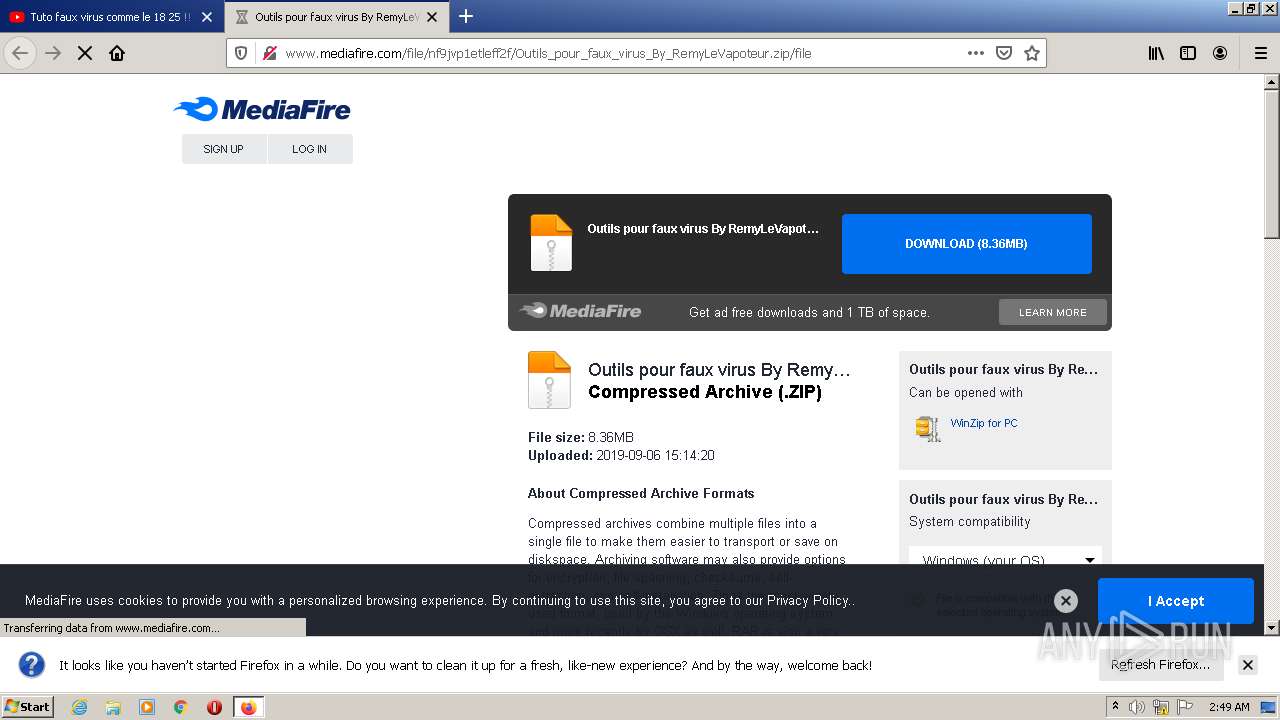
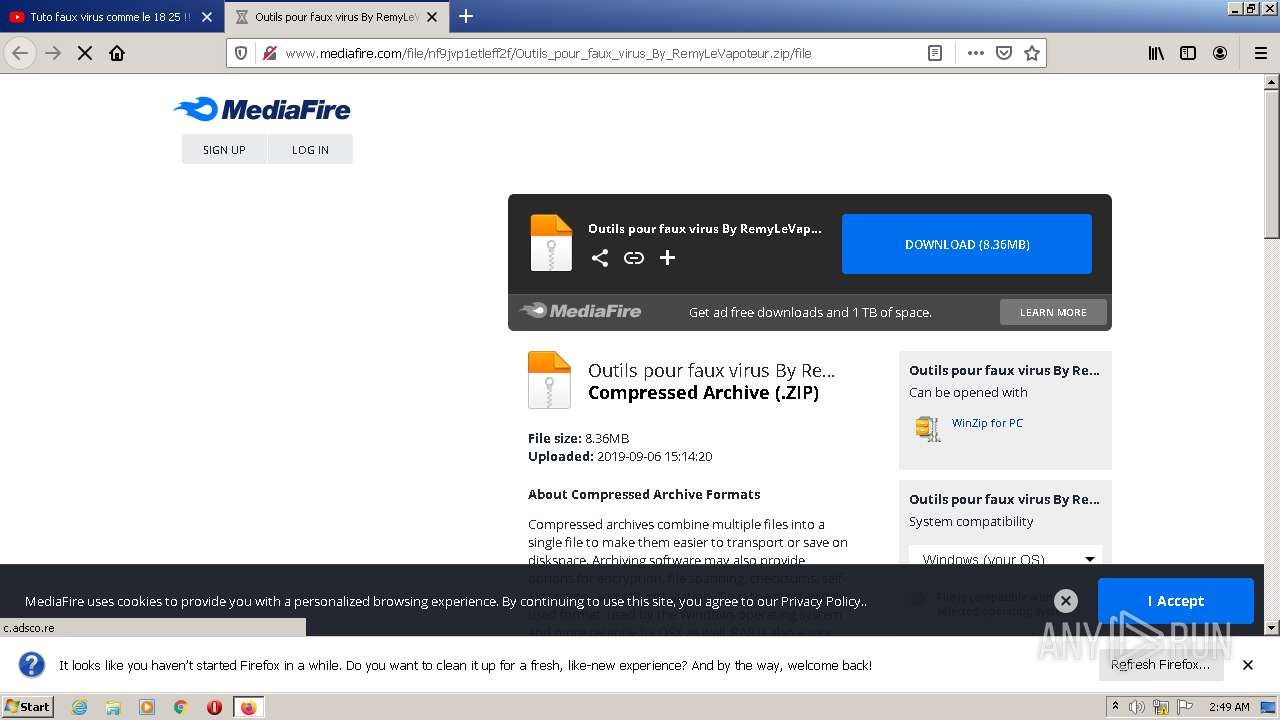
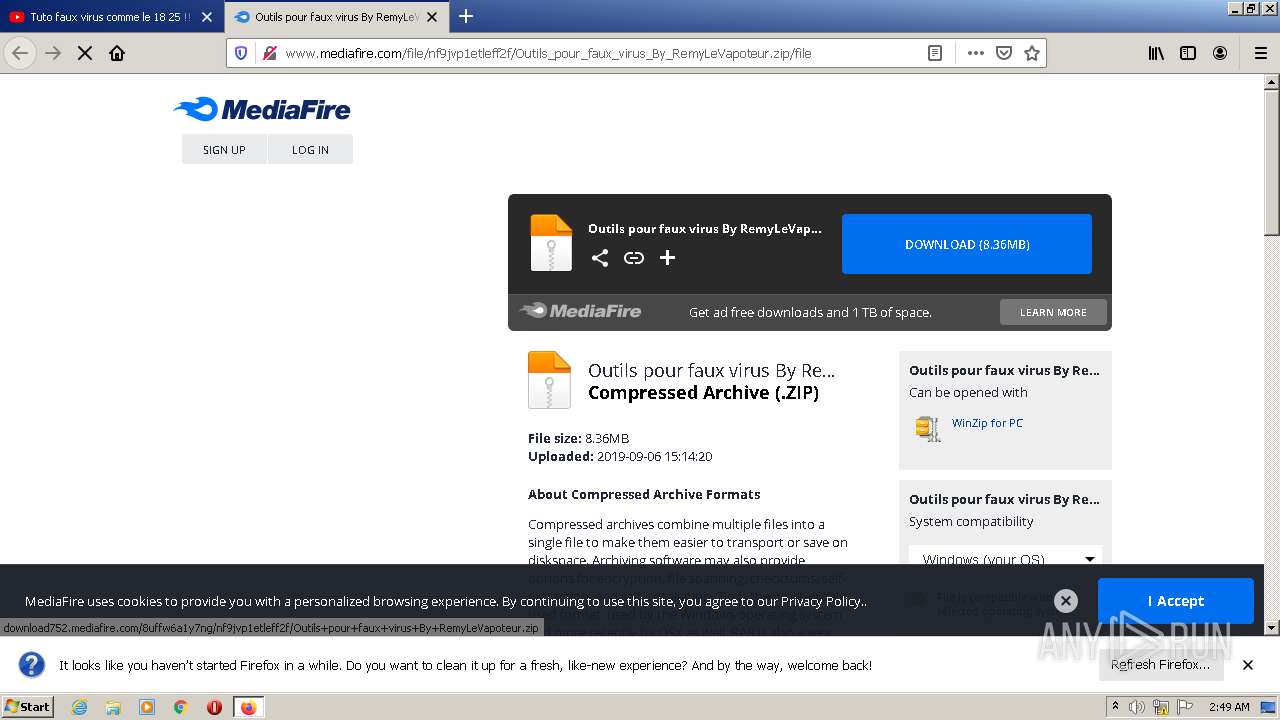
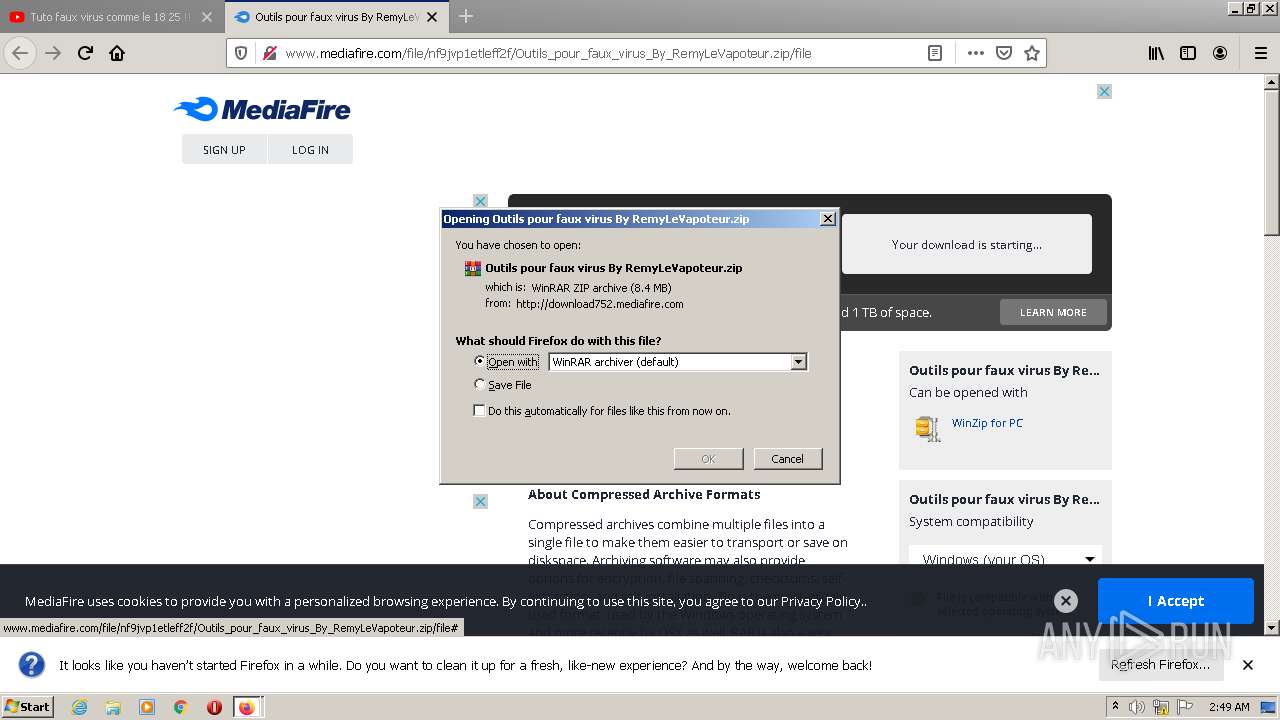
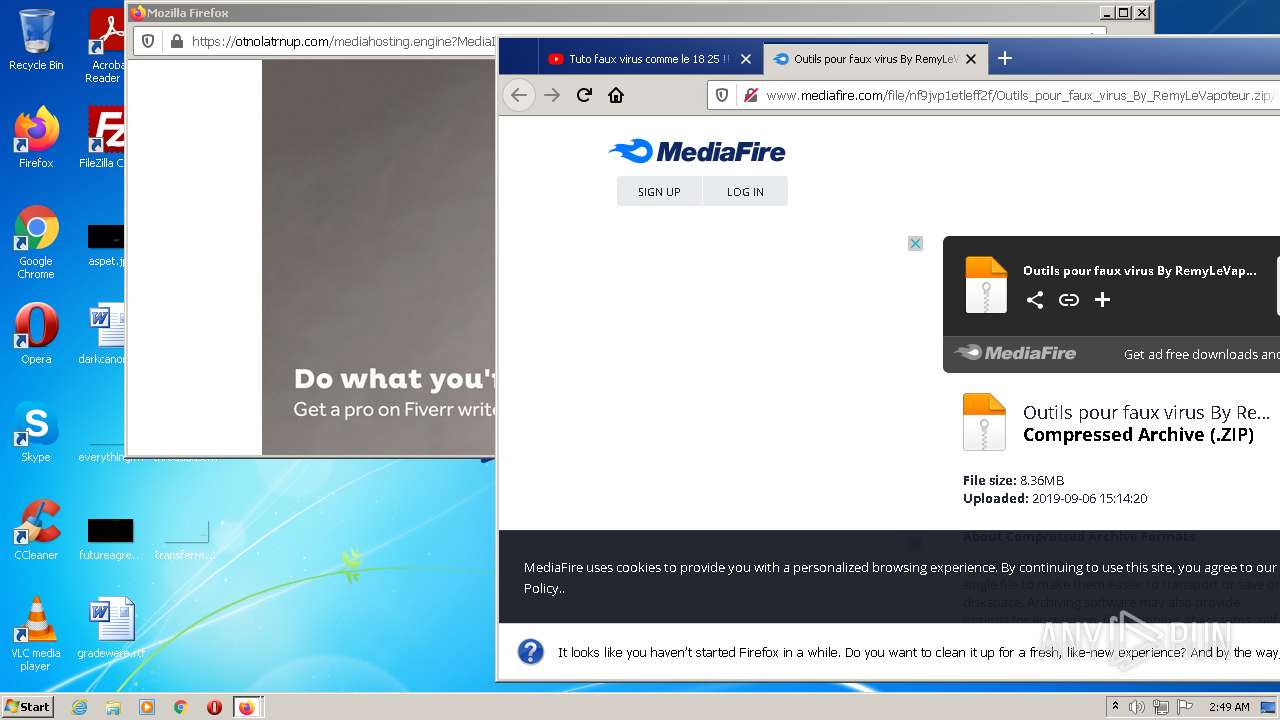
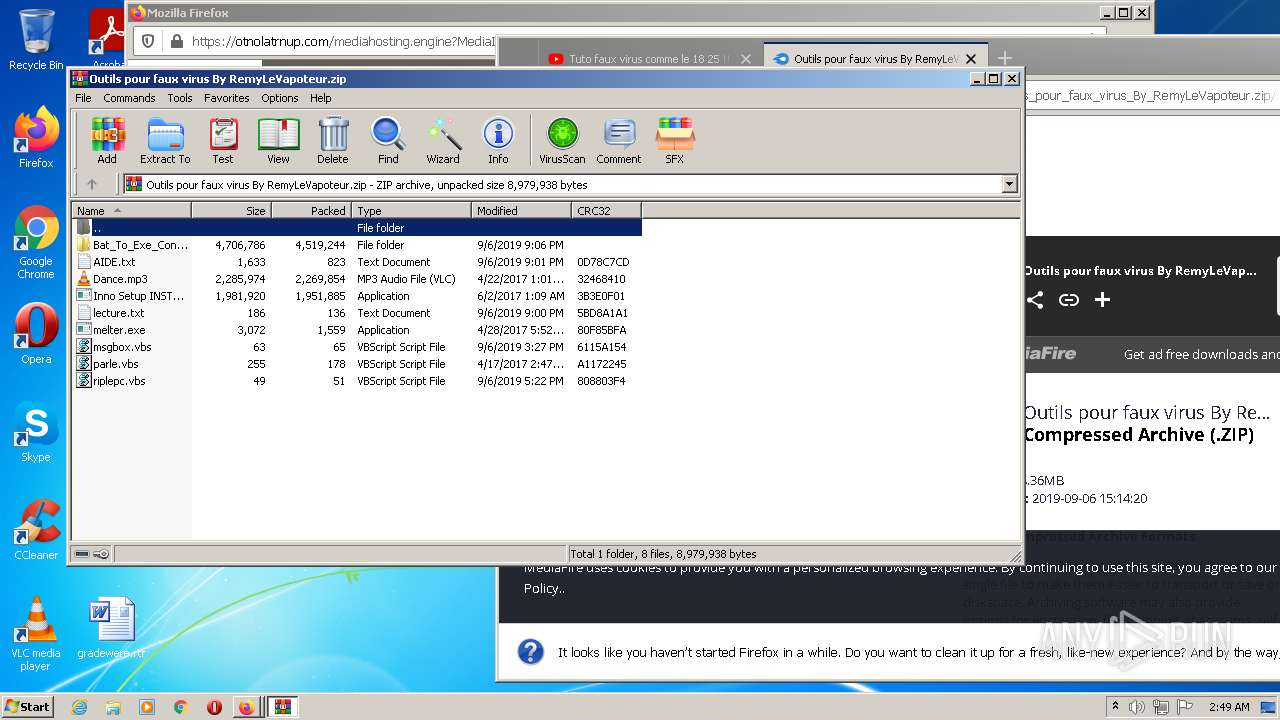
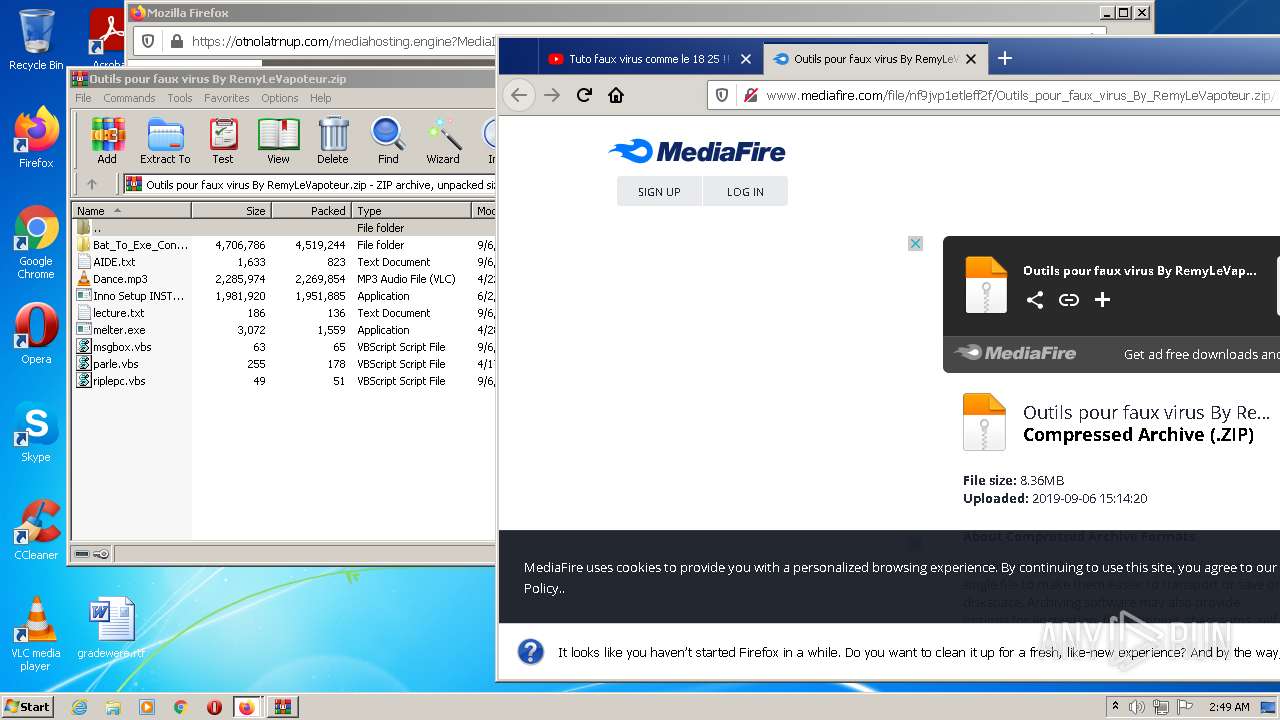
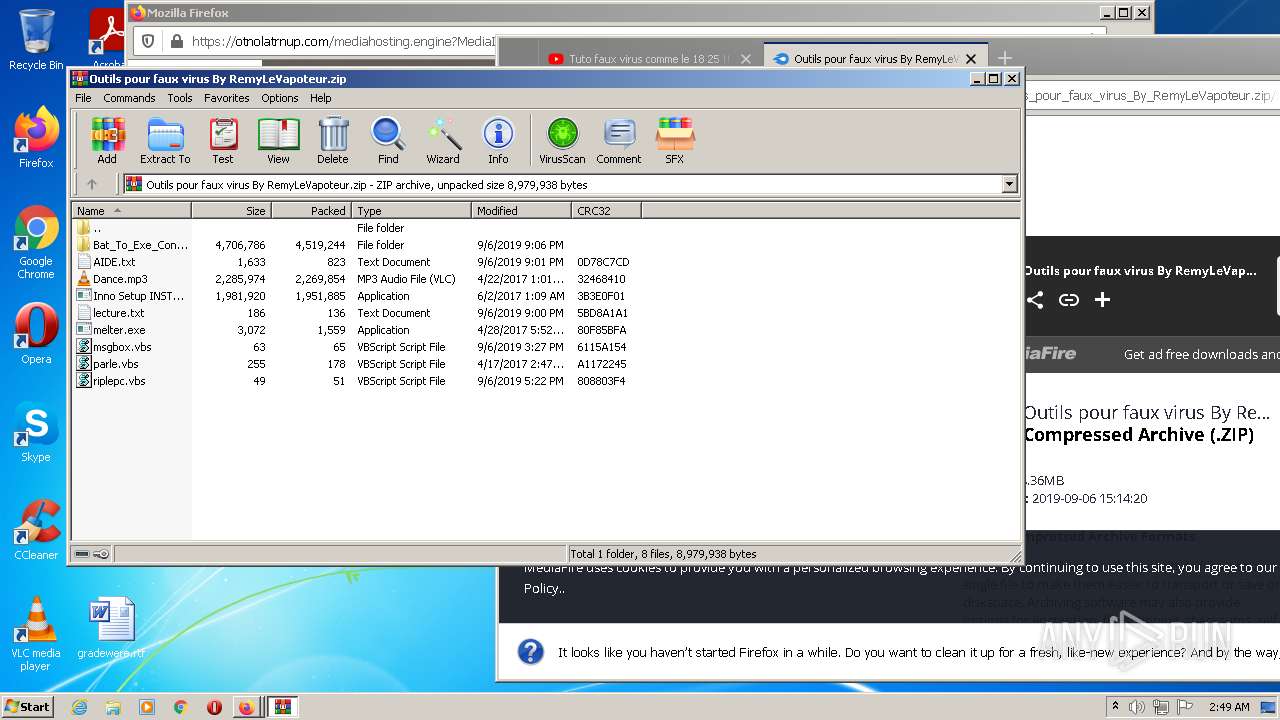
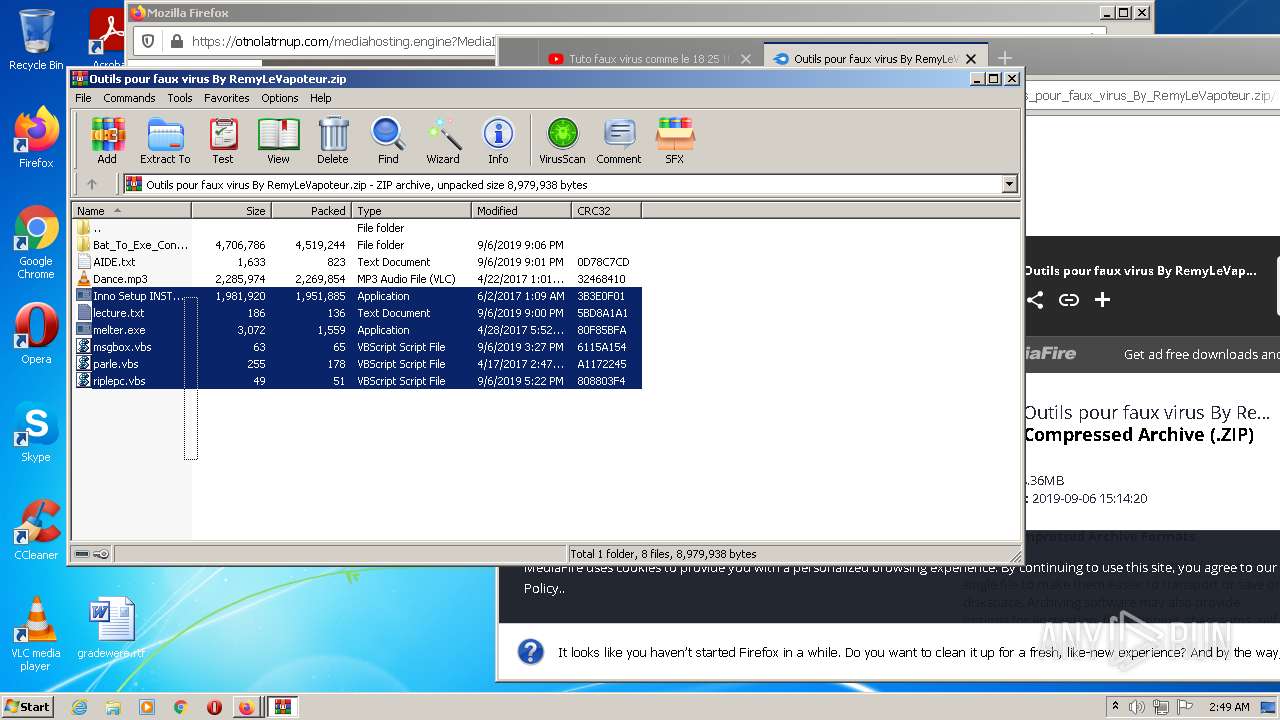
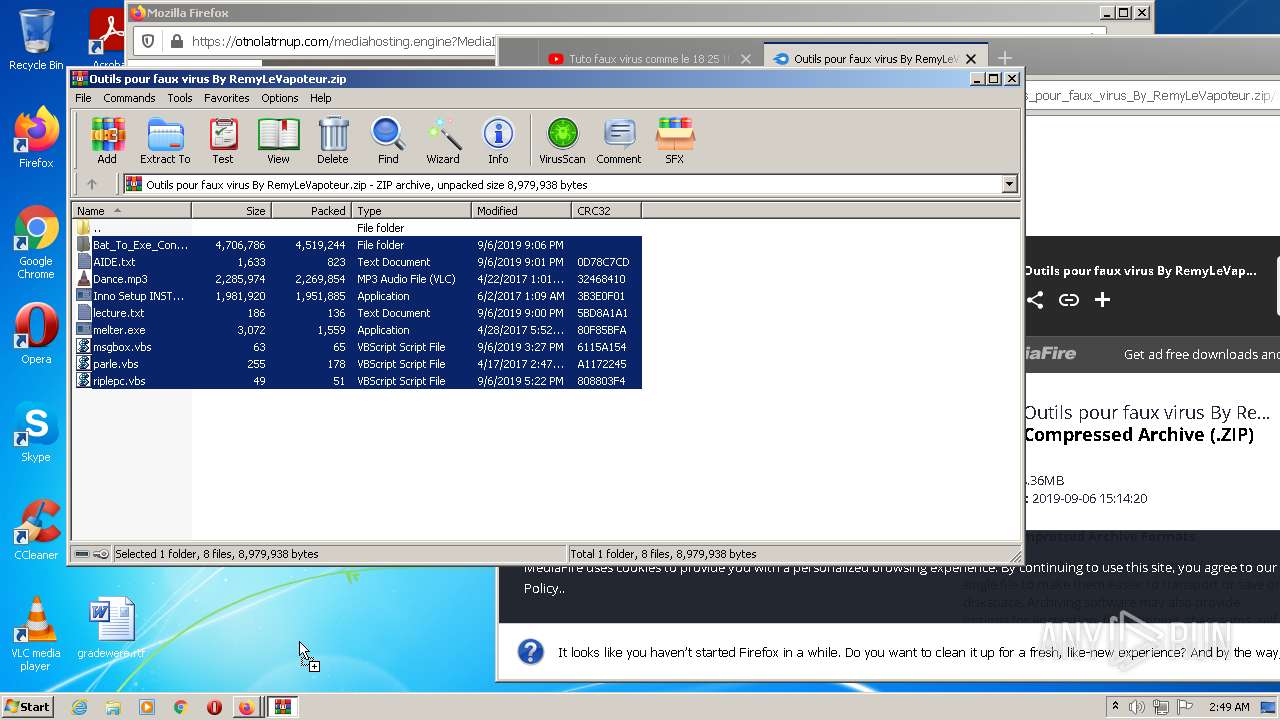
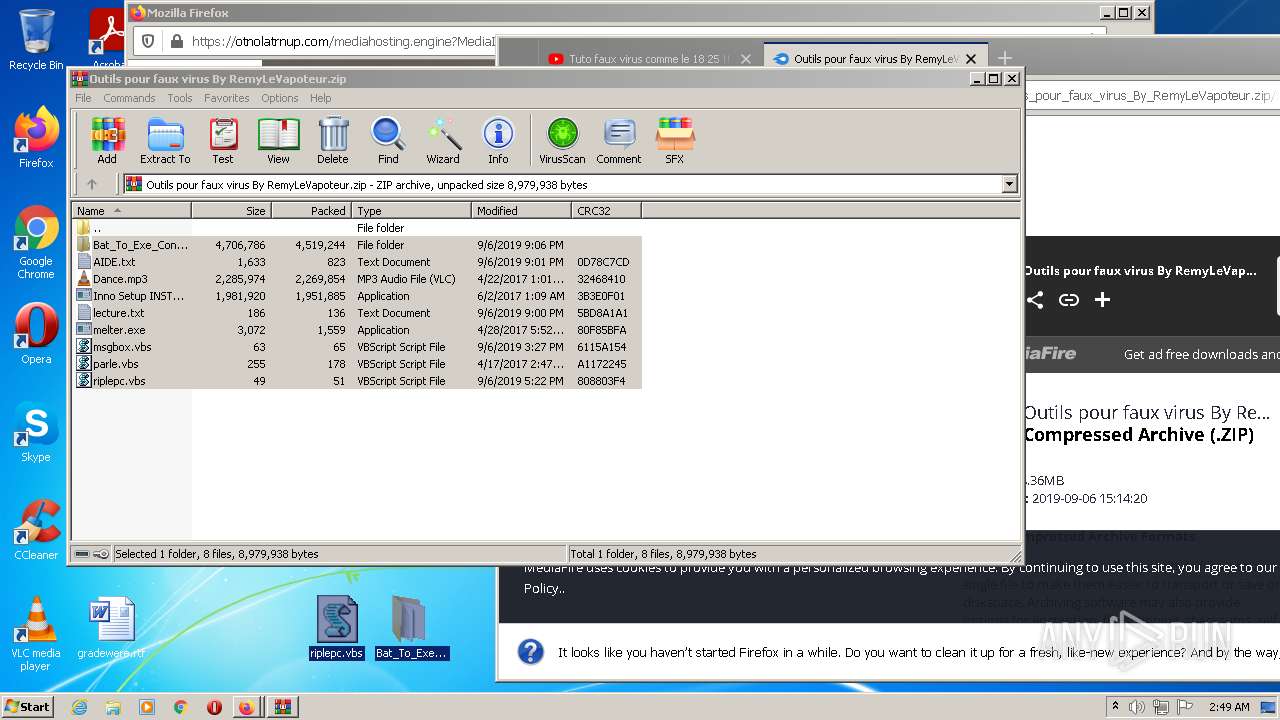
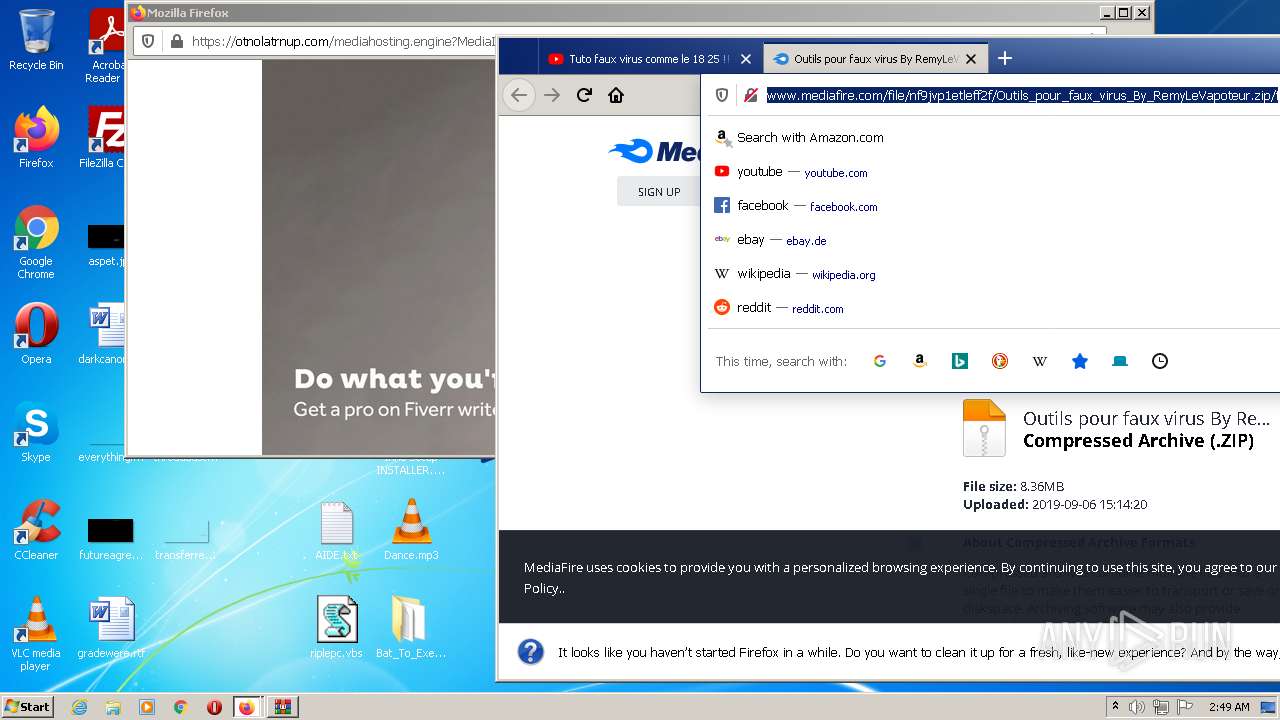
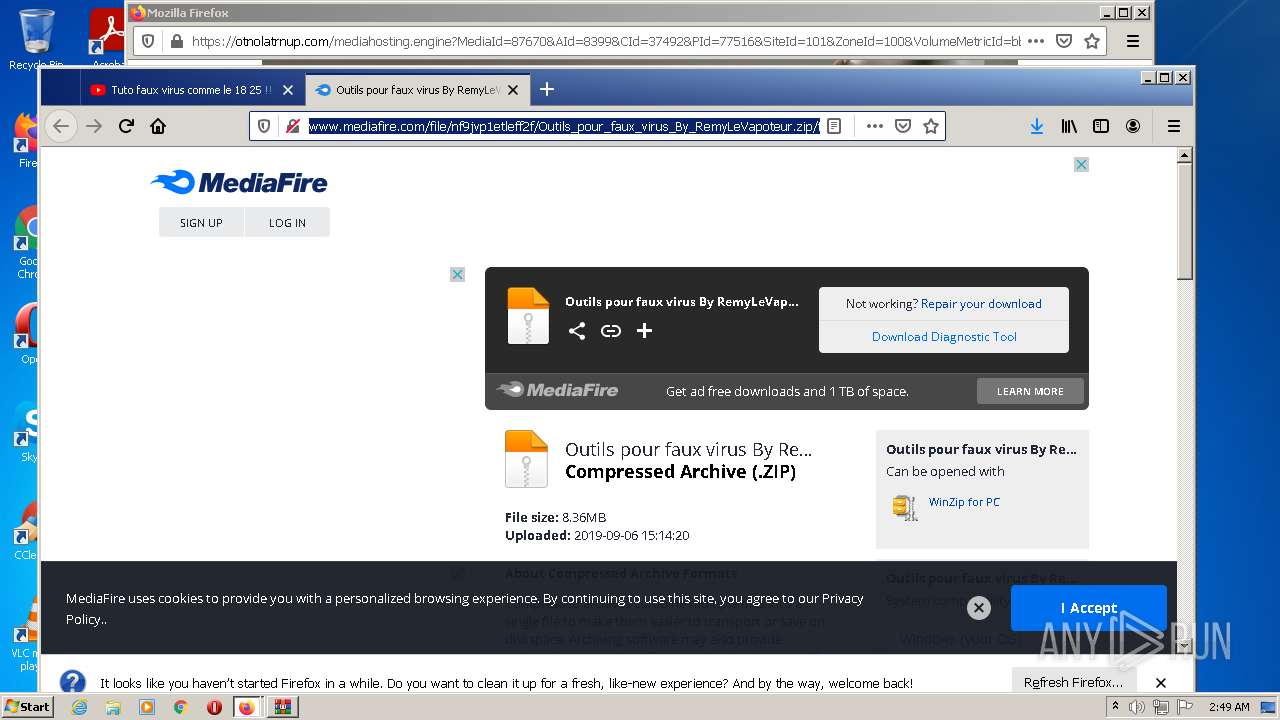
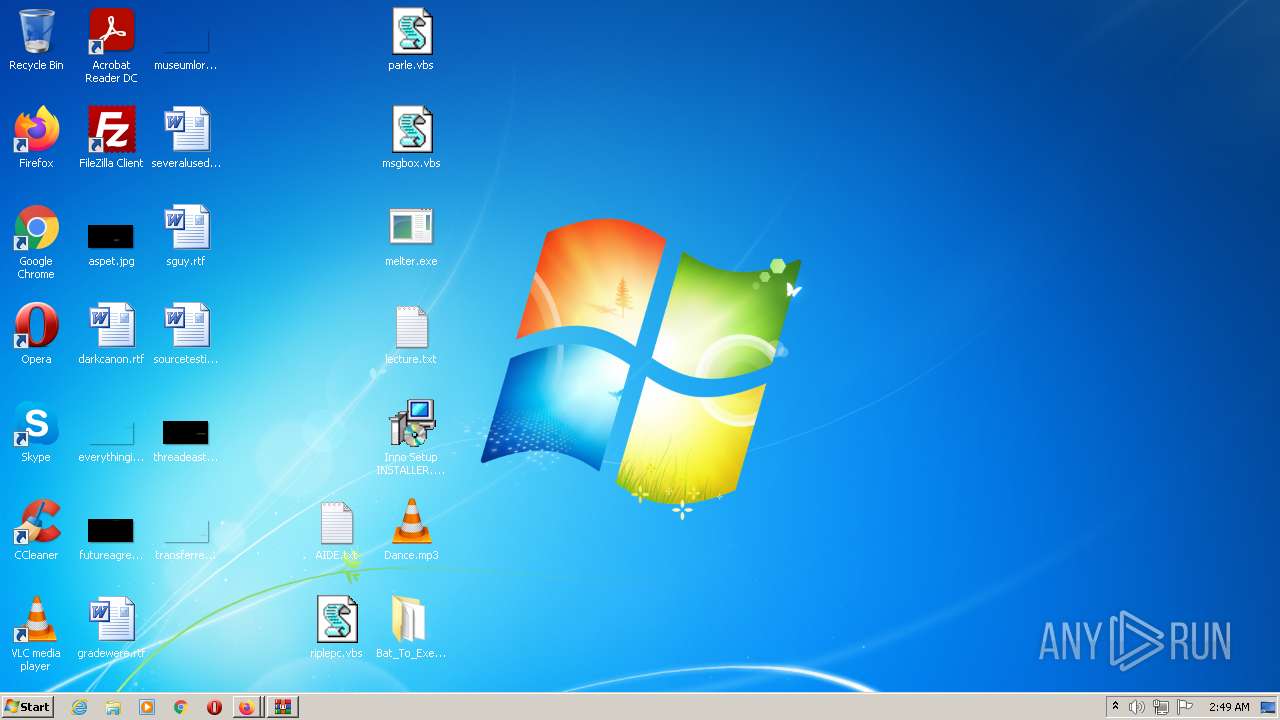
| URL: | https://anonfiles.com/F0ff1aH8x5/CtkuFtVK_png |
| Full analysis: | https://app.any.run/tasks/09fd5ee6-e752-497c-a671-518ae6729e4e |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2022, 02:48:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 341297ADFA7256D95CE91B36A0D19A96 |
| SHA1: | 142225CF0553BFB92FEDA3433FFFAC99991F5D42 |
| SHA256: | 41D17C66B3137DC366913E5BC905570739E92E1C5935F8435C736CEF50116886 |
| SSDEEP: | 3:N8M2utddOxI:2M2iddh |
MALICIOUS
Application was dropped or rewritten from another process
- melter.exe (PID: 2212)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2060)
Reads the computer name
- WinRAR.exe (PID: 568)
Drops a file with too old compile date
- WinRAR.exe (PID: 568)
Checks supported languages
- melter.exe (PID: 2212)
- WinRAR.exe (PID: 568)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 568)
- firefox.exe (PID: 2536)
Drops a file that was compiled in debug mode
- firefox.exe (PID: 2536)
INFO
Checks supported languages
- iexplore.exe (PID: 3568)
- iexplore.exe (PID: 2060)
- firefox.exe (PID: 720)
- firefox.exe (PID: 2536)
- firefox.exe (PID: 2288)
- firefox.exe (PID: 1032)
- firefox.exe (PID: 1576)
- firefox.exe (PID: 2996)
- firefox.exe (PID: 1524)
- firefox.exe (PID: 3052)
- firefox.exe (PID: 1192)
Reads the computer name
- iexplore.exe (PID: 3568)
- iexplore.exe (PID: 2060)
- firefox.exe (PID: 2536)
- firefox.exe (PID: 1032)
- firefox.exe (PID: 1192)
- firefox.exe (PID: 1576)
- firefox.exe (PID: 2996)
- firefox.exe (PID: 3052)
- firefox.exe (PID: 2288)
- firefox.exe (PID: 1524)
Changes internet zones settings
- iexplore.exe (PID: 3568)
Reads settings of System Certificates
- iexplore.exe (PID: 2060)
- iexplore.exe (PID: 3568)
Application launched itself
- iexplore.exe (PID: 3568)
- firefox.exe (PID: 720)
- firefox.exe (PID: 2536)
Reads internet explorer settings
- iexplore.exe (PID: 2060)
Checks Windows Trust Settings
- iexplore.exe (PID: 2060)
- iexplore.exe (PID: 3568)
- firefox.exe (PID: 2536)
Changes settings of System certificates
- iexplore.exe (PID: 3568)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3568)
Reads the date of Windows installation
- iexplore.exe (PID: 3568)
- firefox.exe (PID: 2536)
Manual execution by user
- firefox.exe (PID: 720)
- WinRAR.exe (PID: 568)
- melter.exe (PID: 2212)
Reads CPU info
- firefox.exe (PID: 2536)
Creates files in the program directory
- firefox.exe (PID: 2536)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 2536)
Creates files in the user directory
- firefox.exe (PID: 2536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
13
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
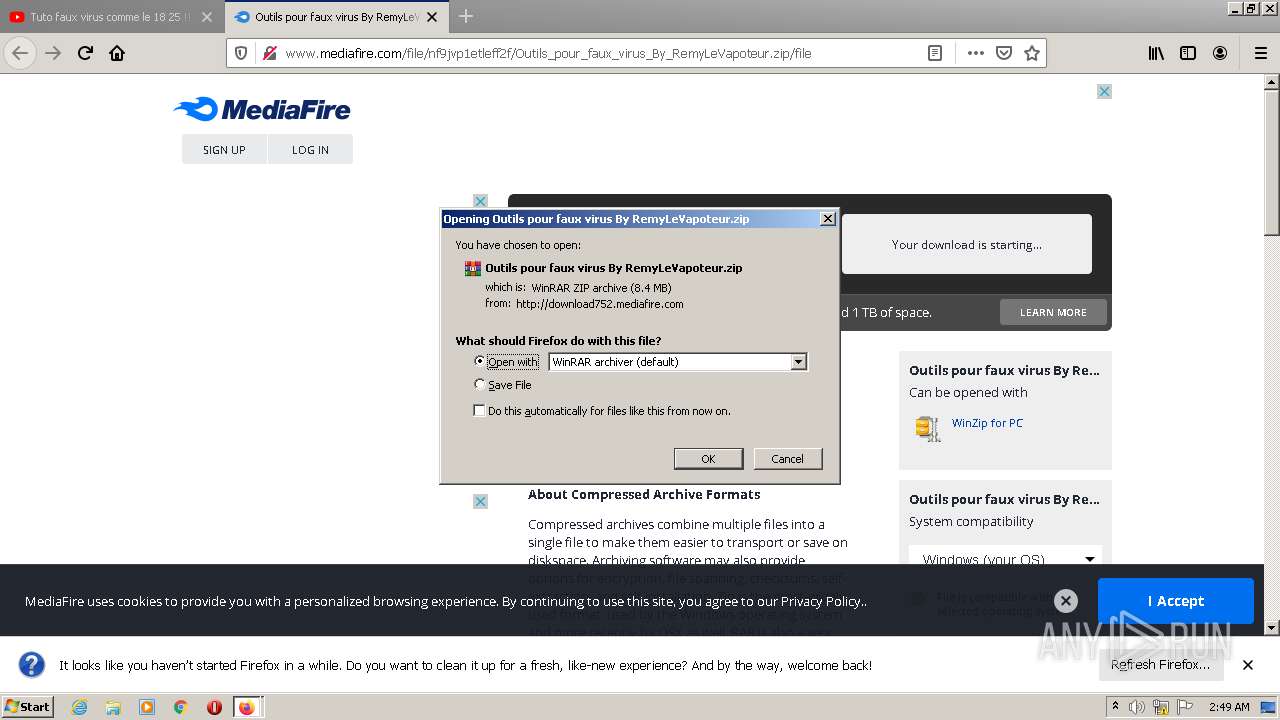
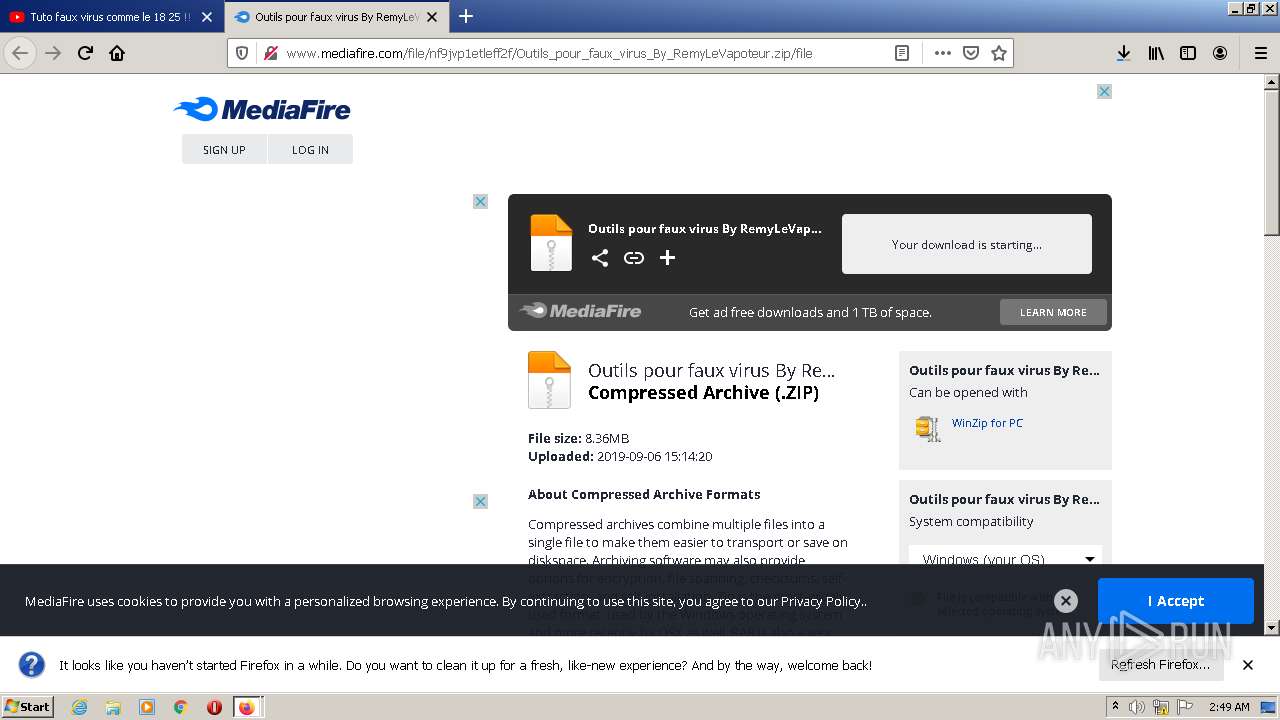
| 568 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Outils pour faux virus By RemyLeVapoteur.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 | ||||
| 720 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | Explorer.EXE |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 1032 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2536.0.1671556805\2120177097" -parentBuildID 20201112153044 -prefsHandle 900 -prefMapHandle 896 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2536 "\\.\pipe\gecko-crash-server-pipe.2536" 1172 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 1192 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2536.27.725584226\120927021" -childID 4 -isForBrowser -prefsHandle 3972 -prefMapHandle 3968 -prefsLen 8231 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2536 "\\.\pipe\gecko-crash-server-pipe.2536" 3984 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 1524 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2536.34.1290412442\1526396876" -parentBuildID 20201112153044 -prefsHandle 3496 -prefMapHandle 8104 -prefsLen 9521 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2536 "\\.\pipe\gecko-crash-server-pipe.2536" 1720 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 1576 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2536.6.140811102\608046647" -childID 1 -isForBrowser -prefsHandle 2204 -prefMapHandle 2200 -prefsLen 181 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2536 "\\.\pipe\gecko-crash-server-pipe.2536" 2216 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 2060 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3568 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 2212 | "C:\Users\admin\Desktop\melter.exe" | C:\Users\admin\Desktop\melter.exe | — | Explorer.EXE |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
| 2288 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2536.38.698995320\1707686319" -childID 5 -isForBrowser -prefsHandle 7720 -prefMapHandle 7832 -prefsLen 9607 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2536 "\\.\pipe\gecko-crash-server-pipe.2536" 3032 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 | ||||
| 2536 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
9
Suspicious files
254
Text files
166
Unknown types
69
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8CF5BD514FD3F41B9B84FC505B8DCD45 | binary | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\CtkuFtVK_png[1].htm | html | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\app[1].js | text | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\anonfiles[1].css | text | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8CF5BD514FD3F41B9B84FC505B8DCD45 | der | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_42D518C245FE7F2F9F026AD6DD212548 | binary | |
MD5:— | SHA256:— | |||
| 2060 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_42D518C245FE7F2F9F026AD6DD212548 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
87
TCP/UDP connections
186
DNS requests
323
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2060 | iexplore.exe | GET | 200 | 92.123.195.107:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNP3fS5KI692THHXqQ23ICPyg%3D%3D | unknown | der | 503 b | shared |
2536 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2536 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3568 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
2060 | iexplore.exe | GET | 200 | 18.66.242.58:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
2536 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
2536 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2536 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
2060 | iexplore.exe | GET | 200 | 143.204.101.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2060 | iexplore.exe | GET | 200 | 18.66.242.62:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2060 | iexplore.exe | 45.154.253.151:443 | anonfiles.com | — | — | suspicious |
2060 | iexplore.exe | 67.26.137.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | malicious |
2060 | iexplore.exe | 104.89.32.83:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | suspicious |
2060 | iexplore.exe | 151.101.194.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
2060 | iexplore.exe | 92.123.195.107:80 | r3.o.lencr.org | Akamai International B.V. | — | suspicious |
2060 | iexplore.exe | 185.157.161.127:443 | cdn-104.anonfiles.com | Obenetwork AB | SE | unknown |
2060 | iexplore.exe | 108.156.253.21:443 | djv99sxoqpv11.cloudfront.net | — | US | unknown |
2060 | iexplore.exe | 104.18.21.226:80 | ocsp2.globalsign.com | Cloudflare Inc | US | shared |
2060 | iexplore.exe | 18.66.242.62:80 | ocsp.rootg2.amazontrust.com | Massachusetts Institute of Technology | US | whitelisted |
2060 | iexplore.exe | 143.204.101.195:80 | o.ss2.us | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
anonfiles.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
vjs.zencdn.net |
| whitelisted |
cdn-104.anonfiles.com |
| suspicious |
djv99sxoqpv11.cloudfront.net |
| shared |
ocsp2.globalsign.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2536 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2536 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
2536 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2536 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |