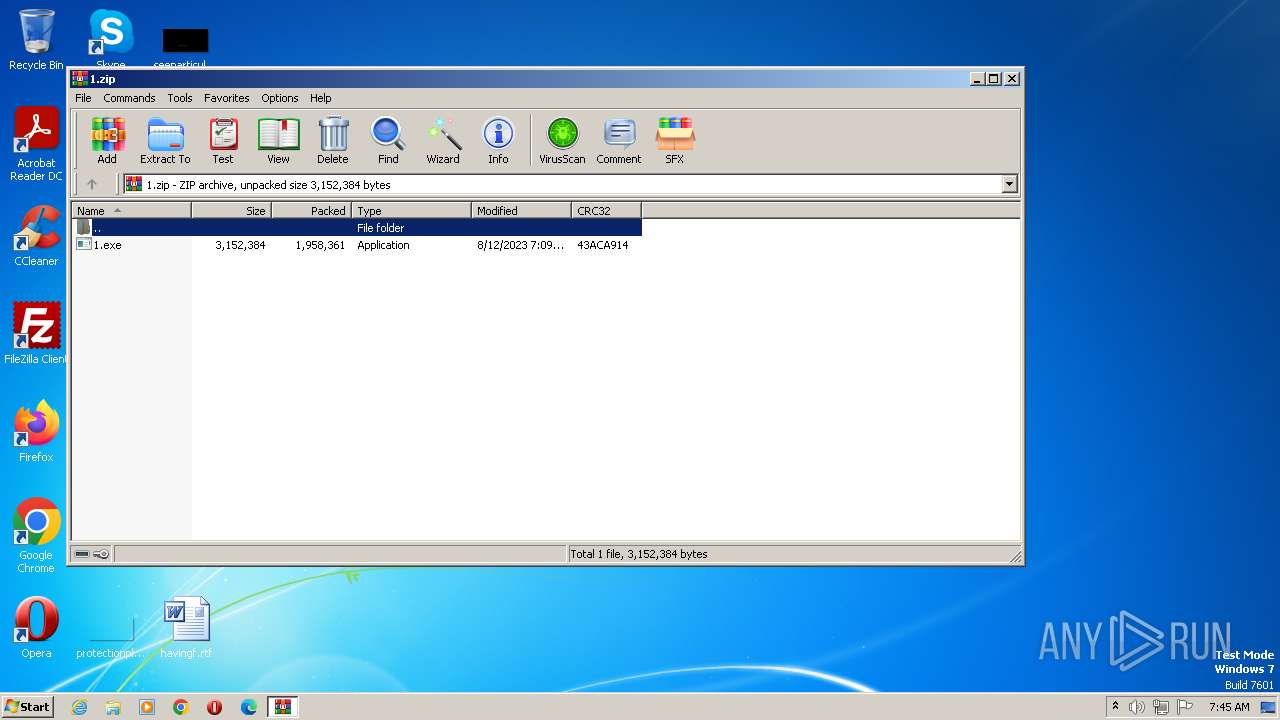
| File name: | 1.zip |
| Full analysis: | https://app.any.run/tasks/a00b3a6f-8246-4b0b-8a7e-94ef8e191658 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2023, 06:45:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 53F62412B4A4B542A8D7F588A8A3F24E |
| SHA1: | 00A502FEE47704B671707E190EA2FABDA849424E |
| SHA256: | 434EB1E351F9CB31E17C5EA3F588404A8BD79D7125836F11B1BB44DD0E8397F3 |
| SSDEEP: | 49152:l1I7PvJNriWnpPfNK/UDmd89oE45VFc+2dfIVuYNxxqTVSf:nI7rrnhfg/gmd89DCVFpSIVuYNxxqZSf |
MALICIOUS
Application was dropped or rewritten from another process
- 1.exe (PID: 2480)
- 1.exe (PID: 1808)
SUSPICIOUS
Connects to unusual port
- 1.exe (PID: 1808)
INFO
Reads the computer name
- 1.exe (PID: 1808)
Checks supported languages
- 1.exe (PID: 1808)
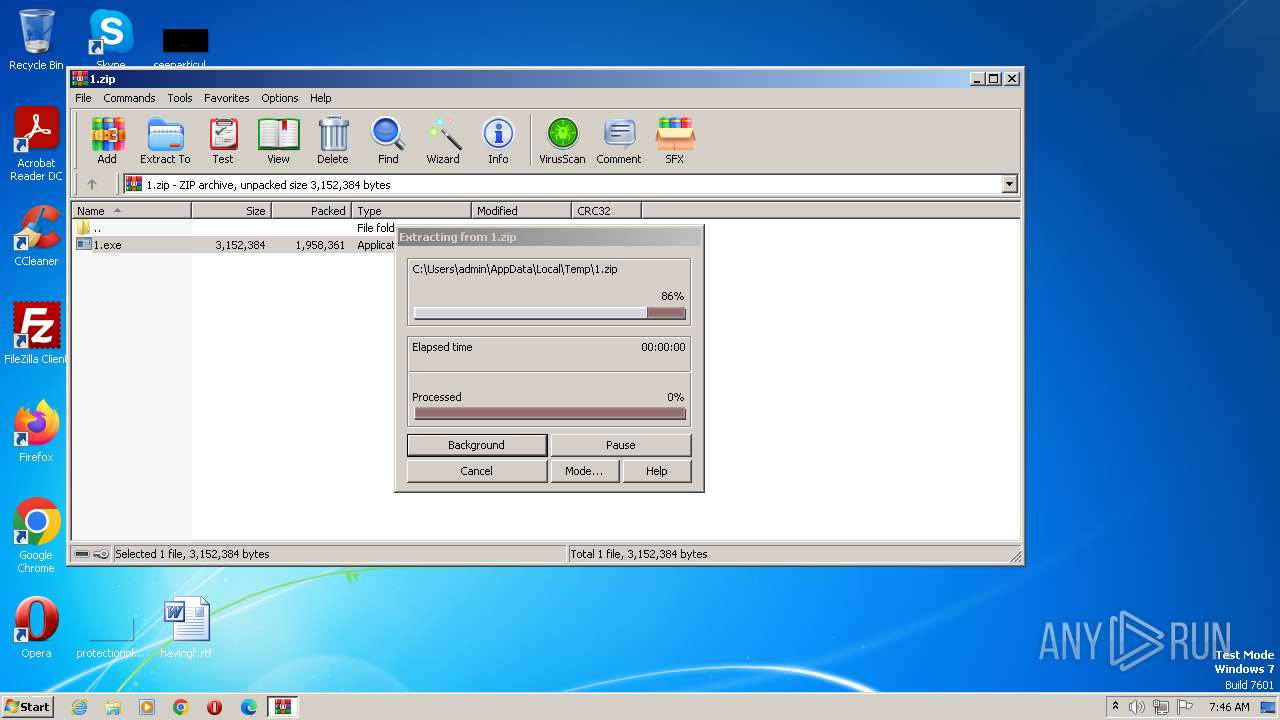
Create files in a temporary directory
- 1.exe (PID: 1808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | 1.exe |
|---|---|
| ZipUncompressedSize: | 3152384 |
| ZipCompressedSize: | 1958361 |
| ZipCRC: | 0x43aca914 |
| ZipModifyDate: | 2023:08:12 14:09:46 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
39
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
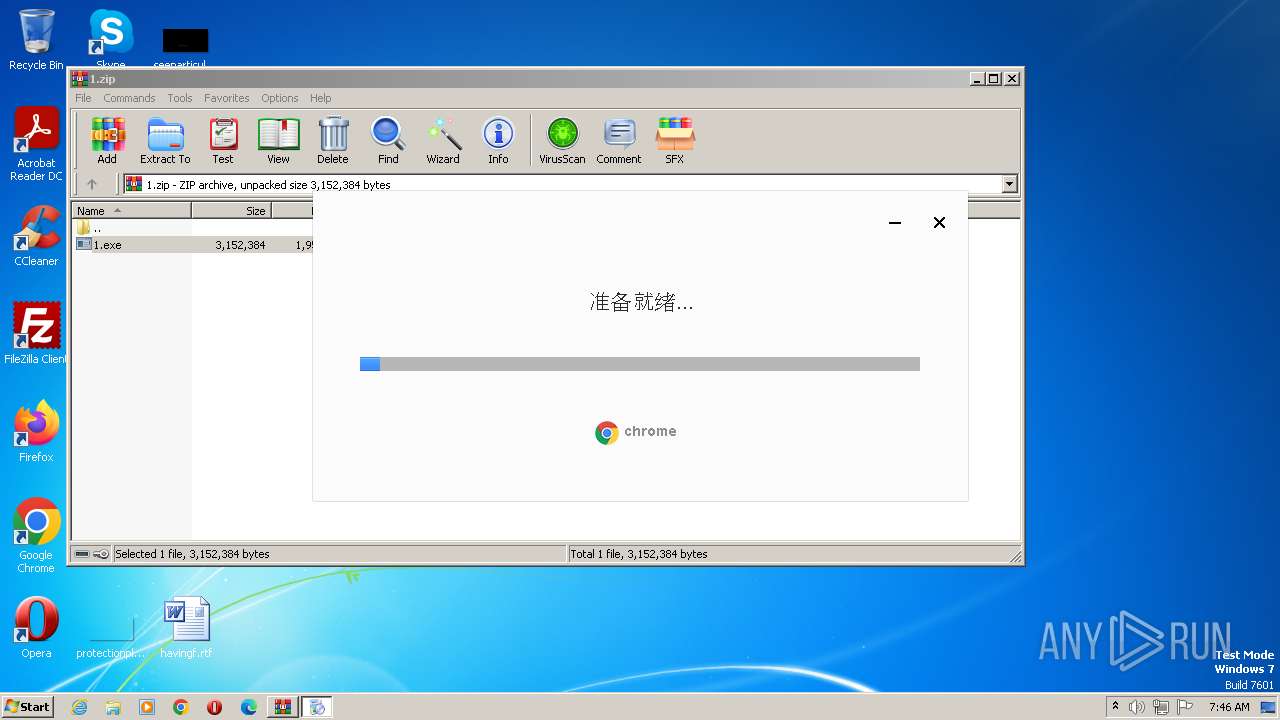
| 1808 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa124.26667\1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa124.26667\1.exe | WinRAR.exe | ||||||||||||
User: admin Company: The Chromium Authors Integrity Level: HIGH Description: Chromium Exit code: 0 Version: 78.0.3904.108 Modules
| |||||||||||||||
| 2480 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa124.26667\1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa124.26667\1.exe | — | WinRAR.exe | |||||||||||
User: admin Company: The Chromium Authors Integrity Level: MEDIUM Description: Chromium Exit code: 3221226540 Version: 78.0.3904.108 Modules
| |||||||||||||||
Total events
1 306
Read events
1 290
Write events
16
Delete events
0
Modification events
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa124.26667\1.exe | executable | |
MD5:D435BAEBFC93648D3BA3F30CA01AB165 | SHA256:1E673A4D2ADFDFAED1DE64B49AB77168FA691B1F794E215ED7C83581D8D6ECA2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
8
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1808 | 1.exe | GET | 200 | 121.199.50.121:88 | http://121.199.50.121:88/chromext/dt/?a=ViXfU6jRczhylRobnTK3YVsXiknXHhrgt+mBdTUSVzVidL9d36/CkcUMgaBG/0q2r4ZTVAPExVvBZTeP8FN47L9GRnq0hwnJfd+WZQGqKXbhjNP86J8CPTC4+2r6P+bL | CN | — | — | suspicious |
1808 | 1.exe | GET | 200 | 121.199.50.121:88 | http://121.199.50.121:88/chromext/dt/?a=ViXfU6jRczhylRobnTK3YXPmC4jQQZc6chElG50ZZfFidL9d36/CkcUMgaBG/0q2r4ZTVAPExVvBZTeP8FN47FUjak5yZmubdTMzUHZWxJ/hjNP86J8CPTC4+2r6P+bL | CN | — | — | suspicious |
1808 | 1.exe | GET | 200 | 121.199.50.121:88 | http://121.199.50.121:88/tt/ | CN | text | 19 b | suspicious |
1808 | 1.exe | GET | — | 163.171.132.18:80 | http://down.xthm.net/down/chromex86V16.zip | US | — | — | suspicious |
1808 | 1.exe | GET | 200 | 121.199.50.121:88 | http://121.199.50.121:88/chromeins/ch-1.0.0.6.php?fn=sBjD0z7sLgaWgJbSqAX2dg== | CN | text | 1.29 Kb | suspicious |
1808 | 1.exe | GET | 200 | 121.199.50.121:88 | http://121.199.50.121:88/tt/ | CN | text | 19 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1808 | 1.exe | 121.199.50.121:88 | chrome.haifti.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | suspicious |
1808 | 1.exe | 163.171.132.18:80 | down.xthm.net | QUANTILNETWORKS | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
chrome.haifti.com |
| suspicious |
down.xthm.net |
| suspicious |