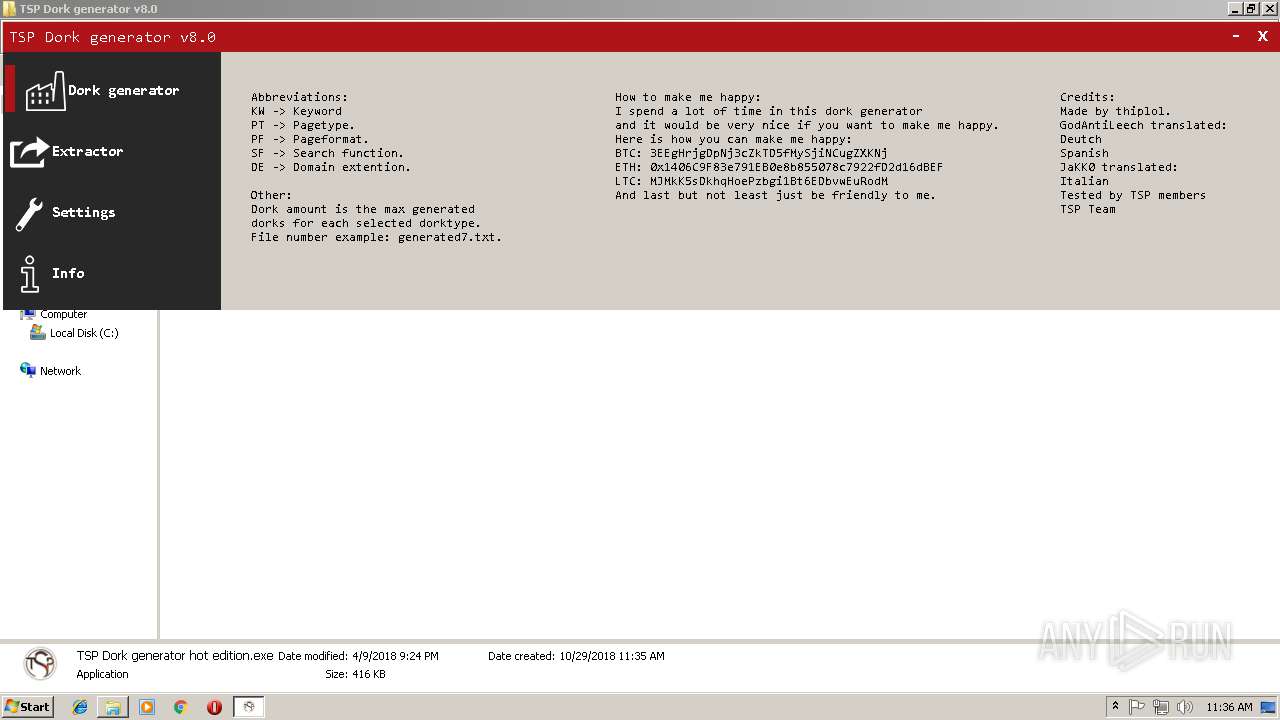
| File name: | TSP Dork generator v8.0.rar |
| Full analysis: | https://app.any.run/tasks/3f4036d5-dabd-4ee5-baa7-60ce90189ccf |
| Verdict: | Malicious activity |
| Analysis date: | October 29, 2018, 11:35:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FD6F4E94278D5A6778B7B2AD491A81B6 |
| SHA1: | E77116C37A43345D1932E045AB0C82F3BC9C69F7 |
| SHA256: | 42EA276F57E0C94ACCEEBB3073B5A04F377530BF5C4EFF6C4D65435253C6FFD1 |
| SSDEEP: | 3072:ulIjgFtA7AZd36w4CZbwb2jn5+JCEsRfcy5wMcnUPNCd24XA:ulUgvA7AZd36w4YVgCEsu8SnqNk2P |
MALICIOUS
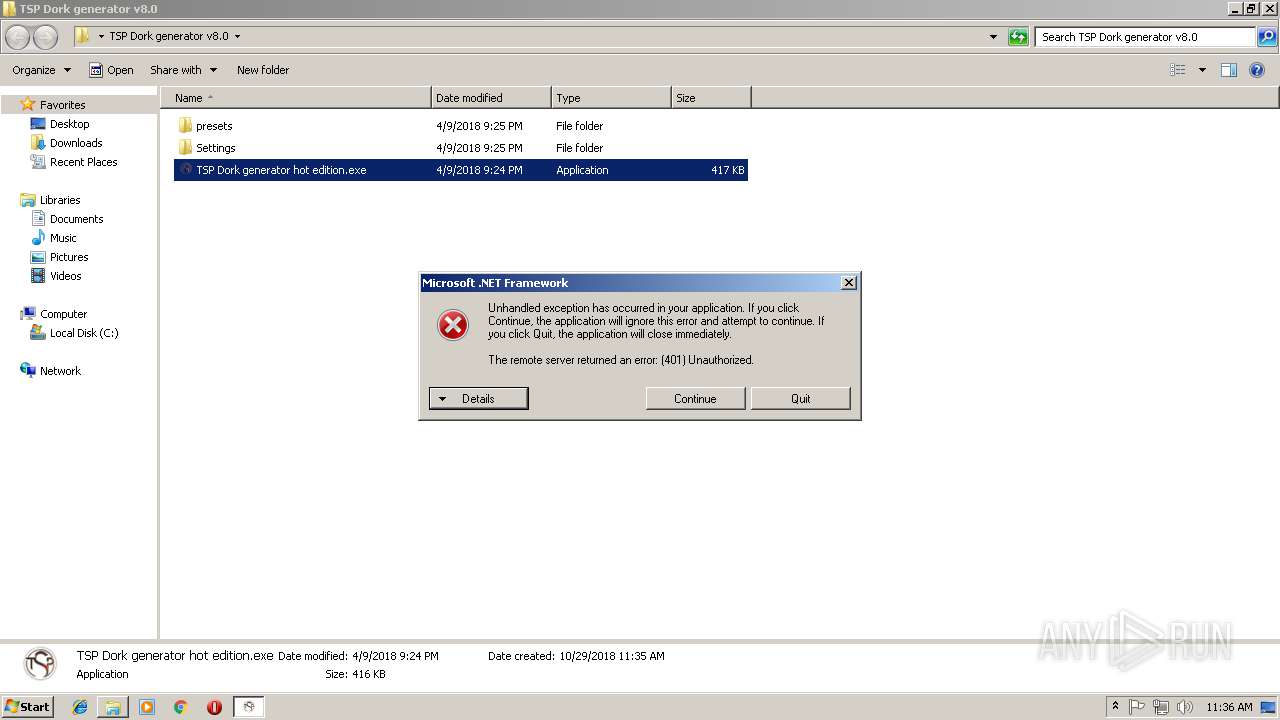
Application was dropped or rewritten from another process
- TSP Dork generator hot edition.exe (PID: 3108)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1688)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 1688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
36
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1688 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TSP Dork generator v8.0.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3108 | "C:\Users\admin\Desktop\TSP Dork generator v8.0\TSP Dork generator hot edition.exe" | C:\Users\admin\Desktop\TSP Dork generator v8.0\TSP Dork generator hot edition.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TSP Dork generator hot edition Exit code: 0 Version: 8.0 Modules
| |||||||||||||||
Total events
490
Read events
449
Write events
41
Delete events
0
Modification events
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TSP Dork generator v8.0.rar | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
1
Suspicious files
0
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\domainextentions\preset2.txt | text | |
MD5:9BC73C29CE06144A655572DEEFCAABDC | SHA256:BF65DF2FCDF6B14147223C9C82172A2FCD9C668924381BD00618C4B57CC4DA2D | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\keywords\preset4.txt | text | |
MD5:0F66E729C9AEC472641B571C2C0BAB26 | SHA256:405F1E7D0F5ECEB5749886F690D1A915A08C7D9F357579E866BF1481B4200566 | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\domainextentions\preset4.txt | text | |
MD5:D226F5E0575E845DDB610E0DAB8654AA | SHA256:946666992DBD0B0F4FE9021F312C616AAD550091D1097524B4FF1DF738B64B7E | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\domainextentions\preset1.txt | text | |
MD5:67815BB37D3B3D1BF9CD8D247DF71921 | SHA256:AB11A70EEF7BA2A8F146864EC8A4E675C0834A71E02087B86815EEF7F3B1F4AD | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\keywords\preset2.txt | text | |
MD5:3B5F91B1BED803B285B6201E23C1DF93 | SHA256:5579FE58E9B7ED2CC17C034DC08DF1CC5996094154F49AEE275B3593C53D5E45 | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\domainextentions\preset3.txt | text | |
MD5:561B8CC2A5E145D78E61EF62B4D15D30 | SHA256:0F37CE78BE139CB3161C45F93FD2E7D502124EF349D9E9DC95386E46350B7A89 | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\pagetypes\preset2.txt | text | |
MD5:5429B5BED87190B6A82E57A4701D7256 | SHA256:85E3265A68C922BFAF3E0435DADCD2D511B7B4E605E31E28FFD54A4D70CFF9E9 | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\searchfunctions\preset2.txt | text | |
MD5:0D1C471E849110783E72C30E42739D84 | SHA256:65660887CD06E72CF738FCF4BAFB40F27D1A444DBBBA82881038ABB9E7A42E62 | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\pageformats\preset4.txt | text | |
MD5:6C7FC3EB438D36797CD28BB6FC12D41F | SHA256:61D2085D7FFB226B76A13E885E9FEF6CB3B77B6D1E54943E9FF3282C17526E1C | |||
| 1688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1688.13048\TSP Dork generator v8.0\presets\pageformats\preset3.txt | text | |
MD5:87F4C2439DDD025A233BD5AAF3656168 | SHA256:516BF2DA52790E61DF36EB8AD74FF5A458D44312E0CCE3D08CA6FD5CD4619835 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3108 | TSP Dork generator hot edition.exe | 162.125.66.6:443 | dl.dropbox.com | Dropbox, Inc. | DE | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl.dropbox.com |
| shared |
dl.dropboxusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3108 | TSP Dork generator hot edition.exe | Misc activity | SUSPICIOUS [PTsecurity] Dropbox SSL Payload Request |
3108 | TSP Dork generator hot edition.exe | Misc activity | SUSPICIOUS [PTsecurity] Dropbox SSL Payload Request |