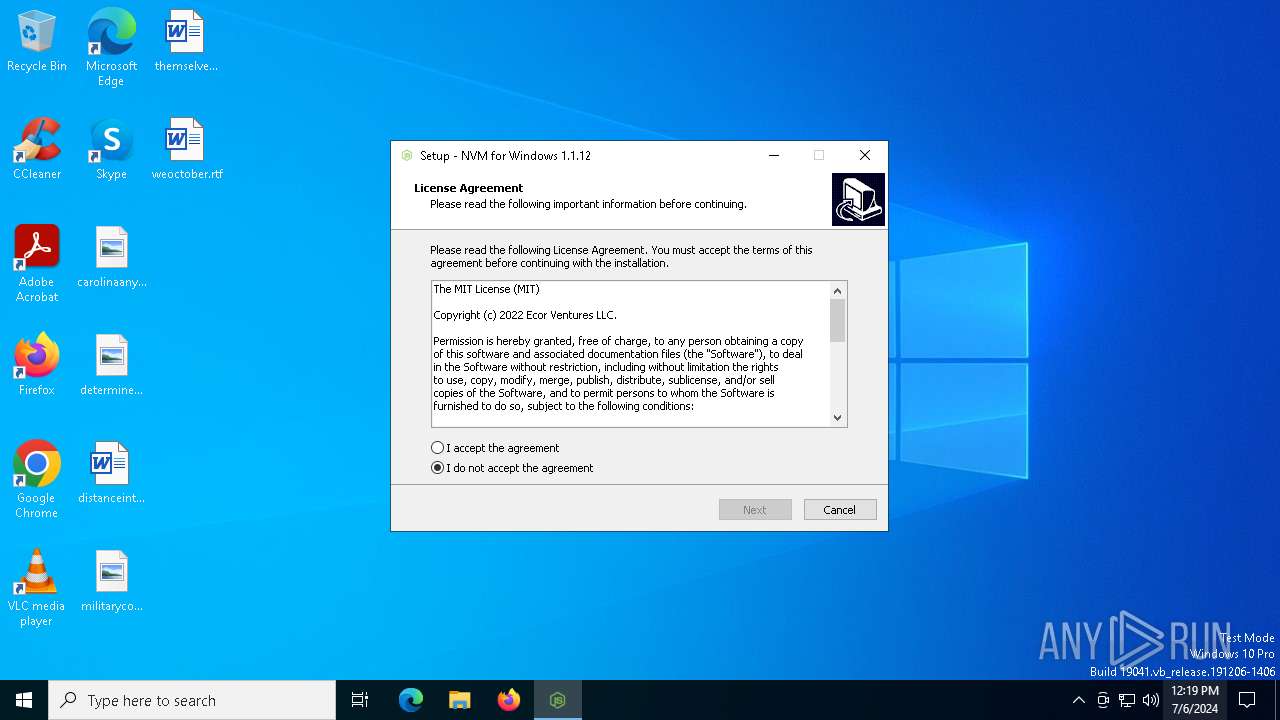
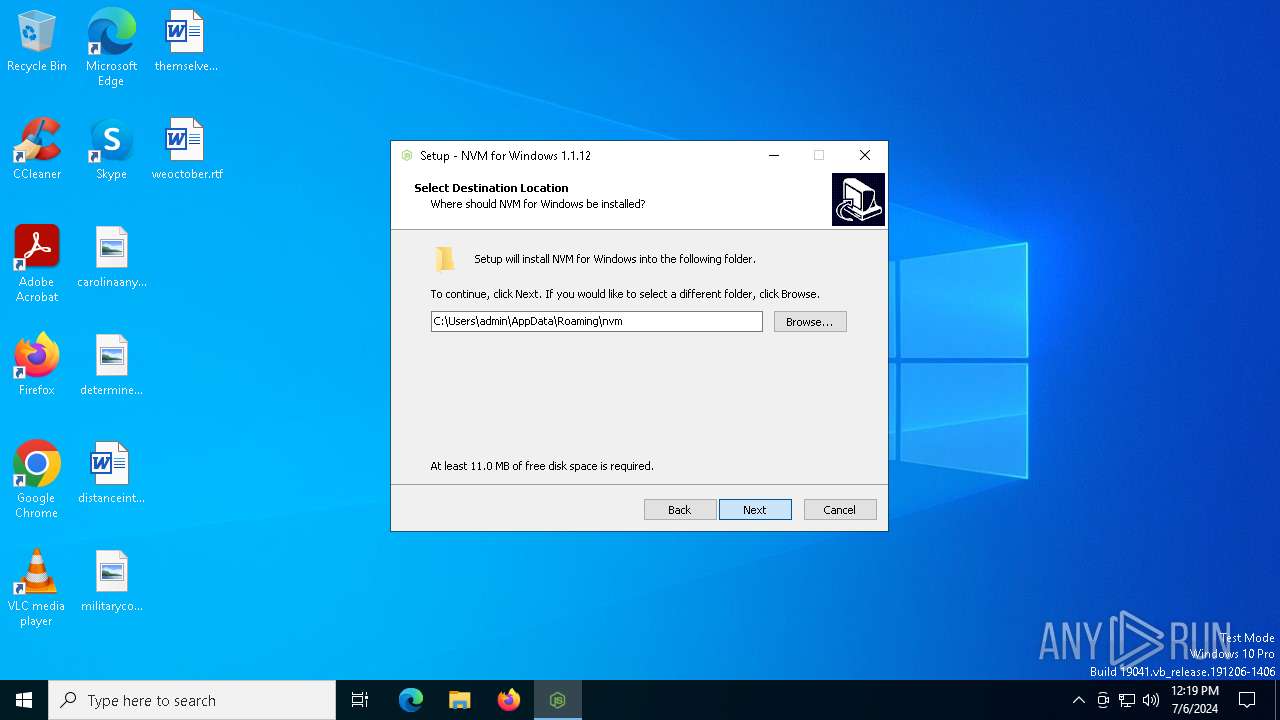
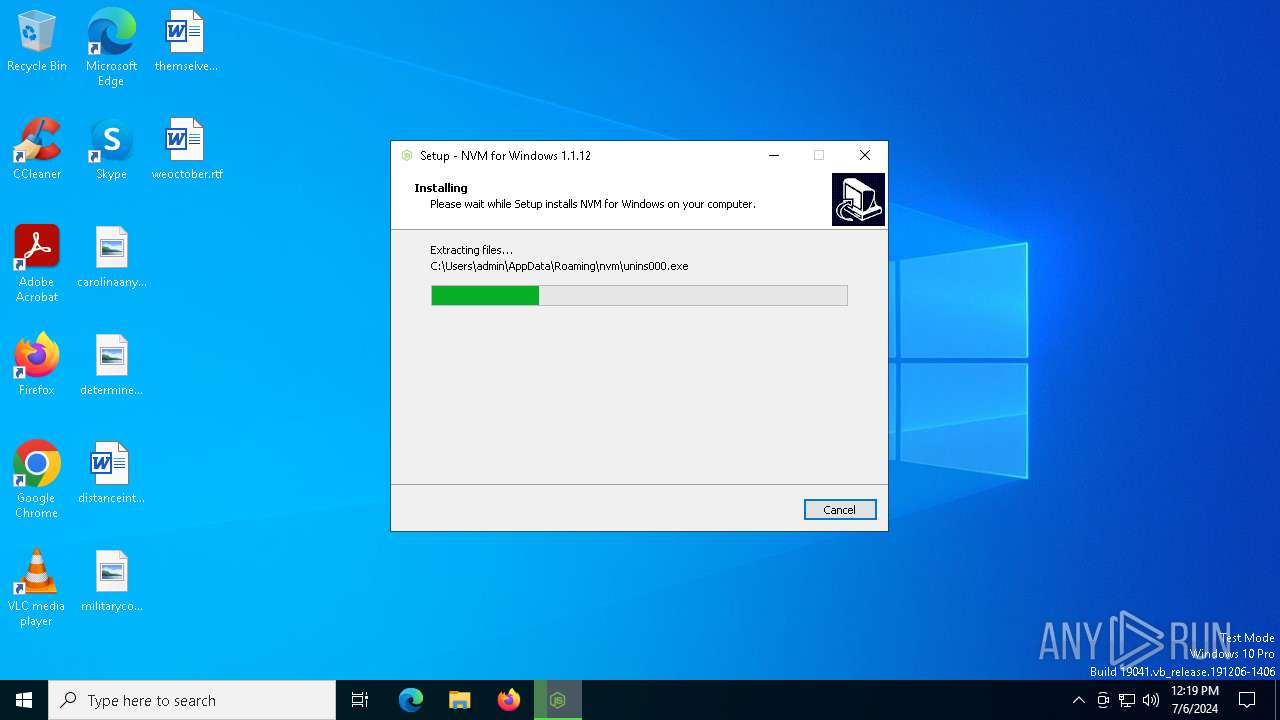
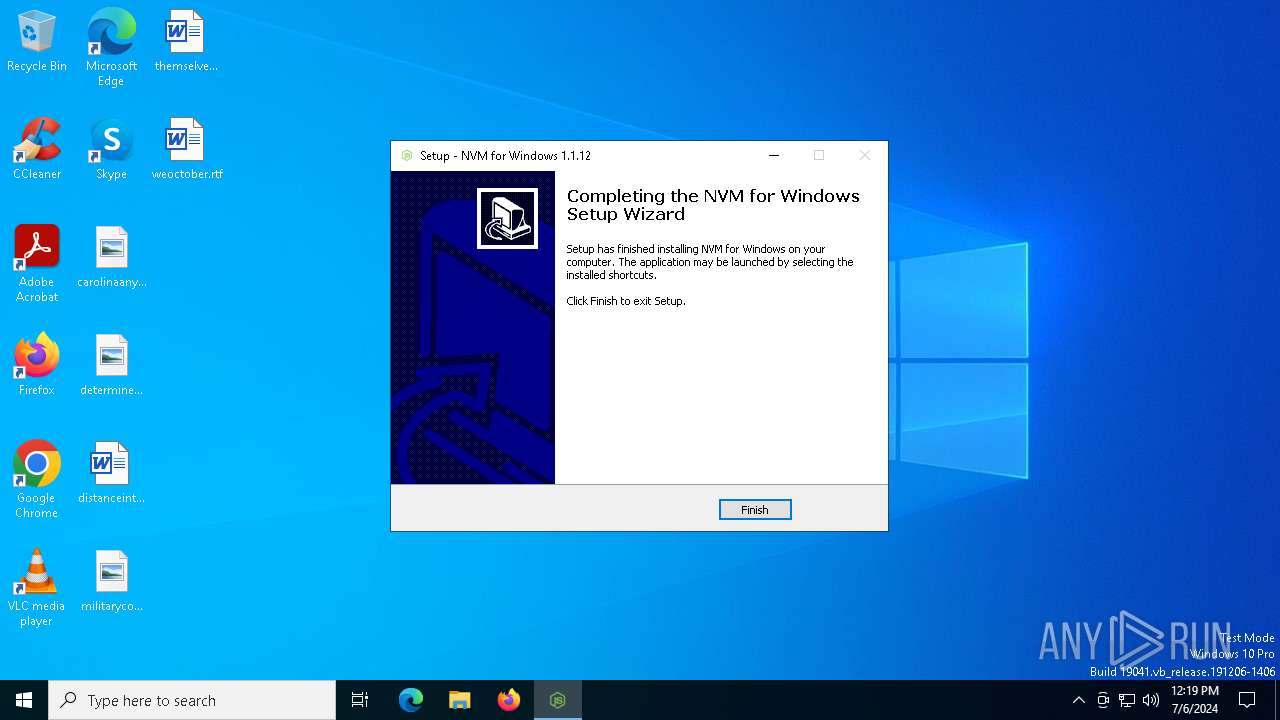
| File name: | nvm-setup.exe |
| Full analysis: | https://app.any.run/tasks/3d8a9cb9-a2b9-40a2-a798-c7b6b813ad48 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2024, 12:19:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1205D8871D0AC6EE7D7F94A7EC33C2DA |
| SHA1: | 2B777791DBECDC9403AD0D3F24F38916607D23D2 |
| SHA256: | 41BE147A7715FAAA74EE404CE920AA7D941F5D6C3B7EDBB0FA097A656AA1A23B |
| SSDEEP: | 98304:7+QqZ8fRSkxloldGXA9BQx1NKXjo7SV4SaogdNPIw3l2+Bm8Ptr+00Dm0MMZICzh:fo5mcjic |
MALICIOUS
Drops the executable file immediately after the start
- nvm-setup.exe (PID: 4724)
- nvm-setup.exe (PID: 6360)
- nvm-setup.tmp (PID: 6468)
SUSPICIOUS
Executable content was dropped or overwritten
- nvm-setup.exe (PID: 4724)
- nvm-setup.exe (PID: 6360)
- nvm-setup.tmp (PID: 6468)
Reads security settings of Internet Explorer
- nvm-setup.tmp (PID: 4544)
Reads the date of Windows installation
- nvm-setup.tmp (PID: 4544)
Reads the Windows owner or organization settings
- nvm-setup.tmp (PID: 6468)
Searches for installed software
- nvm-setup.tmp (PID: 6468)
Starts CMD.EXE for commands execution
- nvm-setup.tmp (PID: 6468)
INFO
Checks supported languages
- nvm-setup.exe (PID: 4724)
- nvm-setup.tmp (PID: 4544)
- nvm-setup.exe (PID: 6360)
- nvm-setup.tmp (PID: 6468)
Reads the computer name
- nvm-setup.tmp (PID: 4544)
- nvm-setup.tmp (PID: 6468)
Create files in a temporary directory
- nvm-setup.exe (PID: 4724)
- nvm-setup.exe (PID: 6360)
- nvm-setup.tmp (PID: 6468)
Creates a software uninstall entry
- nvm-setup.tmp (PID: 6468)
Process checks computer location settings
- nvm-setup.tmp (PID: 4544)
Creates files in the program directory
- nvm-setup.tmp (PID: 6468)
Creates files or folders in the user directory
- nvm-setup.tmp (PID: 6468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 09:48:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 48640 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.12.0 |
| ProductVersionNumber: | 1.1.12.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Ecor Ventures LLC |
| FileDescription: | Node version manager for Windows |
| FileVersion: | 1.1.12 |
| LegalCopyright: | Copyright © 2018-2023 Ecor Ventures LLC, Corey Butler, and contributors. |
| OriginalFileName: | |
| ProductName: | nvm |
| ProductVersion: | 1.1.12 |
Total processes
156
Monitored processes
20
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3868 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3908 | "C:\WINDOWS\system32\cmd.exe" /C node "C:\Users\admin\AppData\Local\Temp\is-HEINH.tmp\nvm_check.js" > "C:\Users\admin\AppData\Local\Temp\is-HEINH.tmp\nvm_node_check.txt" | C:\Windows\System32\cmd.exe | — | nvm-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4052 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4544 | "C:\Users\admin\AppData\Local\Temp\is-QR1NS.tmp\nvm-setup.tmp" /SL5="$802D0,4963729,791040,C:\Users\admin\AppData\Local\Temp\nvm-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-QR1NS.tmp\nvm-setup.tmp | — | nvm-setup.exe | |||||||||||
User: admin Company: Ecor Ventures LLC Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4724 | "C:\Users\admin\AppData\Local\Temp\nvm-setup.exe" | C:\Users\admin\AppData\Local\Temp\nvm-setup.exe | explorer.exe | ||||||||||||
User: admin Company: Ecor Ventures LLC Integrity Level: MEDIUM Description: Node version manager for Windows Exit code: 0 Version: 1.1.12 Modules
| |||||||||||||||
| 4944 | "C:\WINDOWS\system32\cmd.exe" /C node "C:\Users\admin\AppData\Local\Temp\is-HEINH.tmp\nvm_check.js" > "C:\Users\admin\AppData\Local\Temp\is-HEINH.tmp\nvm_node_check.txt" | C:\Windows\System32\cmd.exe | — | nvm-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5004 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 968
Read events
7 923
Write events
39
Delete events
6
Modification events
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 4419000013647BC39ECFDA01 | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: BB8F166208F37A7869073D9850372B8E81096C4507DC40E5A287CEB5ED476978 | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Roaming\nvm\nvm.exe | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 9959264C70DF74E88851B4DC07FDE6DC0CE3CCEC099F7BDDFAD5F58EFEE9A725 | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\40078385-F676-4C61-9A9C-F9028599D6D3_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.1.2 | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\40078385-F676-4C61-9A9C-F9028599D6D3_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Roaming\nvm | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\40078385-F676-4C61-9A9C-F9028599D6D3_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Roaming\nvm\ | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\40078385-F676-4C61-9A9C-F9028599D6D3_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: NVM for Windows | |||
| (PID) Process: | (6468) nvm-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\40078385-F676-4C61-9A9C-F9028599D6D3_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
7
Suspicious files
3
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\install.cmd | text | |
MD5:A664046CEF542C8C08F5F6A14ABFCA83 | SHA256:BF99D720A62A7838C0569C5F8A4925AB8C3ACE00387EC3BA89129C36704A8F7D | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\unins000.exe | executable | |
MD5:58C264F91DAF445EAB1D33CD76AA53C2 | SHA256:18EF332CA725A4148E38556B9038827919A39942F1BC45F973C9E4FEFCAE9953 | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\elevate.cmd | text | |
MD5:E0A963AA9273275A3DA167C0D169490D | SHA256:792D6A485D26B3AE1C926D1D4915E5EAF9A40113AFD623212D1A9591E56BB1D5 | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\is-DK1JC.tmp | image | |
MD5:2AB2CB737FB0BE9751EEE4729D5AB140 | SHA256:FE092FD3556AC40FA2E75CDB7578DC6B9FEA4449EC707D013ECF765E896B8E9A | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\is-SCM2P.tmp | text | |
MD5:7978330486AA4946BB3079CC9F0F0AFA | SHA256:6F54EDD8BAB74D5C722EC00AB2F1FADD38CEB1DDCA5AED60A400A6DD846EEFEF | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\is-82S6F.tmp | text | |
MD5:9C5E28535C95D143C7F76432D01FE7DF | SHA256:76A89F12D74FE66448499C5ADE1F66D0EDB991AF0BBE6D3E2818353F6A7E6A6F | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\unsetuserenv.vbs | text | |
MD5:7978330486AA4946BB3079CC9F0F0AFA | SHA256:6F54EDD8BAB74D5C722EC00AB2F1FADD38CEB1DDCA5AED60A400A6DD846EEFEF | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\is-IVSPR.tmp | executable | |
MD5:3CA84D1CC2425D431C0B7A6E56960561 | SHA256:09C0B24AE56D26CC2AA8C1D583E5C1E58E11C425B0E899EC3124C5551E8F4373 | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-HEINH.tmp\nvm_check.js | text | |
MD5:AC5BC22DFAE4BBE24B053597261A5322 | SHA256:010148603551308C10E6D1567E75329380DA6CEE96C0313EAE52C5C17ADD2C37 | |||
| 6468 | nvm-setup.tmp | C:\Users\admin\AppData\Roaming\nvm\is-BNJ7Q.tmp | text | |
MD5:E0A963AA9273275A3DA167C0D169490D | SHA256:792D6A485D26B3AE1C926D1D4915E5EAF9A40113AFD623212D1A9591E56BB1D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
62
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
4636 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
6212 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
2416 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3508 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3508 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2224 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4656 | SearchApp.exe | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4636 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4636 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
528 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 184.30.17.189:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 52.111.236.23:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |