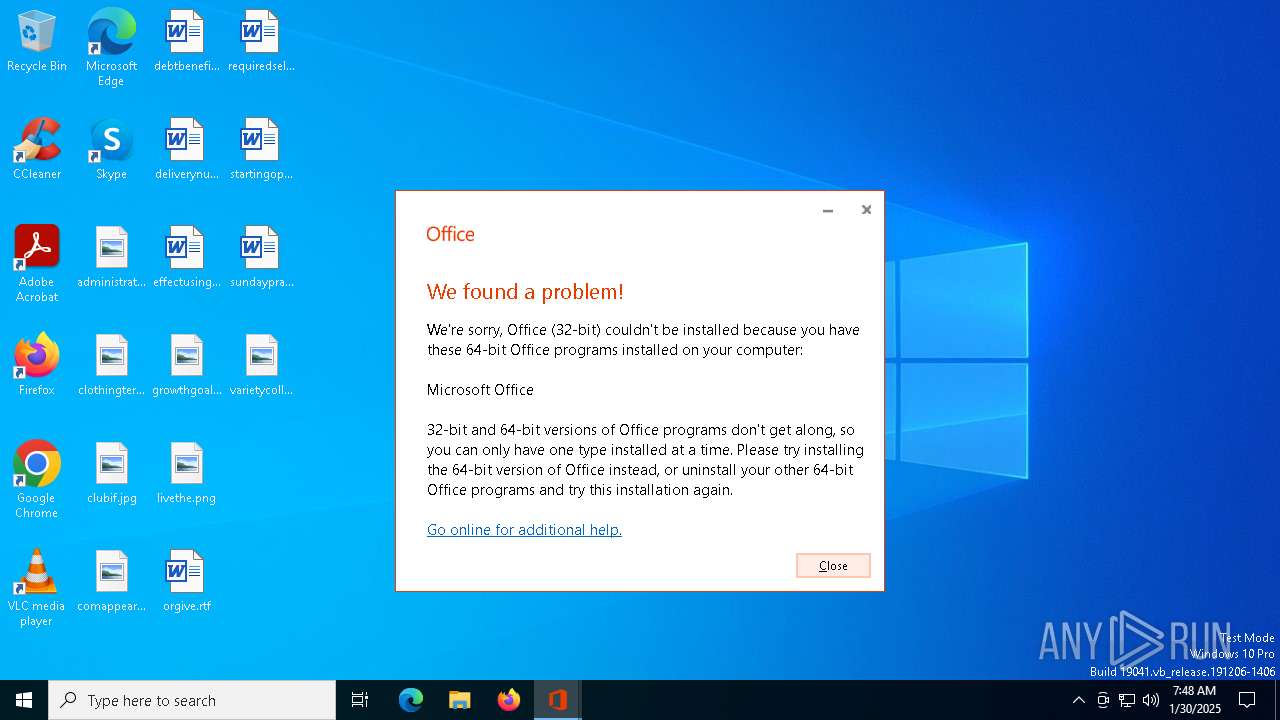
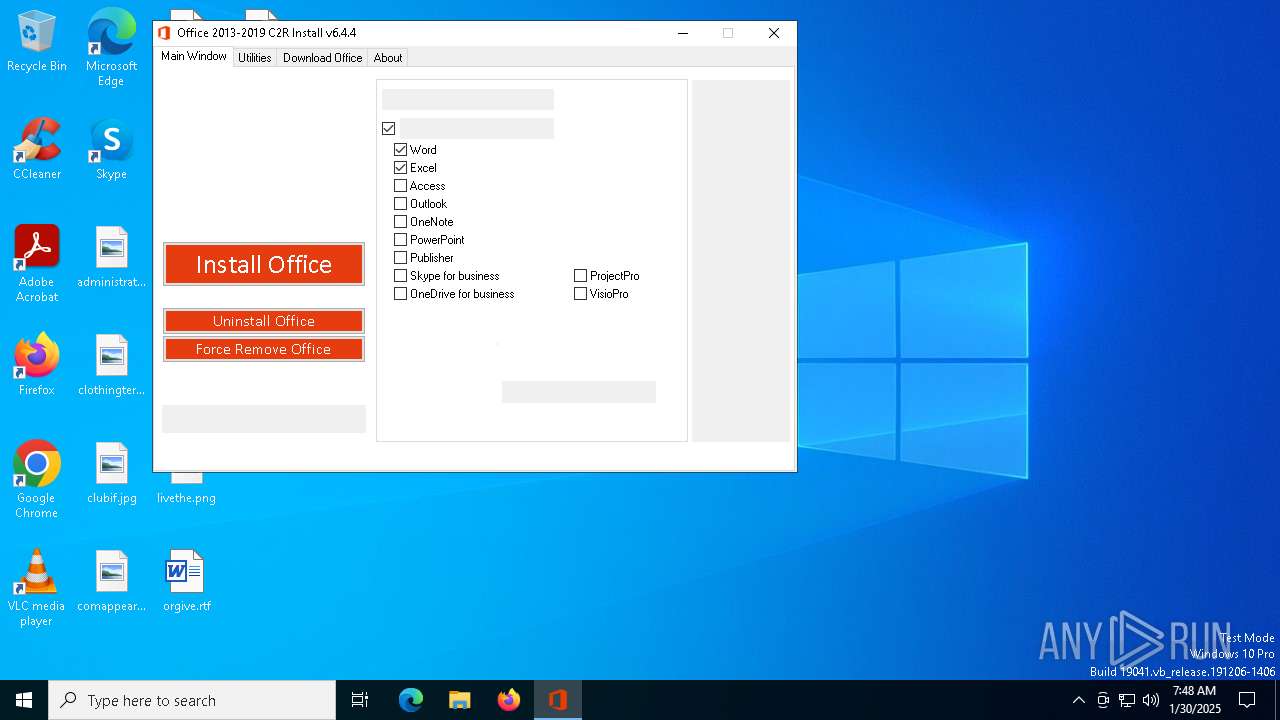
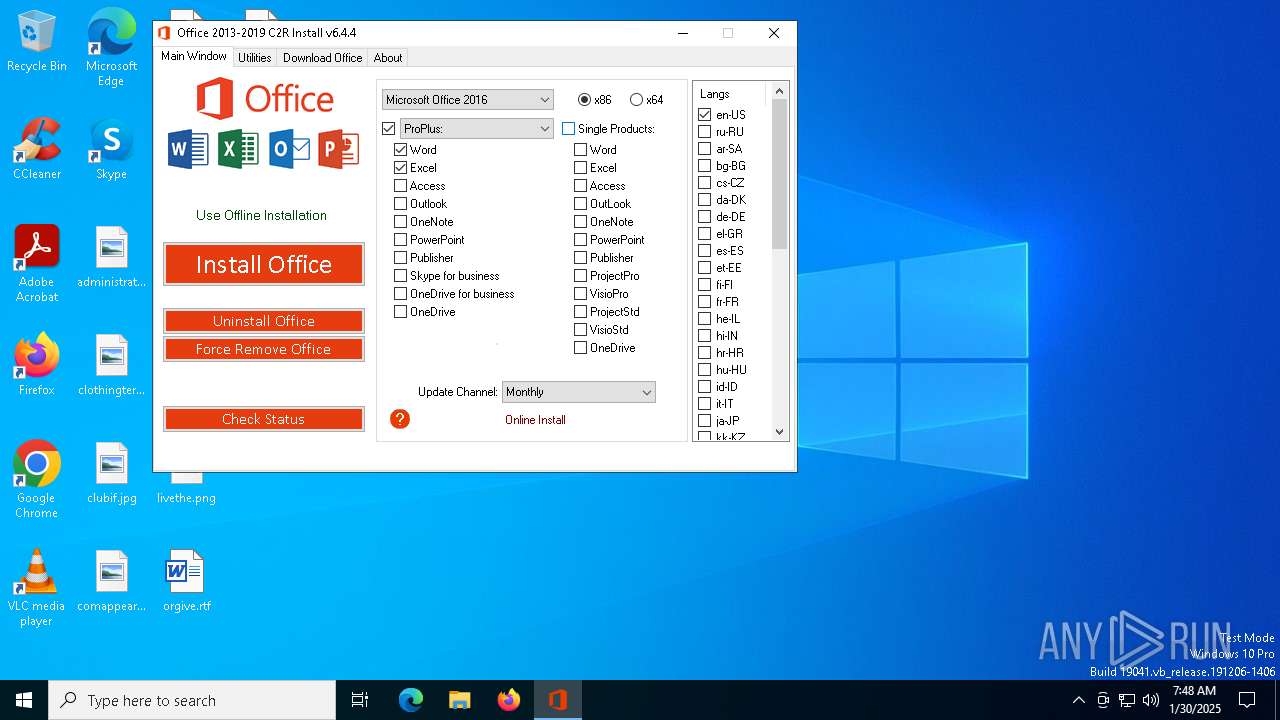
| File name: | OInstall.exe |
| Full analysis: | https://app.any.run/tasks/ea14ccad-2044-4e7c-a2a4-e95b67cc8381 |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2025, 07:47:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | F71556138C9EB716330063156DB4A6BC |
| SHA1: | BD91945D407CBEEE830C15280C8324459F0FF61A |
| SHA256: | 41FF83C380B958E918C4061C02A6077590D7630A01D7F2F0F448DC1A6FBF284A |
| SSDEEP: | 196608:vp1crEM65aqMLvUcm+oz3BkeBTAUW24t13Dr7m0mitn2xe7gXQZ+3jeRBTfYNCH1:hurEzabjm+4keB0vt1Dr7m0mc2xe7gAN |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 5304)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 6440)
Process drops legitimate windows executable
- OInstall.exe (PID: 6292)
- files.dat (PID: 6492)
- OfficeClickToRun.exe (PID: 3700)
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 6292)
Executable content was dropped or overwritten
- OInstall.exe (PID: 6292)
- files.dat (PID: 6492)
- OfficeClickToRun.exe (PID: 3700)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 6292)
The process drops C-runtime libraries
- files.dat (PID: 6492)
- OfficeClickToRun.exe (PID: 3700)
Starts a Microsoft application from unusual location
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
Checks Windows Trust Settings
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
Searches for installed software
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
Reads security settings of Internet Explorer
- setup.exe (PID: 4244)
- setup.exe (PID: 6408)
The process hide an interactive prompt from the user
- setup.exe (PID: 4244)
The process bypasses the loading of PowerShell profile settings
- setup.exe (PID: 4244)
Starts POWERSHELL.EXE for commands execution
- setup.exe (PID: 4244)
INFO
Reads Environment values
- OInstall.exe (PID: 6292)
Reads the computer name
- OInstall.exe (PID: 6292)
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
Checks supported languages
- OInstall.exe (PID: 6292)
- files.dat (PID: 6492)
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with english language support
- OInstall.exe (PID: 6292)
- files.dat (PID: 6492)
- OfficeClickToRun.exe (PID: 3700)
Create files in a temporary directory
- files.dat (PID: 6492)
- OInstall.exe (PID: 6292)
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
- OfficeClickToRun.exe (PID: 3700)
UPX packer has been detected
- OInstall.exe (PID: 6292)
Checks proxy server information
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
- OfficeClickToRun.exe (PID: 3700)
Process checks computer location settings
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
Reads the machine GUID from the registry
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
- OfficeClickToRun.exe (PID: 3700)
Creates files or folders in the user directory
- setup.exe (PID: 6408)
- OfficeClickToRun.exe (PID: 3700)
Reads the software policy settings
- setup.exe (PID: 6408)
- setup.exe (PID: 4244)
Reads CPU info
- setup.exe (PID: 6408)
Reads Microsoft Office registry keys
- setup.exe (PID: 4244)
- setup.exe (PID: 6408)
- OfficeClickToRun.exe (PID: 3700)
Creates files in the program directory
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with arabic language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with bulgarian language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with german language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with spanish language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with Italian language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with french language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with Indonesian language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with russian language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with japanese language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with polish language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with portuguese language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with slovak language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with turkish language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with korean language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with chinese language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with czech language support
- OfficeClickToRun.exe (PID: 3700)
The sample compiled with swedish language support
- OfficeClickToRun.exe (PID: 3700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:08:30 04:58:12+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 9842688 |
| InitializedDataSize: | 90112 |
| UninitializedDataSize: | 8626176 |
| EntryPoint: | 0x119d630 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.4.4.0 |
| ProductVersionNumber: | 6.4.4.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
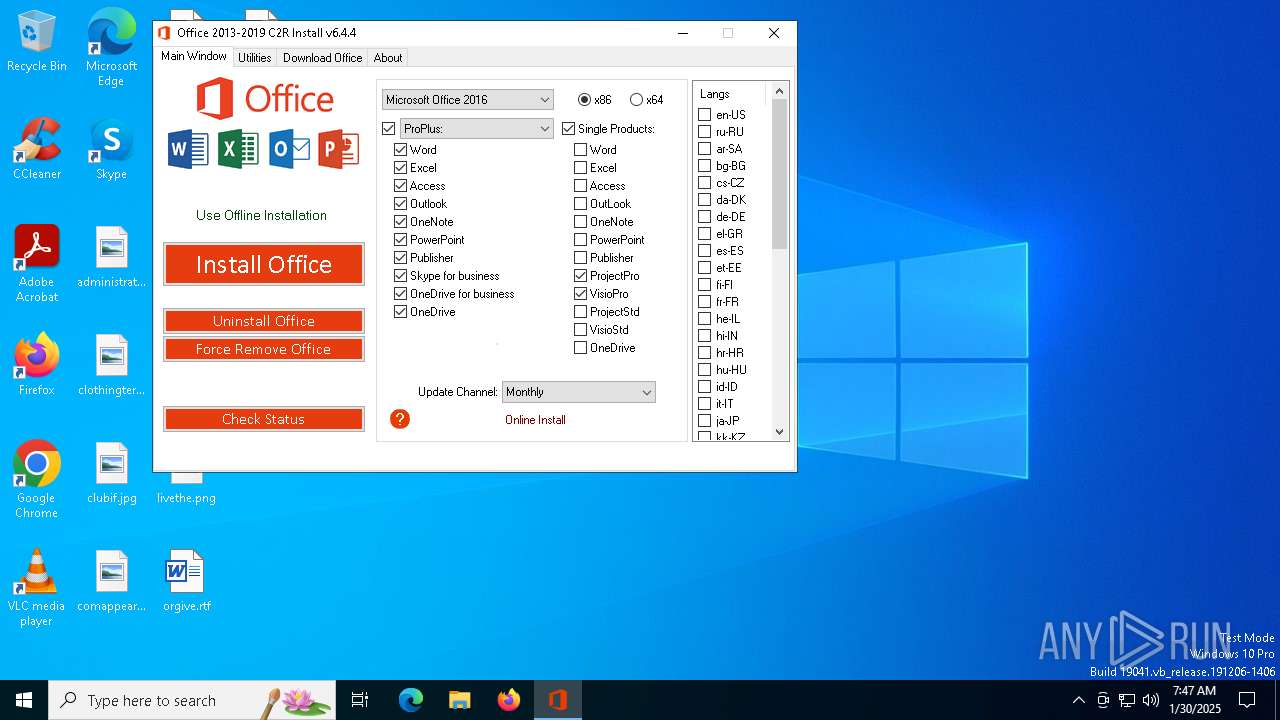
| ProductName: | Office 2013-2016 C2R Install |
| FileDescription: | Office 2013-2016 C2R Install |
Total processes
145
Monitored processes
17
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\WINDOWS\Sysnative\cmd.exe" /D /c C:\Users\admin\AppData\Local\Temp\files\Setup.exe /configure Configure.xml | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1603 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | "C:\Users\admin\AppData\Local\Temp\OInstall.exe" | C:\Users\admin\AppData\Local\Temp\OInstall.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Office 2013-2016 C2R Install Exit code: 3221226540 Modules
| |||||||||||||||
| 3420 | "C:\WINDOWS\Sysnative\cmd.exe" /D /c C:\Users\admin\AppData\Local\Temp\files\Setup.exe /configure Configure.xml | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3700 | OfficeClickToRun.exe deliverymechanism=492350f6-3a01-4f97-b9c0-c7c6ddf67d60 platform=x64 productreleaseid=none forcecentcheck= culture=en-us defaultplatform=False storeid= lcid=1033 b= productstoadd=ProplusRetail.16_en-us_x-none scenario=CLIENTUPDATE acceptalleulas=True updatesenabled=False cdnbaseurl=http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 version=16.0.18429.20132 mediatype=CDN proplusretail.excludedapps=access,publisher,groove,lync,onenote,outlook,powerpoint,onedrive baseurl=http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60 flt.useexptransportinplacepl=unknown flt.useaddons=unknown flt.useofficehelperaddon=unknown flt.useonedriveclientaddon=unknown flt.useoutlookshareaddon=unknown | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.16026.20140 Modules
| |||||||||||||||
| 3820 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | C:\Users\admin\AppData\Local\Temp\files\Setup.exe /configure Configure.xml | C:\Users\admin\AppData\Local\Temp\files\setup.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office Version: 16.0.10810.33603 Modules
| |||||||||||||||
| 5304 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -NonInteractive -WindowStyle Hidden -Command "& { $isOfficeInstalled = Get-AppxPackage Microsoft.Office.Desktop -allusers; if ($isOfficeInstalled -eq $null) { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Centennial.Detection.IsCentennialOfficeInstalled.scratch' -InputObject '0' -Encoding ascii; } else { Out-File -FilePath 'C:\Users\admin\AppData\Local\Temp\Centennial.Detection.IsCentennialOfficeInstalled.scratch' -InputObject '1' -Encoding ascii } }" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6292 | "C:\Users\admin\AppData\Local\Temp\OInstall.exe" | C:\Users\admin\AppData\Local\Temp\OInstall.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Office 2013-2016 C2R Install Modules
| |||||||||||||||
| 6372 | "C:\WINDOWS\Sysnative\cmd.exe" /D /c copy C:\WINDOWS\system32\Tasks\OInstall "C:\WINDOWS\Temp\OInstall.tmp" /Y | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 700
Read events
20 523
Write events
1 082
Delete events
95
Modification events
| (PID) Process: | (6292) OInstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
| (PID) Process: | (6408) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ru-ru |
Value: 2 | |||
Executable files
253
Suspicious files
32
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6292 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\setup.exe | executable | |
MD5:D4A7C7C3C92C4E9BC9BDEE1C660E60DB | SHA256:B95AC36A49E79C3E63E23ECA86EAC3D22ACD80363D0F0AA83BA7EE7799ACF2A5 | |||
| 6408 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FA84E4BCC92AA5DB735AB50711040CDE | SHA256:6D7205E794FDE4219A62D9692ECDDF612663A5CF20399E79BE87B851FCA4CA33 | |||
| 6492 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\cleanospp.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 6492 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 6408 | setup.exe | C:\Users\admin\AppData\Local\Temp\OfficeC2R8C4A6B3E-84AD-4971-B0C9-7B1E310B6FCA\v32_16.0.18429.20132.cab | compressed | |
MD5:181BF9CE6AEF8B2699365FD1867416AE | SHA256:C7F08E2FF8F800EC357E5B937062BFFACCAFAD14D142F60EA74E3D385225B14B | |||
| 6292 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\Configure.xml | text | |
MD5:423B57427D709D53B6647A12F10E852D | SHA256:7FCCB678CCD4097E9201B1BA5AA346D578AA5F892420DA650B5180EE61D8E3E8 | |||
| 6408 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\setup.exe_Rules.xml | xml | |
MD5:D75F3FEA731A83F965F765550FB449F0 | SHA256:61AF6EBA2AB7340032C02E8E6FA63BAEC18907F06D69D1D1BCC97D1DCB6023F7 | |||
| 6408 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:6872FAE8288DB34207D9E7EE350157F4 | SHA256:50795B027E2BC566D3B7ACB89913F8EFD23B70615C9DB9BF5B23323AD3132A7D | |||
| 6492 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\cleanospp.exe | executable | |
MD5:5FD363D52D04AC200CD24F3BCC903200 | SHA256:3FDEFE2AD092A9A7FE0EDF0AC4DC2DE7E5B9CE6A0804F6511C06564194966CF9 | |||
| 6292 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\files.dat | executable | |
MD5:BB81E763AB0E673B3C1AF2FEA2586A9A | SHA256:4D45C64B244C8F997358635C3B5CB9A65743FAC473D65C455D3BA8A25E50D5F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
57
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.78.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.78.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6408 | setup.exe | HEAD | 200 | 23.50.131.75:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32_16.0.16026.20146.cab | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6408 | setup.exe | HEAD | 200 | 23.50.131.75:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32_16.0.18429.20132.cab | unknown | — | — | whitelisted |
6408 | setup.exe | HEAD | 200 | 23.50.131.75:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32_16.0.18429.20132.cab | unknown | — | — | whitelisted |
6408 | setup.exe | GET | 200 | 23.50.131.75:80 | http://officecdn.microsoft.com/pr/492350f6-3a01-4f97-b9c0-c7c6ddf67d60/Office/Data/v32_16.0.18429.20132.cab | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 184.86.251.19:443 | — | Akamai International B.V. | DE | unknown |
4712 | MoUsoCoreWorker.exe | 95.101.78.32:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.78.32:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4300 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 184.86.251.10:443 | — | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
client-office365-tas.msedge.net |
| whitelisted |