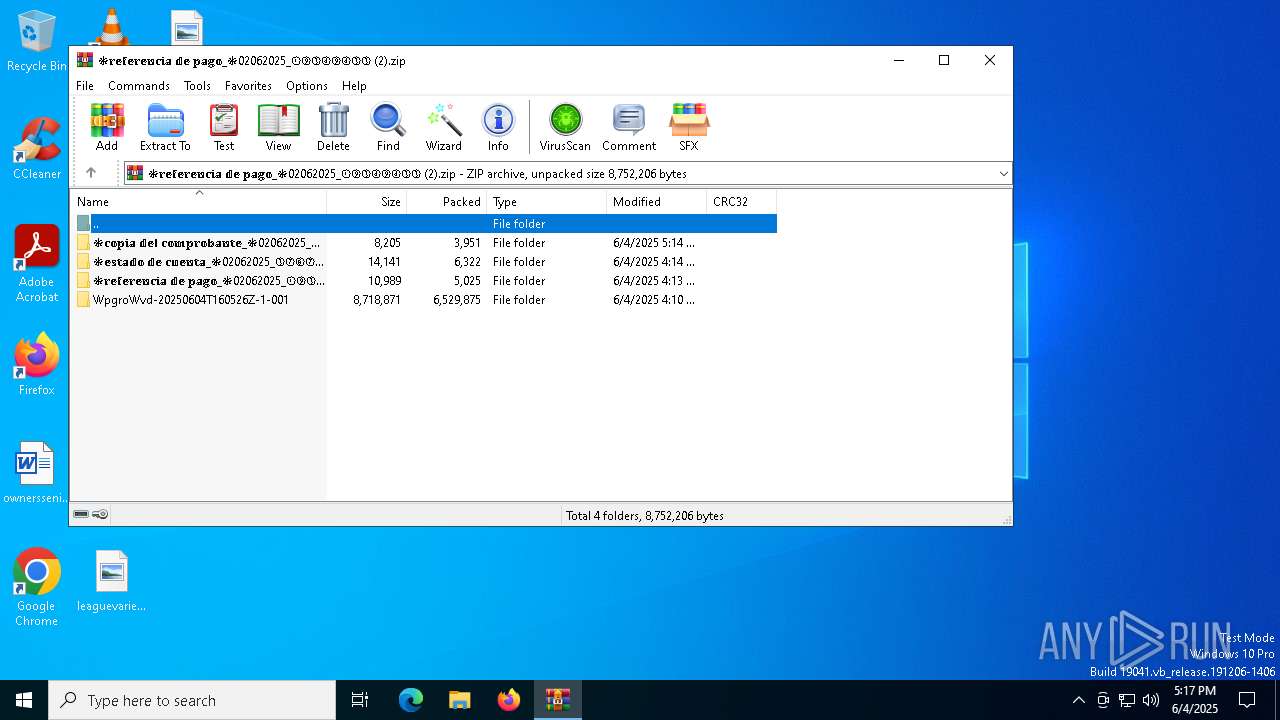
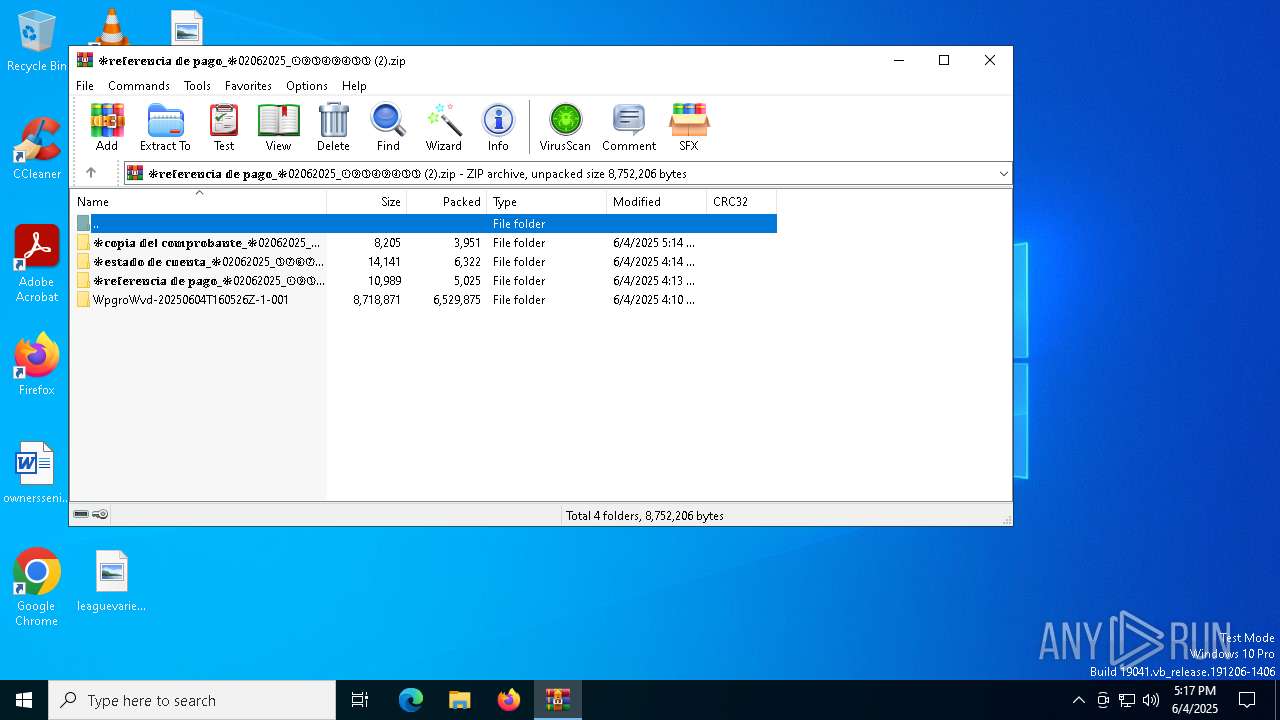
| File name: | ❉𝕣𝕖𝕗𝕖𝕣𝕖𝕟𝕔𝕚𝕒 𝕕𝕖 𝕡𝕒𝕘𝕠_❉02062025_①⑨③④⑨④③③ (2).zip |
| Full analysis: | https://app.any.run/tasks/8afc6d68-87db-41d6-b1d7-b1d2ad418e42 |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2025, 17:17:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 1473E1DB113DB56DD1DFC73AAB5125B7 |
| SHA1: | 0BD414417236631651A06918D0E4A6E52E58C108 |
| SHA256: | 42FA9FCF3407B00E1D172DF982E3C2CF72A9453FCDBFA484A2E99EBF571C2DD1 |
| SSDEEP: | 98304:Z8ggJe2Dr5A/eLO6tK9iQTZxMCUodsLNGyx+zUx8OuYvdCZptWGK3m/BqMISJn0g:Nu8u8OT8E4aG |
MALICIOUS
Gets username (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Accesses environment variables (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Checks whether a specified folder exists (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Accesses BIOS(Win32_BIOS, may evade sandboxes) via WMI (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
SUSPICIOUS
Accesses computer name via WMI (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Gets computer name (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Creates FileSystem object to access computer's file system (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Accesses current user name via WMI (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Executes WMI query (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Accesses language version of the operating system installed via WMI (SCRIPT)
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5960)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5960)
Checks proxy server information
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Manual execution by a user
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Reads Internet Explorer settings
- mshta.exe (PID: 6268)
- mshta.exe (PID: 4424)
- mshta.exe (PID: 2692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:04 10:13:36 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ❉𝕣𝕖𝕗𝕖𝕣𝕖𝕟𝕔𝕚𝕒 𝕕𝕖 𝕡𝕒𝕘𝕠_❉02062025_①⑨③④⑨④③③/ |
Total processes
129
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2692 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Desktop\❉𝕣𝕖𝕗𝕖𝕣𝕖𝕟𝕔𝕚𝕒 𝕕𝕖 𝕡𝕒𝕘𝕠_❉02062025_①⑨③④⑨④③③\❉𝕣𝕖𝕗𝕖𝕣𝕖𝕟𝕔𝕚𝕒 𝕕𝕖 𝕡𝕒𝕘𝕠_❉③④④④③⑥①⑥④.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4404 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4424 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Desktop\❉𝕖𝕤𝕥𝕒𝕕𝕠 𝕕𝕖 𝕔𝕦𝕖𝕟𝕥𝕒_❉02062025_③⑦⑥⑦⑥⑥⑨⑥\❉𝕖𝕤𝕥𝕒𝕕𝕠 𝕕𝕖 𝕔𝕦𝕖𝕟𝕥𝕒_❉⑤⑥⑨⑤②⑦⑦.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5960 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\❉𝕣𝕖𝕗𝕖𝕣𝕖𝕟𝕔𝕚𝕒 𝕕𝕖 𝕡𝕒𝕘𝕠_❉02062025_①⑨③④⑨④③③ (2).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6268 | "C:\Windows\SysWOW64\mshta.exe" "C:\Users\admin\Desktop\❉𝕔𝕠𝕡𝕚𝕒 𝕕𝕖𝕝 𝕔𝕠𝕞𝕡𝕣𝕠𝕓𝕒𝕟𝕥𝕖_❉02062025_④②⑦②⑥③⑥④\❉𝕔𝕠𝕡𝕚𝕒 𝕕𝕖𝕝 𝕔𝕠𝕞𝕡𝕣𝕠𝕓𝕒𝕟𝕥𝕖_❉③⑨⑨⑥①.hta" {1E460BD7-F1C3-4B2E-88BF-4E770A288AF5}{1E460BD7-F1C3-4B2E-88BF-4E770A288AF5} | C:\Windows\SysWOW64\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7576 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 973
Read events
4 929
Write events
31
Delete events
13
Modification events
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\❉𝕣𝕖𝕗𝕖𝕣𝕖𝕟𝕔𝕚𝕒 𝕕𝕖 𝕡𝕒𝕘𝕠_❉02062025_①⑨③④⑨④③③ (2).zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
1
Suspicious files
4
Text files
10
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5960 | WinRAR.exe | C:\Users\admin\Desktop\WpgroWvd-20250604T160526Z-1-001\WpgroWvd\ZCzaYSvwicRt | — | |
MD5:— | SHA256:— | |||
| 5960 | WinRAR.exe | C:\Users\admin\Desktop\❉𝕔𝕠𝕡𝕚𝕒 𝕕𝕖𝕝 𝕔𝕠𝕞𝕡𝕣𝕠𝕓𝕒𝕟𝕥𝕖_❉02062025_④②⑦②⑥③⑥④\❉𝕔𝕠𝕡𝕚𝕒 𝕕𝕖𝕝 𝕔𝕠𝕞𝕡𝕣𝕠𝕓𝕒𝕟𝕥𝕖_❉③⑨⑨⑥①.hta | html | |
MD5:6EABB106B751AFD109396A1A6AD2F6B1 | SHA256:9209D6CE18A88DA583F6925EB94639A87E14C50795942366D80B0448FBD7A466 | |||
| 5960 | WinRAR.exe | C:\Users\admin\Desktop\❉𝕖𝕤𝕥𝕒𝕕𝕠 𝕕𝕖 𝕔𝕦𝕖𝕟𝕥𝕒_❉02062025_③⑦⑥⑦⑥⑥⑨⑥\❉𝕖𝕤𝕥𝕒𝕕𝕠 𝕕𝕖 𝕔𝕦𝕖𝕟𝕥𝕒_❉⑤⑥⑨⑤②⑦⑦.hta | html | |
MD5:F89582F354AEFFDD6E8D2DB44DB1370E | SHA256:016A335D3A73F4A62FAB0635CD410669F1482AE9A5C782369FA2E7261E81EF26 | |||
| 6268 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | der | |
MD5:F2F6BC84AA7D89B5EDC784A6E7260035 | SHA256:80BF6621B5C4CBD53A8DCF3A0FD511C8AFC57716EE9A2426981413B36E11B57C | |||
| 6268 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 6268 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\WlDx6zXe8pF[1].js | text | |
MD5:3EA2742BD8913A3683940152E9B8ECA0 | SHA256:A293207278A17770138C042C58731F5460FF51B9D64A0982E6F56B616654237F | |||
| 6268 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2901C1EE558CDB27F7D117D7B17025D8_07A8408A5E47C21721CF3B9ABAEDBACA | der | |
MD5:04DD9716257E7B4572F375510DFF0F57 | SHA256:36602E790524FB609F789B125ACE95B2102073E42F9750C705EB173BED68C449 | |||
| 6268 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\cid[1].htm | html | |
MD5:601021DCC2126CCE3829EE37309E3A41 | SHA256:2CF3E5DAE89F19EA098D564DE30BFCFC7C69A0210F6DDD5E0D6EF8252A54F4AA | |||
| 6268 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2901C1EE558CDB27F7D117D7B17025D8_07A8408A5E47C21721CF3B9ABAEDBACA | binary | |
MD5:67EDAF7AC1BA52FFBBBB732B2AB80FEF | SHA256:10E4F5FE94823D37EEC077DD8CE639DDC3C4C9C5095F65F3CA66BF8B658AD833 | |||
| 6268 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:675C5648F9C479AE8039599FC1FB1CAA | SHA256:25C5D8FAC3D5405FF1EA3D64CE527811D92A6E5C0EC794C537B69AF08C500AE9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
28
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6268 | mshta.exe | GET | 200 | 95.101.54.195:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgb3i2O7YfwJ0ZwnijX0IE2%2FNw%3D%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6268 | mshta.exe | GET | 200 | 18.245.38.41:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | whitelisted |
6268 | mshta.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
672 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
672 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4424 | mshta.exe | GET | 200 | 18.173.160.201:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEASSLs8bivtMtQSolDXxm6c%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3760 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7784 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
club-ui-static-files.cb.hotmart.com |
| unknown |
145.85.74.97.host.secureserver.net |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |