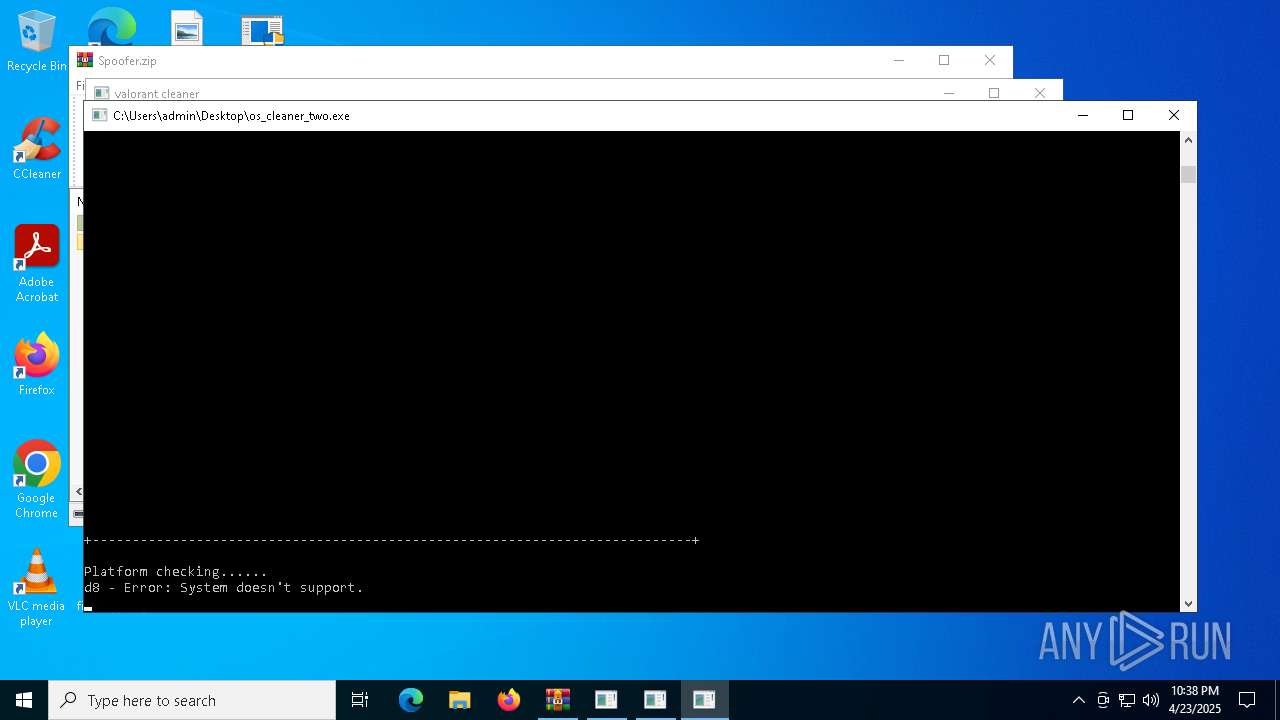
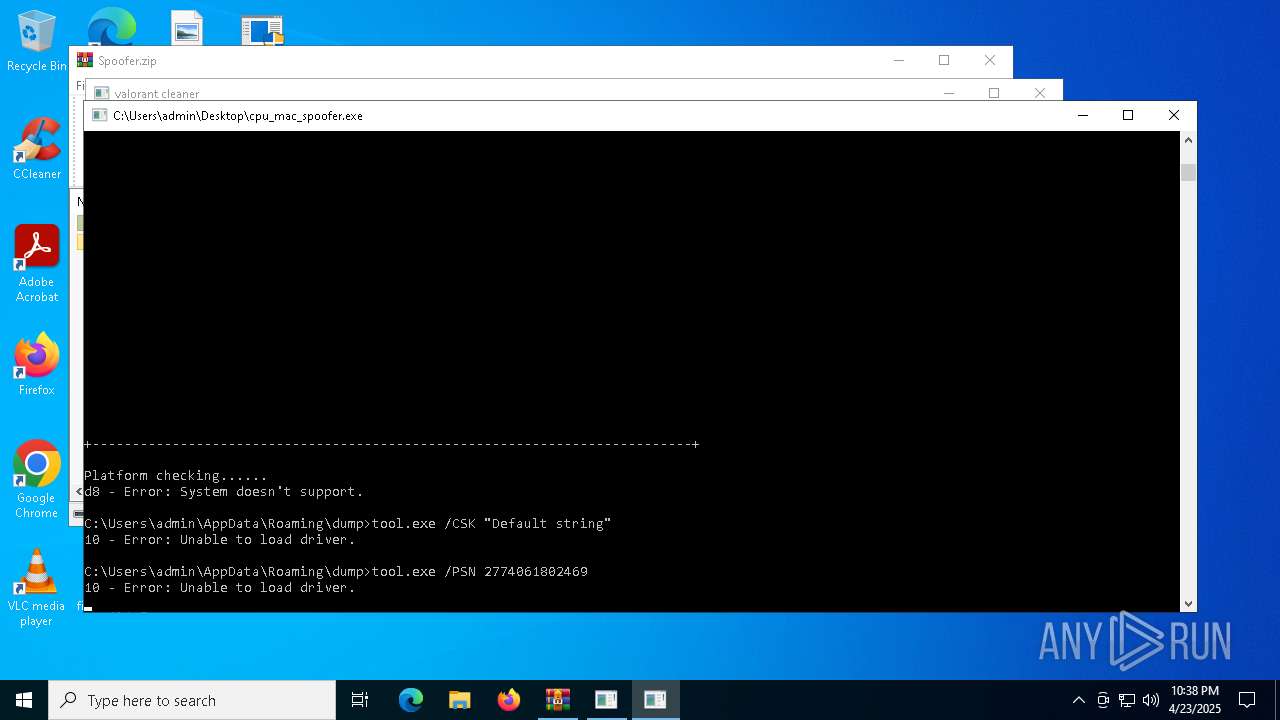
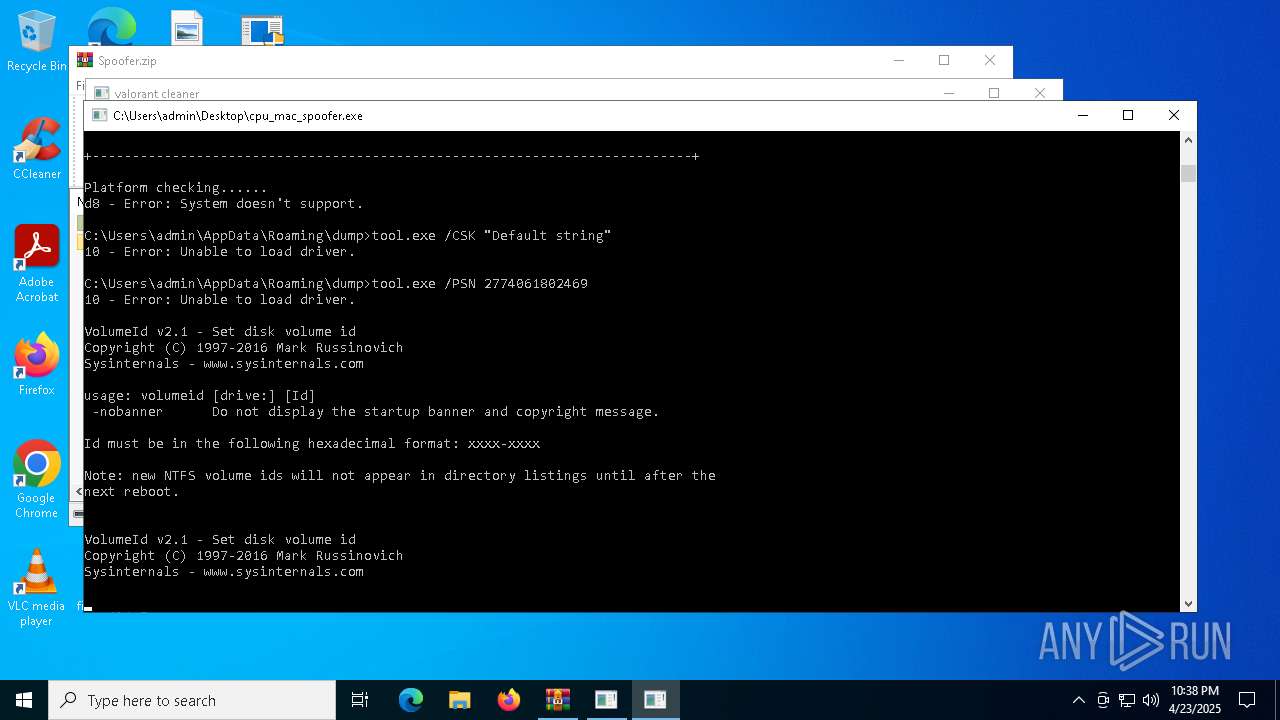
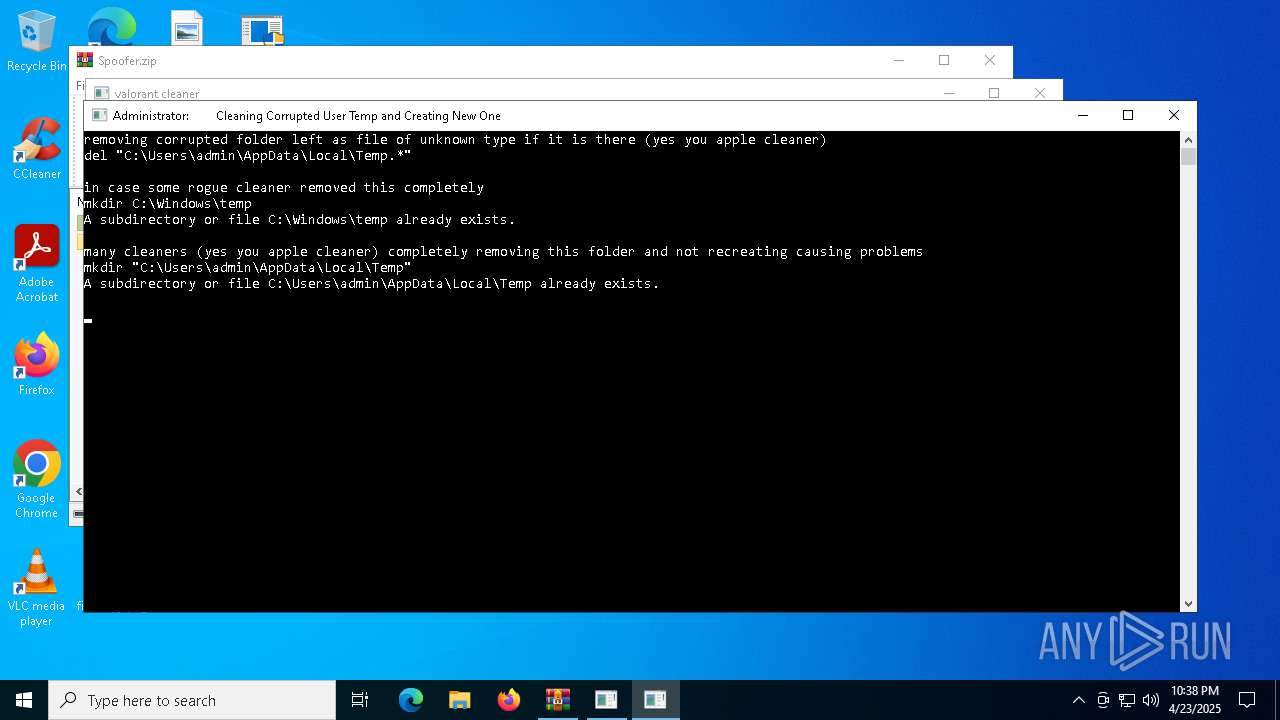
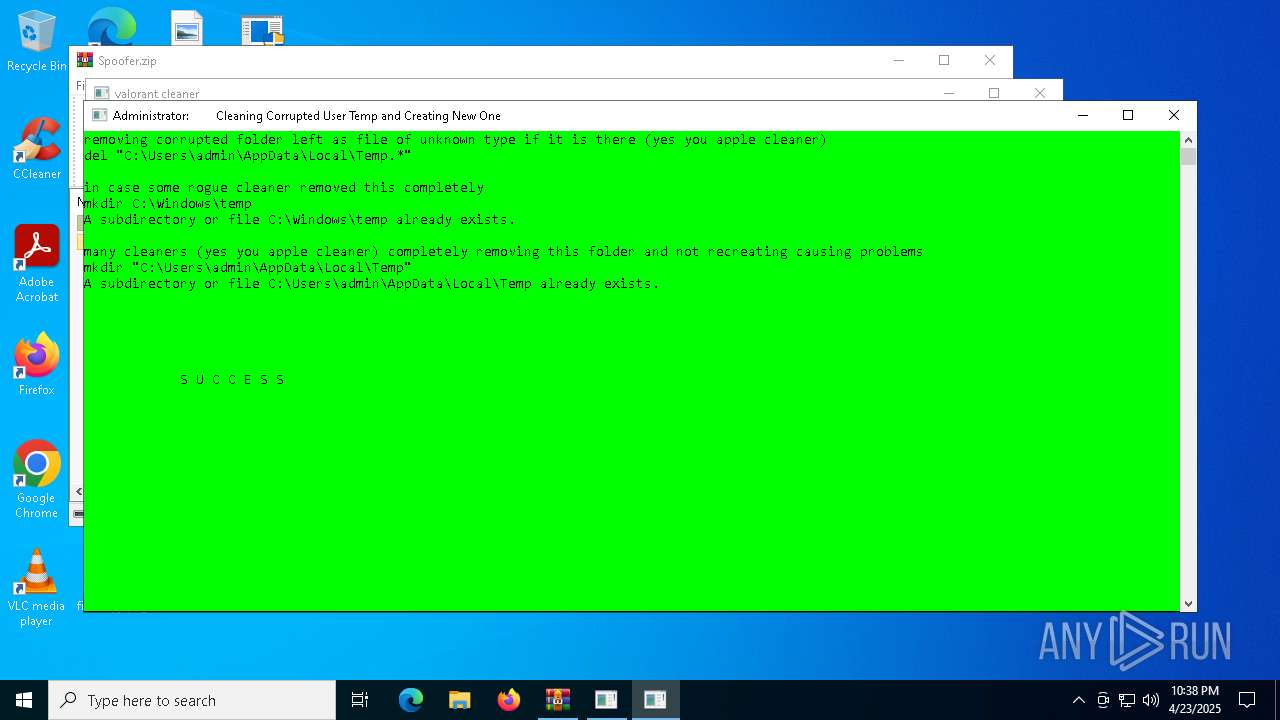
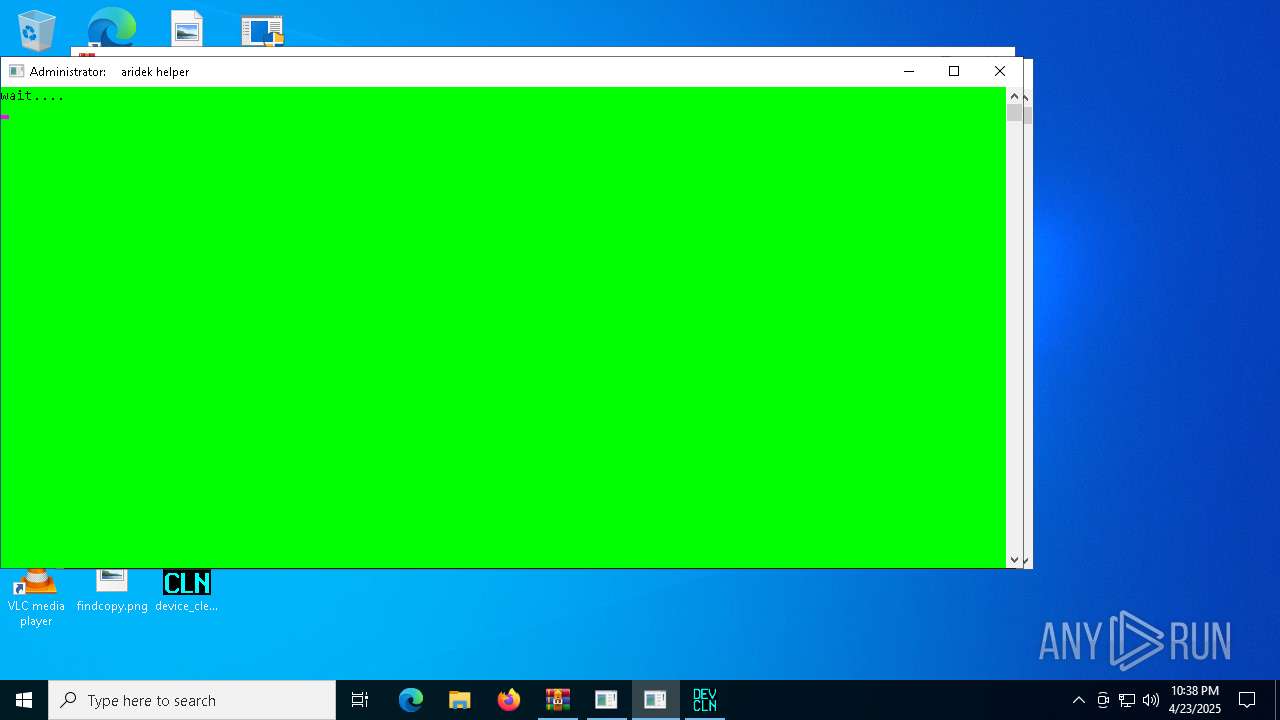
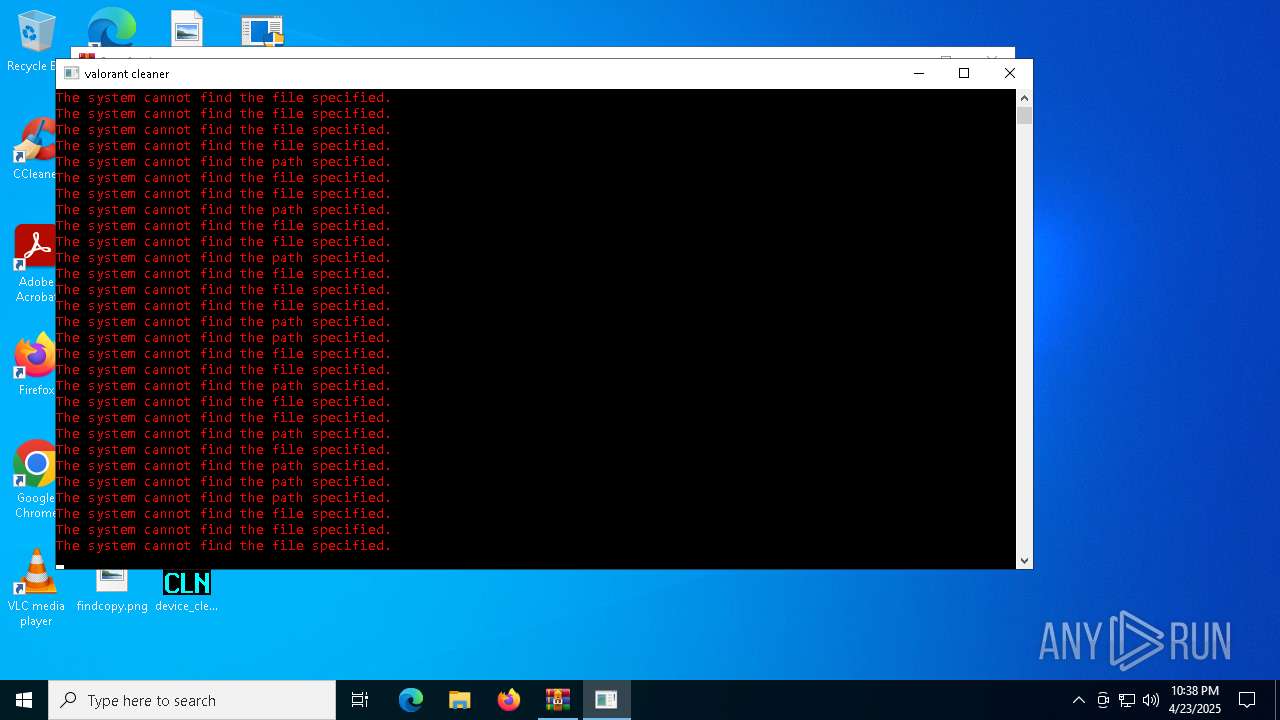
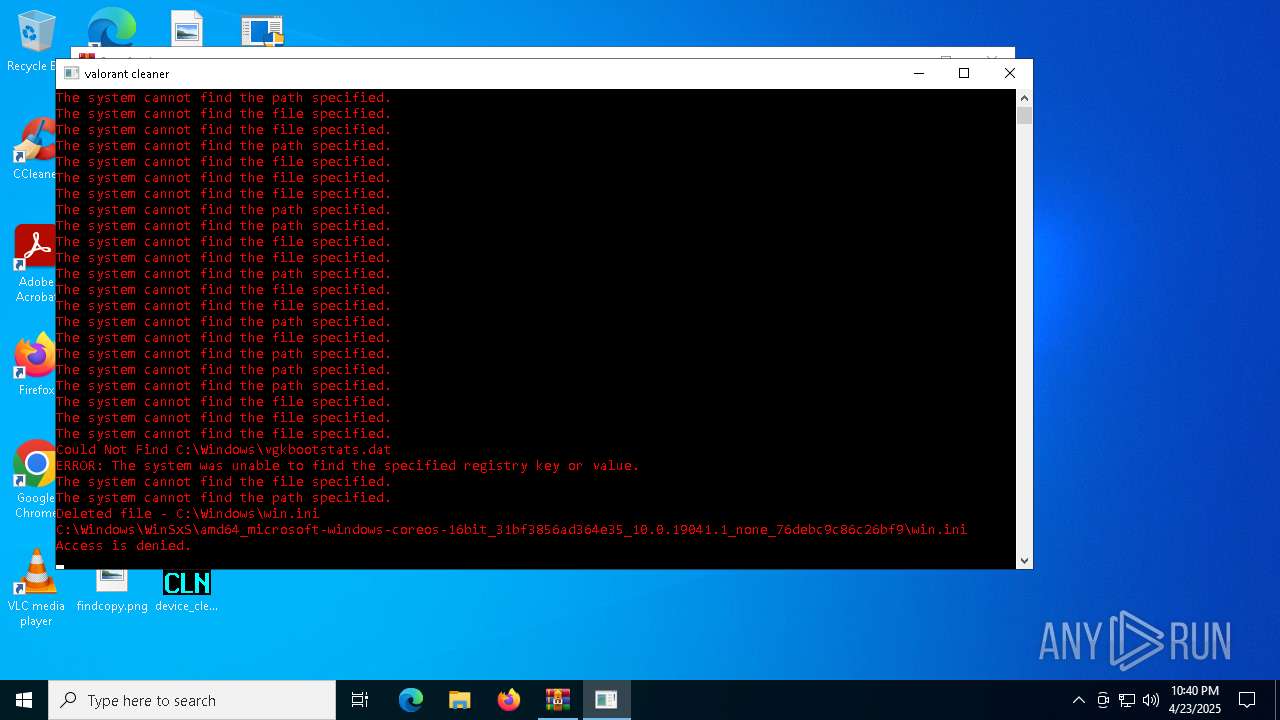
| File name: | Spoofer.zip |
| Full analysis: | https://app.any.run/tasks/7b480003-03a7-427a-bf38-ad535ddb276e |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2025, 22:37:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 52A813BF6C6459ABD5CFA2FC634CE239 |
| SHA1: | 010D866A2EF39839E97185C03E55C61BB302A2AF |
| SHA256: | 41C28661B1453F4470E5799AECFCBFC46FDA8D62D9642919918F13A0C49D822B |
| SSDEEP: | 98304:T14WXCzA1zukBCAFZn+6Br1YRab/Jx6evd+/lgl6zCOfrdAMcB4QaZiD1LiOEBSX:TjfgrqFv |
MALICIOUS
Executing a file with an untrusted certificate
- device_cleanup.exe (PID: 960)
- Volumeid64.exe (PID: 6476)
- Volumeid64.exe (PID: 2384)
- Volumeid64.exe (PID: 736)
- Volumeid64.exe (PID: 780)
- Volumeid64.exe (PID: 4776)
- Volumeid64.exe (PID: 2236)
- DeviceCleanupCmd.exe (PID: 5960)
- DriveCleanup.exe (PID: 3180)
Generic archive extractor
- WinRAR.exe (PID: 1168)
Vulnerable driver has been detected
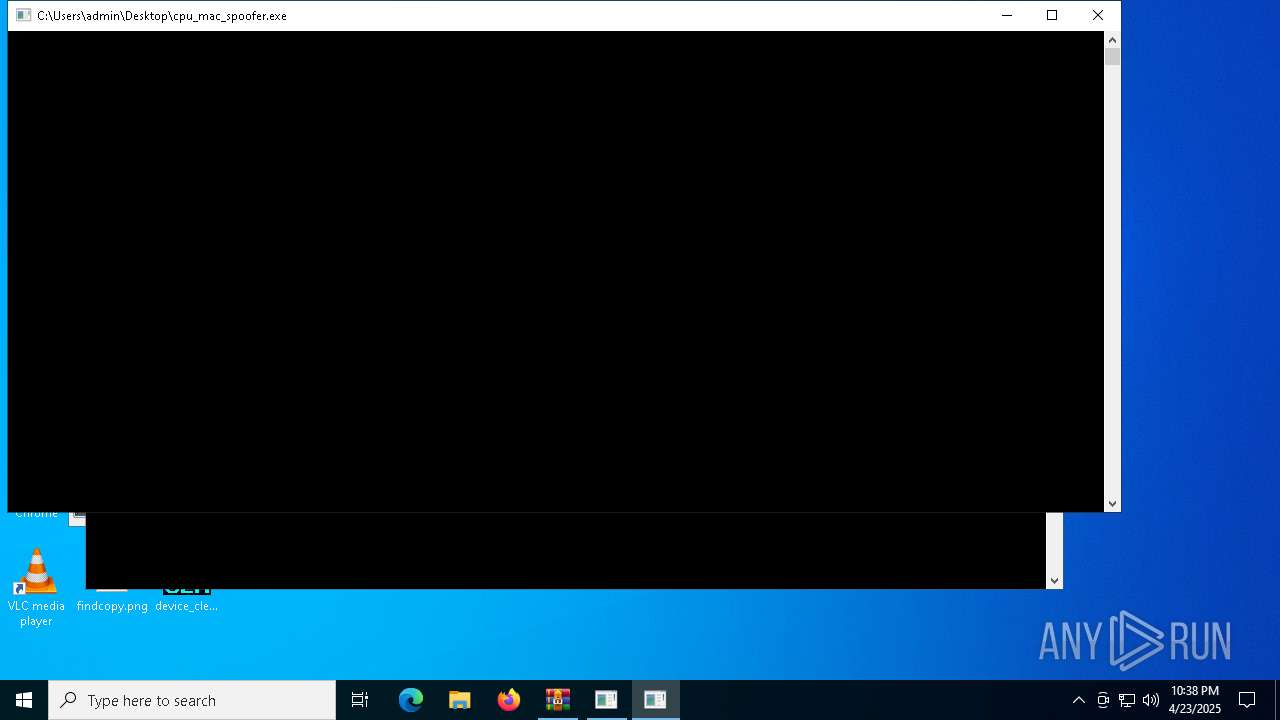
- cpu_mac_spoofer.exe (PID: 5332)
SUSPICIOUS
Starts CMD.EXE for commands execution
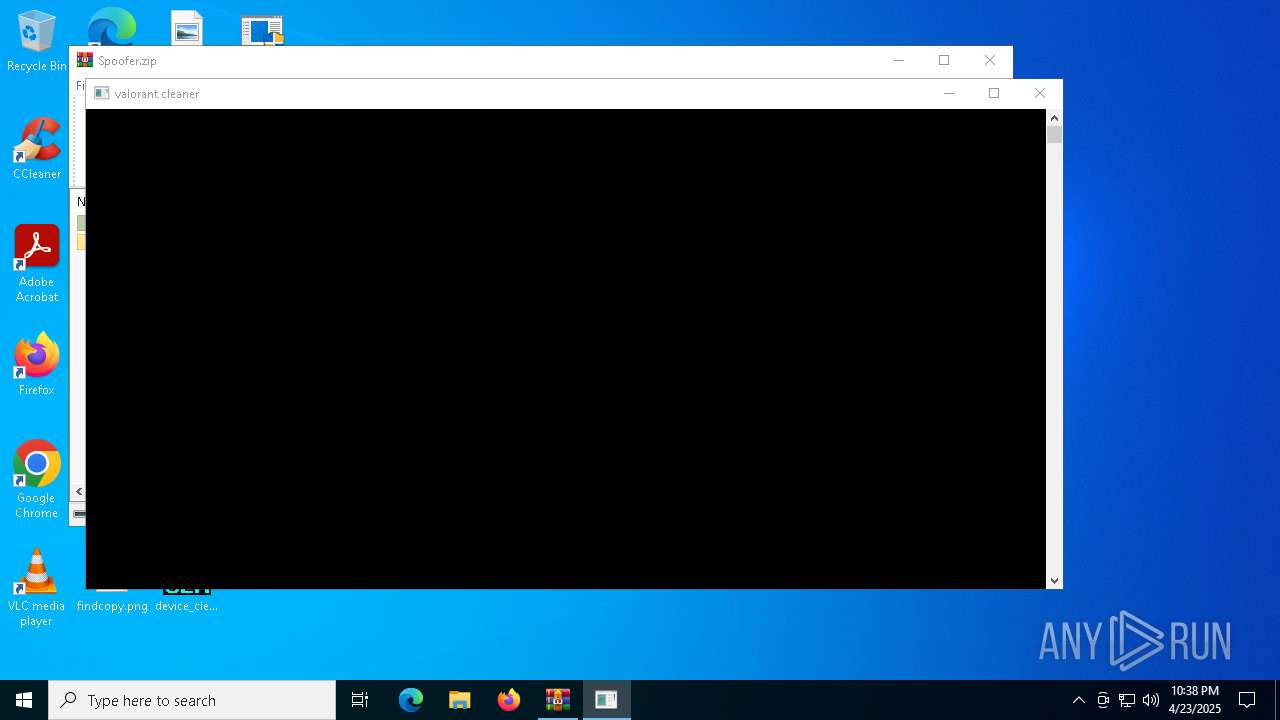
- valorant_cleaner.exe (PID: 2692)
- cpu_mac_spoofer.exe (PID: 5332)
- load.exe (PID: 4040)
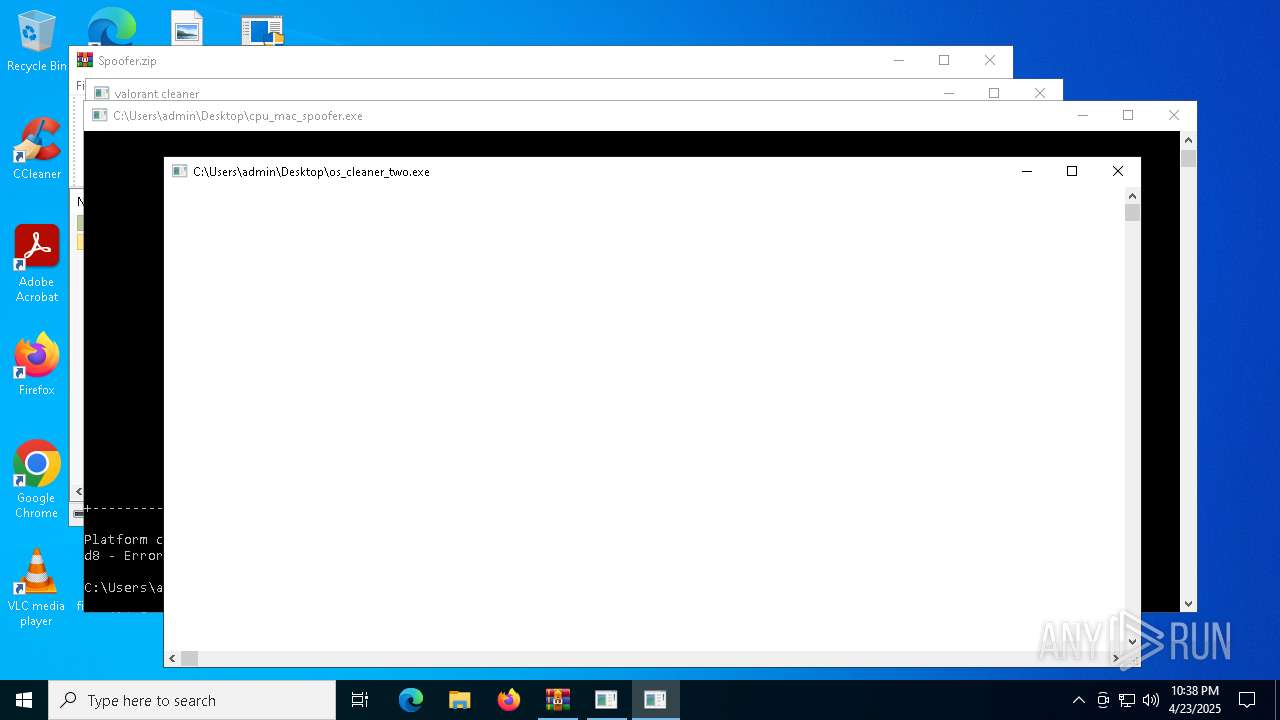
- os_cleaner_two.exe (PID: 632)
- load.exe (PID: 780)
- mac.exe (PID: 1512)
- cmd.exe (PID: 536)
- Volume.exe (PID: 6576)
- cmd.exe (PID: 5304)
- FIXusrTEMPv6.exe (PID: 1512)
Executable content was dropped or overwritten
- cpu_mac_spoofer.exe (PID: 5332)
- os_cleaner_two.exe (PID: 632)
Drops a system driver (possible attempt to evade defenses)
- cpu_mac_spoofer.exe (PID: 5332)
Process drops legitimate windows executable
- cpu_mac_spoofer.exe (PID: 5332)
The process creates files with name similar to system file names
- cpu_mac_spoofer.exe (PID: 5332)
The executable file from the user directory is run by the CMD process
- extd.exe (PID: 2516)
- extd.exe (PID: 5956)
- extd.exe (PID: 1512)
- load.exe (PID: 4040)
- extd.exe (PID: 1040)
- extd.exe (PID: 5256)
- extd.exe (PID: 5392)
- load.exe (PID: 780)
- mac.exe (PID: 1512)
- extd.exe (PID: 4628)
- Volume.exe (PID: 6576)
- FIXusrTEMPv6.exe (PID: 1512)
- DriveCleanup.exe (PID: 3180)
- DevManView.exe (PID: 968)
- DevManView.exe (PID: 4180)
- DeviceCleanupCmd.exe (PID: 5960)
- DevManView.exe (PID: 5124)
- DevManView.exe (PID: 5984)
- DevManView.exe (PID: 5936)
- DevManView.exe (PID: 4068)
- DevManView.exe (PID: 7216)
- DevManView.exe (PID: 7224)
- DevManView.exe (PID: 7176)
- DevManView.exe (PID: 7184)
- DevManView.exe (PID: 7248)
- DevManView.exe (PID: 7256)
- DevManView.exe (PID: 7264)
- DevManView.exe (PID: 7272)
- DevManView.exe (PID: 7280)
- DevManView.exe (PID: 7232)
- DevManView.exe (PID: 7240)
- DevManView.exe (PID: 7312)
- DevManView.exe (PID: 7320)
- DevManView.exe (PID: 7288)
- DevManView.exe (PID: 7296)
- DevManView.exe (PID: 7304)
- DevManView.exe (PID: 7440)
- DevManView.exe (PID: 8024)
- extd.exe (PID: 3676)
Executing commands from a ".bat" file
- cpu_mac_spoofer.exe (PID: 5332)
- load.exe (PID: 4040)
- os_cleaner_two.exe (PID: 632)
- load.exe (PID: 780)
- mac.exe (PID: 1512)
- Volume.exe (PID: 6576)
- cmd.exe (PID: 5304)
- FIXusrTEMPv6.exe (PID: 1512)
Application launched itself
- cmd.exe (PID: 536)
- cmd.exe (PID: 5304)
Uses WMIC.EXE to obtain information about the network interface controller
- cmd.exe (PID: 6392)
- cmd.exe (PID: 5400)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6392)
- cmd.exe (PID: 5400)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 536)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 6752)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 5680)
- cmd.exe (PID: 5260)
- cmd.exe (PID: 1568)
- cmd.exe (PID: 7244)
Uses WMIC.EXE to obtain network information
- cmd.exe (PID: 4696)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 536)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2236)
Read disk information to detect sandboxing environments
- DevManView.exe (PID: 968)
- DevManView.exe (PID: 4180)
- DevManView.exe (PID: 4068)
- DevManView.exe (PID: 5936)
- DevManView.exe (PID: 7176)
- DevManView.exe (PID: 7184)
- DevManView.exe (PID: 5124)
- DevManView.exe (PID: 7304)
- DevManView.exe (PID: 7312)
- DevManView.exe (PID: 5984)
- DevManView.exe (PID: 7440)
- DevManView.exe (PID: 7224)
- DevManView.exe (PID: 7320)
- DevManView.exe (PID: 7288)
- DevManView.exe (PID: 7232)
- DevManView.exe (PID: 7296)
- DevManView.exe (PID: 7216)
- DevManView.exe (PID: 7264)
- DevManView.exe (PID: 7256)
- DevManView.exe (PID: 7280)
- DevManView.exe (PID: 7272)
- DevManView.exe (PID: 7248)
- DevManView.exe (PID: 7240)
- DevManView.exe (PID: 8024)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2236)
INFO
Manual execution by a user
- device_cleanup.exe (PID: 960)
- cpu_mac_spoofer.exe (PID: 5512)
- valorant_cleaner.exe (PID: 2692)
- lgsvcl.exe (PID: 4212)
- lgsvcl.exe (PID: 1280)
- valorant_cleaner.exe (PID: 4212)
- os_cleaner_two.exe (PID: 632)
- cpu_mac_spoofer.exe (PID: 5332)
- os_cleaner_two.exe (PID: 4408)
Checks supported languages
- device_cleanup.exe (PID: 960)
- cpu_mac_spoofer.exe (PID: 5332)
- extd.exe (PID: 2516)
- extd.exe (PID: 5956)
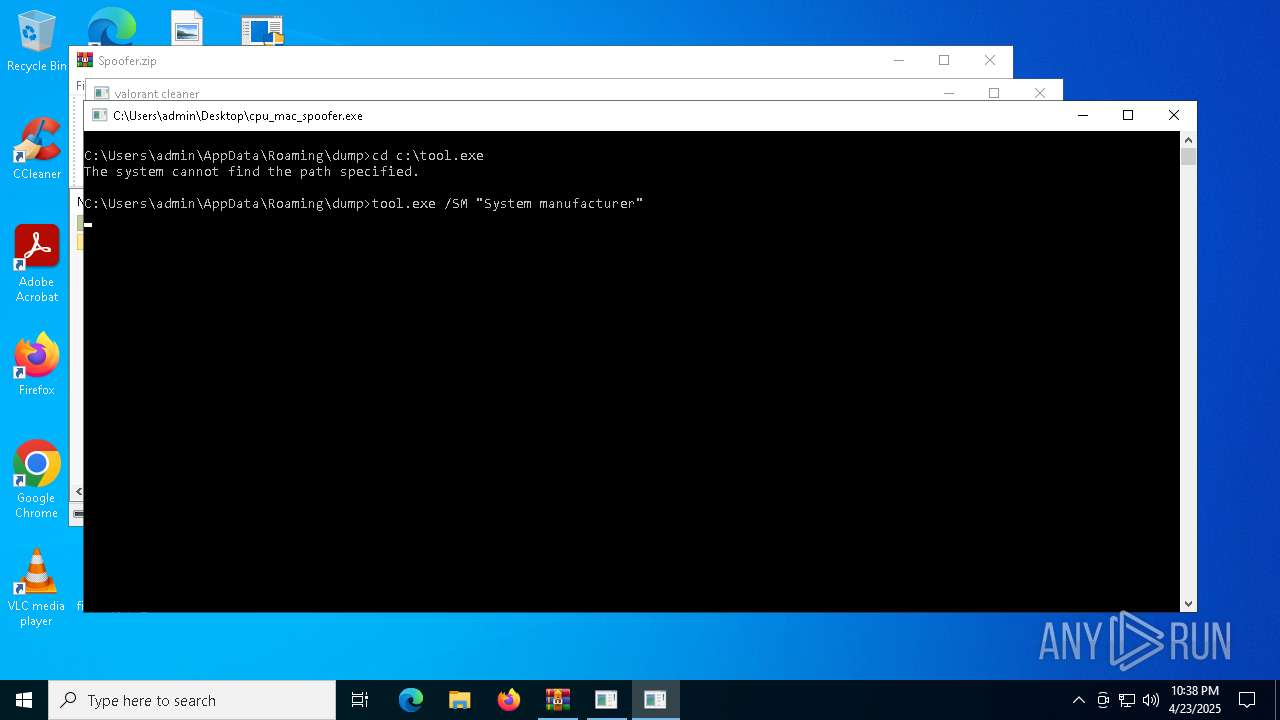
- tool.exe (PID: 5204)
- extd.exe (PID: 1512)
- load.exe (PID: 4040)
- tool.exe (PID: 5064)
- lgsvcl.exe (PID: 1280)
- tool.exe (PID: 3008)
- os_cleaner_two.exe (PID: 632)
- extd.exe (PID: 1040)
- valorant_cleaner.exe (PID: 2692)
- tool.exe (PID: 736)
- tool.exe (PID: 6728)
- extd.exe (PID: 5256)
- extd.exe (PID: 5392)
- tool.exe (PID: 2656)
- load.exe (PID: 780)
- tool.exe (PID: 2984)
- tool.exe (PID: 6244)
- tool.exe (PID: 4464)
- tool.exe (PID: 4212)
- tool.exe (PID: 1188)
- tool.exe (PID: 5228)
- tool.exe (PID: 5608)
- tool.exe (PID: 4812)
- tool.exe (PID: 2772)
- tool.exe (PID: 4628)
- tool.exe (PID: 1240)
- tool.exe (PID: 6112)
- tool.exe (PID: 1660)
- tool.exe (PID: 4996)
- tool.exe (PID: 4212)
- tool.exe (PID: 6728)
- tool.exe (PID: 4696)
- tool.exe (PID: 4188)
- mac.exe (PID: 1512)
- tool.exe (PID: 1348)
- tool.exe (PID: 720)
- tool.exe (PID: 2236)
- tool.exe (PID: 2268)
- tool.exe (PID: 6728)
- tool.exe (PID: 6476)
- tool.exe (PID: 4696)
- extd.exe (PID: 4628)
- tool.exe (PID: 7156)
- Volume.exe (PID: 6576)
- Volumeid64.exe (PID: 6476)
- Volumeid64.exe (PID: 736)
- Volumeid64.exe (PID: 2384)
- Volumeid64.exe (PID: 780)
- Volumeid64.exe (PID: 4776)
- Volumeid64.exe (PID: 2236)
- DriveCleanup.exe (PID: 3180)
- FIXusrTEMPv6.exe (PID: 1512)
- DeviceCleanupCmd.exe (PID: 5960)
- DevManView.exe (PID: 4180)
- DevManView.exe (PID: 5936)
- DevManView.exe (PID: 5984)
- DevManView.exe (PID: 5124)
- DevManView.exe (PID: 4068)
- DevManView.exe (PID: 968)
- DevManView.exe (PID: 7176)
- DevManView.exe (PID: 7184)
- DevManView.exe (PID: 7224)
- DevManView.exe (PID: 7232)
- DevManView.exe (PID: 7240)
- DevManView.exe (PID: 7288)
- DevManView.exe (PID: 7312)
- DevManView.exe (PID: 7304)
- DevManView.exe (PID: 7296)
- DevManView.exe (PID: 7272)
- DevManView.exe (PID: 7264)
- DevManView.exe (PID: 7280)
- DevManView.exe (PID: 7248)
- DevManView.exe (PID: 7256)
- DevManView.exe (PID: 7216)
- DevManView.exe (PID: 7320)
- DevManView.exe (PID: 7440)
- extd.exe (PID: 3676)
- DevManView.exe (PID: 8024)
The sample compiled with english language support
- cpu_mac_spoofer.exe (PID: 5332)
Creates files or folders in the user directory
- cpu_mac_spoofer.exe (PID: 5332)
Reads the computer name
- tool.exe (PID: 5204)
- tool.exe (PID: 5064)
- tool.exe (PID: 3008)
- tool.exe (PID: 4188)
- tool.exe (PID: 736)
- tool.exe (PID: 6244)
- tool.exe (PID: 6728)
- tool.exe (PID: 2656)
- tool.exe (PID: 2984)
- tool.exe (PID: 4464)
- tool.exe (PID: 4212)
- tool.exe (PID: 5228)
- tool.exe (PID: 1188)
- tool.exe (PID: 4812)
- tool.exe (PID: 4628)
- tool.exe (PID: 5608)
- tool.exe (PID: 2772)
- tool.exe (PID: 1240)
- tool.exe (PID: 1660)
- tool.exe (PID: 6112)
- tool.exe (PID: 4996)
- tool.exe (PID: 4212)
- tool.exe (PID: 6728)
- tool.exe (PID: 4696)
- tool.exe (PID: 1348)
- tool.exe (PID: 720)
- tool.exe (PID: 2268)
- tool.exe (PID: 6476)
- tool.exe (PID: 6728)
- tool.exe (PID: 4696)
- tool.exe (PID: 2236)
- tool.exe (PID: 7156)
- DeviceCleanupCmd.exe (PID: 5960)
- DriveCleanup.exe (PID: 3180)
- DevManView.exe (PID: 968)
- DevManView.exe (PID: 4180)
- DevManView.exe (PID: 5936)
- DevManView.exe (PID: 5984)
- DevManView.exe (PID: 7176)
- DevManView.exe (PID: 5124)
- DevManView.exe (PID: 4068)
- DevManView.exe (PID: 7184)
- DevManView.exe (PID: 7232)
- DevManView.exe (PID: 7264)
- DevManView.exe (PID: 7288)
- DevManView.exe (PID: 7312)
- DevManView.exe (PID: 7304)
- DevManView.exe (PID: 7296)
- DevManView.exe (PID: 7272)
- DevManView.exe (PID: 7224)
- DevManView.exe (PID: 7240)
- DevManView.exe (PID: 7280)
- DevManView.exe (PID: 7248)
- DevManView.exe (PID: 7216)
- DevManView.exe (PID: 7256)
- DevManView.exe (PID: 7320)
- DevManView.exe (PID: 7440)
- DevManView.exe (PID: 8024)
Create files in a temporary directory
- load.exe (PID: 4040)
- os_cleaner_two.exe (PID: 632)
- cpu_mac_spoofer.exe (PID: 5332)
- load.exe (PID: 780)
- mac.exe (PID: 1512)
- Volume.exe (PID: 6576)
- FIXusrTEMPv6.exe (PID: 1512)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 856)
- WMIC.exe (PID: 5984)
- WMIC.exe (PID: 1348)
Disables trace logs
- netsh.exe (PID: 1012)
- netsh.exe (PID: 1128)
NirSoft software is detected
- DevManView.exe (PID: 4180)
- DevManView.exe (PID: 968)
- DevManView.exe (PID: 5984)
- DevManView.exe (PID: 4068)
- DevManView.exe (PID: 5936)
- DevManView.exe (PID: 5124)
- DevManView.exe (PID: 7176)
- DevManView.exe (PID: 7216)
- DevManView.exe (PID: 7224)
- DevManView.exe (PID: 7184)
- DevManView.exe (PID: 7256)
- DevManView.exe (PID: 7264)
- DevManView.exe (PID: 7232)
- DevManView.exe (PID: 7240)
- DevManView.exe (PID: 7248)
- DevManView.exe (PID: 7272)
- DevManView.exe (PID: 7304)
- DevManView.exe (PID: 7312)
- DevManView.exe (PID: 7320)
- DevManView.exe (PID: 7288)
- DevManView.exe (PID: 7280)
- DevManView.exe (PID: 7296)
- DevManView.exe (PID: 7440)
- DevManView.exe (PID: 8024)
Checks proxy server information
- slui.exe (PID: 6576)
Reads the software policy settings
- slui.exe (PID: 6576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:03:19 14:08:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | classify_spoofer-main/ |
Total processes
316
Monitored processes
180
Malicious processes
9
Suspicious processes
37
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\WINDOWS\sysnative\cmd" /c "C:\Users\admin\AppData\Local\Temp\E793.tmp\E794.tmp\E795.bat C:\Users\admin\AppData\Roaming\dump\mac.exe" | C:\Windows\System32\cmd.exe | — | mac.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Users\admin\Desktop\os_cleaner_two.exe" | C:\Users\admin\Desktop\os_cleaner_two.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 644 | reg delete HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\UserAssist /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | tool.exe /BLC "Default string" | C:\Users\admin\AppData\Roaming\dump\tool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 216 Modules
| |||||||||||||||
| 720 | C:\WINDOWS\system32\cmd.exe /c RMDIR /S /Q C:\Users\%username%\AppData\Local\VALORANT | C:\Windows\System32\cmd.exe | — | valorant_cleaner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
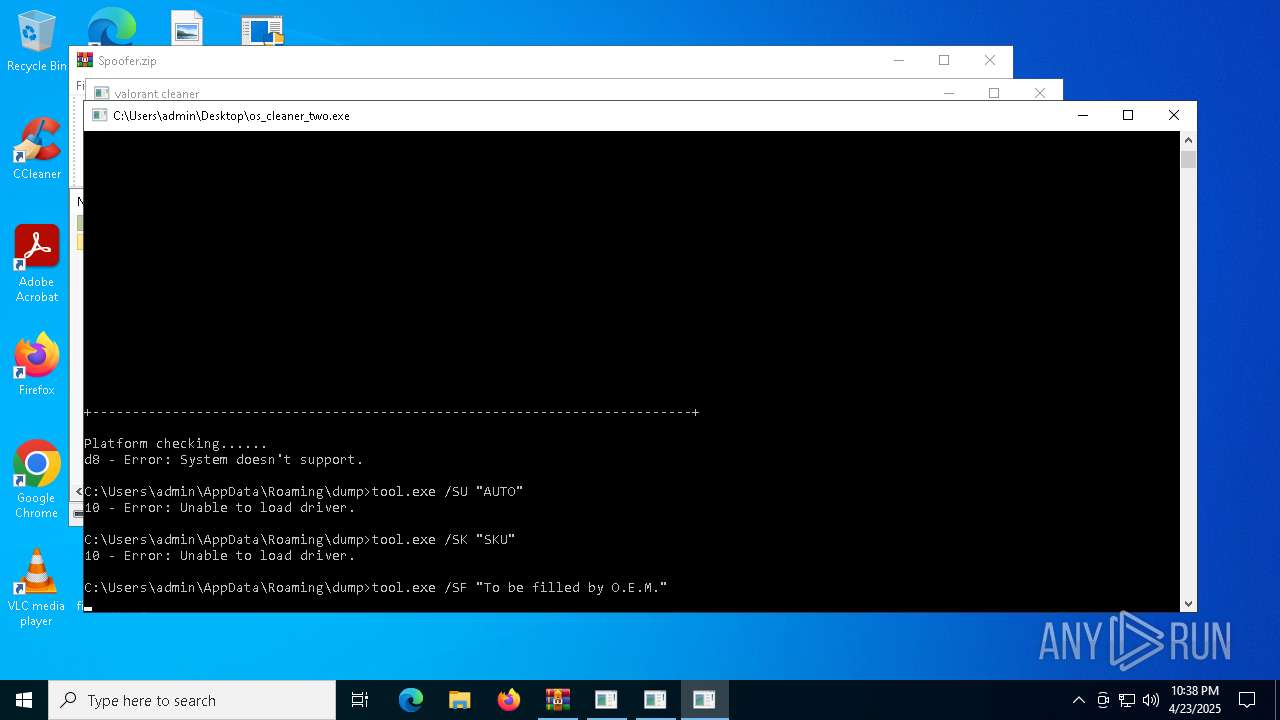
| 736 | tool.exe /SU "AUTO" | C:\Users\admin\AppData\Roaming\dump\tool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 216 Modules
| |||||||||||||||
| 736 | Volumeid64.exe E: 0664-7001 | C:\Users\admin\AppData\Roaming\dump\Volumeid64.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Set disk volume id Exit code: 1 Version: 2.1 Modules
| |||||||||||||||
| 780 | "load.exe" | C:\Users\admin\AppData\Roaming\dump\load.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 216 Modules
| |||||||||||||||
| 780 | Volumeid64.exe F: 4989-6601 | C:\Users\admin\AppData\Roaming\dump\Volumeid64.exe | — | cmd.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Set disk volume id Exit code: 1 Version: 2.1 Modules
| |||||||||||||||
| 856 | wmic nic where physicaladapter=true get deviceid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
76 816
Read events
76 762
Write events
17
Delete events
37
Modification events
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Spoofer.zip | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1168) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5256) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4d36e972-e325-11ce-bfc1-08002be10318}\0010 |
| Operation: | write | Name: | NetworkAddress |
Value: 82B4D48519B7 | |||
| (PID) Process: | (5204) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4d36e972-e325-11ce-bfc1-08002be10318}\0010 |
| Operation: | write | Name: | PnPCapabilities |
Value: 24 | |||
Executable files
15
Suspicious files
6
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Local\Temp\D747.tmp\D748.tmp\D749.bat | text | |
MD5:05A549C77B6F9502328216ADC3A07D17 | SHA256:2390A95953E364F99CEC3C7FE535FCAA9BBD9A8F4A946DB4FC08FD23340EA55D | |||
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Local\Temp\D747.tmp\D748.tmp\extd.exe | executable | |
MD5:C14CE13AB09B4829F67A879D735A10A1 | SHA256:EF2699BA677FCDB8A3B70A711A59A5892D8439E108E3AC4D27A7F946C4D01A4A | |||
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Roaming\dump\DriveCleanup.exe | executable | |
MD5:6F6D0FD357DDD2661F0035F3440C0EC4 | SHA256:7DF319E036EB145DC9ADF9AD0AFC03EB4D18D72851CBCCA8A00C574BCA86FC78 | |||
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Roaming\dump\convert.bat | text | |
MD5:9154D12F6AE25EEE3A2350A4D419E51C | SHA256:9BFCE540D339A8371E6EBBF7CD2EF8CE6DEAC8B179061D74F520269317D40409 | |||
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Roaming\dump\load.exe | executable | |
MD5:5700CABC6BF4E6AEA2F3535FE34F14E2 | SHA256:18C0DA701463F2F99E5B8C91D2AA6315B4538960FE883A6BFB519F623FC2696B | |||
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Roaming\dump\devcom.bat | text | |
MD5:3AE95F1361B860B03D0704A1E153E0F9 | SHA256:468D8B4AF93B555A261E9B3909526F86994D0555C494F5A2B560504142BD74EF | |||
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Roaming\dump\DevManView.cfg | text | |
MD5:F71E8C379C76568CE0472A9F94F399E5 | SHA256:43788AA272943CA270314FD0EC0D2BF9F30179093001FE2D846162C51F8A3DB7 | |||
| 2236 | Volumeid64.exe | \Device\HarddiskVolume2 | — | |
MD5:— | SHA256:— | |||
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Roaming\dump\NO-RUNdevcon.exe | executable | |
MD5:D153A0BC6F0476457B56FC38795DEA01 | SHA256:DF048DF347A738B6ADDEC6F3FD65C73E371D0E11E2DC02F88F8EF307B964E1B7 | |||
| 5332 | cpu_mac_spoofer.exe | C:\Users\admin\AppData\Roaming\dump\amifldrv64.sys | executable | |
MD5:785045F8B25CD2E937DDC6B09DEBE01A | SHA256:37073E42FFA0322500F90CD7E3C8D02C4CDD695D31C77E81560ABEC20BFB68BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
54
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4024 | RUXIMICS.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4024 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
472 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 13.95.31.18:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
472 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
472 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
472 | SIHClient.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
472 | SIHClient.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
472 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4024 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4024 | RUXIMICS.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4024 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2196 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
2196 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
472 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |