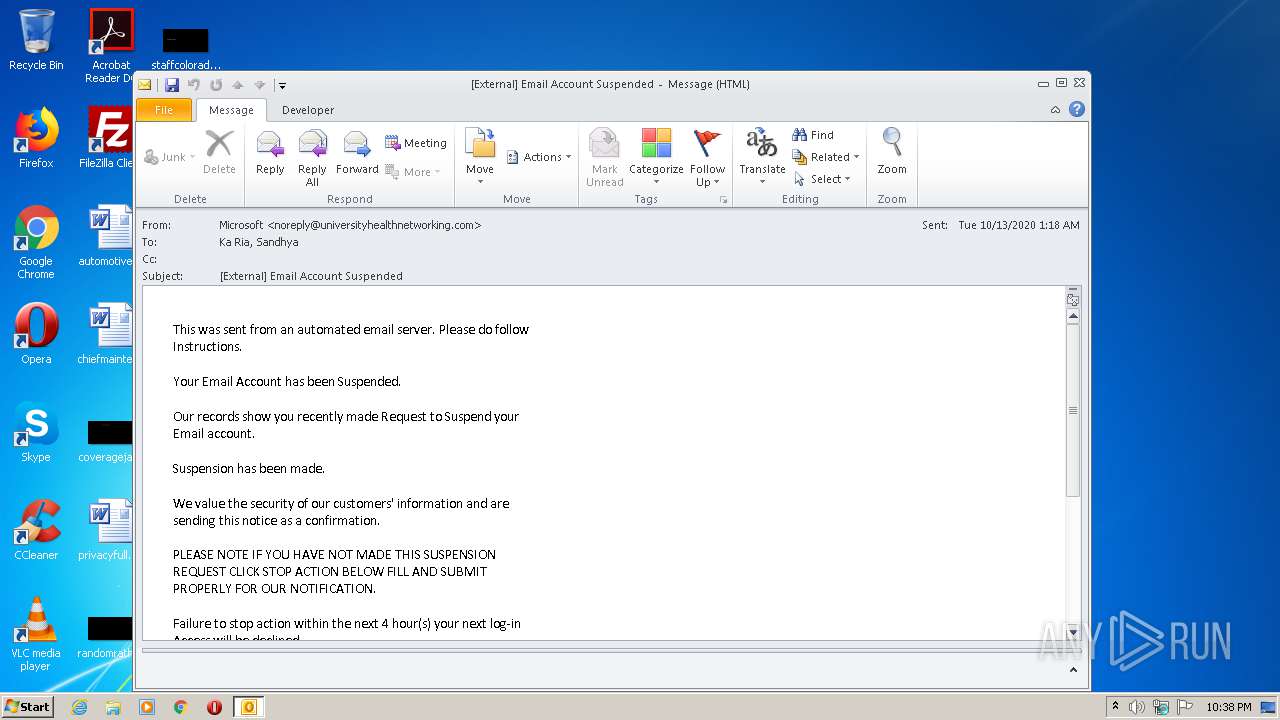
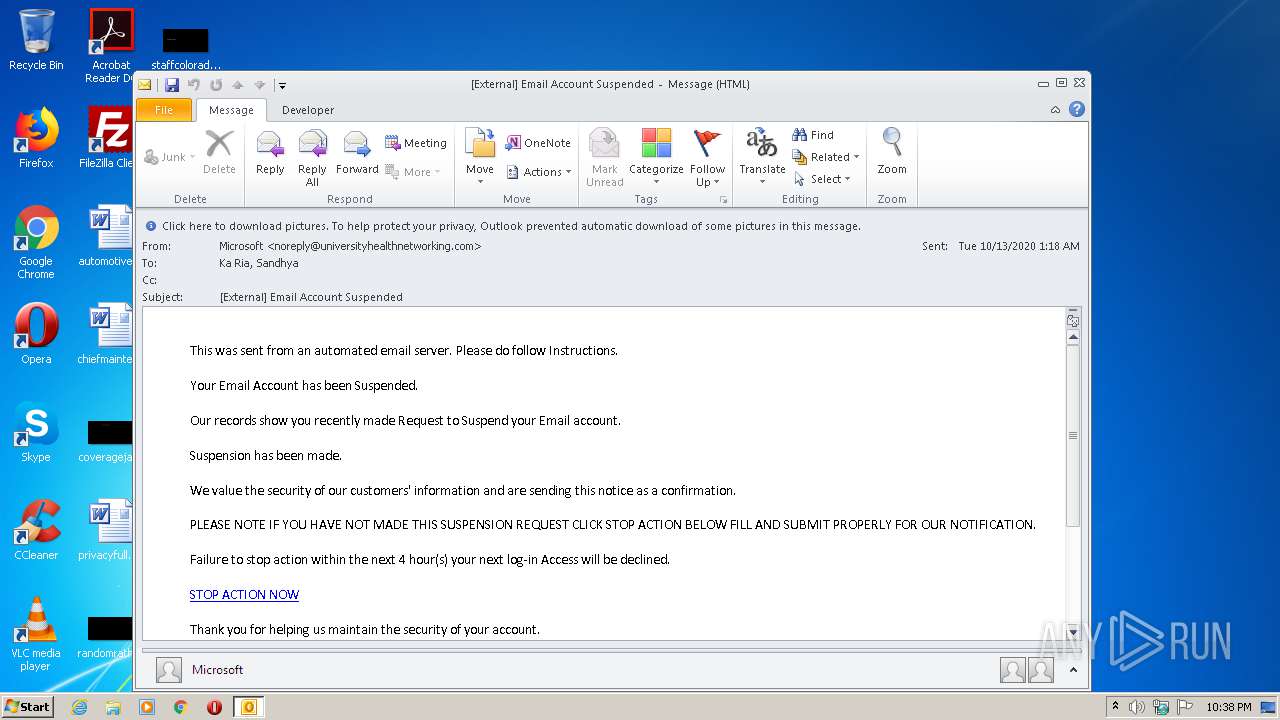
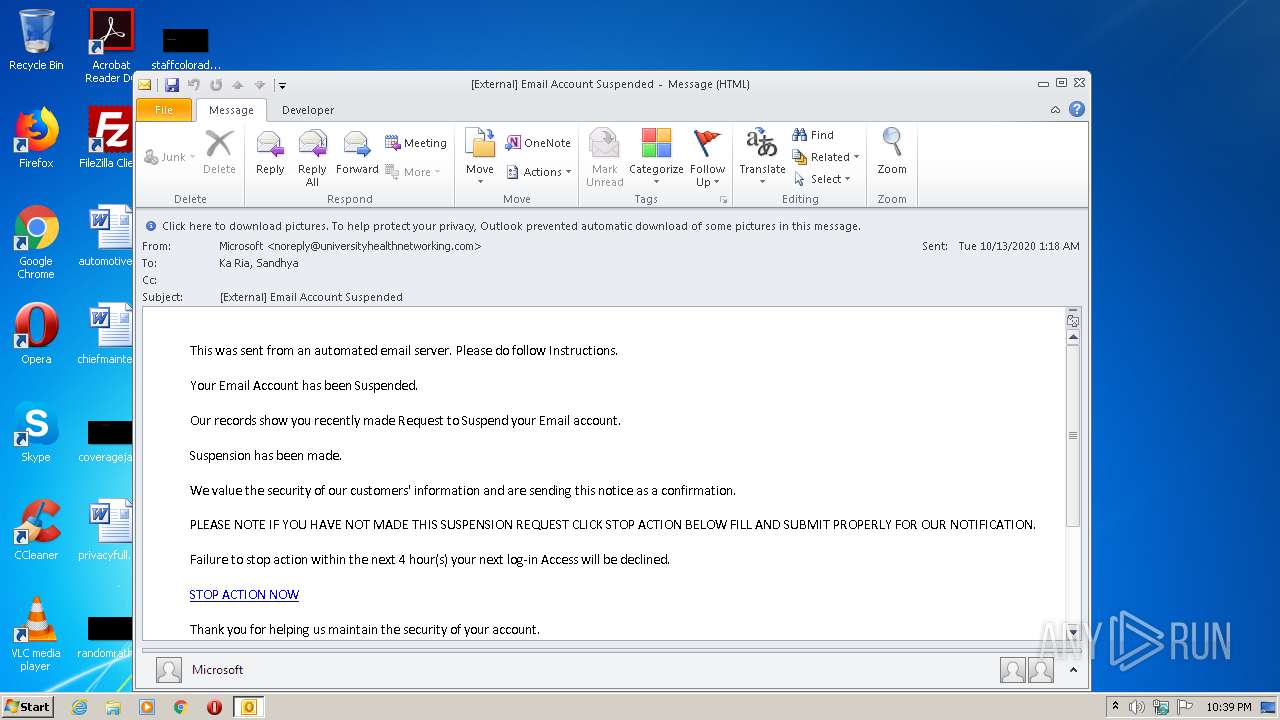
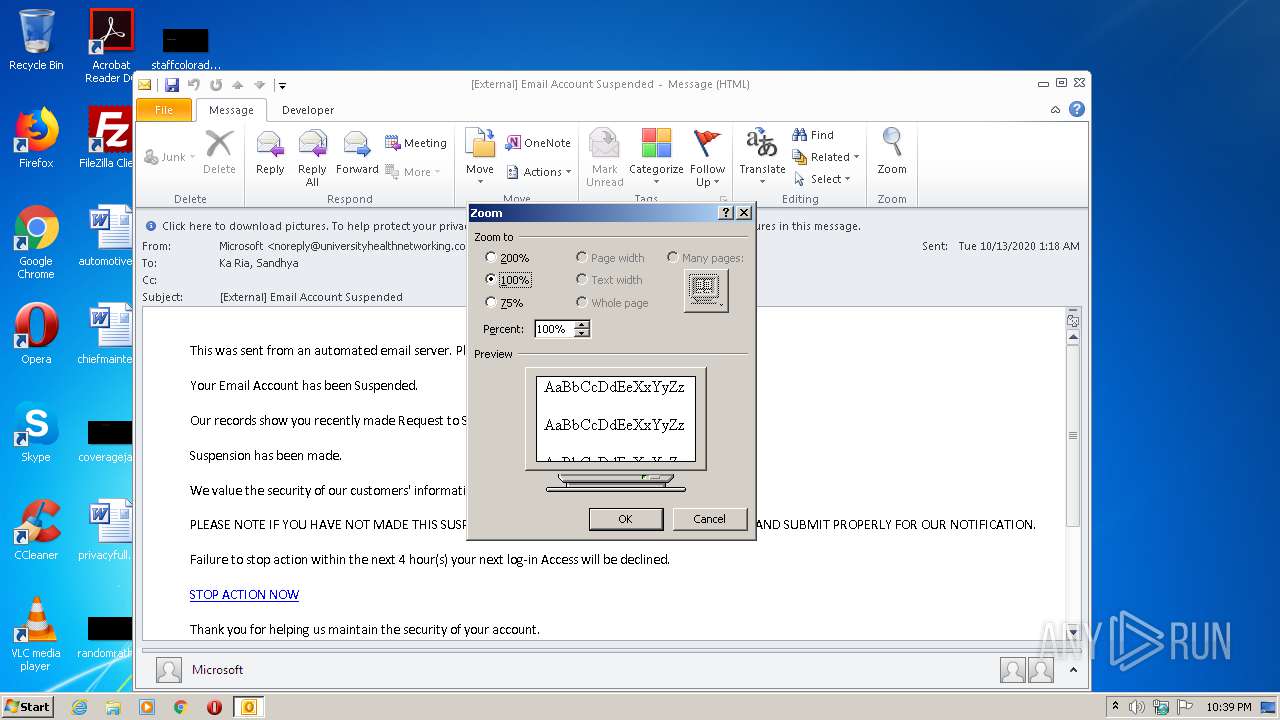
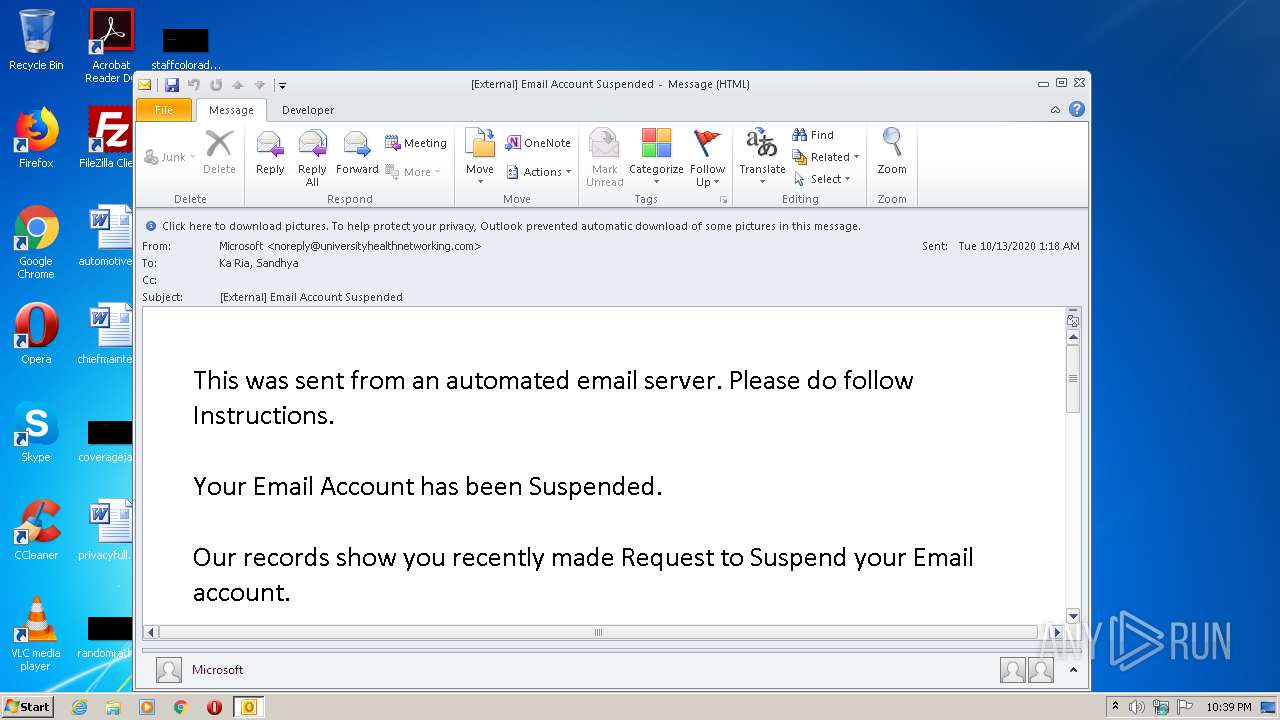
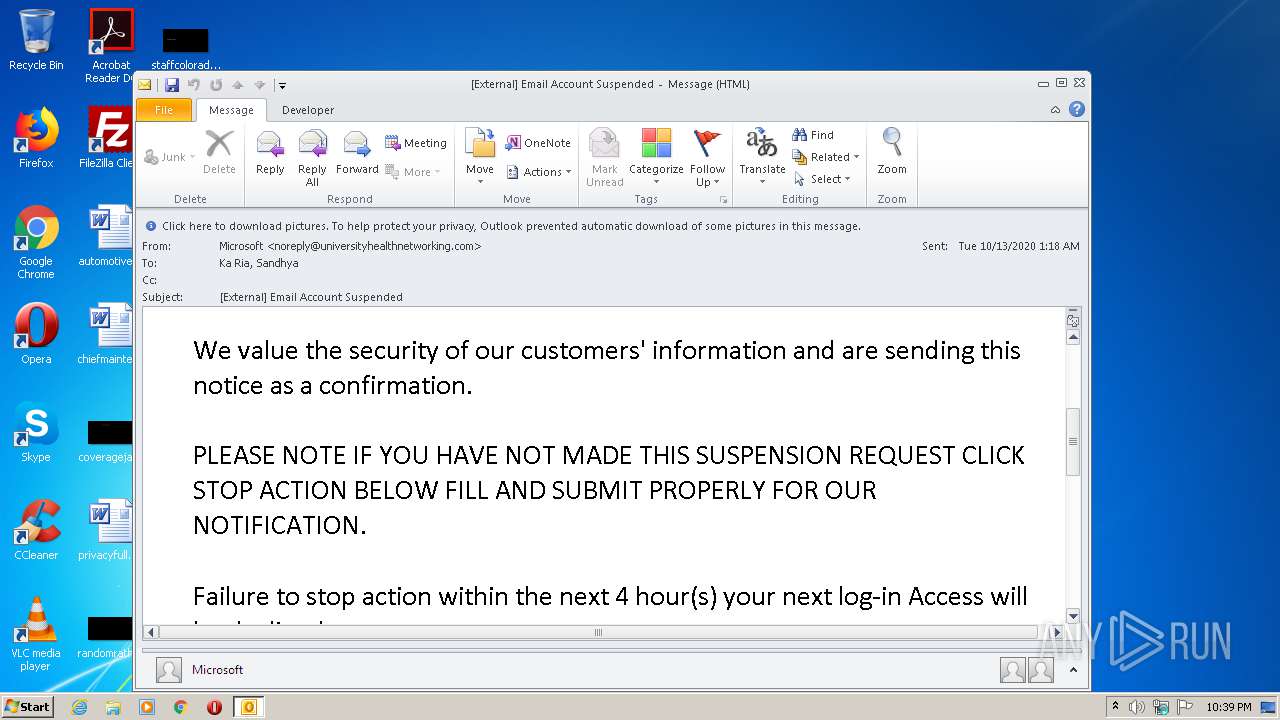
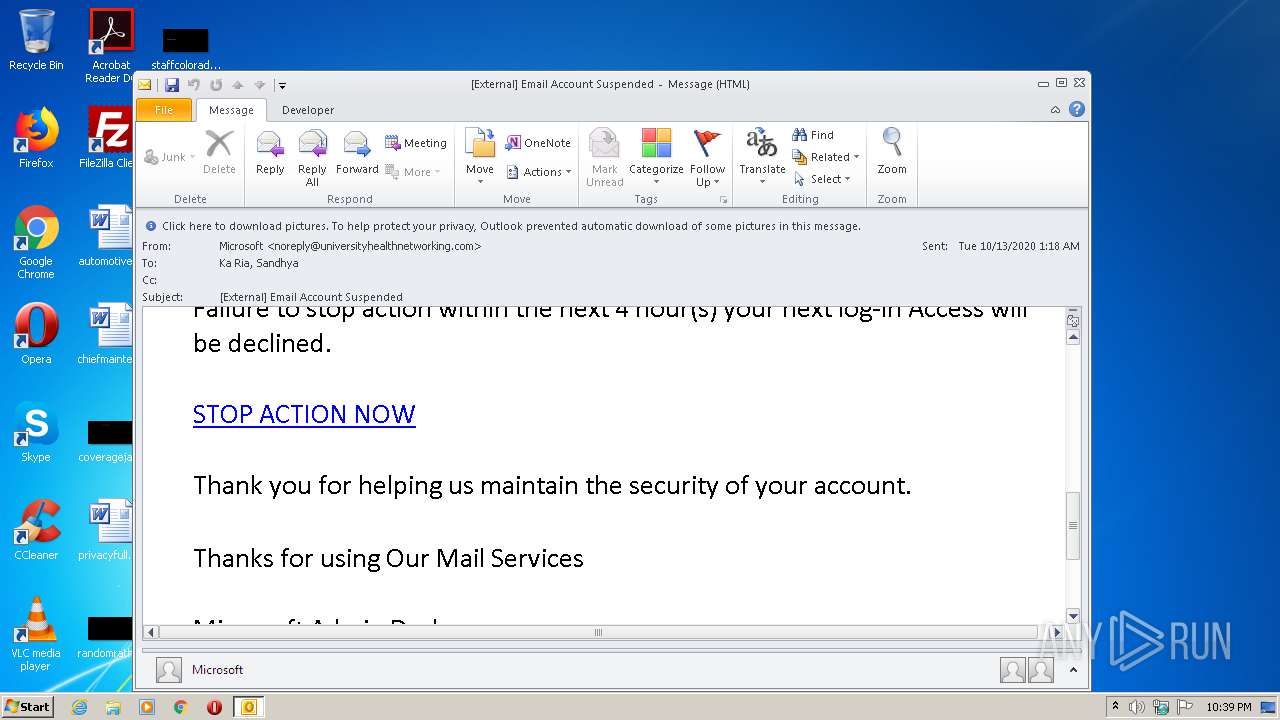
| File name: | External Email Account Suspended.msg |
| Full analysis: | https://app.any.run/tasks/9a4050c8-0dec-41ec-af51-2b083bab172e |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2020, 21:38:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 3D749FEB17B9B0B0DD9CA3D301F04A78 |
| SHA1: | F3425696B496E467F50290DA8571EA171DA8EA23 |
| SHA256: | 41EDBF9C5C211C30E95FAE68C6BD0F321CCEE1F755F35757FC0BAE103FBCCFB7 |
| SSDEEP: | 1536:evz/MF/MswMYgNkEGWDWQ/YL9WCOQqcq3wOWbHY1:ebY9wb7ExYL21LQHY1 |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3068)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3068)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3068)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3068)
- iexplore.exe (PID: 3180)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3068)
- iexplore.exe (PID: 3488)
- iexplore.exe (PID: 3180)
Reads settings of System Certificates
- iexplore.exe (PID: 3180)
Application launched itself
- iexplore.exe (PID: 3488)
Reads internet explorer settings
- iexplore.exe (PID: 3180)
Changes internet zones settings
- iexplore.exe (PID: 3488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3068 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\External Email Account Suspended.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3180 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3488 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
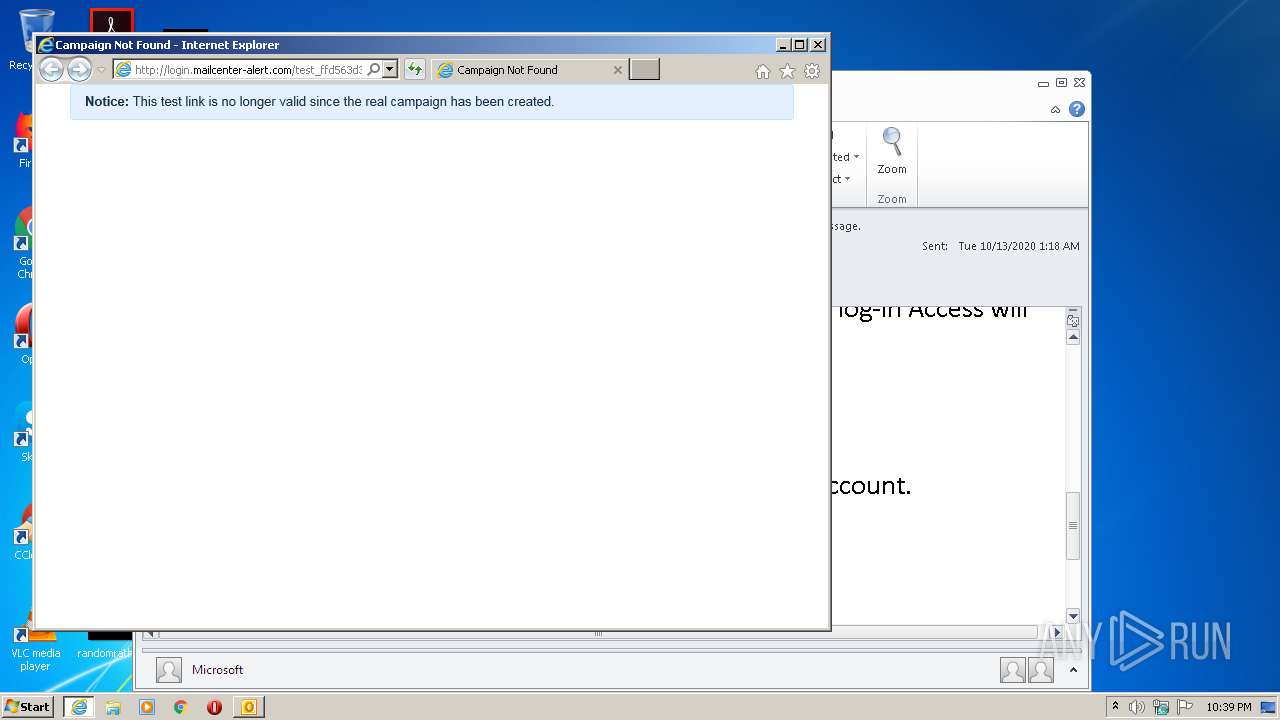
| 3488 | "C:\Program Files\Internet Explorer\iexplore.exe" https://urldefense.com/v3/__http:/login.mailcenter-alert.com/test_ffd563d352?l=64__;!!CjcC7IQ!emB6UfMrfeUvceQ4qQfp-RIwdu7MhJQLjhh-EdZEPUB5MaMrATg9WC3UIoy2_hyUlcs$ | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
1 945
Read events
1 331
Write events
595
Delete events
19
Modification events
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3068) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
34
Text files
32
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3068 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR5028.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9915FBCE5ECE56452A09FB65EDE2FAD2_18932885610B5B91D0B9280DC39653E2 | — | |
MD5:— | SHA256:— | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarEC79.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3068 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_D93C575AD9E9AF9B95268A3CB953B5A1 | binary | |
MD5:— | SHA256:— | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8828F39C7C0CE9A14B25C7EB321181BA_BD8B98368542C3BBAE3413A0EF3BB623 | der | |
MD5:— | SHA256:— | |||
| 3068 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_E7989F4C8B0E634B984E95399B55FDAD.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
| 3068 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 3180 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\YBB3T4LW.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
27
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://status.thawte.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSFvn094QJ%2BcWGTwWWEy%2BBXPZkW8AQUo8heZVTlMHjBBeoHCmpZzLn%2B3loCEA53cAOejRmtccb8jN4MVZM%3D | US | der | 471 b | whitelisted |
3180 | iexplore.exe | GET | 410 | 34.238.141.30:80 | http://login.mailcenter-alert.com/test_ffd563d352?l=64 | US | html | 1.61 Kb | whitelisted |
3180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
3180 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
3180 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
3180 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJaiu8Zb34NbCEEshrmcCs%3D | US | der | 471 b | whitelisted |
3180 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEBMtUwvbZX3eCAAAAABbLrM%3D | US | der | 471 b | whitelisted |
3180 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
3180 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEBMtUwvbZX3eCAAAAABbLrM%3D | US | der | 471 b | whitelisted |
3180 | iexplore.exe | GET | 302 | 172.217.21.206:80 | http://www.google-analytics.com/r/__utm.gif?utmwv=5.7.2&utms=1&utmn=2145069375&utmhn=login.mailcenter-alert.com&utmcs=utf-8&utmsr=1280x720&utmvp=792x544&utmsc=24-bit&utmul=en-us&utmje=1&utmfl=26.0%20r0&utmdt=Campaign%20Not%20Found&utmhid=1087498912&utmr=-&utmp=%2Ftest_ffd563d352%3Fl%3D64&utmht=1603143563194&utmac=UA-83403-16&utmcc=__utma%3D145006633.190772954.1603143563.1603143563.1603143563.1%3B%2B__utmz%3D145006633.1603143563.1.1.utmcsr%3D(direct)%7Cutmccn%3D(direct)%7Cutmcmd%3D(none)%3B&utmjid=488345768&utmredir=1&utmu=qAAAAAAAAAAAAAAAAAAAAAAE~ | US | html | 367 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3180 | iexplore.exe | 52.6.56.188:443 | urldefense.com | Amazon.com, Inc. | US | suspicious |
3068 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3180 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3180 | iexplore.exe | 172.217.21.206:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3180 | iexplore.exe | 13.35.253.17:443 | d25q7gseii1o1q.cloudfront.net | — | US | suspicious |
— | — | 23.37.43.27:80 | s.symcd.com | Akamai Technologies, Inc. | NL | whitelisted |
— | — | 34.238.141.30:80 | login.mailcenter-alert.com | Amazon.com, Inc. | US | unknown |
3180 | iexplore.exe | 173.194.76.157:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
3488 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
urldefense.com |
| shared |
ocsp.digicert.com |
| whitelisted |
status.thawte.com |
| whitelisted |
login.mailcenter-alert.com |
| unknown |
d25q7gseii1o1q.cloudfront.net |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
s.symcd.com |
| shared |
www.google-analytics.com |
| whitelisted |