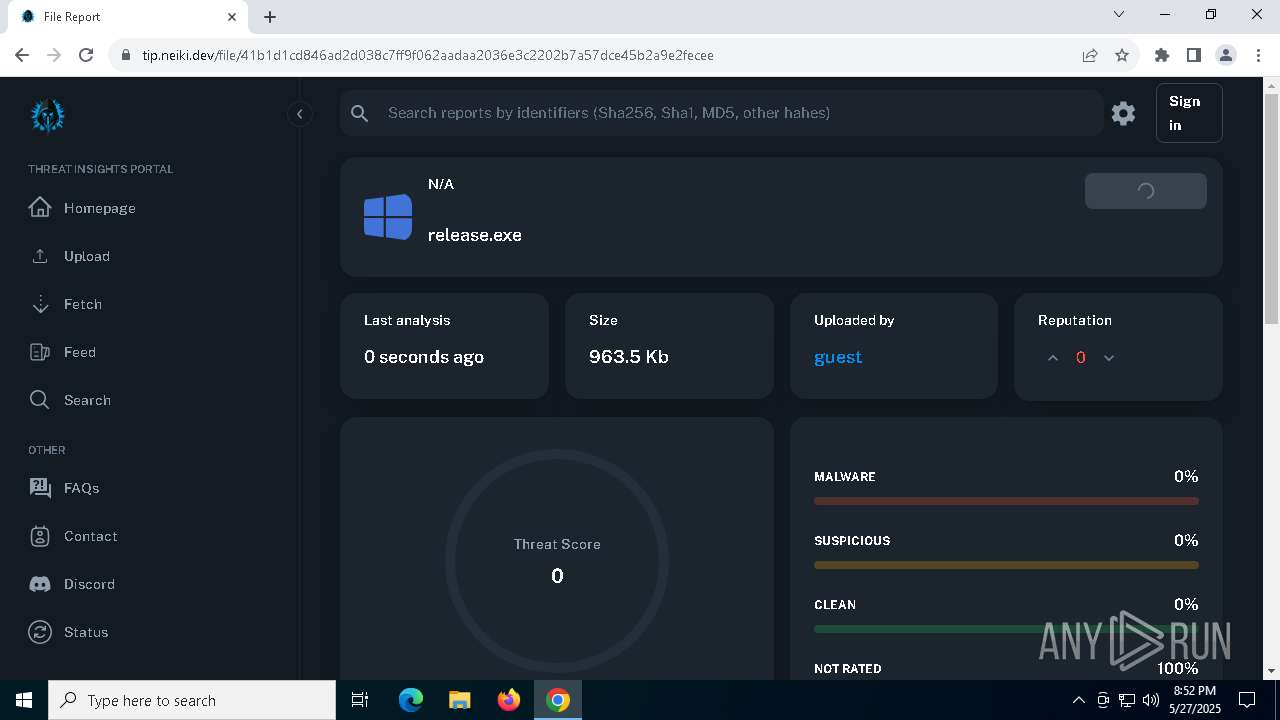
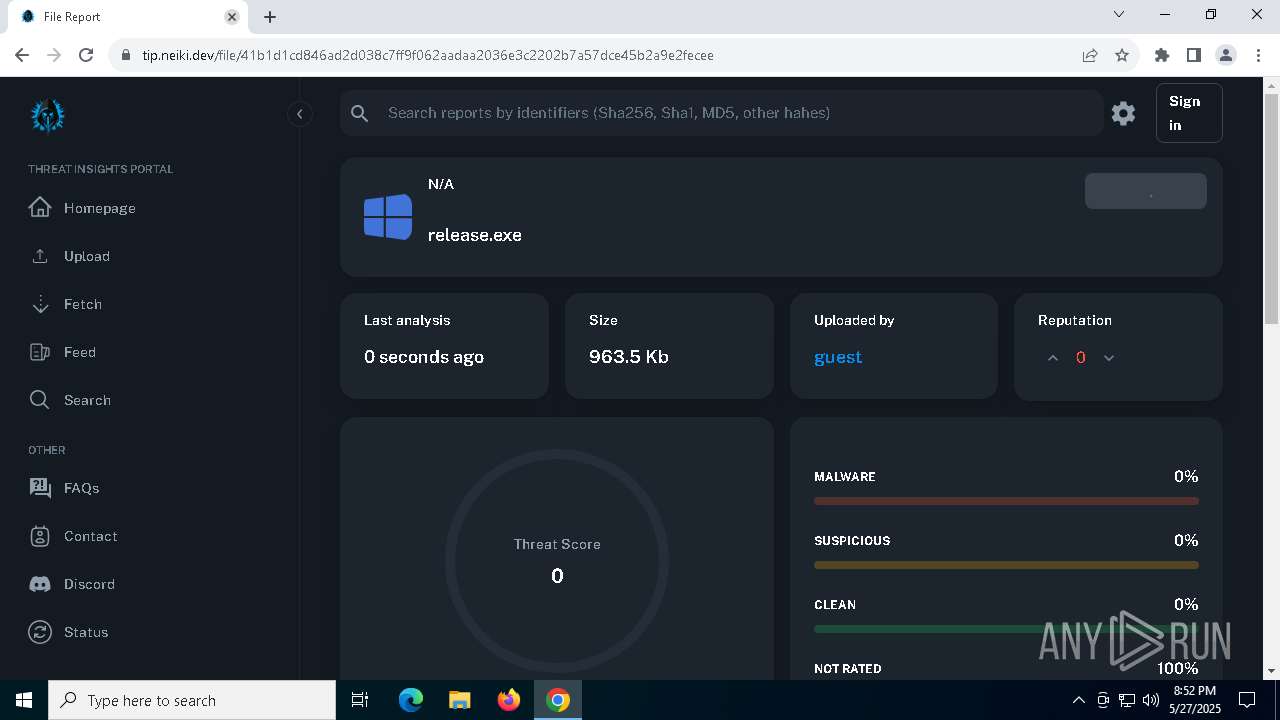
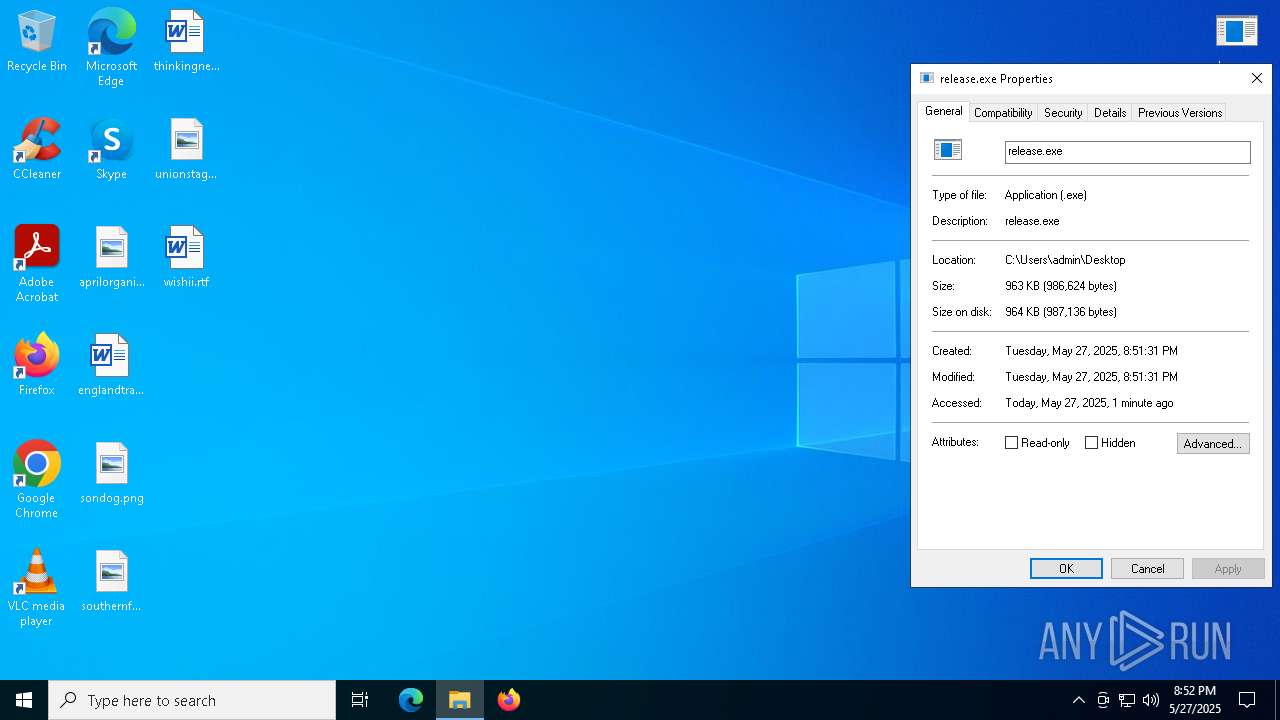
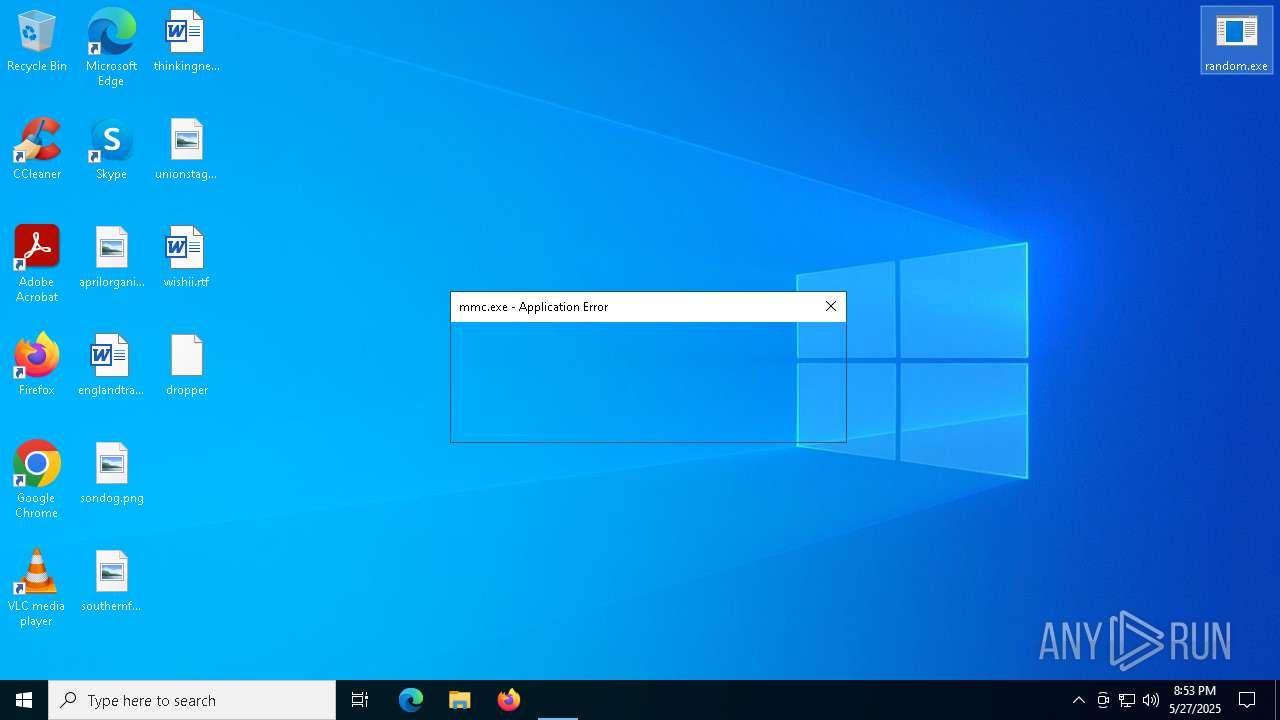
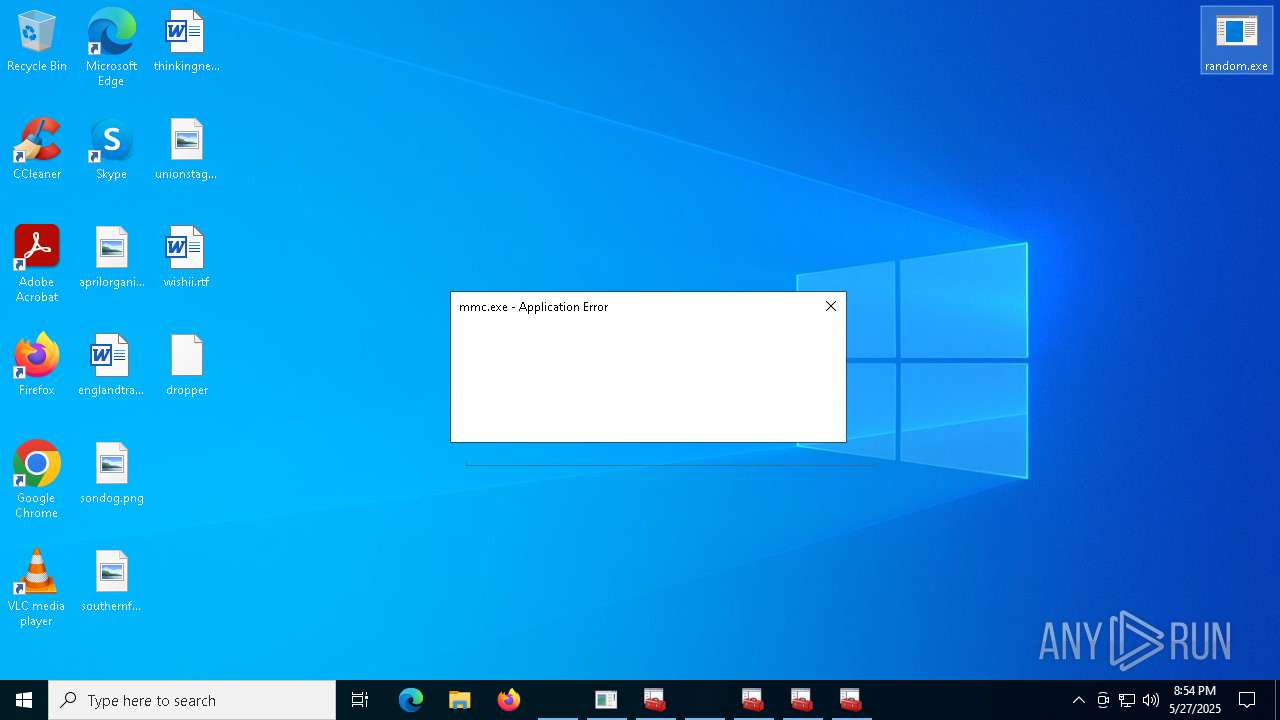
| File name: | release.exe |
| Full analysis: | https://app.any.run/tasks/5c741676-d5f5-40a1-a078-d2b9c46088ae |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 20:51:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | EDC85FCBD8F79E61687081AD99C9DB93 |
| SHA1: | B44643D580A9DBB10F66409F84DB0FD43678F3A4 |
| SHA256: | 41B1D1CD846AD2D038C7FF9F062AADAA2036E3C2202B7A57DCE45B2A9E2FECEE |
| SSDEEP: | 49152:BFgBnQWSkg1MU907V+0CjbgiG+vITnTpUlZvEl6wKNm2b/yqK:BFgBnQWSH19NblG+oEJElkAxV |
MALICIOUS
No malicious indicators.SUSPICIOUS
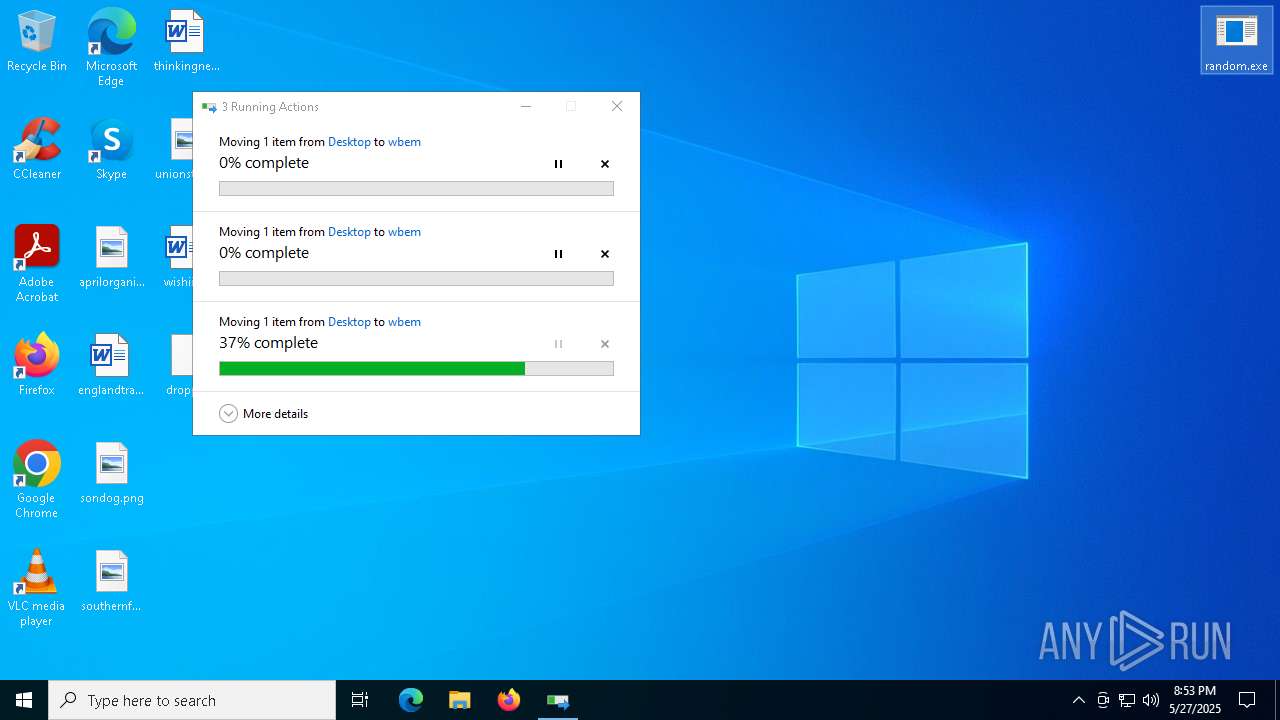
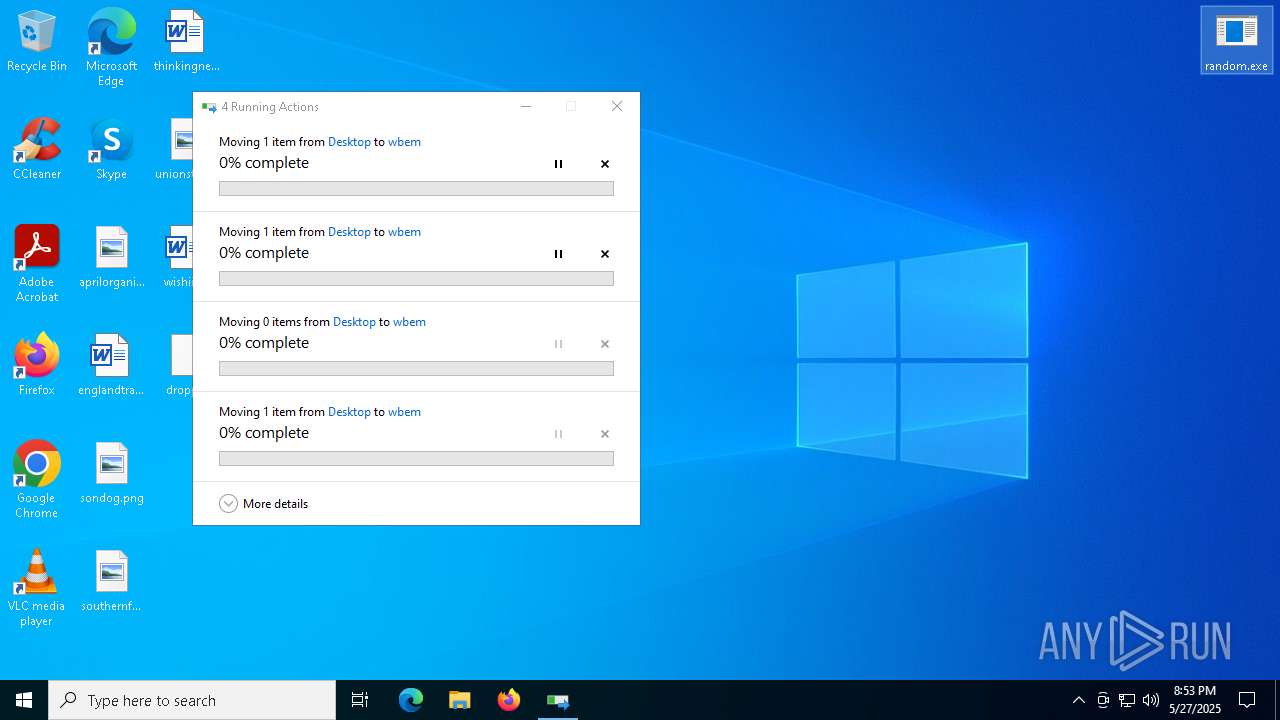
Process drops legitimate windows executable
- release.exe (PID: 6620)
- release.exe (PID: 3896)
- random.exe (PID: 4152)
- random.exe (PID: 10280)
- random.exe (PID: 11032)
- random.exe (PID: 10444)
- random.exe (PID: 10480)
- random.exe (PID: 5984)
- random.exe (PID: 10796)
- random.exe (PID: 10344)
- random.exe (PID: 9336)
- random.exe (PID: 11284)
- random.exe (PID: 11568)
- random.exe (PID: 10944)
- random.exe (PID: 2244)
- random.exe (PID: 11120)
Executable content was dropped or overwritten
- release.exe (PID: 6620)
- dllhost.exe (PID: 7300)
- release.exe (PID: 7460)
- dllhost.exe (PID: 7284)
- release.exe (PID: 4740)
- release.exe (PID: 3896)
- random.exe (PID: 6940)
- random.exe (PID: 4152)
- dllhost.exe (PID: 9124)
- random.exe (PID: 10796)
- random.exe (PID: 11032)
- random.exe (PID: 10480)
- random.exe (PID: 5984)
- random.exe (PID: 10444)
- random.exe (PID: 10280)
- random.exe (PID: 10344)
- random.exe (PID: 9336)
- random.exe (PID: 11284)
- random.exe (PID: 12172)
- random.exe (PID: 10604)
- random.exe (PID: 12252)
- random.exe (PID: 11220)
- random.exe (PID: 10716)
- random.exe (PID: 9688)
- random.exe (PID: 9136)
- random.exe (PID: 11568)
- random.exe (PID: 12040)
- random.exe (PID: 12168)
- random.exe (PID: 9388)
- random.exe (PID: 12284)
- random.exe (PID: 10924)
- random.exe (PID: 10944)
- random.exe (PID: 11560)
- random.exe (PID: 12216)
- random.exe (PID: 9600)
- random.exe (PID: 11120)
- random.exe (PID: 2244)
- random.exe (PID: 8860)
Reads security settings of Internet Explorer
- release.exe (PID: 6620)
- release.exe (PID: 3896)
Reads the date of Windows installation
- release.exe (PID: 6620)
- release.exe (PID: 3896)
Drops a system driver (possible attempt to evade defenses)
- release.exe (PID: 7460)
- release.exe (PID: 4740)
- random.exe (PID: 6940)
- random.exe (PID: 9136)
- random.exe (PID: 12172)
- random.exe (PID: 12252)
- random.exe (PID: 10604)
- random.exe (PID: 11220)
- random.exe (PID: 9688)
- random.exe (PID: 10716)
- random.exe (PID: 12040)
- random.exe (PID: 10924)
- random.exe (PID: 12284)
- random.exe (PID: 12216)
- random.exe (PID: 9600)
- random.exe (PID: 11560)
- random.exe (PID: 12168)
- random.exe (PID: 9388)
- random.exe (PID: 8860)
Hides command output
- cmd.exe (PID: 7660)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 7848)
- cmd.exe (PID: 7968)
Stops a currently running service
- sc.exe (PID: 7728)
Starts SC.EXE for service management
- cmd.exe (PID: 7660)
- cmd.exe (PID: 7848)
- cmd.exe (PID: 7968)
- cmd.exe (PID: 7756)
Windows service management via SC.EXE
- sc.exe (PID: 7820)
- sc.exe (PID: 8032)
Creates a new Windows service
- sc.exe (PID: 7940)
Starts CMD.EXE for commands execution
- release.exe (PID: 7460)
INFO
Reads the machine GUID from the registry
- release.exe (PID: 6620)
- release.exe (PID: 3896)
Checks supported languages
- release.exe (PID: 6620)
- release.exe (PID: 7460)
- release.exe (PID: 3896)
- release.exe (PID: 4740)
- random.exe (PID: 6940)
- random.exe (PID: 4728)
- random.exe (PID: 7884)
- random.exe (PID: 7300)
- random.exe (PID: 8056)
- random.exe (PID: 7152)
- random.exe (PID: 7980)
- random.exe (PID: 4152)
- random.exe (PID: 4164)
- random.exe (PID: 8100)
- random.exe (PID: 7476)
- random.exe (PID: 8128)
- random.exe (PID: 732)
- random.exe (PID: 5436)
- random.exe (PID: 5308)
- random.exe (PID: 4188)
- random.exe (PID: 2268)
- random.exe (PID: 6676)
- random.exe (PID: 2772)
- random.exe (PID: 4464)
- random.exe (PID: 5332)
- random.exe (PID: 6652)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 7300)
- mmc.exe (PID: 7428)
- dllhost.exe (PID: 7284)
- mmc.exe (PID: 7660)
Reads the computer name
- release.exe (PID: 6620)
- release.exe (PID: 3896)
Checks transactions between databases Windows and Oracle
- release.exe (PID: 6620)
- release.exe (PID: 3896)
The sample compiled with english language support
- release.exe (PID: 6620)
- dllhost.exe (PID: 7300)
- release.exe (PID: 7460)
- dllhost.exe (PID: 7284)
- release.exe (PID: 3896)
- random.exe (PID: 4152)
- dllhost.exe (PID: 9124)
- random.exe (PID: 10280)
- random.exe (PID: 10796)
- random.exe (PID: 11032)
- random.exe (PID: 10480)
- random.exe (PID: 5984)
- random.exe (PID: 10444)
- random.exe (PID: 10344)
- random.exe (PID: 9336)
- random.exe (PID: 11284)
- random.exe (PID: 11568)
- random.exe (PID: 10944)
- random.exe (PID: 11120)
- random.exe (PID: 2244)
Reads Microsoft Office registry keys
- release.exe (PID: 6620)
- release.exe (PID: 3896)
Process checks computer location settings
- release.exe (PID: 6620)
- release.exe (PID: 3896)
Manual execution by a user
- chrome.exe (PID: 4844)
- release.exe (PID: 3896)
- random.exe (PID: 6940)
- random.exe (PID: 4152)
- random.exe (PID: 4164)
- random.exe (PID: 7152)
- random.exe (PID: 7300)
- random.exe (PID: 7884)
- random.exe (PID: 8056)
- random.exe (PID: 8100)
- random.exe (PID: 7980)
- random.exe (PID: 8128)
- random.exe (PID: 4728)
- random.exe (PID: 7476)
- random.exe (PID: 4464)
- random.exe (PID: 5436)
- random.exe (PID: 5308)
- random.exe (PID: 4188)
- random.exe (PID: 2268)
- random.exe (PID: 2772)
- random.exe (PID: 6676)
- random.exe (PID: 732)
- random.exe (PID: 3032)
- random.exe (PID: 7212)
- random.exe (PID: 2100)
- random.exe (PID: 6652)
- random.exe (PID: 5332)
- random.exe (PID: 1600)
- random.exe (PID: 7856)
- random.exe (PID: 5036)
- random.exe (PID: 6816)
- random.exe (PID: 7260)
- random.exe (PID: 2568)
- random.exe (PID: 2316)
- random.exe (PID: 7512)
- random.exe (PID: 664)
- random.exe (PID: 3132)
- random.exe (PID: 4988)
- random.exe (PID: 1052)
- random.exe (PID: 3304)
- random.exe (PID: 1020)
- random.exe (PID: 2896)
- random.exe (PID: 3480)
- random.exe (PID: 8316)
- random.exe (PID: 8644)
- random.exe (PID: 8636)
- random.exe (PID: 8808)
- random.exe (PID: 8652)
- random.exe (PID: 9024)
- random.exe (PID: 9064)
- random.exe (PID: 2040)
- random.exe (PID: 5796)
- random.exe (PID: 1276)
- random.exe (PID: 8804)
- random.exe (PID: 8404)
- random.exe (PID: 8816)
- random.exe (PID: 1196)
- random.exe (PID: 8900)
- random.exe (PID: 2600)
- random.exe (PID: 8380)
- random.exe (PID: 7376)
- random.exe (PID: 8368)
- random.exe (PID: 9080)
- random.exe (PID: 9000)
- random.exe (PID: 7700)
- random.exe (PID: 9228)
- random.exe (PID: 8776)
- random.exe (PID: 9392)
- random.exe (PID: 9464)
- random.exe (PID: 9528)
- random.exe (PID: 8720)
- random.exe (PID: 8568)
- random.exe (PID: 8540)
- random.exe (PID: 8416)
- random.exe (PID: 7612)
- random.exe (PID: 9012)
- random.exe (PID: 9748)
- random.exe (PID: 9904)
- random.exe (PID: 9888)
- random.exe (PID: 10144)
- random.exe (PID: 10136)
- random.exe (PID: 10280)
- random.exe (PID: 10592)
- random.exe (PID: 10524)
- random.exe (PID: 10624)
- random.exe (PID: 10796)
- random.exe (PID: 10788)
- random.exe (PID: 11032)
- random.exe (PID: 9588)
- random.exe (PID: 9648)
- random.exe (PID: 9656)
- random.exe (PID: 5984)
- random.exe (PID: 10480)
- random.exe (PID: 10344)
- random.exe (PID: 10444)
- random.exe (PID: 9336)
- random.exe (PID: 10512)
- random.exe (PID: 11284)
- random.exe (PID: 11992)
- random.exe (PID: 11568)
- random.exe (PID: 11384)
- random.exe (PID: 12244)
- random.exe (PID: 10164)
- random.exe (PID: 10944)
- random.exe (PID: 11120)
- random.exe (PID: 4032)
- random.exe (PID: 2244)
- random.exe (PID: 7748)
- random.exe (PID: 9316)
Application launched itself
- chrome.exe (PID: 4844)
Reads the software policy settings
- slui.exe (PID: 5024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:26 19:47:06+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 295936 |
| InitializedDataSize: | 697344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1a724 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
625
Monitored processes
308
Malicious processes
1
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\WINDOWS\system32\mmc.exe" "C:\Windows\System32\WmiMgmt.msc" | C:\Windows\System32\mmc.exe | — | random.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | "C:\Users\admin\Desktop\random.exe" | C:\Users\admin\Desktop\random.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 732 | "C:\Users\admin\Desktop\random.exe" | C:\Users\admin\Desktop\random.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\Desktop\random.exe" | C:\Users\admin\Desktop\random.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\Desktop\random.exe" | C:\Users\admin\Desktop\random.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1056 | "C:\WINDOWS\system32\mmc.exe" "C:\Windows\System32\WmiMgmt.msc" | C:\Windows\System32\mmc.exe | — | random.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1176 | "C:\WINDOWS\system32\mmc.exe" "C:\Windows\System32\WmiMgmt.msc" | C:\Windows\System32\mmc.exe | random.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\Desktop\random.exe" | C:\Users\admin\Desktop\random.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2516 --field-trial-handle=1412,i,9922085217746745380,5377115346004076997,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\Desktop\random.exe" | C:\Users\admin\Desktop\random.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
95 880
Read events
95 674
Write events
201
Delete events
5
Modification events
| (PID) Process: | (6620) release.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msc\OpenWithProgids |
| Operation: | write | Name: | MSCFile |
Value: | |||
| (PID) Process: | (4844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4844) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4844) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
| (PID) Process: | (8008) chrome.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (8008) chrome.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0E000000040000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (8008) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
Executable files
39
Suspicious files
114
Text files
53
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10f510.TMP | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10f510.TMP | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10f520.TMP | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10f520.TMP | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10f520.TMP | — | |
MD5:— | SHA256:— | |||
| 4844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
58
DNS requests
49
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8048 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8048 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6240 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6240 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6240 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
6240 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |