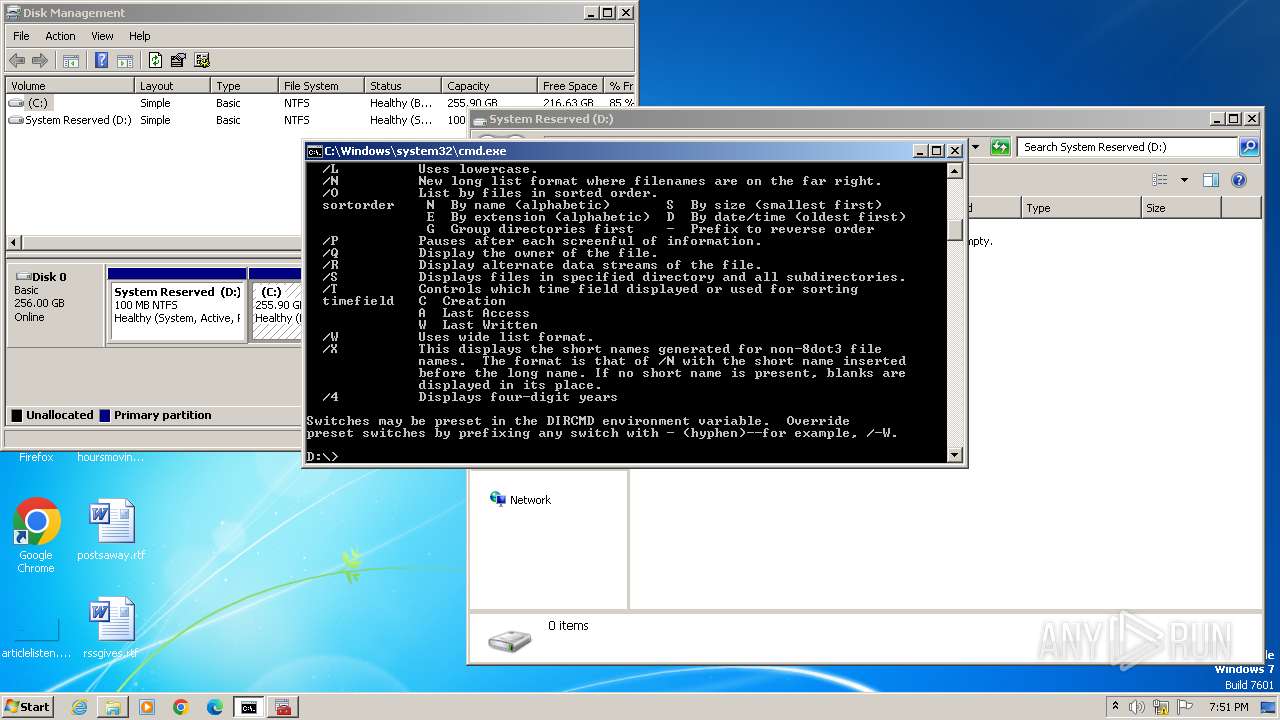
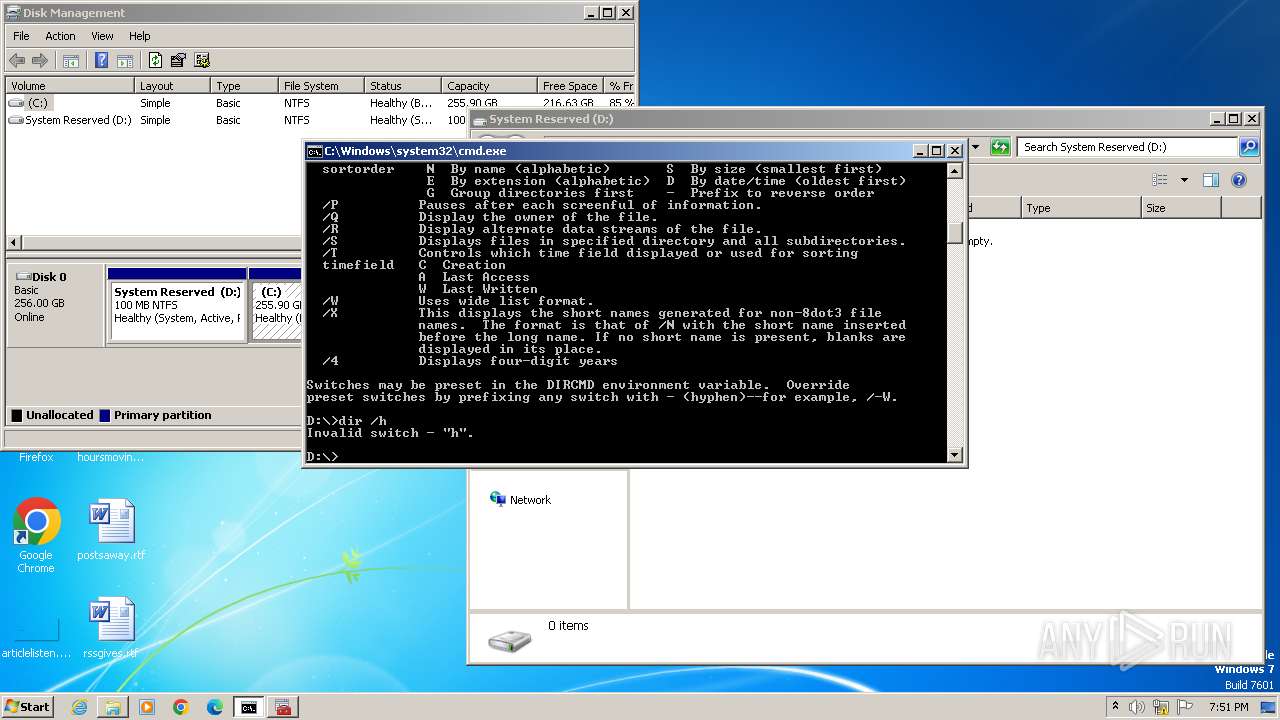
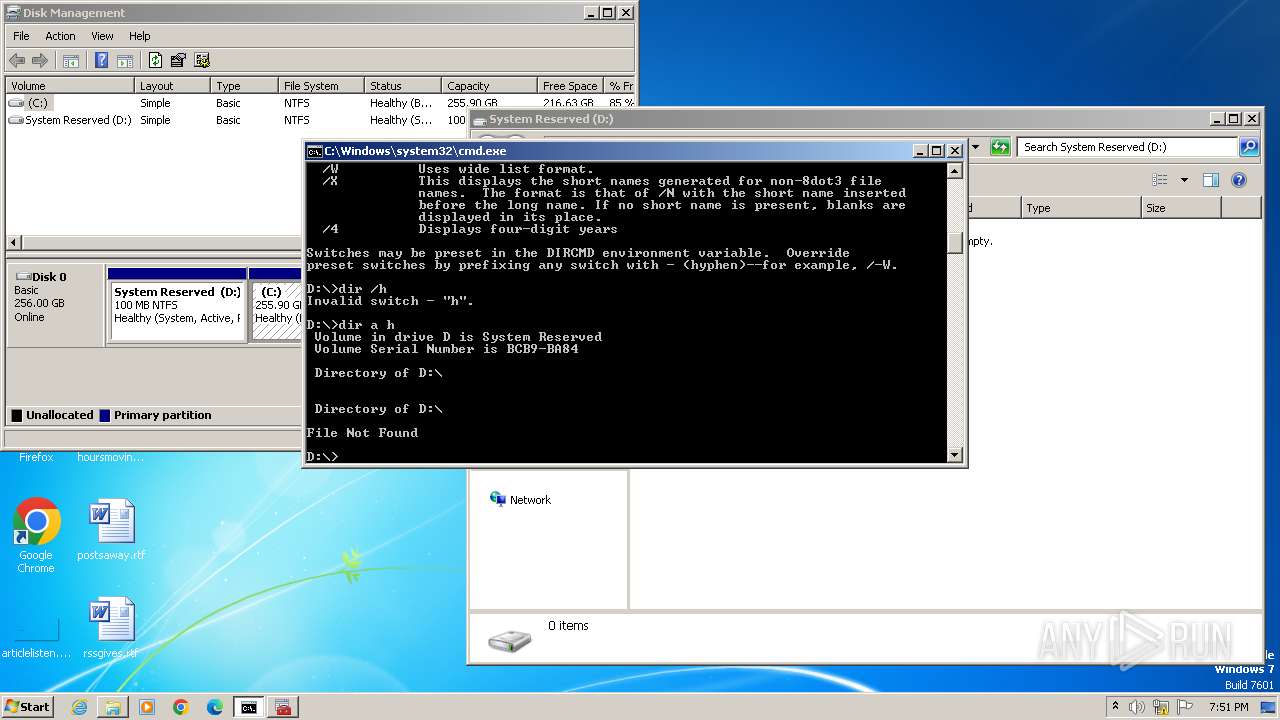
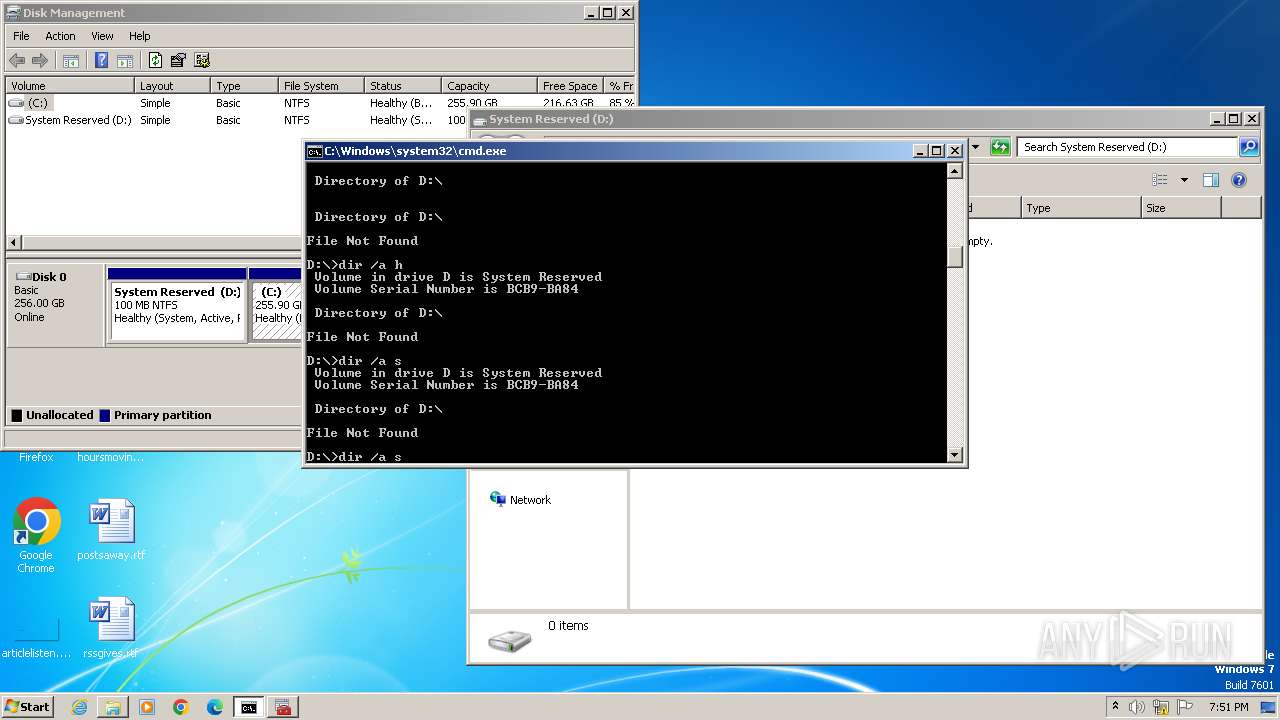
| File name: | notmyfault.exe |
| Full analysis: | https://app.any.run/tasks/4c57459c-b6bf-4fd4-bc2d-f8c041e4c987 |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2024, 19:50:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 833D5BBDF80D17A384E9B27798EA4D6C |
| SHA1: | 4AB55A97E76FD2CDB55ED305C984D87E9A06B1B1 |
| SHA256: | 41DDB886060471D702693CBFF1E7AA73C8ADA5B29D9EE313DE9972AB663A100D |
| SSDEEP: | 6144:whvkHmbGp7MCvRDlfJHbwZCjO0fNg1iyk:whMGbGlR5Pm1i/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- vds.exe (PID: 2648)
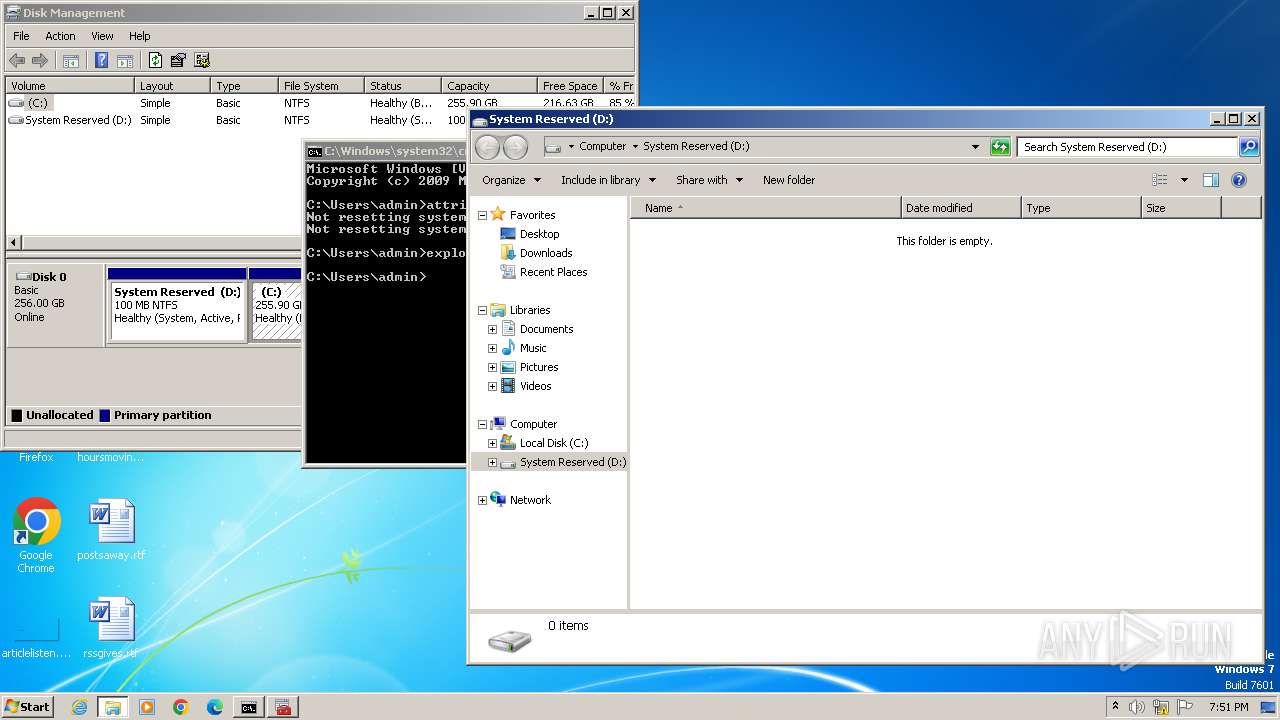
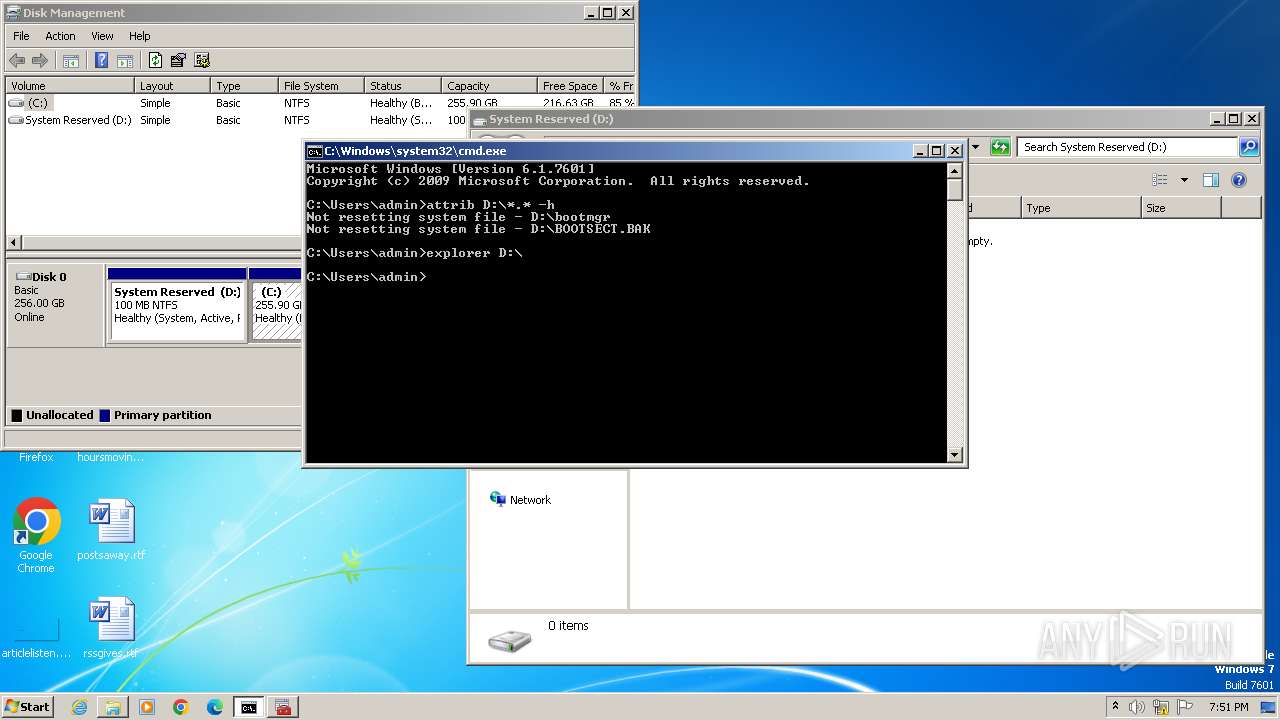
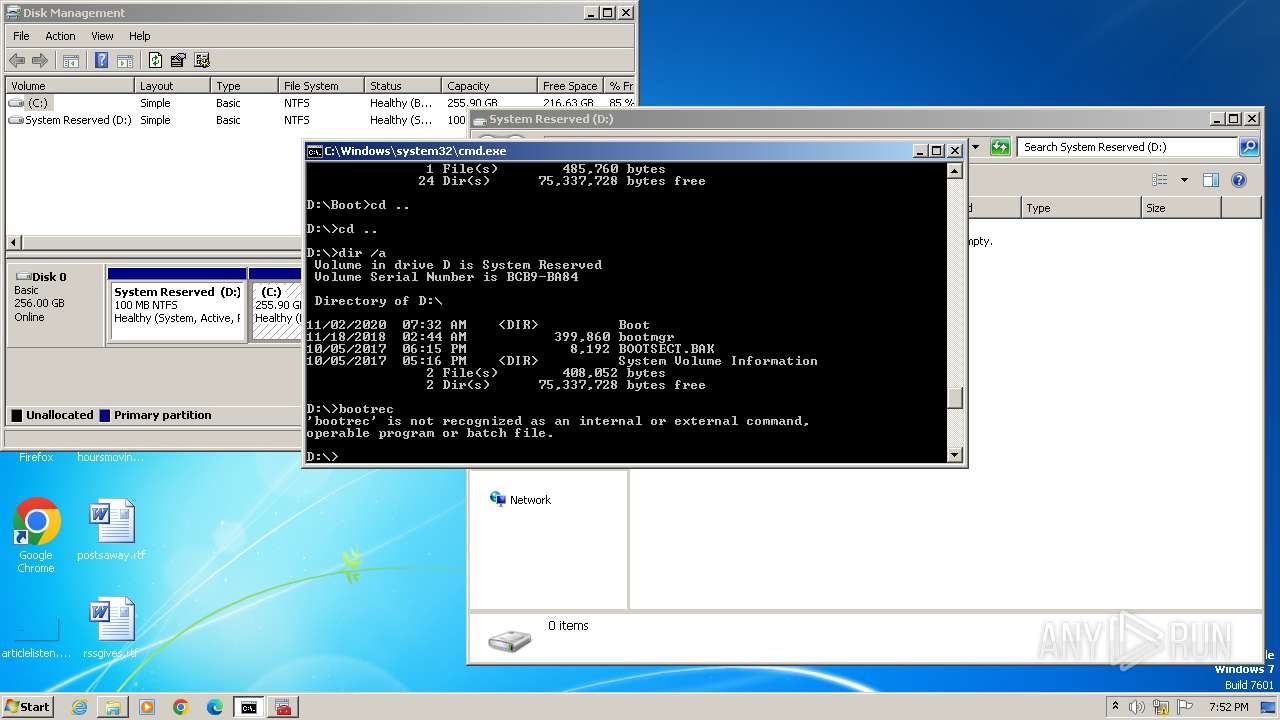
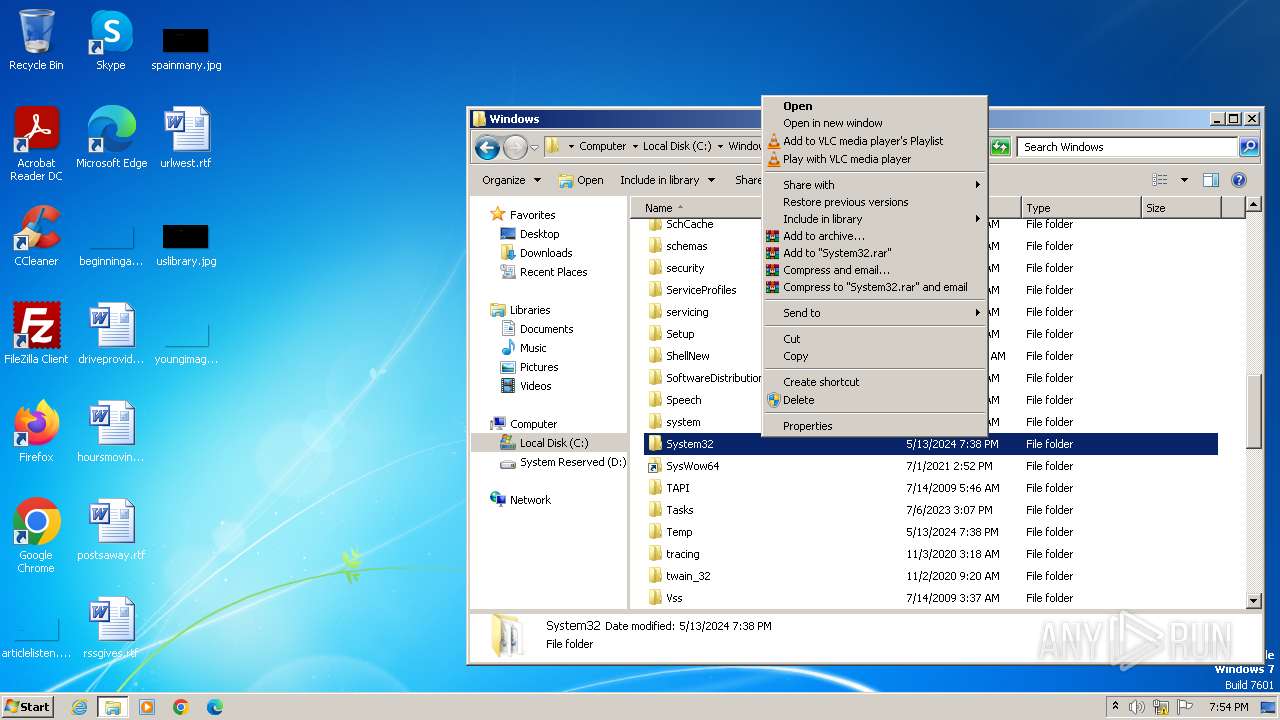
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2244)
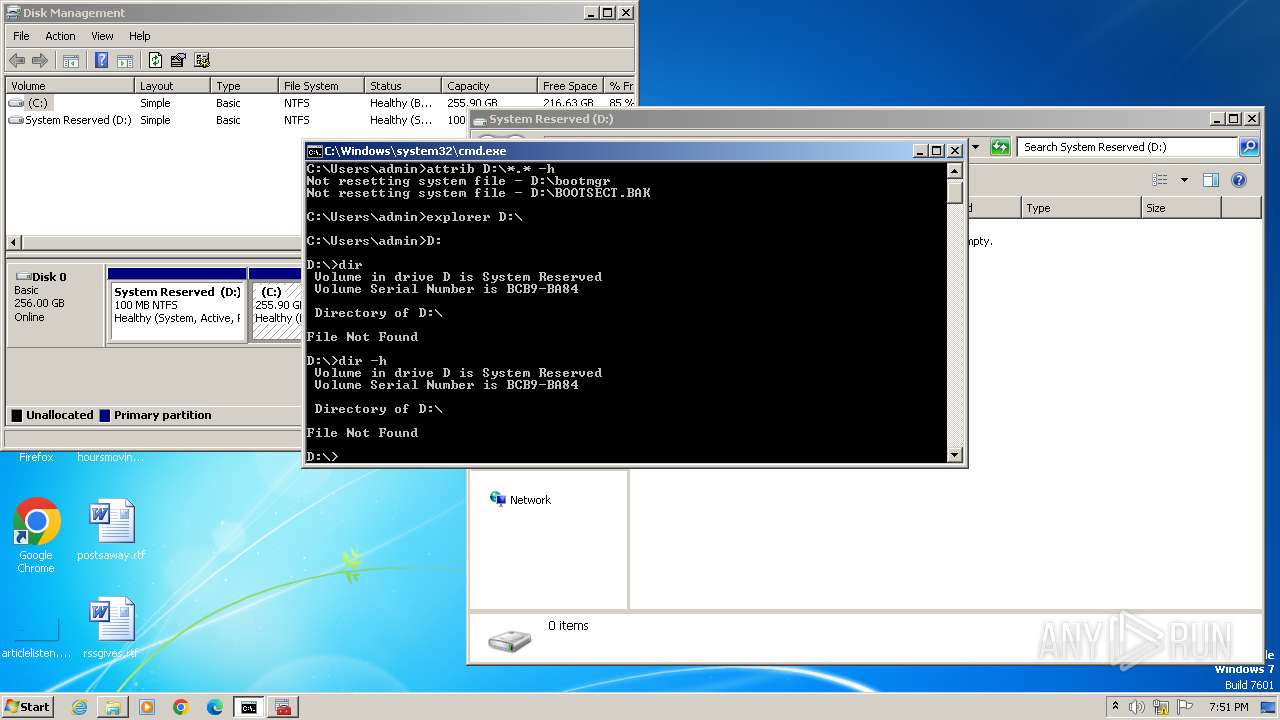
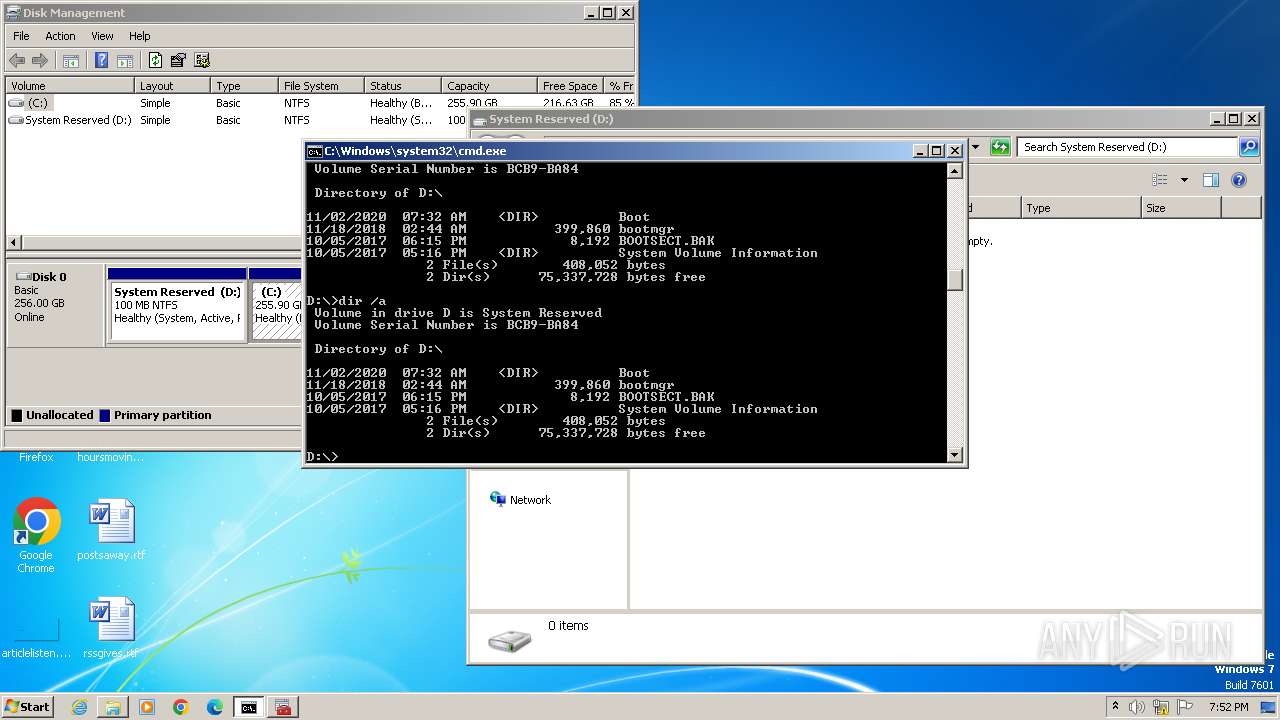
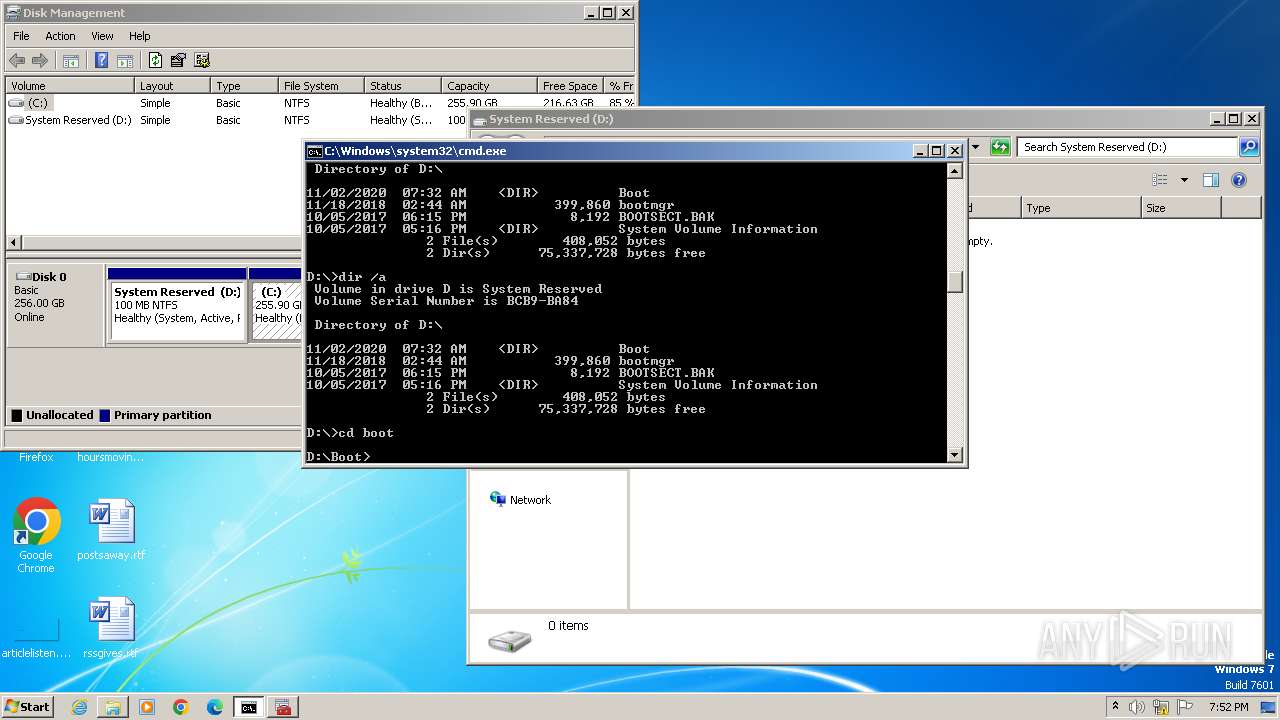
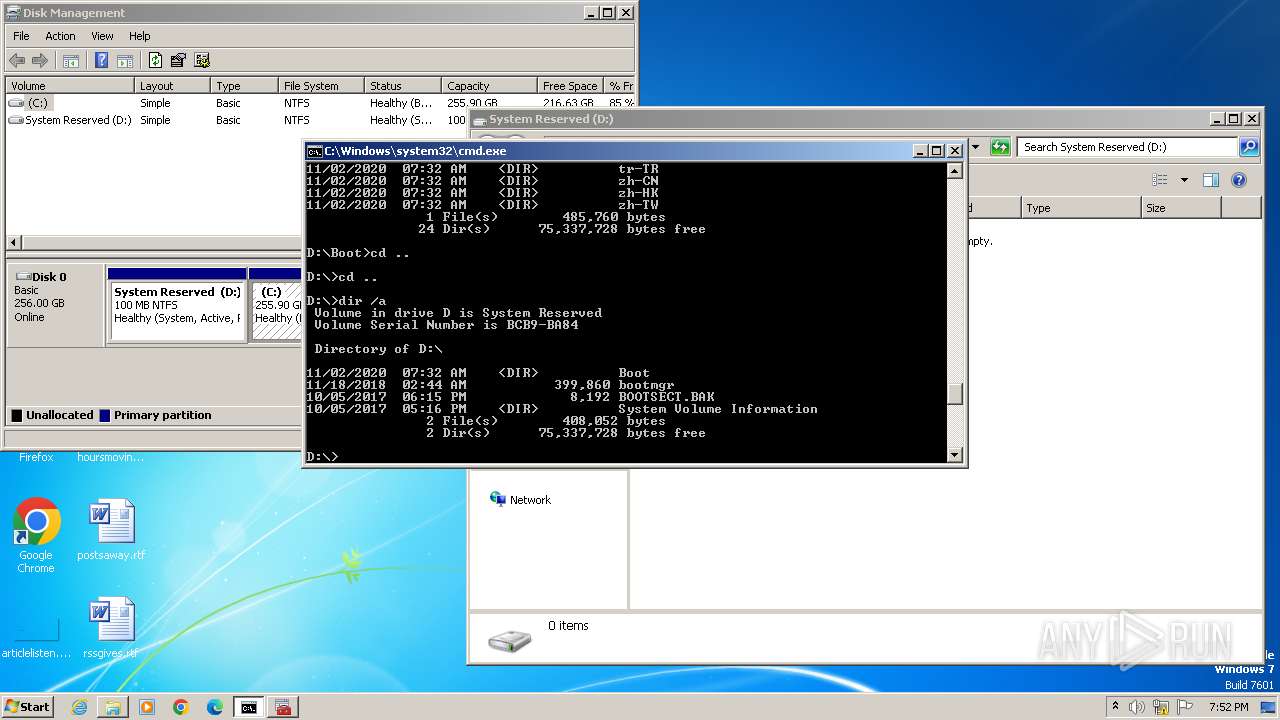
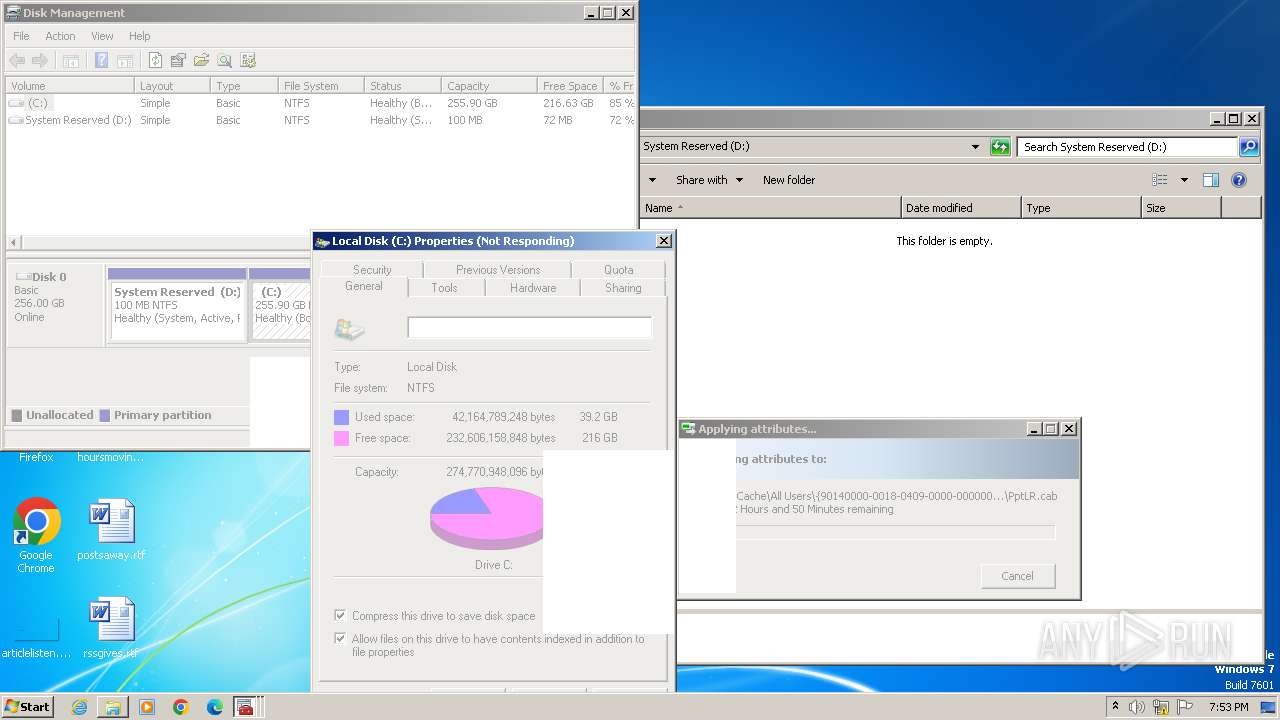
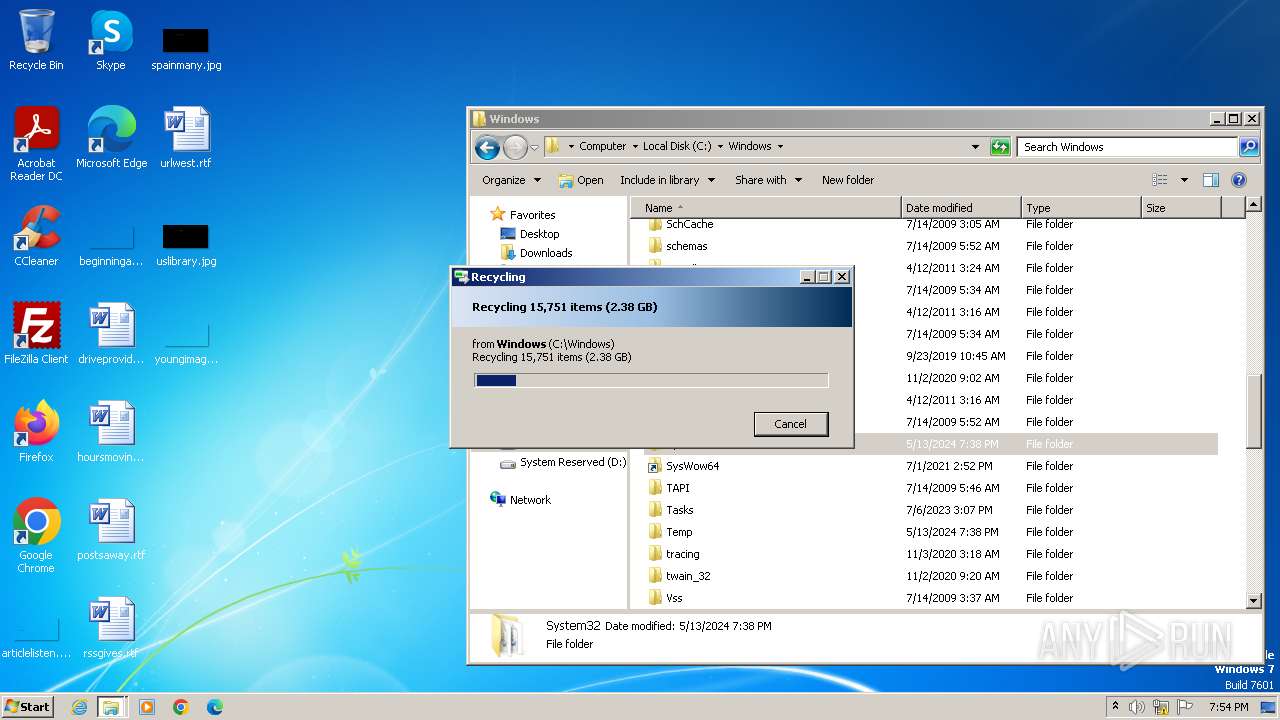
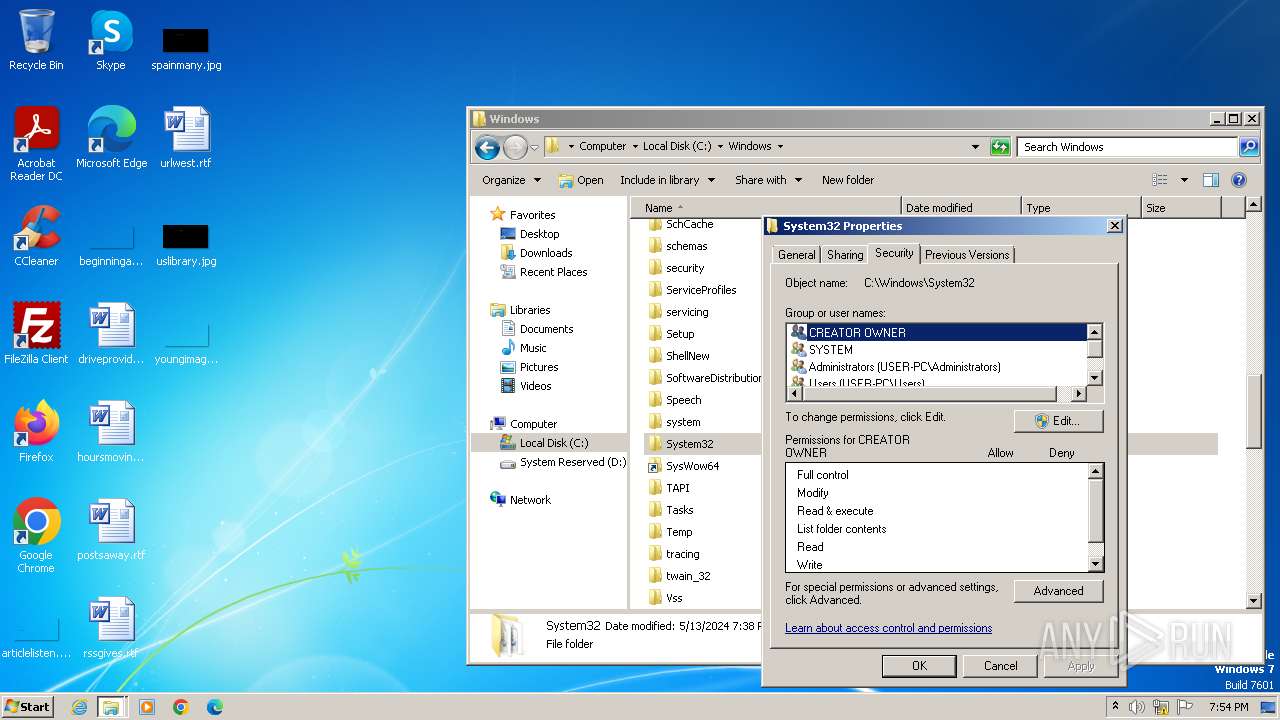
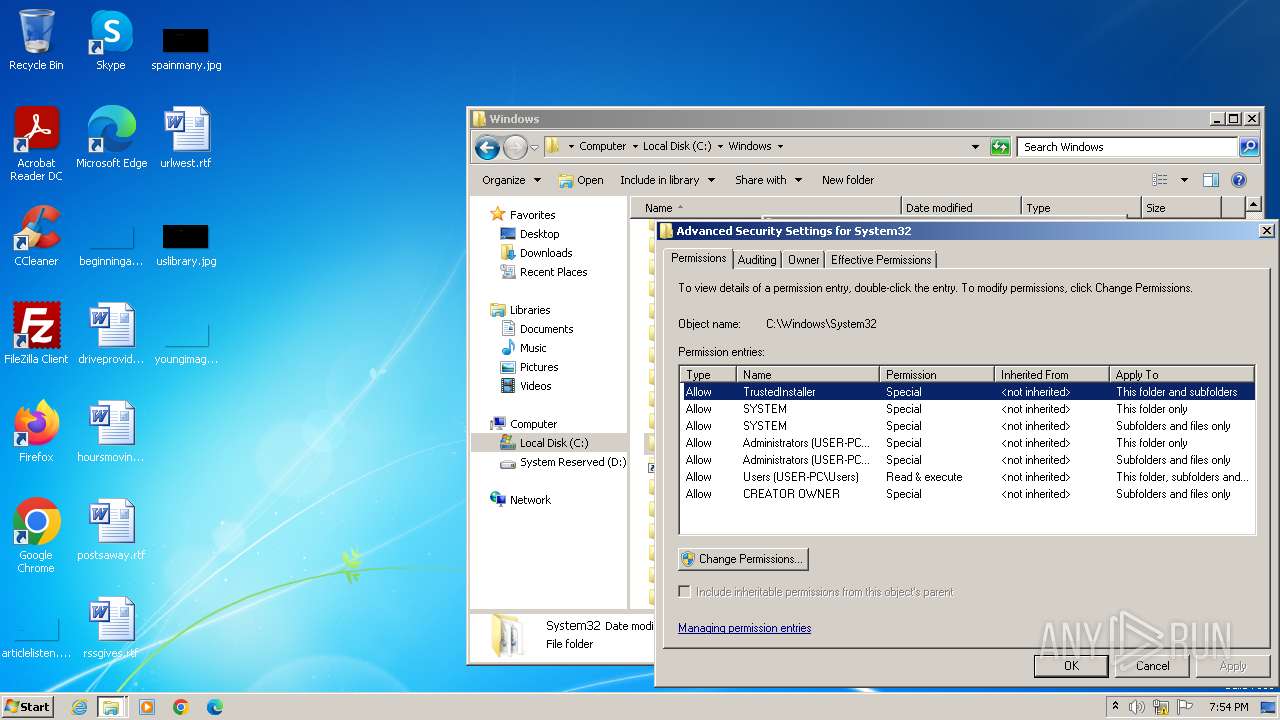
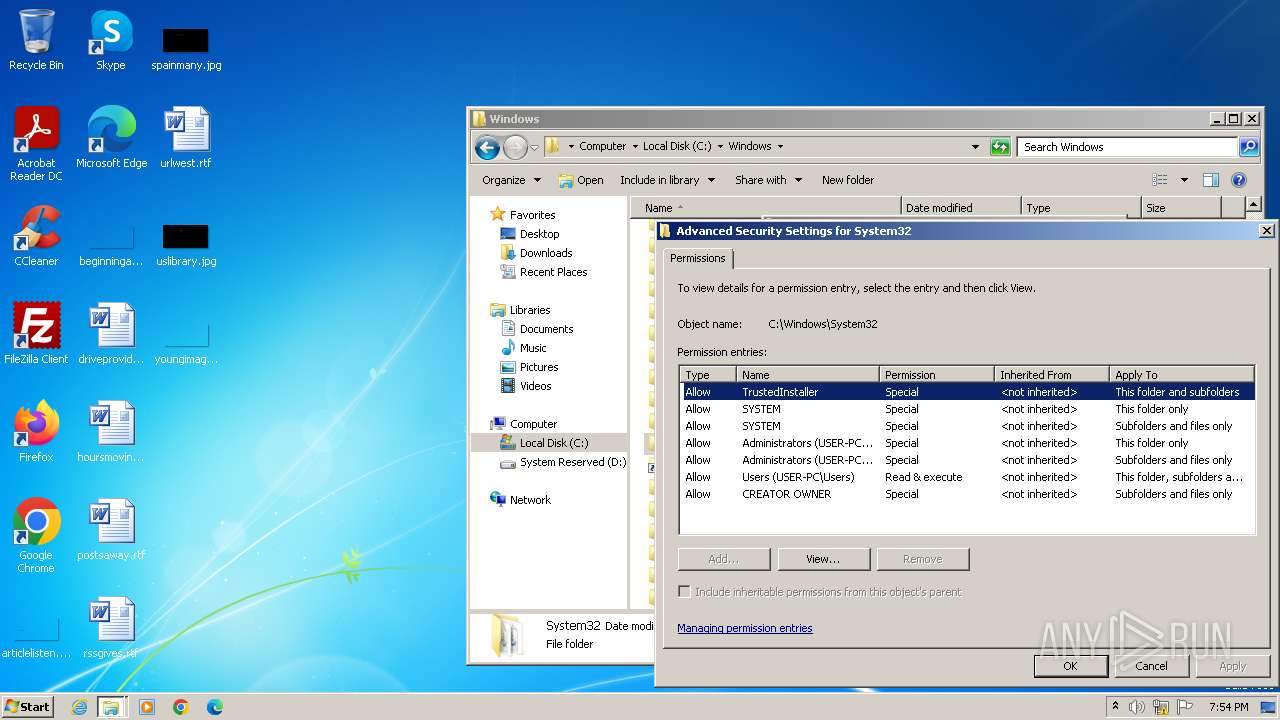
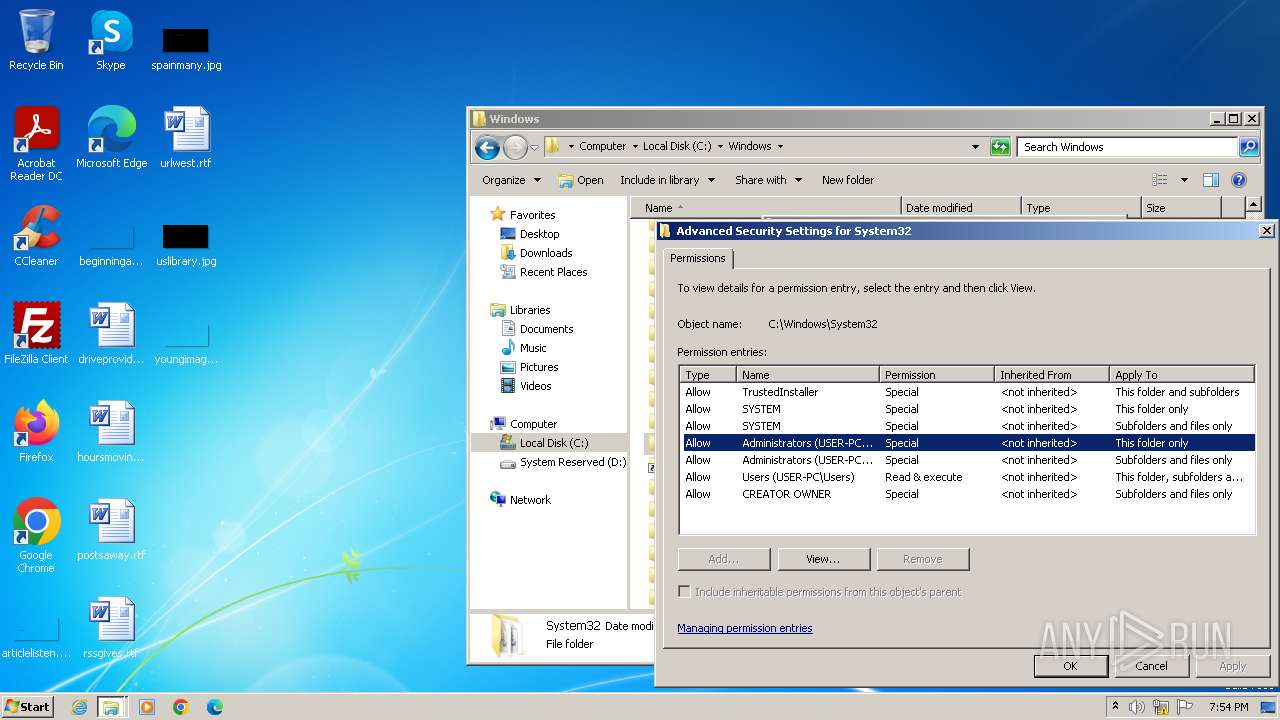
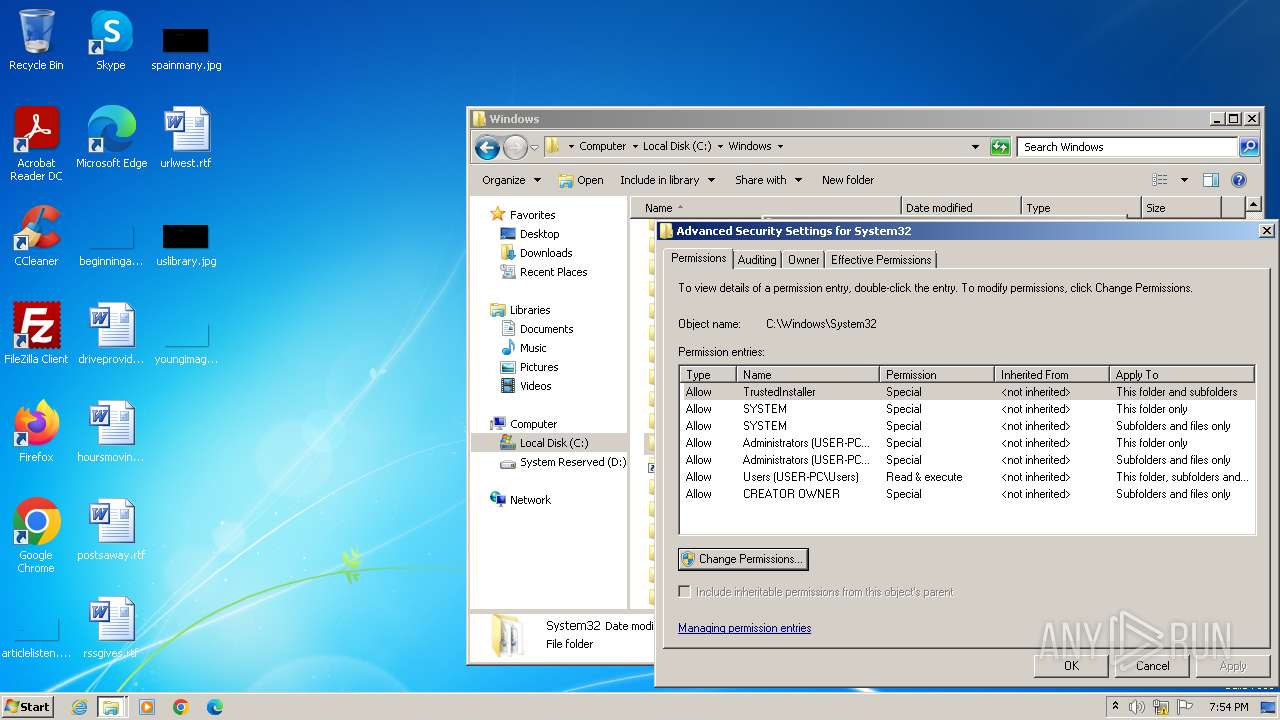
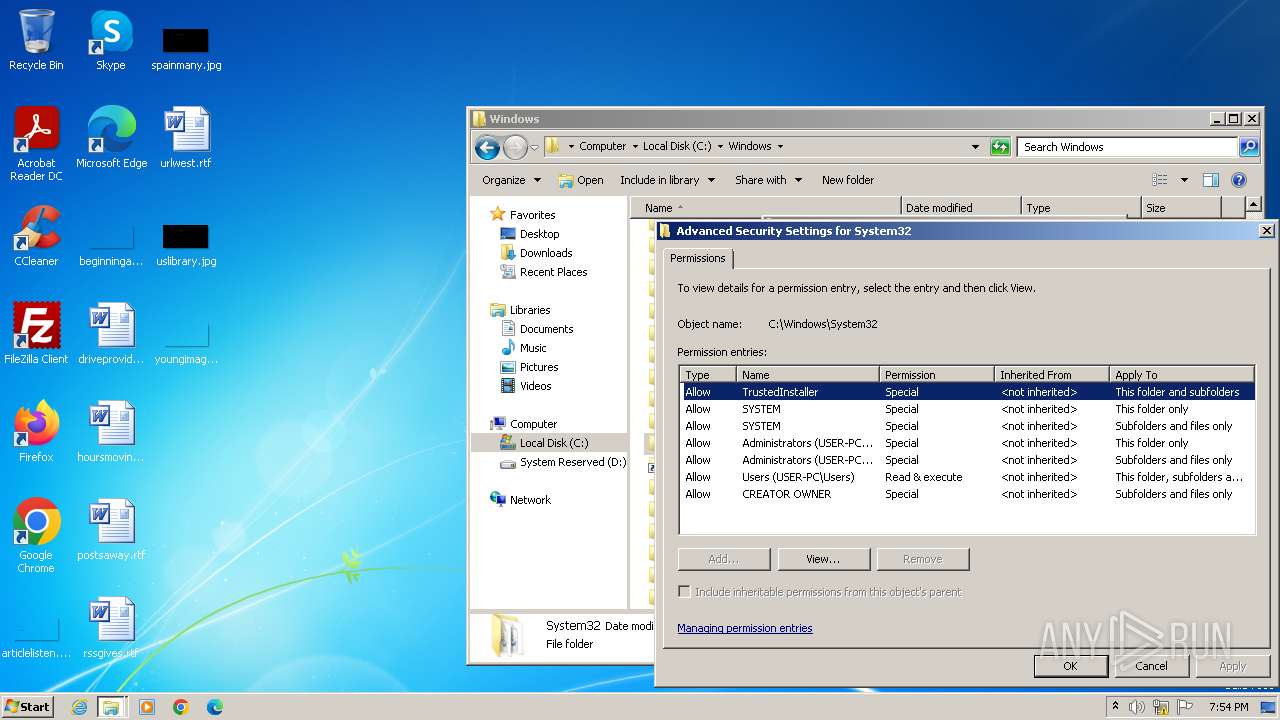
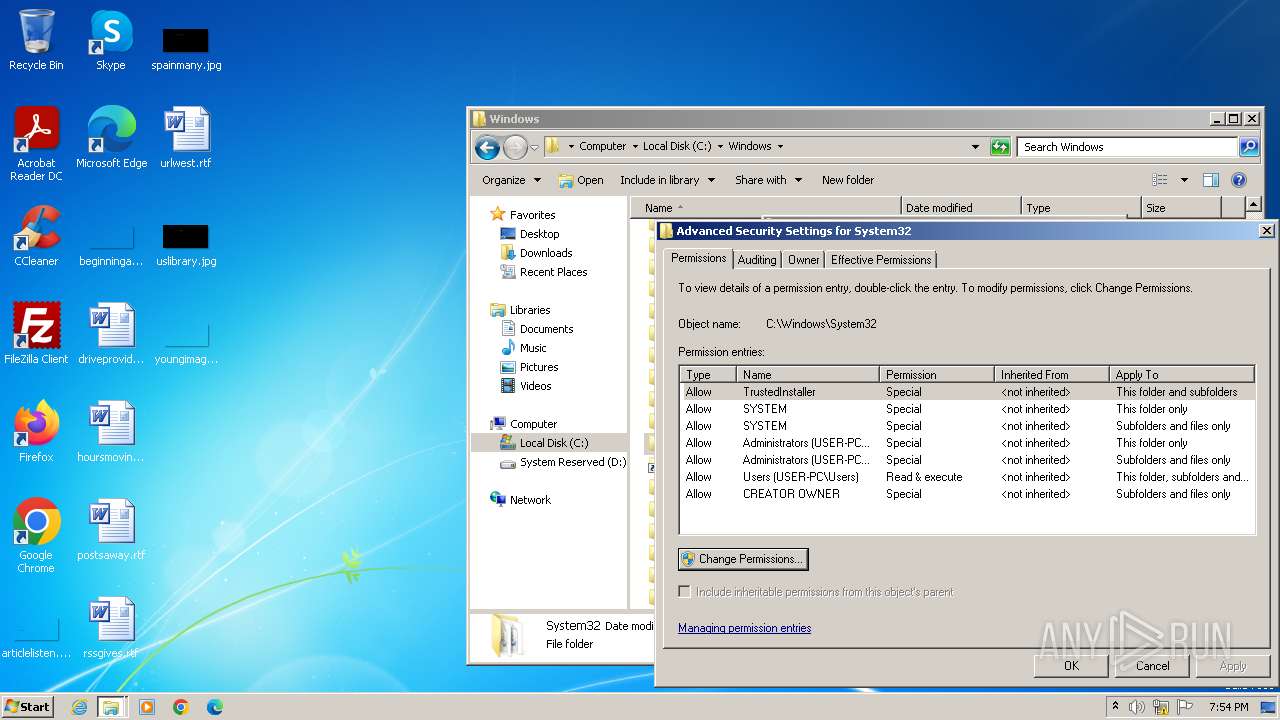
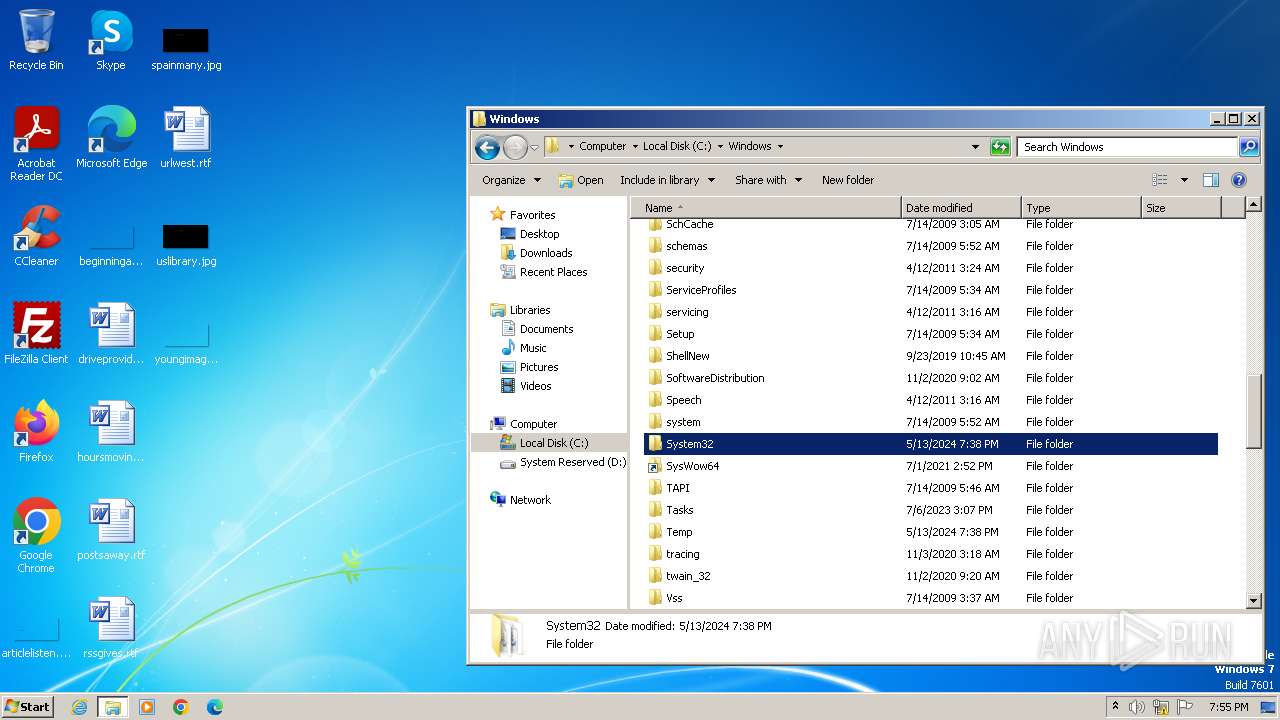
Creates file in the systems drive root
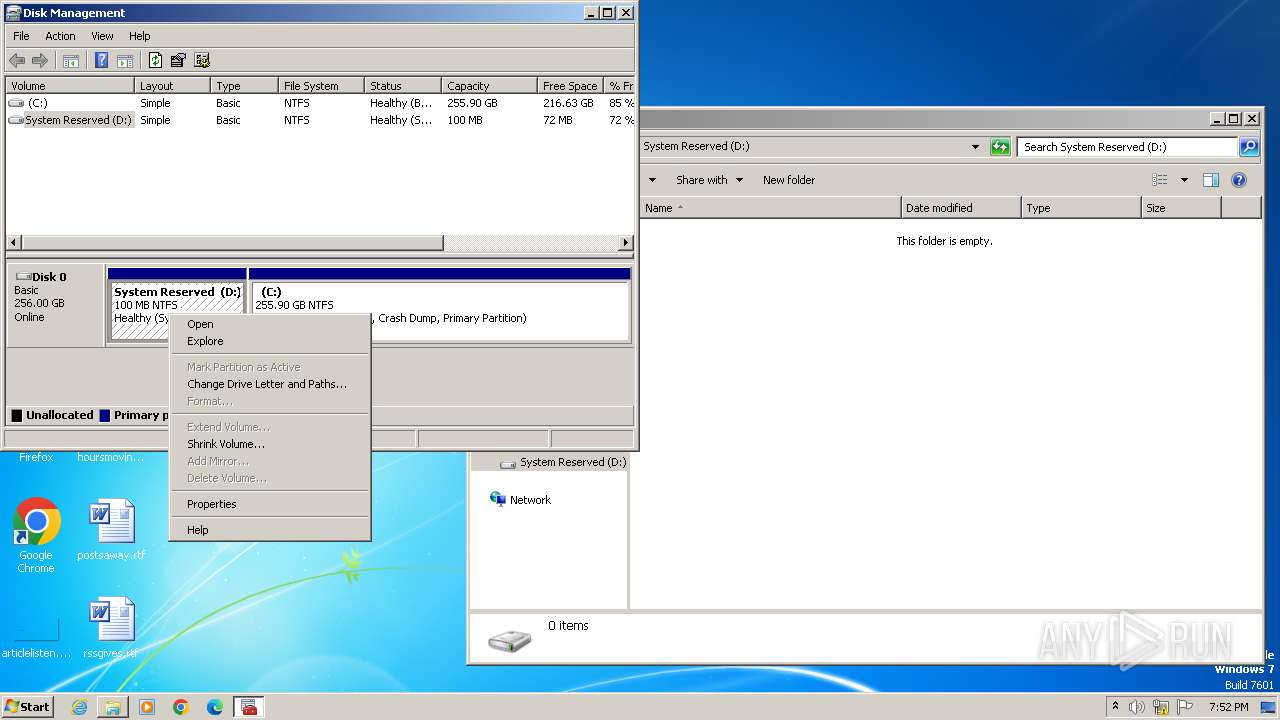
- mmc.exe (PID: 3104)
- explorer.exe (PID: 3380)
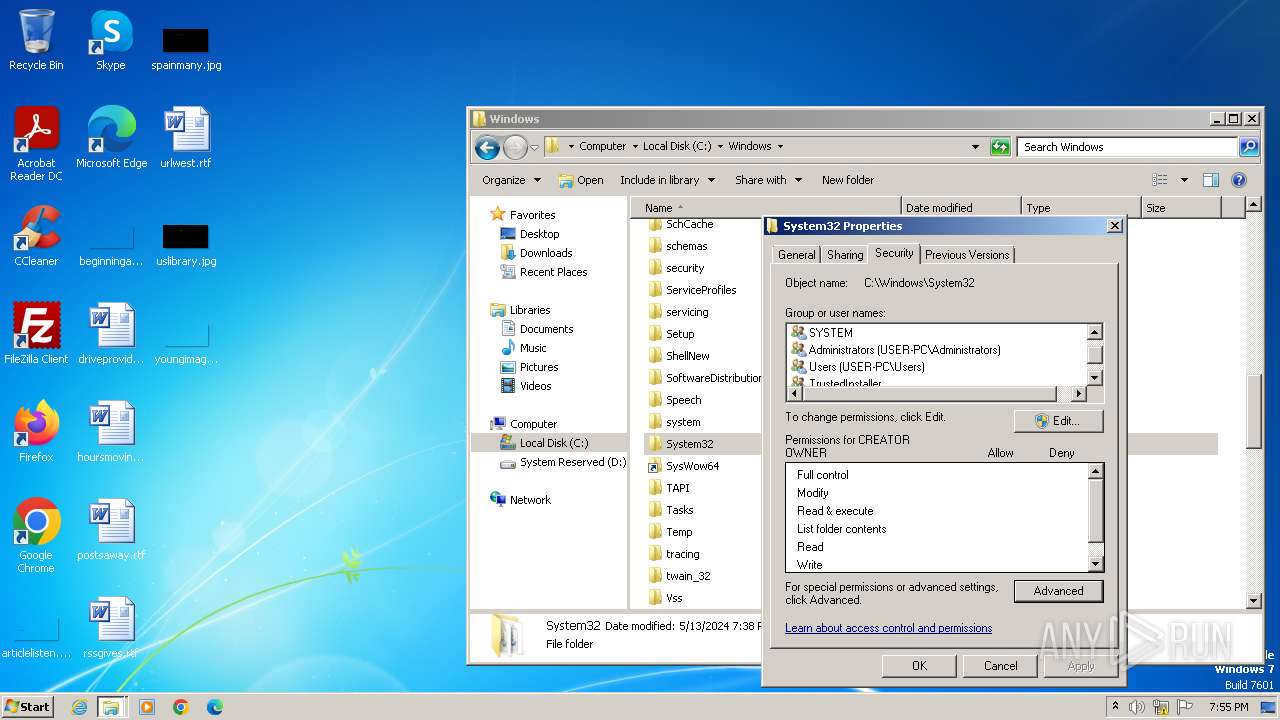
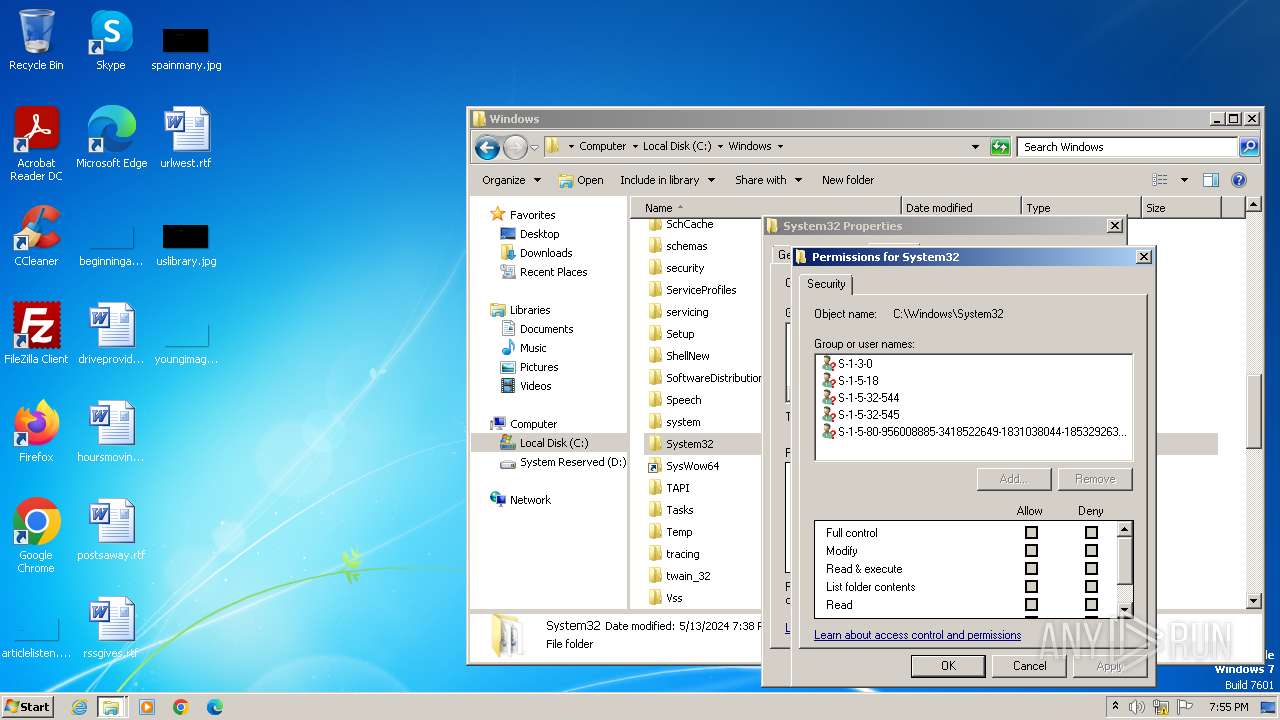
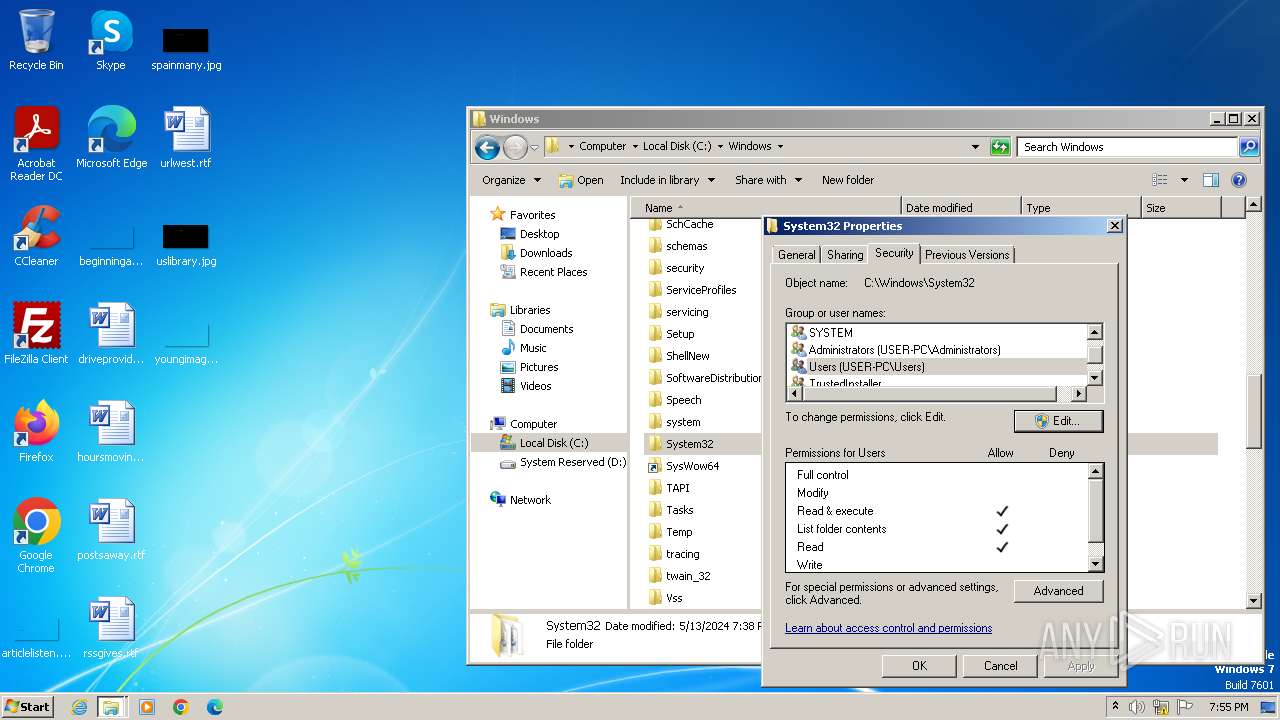
Detected use of alternative data streams (AltDS)
- mmc.exe (PID: 3104)
Write to the desktop.ini file (may be used to cloak folders)
- mmc.exe (PID: 3104)
The process checks if it is being run in the virtual environment
- explorer.exe (PID: 3380)
INFO
Reads Environment values
- notmyfault.exe (PID: 1740)
The sample compiled with english language support
- notmyfault.exe (PID: 1740)
Reads product name
- notmyfault.exe (PID: 1740)
Manual execution by a user
- cmd.exe (PID: 2244)
- mmc.exe (PID: 580)
- mmc.exe (PID: 3104)
Checks supported languages
- notmyfault.exe (PID: 1740)
Reads security settings of Internet Explorer
- explorer.exe (PID: 3380)
Reads the Internet Settings
- explorer.exe (PID: 3380)
Checks transactions between databases Windows and Oracle
- explorer.exe (PID: 3380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:29 16:22:37+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 132096 |
| InitializedDataSize: | 165888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3fdb |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.21.0.0 |
| ProductVersionNumber: | 4.21.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Driver Bug Test Program |
| FileVersion: | 4.21 |
| InternalName: | Sysinternals NotMyfault |
| LegalCopyright: | Copyright (C) 2002-2022 Mark Russinovich |
| OriginalFileName: | NotMyfault.exe |
| ProductName: | Sysinternals NotMyfault |
| ProductVersion: | 4.21 |
Total processes
71
Monitored processes
17
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\system32\DllHost.exe /Processid:{1F2E5C40-9550-11CE-99D2-00AA006E086C} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
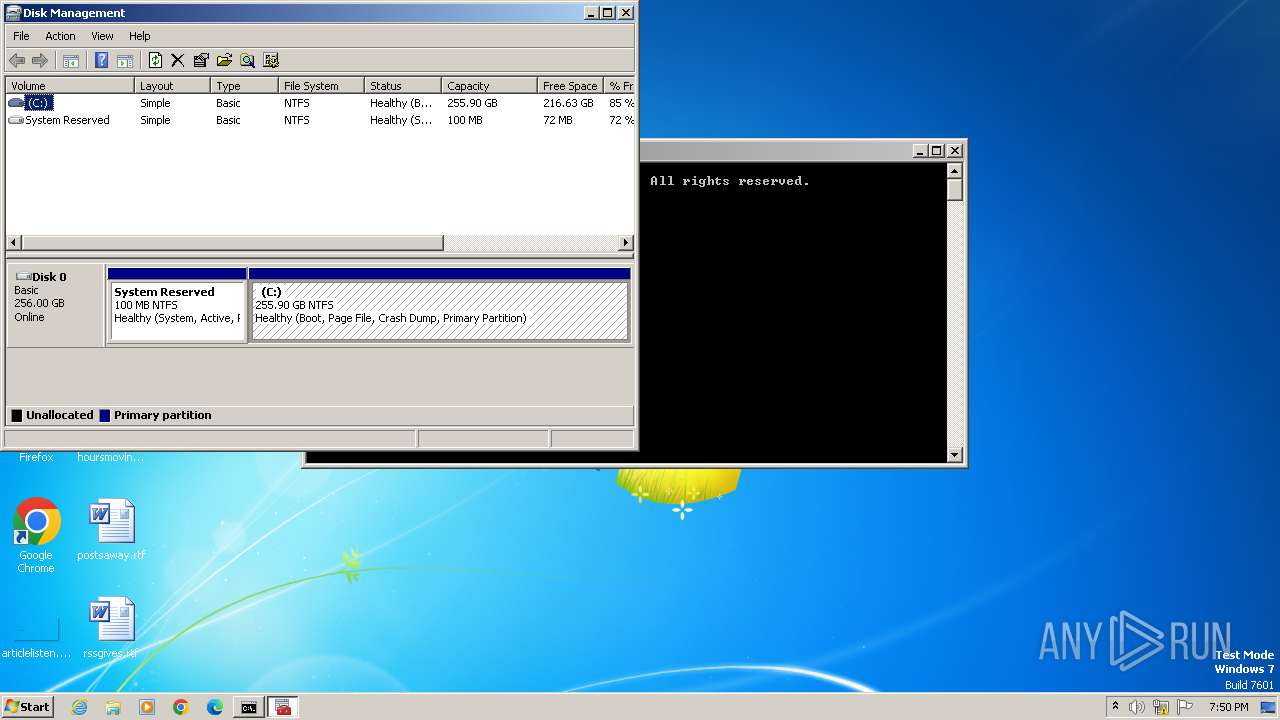
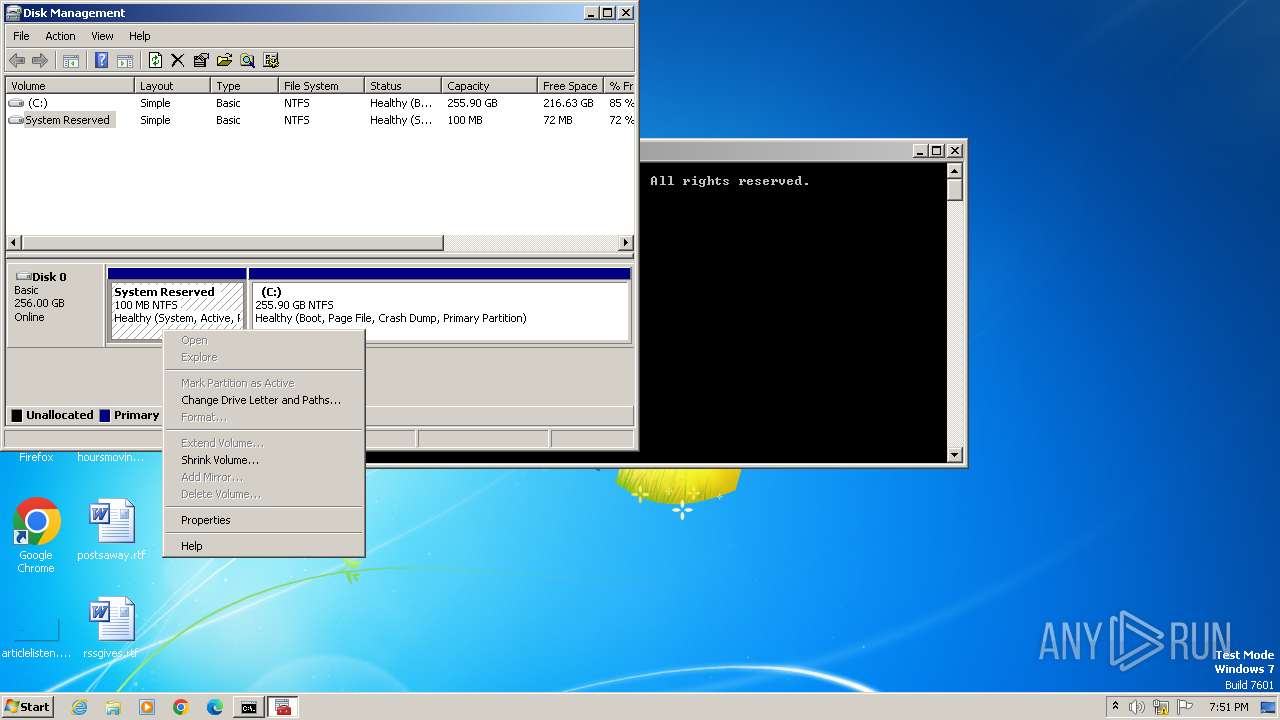
| 580 | "C:\Windows\system32\mmc.exe" C:\Windows\system32\diskmgmt.msc | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\AppData\Local\Temp\notmyfault.exe" | C:\Users\admin\AppData\Local\Temp\notmyfault.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Driver Bug Test Program Exit code: 1 Version: 4.21 Modules
| |||||||||||||||
| 1848 | "C:\Users\admin\AppData\Local\Temp\notmyfault.exe" | C:\Users\admin\AppData\Local\Temp\notmyfault.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Driver Bug Test Program Exit code: 3221226540 Version: 4.21 Modules
| |||||||||||||||
| 1916 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1932 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1992 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2000 | explorer D:\ | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2384 | C:\Windows\system32\DllHost.exe /Processid:{1F2E5C40-9550-11CE-99D2-00AA006E086C} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 211
Read events
9 058
Write events
150
Delete events
3
Modification events
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0100000002000000070000000E000000000000000B000000060000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1 |
| Operation: | write | Name: | 1 |
Value: 19002F443A5C000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3380) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\1 |
| Operation: | delete value | Name: | MRUList |
Value: | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3104 | mmc.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963}\$RECYCLE.BIN\S-1-5-21-1302019708-1500728564-335382590-1000\desktop.ini | text | |
MD5:AD0B0B4416F06AF436328A3C12DC491B | SHA256:23521DE51CA1DB2BC7B18E41DE7693542235284667BF85F6C31902547A947416 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |