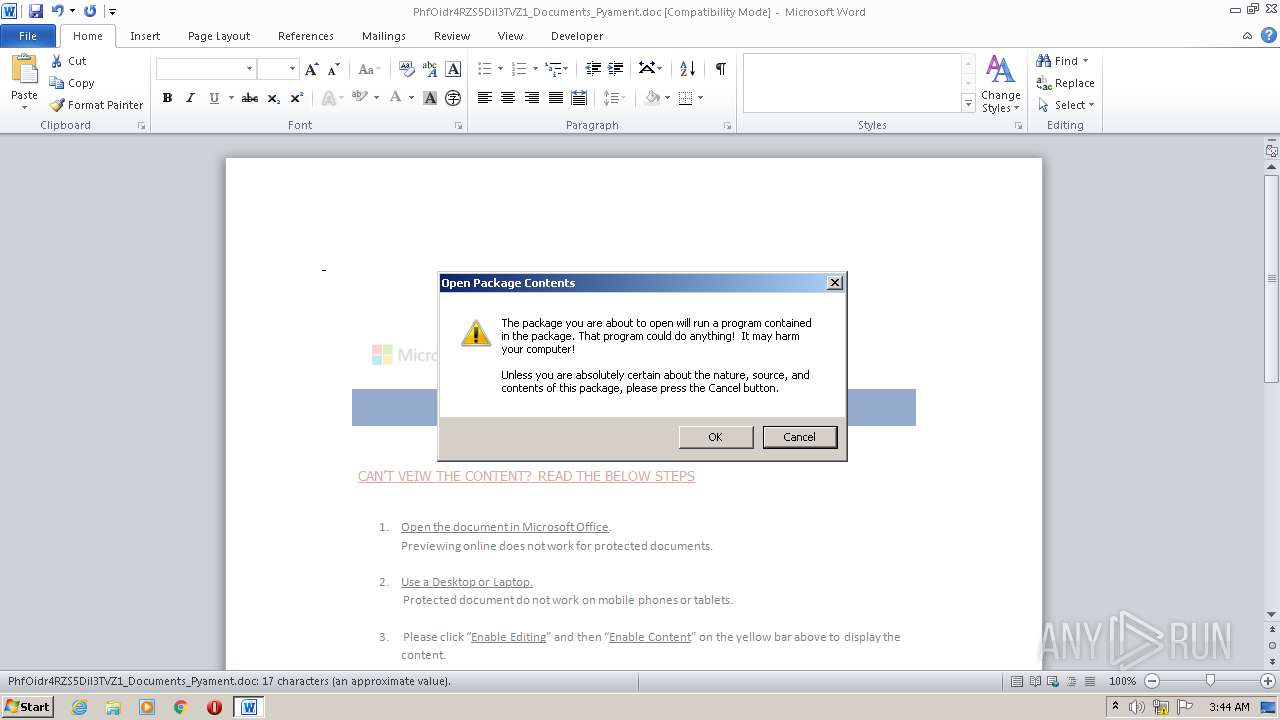
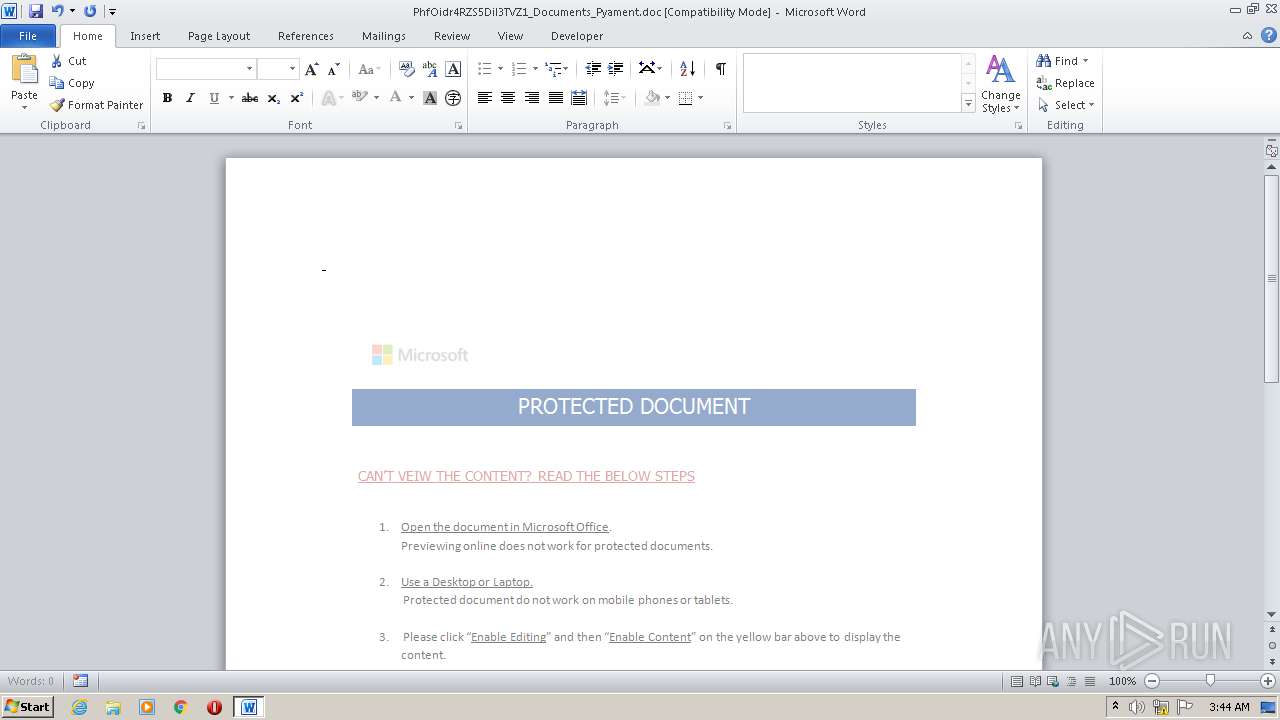
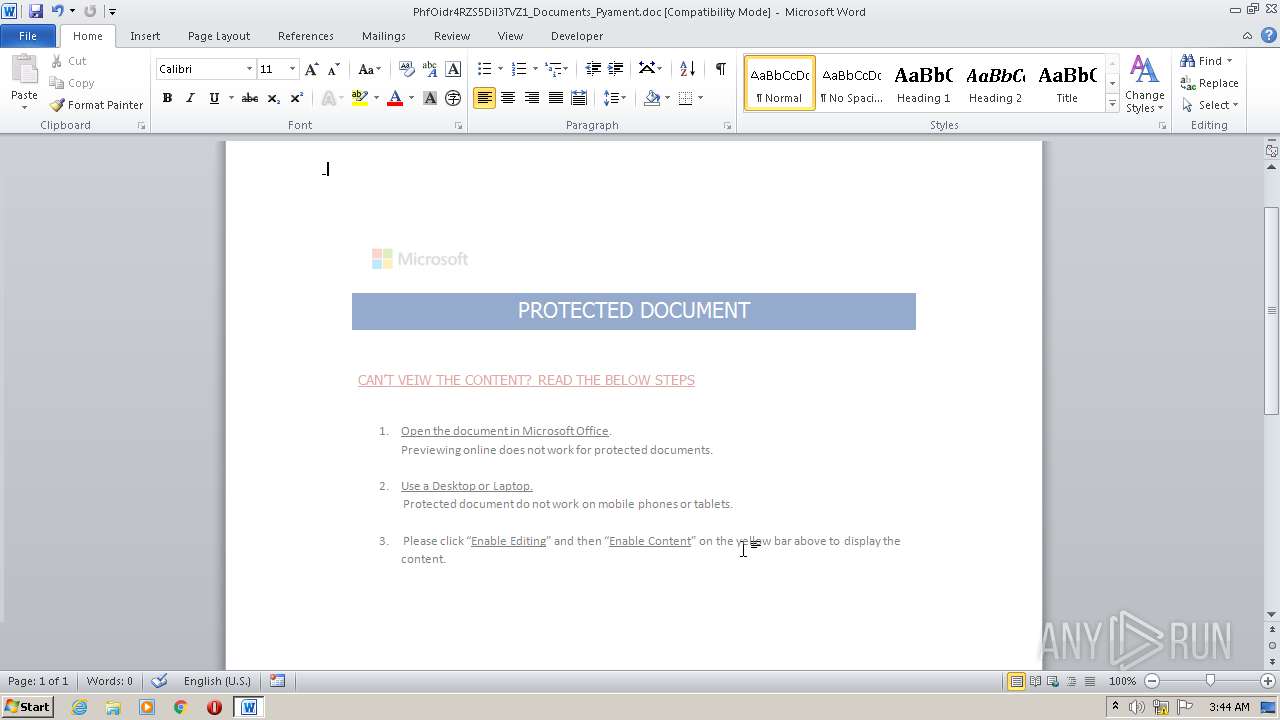
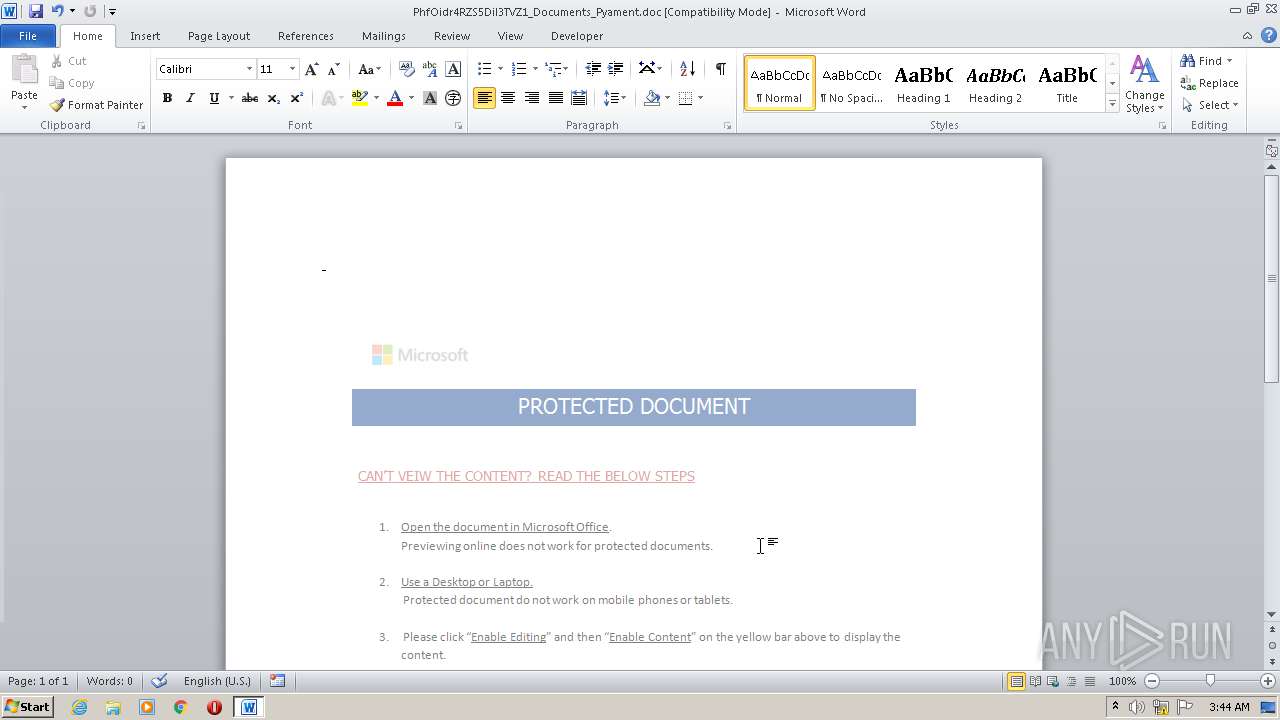
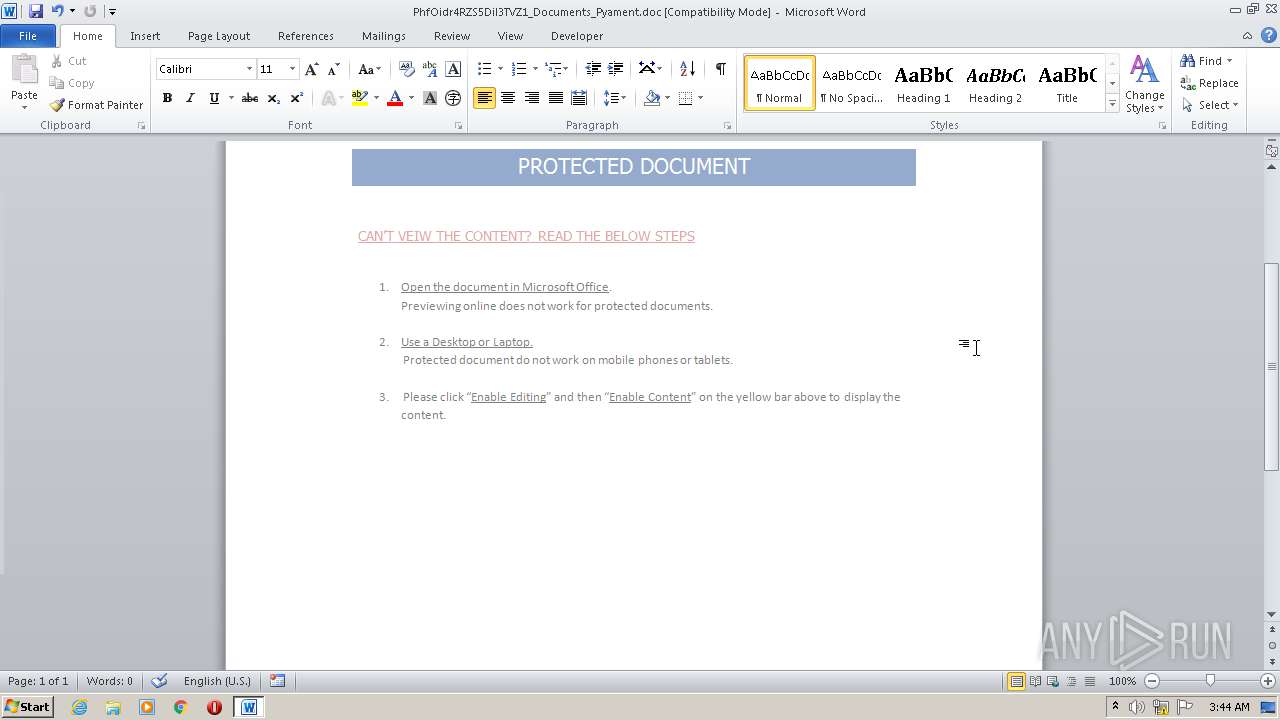
| File name: | PhfOidr4RZS5Dil3TVZ1_Documents_Pyament.doc |
| Full analysis: | https://app.any.run/tasks/4690c074-5379-4690-ba9d-b5d2d6b3ee84 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2020, 03:43:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: Windows User, Template: Normal, Last Saved By: milesco58@hotmail.com, Revision Number: 6, Name of Creating Application: Microsoft Office Word, Total Editing Time: 02:00, Create Time/Date: Fri Feb 28 03:49:00 2020, Last Saved Time/Date: Fri Nov 27 17:37:00 2020, Number of Pages: 1, Number of Words: 3, Number of Characters: 18, Security: 0 |
| MD5: | 44478B1455526CB5DF17C3821E5BDBE7 |
| SHA1: | 834E0A5DF8357DB3C1958D15F461878337E27828 |
| SHA256: | 42186A0DEC773C2E918B53A1FEF4C500713C6E95B2CC1342B77F3656BBE21BA6 |
| SSDEEP: | 24576:v/1JiitSQ7STXy/8Vef+qN56cOgK9x6wYFIXf8XGd0NZP9HHsuMQh:vNJiitDoXj0f+E56Lgcx6wYFIXf8XGdg |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2248)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2248)
Application was dropped or rewritten from another process
- Documents_payments.exe (PID: 868)
SUSPICIOUS
Drops a file with a compile date too recent
- WINWORD.EXE (PID: 2248)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2248)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Windows User |
| Keywords: | - |
| Template: | Normal |
| LastModifiedBy: | milesco58@hotmail.com |
| RevisionNumber: | 6 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 2.0 minutes |
| CreateDate: | 2020:02:28 03:49:00 |
| ModifyDate: | 2020:11:27 17:37:00 |
| Pages: | 1 |
| Words: | 3 |
| Characters: | 18 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 20 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
35
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 868 | "C:\Users\admin\AppData\Local\Temp\Documents_payments.exe" | C:\Users\admin\AppData\Local\Temp\Documents_payments.exe | — | WINWORD.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2248 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\PhfOidr4RZS5Dil3TVZ1_Documents_Pyament.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 796
Read events
1 040
Write events
612
Delete events
144
Modification events
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | v>8 |
Value: 763E3800C8080000010000000000000000000000 | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2248) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2248 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8276.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2248 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2248 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$fOidr4RZS5Dil3TVZ1_Documents_Pyament.doc | pgc | |
MD5:— | SHA256:— | |||
| 2248 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Documents_payments.exe | executable | |
MD5:— | SHA256:— | |||
| 2248 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\111F65ED.emf | emf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report