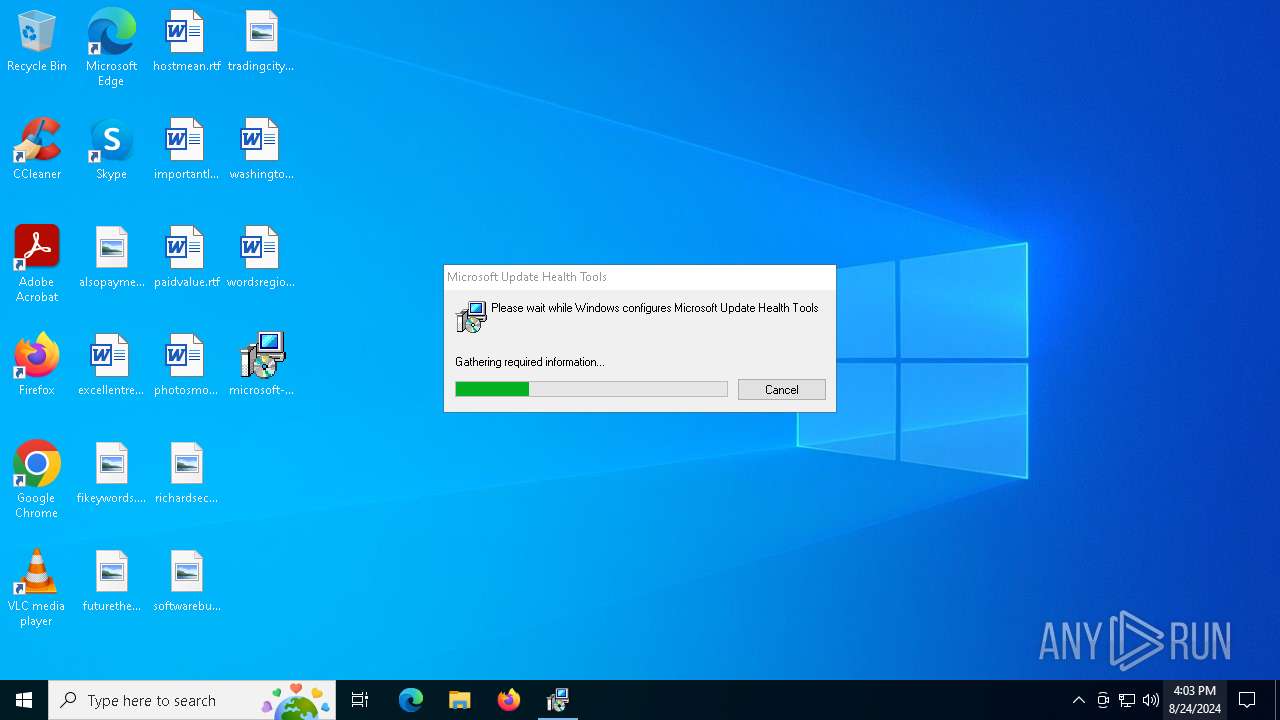
| File name: | microsoft-system-repair.msi |
| Full analysis: | https://app.any.run/tasks/0bd1bb36-e0a8-47cb-8904-23dc280f6299 |
| Verdict: | Malicious activity |
| Analysis date: | August 24, 2024, 16:01:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Microsoft Update Health Tools 5.72.0.0, Subject: Microsoft Update Health Tools, Author: Microsoft Corporation, Keywords: Installer, Template: Intel;1033, Revision Number: {8975BF53-0E19-4191-87AC-5834FC10BF5A}, Create Time/Date: Thu Jan 11 14:59:44 2024, Last Saved Time/Date: Thu Jan 11 14:59:44 2024, Number of Pages: 200, Number of Words: 2, Name of Creating Application: MSI Wrapper (11.0.53.0), Security: 2 |
| MD5: | 56130894F8BFB3A0F4B33CD2F9D765B4 |
| SHA1: | 26680EFEA5D365E27C3396CF19C8280D66160ED4 |
| SHA256: | 42449A23A43B96161F6360E53895CA8DC6487C2966AB579889FFA76B3223F75E |
| SSDEEP: | 6144:iQH4c67GiaM6YULcofB9SpB8PbmiJCAVGNL:XUGxJYULcorSDYmiJCAVIL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6668)
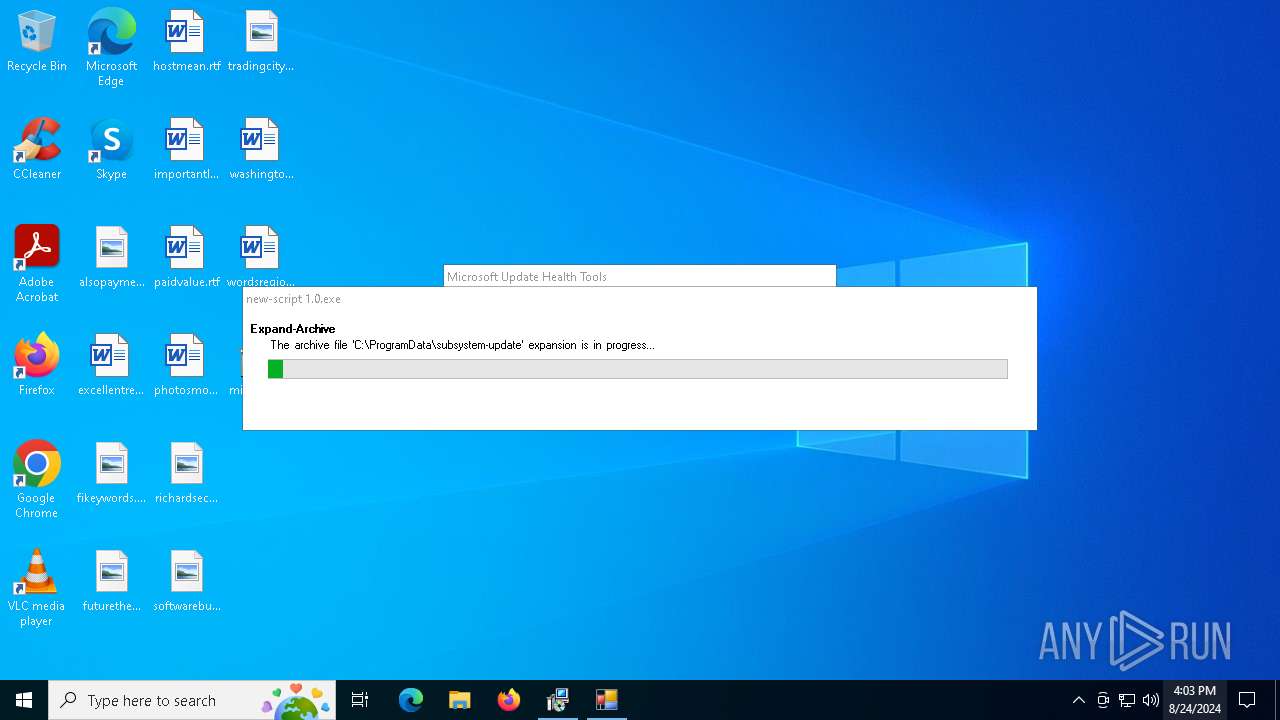
Drops the executable file immediately after the start
- msiexec.exe (PID: 6592)
- msiexec.exe (PID: 6668)
- expand.exe (PID: 6232)
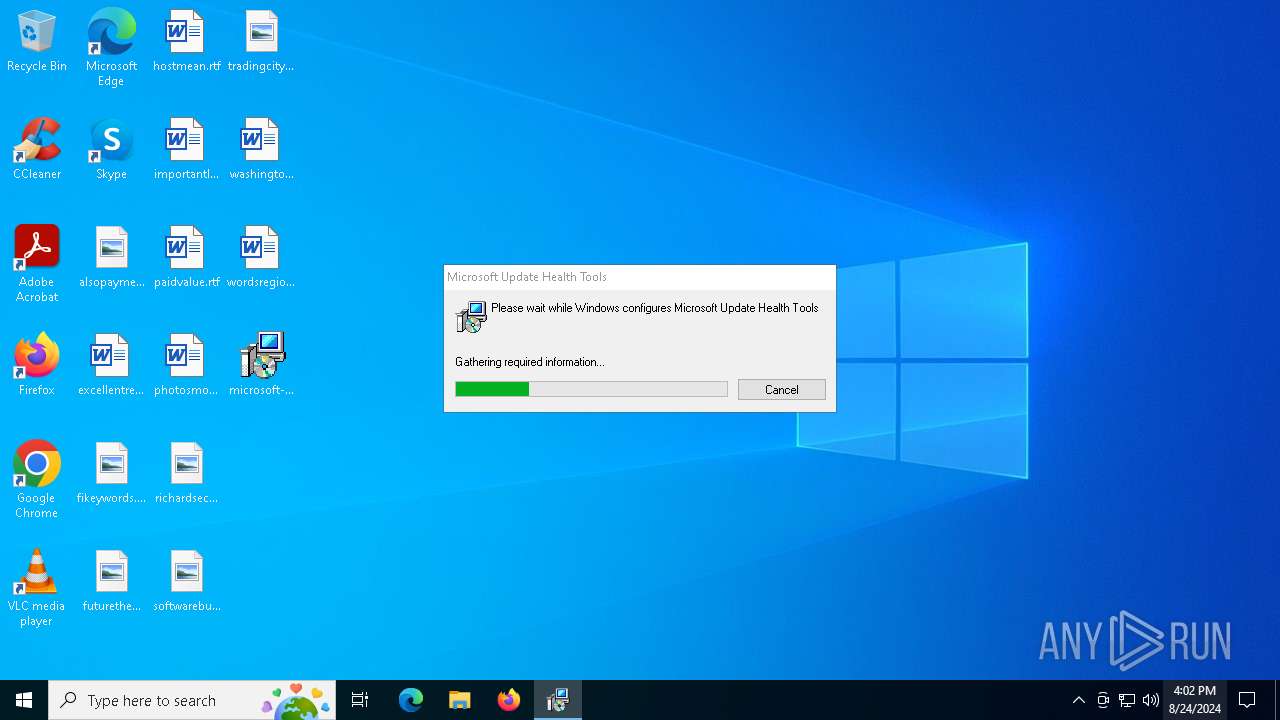
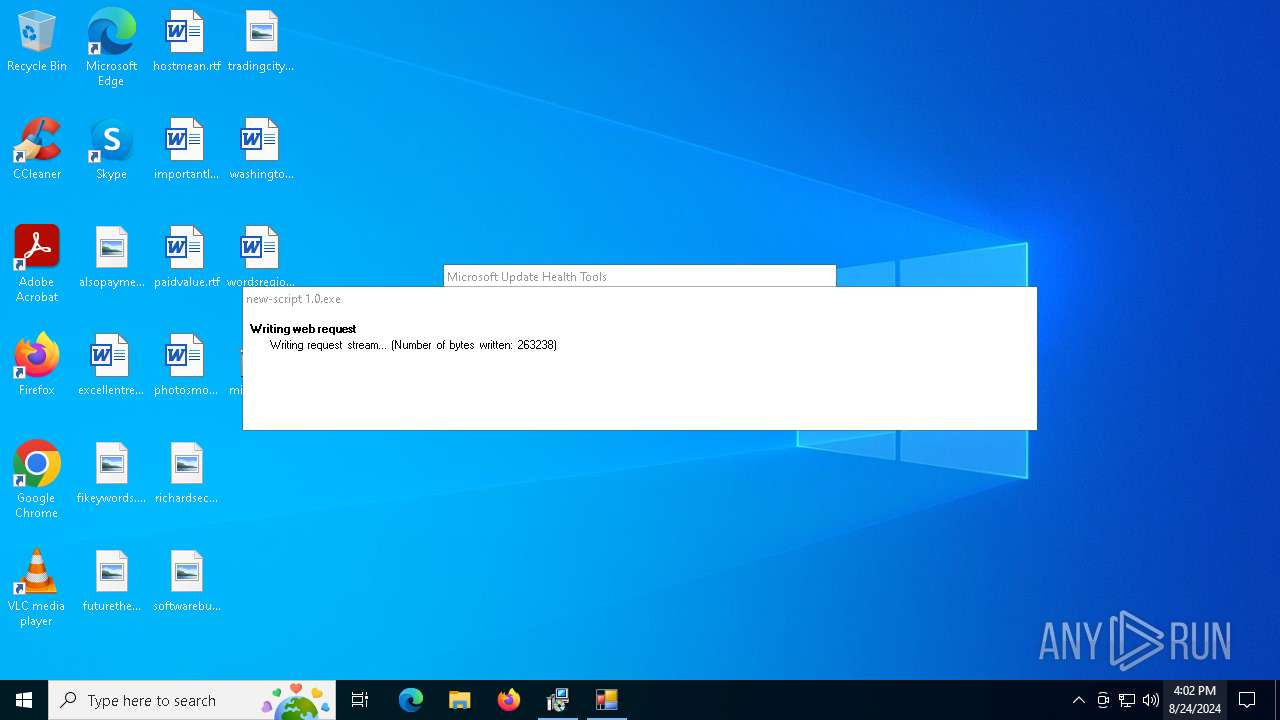
- new-script 1.0.exe (PID: 4128)
Executes as Windows Service
- VSSVC.exe (PID: 6716)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6224)
- new-script 1.0.exe (PID: 4128)
Reads the date of Windows installation
- msiexec.exe (PID: 6224)
Unpacks CAB file
- expand.exe (PID: 6232)
Executable content was dropped or overwritten
- expand.exe (PID: 6232)
- new-script 1.0.exe (PID: 4128)
Uses ATTRIB.EXE to modify file attributes
- new-script 1.0.exe (PID: 4128)
Gets file extension (POWERSHELL)
- new-script 1.0.exe (PID: 4128)
Checks Windows Trust Settings
- new-script 1.0.exe (PID: 4128)
Uses REG/REGEDIT.EXE to modify registry
- new-script 1.0.exe (PID: 4128)
Identifying current user with WHOAMI command
- new-script 1.0.exe (PID: 4128)
INFO
Reads the computer name
- msiexec.exe (PID: 6668)
- msiexec.exe (PID: 6224)
- new-script 1.0.exe (PID: 4128)
Checks supported languages
- msiexec.exe (PID: 6668)
- msiexec.exe (PID: 6224)
- expand.exe (PID: 6232)
- new-script 1.0.exe (PID: 4128)
- H.exe (PID: 2032)
- H.exe (PID: 2368)
- H.exe (PID: 2820)
Create files in a temporary directory
- msiexec.exe (PID: 6224)
- new-script 1.0.exe (PID: 4128)
- expand.exe (PID: 6232)
Reads the machine GUID from the registry
- new-script 1.0.exe (PID: 4128)
- msiexec.exe (PID: 6224)
- expand.exe (PID: 6232)
Process checks computer location settings
- msiexec.exe (PID: 6224)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6668)
Gets data length (POWERSHELL)
- new-script 1.0.exe (PID: 4128)
Creates files in the program directory
- new-script 1.0.exe (PID: 4128)
Checks proxy server information
- new-script 1.0.exe (PID: 4128)
Disables trace logs
- new-script 1.0.exe (PID: 4128)
Checks whether the specified file exists (POWERSHELL)
- new-script 1.0.exe (PID: 4128)
Reads Environment values
- new-script 1.0.exe (PID: 4128)
Reads the software policy settings
- new-script 1.0.exe (PID: 4128)
Checks if a key exists in the options dictionary (POWERSHELL)
- new-script 1.0.exe (PID: 4128)
Uses string replace method (POWERSHELL)
- new-script 1.0.exe (PID: 4128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
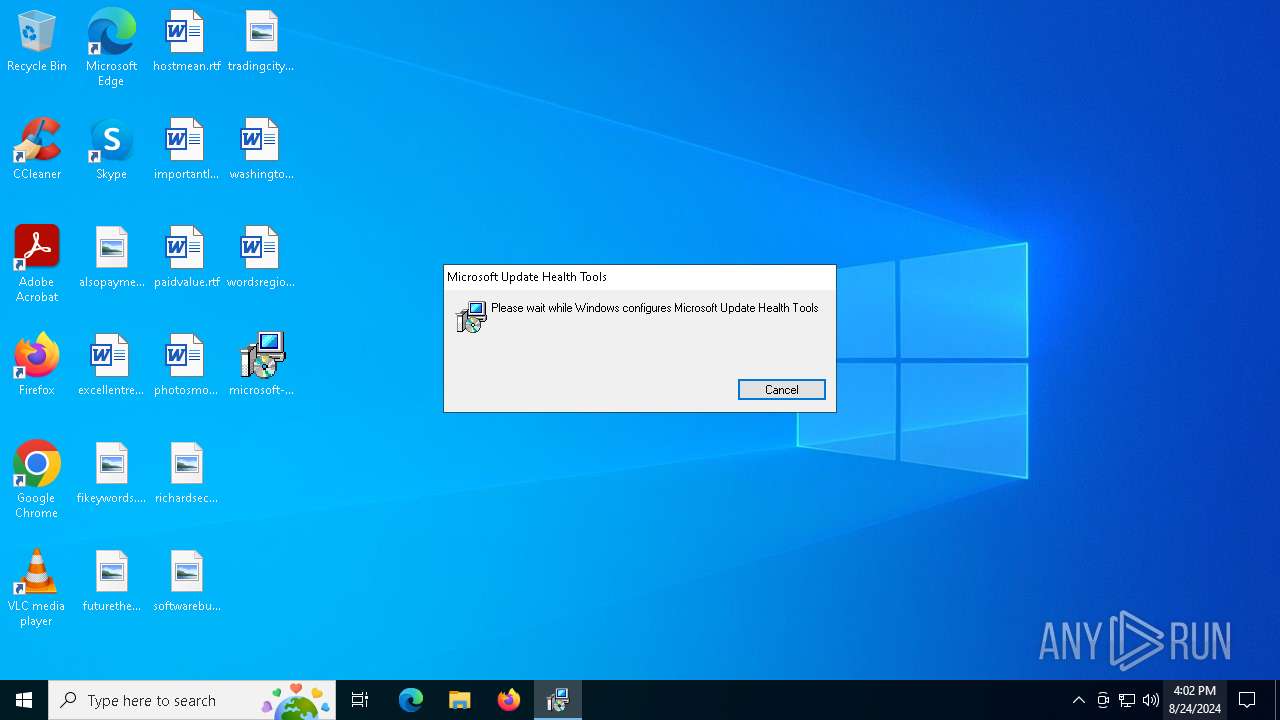
| Title: | Microsoft Update Health Tools 5.72.0.0 |
|---|---|
| Subject: | Microsoft Update Health Tools |
| Author: | Microsoft Corporation |
| Keywords: | Installer |
| Template: | Intel;1033 |
| RevisionNumber: | {8975BF53-0E19-4191-87AC-5834FC10BF5A} |
| CreateDate: | 2024:01:11 14:59:44 |
| ModifyDate: | 2024:01:11 14:59:44 |
| Pages: | 200 |
| Words: | 2 |
| Software: | MSI Wrapper (11.0.53.0) |
| Security: | Read-only recommended |
| CodePage: | Windows Latin 1 (Western European) |
| LocaleIndicator: | 1033 |
| Company: | Microsoft Corporation |
Total processes
147
Monitored processes
18
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1656 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | new-script 1.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2032 | "C:\ProgramData\subsystem-update\H.exe" -i C:\ProgramData\subsystem-update\2.zip -m decrypt -k C:\ProgramData\subsystem-update\k554gr | C:\ProgramData\subsystem-update\H.exe | — | new-script 1.0.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2368 | "C:\ProgramData\subsystem-update\H.exe" -i C:\ProgramData\subsystem-update\2.reg -m decrypt -k C:\ProgramData\subsystem-update\0m39js | C:\ProgramData\subsystem-update\H.exe | — | new-script 1.0.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2820 | "C:\ProgramData\subsystem-update\H.exe" -i C:\ProgramData\subsystem-update\220.exe -m decrypt -k C:\ProgramData\subsystem-update\9f722e | C:\ProgramData\subsystem-update\H.exe | — | new-script 1.0.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 4128 | "C:\Users\admin\AppData\Local\Temp\MW-867a893e-dba0-4796-9cae-1301ec4fbd62\files\new-script 1.0.exe" | C:\Users\admin\AppData\Local\Temp\MW-867a893e-dba0-4796-9cae-1301ec4fbd62\files\new-script 1.0.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 4392 | "C:\WINDOWS\system32\reg.exe" import C:\ProgramData\subsystem-update\2.reg | C:\Windows\System32\reg.exe | new-script 1.0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4944 | "C:\WINDOWS\system32\attrib.exe" +s +h C:\ProgramData\subsystem-update | C:\Windows\System32\attrib.exe | — | new-script 1.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5464 | "C:\WINDOWS\system32\whoami.exe" | C:\Windows\System32\whoami.exe | — | new-script 1.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6224 | C:\Windows\syswow64\MsiExec.exe -Embedding 3203869C9A5441FB471C089A397CAB4D | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 701
Read events
17 474
Write events
213
Delete events
14
Modification events
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000000401AEF63EF6DA010C1A00002C1A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000000401AEF63EF6DA010C1A00002C1A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000F9F167F73EF6DA010C1A00002C1A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000F9F167F73EF6DA010C1A00002C1A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000B8E586F73EF6DA010C1A00002C1A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000D6178EF73EF6DA010C1A00002C1A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000939EA2F83EF6DA010C1A00002C1A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6668) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000019D4A9F83EF6DA010C1A0000F01A0000E8030000010000000000000000000000969FB7D93F05464987720DB0911E84BE00000000000000000000000000000000 | |||
| (PID) Process: | (6716) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C610B8F83EF6DA013C1A0000881A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
6
Suspicious files
17
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6668 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4128 | new-script 1.0.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lgtfft5l.uri.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6668 | msiexec.exe | C:\Windows\Installer\MSI5E45.tmp | executable | |
MD5:0C8921BBCC37C6EFD34FAF44CF3B0CB5 | SHA256:FD622CF73EA951A6DE631063ABA856487D77745DD1500ADCA61902B8DDE56FE1 | |||
| 6668 | msiexec.exe | C:\Windows\Temp\~DFDC778AC4A11F88F9.TMP | binary | |
MD5:296063F426FC5A5EFEB81EC3F925C21B | SHA256:822332353CB4C2E8BFC582210C351C0F221B889EF8E33B03E6DC8A4863023429 | |||
| 4128 | new-script 1.0.exe | C:\ProgramData\subsystem-update\H.exe | executable | |
MD5:6690CED00D7CD246889A0E429AA21FF4 | SHA256:95E58C7C487542E258D39558C5F3A90A229A2971877A95B296CE07B2D956EB52 | |||
| 6668 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:93B8CEB5CB1727C0B33C71901609CD9A | SHA256:18AC41C9DEFFFDEA2A1E01EC90A0FDAD004F32B1CE002BFCCA5BE71A8BFEC5DF | |||
| 4128 | new-script 1.0.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:2AF279E73EBE24F3A6E689A595D21DA6 | SHA256:744A9C29CC187A660EF373FE35642BAC63B4CF8A94D301D90307F3FB0775D35F | |||
| 6668 | msiexec.exe | C:\Windows\Installer\MSI139D.tmp | executable | |
MD5:0C8921BBCC37C6EFD34FAF44CF3B0CB5 | SHA256:FD622CF73EA951A6DE631063ABA856487D77745DD1500ADCA61902B8DDE56FE1 | |||
| 4128 | new-script 1.0.exe | C:\ProgramData\subsystem-update\bnkqupmaadfdgzoko.zip | compressed | |
MD5:C2173046CE8C5CDE87F9AEA2B58FACB0 | SHA256:E7769EEFA4E44AF82E07AB8C9819DB86280C73BFA62F2D07462DE18EE64D11AC | |||
| 4128 | new-script 1.0.exe | C:\ProgramData\subsystem-update\2.zip | binary | |
MD5:3E1D66DF81CA8D0C2FBA305F9056D3C2 | SHA256:D14706C47115C68B7FE077551C7F985BAE06E0688035A5054E4C39AFC8F7E571 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
16
DNS requests
5
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4128 | new-script 1.0.exe | GET | 200 | 91.92.244.233:80 | http://subsystem.servehttp.com/mgauyenavzzejbjcji/bnkqupmaadfdgzoko.zip | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2580 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
872 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2580 | svchost.exe | 52.140.118.28:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IN | unknown |
2120 | MoUsoCoreWorker.exe | 52.140.118.28:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IN | unknown |
4324 | svchost.exe | 52.140.118.28:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IN | unknown |
2344 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4128 | new-script 1.0.exe | 91.92.244.233:80 | subsystem.servehttp.com | Natskovi & Sie Ltd. | BG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
subsystem.servehttp.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
4128 | new-script 1.0.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.servehttp .com Domain |
4128 | new-script 1.0.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
Process | Message |
|---|---|
reg.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|