| File name: | shfolder.bin |
| Full analysis: | https://app.any.run/tasks/37253963-c5c0-4a03-bb3f-33611912b711 |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2019, 17:23:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5: | 189FBCFEB349F505D04D7D8CCA6D4DAF |
| SHA1: | EC649DD098D067BEC6DD79670EEFC0AF9ECB4C0D |
| SHA256: | 4236F4D3626E61DC37D83CBD26597EE2CE1ADCBFDB36BF101435D0D3E134B4EA |
| SSDEEP: | 196608:LICliCxw+cBXnRIW6oveeGD/Y+0LAPpksOXckwTdxyhBdo:SC6Vnv+xPposkwxchD |
MALICIOUS
Loads dropped or rewritten executable
- WerFault.exe (PID: 3188)
SUSPICIOUS
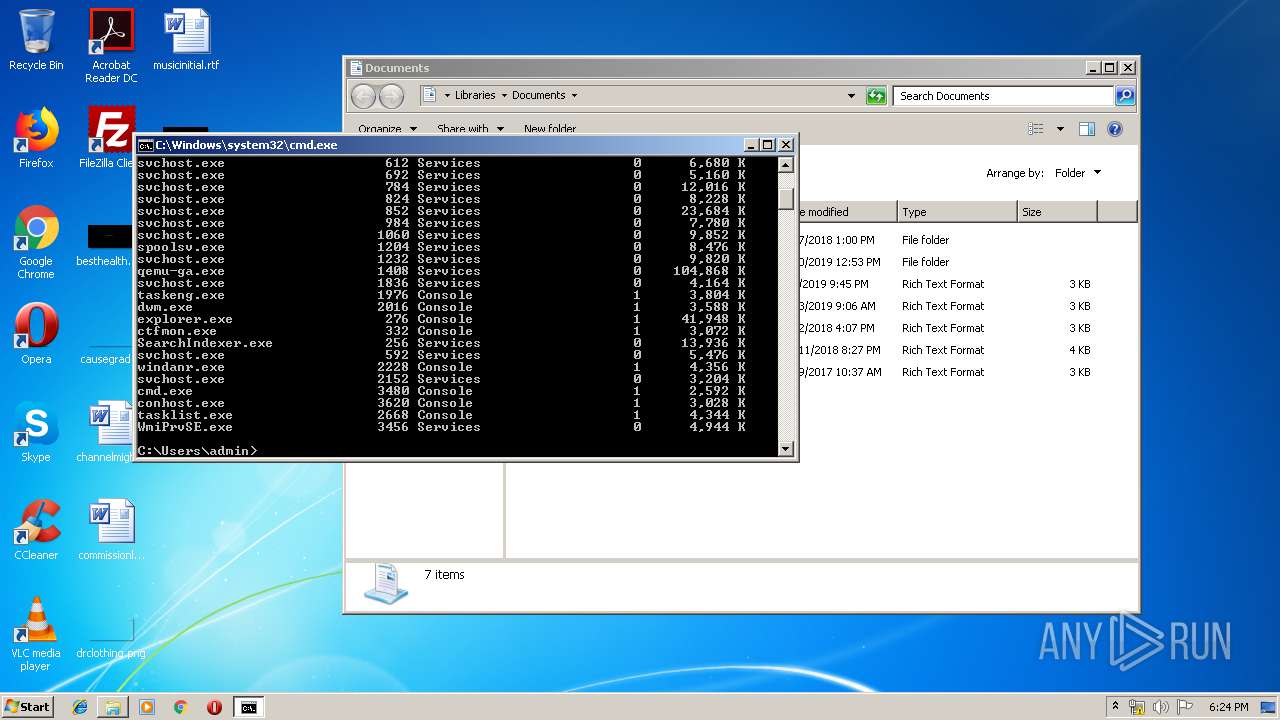
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 3480)
INFO
Loads main object executable
- rundll32.exe (PID: 3756)
Manual execution by user
- cmd.exe (PID: 3480)
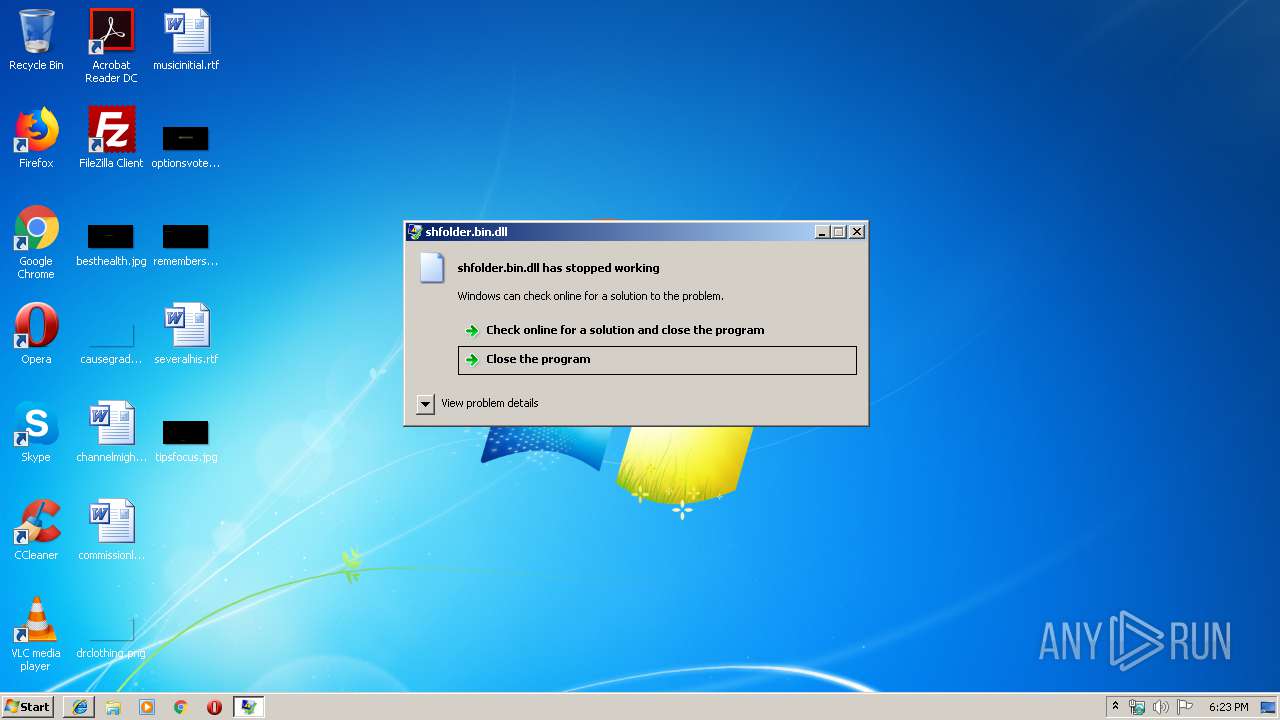
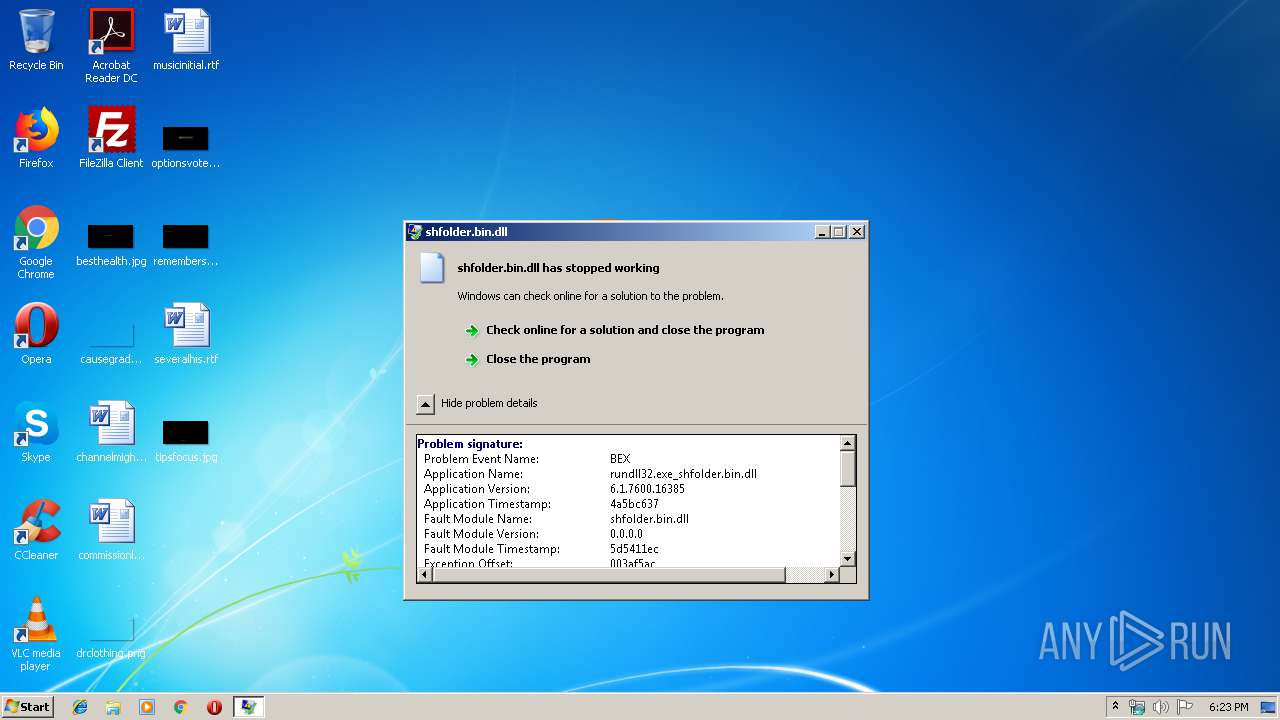
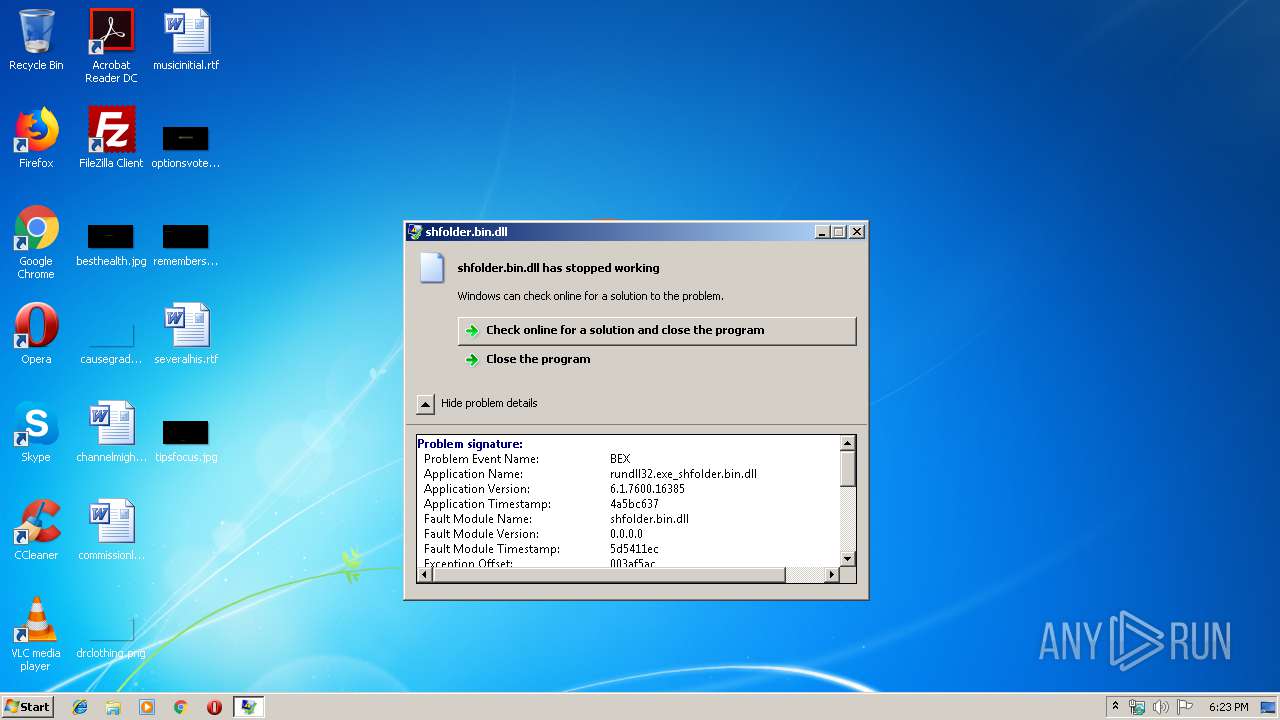
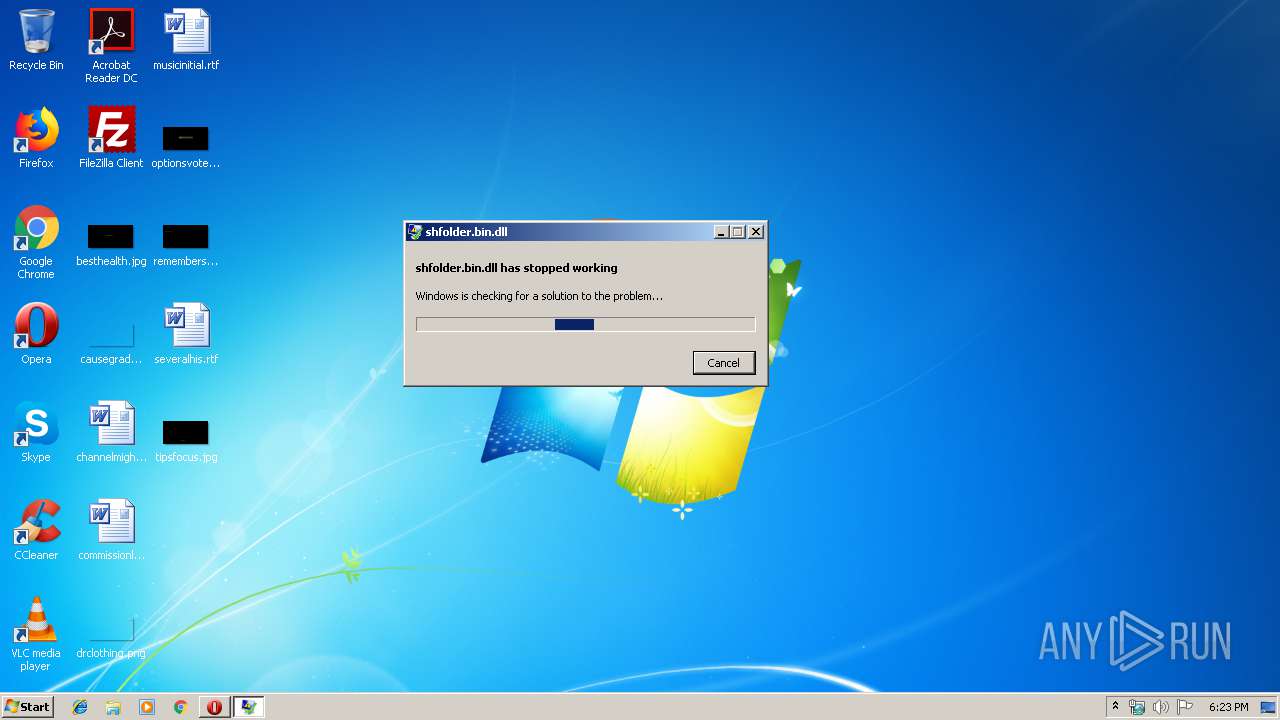
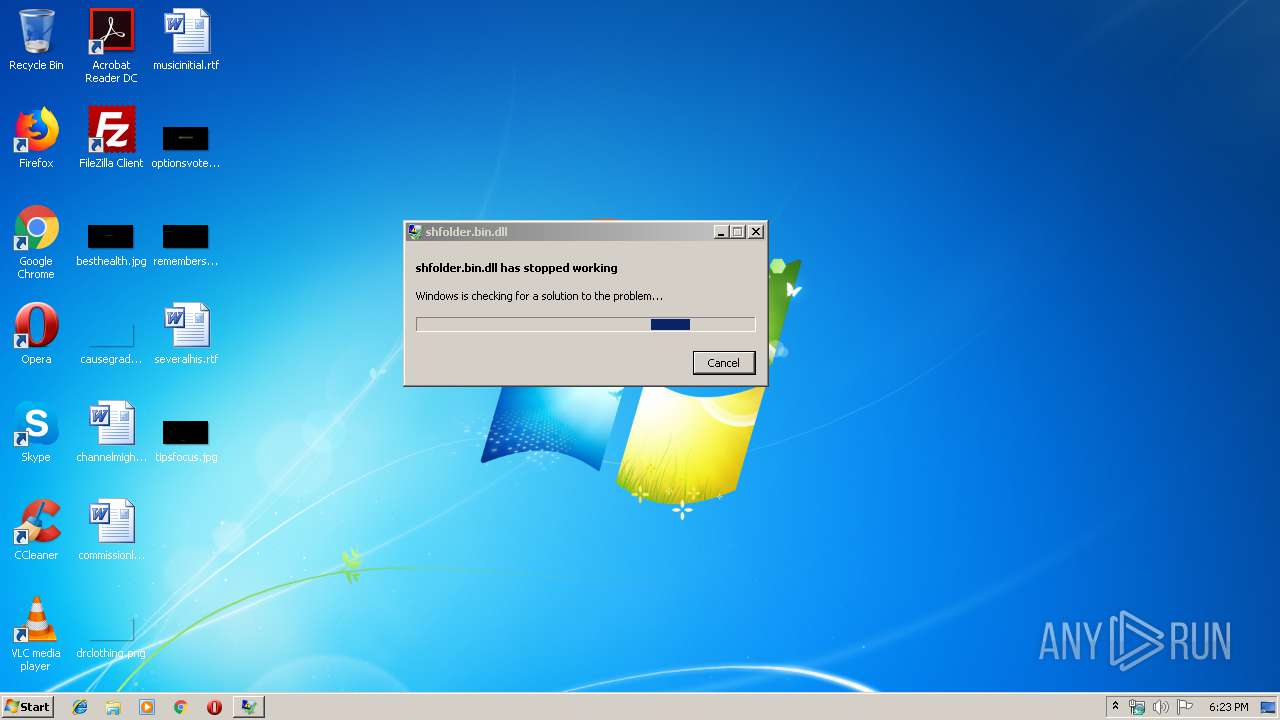
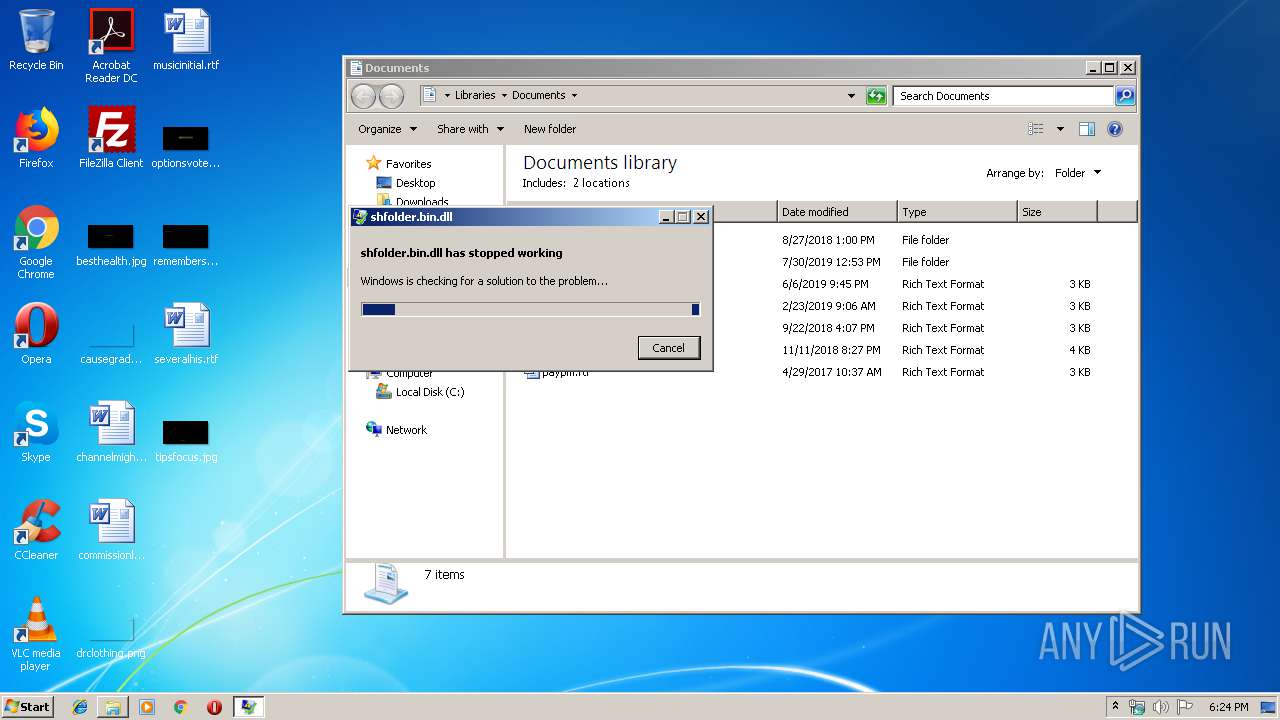
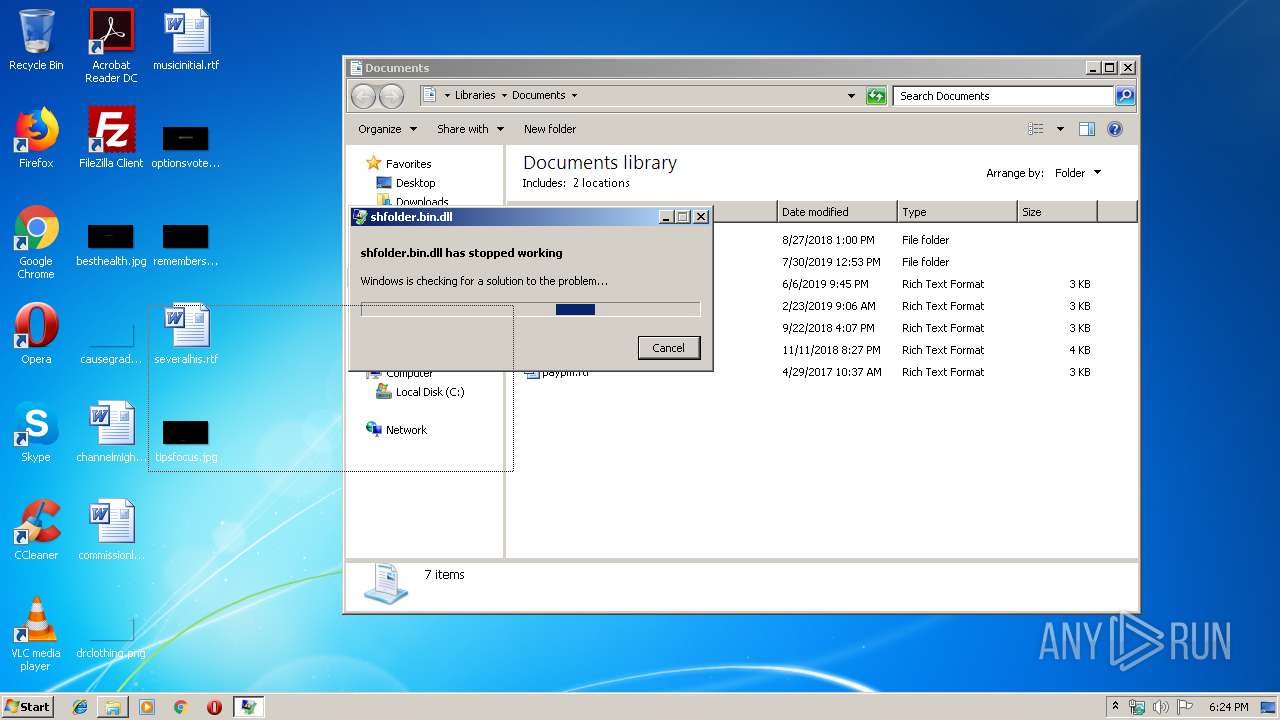
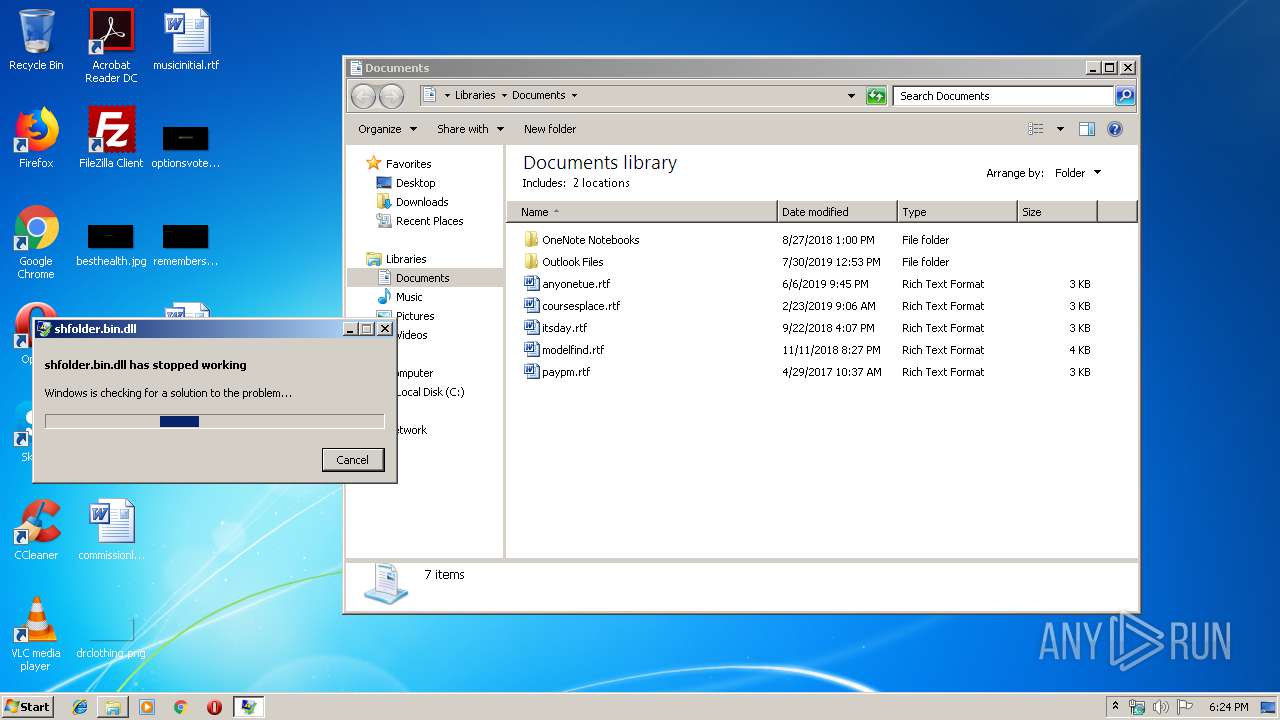
Application was crashed
- rundll32.exe (PID: 3756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:08:14 15:51:40+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 3757568 |
| InitializedDataSize: | 3643392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb0c033 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 14-Aug-2019 13:51:40 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 11 |
| Time date stamp: | 14-Aug-2019 13:51:40 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
5>@98=[hh,9 | 0x00001000 | 0x00392C68 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
SBy40?9m4' | 0x00394000 | 0x00002734 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
KY:"0ev_\xe4E\x01 | 0x00397000 | 0x000145E4 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
<xohdMPs\x8co | 0x003AC000 | 0x00006F8C | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
uhV4E`gF\x12G | 0x003B3000 | 0x00004712 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
sTNHb7!_\x08\x0c | 0x003B8000 | 0x00000C08 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
_7!]hi_^\xe2 | 0x003B9000 | 0x000000E2 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
x**FPRI;E | 0x003BA000 | 0x00000045 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
47n27PlN\xe4SV | 0x003BB000 | 0x005653E4 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
7mm'F\Q-\xf0\xbe\x84 | 0x00921000 | 0x0084BEF0 | 0x0084C000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.9715 |
Imports
WTSAPI32.dll |
advapi32.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
msvcrt.dll |
netapi32.dll |
ole32.dll |
oleaut32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 0x003AF5AC |
__dbk_fcall_wrapper | 2 | 0x00011F34 |
TMethodImplementationIntercept | 3 | 0x00067988 |
SHGetFolderPathW | 4 | 0x00389158 |
DGYOH0Z3T8B3FTB299Z4PKU6SA4 | 5 | 0x00389118 |
Total processes
40
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2668 | tasklist | C:\Windows\system32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3188 | C:\Windows\system32\WerFault.exe -u -p 3756 -s 244 | C:\Windows\system32\WerFault.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3480 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3756 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\AppData\Local\Temp\shfolder.bin.dll", dbkFCallWrapperAddr | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
40
Read events
40
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
1
Text files
5
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER6218.tmp.mdmp | — | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERE40B.tmp.WERInternalMetadata.xml | xml | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_rundll32.exe_shf_921b6b569f4127861d44e53c99d49ba29b551c72_cab_0c6362c1\WER610C.tmp.appcompat.txt | xml | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_rundll32.exe_shf_921b6b569f4127861d44e53c99d49ba29b551c72_cab_0c6362c1\WERE40B.tmp.WERInternalMetadata.xml | xml | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER614C.tmp.hdmp | dmp | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER610C.tmp.appcompat.txt | xml | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_rundll32.exe_shf_921b6b569f4127861d44e53c99d49ba29b551c72_cab_0c6362c1\WER614C.tmp.hdmp | dmp | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_rundll32.exe_shf_921b6b569f4127861d44e53c99d49ba29b551c72_cab_0c6362c1\Report.wer | binary | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_rundll32.exe_shf_921b6b569f4127861d44e53c99d49ba29b551c72_cab_0c6362c1\WER6218.tmp.mdmp | dmp | |
MD5:— | SHA256:— | |||
| 3188 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\rundll32.exe.3756.dmp | dmp | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3188 | WerFault.exe | GET | — | 52.158.209.219:80 | http://watson.microsoft.com/StageOne/Generic/BEX/rundll32_exe_shfolder_bin_dll/6_1_7600_16385/4a5bc637/shfolder_bin_dll/0_0_0_0/5d5411ec/003af5ac/c0000005/00000008.htm?LCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=DELL&SPN=DELL&BV=DELL&MID=3ADE2C42-4AB9-49B7-B142-BE9AEEA69063 | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3188 | WerFault.exe | 52.158.209.219:80 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3188 | WerFault.exe | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |
3188 | WerFault.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |