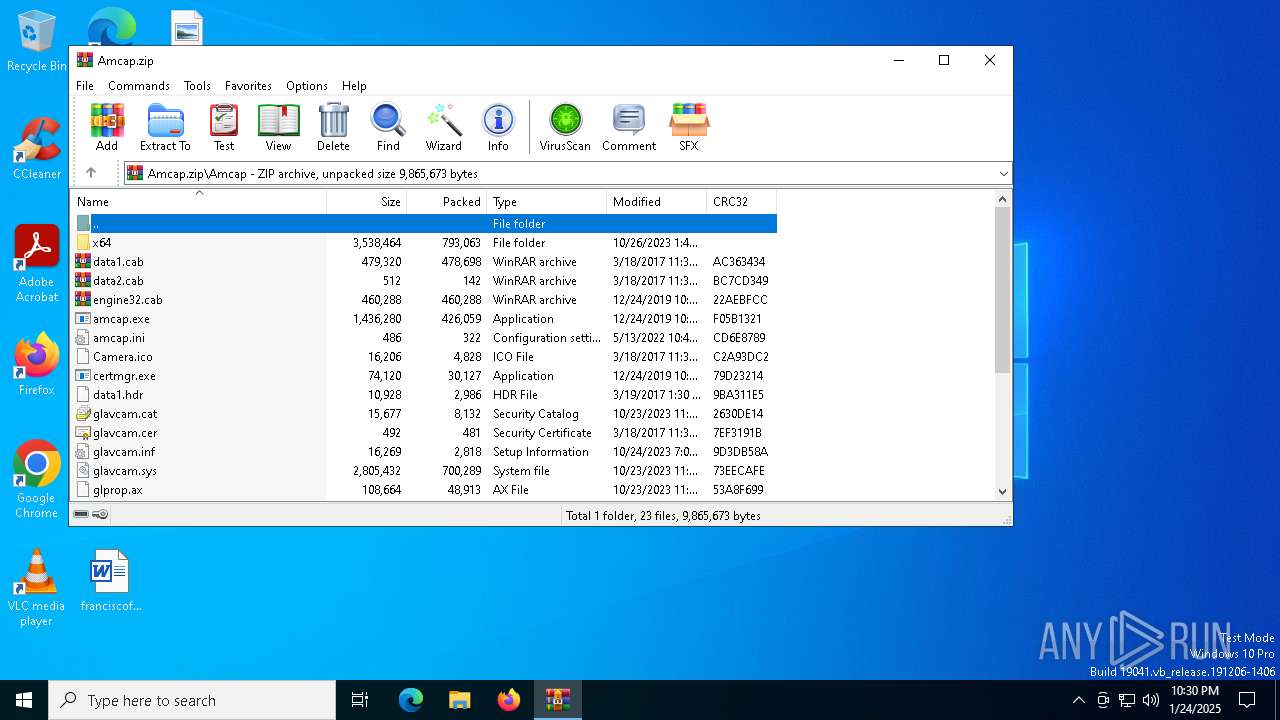
| File name: | Amcap.zip |
| Full analysis: | https://app.any.run/tasks/9ea53b31-0d84-47d5-8e31-65df990936ae |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2025, 22:29:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | B52CEDCC3B09FB05717EDB7CD4F2FD41 |
| SHA1: | EFA51A5C2CDB4EC45345E8DAE026BCB4B3DF780A |
| SHA256: | 43252059E931C650E4A21CEF2964471BC867D5316A654D07E79107F13FDC01D4 |
| SSDEEP: | 98304:pkMAPaEOJM54XO/gfvF/SUNaKdrE6UVlvbhjsmlxdYE/xnKBWgSJvjRN9JeRfJkw:p296+1DBdm |
MALICIOUS
Changes the autorun value in the registry
- rundll32.exe (PID: 6864)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6232)
Application launched itself
- setup.exe (PID: 4724)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6232)
- drvinst.exe (PID: 1488)
- rundll32.exe (PID: 6864)
Executable content was dropped or overwritten
- setup.exe (PID: 5008)
- rundll32.exe (PID: 6864)
- drvinst.exe (PID: 1488)
Creates/Modifies COM task schedule object
- setup.exe (PID: 5008)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 5008)
- setup.exe (PID: 4724)
Creates files in the driver directory
- drvinst.exe (PID: 1488)
Checks Windows Trust Settings
- drvinst.exe (PID: 1488)
Searches for installed software
- setup.exe (PID: 5008)
- dllhost.exe (PID: 5320)
Creates a software uninstall entry
- setup.exe (PID: 5008)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2916)
Executes as Windows Service
- VSSVC.exe (PID: 5000)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6232)
- setup.exe (PID: 5008)
- drvinst.exe (PID: 1488)
- rundll32.exe (PID: 6864)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6232)
Checks supported languages
- setup.exe (PID: 4724)
- setup.exe (PID: 5008)
- drvinst.exe (PID: 1488)
- PLUGScheduler.exe (PID: 2916)
- amcap.exe (PID: 6352)
- monitorpad.exe (PID: 6432)
Manual execution by a user
- setup.exe (PID: 4724)
- setup.exe (PID: 4824)
- monitorpad.exe (PID: 6432)
- amcap.exe (PID: 6352)
Creates files or folders in the user directory
- setup.exe (PID: 5008)
Reads the machine GUID from the registry
- setup.exe (PID: 5008)
- drvinst.exe (PID: 1488)
Creates files in the program directory
- setup.exe (PID: 5008)
- PLUGScheduler.exe (PID: 2916)
- amcap.exe (PID: 6352)
Reads the computer name
- setup.exe (PID: 5008)
- drvinst.exe (PID: 1488)
- amcap.exe (PID: 6352)
- PLUGScheduler.exe (PID: 2916)
Manages system restore points
- SrTasks.exe (PID: 6572)
Create files in a temporary directory
- rundll32.exe (PID: 6864)
- setup.exe (PID: 5008)
Reads the software policy settings
- drvinst.exe (PID: 1488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (40) |
|---|---|---|
| .zip | | | ZIP compressed archive (20) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:10:26 09:44:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Amcap/ |
Total processes
259
Monitored processes
19
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{0ae79a90-14c0-b346-8d85-b3903f6befa1}\glavcam.inf" "9" "425433e07" "00000000000001CC" "WinSta0\Default" "00000000000001DC" "208" "C:\Users\admin\Desktop\Amcap" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2916 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | "C:\Users\admin\Desktop\Amcap\setup.exe" | C:\Users\admin\Desktop\Amcap\setup.exe | explorer.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 10.0.159 Modules
| |||||||||||||||
| 4824 | "C:\Users\admin\Desktop\Amcap\setup.exe" | C:\Users\admin\Desktop\Amcap\setup.exe | — | explorer.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: MEDIUM Description: Setup.exe Exit code: 3221226540 Version: 10.0.159 Modules
| |||||||||||||||
| 5000 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | -deleter | C:\Users\admin\Desktop\Amcap\setup.exe | setup.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 10.0.159 Modules
| |||||||||||||||
| 5320 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6232 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Amcap.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6352 | "C:\Program Files (x86)\CoolingTech_PC_Camera\amcap.exe" | C:\Program Files (x86)\CoolingTech_PC_Camera\amcap.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Capture Application Version: 3.0.1.7 Modules
| |||||||||||||||
| 6432 | "C:\Program Files (x86)\CoolingTech_PC_Camera\monitorpad.exe" | C:\Program Files (x86)\CoolingTech_PC_Camera\monitorpad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
8 957
Read events
8 395
Write events
544
Delete events
18
Modification events
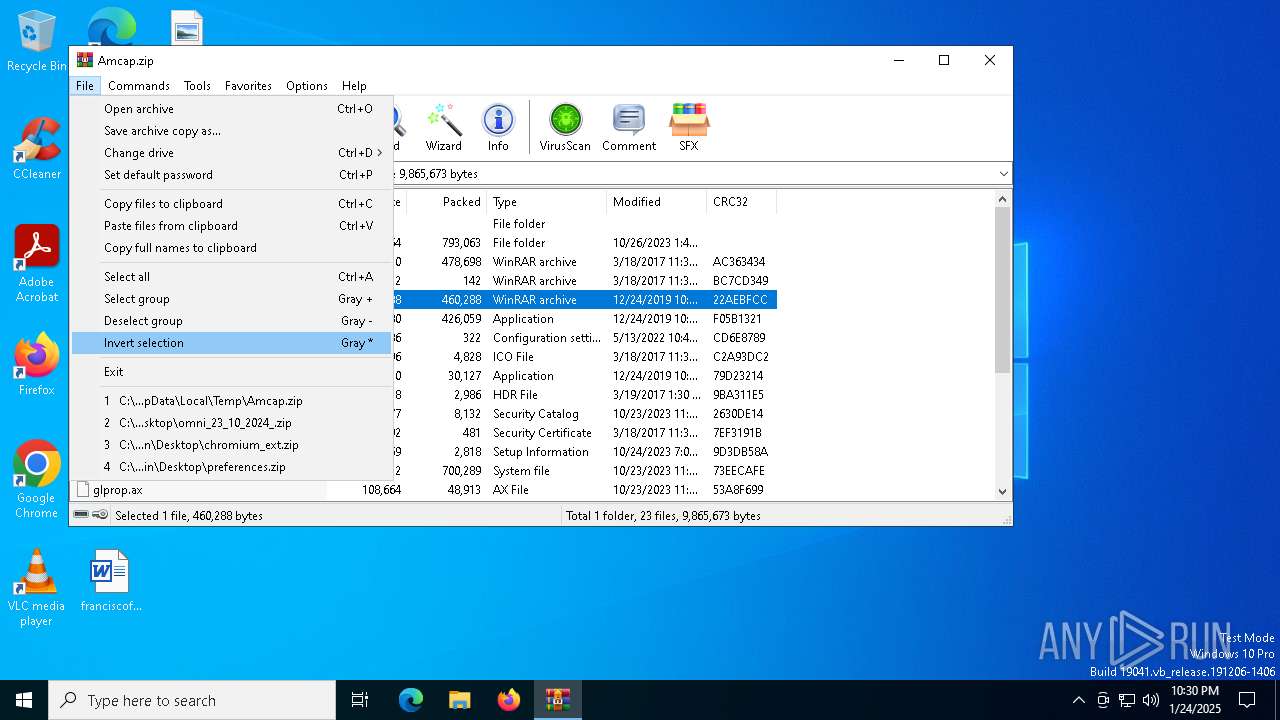
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Amcap.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
63
Suspicious files
83
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\data2.cab | compressed | |
MD5:12D7984F1B43B433C3FED35E37D201C8 | SHA256:13468E8A6E7467DA55D1B133D7FD23448618CEB4BD2323F0B5A1BF62344C0398 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\ProductName.ini | text | |
MD5:5764E37F49DC8C959A02B66415EF753E | SHA256:A4ECD3A31FE43F9782EDBDED2EAD2E22FB905D45AC33A64C05F910394D8466EC | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\certmgr.exe | executable | |
MD5:F9CA5632385711E18828588B24032E73 | SHA256:3B7A2EF688657602342F63A3108BC18578E8AA153B1ABE166829E2CF54A3FEB1 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\Camera.ico | image | |
MD5:C7F02CBEBD24E9550E19D86D49D49D01 | SHA256:781E22DB95836D5A8783B02509225C18941597218E15B8104C691DBC8AAFB215 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\data1.cab | compressed | |
MD5:47872FFB4D8C7A46E451B7BDBB52D763 | SHA256:062EC9ED02097CE00B75E165C05D5D26DE5EFBC23B0B1767D096732F0B3B0223 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\engine32.cab | compressed | |
MD5:E1D8D157E693EA5DA71DFE17A451AE82 | SHA256:A215C6648EB5B27A795E6372F8A0AD86F5A36B444541B3F2F129DE30DD8DD8F0 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\setup.ibt | binary | |
MD5:83BBBA8F7483051F5BE6BB212235D532 | SHA256:2453DFFD4CFCACE8AB5403D5FD87137057B5CBC20956A709391D071BE5F91847 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\glavcam.inf | binary | |
MD5:A6C1291BB51E90C98CC686E42E0EE507 | SHA256:1822A19485988E84F3B8679641D4A6A8E5966DA0EF0FD676A4F28C7727ADB7F2 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\layout.bin | binary | |
MD5:87E4898AE005BC62AA0A674B0FA8A617 | SHA256:2E3A5F7EFFAC57ED006C026A6421573ECB7B3EEA32795155600250B872005FC4 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.12766\Amcap\readme.txt | text | |
MD5:249F90B878F0178469DAFD3AAA1FEFF4 | SHA256:74EAF54192FA2EBE2894E5390FABBA49ED80C1E7B7FB588A7847FDB959DC7A39 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
49
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5712 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7128 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7128 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3460 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5496 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
setup.exe | IsOS64bit 1
|
setup.exe | DLL load reason 1
|
setup.exe | OS Version 6:2
|
setup.exe | DLL load reason 0
|
rundll32.exe | C:\Users\admin\Desktop\Amcap\
|
rundll32.exe | OS Maj 10, Min 0; 64 bit
|
rundll32.exe | cmdline len = 29
|
rundll32.exe | DLL load reason 1
|
rundll32.exe | Class: Image
|
rundll32.exe | BuildSupportList-- C:\Users\admin\Desktop\Amcap\\glavcam.inf |