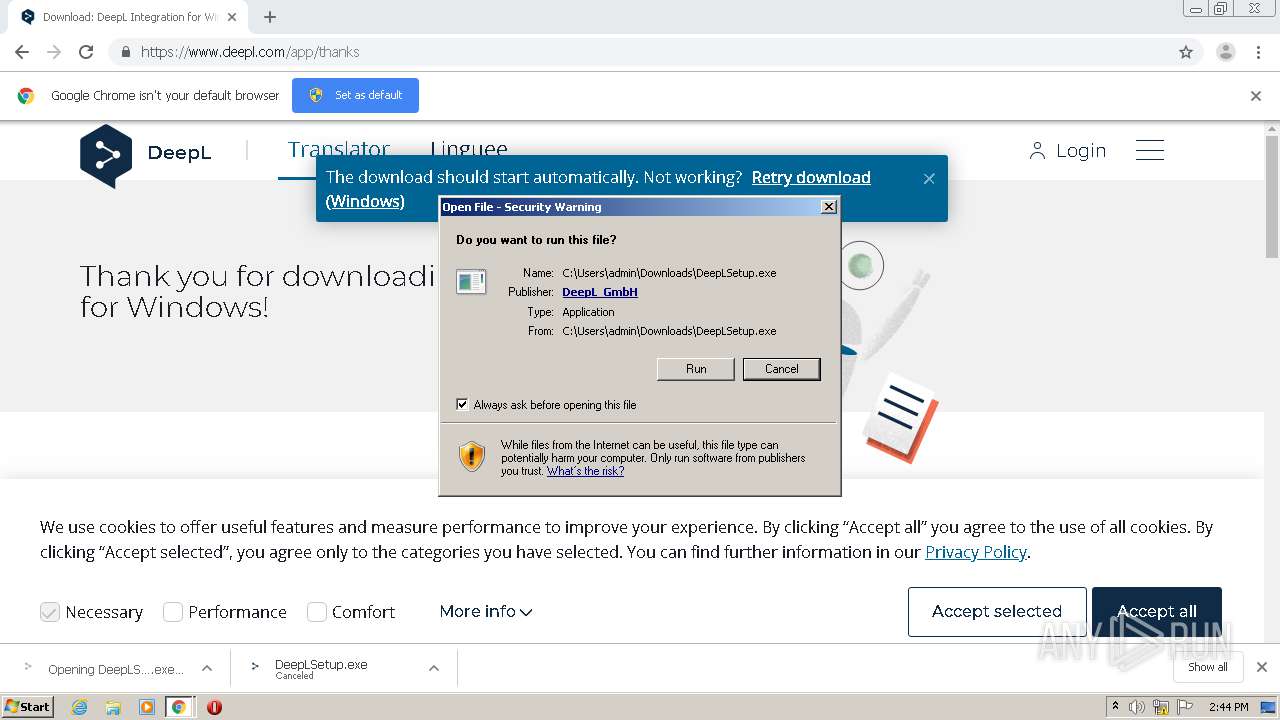
| URL: | https://www.deepl.com/translator |
| Full analysis: | https://app.any.run/tasks/a603fef8-fc40-4da6-9bc8-46b383bc36de |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2020, 13:40:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A0D2E0E8AD95434EE262BD09E90FFD9A |
| SHA1: | 3EFE49896F468008E2E9D38383B61D1A8C151CC4 |
| SHA256: | 429AF0DF17A5AFA5DB9EB71CE8638E1644C18F926F1B704C31779777A551A0CB |
| SSDEEP: | 3:N8DSLVJZ3RXELO4M:2OLjZ3CZM |
MALICIOUS
Application was dropped or rewritten from another process
- DeepLSetup.exe (PID: 1776)
- Update.exe (PID: 2736)
- DeepL.exe (PID: 496)
- DeepL.exe (PID: 2644)
- CefSharp.BrowserSubprocess.exe (PID: 2504)
- CefSharp.BrowserSubprocess.exe (PID: 2052)
- CefSharp.BrowserSubprocess.exe (PID: 3360)
- CefSharp.BrowserSubprocess.exe (PID: 2876)
Changes settings of System certificates
- DeepL.exe (PID: 496)
- DeepL.exe (PID: 2644)
Loads dropped or rewritten executable
- DeepL.exe (PID: 496)
- DeepL.exe (PID: 2644)
- CefSharp.BrowserSubprocess.exe (PID: 3360)
- CefSharp.BrowserSubprocess.exe (PID: 2876)
- CefSharp.BrowserSubprocess.exe (PID: 2052)
- CefSharp.BrowserSubprocess.exe (PID: 2504)
Changes the autorun value in the registry
- DeepL.exe (PID: 496)
SUSPICIOUS
Executable content was dropped or overwritten
- DeepLSetup.exe (PID: 1776)
- chrome.exe (PID: 2820)
- chrome.exe (PID: 2180)
- Update.exe (PID: 2736)
Reads Environment values
- DeepL.exe (PID: 496)
- DeepL.exe (PID: 2644)
Creates a software uninstall entry
- DeepL.exe (PID: 496)
- Update.exe (PID: 2736)
Adds / modifies Windows certificates
- DeepL.exe (PID: 496)
- DeepL.exe (PID: 2644)
Creates files in the program directory
- DeepL.exe (PID: 496)
- DeepL.exe (PID: 2644)
Creates files in the user directory
- DeepL.exe (PID: 496)
Searches for installed software
- Update.exe (PID: 2736)
INFO
Application launched itself
- chrome.exe (PID: 2820)
Reads settings of System Certificates
- chrome.exe (PID: 2180)
- chrome.exe (PID: 2820)
Reads the hosts file
- chrome.exe (PID: 2820)
- CefSharp.BrowserSubprocess.exe (PID: 2876)
- chrome.exe (PID: 2180)
- DeepL.exe (PID: 2644)
Reads Internet Cache Settings
- chrome.exe (PID: 2820)
Dropped object may contain Bitcoin addresses
- Update.exe (PID: 2736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
60
Monitored processes
20
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | "C:\Users\admin\AppData\Local\DeepL\app-1.12.2\DeepL.exe" --squirrel-install 1.12.2 | C:\Users\admin\AppData\Local\DeepL\app-1.12.2\DeepL.exe | Update.exe | ||||||||||||
User: admin Company: DeepL GmbH Integrity Level: MEDIUM Description: DeepL Exit code: 0 Version: 1.12.2 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1008,5807226762888257717,15424095242628835674,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=12010578128510912294 --mojo-platform-channel-handle=3948 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1776 | "C:\Users\admin\Downloads\DeepLSetup.exe" | C:\Users\admin\Downloads\DeepLSetup.exe | chrome.exe | ||||||||||||
User: admin Company: DeepL GmbH Integrity Level: MEDIUM Description: DeepL for Windows. Exit code: 0 Version: 1.12.2 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,5807226762888257717,15424095242628835674,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4490287910669378714 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2472 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2052 | "C:\Users\admin\AppData\Local\DeepL\app-1.12.2\x86\CefSharp.BrowserSubprocess.exe" --type=gpu-process --field-trial-handle=2392,3523843781818885888,4784639593754908598,131072 --disable-features=MimeHandlerViewInCrossProcessFrame --no-sandbox --log-file="C:\Users\admin\AppData\Local\DeepL\app-1.12.2\debug.log" --lang=en-US --cefsharpexitsub --gpu-preferences=KAAAAAAAAADgAAAwAAAAAAAAYAAAAAAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Users\admin\AppData\Local\DeepL\app-1.12.2\debug.log" --service-request-channel-token=6872465857066503984 --mojo-platform-channel-handle=2420 /prefetch:2 --host-process-id=2644 | C:\Users\admin\AppData\Local\DeepL\app-1.12.2\x86\CefSharp.BrowserSubprocess.exe | — | DeepL.exe | |||||||||||
User: admin Company: The CefSharp Authors Integrity Level: MEDIUM Description: CefSharp.BrowserSubprocess Exit code: 0 Version: 79.1.360.0 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,5807226762888257717,15424095242628835674,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=13937312914454058339 --mojo-platform-channel-handle=1564 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1008,5807226762888257717,15424095242628835674,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=10288072136259393804 --mojo-platform-channel-handle=1044 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2504 | "C:\Users\admin\AppData\Local\DeepL\app-1.12.2\x86\CefSharp.BrowserSubprocess.exe" --type=gpu-process --field-trial-handle=2392,3523843781818885888,4784639593754908598,131072 --disable-features=MimeHandlerViewInCrossProcessFrame --no-sandbox --log-file="C:\Users\admin\AppData\Local\DeepL\app-1.12.2\debug.log" --lang=en-US --cefsharpexitsub --gpu-preferences=KAAAAAAAAADgAAAwAAAAAAAAYAAAAAAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --log-file="C:\Users\admin\AppData\Local\DeepL\app-1.12.2\debug.log" --service-request-channel-token=2827049123625923105 --mojo-platform-channel-handle=2420 /prefetch:2 --host-process-id=2644 | C:\Users\admin\AppData\Local\DeepL\app-1.12.2\x86\CefSharp.BrowserSubprocess.exe | DeepL.exe | ||||||||||||
User: admin Company: The CefSharp Authors Integrity Level: MEDIUM Description: CefSharp.BrowserSubprocess Exit code: 4 Version: 79.1.360.0 Modules
| |||||||||||||||
| 2644 | "C:\Users\admin\AppData\Local\DeepL\app-1.12.2\DeepL.exe" --squirrel-firstrun | C:\Users\admin\AppData\Local\DeepL\app-1.12.2\DeepL.exe | Update.exe | ||||||||||||
User: admin Company: DeepL GmbH Integrity Level: MEDIUM Description: DeepL Exit code: 0 Version: 1.12.2 Modules
| |||||||||||||||
| 2736 | "C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe" --install . | C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe | DeepLSetup.exe | ||||||||||||
User: admin Company: GitHub Integrity Level: MEDIUM Description: Update Exit code: 0 Version: 1.9.1.0 Modules
| |||||||||||||||
Total events
2 345
Read events
2 147
Write events
189
Delete events
9
Modification events
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2860) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2820-13242922838920750 |
Value: 259 | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2820) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2832-13239195546717773 |
Value: 0 | |||
Executable files
291
Suspicious files
87
Text files
115
Unknown types
146
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF19113c.TMP | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\5a7e9e44-cb19-490f-bd03-b90962229d5b.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF19113c.TMP | text | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF191330.TMP | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
39
DNS requests
18
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2180 | chrome.exe | 104.18.11.234:443 | static.deepl.com | Cloudflare Inc | US | unknown |
2180 | chrome.exe | 216.58.206.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2180 | chrome.exe | 216.58.208.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
2180 | chrome.exe | 216.58.205.238:443 | clients1.google.com | Google Inc. | US | whitelisted |
2180 | chrome.exe | 62.138.14.29:443 | appdownload.deepl.com | Host Europe GmbH | DE | unknown |
2180 | chrome.exe | 172.217.22.4:443 | www.google.com | Google Inc. | US | whitelisted |
2180 | chrome.exe | 172.217.16.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2180 | chrome.exe | 216.58.205.234:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2180 | chrome.exe | 172.217.22.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2180 | chrome.exe | 172.217.16.142:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.deepl.com |
| suspicious |
accounts.google.com |
| shared |
static.deepl.com |
| suspicious |
s.deepl.com |
| suspicious |
clients1.google.com |
| whitelisted |
www.google.com |
| malicious |
appdownload.deepl.com |
| suspicious |
ssl.gstatic.com |
| whitelisted |
clients2.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
DeepL.exe | Native library pre-loader is trying to load native SQLite library "C:\Users\admin\AppData\Local\DeepL\app-1.12.2\x86\SQLite.Interop.dll"...
|
DeepL.exe | Native library pre-loader is trying to load native SQLite library "C:\Users\admin\AppData\Local\DeepL\app-1.12.2\x86\SQLite.Interop.dll"...
|
CefSharp.BrowserSubprocess.exe | [0826/144438.870:ERROR:gl_surface_egl.cc(1115)] eglInitialize D3D11 failed with error EGL_NOT_INITIALIZED, trying next display type
|
CefSharp.BrowserSubprocess.exe | [0826/144438.870:ERROR:gl_surface_egl.cc(668)] EGL Driver message (Critical) eglInitialize: No available renderers.
|
CefSharp.BrowserSubprocess.exe | [0826/144439.909:ERROR:gl_surface_egl.cc(1115)] eglInitialize D3D9 failed with error EGL_NOT_INITIALIZED
|
CefSharp.BrowserSubprocess.exe | [0826/144439.909:ERROR:gl_initializer_win.cc(196)] GLSurfaceEGL::InitializeOneOff failed.
|
CefSharp.BrowserSubprocess.exe | [0826/144439.909:ERROR:gl_surface_egl.cc(668)] EGL Driver message (Critical) eglInitialize: No available renderers.
|
CefSharp.BrowserSubprocess.exe | [0826/144439.927:ERROR:viz_main_impl.cc(180)] Exiting GPU process due to errors during initialization
|
DeepL.exe | [0826/144440.100:WARNING:gpu_process_host.cc(1213)] The GPU process has crashed 1 time(s)
|
DeepL.exe | [0826/144440.989:WARNING:gpu_process_host.cc(982)] Reinitialized the GPU process after a crash. The reported initialization time was 166 ms
|