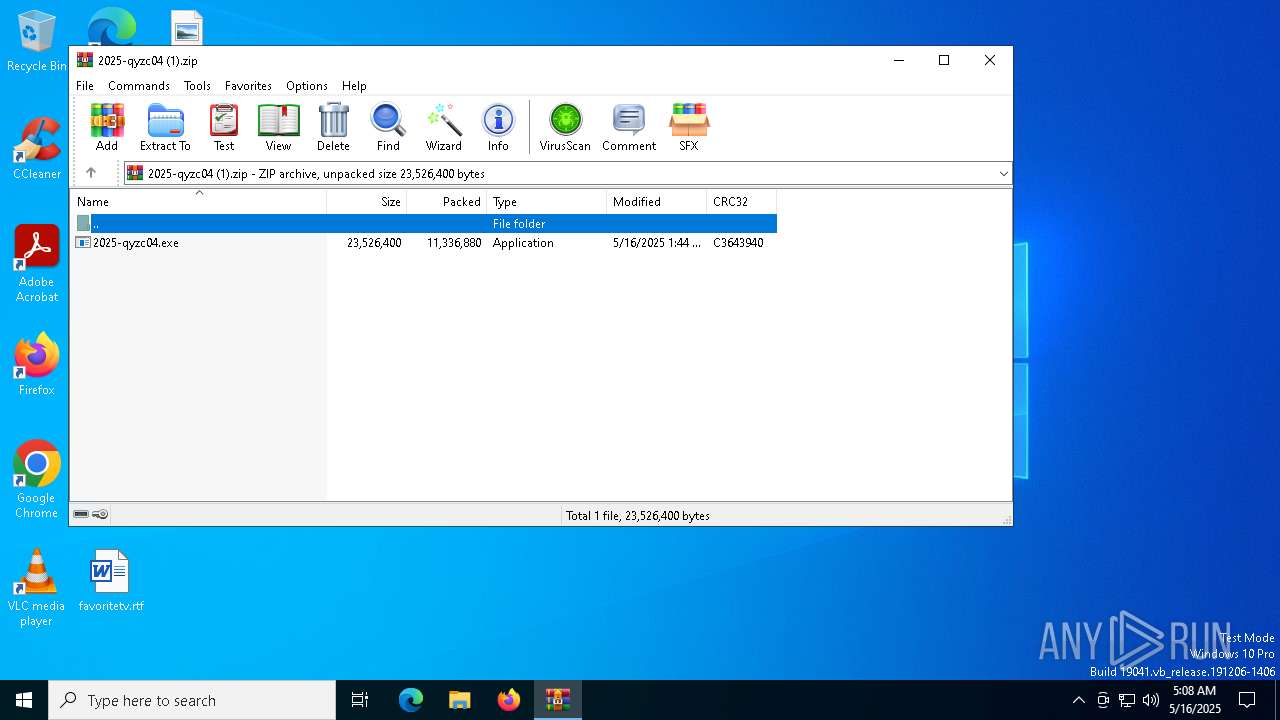
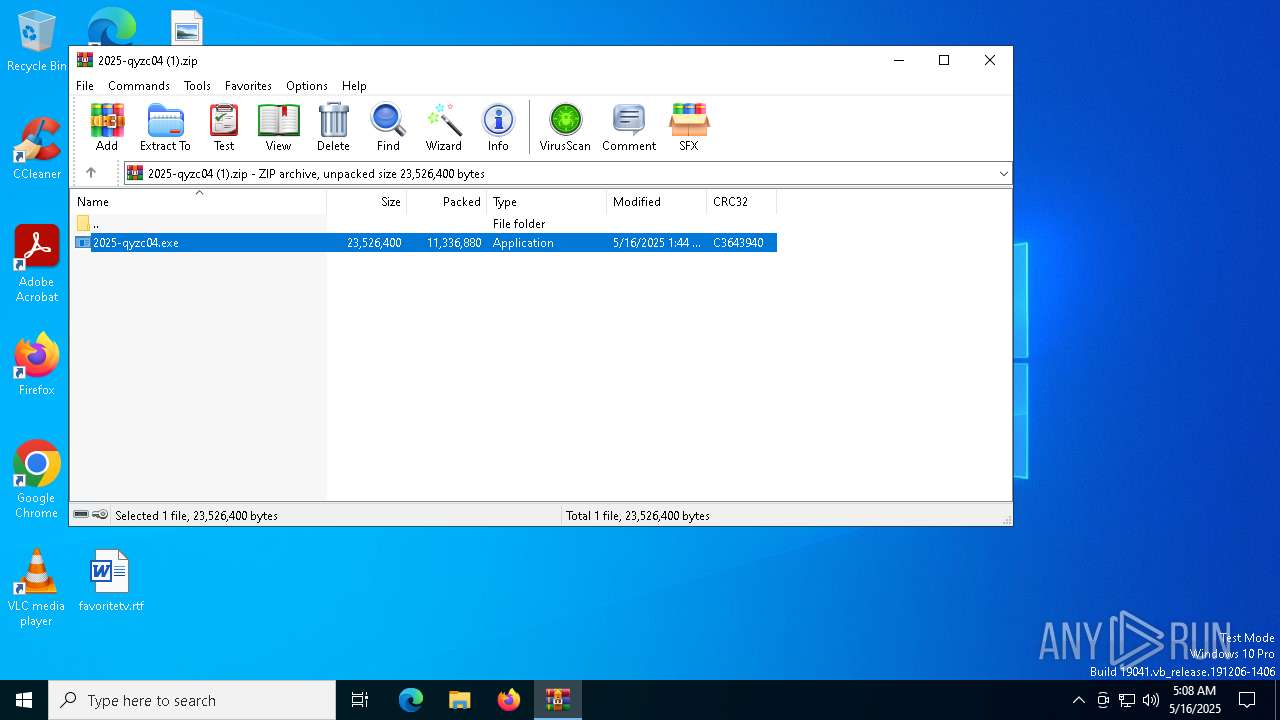
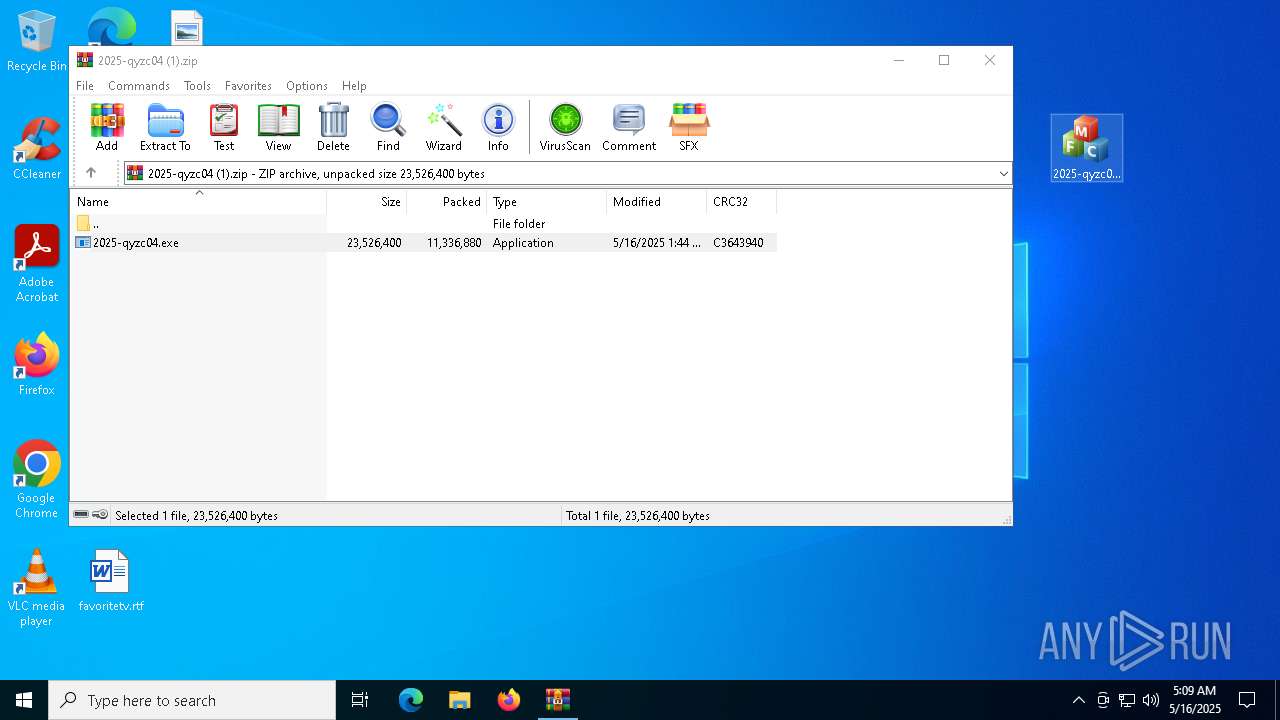
| File name: | 2025-qyzc04 (1).zip |
| Full analysis: | https://app.any.run/tasks/e33a4c41-1c73-4d91-bcb4-8e3e66788af5 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 05:08:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C60AAF430F84E029BF0FDA0F0E472BDA |
| SHA1: | 1D4D9002FA89E80D7411B48D7060231E784C8D01 |
| SHA256: | 420663EF78C40107782CD25A5C14763BE63EF2264F4C86683D4E34A7D5268939 |
| SSDEEP: | 98304:t5nifAWqhmvIlS5+P00ikkfRxaMQCWCvMaN9T2OFOFVDLa7cl2VOoE4uFKK4ZKwa:S7fm5aq0SZf9+n0B |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7416)
Application was injected by another process
- svchost.exe (PID: 1260)
Runs injected code in another process
- VSSVC.exe (PID: 7964)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7416)
Executes as Windows Service
- VSSVC.exe (PID: 7964)
The process executes via Task Scheduler
- svchost.exe (PID: 8024)
- svchost.exe (PID: 5728)
There is functionality for taking screenshot (YARA)
- VSSVC.exe (PID: 7964)
- svchost.exe (PID: 5728)
- dllhost.exe (PID: 6872)
- svchost.exe (PID: 8024)
- dllhost.exe (PID: 8060)
Application launched itself
- svchost.exe (PID: 1260)
INFO
The sample compiled with chinese language support
- WinRAR.exe (PID: 7416)
Checks supported languages
- 2025-qyzc04.exe (PID: 7840)
- 2025-qyzc04.exe (PID: 7932)
- 2025-qyzc04.exe (PID: 7296)
- 2025-qyzc04.exe (PID: 5116)
Reads the computer name
- 2025-qyzc04.exe (PID: 7932)
- 2025-qyzc04.exe (PID: 7840)
- 2025-qyzc04.exe (PID: 5116)
- 2025-qyzc04.exe (PID: 7296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7416)
Reads the software policy settings
- slui.exe (PID: 6388)
Checks proxy server information
- slui.exe (PID: 6388)
Manual execution by a user
- 2025-qyzc04.exe (PID: 7296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:16 09:44:38 |
| ZipCRC: | 0xc3643940 |
| ZipCompressedSize: | 11336880 |
| ZipUncompressedSize: | 23526400 |
| ZipFileName: | 2025-qyzc04.exe |
Total processes
148
Monitored processes
16
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1260 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s Schedule | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | 2025-qyzc04.exe | C:\Users\admin\Desktop\2025-qyzc04.exe | Taskmgr.exe | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: HIGH Description: Server2010 Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 5640 | C:\windows\system32\taskmgr.exe | C:\Windows\System32\Taskmgr.exe | 2025-qyzc04.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5728 | C:\WINDOWS\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5968 | C:\windows\system32\winver.exe | C:\Windows\System32\winver.exe | — | 2025-qyzc04.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Version Reporter Applet Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | C:\WINDOWS\system32\dllhost.exe /Processid:{F8284233-48F4-4680-ADDD-F8284233} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7296 | "C:\Users\admin\Desktop\2025-qyzc04.exe" | C:\Users\admin\Desktop\2025-qyzc04.exe | explorer.exe | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: MEDIUM Description: Server2010 Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 7416 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\2025-qyzc04 (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7840 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7416.43675\2025-qyzc04.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7416.43675\2025-qyzc04.exe | WinRAR.exe | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: MEDIUM Description: Server2010 Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
6 385
Read events
6 203
Write events
101
Delete events
81
Modification events
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\2025-qyzc04 (1).zip | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1260) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{4671B5C1-A383-4428-A45A-8D348E4CB873} |
| Operation: | write | Name: | DynamicInfo |
Value: 030000009F7DFD23AAB7D801AEB51D9120C6DB0100000000000000006A38359420C6DB01 | |||
| (PID) Process: | (1260) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{0CEC0B91-4AE9-4E8A-ACB2-3B4C811F442C} |
| Operation: | write | Name: | DynamicInfo |
Value: 0300000059EDC123AAB7D801AEB51D9120C6DB0100000000000000008D0C459520C6DB01 | |||
Executable files
2
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1260 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Work | xml | |
MD5:5FADF13CCFBDCC5DD728380F7A615B28 | SHA256:FF1F73395F6B5B22D5FDA367521FE0DCC31FF252849B7FA85FA346B953A40451 | |||
| 1260 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Maintenance Work | xml | |
MD5:4838EE953DAB2C7A1BF57E0C6620A79D | SHA256:22C798E00C4793749EAC39CFB6EA3DD75112FD4453A3706E839038A64504D45D | |||
| 1260 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\AppID\.NET Framework NGEN v4.0.30416 | binary | |
MD5:D21FC7CFFDE77AEE3687968AB87AAE7E | SHA256:F41D887AE6672EF704DAF62555B23A615FBAA5F89CC8D0FF500DDB113DA431DB | |||
| 7416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7416.43675\2025-qyzc04.exe | executable | |
MD5:56ACBE6043570E74416B45E266B1023E | SHA256:1996B707C1FBA756658968BB791784A8EE15C4C7D4758FDEF244EE34D24EEE6B | |||
| 1260 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Schedule Wake To Work | xml | |
MD5:C6086D02F8CE044F5FA07A98303DC7EB | SHA256:8901D9C9AEA465DA4EA7AA874610A90B8CF0A71EBA0E321CF9675FCEEE0B54A0 | |||
| 7416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7416.45367\2025-qyzc04.exe | executable | |
MD5:56ACBE6043570E74416B45E266B1023E | SHA256:1996B707C1FBA756658968BB791784A8EE15C4C7D4758FDEF244EE34D24EEE6B | |||
| 1260 | svchost.exe | C:\Windows\System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTask | binary | |
MD5:87E7D15B302E5D84C2C54A1812727C3A | SHA256:42C048E24D9855C8DCF164B504533E594093787DED14133B3D4BC2EBFB1625DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6068 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6068 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7840 | 2025-qyzc04.exe | 103.235.46.102:80 | www.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | whitelisted |
7932 | 2025-qyzc04.exe | 103.235.46.102:80 | www.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.baidu.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |