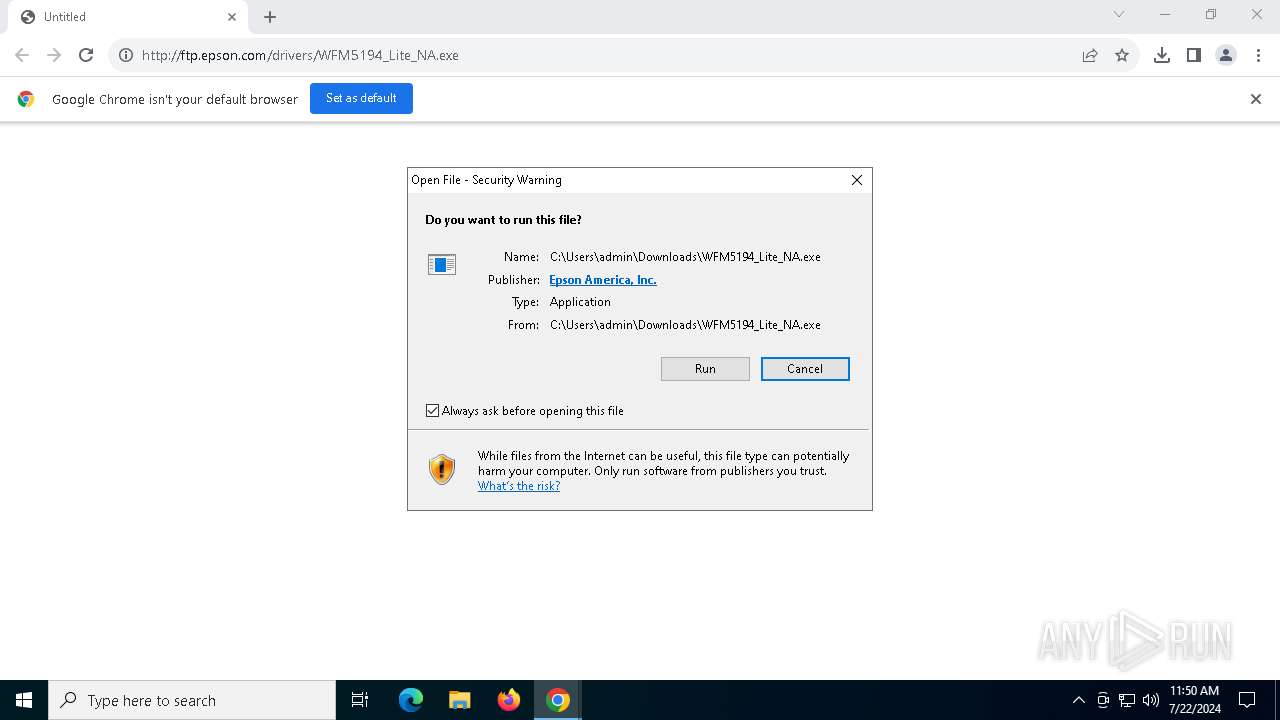
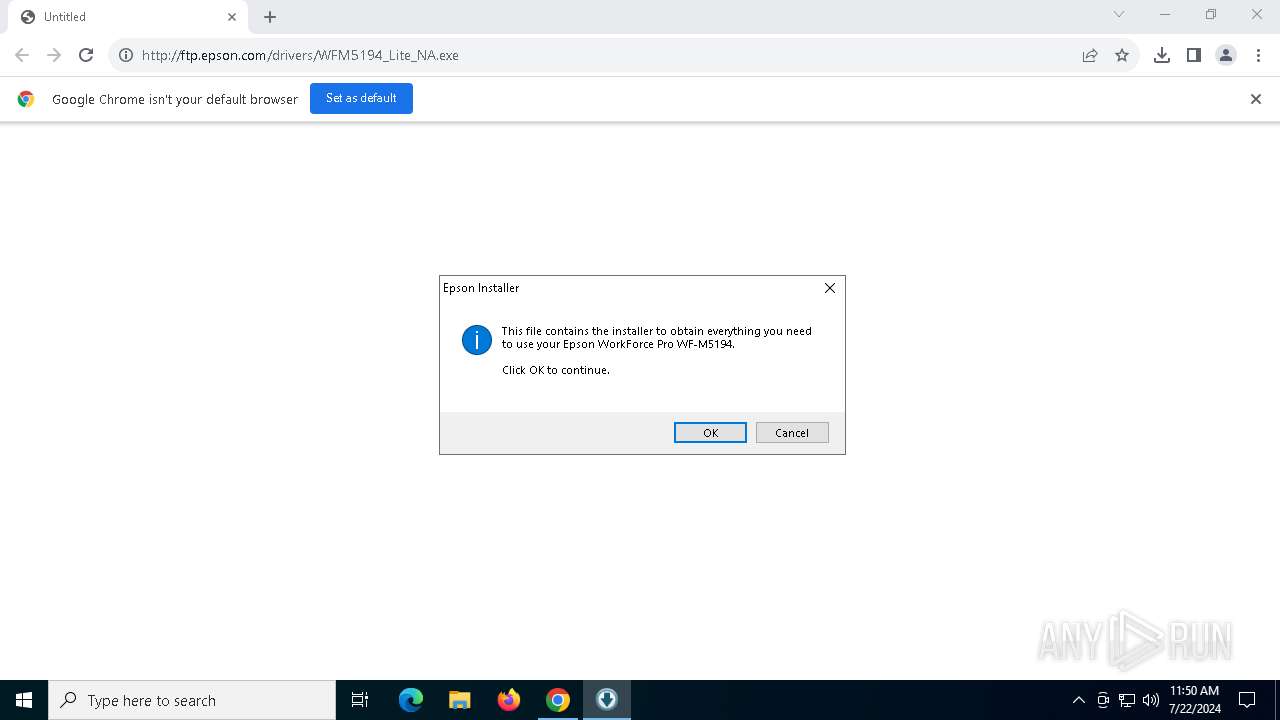
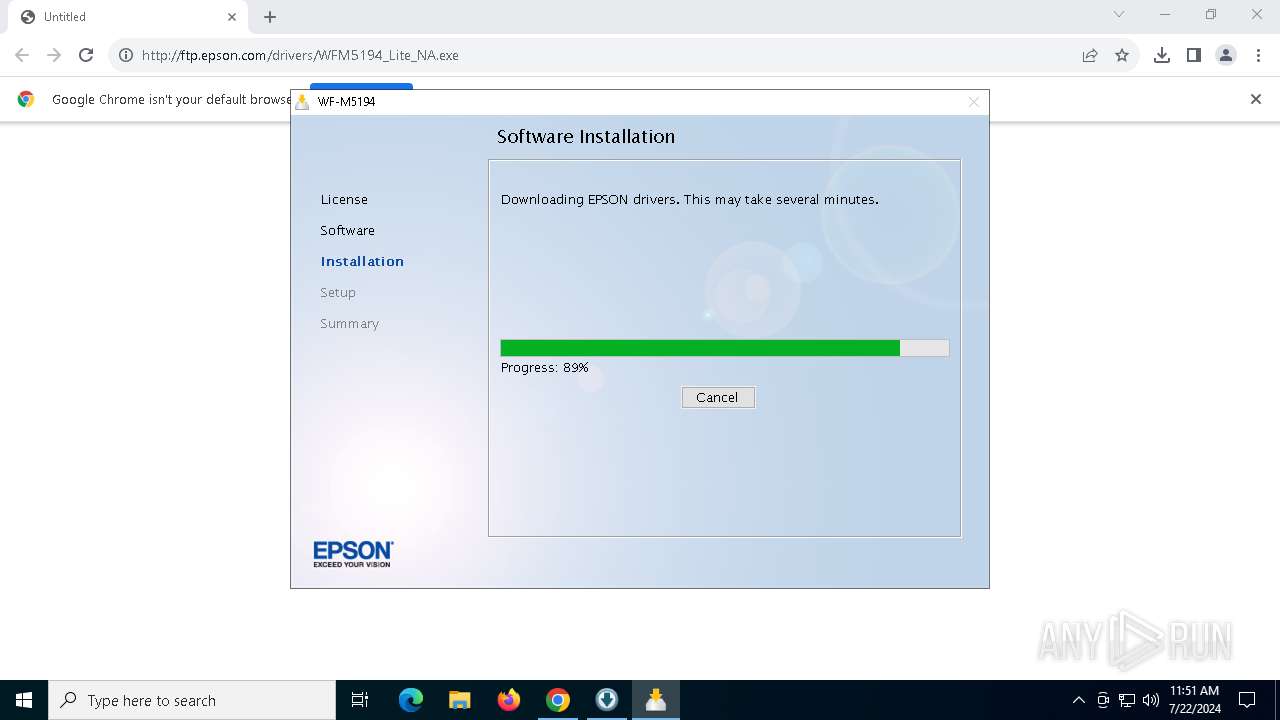
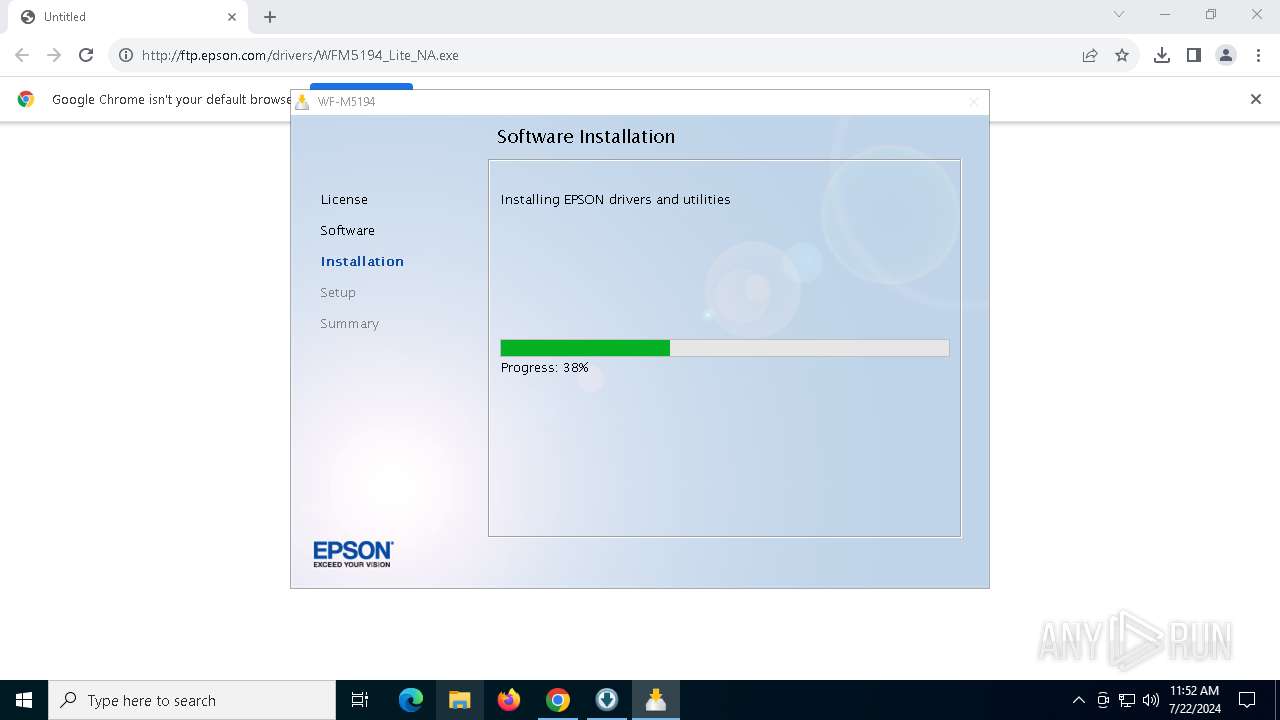
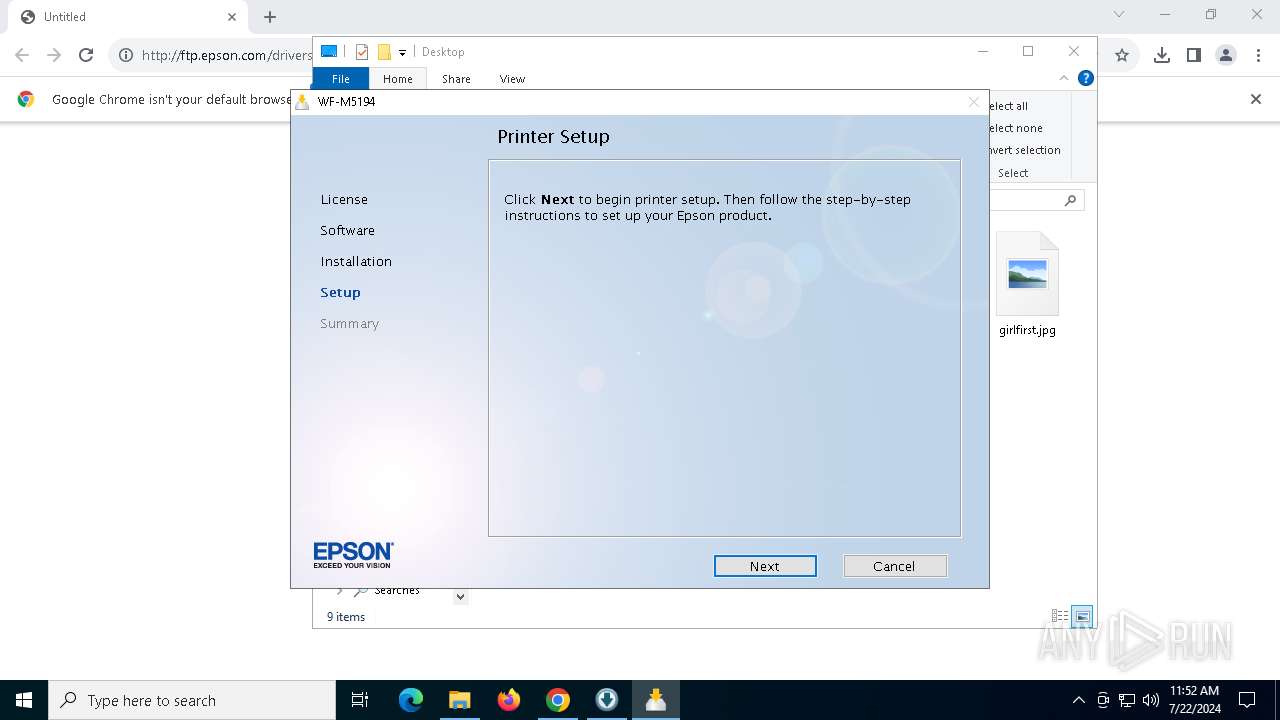
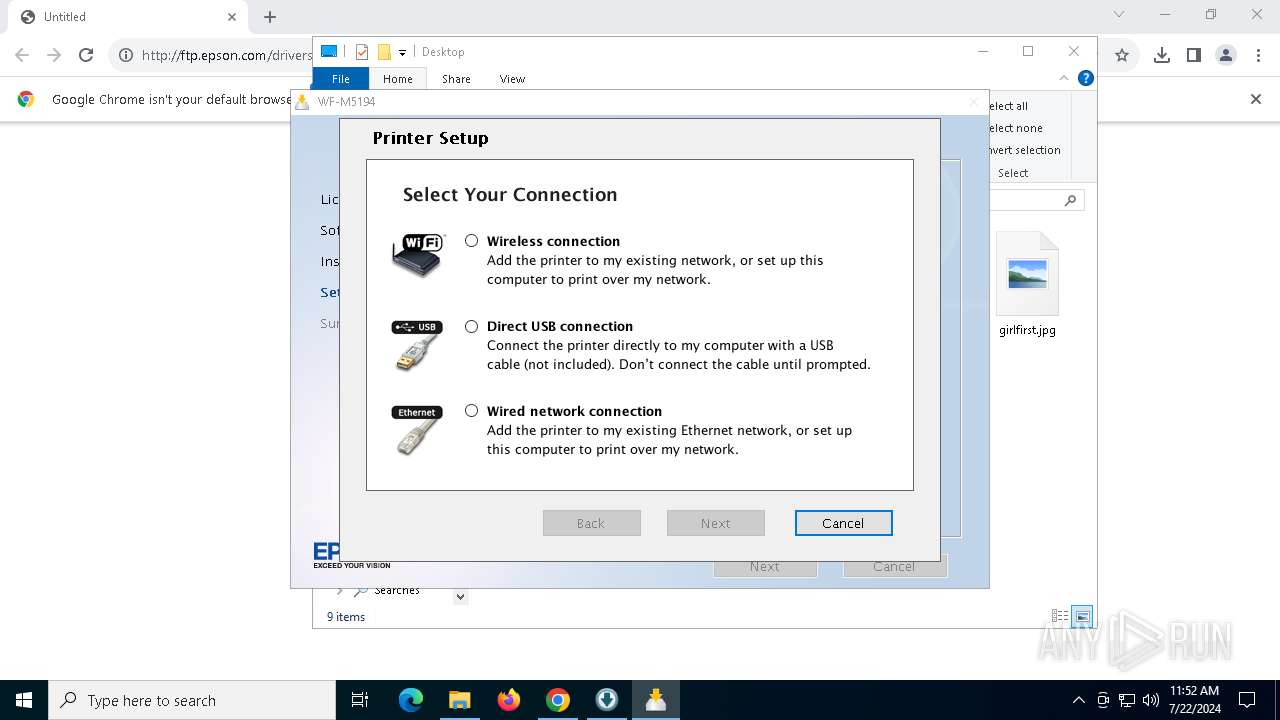
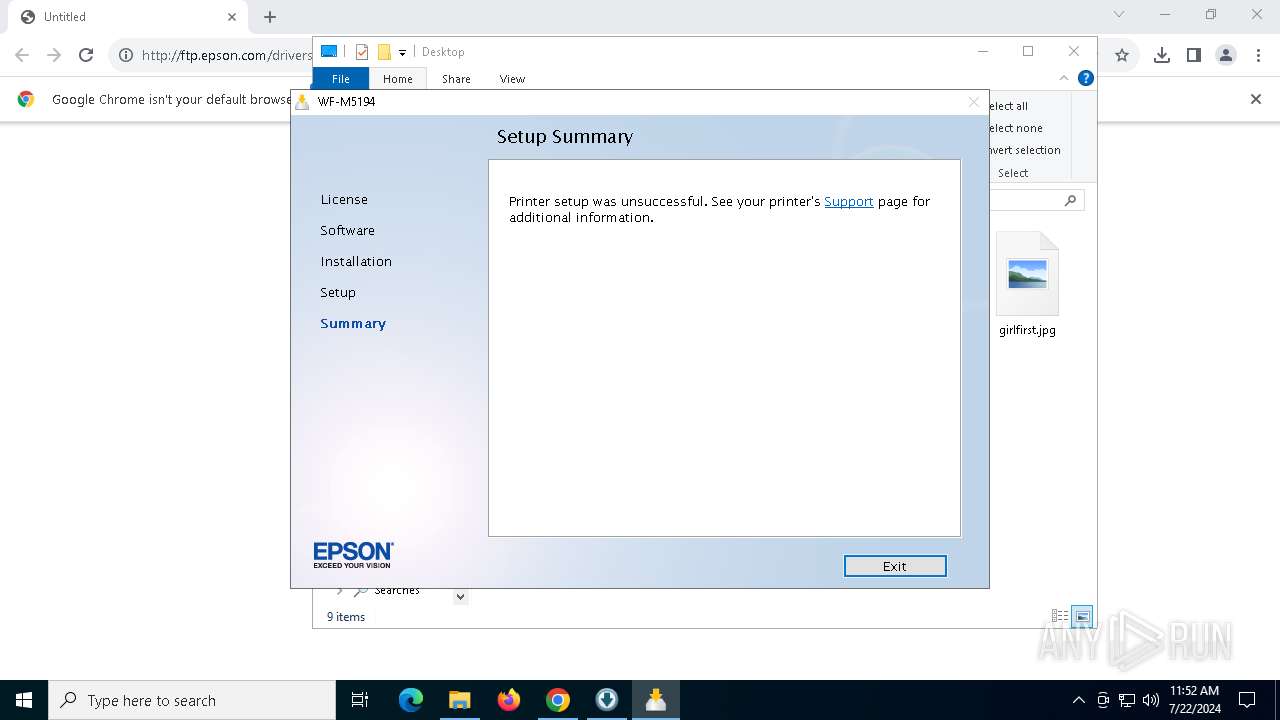
| URL: | ftp.epson.com/drivers/WFM5194_Lite_NA.exe |
| Full analysis: | https://app.any.run/tasks/a4ff181f-34b2-45d6-acf4-1125c44a1936 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2024, 11:50:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 847B933F81AB5163EC37CD53F7FDDFF5 |
| SHA1: | 0D90BABFFA453B5B10A1A070243D5510A6235E63 |
| SHA256: | 422DAEC5D74B56FF9FEC90964F3D9C8FB114634698F2A88379EA63B68104B049 |
| SSDEEP: | 3:Hs8aXsJUcHDCNn:M8EaD2n |
MALICIOUS
Drops the executable file immediately after the start
- WFM5194_Lite_NA.exe (PID: 6168)
- WFM5194_Lite_NA.exe (PID: 1596)
- WFM5194_Lite_NA.tmp (PID: 7072)
- Setup.exe (PID: 5320)
- drvinst.exe (PID: 2020)
- SETUP64.EXE (PID: 3128)
- msiexec.exe (PID: 7788)
- msiexec.exe (PID: 7600)
- setup.exe (PID: 7420)
- Setup.tmp (PID: 7164)
Scans artifacts that could help determine the target
- Setup.exe (PID: 5320)
Changes the autorun value in the registry
- msiexec.exe (PID: 7600)
SUSPICIOUS
Executable content was dropped or overwritten
- WFM5194_Lite_NA.exe (PID: 6168)
- WFM5194_Lite_NA.exe (PID: 1596)
- WFM5194_Lite_NA.tmp (PID: 7072)
- Setup.exe (PID: 5320)
- SETUP64.EXE (PID: 3128)
- drvinst.exe (PID: 2020)
- setup.exe (PID: 7420)
- Setup.tmp (PID: 7164)
Reads security settings of Internet Explorer
- WFM5194_Lite_NA.tmp (PID: 6992)
- Setup.exe (PID: 5320)
- SETUP64.EXE (PID: 3128)
- ENP.exe (PID: 2356)
- Setup.exe (PID: 5528)
- Setup.exe (PID: 2472)
- msiexec.exe (PID: 6864)
Reads the date of Windows installation
- WFM5194_Lite_NA.tmp (PID: 6992)
- Setup.exe (PID: 5320)
- ENP.exe (PID: 2356)
- Setup.exe (PID: 5528)
- Setup.exe (PID: 2472)
Reads the Windows owner or organization settings
- WFM5194_Lite_NA.tmp (PID: 7072)
- msiexec.exe (PID: 7788)
- Setup.tmp (PID: 7164)
Process drops legitimate windows executable
- WFM5194_Lite_NA.tmp (PID: 7072)
- Setup.exe (PID: 5320)
- SETUP64.EXE (PID: 3128)
- drvinst.exe (PID: 2020)
- msiexec.exe (PID: 7788)
- Setup.tmp (PID: 7164)
Checks Windows Trust Settings
- Setup.exe (PID: 5320)
- SETUP64.EXE (PID: 3128)
- drvinst.exe (PID: 2020)
- msiexec.exe (PID: 7788)
The process drops C-runtime libraries
- Setup.exe (PID: 5320)
- msiexec.exe (PID: 7788)
Creates files in the driver directory
- drvinst.exe (PID: 2020)
Sets XML DOM element text (SCRIPT)
- msiexec.exe (PID: 6864)
Executes as Windows Service
- EPCP.exe (PID: 5252)
Starts CMD.EXE for commands execution
- WFM5194_Lite_NA.tmp (PID: 7072)
INFO
Application launched itself
- chrome.exe (PID: 1668)
- msiexec.exe (PID: 7788)
Create files in a temporary directory
- WFM5194_Lite_NA.exe (PID: 6168)
- WFM5194_Lite_NA.exe (PID: 1596)
- WFM5194_Lite_NA.tmp (PID: 7072)
- Setup.exe (PID: 5320)
- SETUP64.EXE (PID: 3128)
- msiexec.exe (PID: 6864)
- setup.exe (PID: 7420)
- Setup.tmp (PID: 7164)
Checks supported languages
- WFM5194_Lite_NA.exe (PID: 6168)
- WFM5194_Lite_NA.tmp (PID: 6992)
- WFM5194_Lite_NA.exe (PID: 1596)
- WFM5194_Lite_NA.tmp (PID: 7072)
- Setup.exe (PID: 5320)
- Splash.exe (PID: 3544)
- SETUP64.EXE (PID: 3128)
- drvinst.exe (PID: 2020)
- ENP.exe (PID: 2356)
- msiexec.exe (PID: 4428)
- msiexec.exe (PID: 7788)
- msiexec.exe (PID: 7500)
- Setup.exe (PID: 5528)
- msiexec.exe (PID: 7600)
- Setup.exe (PID: 2472)
- msiexec.exe (PID: 6864)
- EPCP.exe (PID: 7612)
- msiexec.exe (PID: 5940)
- setup.exe (PID: 7420)
- EPCP.exe (PID: 5252)
- Setup.tmp (PID: 7164)
- EPAUDFLG.exe (PID: 7956)
Reads Microsoft Office registry keys
- chrome.exe (PID: 1668)
The process uses the downloaded file
- chrome.exe (PID: 1668)
- chrome.exe (PID: 6344)
Reads the computer name
- WFM5194_Lite_NA.tmp (PID: 6992)
- WFM5194_Lite_NA.tmp (PID: 7072)
- Setup.exe (PID: 5320)
- Splash.exe (PID: 3544)
- SETUP64.EXE (PID: 3128)
- drvinst.exe (PID: 2020)
- ENP.exe (PID: 2356)
- msiexec.exe (PID: 7788)
- msiexec.exe (PID: 4428)
- msiexec.exe (PID: 7500)
- Setup.exe (PID: 5528)
- msiexec.exe (PID: 7600)
- Setup.exe (PID: 2472)
- msiexec.exe (PID: 6864)
- EPCP.exe (PID: 7612)
- msiexec.exe (PID: 5940)
- EPCP.exe (PID: 5252)
- Setup.tmp (PID: 7164)
Process checks computer location settings
- WFM5194_Lite_NA.tmp (PID: 6992)
- Setup.exe (PID: 5320)
- ENP.exe (PID: 2356)
- Setup.exe (PID: 5528)
- Setup.exe (PID: 2472)
- msiexec.exe (PID: 6864)
Executable content was dropped or overwritten
- chrome.exe (PID: 1668)
- msiexec.exe (PID: 7788)
- msiexec.exe (PID: 7600)
Drops the executable file immediately after the start
- chrome.exe (PID: 1668)
Checks proxy server information
- Setup.exe (PID: 5320)
Reads the machine GUID from the registry
- Setup.exe (PID: 5320)
- SETUP64.EXE (PID: 3128)
- drvinst.exe (PID: 2020)
- msiexec.exe (PID: 7788)
Reads the software policy settings
- Setup.exe (PID: 5320)
- SETUP64.EXE (PID: 3128)
- drvinst.exe (PID: 2020)
- msiexec.exe (PID: 7788)
Creates files or folders in the user directory
- Setup.exe (PID: 5320)
Reads product name
- SETUP64.EXE (PID: 3128)
Creates files in the program directory
- SETUP64.EXE (PID: 3128)
- Setup.tmp (PID: 7164)
Reads Environment values
- SETUP64.EXE (PID: 3128)
- msiexec.exe (PID: 6864)
Creates a software uninstall entry
- msiexec.exe (PID: 7788)
- Setup.tmp (PID: 7164)
Creates or modifies Windows services
- msiexec.exe (PID: 5940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
205
Monitored processes
53
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | "C:\WINDOWS\system32\cmd.exe" /C rd /S /Q "C:\Users\admin\AppData\Local\Temp\WF-M5194" | C:\Windows\SysWOW64\cmd.exe | — | WFM5194_Lite_NA.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4768 --field-trial-handle=1848,i,5684948883003884783,11810056789566533461,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6084 --field-trial-handle=1848,i,5684948883003884783,11810056789566533461,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1596 | "C:\Users\admin\Downloads\WFM5194_Lite_NA.exe" /SPAWNWND=$402EA /NOTIFYWND=$702B0 | C:\Users\admin\Downloads\WFM5194_Lite_NA.exe | WFM5194_Lite_NA.tmp | ||||||||||||
User: admin Company: Epson America, Inc. Integrity Level: HIGH Description: EPSON Driver Package Setup Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 1668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "ftp.epson.com/drivers/WFM5194_Lite_NA.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2020 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{d25b21c5-8772-5f43-bab1-e74c5708d69e}\E_WF1MLE.INF" "9" "4cb17c8e7" "00000000000001C8" "WinSta0\Default" "00000000000001EC" "208" "C:\Users\admin\AppData\Local\Temp\EPSON WF-M5190 Series\Driver\Printer\Driver\WINX64\SETUP\WINX64" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2252 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2224 --field-trial-handle=1848,i,5684948883003884783,11810056789566533461,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\AppData\Local\Temp\EPSON WF-M5190 Series\Network\EpsonNetPrint\English\Data\ENP.exe" /s | C:\Users\admin\AppData\Local\Temp\EPSON WF-M5190 Series\Network\EpsonNetPrint\English\Data\ENP.exe | — | Setup.exe | |||||||||||
User: admin Company: SEIKO EPSON CORPORATION Integrity Level: HIGH Description: EpsonNet Print Exit code: 0 Version: 3.1.4.1 Modules
| |||||||||||||||
| 2472 | "C:\Users\admin\AppData\Local\Temp\EPSON WF-M5190 Series\Usage Panel EAI\Setup.exe" DEVICEID="WF-M5190 Series" | C:\Users\admin\AppData\Local\Temp\EPSON WF-M5190 Series\Usage Panel EAI\Setup.exe | — | Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Epson Customer Research Participation Installer Launcher Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 2788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5972 --field-trial-handle=1848,i,5684948883003884783,11810056789566533461,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
49 904
Read events
49 329
Write events
536
Delete events
39
Modification events
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
379
Suspicious files
474
Text files
868
Unknown types
70
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF429a4b.TMP | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF429a4b.TMP | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\USERS\ADMIN\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\LAST VERSION | text | |
MD5:FCE53E052E5CF7C20819320F374DEA88 | SHA256:CD95DE277E746E92CC2C53D9FC92A8F6F0C3EDFB7F1AD9A4E9259F927065BC89 | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old | text | |
MD5:668BAE5C0A00EF466FA52102A122346C | SHA256:A366BA8B2FD21BB25B17C6AC8A2C07428AEE94E6EA8CB14E204E4F77F61E2D40 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
64
DNS requests
39
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5320 | Setup.exe | GET | 200 | 184.30.20.97:80 | http://download.ebz.epson.net/dsc/f/01/00/02/11/00/43abdddddaf3ca7223aa0d65324a4dfe3d4c713f/UsagePanelInfo.txt?LGW=0x409&CNW=0xF4&OSV=WIN64_10.0&EXE=Setup&VER=00000014 | unknown | — | — | whitelisted |
3400 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
3400 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
3400 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
5320 | Setup.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
5320 | Setup.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
5320 | Setup.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAeGBCzjlivnamPf%2BeFAd20%3D | unknown | — | — | whitelisted |
5320 | Setup.exe | GET | 200 | 152.199.19.74:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEFR7ce3b%2Bg1jbKL5GvJmUl4%3D | unknown | — | — | whitelisted |
1668 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://s1.symcb.com/pca3-g5.crl | unknown | — | — | whitelisted |
1668 | chrome.exe | GET | 200 | 152.199.19.74:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4716 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7856 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1668 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7144 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | unknown |
7144 | chrome.exe | 45.60.47.158:443 | ftp.epson.com | INCAPSULA | US | unknown |
7144 | chrome.exe | 45.60.47.158:80 | ftp.epson.com | INCAPSULA | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ftp.epson.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
s2.symcb.com |
| whitelisted |
s1.symcb.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |