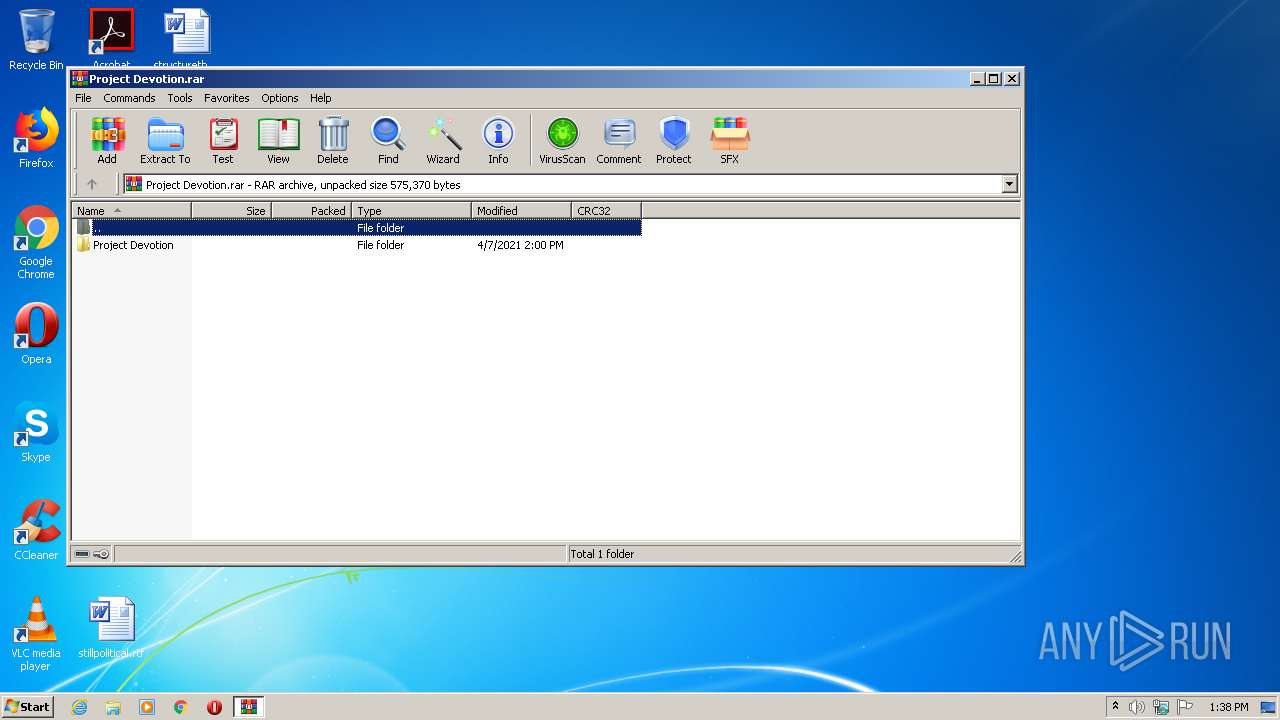
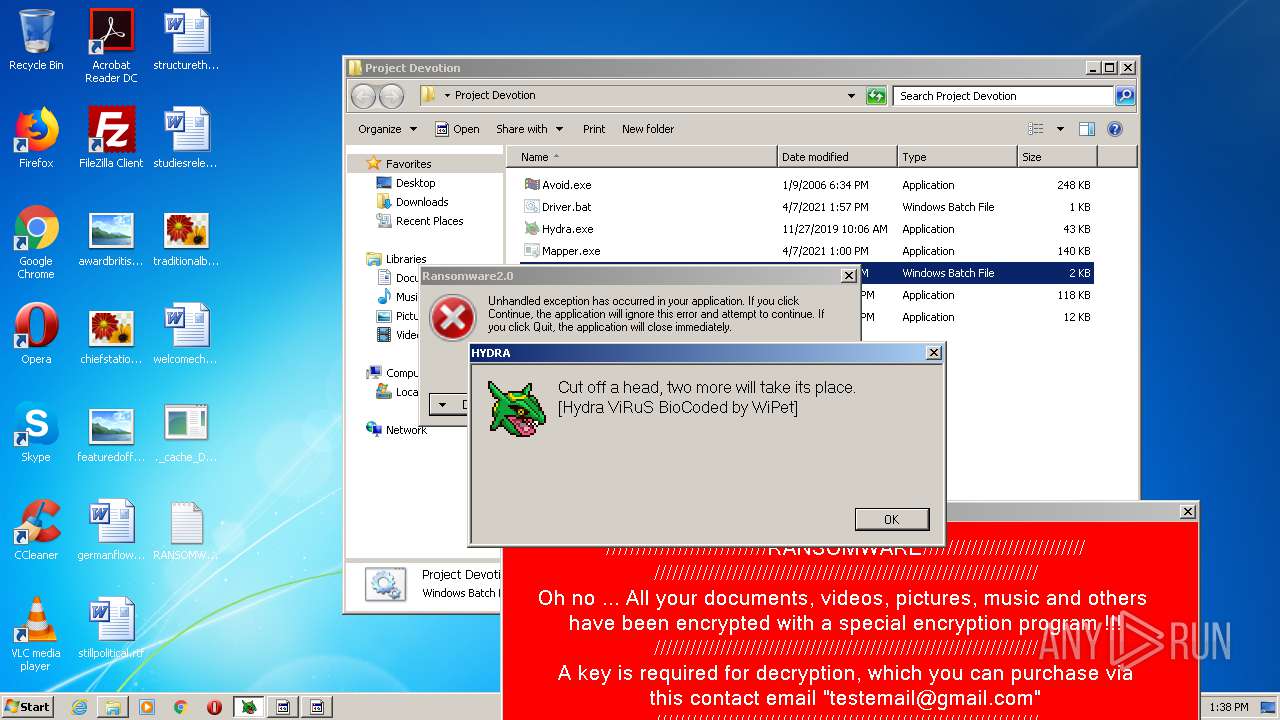
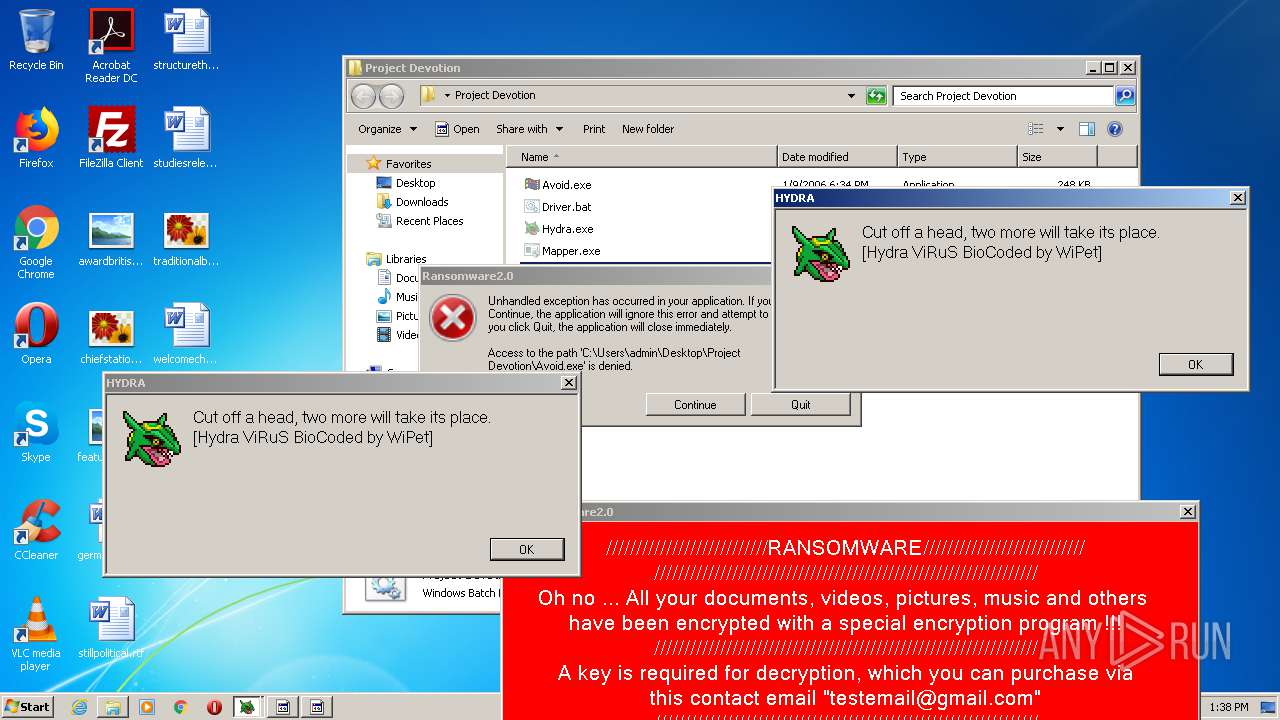
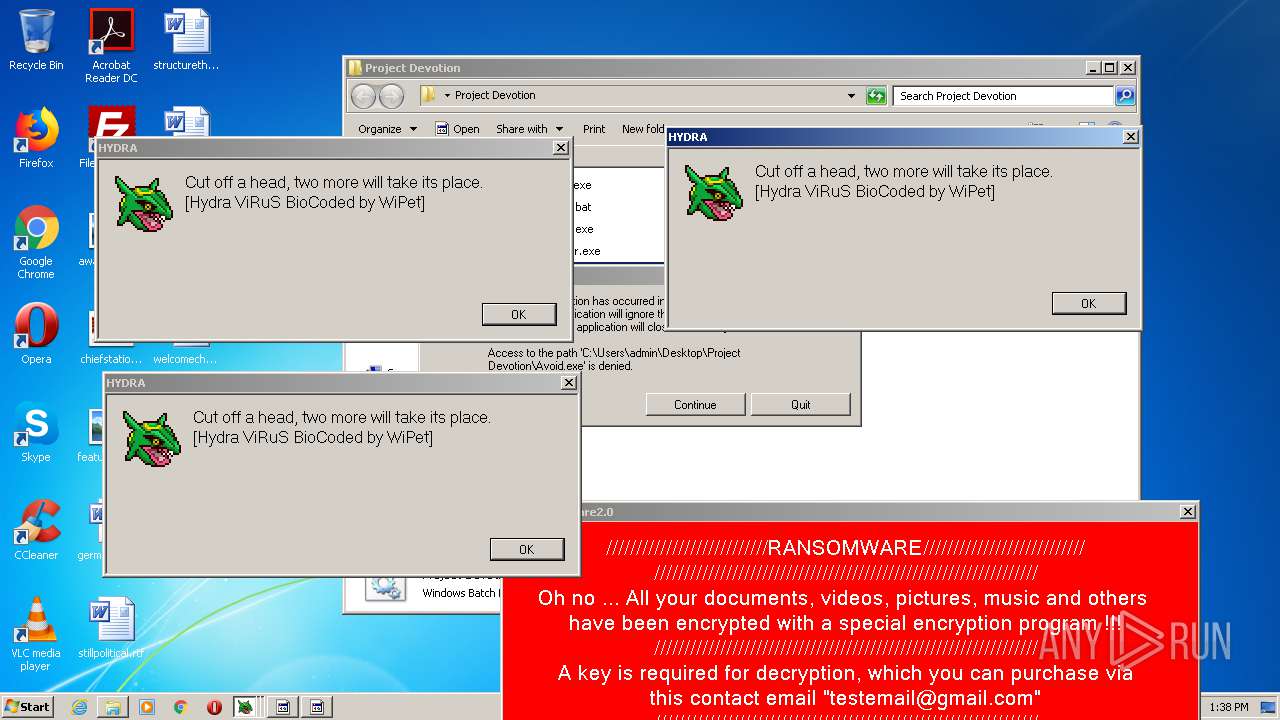
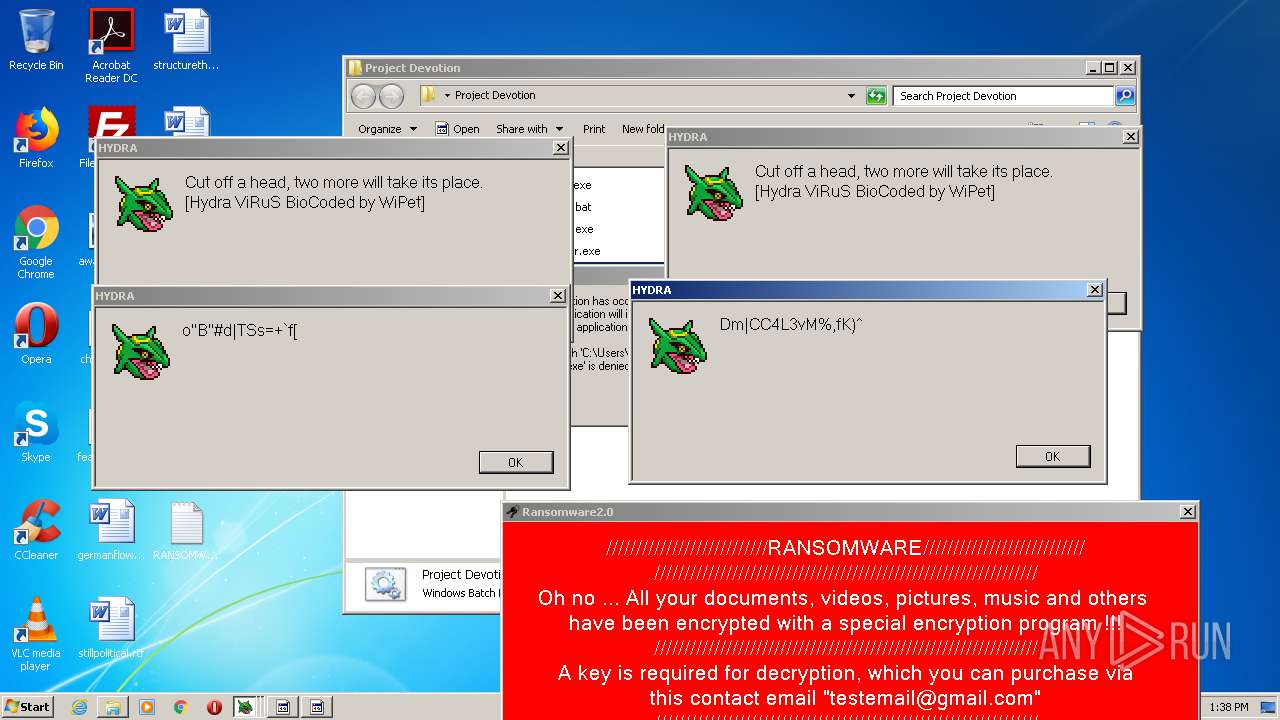
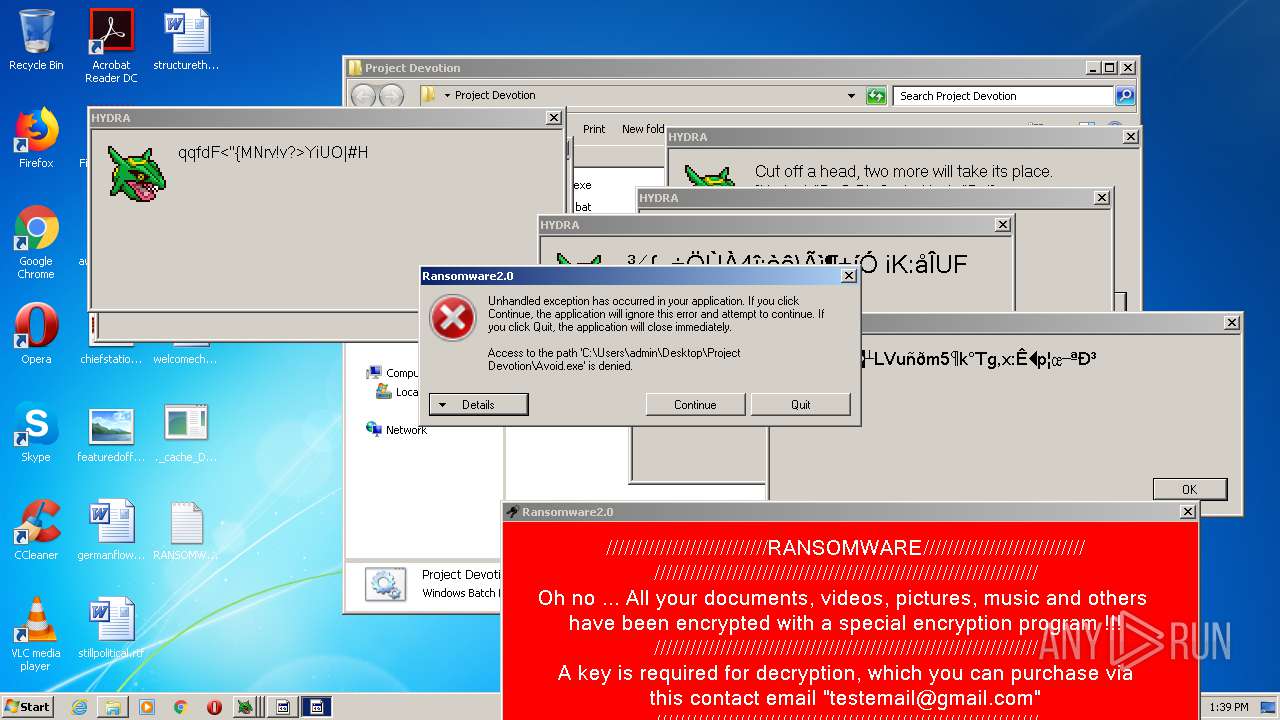
| File name: | Project Devotion.rar |
| Full analysis: | https://app.any.run/tasks/cffb5540-9aee-4bae-b178-eb02957db2d5 |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2021, 12:38:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EB7F4BC04853A30F1F9FBBBEF694A2D5 |
| SHA1: | 38B6DB0286F8C93FDBA9266C40C13CC4A4115BC6 |
| SHA256: | 431BEF6A710EE247D29F8255DCC32ACF2D349D5E596F502B5A31EF768E89CA0E |
| SSDEEP: | 6144:XCE5kv2/BGP3enpAgXfqcR9sqcb2tzQvoMx1bfeLX:X3ui0P3UpBXZMqcSuoW1b4 |
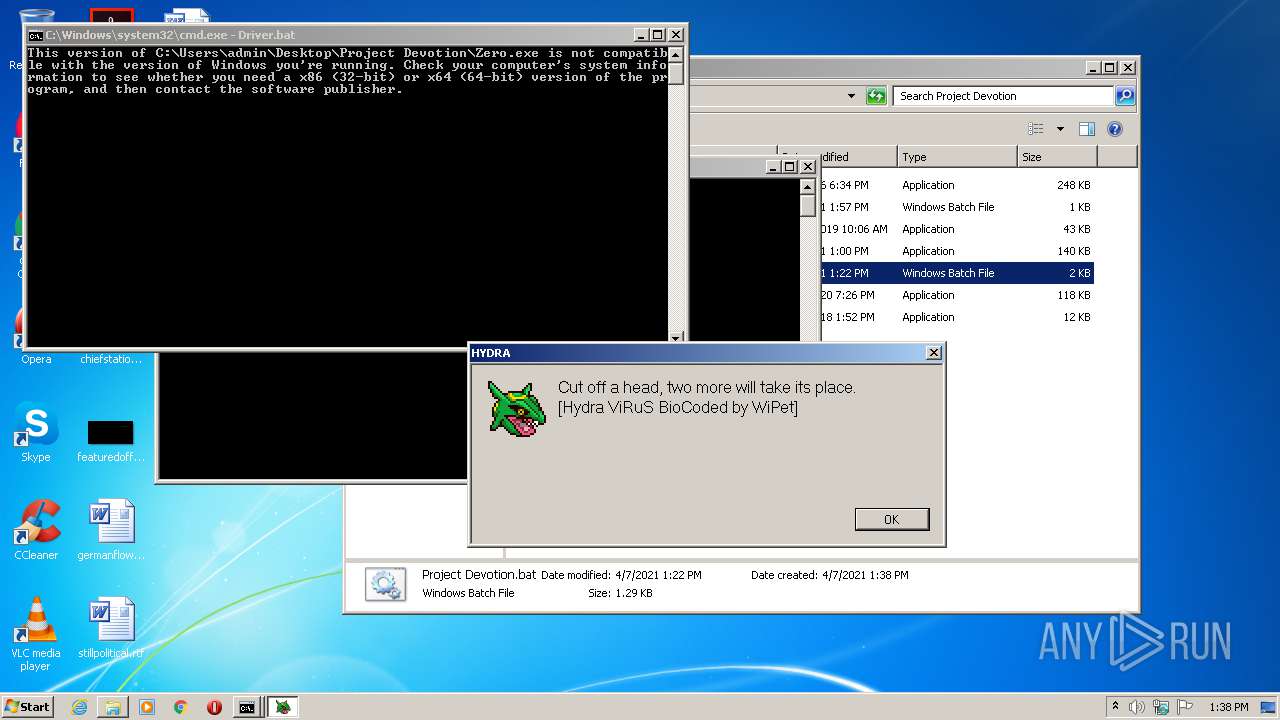
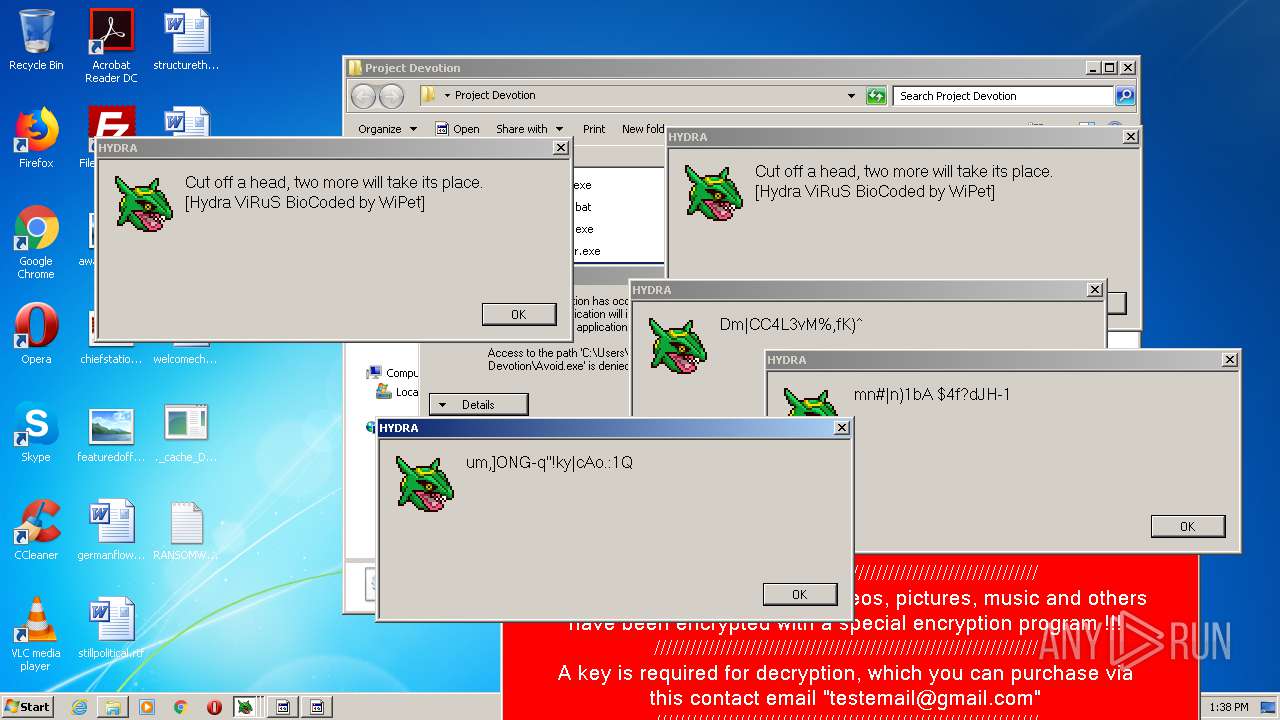
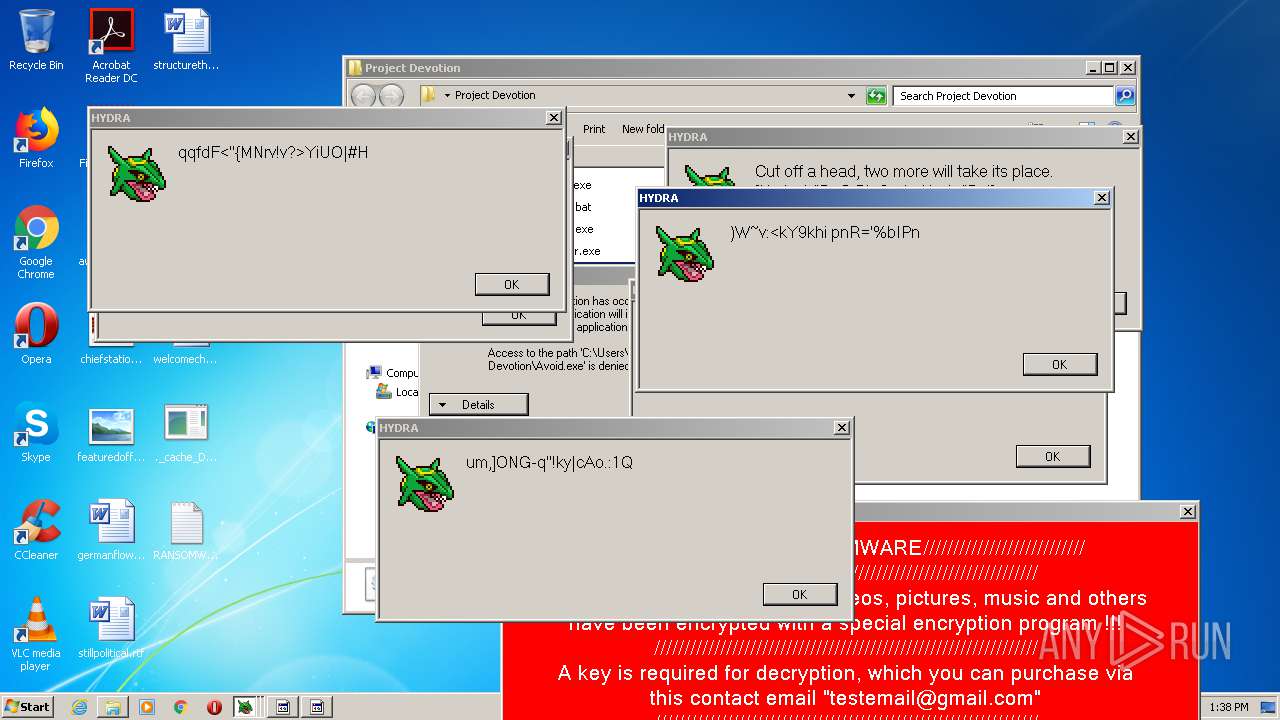
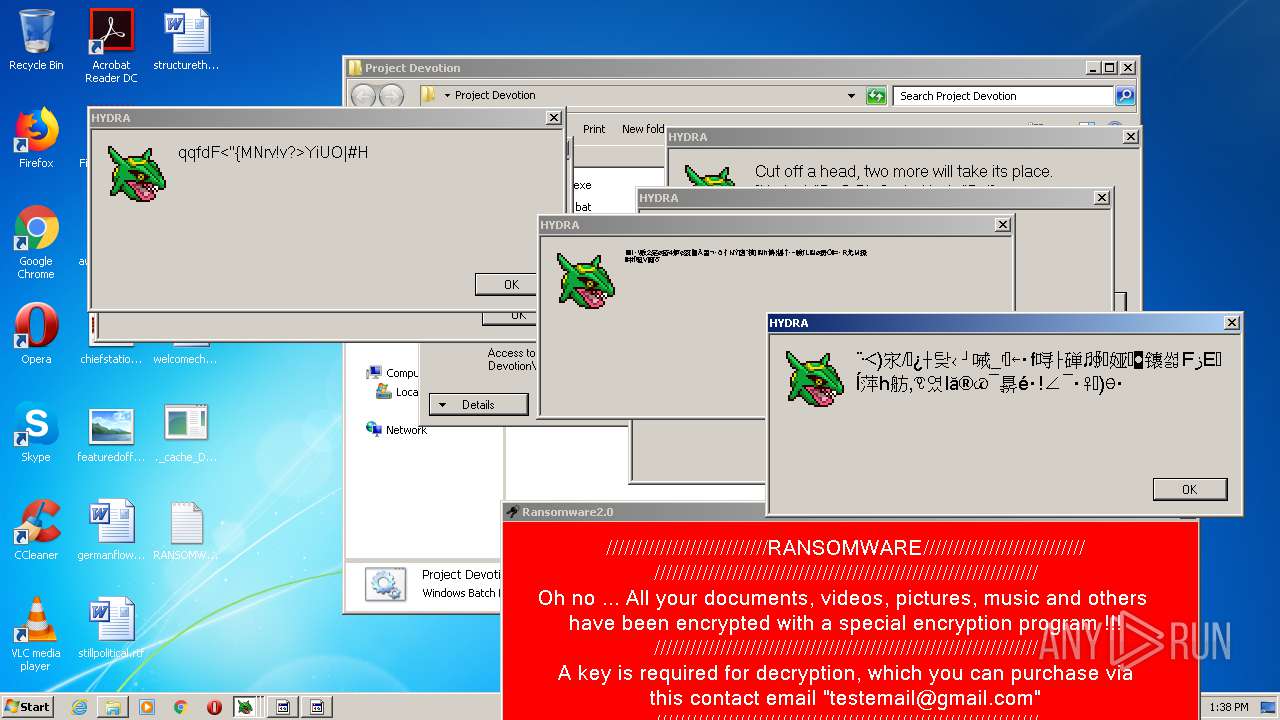
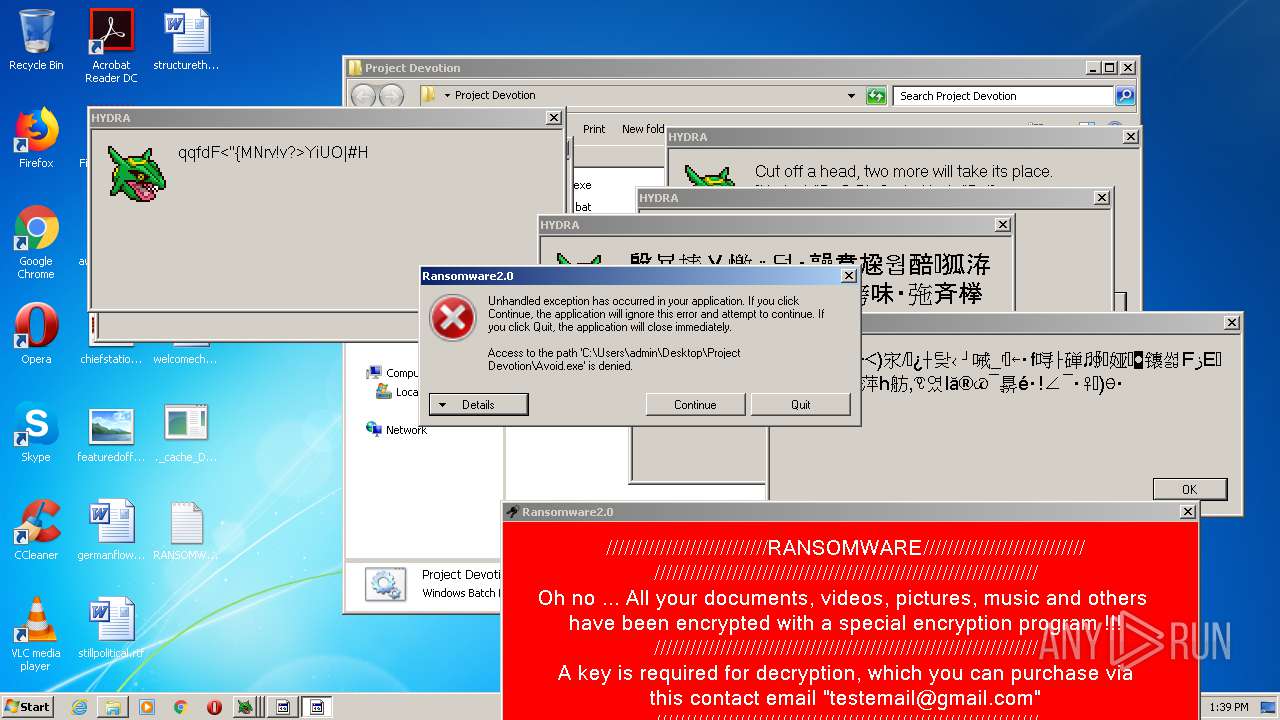
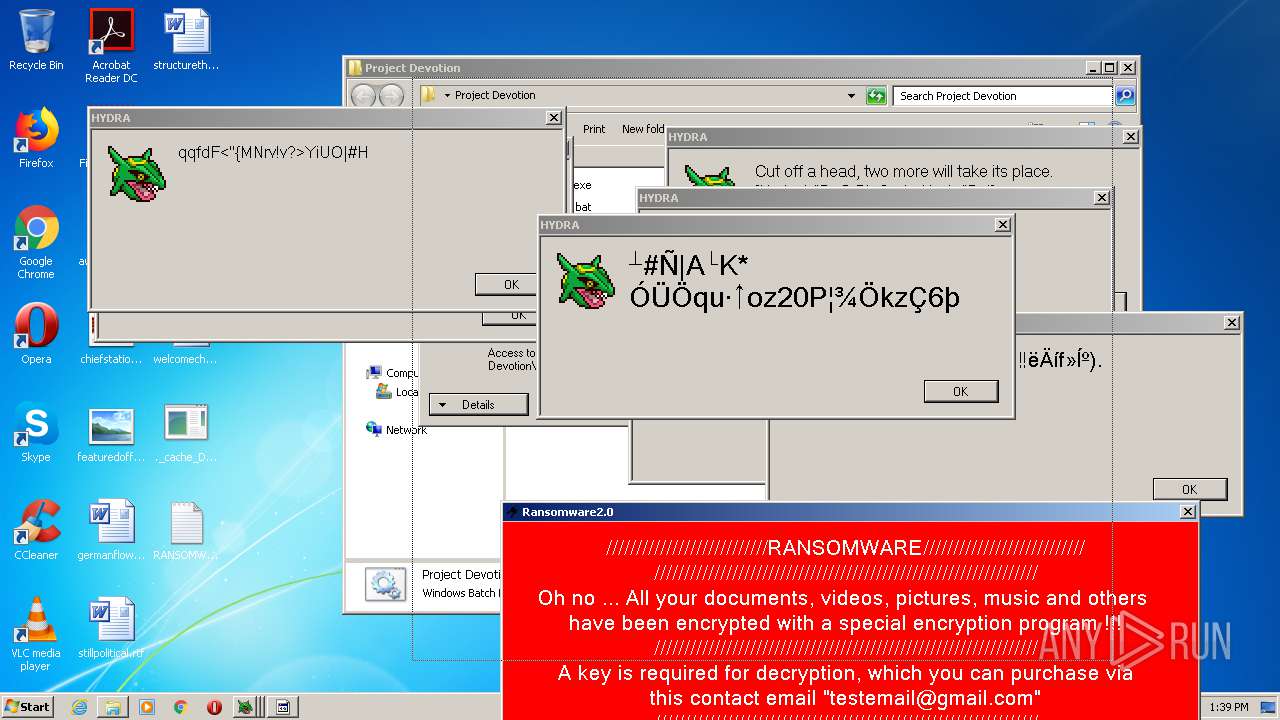
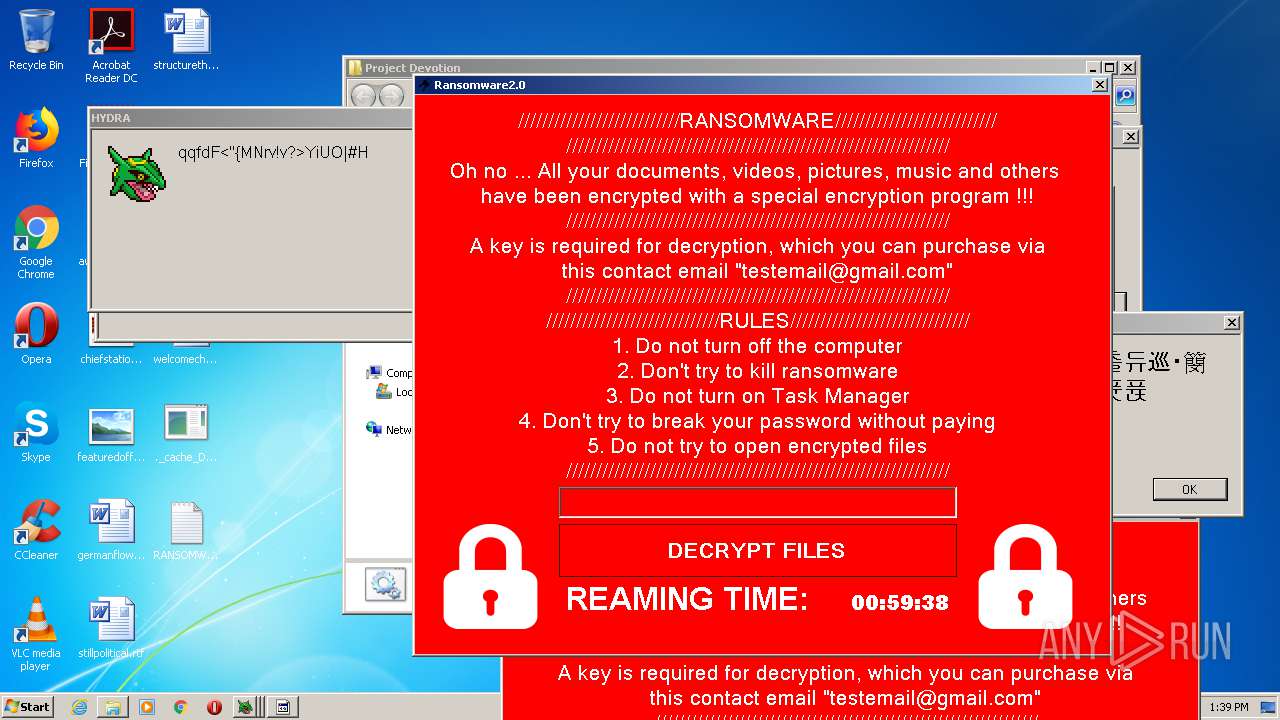
MALICIOUS
Application was dropped or rewritten from another process
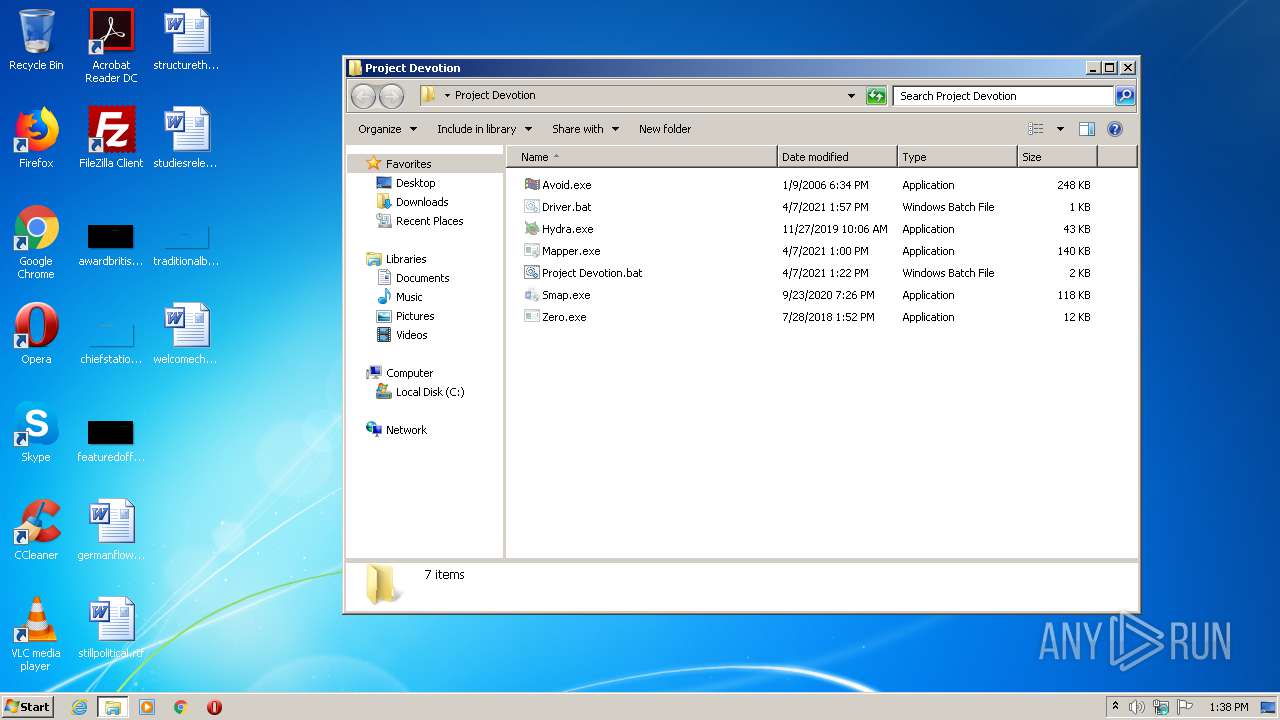
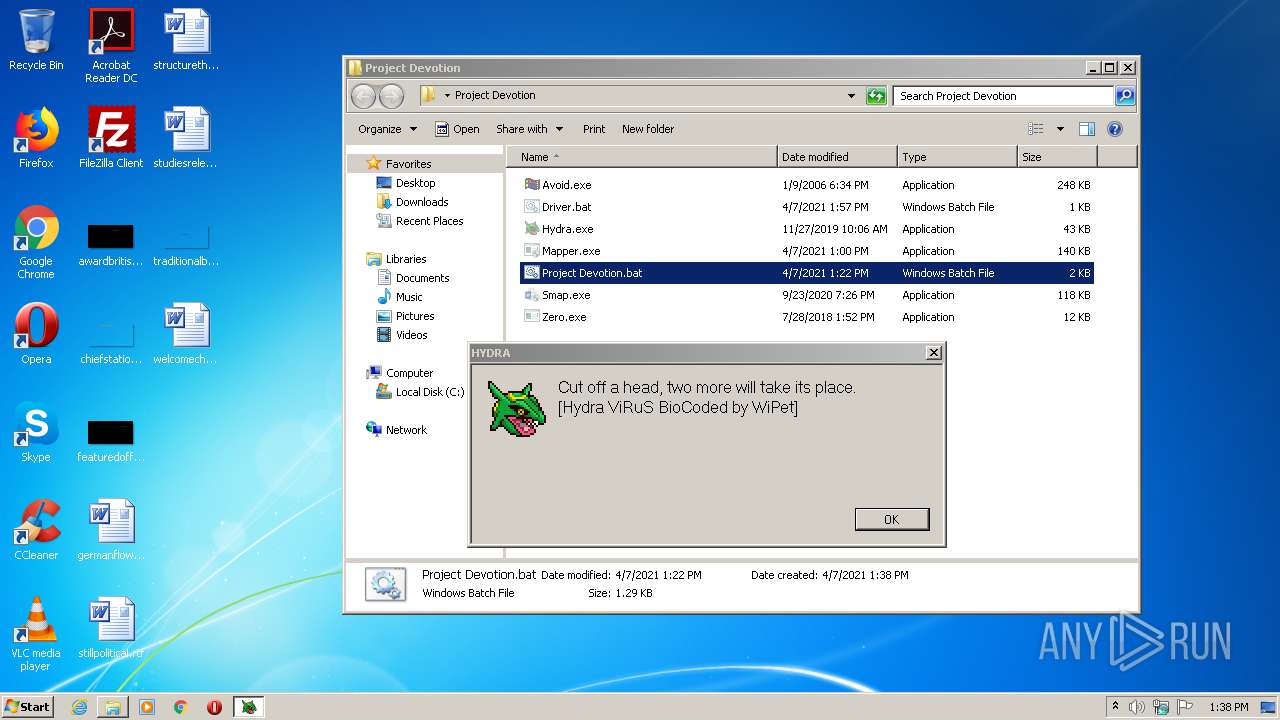
- Hydra.exe (PID: 956)
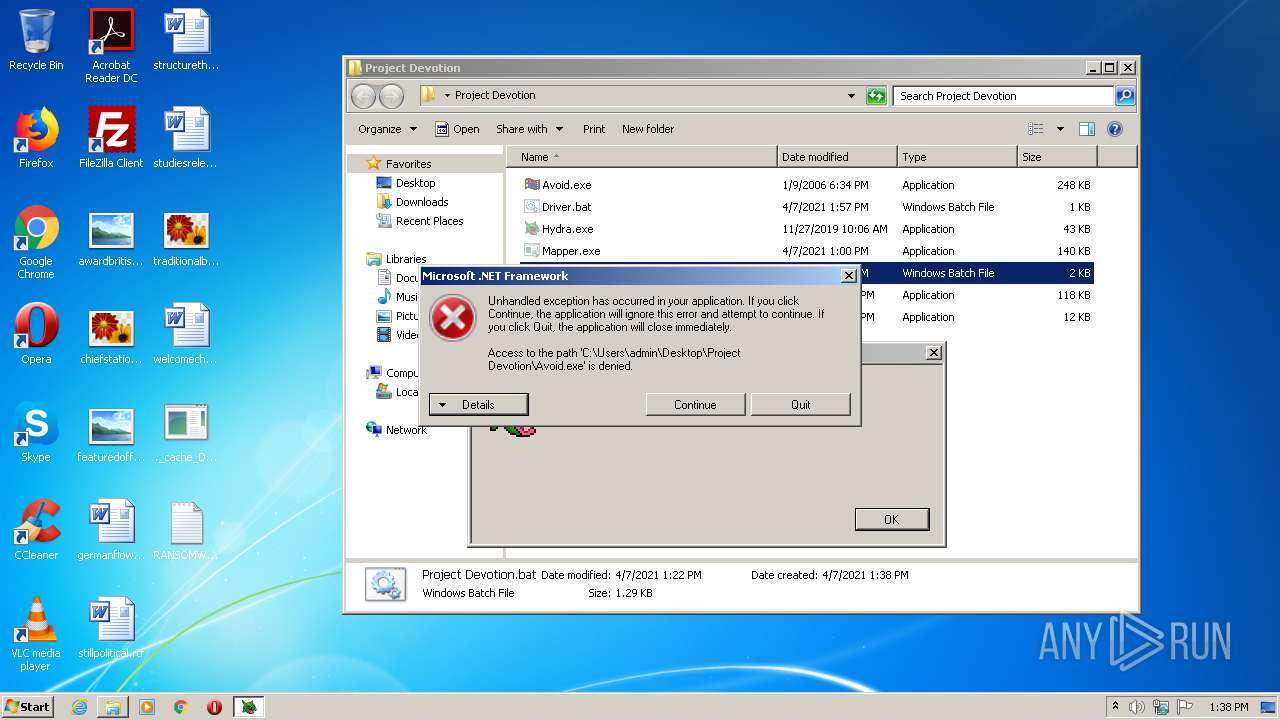
- Avoid.exe (PID: 2540)
- Mapper.exe (PID: 2756)
- Mapper.exe (PID: 2480)
- Mapper.exe (PID: 888)
- Smap.exe (PID: 2560)
- Smap.exe (PID: 3876)
- Smap.exe (PID: 3784)
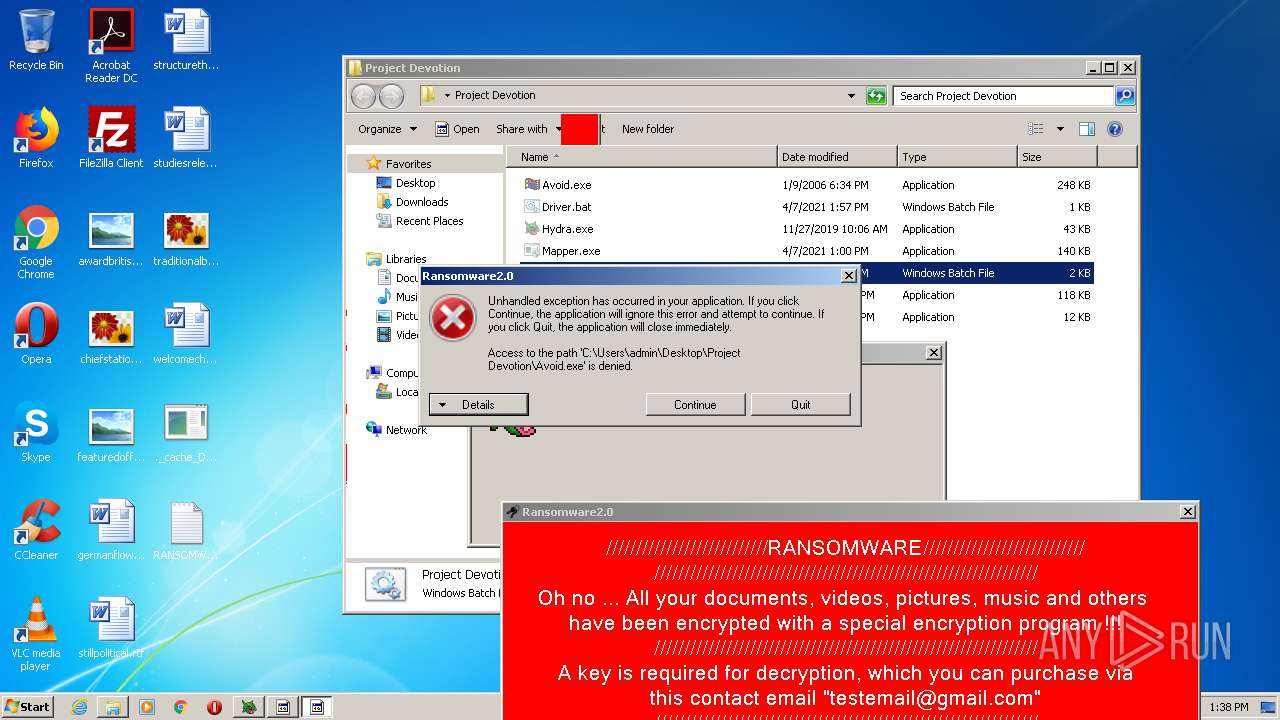
- Ransomware2.0.exe (PID: 3688)
Task Manager has been disabled (taskmgr)
- Mapper.exe (PID: 888)
- Ransomware2.0.exe (PID: 3688)
Changes the login/logoff helper path in the registry
- Mapper.exe (PID: 888)
- Ransomware2.0.exe (PID: 3688)
Changes settings of System certificates
- Smap.exe (PID: 3784)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3280)
- Smap.exe (PID: 3784)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3280)
- Smap.exe (PID: 3784)
Drops a file with too old compile date
- WinRAR.exe (PID: 3280)
- Smap.exe (PID: 3784)
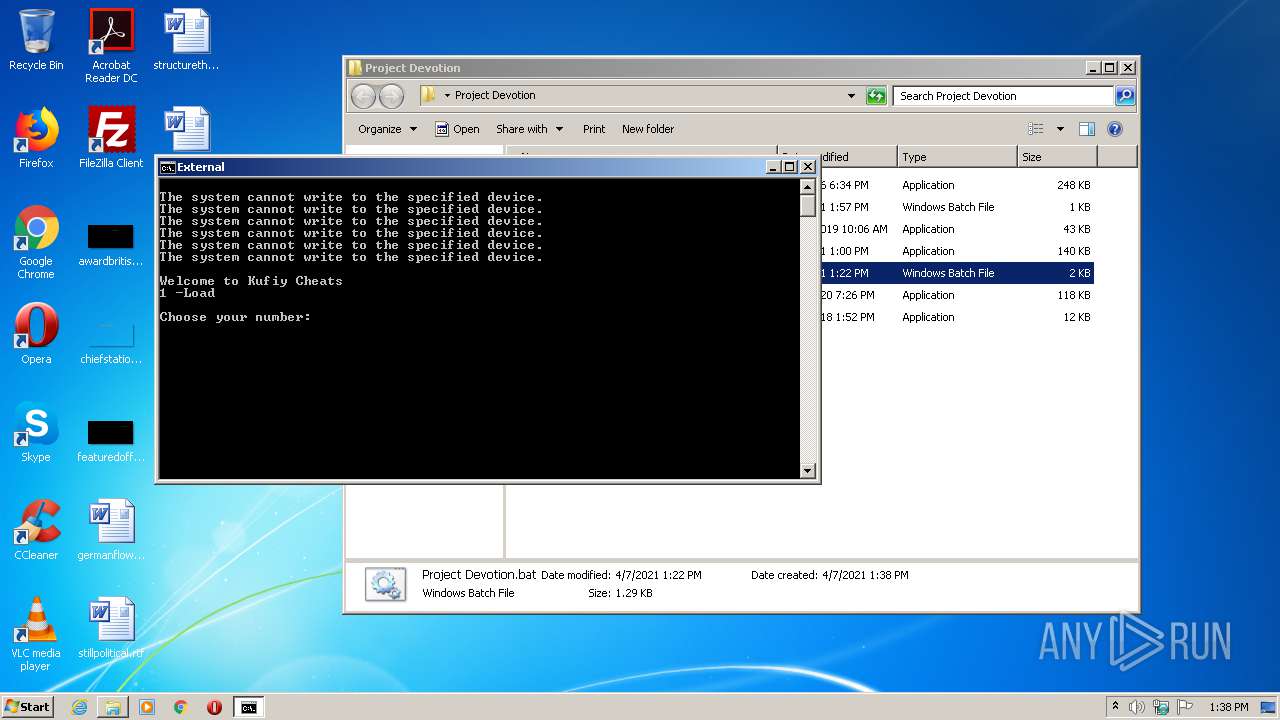
Application launched itself
- cmd.exe (PID: 3984)
Starts application with an unusual extension
- cmd.exe (PID: 3984)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3984)
Changes the desktop background image
- Mapper.exe (PID: 888)
- Ransomware2.0.exe (PID: 3688)
Creates a directory in Program Files
- Smap.exe (PID: 3784)
Creates files in the program directory
- Smap.exe (PID: 3784)
Adds / modifies Windows certificates
- Smap.exe (PID: 3784)
INFO
Manual execution by user
- cmd.exe (PID: 3984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
57
Monitored processes
13
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | "C:\Users\admin\Desktop\Project Devotion\Mapper.exe" | C:\Users\admin\Desktop\Project Devotion\Mapper.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Rasomware2.0 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 956 | Hydra.exe | C:\Users\admin\Desktop\Project Devotion\Hydra.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Hydra Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1016 | C:\Windows\system32\cmd.exe /K Driver.bat | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2480 | "C:\Users\admin\Desktop\Project Devotion\Mapper.exe" | C:\Users\admin\Desktop\Project Devotion\Mapper.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Rasomware2.0 Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2540 | Avoid.exe | C:\Users\admin\Desktop\Project Devotion\Avoid.exe | — | cmd.exe | |||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Start Button avoids the mouse cursor. Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 2560 | Smap.exe | C:\Users\admin\Desktop\Project Devotion\Smap.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: launcher2.0 Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2756 | Mapper.exe | C:\Users\admin\Desktop\Project Devotion\Mapper.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Rasomware2.0 Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3168 | chcp 65001 | C:\Windows\system32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3280 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Project Devotion.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3688 | "C:\Program Files\System32\Ransomware2.0.exe" | C:\Program Files\System32\Ransomware2.0.exe | Smap.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Rasomware2.0 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
693
Read events
623
Write events
70
Delete events
0
Modification events
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Project Devotion.rar | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3280) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ArcName |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Project Devotion.rar | |||
Executable files
11
Suspicious files
22
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rar_3280.43725 | — | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.43540\Project Devotion\Mapper.exe | executable | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.43540\Project Devotion\Project Devotion.bat | text | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.43540\Project Devotion\Driver.bat | text | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Project Devotion.bak3280.43729 | compressed | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Project Devotion.rar | compressed | |
MD5:— | SHA256:— | |||
| 888 | Mapper.exe | C:\Users\admin\Desktop\._cache_DCQPKX.exe | binary | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.43540\Project Devotion\Avoid.exe | executable | |
MD5:20D2C71D6D9DAF4499FFC4A5D164F1C3 | SHA256:3AC8CC58DCBCEAEC3DAB046AEA050357E0E2248D30B0804C738C9A5B037C220D | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.43929\Project Devotion\Driver.bat | text | |
MD5:— | SHA256:— | |||
| 3280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3280.43929\Project Devotion\Mapper.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3784 | Smap.exe | 185.199.109.133:443 | raw.githubusercontent.com | GitHub, Inc. | NL | malicious |
3784 | Smap.exe | 140.82.121.3:443 | github.com | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
raw.githubusercontent.com |
| shared |