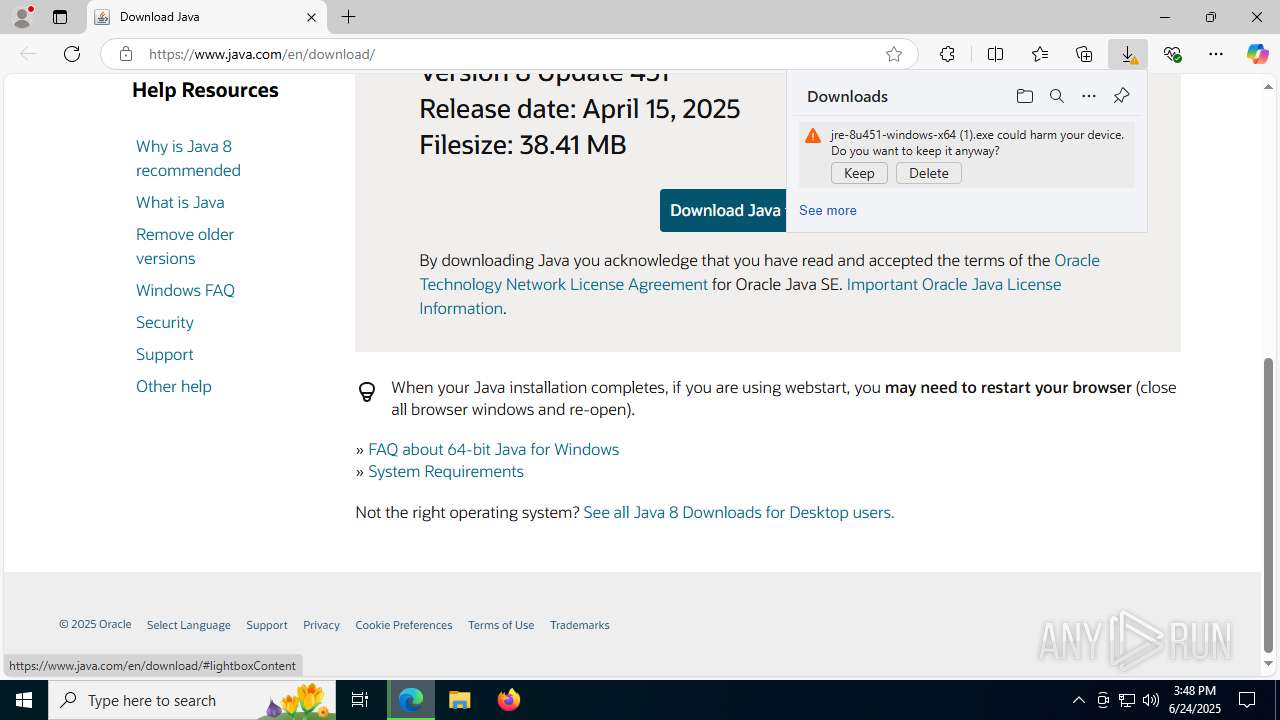
| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/b369c563-e416-40bc-a2fd-3109842b82fe |
| Verdict: | Malicious activity |
| Analysis date: | June 24, 2025, 15:45:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | E5ADEB5BA182A336EC298E591D1A08C2 |
| SHA1: | BFBD753CE7B0730CEDAEC6B70B642EE724056949 |
| SHA256: | 41D35E55001CA6C407BF37D5E49D504DFBF0A8F82C29CDCCCDB92C5E1A1DF2C1 |
| SSDEEP: | 196608:OKYkWxr3DrZXTVorXeFaDNmUcHUv3B2XtJx9h:OKRe3DrZXK2ahcHUvQtJb |
MALICIOUS
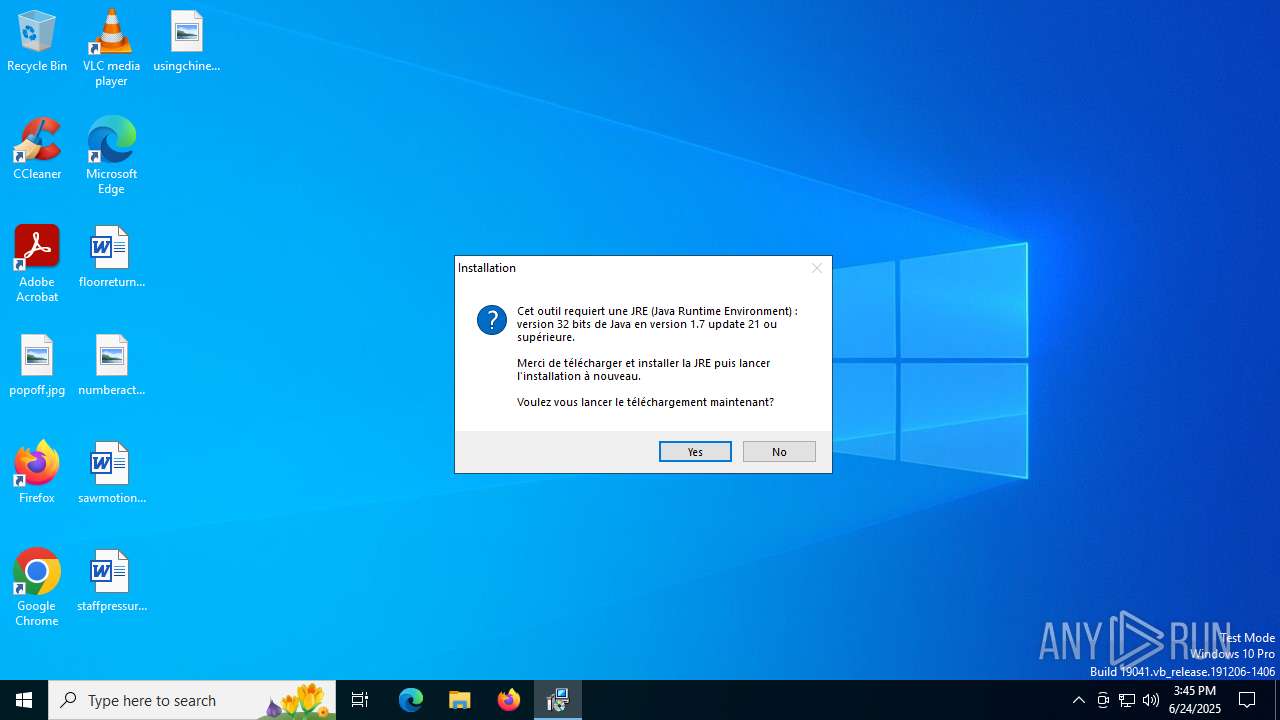
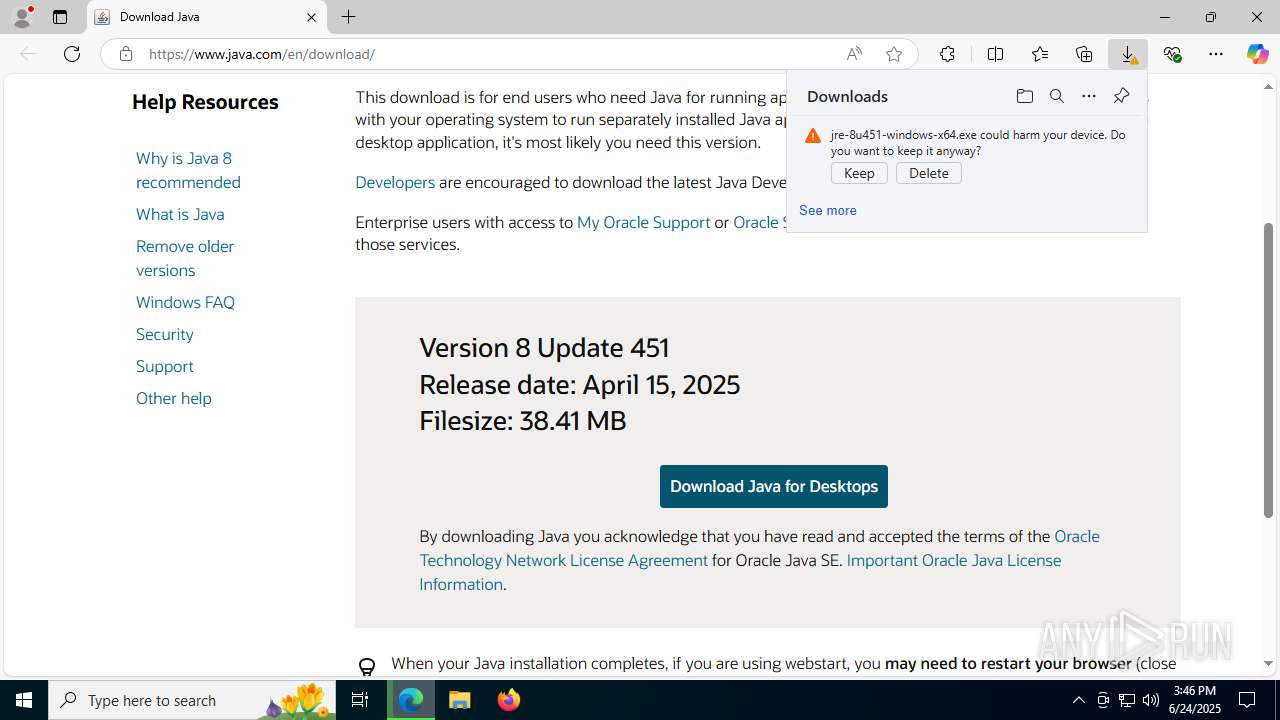
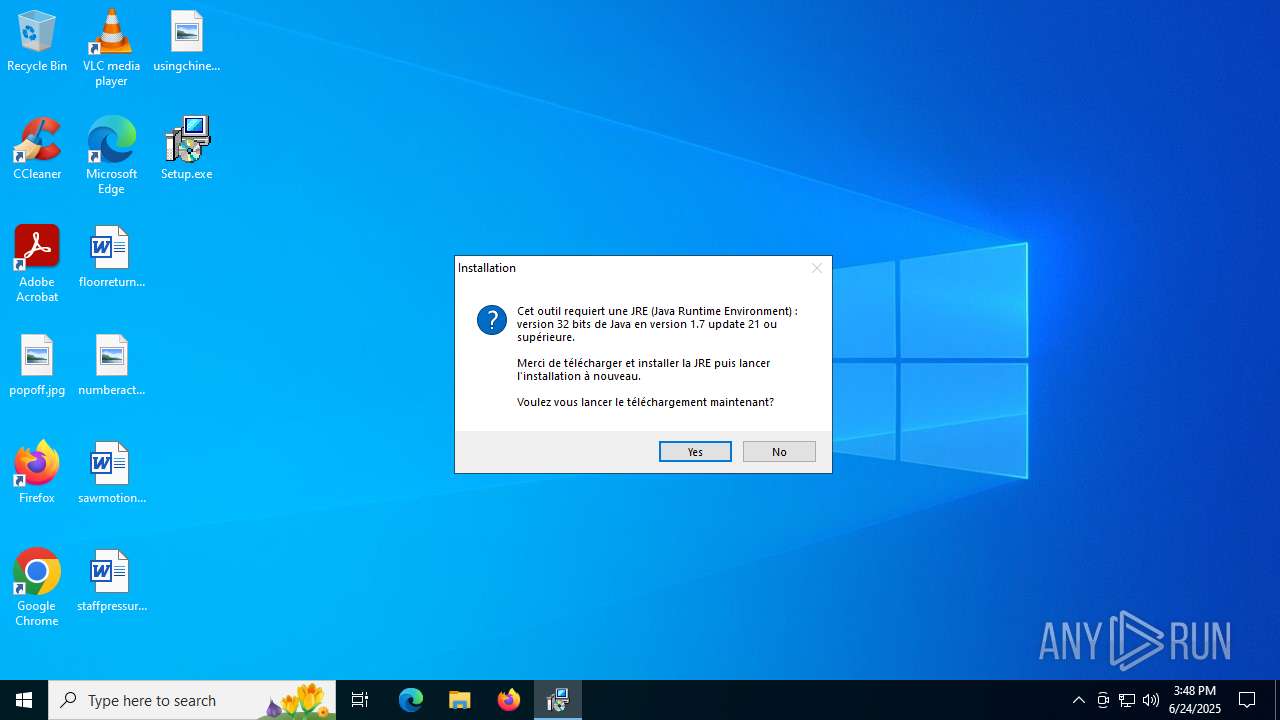
Executing a file with an untrusted certificate
- Setup.exe (PID: 2996)
- Setup.exe (PID: 2780)
- Setup.exe (PID: 2732)
- Setup.exe (PID: 1964)
SUSPICIOUS
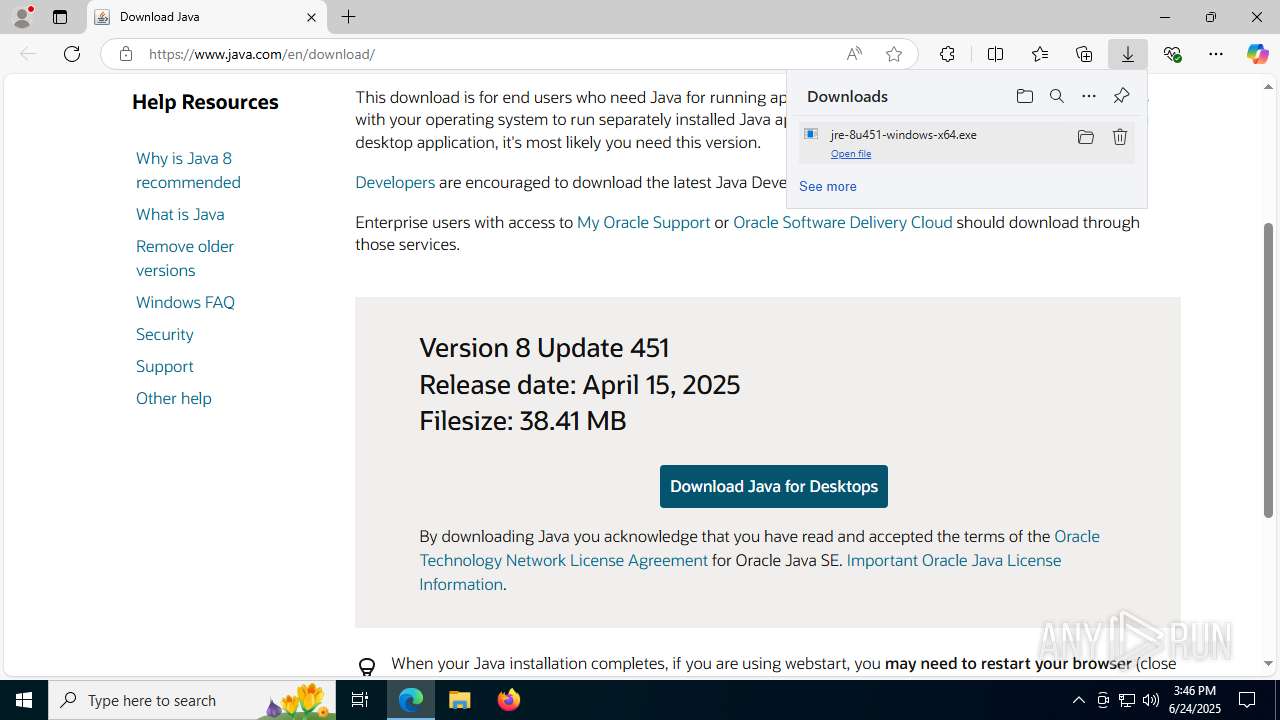
Executable content was dropped or overwritten
- Setup.exe (PID: 2996)
- Setup.exe (PID: 2780)
- Setup.tmp (PID: 5480)
- installer.exe (PID: 7528)
- jre-8u451-windows-x64.exe (PID: 7980)
- Setup.exe (PID: 1964)
- Setup.exe (PID: 2732)
- Setup.tmp (PID: 6700)
Reads the Windows owner or organization settings
- Setup.tmp (PID: 5480)
- msiexec.exe (PID: 8164)
- Setup.tmp (PID: 6700)
Reads security settings of Internet Explorer
- Setup.tmp (PID: 5480)
- Setup.tmp (PID: 2124)
- jre-8u451-windows-x64.exe (PID: 7980)
- installer.exe (PID: 7528)
- jp2launcher.exe (PID: 7688)
- jp2launcher.exe (PID: 4444)
- Setup.tmp (PID: 5628)
- Setup.tmp (PID: 6700)
Reads Microsoft Outlook installation path
- jre-8u451-windows-x64.exe (PID: 7980)
Reads Internet Explorer settings
- jre-8u451-windows-x64.exe (PID: 7980)
Checks for Java to be installed
- jre-8u451-windows-x64.exe (PID: 7980)
- msiexec.exe (PID: 7384)
- msiexec.exe (PID: 8164)
- installer.exe (PID: 7528)
- jp2launcher.exe (PID: 7688)
- ssvagent.exe (PID: 2144)
- msiexec.exe (PID: 2464)
- jp2launcher.exe (PID: 4444)
- javaw.exe (PID: 6236)
Application launched itself
- msiexec.exe (PID: 8164)
Reads Mozilla Firefox installation path
- MSIE52D.tmp (PID: 7440)
- installer.exe (PID: 7528)
There is functionality for taking screenshot (YARA)
- jre-8u451-windows-x64.exe (PID: 7980)
Process drops legitimate windows executable
- msiexec.exe (PID: 8164)
The process drops C-runtime libraries
- msiexec.exe (PID: 8164)
Creates/Modifies COM task schedule object
- ssvagent.exe (PID: 2144)
- installer.exe (PID: 7528)
INFO
Checks supported languages
- Setup.tmp (PID: 2124)
- Setup.exe (PID: 2996)
- Setup.tmp (PID: 5480)
- identity_helper.exe (PID: 7204)
- jre-8u451-windows-x64.exe (PID: 7956)
- jre-8u451-windows-x64.exe (PID: 7980)
- msiexec.exe (PID: 8164)
- MSIE52D.tmp (PID: 7440)
- msiexec.exe (PID: 7384)
- installer.exe (PID: 7528)
- javaw.exe (PID: 7552)
- jaureg.exe (PID: 4080)
- identity_helper.exe (PID: 7568)
- ssvagent.exe (PID: 2144)
- javaws.exe (PID: 7672)
- jp2launcher.exe (PID: 7688)
- jp2launcher.exe (PID: 4444)
- Setup.exe (PID: 2780)
- javaws.exe (PID: 5712)
- msiexec.exe (PID: 2464)
- msiexec.exe (PID: 2680)
- javaw.exe (PID: 6236)
- javaw.exe (PID: 4120)
- javaw.exe (PID: 5540)
- msiexec.exe (PID: 7188)
- msiexec.exe (PID: 2864)
- Setup.exe (PID: 1964)
- Setup.tmp (PID: 6700)
- Setup.exe (PID: 2732)
- Setup.tmp (PID: 5628)
Application launched itself
- msedge.exe (PID: 2528)
- msedge.exe (PID: 4412)
- msedge.exe (PID: 4112)
- msedge.exe (PID: 7800)
- msedge.exe (PID: 5012)
Create files in a temporary directory
- Setup.exe (PID: 2780)
- Setup.tmp (PID: 5480)
- jre-8u451-windows-x64.exe (PID: 7956)
- MSIE52D.tmp (PID: 7440)
- javaw.exe (PID: 7552)
- Setup.exe (PID: 2996)
- jp2launcher.exe (PID: 7688)
- jp2launcher.exe (PID: 4444)
- javaw.exe (PID: 5540)
- Setup.tmp (PID: 6700)
- Setup.exe (PID: 2732)
- Setup.exe (PID: 1964)
Reads the computer name
- Setup.tmp (PID: 5480)
- Setup.tmp (PID: 2124)
- identity_helper.exe (PID: 7204)
- jre-8u451-windows-x64.exe (PID: 7956)
- jre-8u451-windows-x64.exe (PID: 7980)
- msiexec.exe (PID: 8164)
- msiexec.exe (PID: 7384)
- MSIE52D.tmp (PID: 7440)
- identity_helper.exe (PID: 7568)
- installer.exe (PID: 7528)
- jp2launcher.exe (PID: 7688)
- javaws.exe (PID: 7672)
- javaws.exe (PID: 5712)
- msiexec.exe (PID: 2680)
- jp2launcher.exe (PID: 4444)
- msiexec.exe (PID: 2464)
- javaw.exe (PID: 6236)
- javaw.exe (PID: 4120)
- msiexec.exe (PID: 7188)
- msiexec.exe (PID: 2864)
- javaw.exe (PID: 5540)
- Setup.tmp (PID: 6700)
- Setup.tmp (PID: 5628)
Manual execution by a user
- msedge.exe (PID: 4112)
- Setup.exe (PID: 2732)
Reads Environment values
- identity_helper.exe (PID: 7204)
- jre-8u451-windows-x64.exe (PID: 7980)
- identity_helper.exe (PID: 7568)
Executable content was dropped or overwritten
- msedge.exe (PID: 4112)
- msiexec.exe (PID: 8164)
- msedge.exe (PID: 7800)
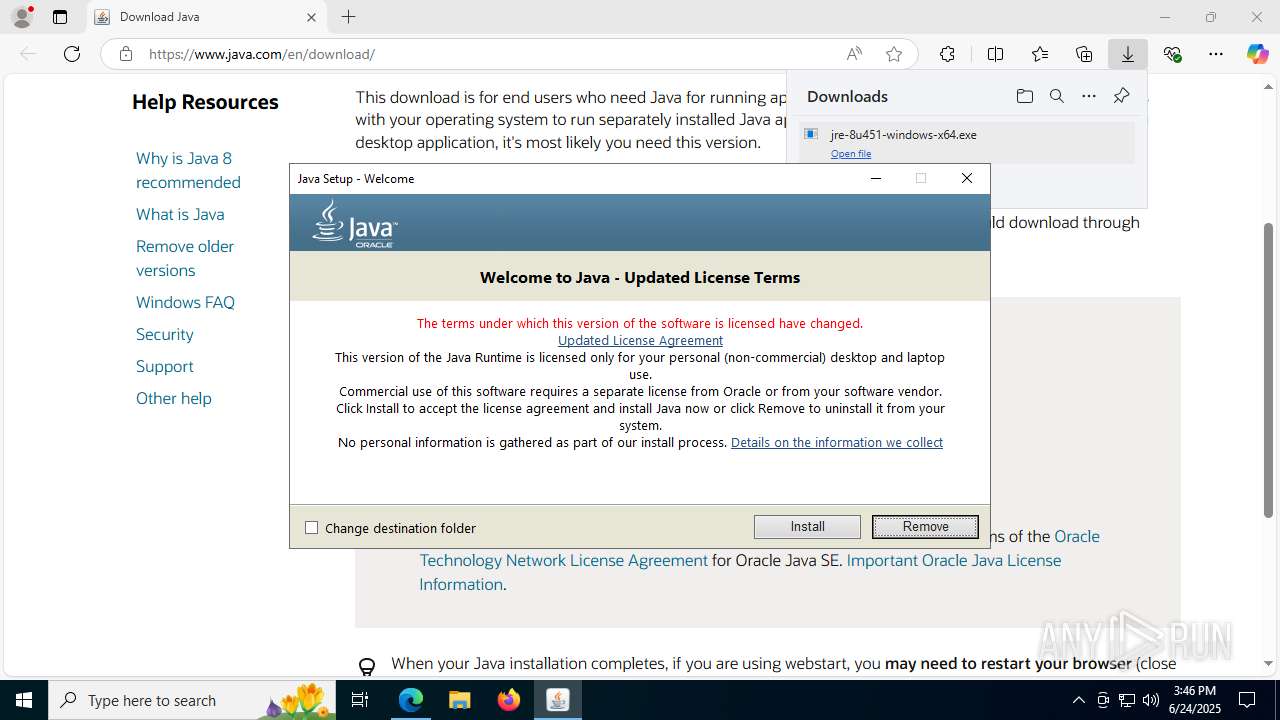
Java executable
- jre-8u451-windows-x64.exe (PID: 7956)
- jre-8u451-windows-x64.exe (PID: 7980)
- jre-8u451-windows-x64.exe (PID: 7908)
- MSIE52D.tmp (PID: 7440)
- installer.exe (PID: 7528)
Reads the machine GUID from the registry
- jre-8u451-windows-x64.exe (PID: 7980)
- msiexec.exe (PID: 8164)
Reads the software policy settings
- jre-8u451-windows-x64.exe (PID: 7980)
- msiexec.exe (PID: 8164)
- slui.exe (PID: 7136)
Checks proxy server information
- jre-8u451-windows-x64.exe (PID: 7980)
- jp2launcher.exe (PID: 7688)
- jp2launcher.exe (PID: 4444)
- slui.exe (PID: 7136)
Creates files or folders in the user directory
- jre-8u451-windows-x64.exe (PID: 7980)
- msiexec.exe (PID: 8164)
The sample compiled with english language support
- msiexec.exe (PID: 8164)
- installer.exe (PID: 7528)
- jre-8u451-windows-x64.exe (PID: 7980)
Starts application with an unusual extension
- msiexec.exe (PID: 8164)
Reads CPU info
- msiexec.exe (PID: 8164)
Creates a software uninstall entry
- msiexec.exe (PID: 8164)
Creates files in the program directory
- installer.exe (PID: 7528)
- javaw.exe (PID: 7552)
JAVA mutex has been found
- jp2launcher.exe (PID: 7688)
- jp2launcher.exe (PID: 4444)
- msiexec.exe (PID: 2680)
- msiexec.exe (PID: 7188)
Process checks computer location settings
- Setup.tmp (PID: 2124)
- Setup.tmp (PID: 5628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41472 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa98 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | ATEXO |
| FileDescription: | Atexo Sign Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | Atexo Sign |
| ProductVersion: | 4 |
Total processes
232
Monitored processes
93
Malicious processes
11
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2732,i,6262352763439135047,12519037007915075754,262144 --variations-seed-version --mojo-platform-channel-handle=2744 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --subproc-heap-profiling --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --always-read-main-dll --field-trial-handle=2824,i,6499974376906040208,13380467503171187786,262144 --variations-seed-version --mojo-platform-channel-handle=3632 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --pdf-upsell-enabled --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --always-read-main-dll --field-trial-handle=6412,i,6262352763439135047,12519037007915075754,262144 --variations-seed-version --mojo-platform-channel-handle=6428 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1832 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7332,i,6262352763439135047,12519037007915075754,262144 --variations-seed-version --mojo-platform-channel-handle=7312 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\Desktop\Setup.exe" /SPAWNWND=$50318 /NOTIFYWND=$30364 | C:\Users\admin\Desktop\Setup.exe | Setup.tmp | ||||||||||||
User: admin Company: ATEXO Integrity Level: HIGH Description: Atexo Sign Setup Exit code: 1 Version: Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\AppData\Local\Temp\is-FIRT3.tmp\Setup.tmp" /SL5="$60282,12788763,57856,C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-FIRT3.tmp\Setup.tmp | — | Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 1 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2144 | "C:\Program Files\Java\jre1.8.0_451\bin\ssvagent.exe" -doHKCUSSVSetup | C:\Program Files\Java\jre1.8.0_451\bin\ssvagent.exe | — | installer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 11.451.0.10 Modules
| |||||||||||||||
| 2192 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x284,0x288,0x28c,0x27c,0x294,0x7ffc4439f208,0x7ffc4439f214,0x7ffc4439f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2464 | C:\Windows\System32\MsiExec.exe -Embedding 99398E7D373D412EE59674972C720E63 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2528 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --edge-skip-compat-layer-relaunch --single-argument http://www.java.com/getjava/ | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 1 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
52 219
Read events
24 308
Write events
13 076
Delete events
14 835
Modification events
| (PID) Process: | (5480) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5480) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5480) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 1 | |||
| (PID) Process: | (2528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5480) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2528) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2528) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 97ABAF81E9962F00 | |||
Executable files
354
Suspicious files
237
Text files
290
Unknown types
113
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4112 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF177fa0.TMP | — | |
MD5:— | SHA256:— | |||
| 4112 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4112 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF177fce.TMP | — | |
MD5:— | SHA256:— | |||
| 4112 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF177e67.TMP | binary | |
MD5:DBBA201B22DE9AA45258E642BD5CBFDE | SHA256:CAAA68730183AA43A172516DCCEA7FAC02370764A337B87758887BAB62272872 | |||
| 4112 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF177fee.TMP | — | |
MD5:— | SHA256:— | |||
| 5480 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-8AHRG.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4112 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2528 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:BAC9FEB21F102B8ED4CD3E469213E59B | SHA256:84ACD485899333CBDF5AD1F68D8C31658D5ECC9EE8DDDF62098A2218687D7E77 | |||
| 4112 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF177fee.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
141
DNS requests
152
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7704 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3624 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:YKQv-vqrN3TKromBHCggAeerdf_TUXMo7zjEJsS5ldk&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
7704 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7980 | jre-8u451-windows-x64.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
8164 | msiexec.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
8164 | msiexec.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
8164 | msiexec.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAqhj2P5bxF3HLsLQ%2BTWkLg%3D | unknown | — | — | whitelisted |
7980 | jre-8u451-windows-x64.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAsA6S1NbXMfyjBZx8seGIY%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1352 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3624 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3624 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.java.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
consent.trustarc.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |