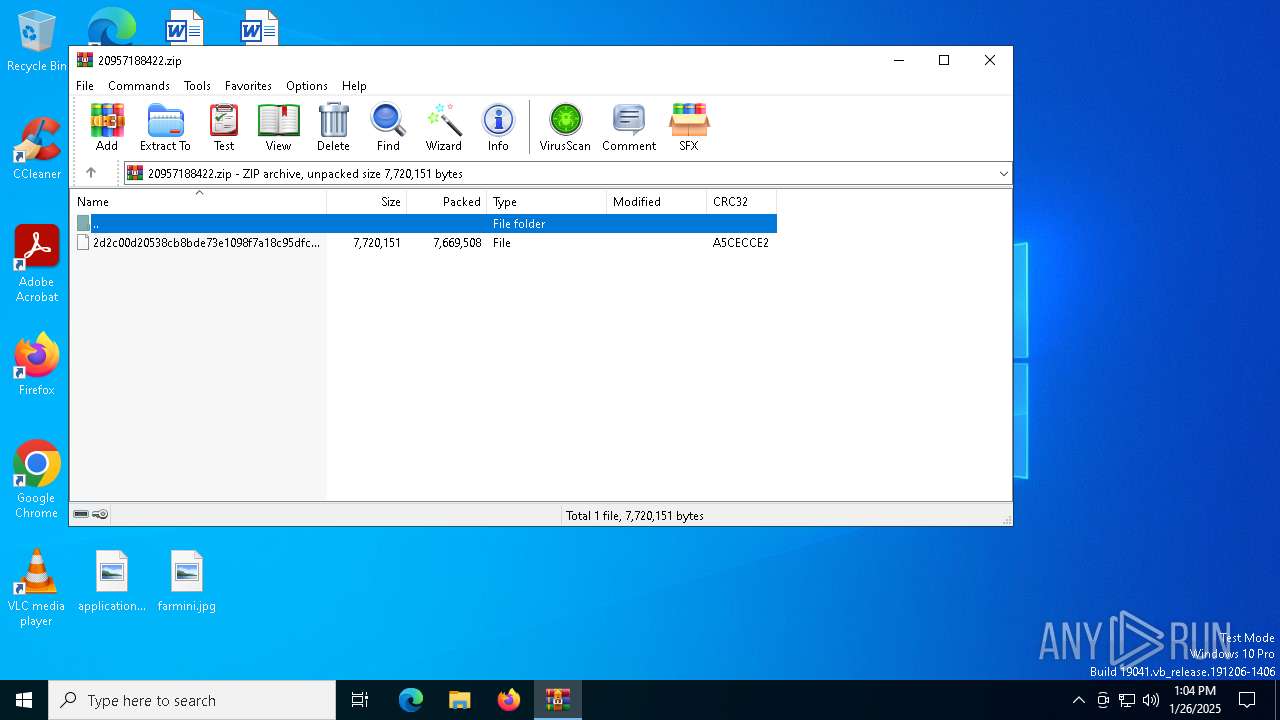
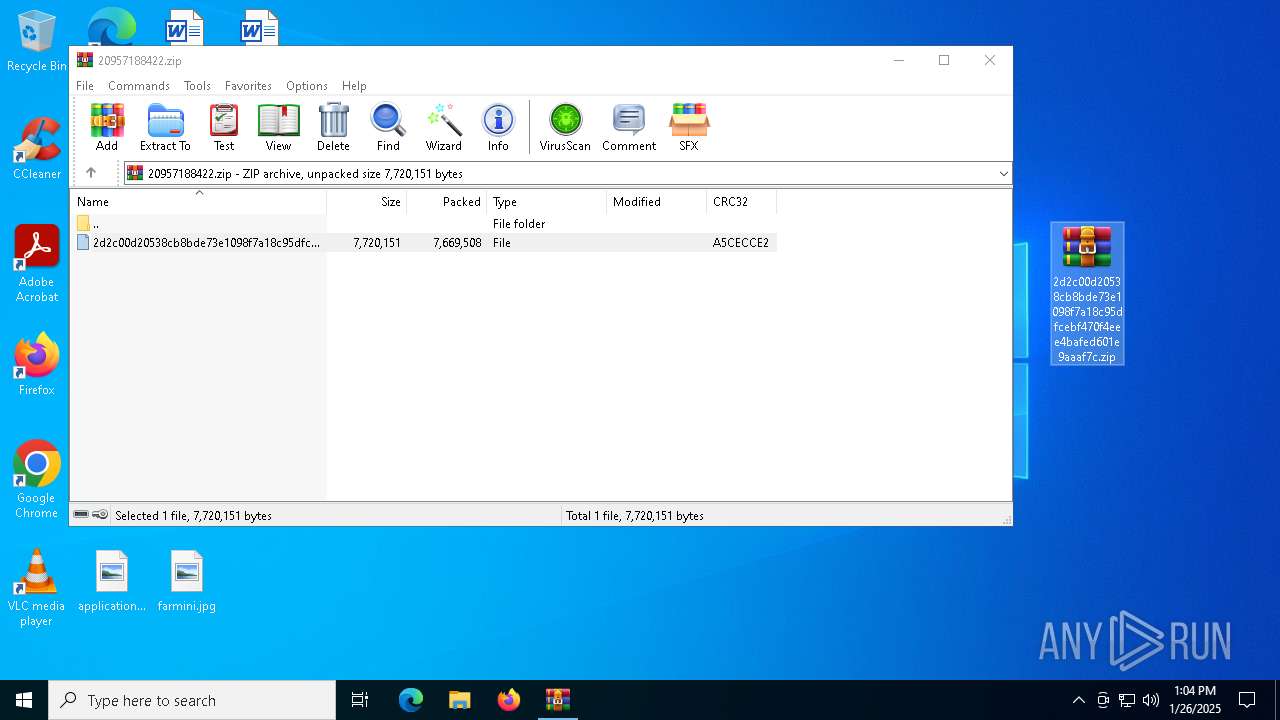
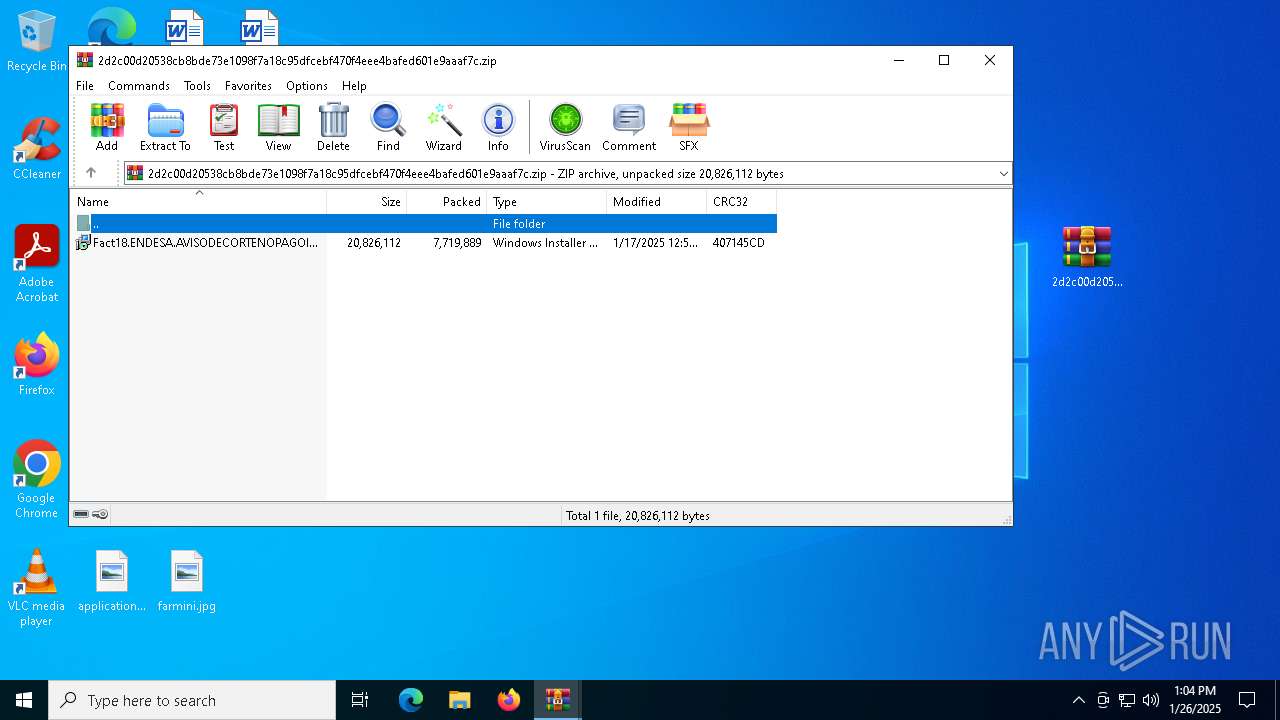
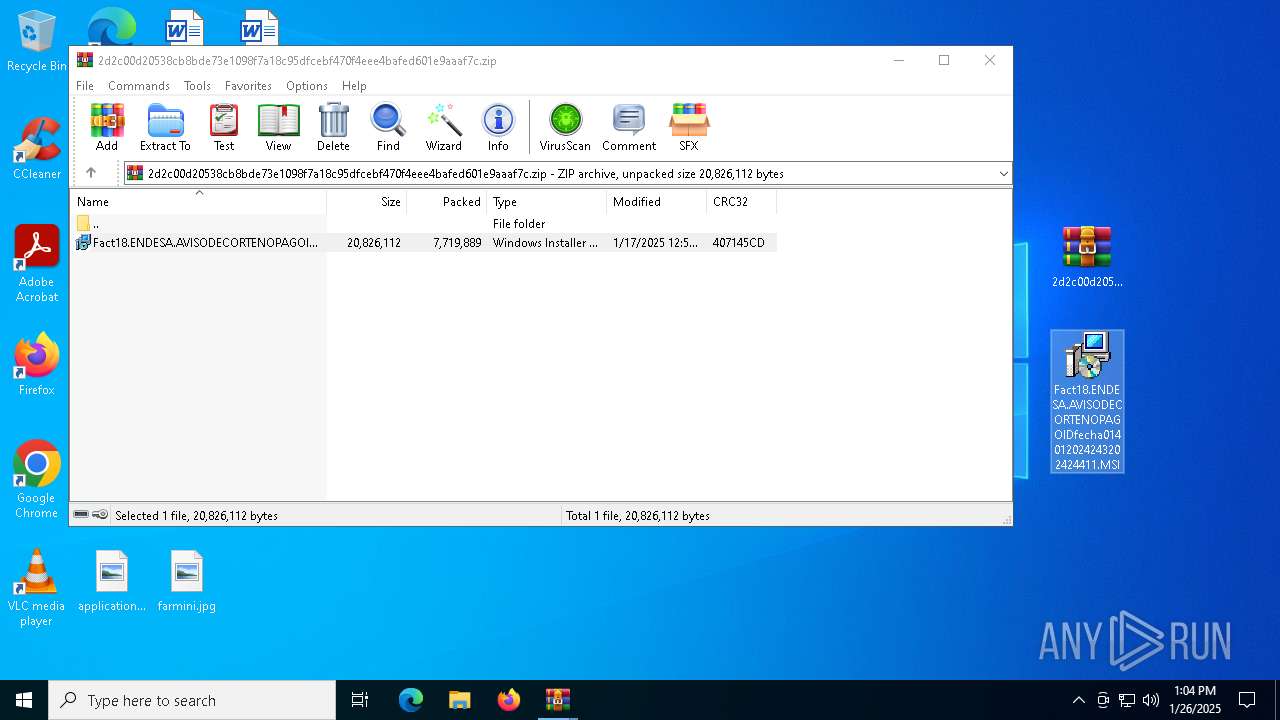
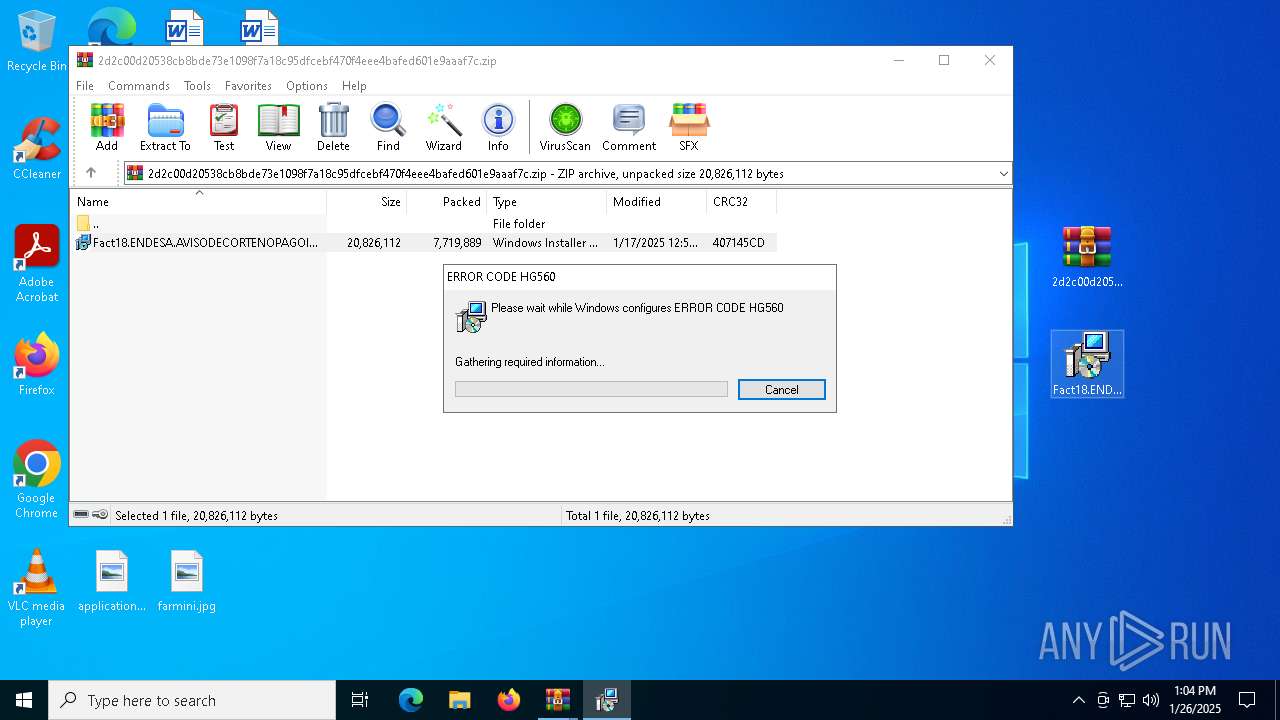
| File name: | 20957188422.zip |
| Full analysis: | https://app.any.run/tasks/82b93ec3-e9d5-4e4d-9e28-66613981c0b0 |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2025, 13:04:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5A5B5646233F2F29882455C833392C10 |
| SHA1: | 8A5D8C34A22121F76F4B2EC1151C58E33AD9844F |
| SHA256: | 42C2BCDF1AC2DB69094F0E936FFF6A91964B2F774F22FAE591AC72B74DB47AA9 |
| SSDEEP: | 98304:o/DKrB1LAgyBacCyD9sDz2ecTZKIhx8lUn+skONOwEYsC93pi2VdjnPWGYIhLtoQ:VCirFwi+grSKvQh2K359 |
MALICIOUS
Changes the autorun value in the registry
- PLUCSX.exe (PID: 6156)
Create files in the Startup directory
- PLUCSX.exe (PID: 6156)
Executing a file with an untrusted certificate
- PLUCSX.exe (PID: 6156)
SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1476)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5592)
Checks Windows Trust Settings
- msiexec.exe (PID: 5592)
There is functionality for taking screenshot (YARA)
- msiexec.exe (PID: 5592)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6864)
- msiexec.exe (PID: 1476)
- msiexec.exe (PID: 5592)
Reads the computer name
- msiexec.exe (PID: 1476)
- msiexec.exe (PID: 5592)
- PLUCSX.exe (PID: 6156)
Manual execution by a user
- msiexec.exe (PID: 6300)
- WinRAR.exe (PID: 6712)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1476)
- msiexec.exe (PID: 5592)
Checks supported languages
- msiexec.exe (PID: 5592)
- msiexec.exe (PID: 1476)
- PLUCSX.exe (PID: 6156)
Checks proxy server information
- msiexec.exe (PID: 5592)
Reads the software policy settings
- msiexec.exe (PID: 5592)
Creates files or folders in the user directory
- msiexec.exe (PID: 5592)
- PLUCSX.exe (PID: 6156)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5592)
Compiled with Borland Delphi (YARA)
- msiexec.exe (PID: 6300)
- msiexec.exe (PID: 5592)
- PLUCSX.exe (PID: 6156)
- msiexec.exe (PID: 1476)
Process checks computer location settings
- msiexec.exe (PID: 5592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xa5cecce2 |
| ZipCompressedSize: | 7669508 |
| ZipUncompressedSize: | 7720151 |
| ZipFileName: | 2d2c00d20538cb8bde73e1098f7a18c95dfcebf470f4eee4bafed601e9aaaf7c |
Total processes
133
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1476 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5592 | C:\Windows\syswow64\MsiExec.exe -Embedding D21F7547F179F0B4D01093C77942534F | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6156 | "C:\Newinvhens\PLUCSX.exe" | C:\Newinvhens\PLUCSX.exe | msiexec.exe | ||||||||||||
User: admin Company: Evernote Corp., 305 Walnut Street, Redwood City, CA 94063 Integrity Level: MEDIUM Description: Evernote Clipper Version: 4,6,2,7927 Modules
| |||||||||||||||
| 6300 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\Desktop\Fact18.ENDESA.AVISODECORTENOPAGOIDfecha014012024243202424411.MSI" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6712 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\2d2c00d20538cb8bde73e1098f7a18c95dfcebf470f4eee4bafed601e9aaaf7c.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6864 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\20957188422.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 880
Read events
5 839
Write events
32
Delete events
9
Modification events
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\20957188422.zip | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
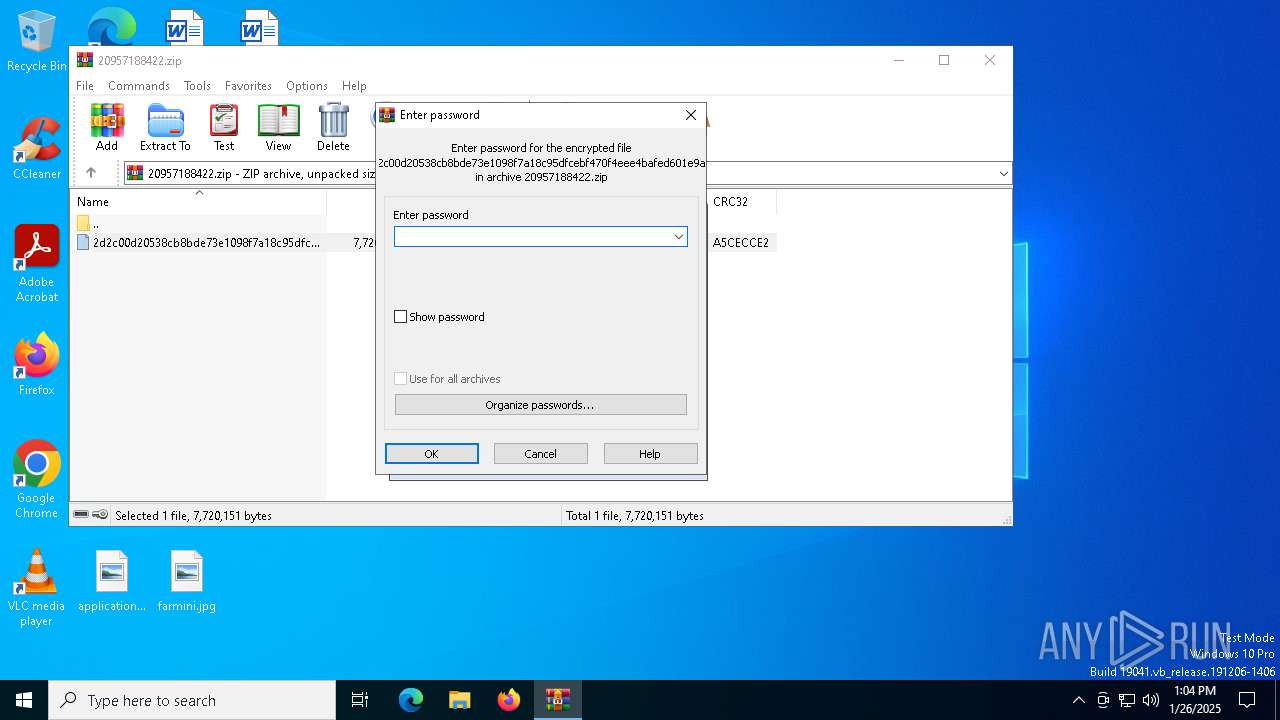
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6712) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
7
Suspicious files
23
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6712 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6712.49809\Fact18.ENDESA.AVISODECORTENOPAGOIDfecha014012024243202424411.MSI | — | |
MD5:— | SHA256:— | |||
| 1476 | msiexec.exe | C:\Windows\Installer\13d5f1.msi | — | |
MD5:— | SHA256:— | |||
| 5592 | msiexec.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\daveztotal[1].zip | — | |
MD5:— | SHA256:— | |||
| 5592 | msiexec.exe | C:\Newinvhens\admin | — | |
MD5:— | SHA256:— | |||
| 5592 | msiexec.exe | C:\Newinvhens\makosrc.dll | — | |
MD5:— | SHA256:— | |||
| 5592 | msiexec.exe | C:\Newinvhens\encrashrep.dll | — | |
MD5:— | SHA256:— | |||
| 6864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6864.47200\2d2c00d20538cb8bde73e1098f7a18c95dfcebf470f4eee4bafed601e9aaaf7c | compressed | |
MD5:BBF2C296C08FE4B7CD6A2F984ACA8CE0 | SHA256:2D2C00D20538CB8BDE73E1098F7A18C95DFCEBF470F4EEE4BAFED601E9AAAF7C | |||
| 1476 | msiexec.exe | C:\Windows\Temp\~DF19E82A597D280EFF.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 5592 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\35DDEDF268117918D1D277A171D8DF7B_AC6C8151D8AADA0589BAFF1410478088 | binary | |
MD5:7EF6BDC05163C9F2D1E81C84FE998F77 | SHA256:BC69788DC3D49ECE2EE11B6304525B8B644ABF441BA37EC091A83B4C99D7931E | |||
| 1476 | msiexec.exe | C:\Windows\Installer\MSID8E2.tmp | executable | |
MD5:55947B6781BACBD4A86219C62C10F4BB | SHA256:34F879C73B747366A14AB5769E536D560E2AA6760BED58827C203785BE0E442A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
33
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4308 | svchost.exe | GET | 200 | 23.48.23.140:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6568 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6636 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4308 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5592 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAfFsPuRVuQjKpGebeJZ9Vw%3D | unknown | — | — | whitelisted |
6636 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5592 | msiexec.exe | GET | 301 | 213.13.26.153:80 | http://cld.pt/dl/download/10402cd3-94e1-4392-88a7-60dcbe6d8d2a/daveztotal.zip?admin-English%20(United%20States) | unknown | — | — | whitelisted |
5592 | msiexec.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.140:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 23.48.23.140:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4308 | svchost.exe | 23.48.23.140:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4308 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.7:443 | — | Akamai International B.V. | DE | unknown |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Public Cloud Domain in DNS Lookup (cld .pt) |
5592 | msiexec.exe | Potentially Bad Traffic | ET INFO Observed Public Cloud Domain (cld .pt in TLS SNI) |